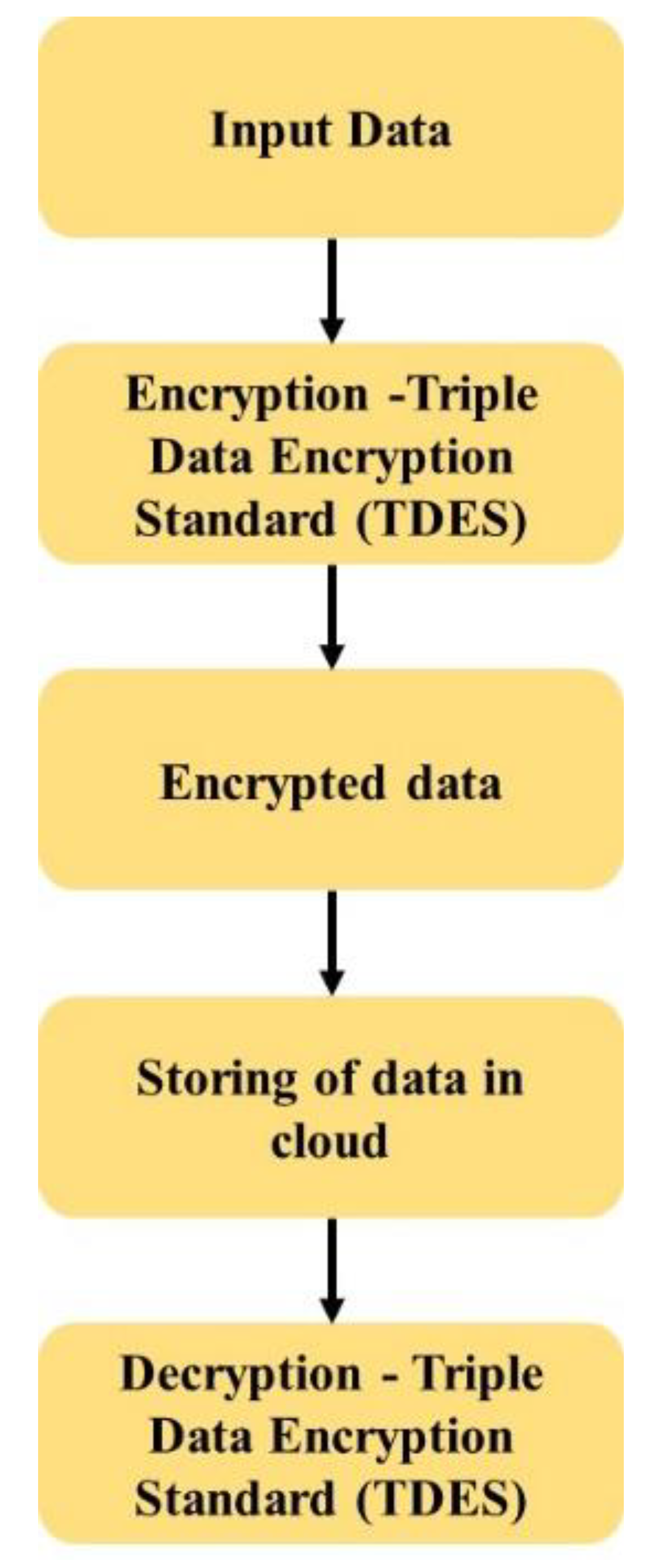
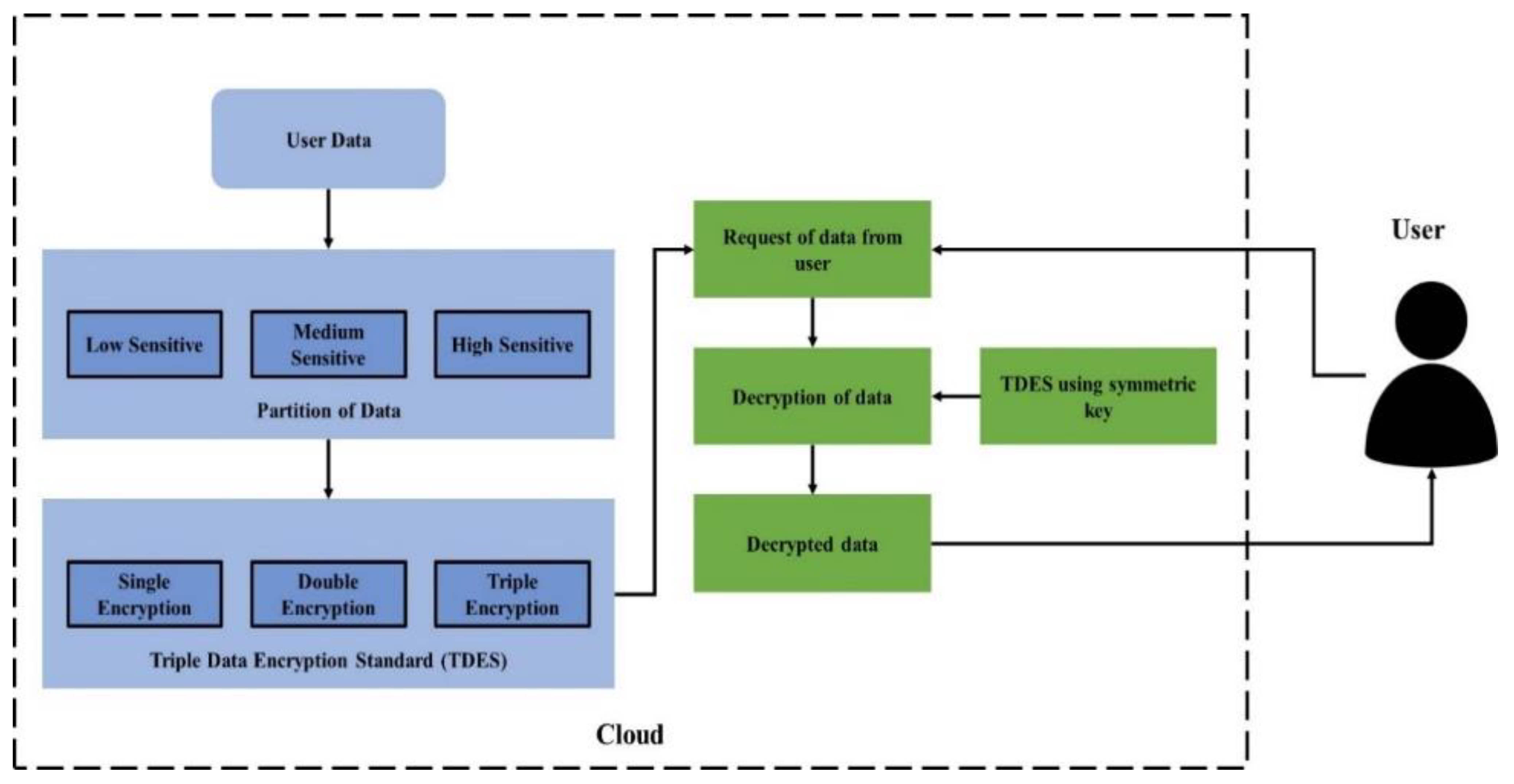
The Cloud includes many advantages but still it has limitations in providing the security for storage of big data. Various existing methods were developed to provide the security for big data storage in the Cloud. The existing privacy preserving approaches showed several drawbacks such as a lack of data privacy and accurate data analysis, a lack of efficiency of performance and reliance on a third party, which considers the vulnerability of security and reveals the private data of the individual. The TDES methodology is proposed to improve security of medical data in Cloud computing using Python software on a system with 6 GB GPU, 16 GB RAM, i7 core processor and Windows 10 OS environment. The TDES methodology evaluation uses performance measures as explained in this section. The comparison of the proposed method with the existing methods is described in this section.
