Analysis of Information Security News Content and Abnormal Returns of Enterprises
Abstract
1. Introduction
2. Literature Review
2.1. Event Study
2.2. Studies of Information Security Breaches
2.3. Analysis Methods
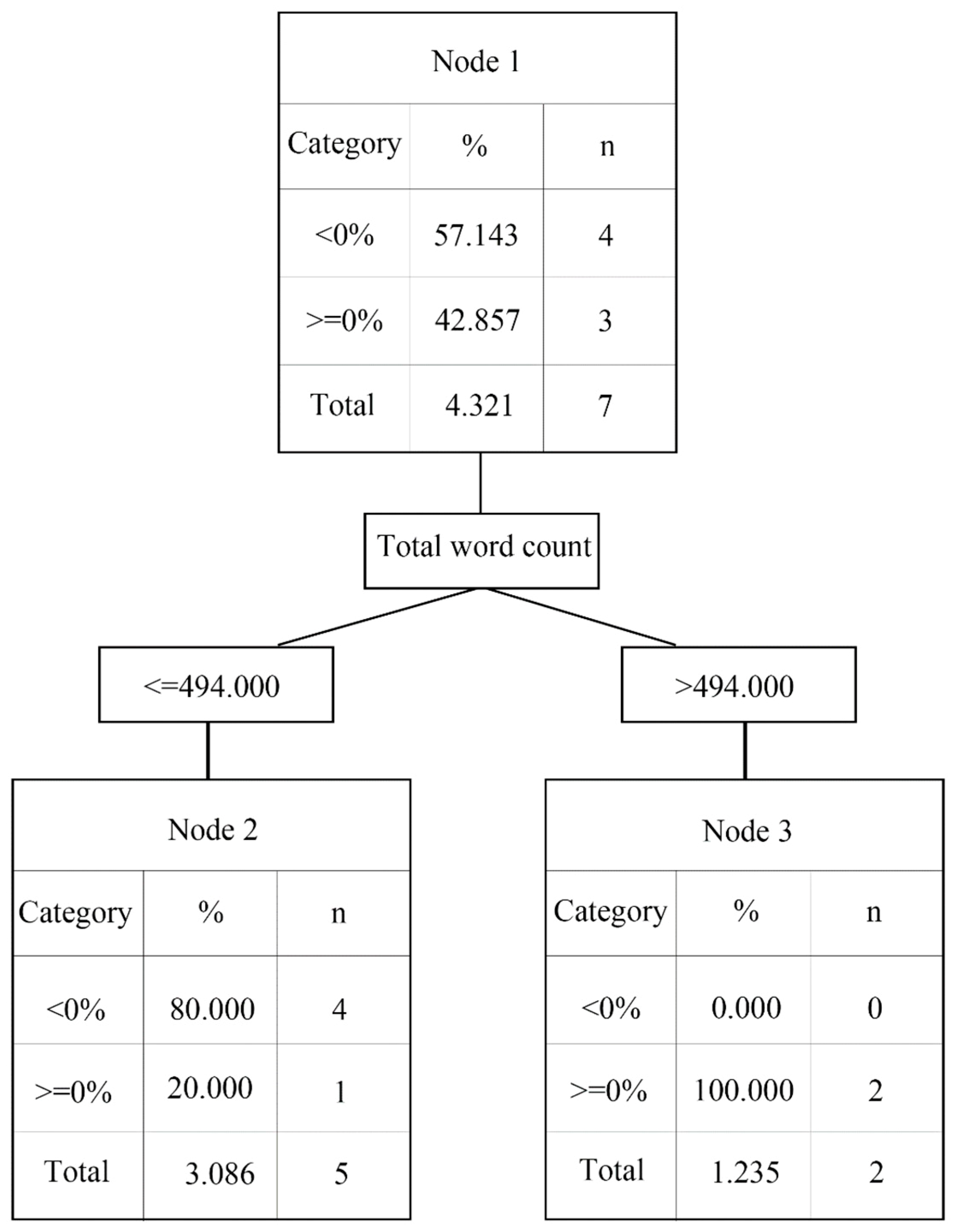
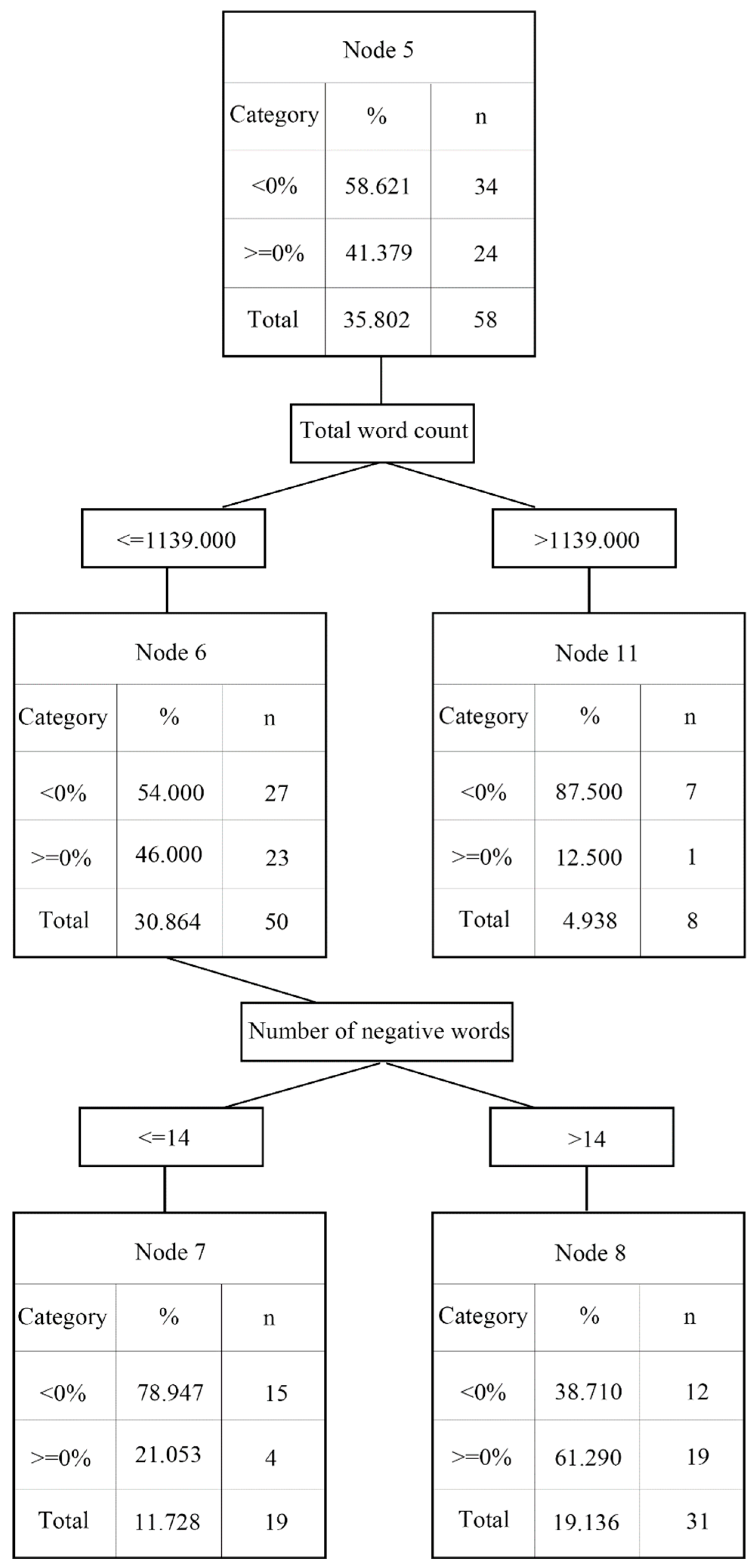
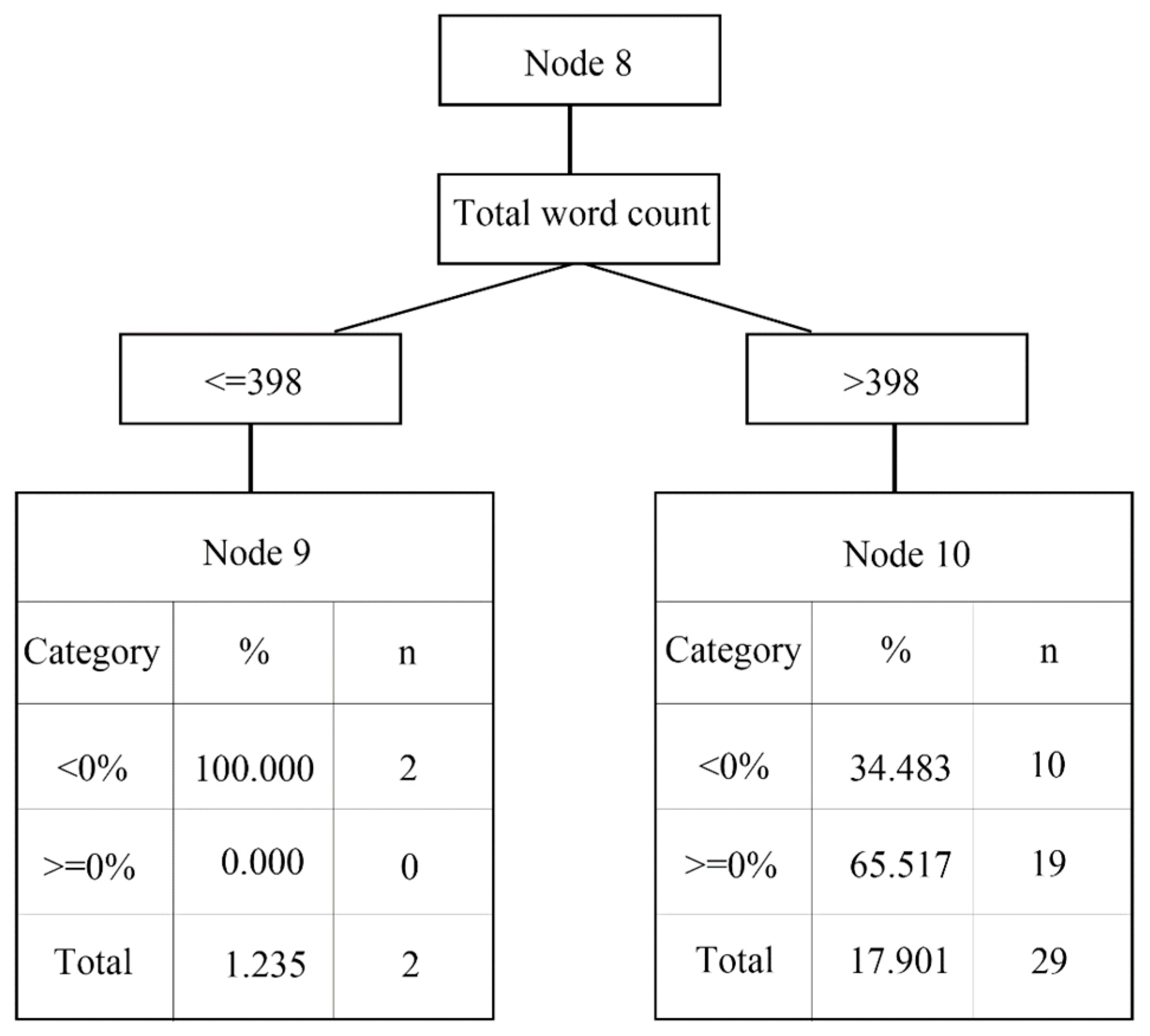
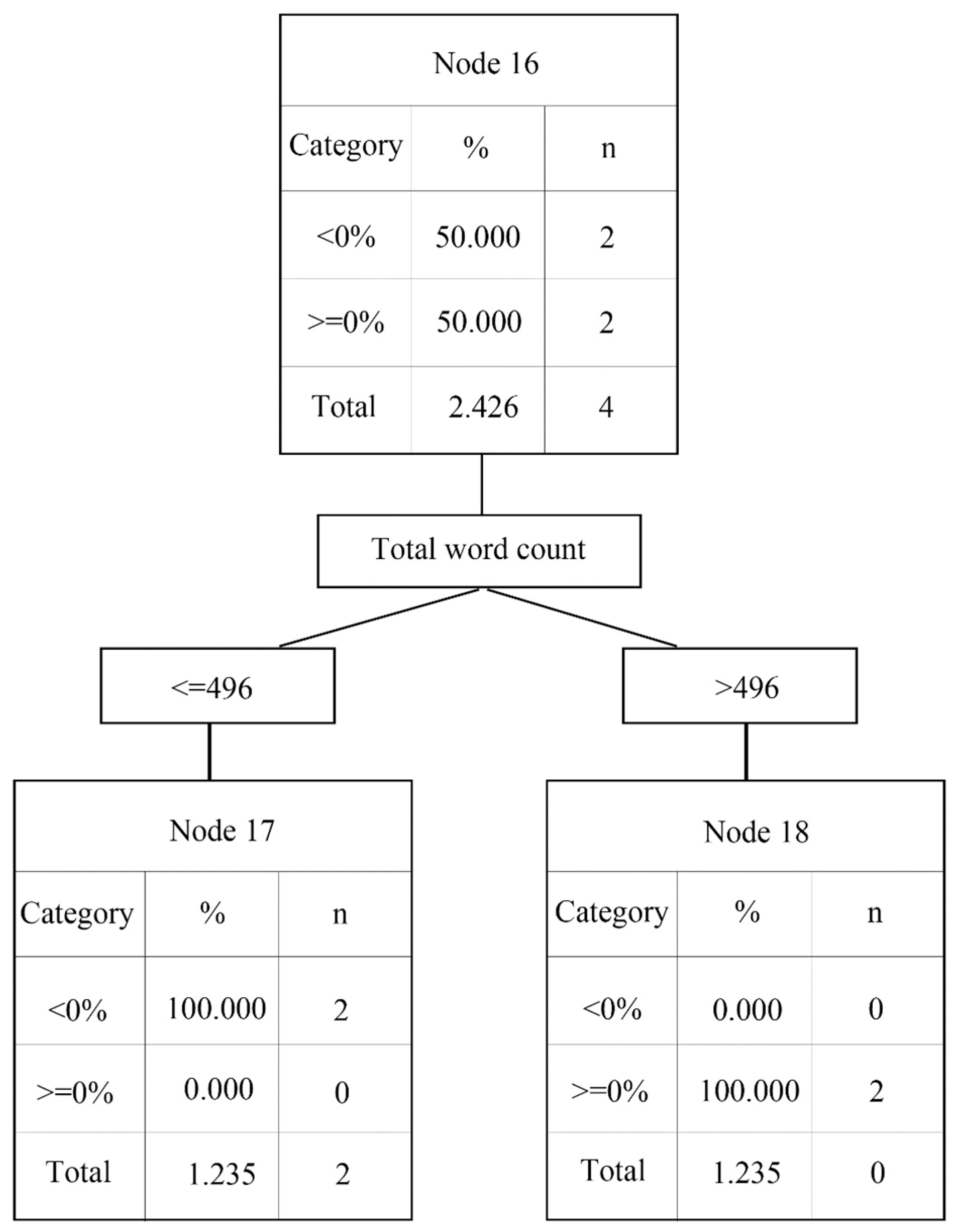
2.3.1. Decision Tree
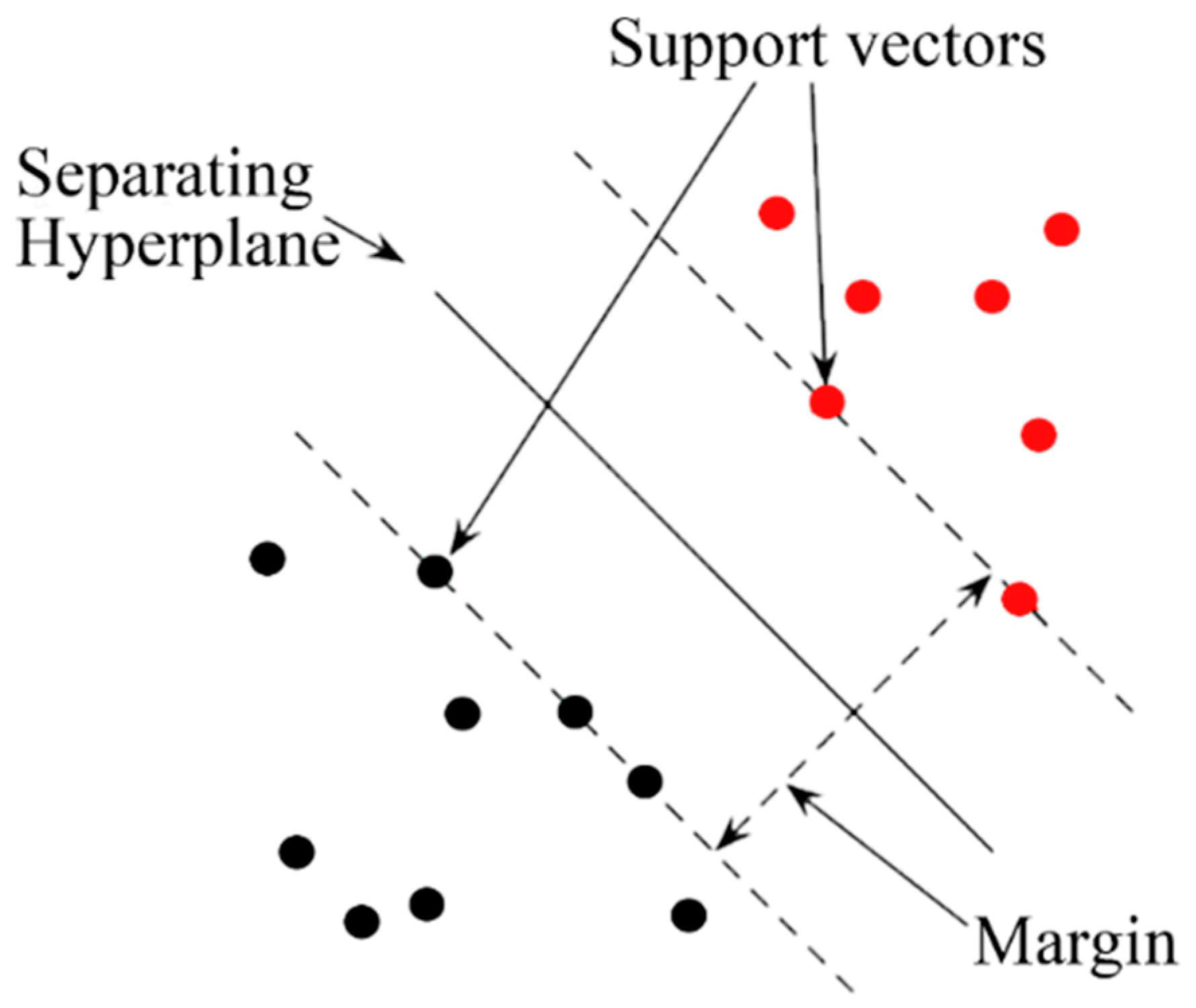
2.3.2. Support Vector Machine (SVM)
2.3.3. Random Forest
3. Research Methods
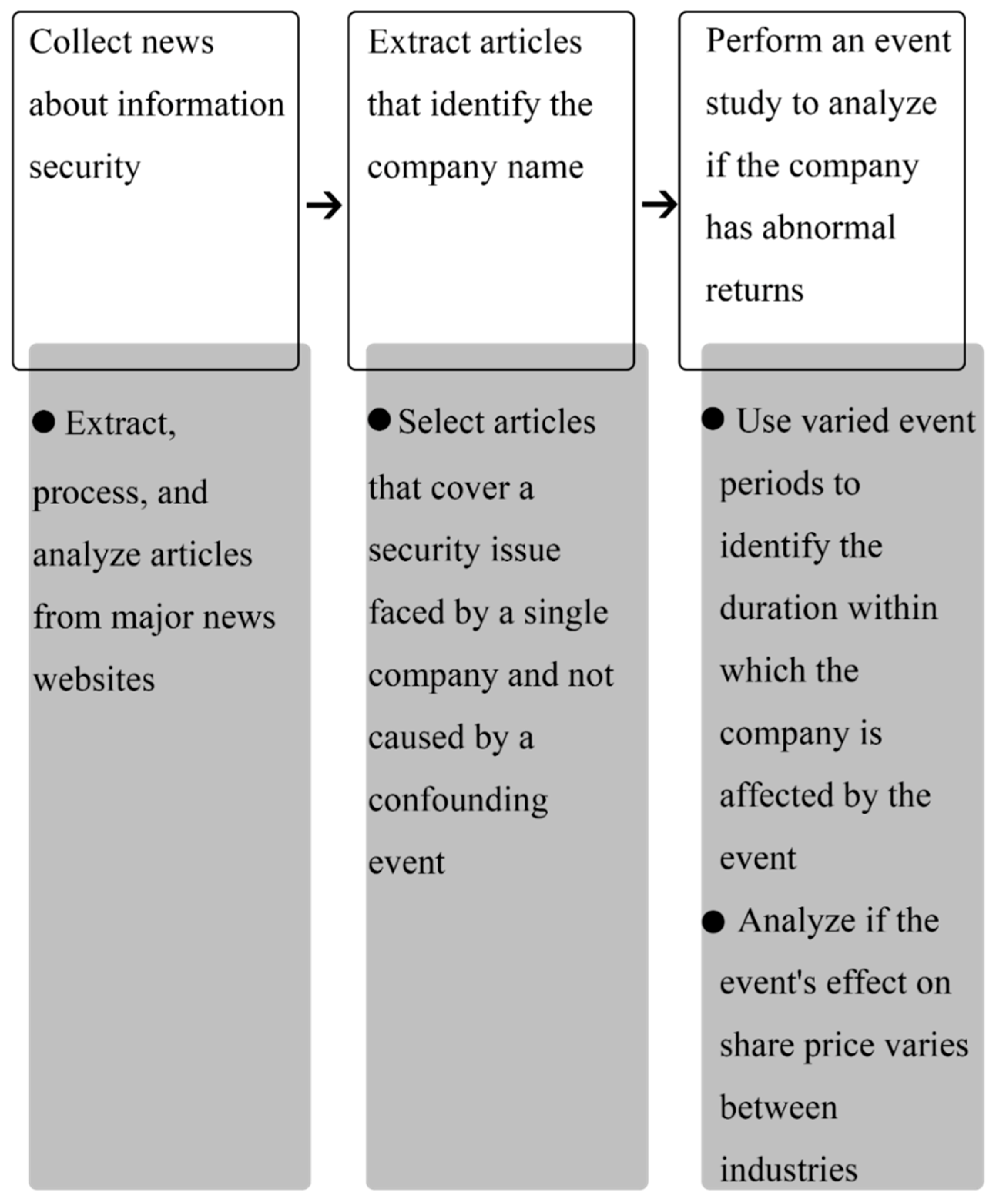
3.1. Research Procedure
3.2. Data Collection and Selection
- The firm involved in the event must belong to the S&P 500 index.
- The event was reported in major newspapers in the U.S.
- The firm has share trading records for 180 consecutive days before the event day.
- Avoidance of the confounding effect, that is, the effect caused by another event that affects the estimation result, such as a corporate merger, release of financial statement, and turnover of high-ranking officers. Events affected by a confounding effect must be dropped to avoid confusion.
- Event day is defined as the day on which the first article about the event is published.