5.2. Comparative Analysis
The values obtained for the proposed TDES methodology to provide security for the big medical data in Cloud computing and existing methods are explained in this section. The comparison among proposed TDES methodology and existing methods such as IFHDS [
14] and SA_EDS_AES [
15] in terms of performance measures is given in
Table 3.
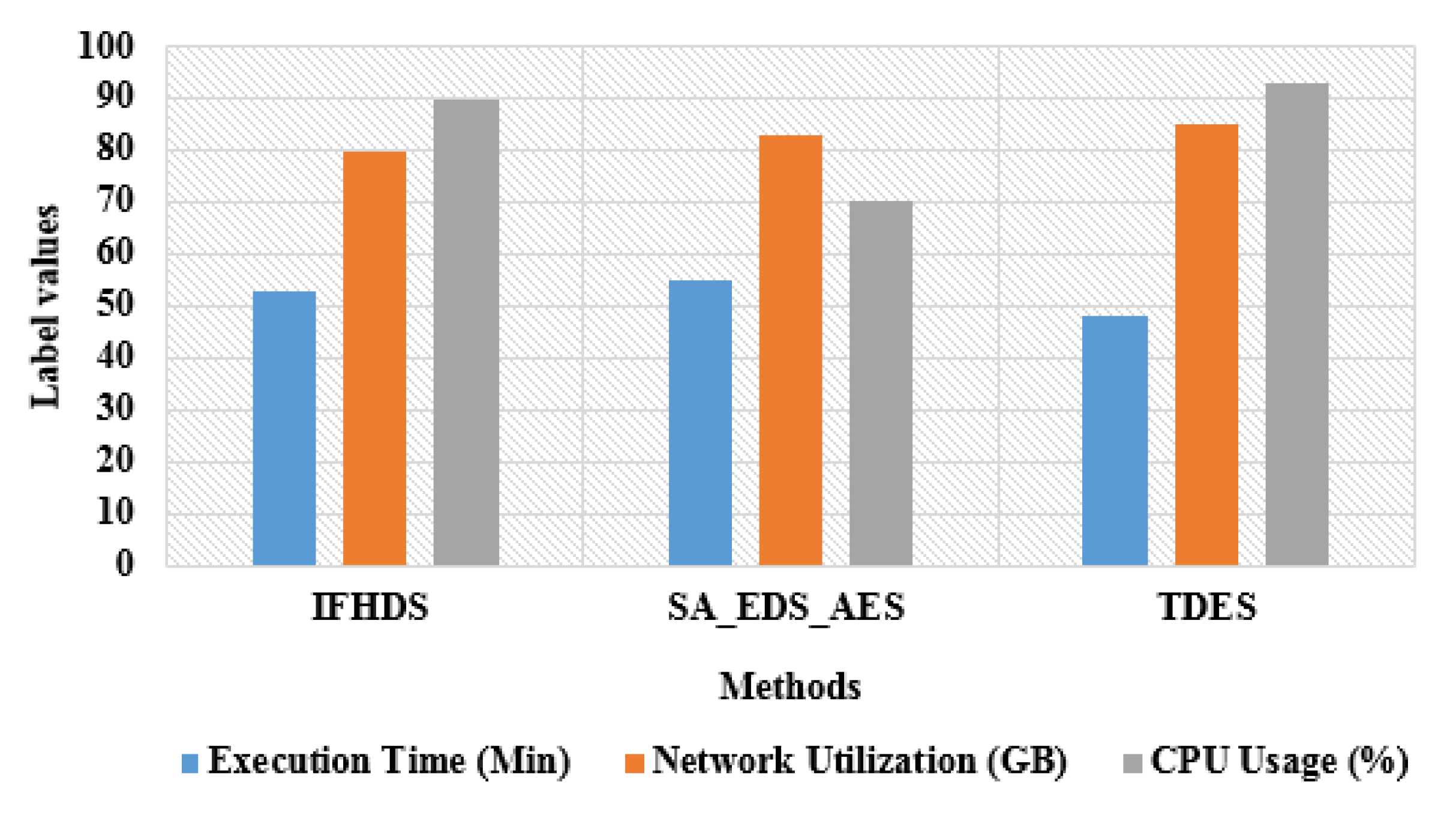
Table 3 shows the performance of the proposed method and existing methods in terms of execution time, network utilization and CPU usage. The time taken for encryption, transmission and decryption in medical data is execution time in TDES methodology. The network utilization for the TDES methodology to encrypt, decrypt and transmit the data is estimated. The end-to-end execution utilizes the CPU to deliver better performance and to meet the requirements of security. The proposed TDES methodology has a reduced execution time of 48 min for encryption, storage and decryption as compared to existing methods. The network utilization of proposed method is 85 GB where existing methods used 80 GB and 83 GB. The CPU utilization of to execute the task of proposed TDES methodology is 93%. The proposed TDES methodology provides a simpler technique by increasing the sizes of keys in DES to protect against the attacks and defends the privacy of data. The plotted graph of proposed TDES methodology with the existing method is shown in
Figure 3.