3.3. The Calculation of Abnormal Returns
3.4. Analysis of the Correlation between News Content and Abnormal Returns
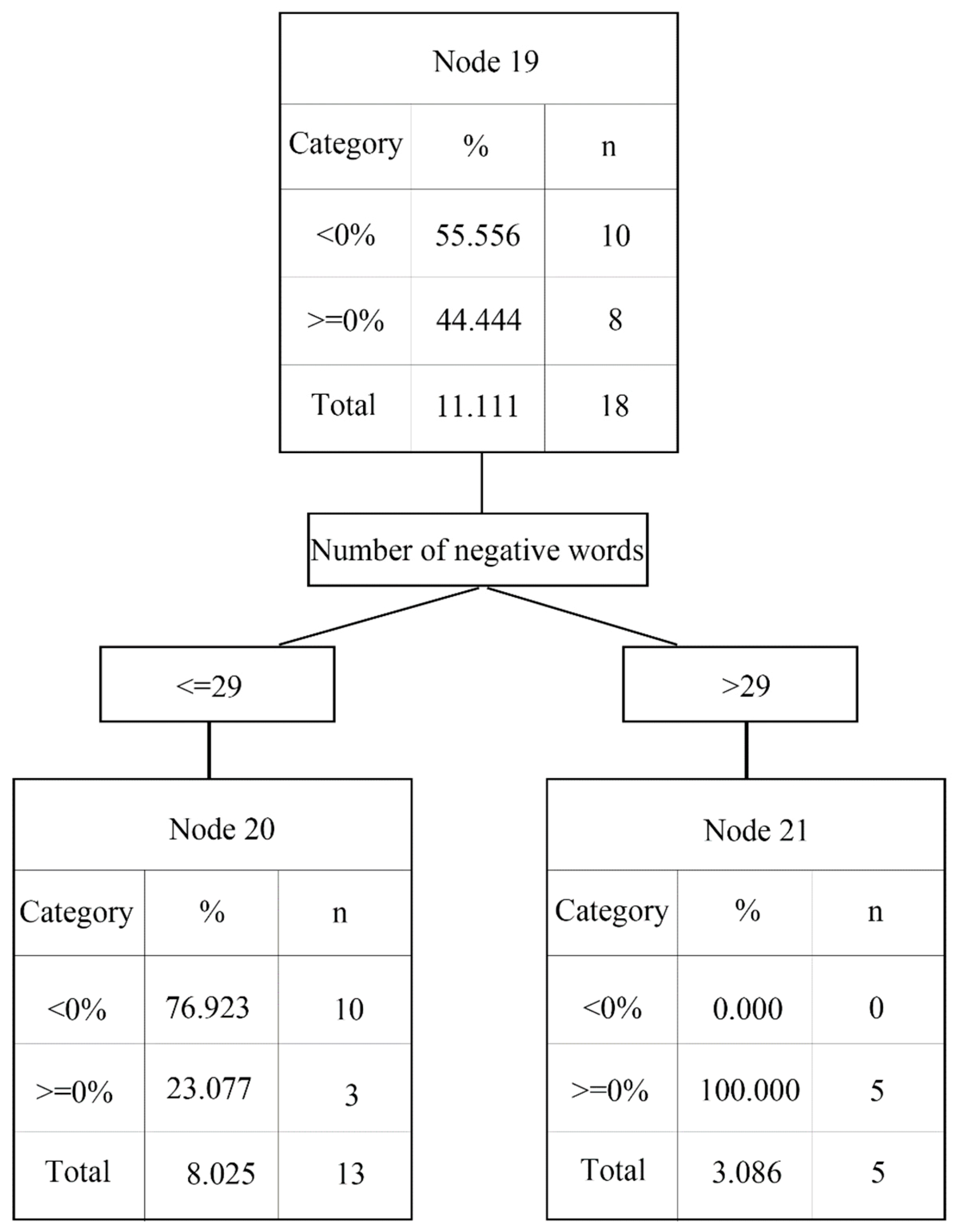
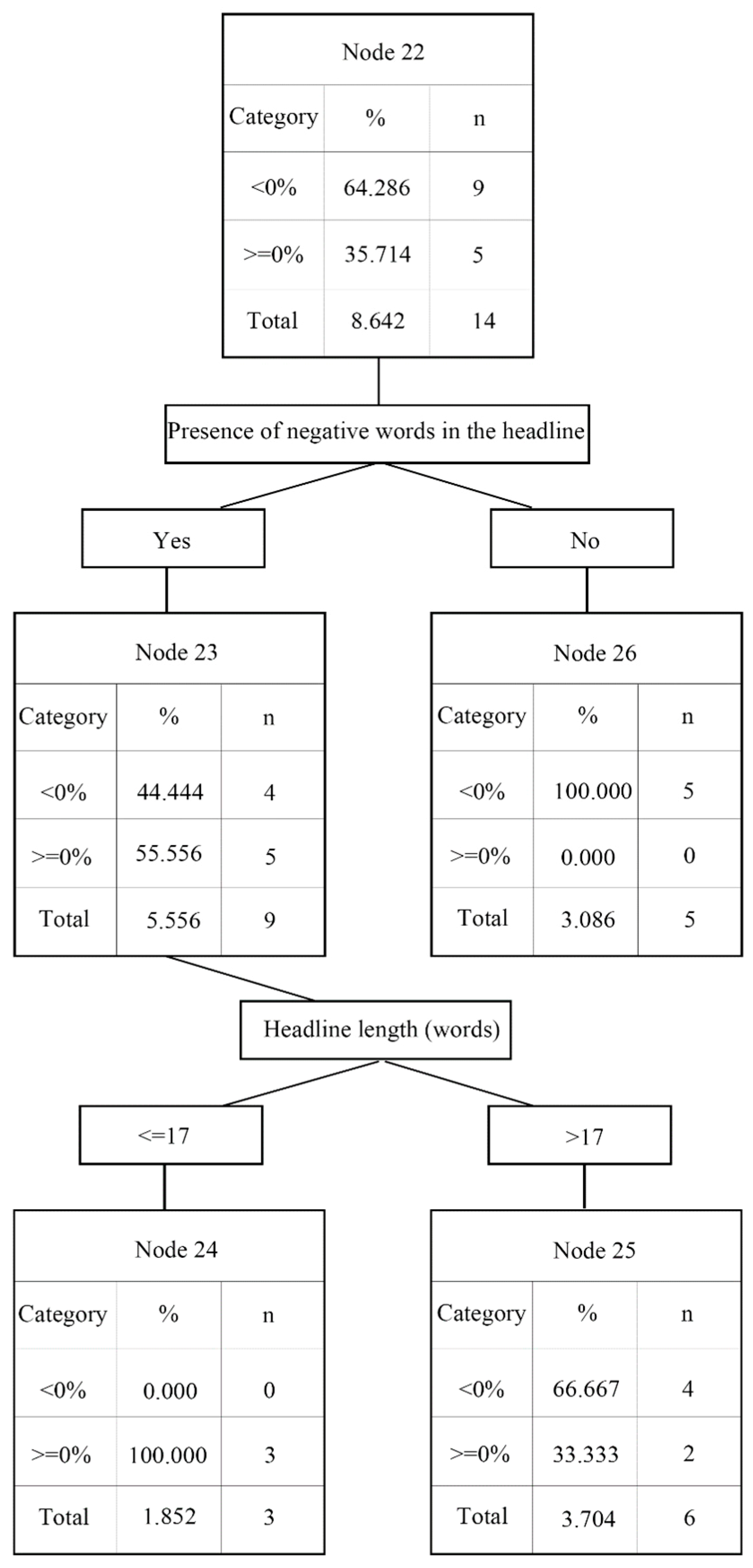
4. Research Results
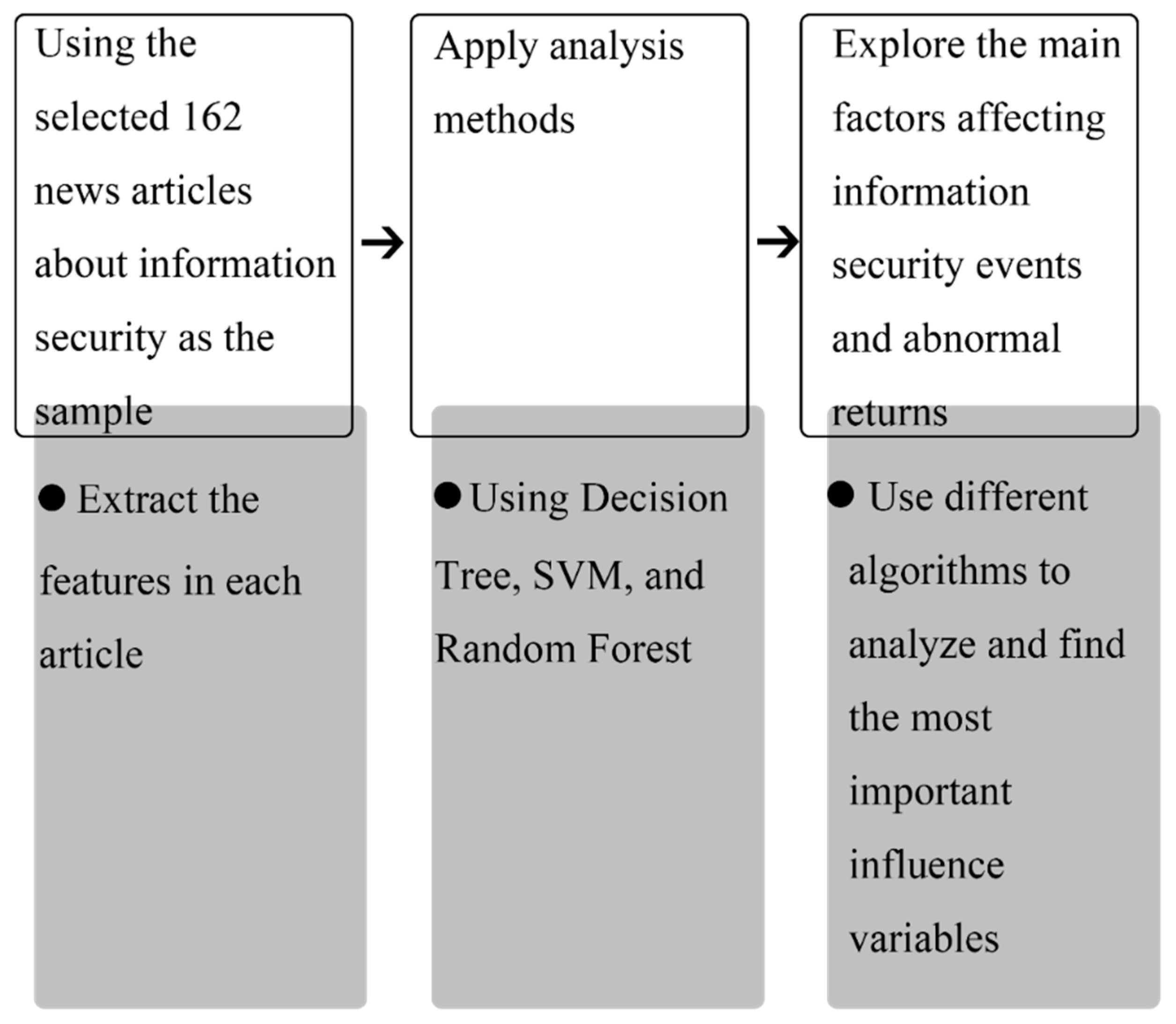
4.1. Data Analysis
Event Sample Selection and Classification
- Search on Factiva for announcements of any major news about the company within a certain period of time before and after the event day. Events such as corporate merger, release of financial statements or turnover of high-ranking executives may cause an effect on a company’s share prices. The event should be dropped if any confounding event is detected.
- Use Google Search to make sure again that the company has no other incident around the event day.
4.2. Analysis Results
Calculating Abnormal Returns
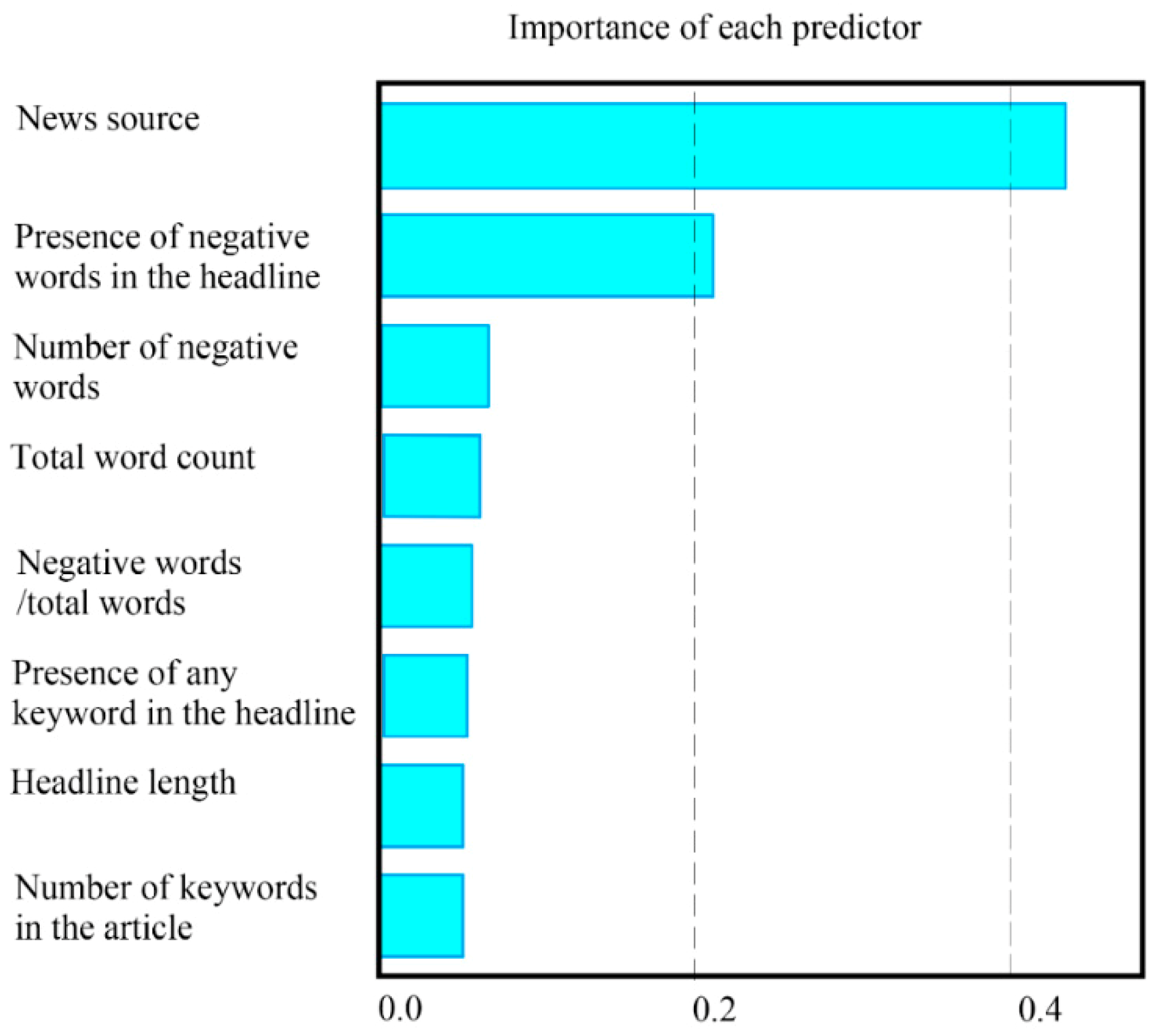
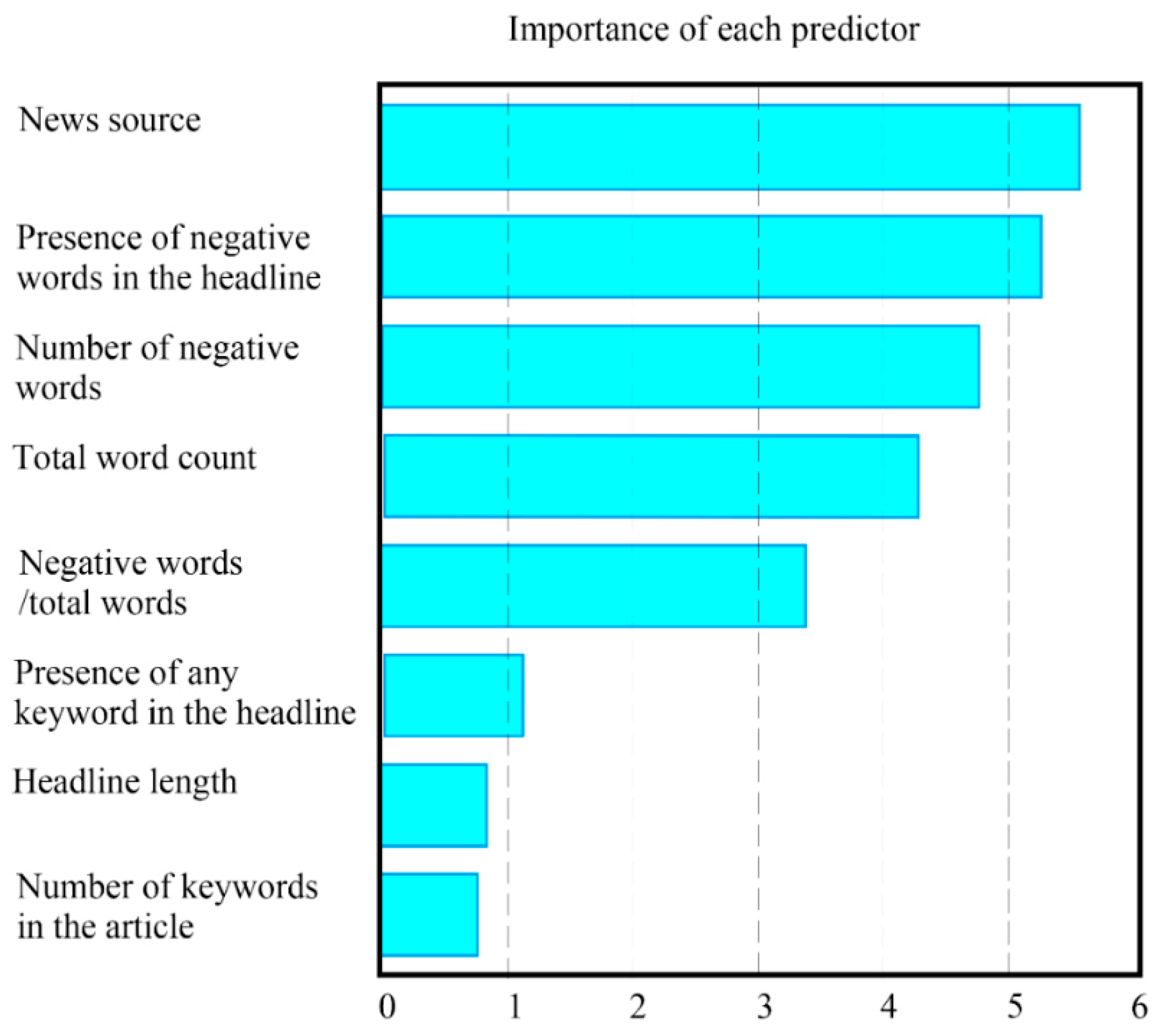
4.3. Analyzing News Content and Abnormal Returns
5. Conclusions
- (1)
- The empirical evidence indicates that news coverage of corporate information security events diffuses negative messages among investors, which would in