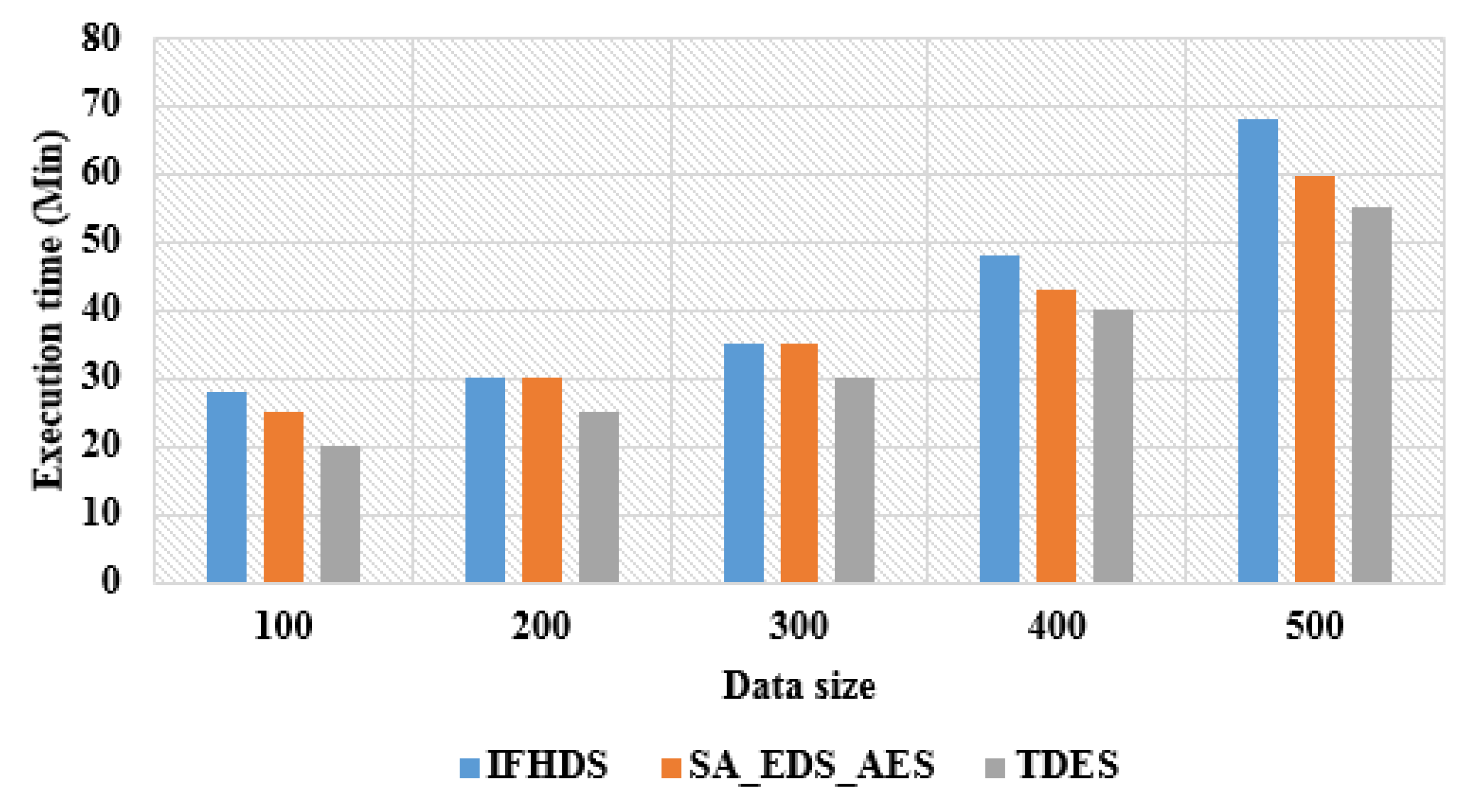
Table 4 shows the execution time of the proposed TDES methodology for 100 to 500 data size as compared with the existing methods. The execution time will be based on security level of methodology. The proposed TDES has a lower execution time and shows effective encryption, decryption and storage performance. The execution time of proposed TDES methodology for the data size of 500 is 55 min and it provides effective security to the model. The existing IFHDS [
14] and SA_EDS_AES [
15] consumed more execution time and did not meet all the security requirements. The graphical representation of proposed TDES methodology with existing method in terms of execution time is shown in
Figure 4.