turn cause fluctuation in the firm’s share prices and generation of negative returns.
- (2)
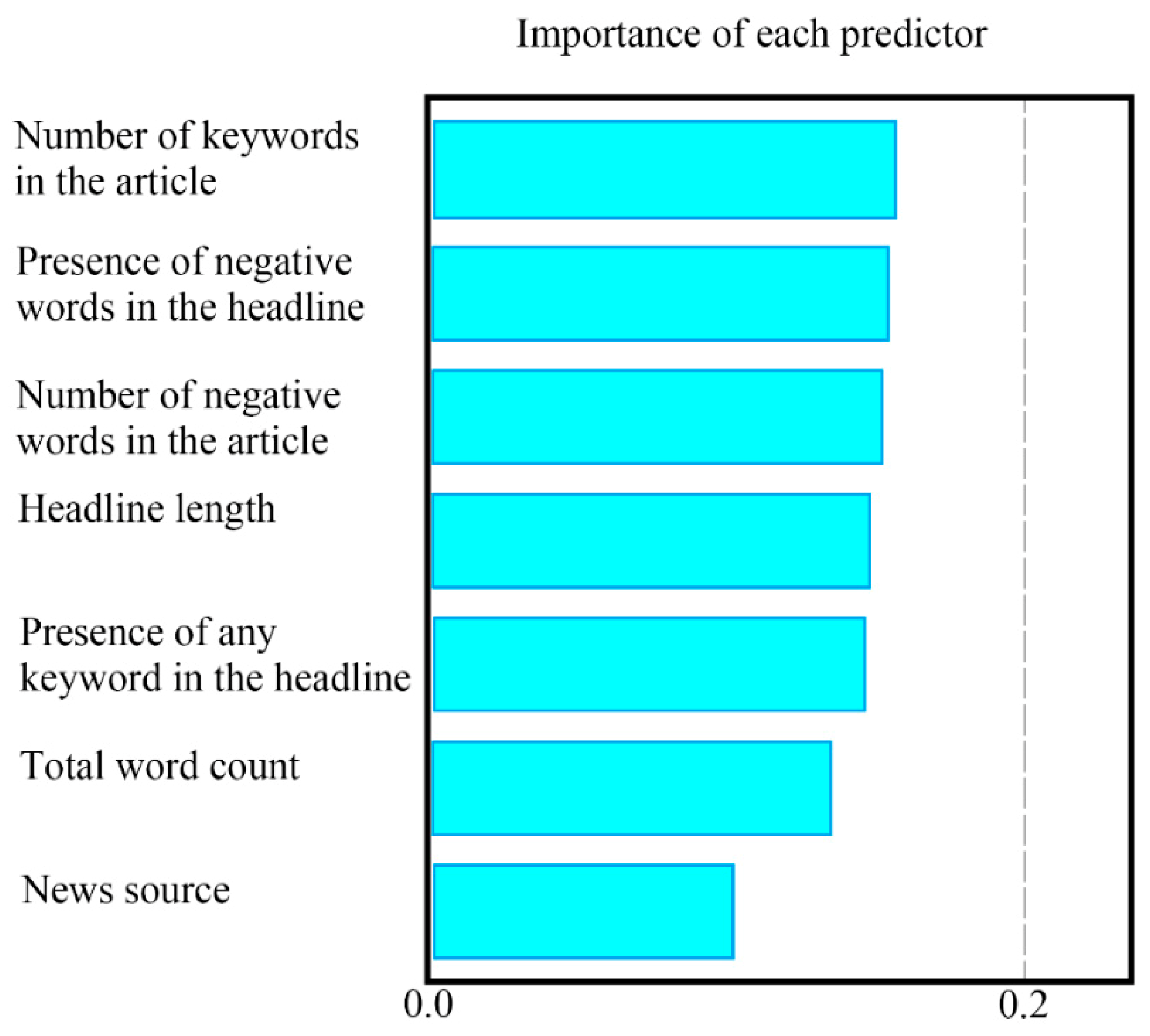
- The decision tree analysis shows that the news source and negative words are critically important factors that affect abnormal returns.
- (3)
- In further SVM and random forest analyses, other factors are examined, including the number of negative words, presence of negative words in the headline, and total word count. These are found to also be important variables that influence the effect of a news event on abnormal returns.