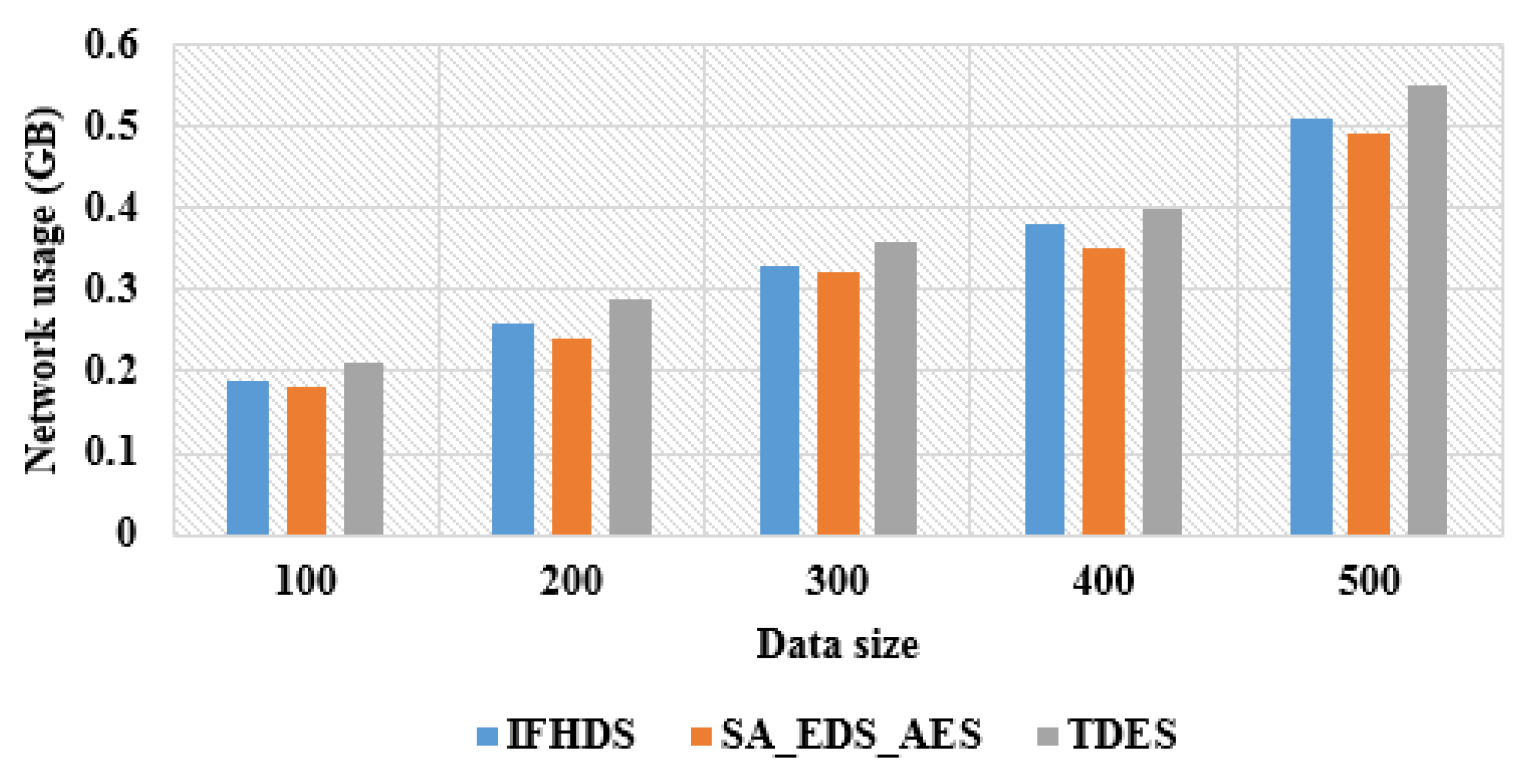
The
Table 5 shows the network usage of proposed TDES methodology for 100 to 500 data sizes as compared with the existing methods. The network utilization for the TDES methodology to encrypt, decrypt and transmit the data is estimated. The network utilization of proposed method is higher compared to existing methods. The network utilization is the amount of data transmitted among the workers over the clusters during the process of encryption and decryption. The proposed TDES methodology utilizes the network of 0.55 GB for the 500 data size. The proposed TDES methodology provides a simpler technique by increasing the sizes of keys in DES to protect against the attacks and defends the privacy of data. The graphical representation of proposed TDES methodology with existing method in terms of network usage is shown in
Figure 5.
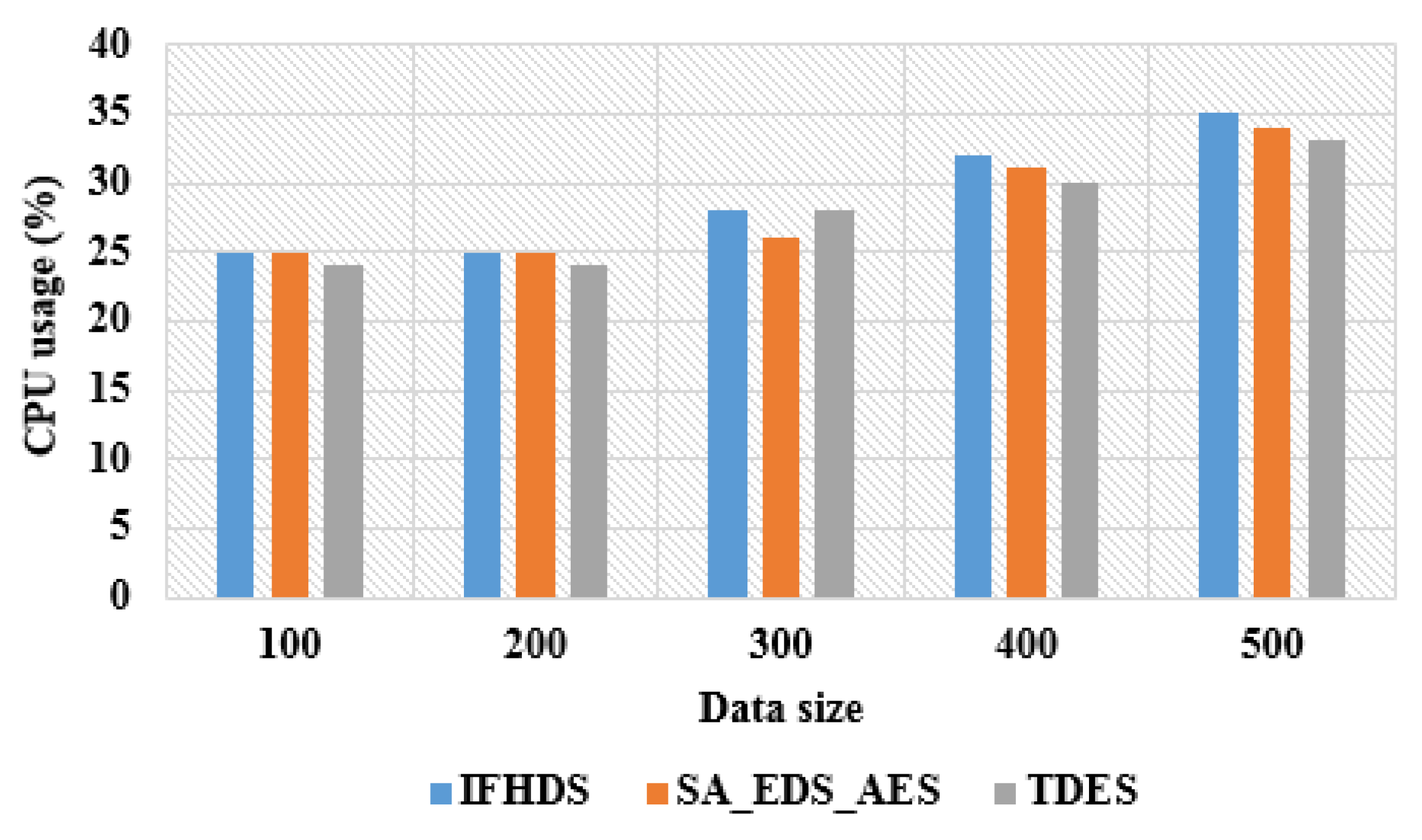
The comparison table of the proposed TDES methodology with existing methods in terms of CPU utilization is shown.
Table 6 shows the CPU utilization of the proposed TDES methodology for 100 to 500 data sizes compared with the existing methods. The end-to-end execution utilizes the CPU to deliver better performance and to meet the requirements of security. The proposed TDES methodology utilizes the CPU of 33% for 500 data size, whereas the existing IFHDS [
14] method utilized CPU of 35% and SA_EDS_AES [
15] of 34%. The proposed TDES methodology provides a simpler technique by increasing the sizes of keys in DES to protect against the attacks and defends the privacy of data. The graphical representation of the proposed TDES methodology compared with existing methods in terms of CPU utilization is shown in
Figure 6.
The TDES methodology and existing techniques were implemented with the same data and in the same environment to test their performance. Some recent existing methods such as Hybrid Encryption [
16], MA-ABE [
18], and Tabu [
20] were compared with TDES methodology in the network.
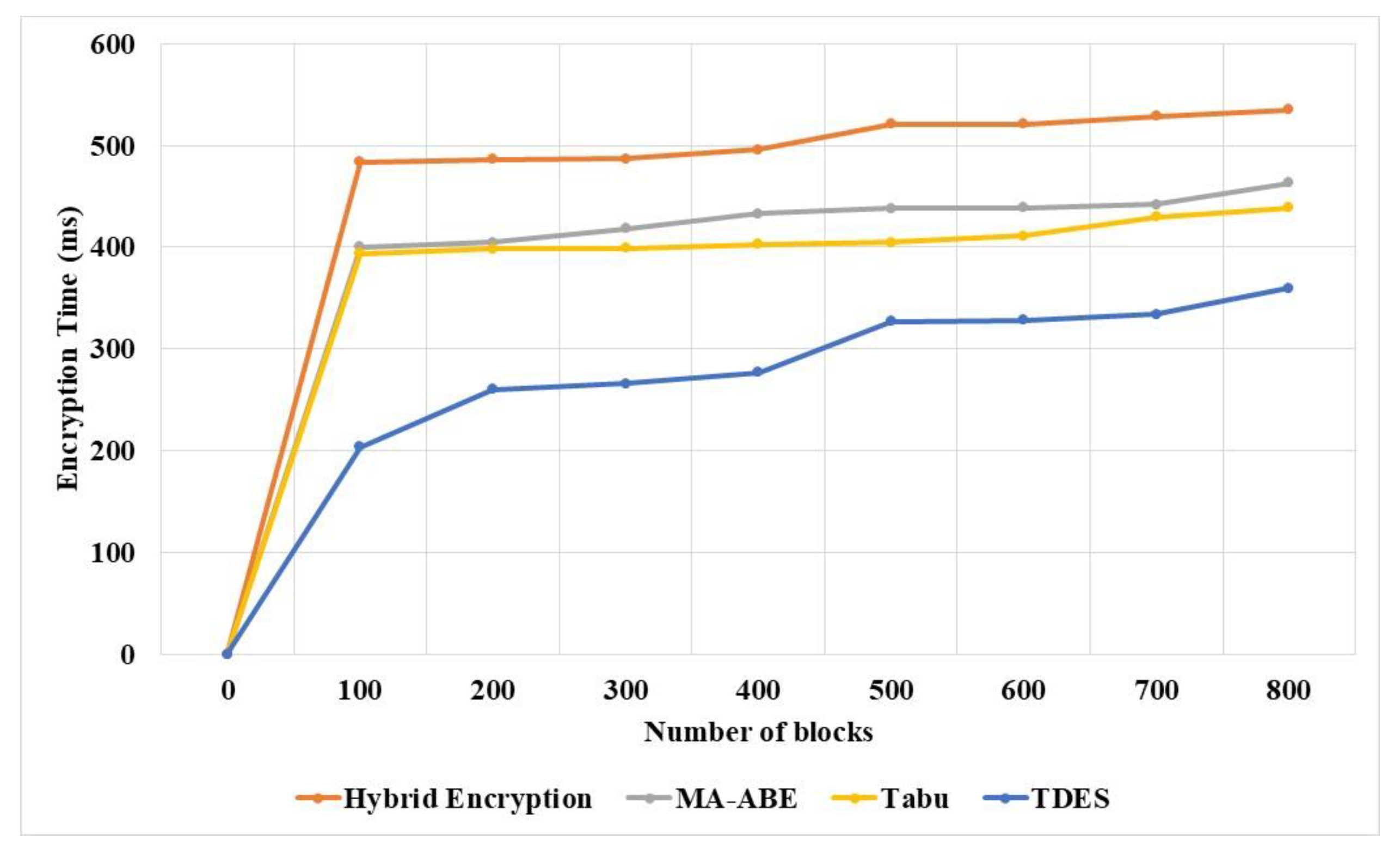
The encryption time of TDES and existing methodologies for various number of blocks were measured and compared, as shown in
Table 7 and
Figure 7. The number of blocks varied from 100 to 800 to evaluate the TDES and existing methodologies’ performance. The TDES methodology has the advantage of balancing the key length and strength of the key based on the importance of data. This methodology helps to reduce the encryption time of the data compared to existing techniques. The symmetric key is applied to handle the structure of data, which supports reading, storing and editing. The proper structure of data handling further reduces the encryption time in TDES methodology. The Hybrid encryption [
16] and MA-ABE [
18] techniques require encryption for attributes and data that increases the encryption time of the model. The Tabu search techniques has local optima that provides more key length and increases the encryption time. The TDES methodology requires encryption time of 360 ms, Tabu search [
20] requires 439 ms encryption time, MA-ABE [
18] technique requires 463 ms encryption time and Hybrid encryption requires 535 ms encryption time.