Funding
Acknowledgments
Conflicts of Interest
References
- Mohr, J.J. The management and control of information in high-technology firms. J. High Technol. Manag. Res. 1996, 7, 245–268. [Google Scholar] [CrossRef]
- Arya, B.; Zhang, G. Institutional Reforms and Investor Reactions to CSR Announcements: Evidence from an Emerging Economy. J. Manag. Stud. 2009, 46, 1089–1112. [Google Scholar] [CrossRef]
- Carow, K.; Heron, R.; Saxton, T. Do early birds get the returns? An empirical investigation of early-mover advantages in acquisitions. Strateg. Manag. J. 2004, 25, 563–585. [Google Scholar] [CrossRef]
- Chen, Y.; Ganesan, S.; Liu, Y. Does a Firm’s Product-Recall Strategy Affect Its Financial Value? An Examination of Strategic Alternatives during Product-Harm Crises. J. Mark. 2009, 73, 214–226. [Google Scholar] [CrossRef]
- Konchitchki, Y.; O’Leary, D.E. Event study methodologies in information systems research. Int. J. Account. Inf. Syst. 2011, 12, 99–115. [Google Scholar] [CrossRef]
- Wang, T.; Ulmer, J.R.; Kannan, K. The Textual Contents of Media Reports of Information Security Breaches and Profitable Short-Term Investment Opportunities. J. Organ. Comput. Electron. Commer. 2013, 23, 200–223. [Google Scholar] [CrossRef]
- Huang, C.K.; Wang, T.T.; Tsai, Y.T. Market reactions to big data implementation announcements. In Proceedings of the Pacific Asia Conference on Information Systems, Chiayi, Taiwan, 27 June–1 July 2016. [Google Scholar]
- Dos Santos, B.L.; Peffers, K.; Mauer, D.C. The Impact of Information Technology Investment Announcements on the Market Value of the Firm. Inf. Syst. Res. 1993, 4, 1–23. [Google Scholar] [CrossRef]
- Son, I.; Lee, D.; Lee, J.N.; Chang, Y.B. Market perception on cloud computing initiatives in organizations: An extended resource-based view. Inf. Manag. 2014, 51, 653–669. [Google Scholar] [CrossRef]
- Rubin, E.; Rubin, A. The impact of Business Intelligence systems on stock return volatility. Inf. Manag. 2013, 50, 67–75. [Google Scholar] [CrossRef]
- Songur, H.; Heavilin, J.E. Abnormal research and development investments and stock returns. North Am. J. Econ. Finance 2017, 42, 237–249. [Google Scholar] [CrossRef]
- Song, X.; Tippett, M.; Vivian, A. Assessing abnormal returns: The case of Chinese M & A acquiring firms. Res. Int. Bus. Finance 2017, 42, 191–207. [Google Scholar]
- Modi, S.B.; Wiles, M.A.; Mishra, S. Shareholder value implications of service failures in triads: The case of customer information security breaches. J. Oper. Manag. 2015, 35, 21–39. [Google Scholar] [CrossRef]
- Leitch, D.; Sherif, M. Twitter mood, CEO succession announcements and stock returns. J. Comput. Sci. 2017, 21, 1–10. [Google Scholar] [CrossRef]
- Siponen, M.T. Six Design Theories for IS Security Policies and Guidelines. J. AIS 2006, 7, 19. [Google Scholar] [CrossRef]
- Straub Jr, D.W. Effective IS security: An. empirical study. Inf. Syst. Res. 1990, 1, 255–276. [Google Scholar] [CrossRef]
- Gal-Or, E.; Ghose, A. The Economic Incentives for Sharing Security Information. Inf. Syst. Res. 2005, 16, 186–208. [Google Scholar] [CrossRef]
- Schechter, S.E.; Smith, M.D. How Much Security Is Enough to Stop a Thief? In Financial Cryptography, Proceeding of the 7th International Conference, Guadeloupe, French, 27–30 January 2003; Wright, R.N., Ed.; Springer: Berlin/Heidelberg, Germany, 2003; pp. 122–137. [Google Scholar]
- Kwon, J.; Ulmer, J.R.; Wang, T. The Association between Top Management Involvement and Compensation and Information Security Breaches. J. Inf. Syst. 2013, 27, 219–236. [Google Scholar] [CrossRef]
- Gordon, L.A.; Loeb, M.P.; Sohail, T. Market value of voluntary disclosures concerning information security. MIS Q. 2010, 34, 567–594. [Google Scholar] [CrossRef]
- Kositanurit, B.; Osei-Bryson, K.M.; Ngwenyama, O. Re-examining information systems user performance: Using data mining to identify properties of IS that lead to highest levels of user performance. Expert Syst. Appl. 2011, 38, 7041–7050. [Google Scholar] [CrossRef]
- Feldman, R.; Sanger, J. The Text Mining Handbook: Advanced Approaches in Analyzing Unstructured Data; Cambridge University Press: Cambridge, UK, 2006. [Google Scholar]
- Han, J.; Altman, R.B.; Kumar, V.; Mannila, H.; Pregibon, D. Emerging scientific applications in data mining. Commun. ACM 2002, 45, 54–58. [Google Scholar] [CrossRef]
- Cecchini, M.; Aytug, H.; Koehler, G.J.; Pathak, P. Detecting Management Fraud in Public Companies. Manag. Sci. 2010, 56, 1146–1160. [Google Scholar] [CrossRef]
- Cortes, C.; Vapnik, V. Support-vector networks. Mach. Learn. 1995, 20, 273–297. [Google Scholar] [CrossRef]
- Pal, R.; Kupka, K.; Aneja, A.P.; Militky, J. Business health characterization: A hybrid regression and support vector machine analysis. Expert Syst. Appl. 2016, 49, 48–59. [Google Scholar] [CrossRef]
- Niklis, D.; Doumpos, M.; Zopounidis, C. Combining market and accounting-based models for credit scoring using a classification scheme based on support vector machines. Appl. Math. Comput. 2014, 234, 69–81. [Google Scholar] [CrossRef]
- Al-Yaseen, W.L.; Othman, Z.A.; Nazri, M.Z.A. Multi-level hybrid support vector machine and extreme learning machine based on modified K-means for intrusion detection system. Expert Syst. Appl. 2017, 67, 296–303. [Google Scholar] [CrossRef]
- Khalifi, H.; Elqadi, A.; Ghanou, Y. Support Vector Machines for a new Hybrid Information Retrieval System. Procedia Comput. Sci. 2018, 127, 139–145. [Google Scholar] [CrossRef]
- Bellazzi, R.; Zupan, B. Predictive data mining in clinical medicine: Current issues and guidelines. Int. J. Med. Inf. 2008, 77, 81–97. [Google Scholar] [CrossRef]
- Breiman, L. Random Forests. Mach. Learn. 2001, 45, 5–32. [Google Scholar] [CrossRef]
- Xie, Y.; Li, X.; Ngai, E.W.T.; Ying, W. Customer churn prediction using improved balanced random forests. Expert Syst. Appl. 2009, 36, 5445–5449. [Google Scholar] [CrossRef]
- Whitrow, C.; Hand, D.J.; Juszczak, P.; Weston, D.; Adams, N.M. Transaction aggregation as a strategy for credit card fraud detection. Data Min. Knowl. Discov. 2009, 18, 30–55. [Google Scholar] [CrossRef]
- Kouzani, A.Z. Faceparts for Recognition. In Proceedings of the TENCON 2006—2006 IEEE Region 10 Conference, Hong Kong, China, 14–17 November 2006; pp. 1–4. [Google Scholar]
- Gupta, R.; Pierdzioch, C.; Vivian, A.J.; Wohar, M.E. The predictive value of inequality measures for stock returns: An analysis of long-span UK data using quantile random forests. Financ. Res. Lett. 2018. [Google Scholar] [CrossRef]
- Hung, C.C.; Huang, C.K.; Ku, C.Y. Research on Abnormal Return of Enterprise Stock Price for the Information Security News. J. Inf. Manag. 2018, 25, 283–306. [Google Scholar]
- Campbell, K.; Gordon, L.A.; Loeb, M.P.; Zhou, L. The economic cost of publicly announced information security breaches: Empirical evidence from the stock market. J. Comput. Secur. 2003, 11, 431–448. [Google Scholar] [CrossRef]
- Sharpe, W.F. Capital Asset Prices: A Theory of Market Equilibrium under Conditions of Risk. J. Finance 1964, 19, 425–442. [Google Scholar]
- McWilliams, A.; Siegel, D. Event Studies in Management Research: Theoretical and Empirical Issues. Acad. Manag. J. 1997, 40, 626–657. [Google Scholar]

| Author(s) | Factor(s) Affecting Stock Prices | Major Finding |
|---|---|---|
| Carow et al., 2004 | Expanding business through a merger or acquisition | When a merger or acquisition is initiated, the firms involved will experience positive abnormal returns. |