Decryption time of the TDES and existing techniques was measured and compared for various numbers of blocks, as shown in
Table 8 and
Figure 8. The TDES shows significant reduction of decryption time compared to existing techniques in Cloud data security. The TDES methodology has the advantages of handling structured data using symmetric key and balance key length–strength, based on the importance of data. The decryption time is significantly reduced due to key and structure handling. The triple encryption is applied to sensitive data and increases the strength of encryption. The Tabu search techniques [
20] uses large key strength to encrypt the data due to local optima in search process. The MA-ABE [
18] and Hybrid encryption [
16] techniques require decrypting the attribute and data, which increases the decryption time. The TDES methodology requires 475 ms decryption time, Tabu search [
20] requires 603 ms, MA-ABE [
18] requires 740 ms and Hybrid encryption [
16] requires 793 ms decryption time for 800 blocks of data.
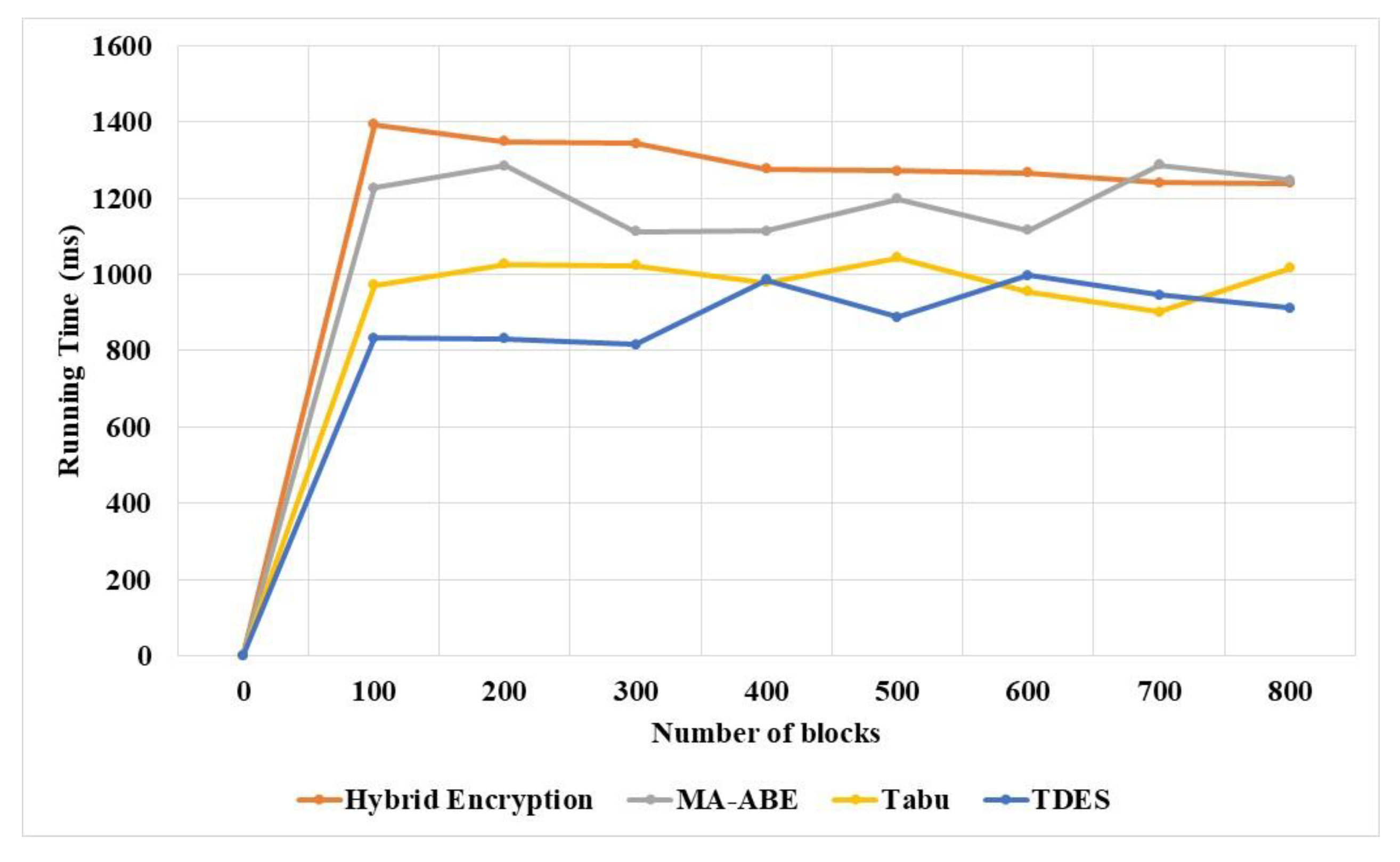
The running time of TDES and existing techniques was measured and compared for various numbers of blocks, as shown in
Table 9 and
Figure 9. The TDES running time is less compared to existing techniques, due to its efficiency in data structure handling and balance of key length–strength. The TDES methodology partitions the data into three categories based on importance: high sensitive data are applied with triple encryption, medium sensitive data are applied with double encryption, and low sensitive data are applied with single encryption. This methodology helps to reduce total running time of the model compared to existing techniques. The Hybrid encryption [
16] and MA-ABE [
18] technique have more running time due to encrypting and decrypting both attributes and data. The Tabu [
20] search has a high running time and high key strength due to local optima in the search process.
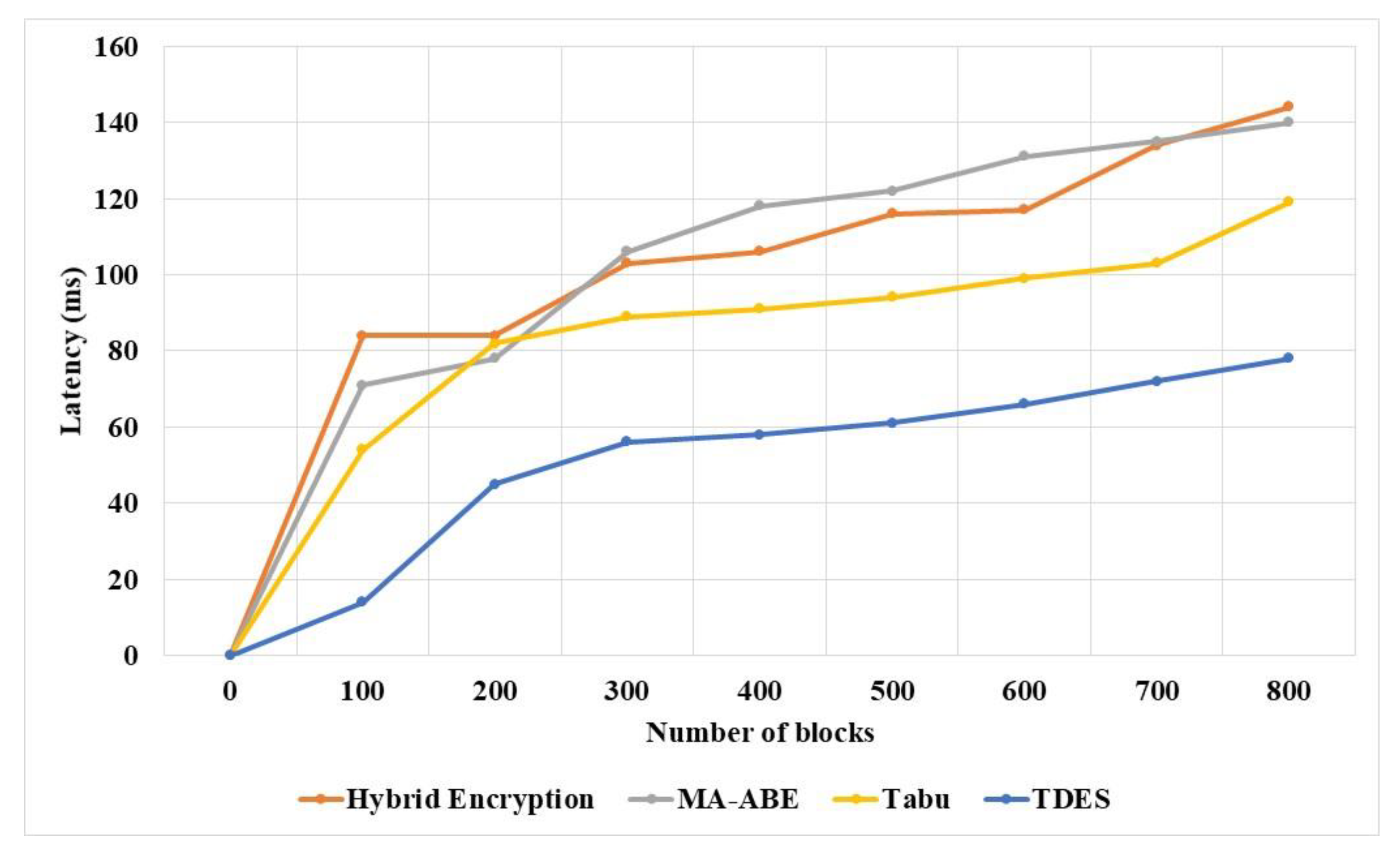
Latency of TDES and existing techniques were measured and compared for various numbers of blocks, as shown in
Table 10 and
Figure 10. The TDES has significantly lower latency in the model compared to existing techniques, due to its proper structure of data using symmetric key. The Tabu [
20], MA-ABE [
18] and Hybrid encryption [
16] do not maintain proper structure of data, which involves increases in the latency of the model. The TDES methodology has 78 ms latency, Tabu [
20] has 119 ms, MA-ABE has 140 ms and Hybrid encryption has 144 ms latency for 800 number of blocks.
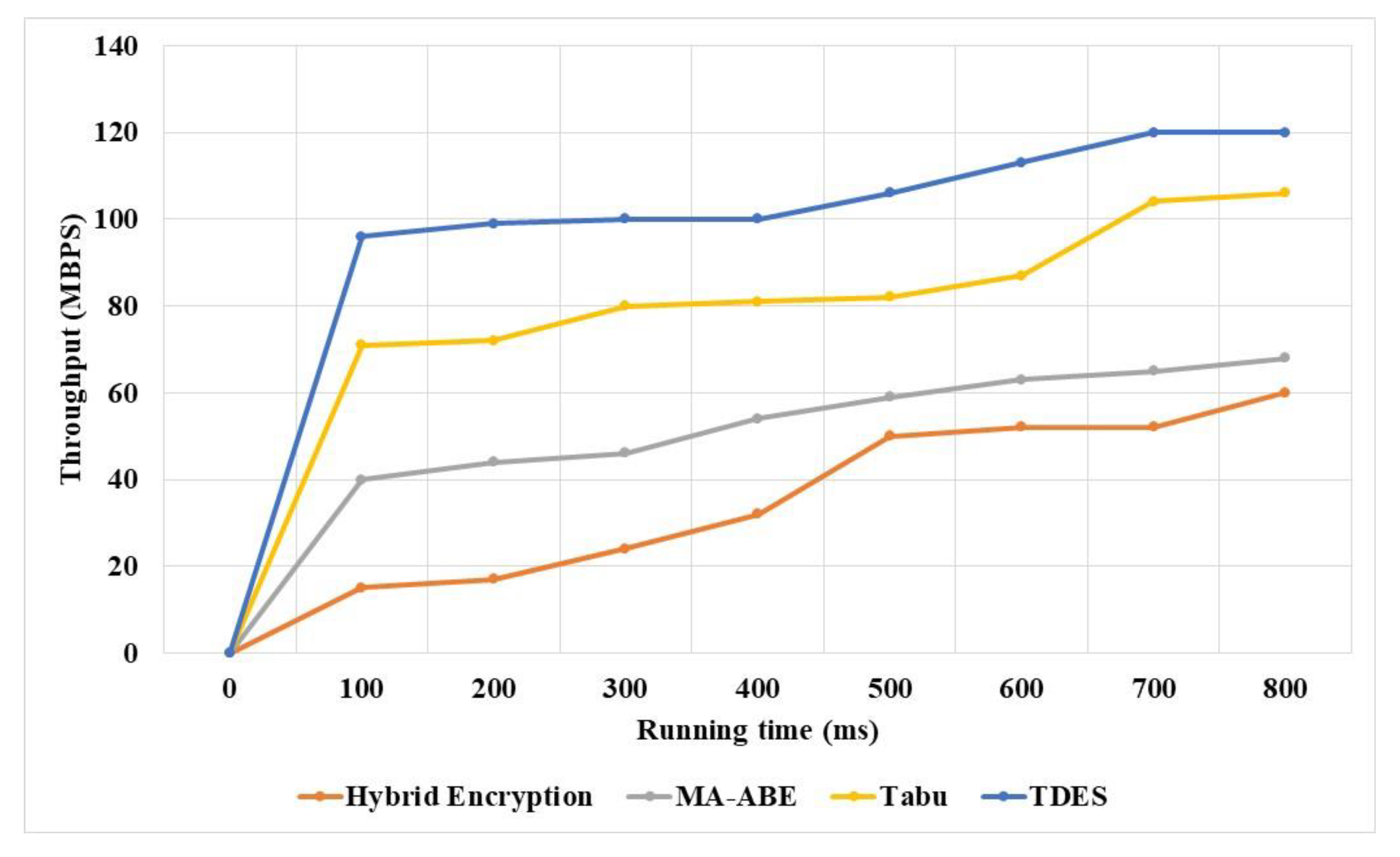
The TDES and existing techniques throughput were measured and compared in
Table 11 and
Figure 11. The TDES methodology supports higher throughput than existing techniques due to its efficiency in structure data handling using symmetric key. The TDES methodology partition the data into three categories based on data importance. The TDES methodology transfers the low sensitive data in high speed due to its single encryption. The Tabu [
20], MA-ABE [
18] and Hybrid encryption [
16] methods do not maintain proper structure and this reduces the throughput of the network. The TDES has throughput of 120 MBPS, and existing Tabu [
20] has 106 MBPS, MA-ABE [
18] has 68 MBPS throughput, and Hybrid encryption [
16] has 60 MBPS throughput.