| Arya & Zhang, 2009 | Institutional reforms driven by new regulations and corporate social responsibility requirements | Institutional reforms aimed at fulfilling CSR (Corporate Social Responsibility) are viewed positively by investors. |
| Konchitchki & O’Leary, 2011 | Corporate investment in knowledge management systems | Investment in knowledge management systems can create a 1.25% positive abnormal return and bring positive benefits to the future operation of the company. |
| Rubin & Rubin, 2013 | Business Intelligence (BI) systems | Business Intelligence (BI) systems facilitate sharing of information, so they can not only support decision-making but also help reduce the firm’s financial risks and stock price volatility. |
| Son et al., 2014 | Investment in cloud computing | Investing in cloud computing brings significantly positive abnormal returns to a company. |
| H. Songur & J.E. Heavilin, 2017 [11] | Research and development (R&D) investments | Firms proactive in R&D investment tend to have significantly positive abnormal returns. |
| Song et al., 2017 [12] | Merger and acquisition (M&A) | Generally, M&A creates positive abnormal returns to acquirers. |
| Modi et al. 2015 [13] | Security breaches and negative abnormal returns | Security breaches that arise from negligence of a third-party front-end service provider may result in negative abnormal returns of the buyer firm. |
| Leitch & Sherif, 2017 [14] | Twitter mood, CEO succession announcements and stock returns | There is a negative relationship between Twitter sentiment and stock returns. Older CEOs are associated with larger fluctuations of the stock price. |
| Access Control | Cyber Security | Network Security |
| Authentication | Cybersecurity | Security Breach |
| Business Continuity | Denial of Service | Security Expenditure |
| Computer Breach | Disaster Recovery | Security Incident |
| Computer Intrusion | Encryption | Security Management |
| Computer Security | Hacker | Security Measure |
| Computer System Security | Information Security | Security Monitoring |
| Computer Virus | Infosec | Intrusion |
| Cyber Attack |
| Computer Attack | Computer Worm | Identity Theft |
| Computer Breach | Cyber Fraud | Network Intrusion |
| Computer Break-in | Cyber-attack | Phishing |
| Computer Intrusion | Data Theft | Security Breach |
| Computer Security | Denial of Service | Security Controls |
| Computer Virus | Hacker | Security Incident |
| News Source | Headline Length (Words) | Total Word Count |
|---|---|---|
| Number of keywords in the article | Presence of negative words in the headline | Number of negative words in the article |
| Negative words/total words | Presence of any keyword in the headline |
| The New York Times | Washington Post | San Jose Mercury News |
| USA Today | Los Angeles Times | The Washington Post |
| New York Daily News | New York Post | Chicago Tribune |
| Chicago Sun-Times | The Denver Post | The Wall Street Journal |
| The Dallas Morning News | Newsday | The Orange County Register |
| Houston Chronicle |
| Keywords | Total Number of News Articles | Number of Usable News Articles | Number of Repetitive News Articles |
|---|---|---|---|
| Computer Attack | 26 | 20 | 6 |
| Computer Breach | 16 | 15 | 1 |
| Computer Break-in | 0 | 0 | 0 |
| Computer Intrusion | 13 | 10 | 3 |
| Computer Security | 668 | 529 | 139 |
| Computer Virus | 63 | 50 | 13 |
| Computer Worm | 30 | 22 | 8 |
| Cyber Fraud | 1 | 1 | 0 |
| Cyber-attack | 157 | 142 | 15 |
| Data Theft | 134 | 110 | 24 |
| Denial of Service | 200 | 156 | 44 |
| Hacker | 964 | 786 | 178 |
| Identity Theft | 753 | 591 | 162 |
| Network Intrusion | 1 | 1 | 0 |
| Phishing | 326 | 256 | 70 |
| Security Breach | 427 | 348 | 79 |
| Security Controls | 46 | 33 | 13 |
| Security Incident | 21 | 15 | 6 |
| Total | 3846 | 3085 | 761 |
| Event Day | Number of News Articles | Average Abnormal Return (%) | Standard Deviation |
|---|---|---|---|
| −10 | 162 | 0.000953 | 0.017391 |
| −9 | 162 | −0.00057 | 0.012463 |
| −8 | 162 | −0.00053 | 0.01217 |
| −7 | 162 | 0.000293 | 0.0127 |
| −6 | 162 | −0.00051 | 0.016119 |
| −5 | 162 | −0.00167 | 0.01615 |
| −4 | 162 | 0.001379 | 0.013438 |
| −3 | 162 | −0.00012 | 0.012967 |
| −2 | 162 | −0.0002 | 0.011417 |
| −1 | 162 | −0.00044 | 0.014416 |
| 0 | 162 | 0.0002 | 0.014837 |
| 1 | 162 | −0.00214 | 0.010874 |
| 2 | 162 | 0.00174 | 0.014141 |
| 3 | 162 | −0.00068 | 0.01466 |
| 4 | 162 | −0.00029 | 0.014945 |
| 5 | 162 | −0.0017 | 0.013769 |
| 6 | 162 | −0.00202 | 0.017384 |
| 7 | 162 | −0.00114 | 0.012772 |
| 8 | 162 | 0.001956 | 0.015479 |
| 9 | 162 | −0.00216 | 0.013369 |
| 10 | 162 | −0.00062 | 0.013967 |
| N01 | USA Today | N02 | The Orange County Register |
| N03 | The Wall Street Journal | N04 | San Jose Mercury News |
| N05 | Houston Chronicle | N06 | The New York Times |
| N07 | Newsday | N08 | New York Post |
| N09 | Los Angeles Times | N10 | The Washington Post |
| N11 | Chicago Tribune | N12 | Washington Post |
| N13 | New York Daily News |
| Node 0 | ||
|---|---|---|
| Category | % | n |
| <0% | 51.852 | 84 |
| >=0% | 48.148 | 78 |
| Total | 100.000 | 162 |
| Node 4 | ||
|---|---|---|
| Category | % | n |
| <0% | 16.667 | 3 |
| >=0% | 83.333 | 15 |
| Total | 11.111 | 18 |
| Node 12 | ||
|---|---|---|
| Category | % | n |
| <0% | 60.000 | 3 |
| >=0% | 40.000 | 2 |
| Total | 3.086 | 5 |
| “Abnormal Return” is the Highest Decision Rule for the Following Items | ||||
|---|---|---|---|---|
| Decision Rule | The Most Common Type | Rule Precision | Forest Precision | Interest Index |
| (Number of negative words in the article <= 38.0) and (News source = {N01,N02,N03,N04,N05,N06,N08,N09,N10,N11,N12,N13}) and (Negative words/total word count > 3.633) and (Headline length (words) <= 13.0) and (Presence of negative words in the headline={No}) | <0% | 1.000 | 1.000 | 1.000 |
| (Total word count > 1215.0) and (Headline length (words) <= 23.0) and (News source = {N03,N04,N08}) and (News source = {N01,N03,N04,N08,N10}) | <0% | 1.000 | 1.000 | 1.000 |
| (Number of negative words in the article <= 38.0) and (Negative words/total word count <= 3.633) and (Headline length (words) <= 9.0) and (Presence of negative words in the headline ={No}) and (Headline length (words) > 6.0) | <0% | 1.000 | 1.000 | 1.000 |
| (Headline length (words) <= 6.0) and (Number of negative words in the article <= 38.0) and (Number of negative words in the article > 11.0) and (News source = {N04,N06}) and (News source = {N01,N04,N06,N08,N09,N10}) | <0% | 1.000 | 1.000 | 1.000 |
| (Number of negative words in the article > 38.0) and (Number of negative words in the article > 11.0) and (News source = {N04,N06}) and (News source = {N01,N04,N06,N08,N09,N10}) | >=0% | 1.000 | 1.000 | 1.000 |
© 2019 by the author. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Hung, C.-C. Analysis of Information Security News Content and Abnormal Returns of Enterprises. Big Data Cogn. Comput. 2019, 3, 24. https://doi.org/10.3390/bdcc3020024
Hung C-C. Analysis of Information Security News Content and Abnormal Returns of Enterprises. Big Data and Cognitive Computing. 2019; 3(2):24. https://doi.org/10.3390/bdcc3020024
Chicago/Turabian StyleHung, Chia-Ching. 2019. "Analysis of Information Security News Content and Abnormal Returns of Enterprises" Big Data and Cognitive Computing 3, no. 2: 24. https://doi.org/10.3390/bdcc3020024
APA StyleHung, C.-C. (2019). Analysis of Information Security News Content and Abnormal Returns of Enterprises. Big Data and Cognitive Computing, 3(2), 24. https://doi.org/10.3390/bdcc3020024