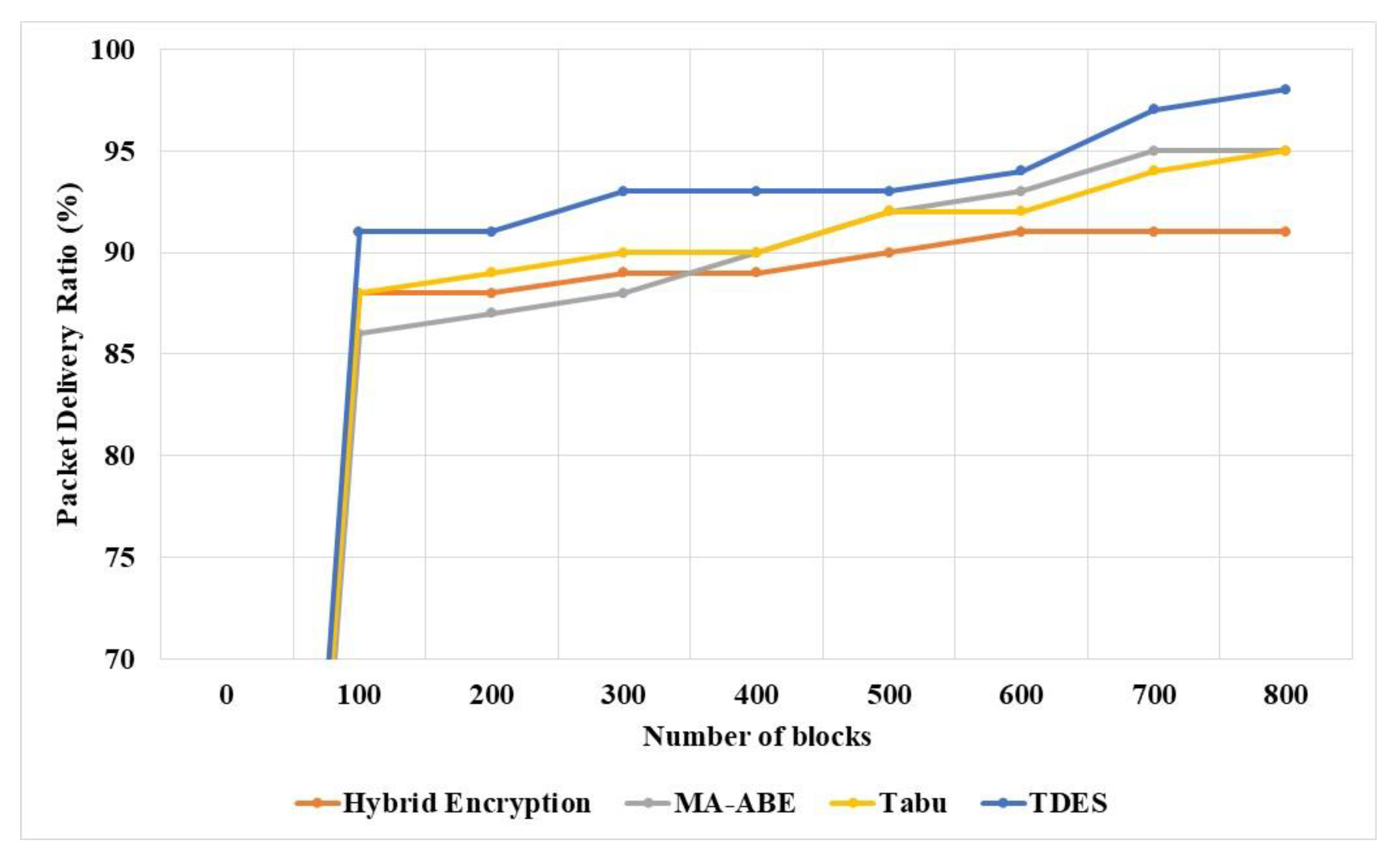
The packet delivery ratio of TDES and existing techniques were measured and compared for various numbers of blocks, as shown in
Table 12 and
Figure 12. The TDES methodology has higher packet delivery ratio due to the partitioning of data and structure of handling. The Tabu [
20], MA-ABE [
18] and Hybrid encryption [
16] methods do not maintain proper structure and this reduces the packet delivery ratio in the network. The TDES methodology has 98% packet delivery ratio, Tabu [
20] has 95%, MA-ABE method has 95% and Hybrid encryption has 91% packet delivery ratio.