Analysis of Nonlinear Bypass Route Computation for Wired and Wireless Network Cooperation Recovery System
Abstract
1. Introduction
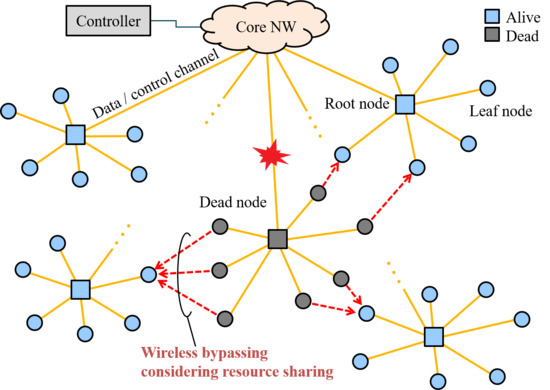
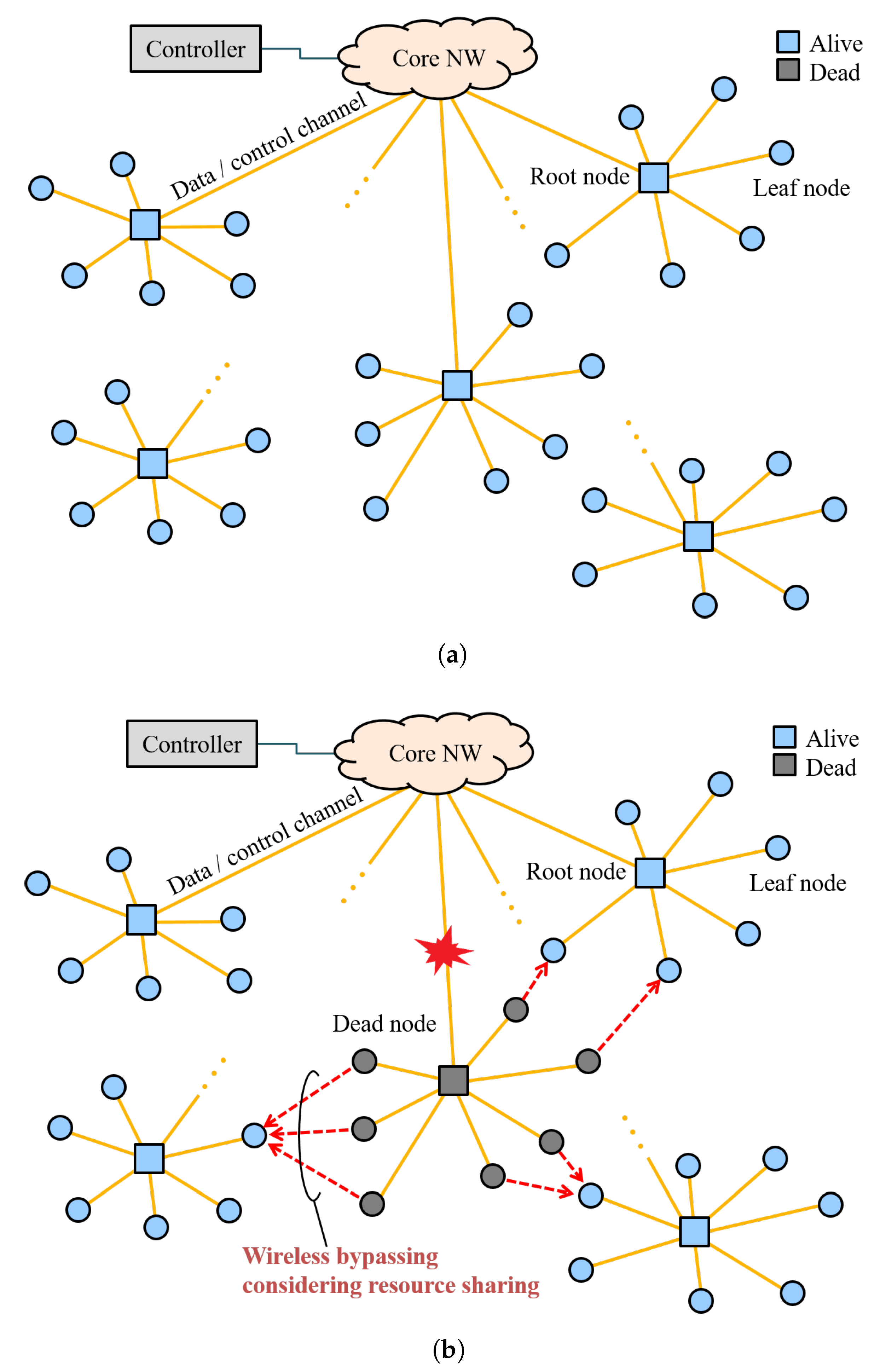
2. NeCo System
2.1. Overview
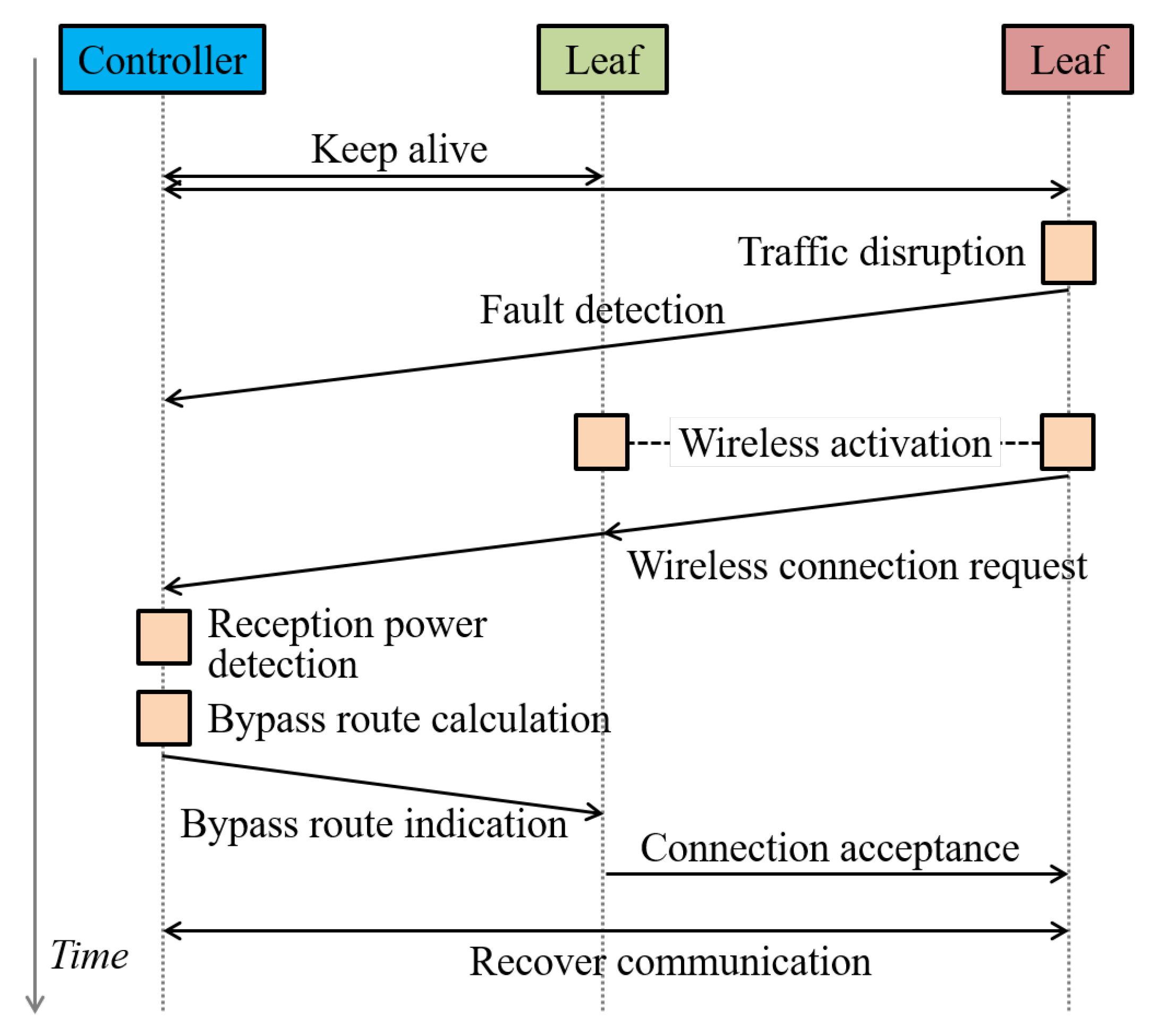
2.2. Routing
3. Proposed Routing
3.1. Concept
3.2. Formulation
3.3. Algorithm
| Algorithm 1 Route calculation algorithm. |
|
4. Computer Simulation
4.1. Simulation Condition
4.1.1. Transceiver Definitions
4.1.2. Channel and Traffic Models
4.1.3. Evaluation Metrics
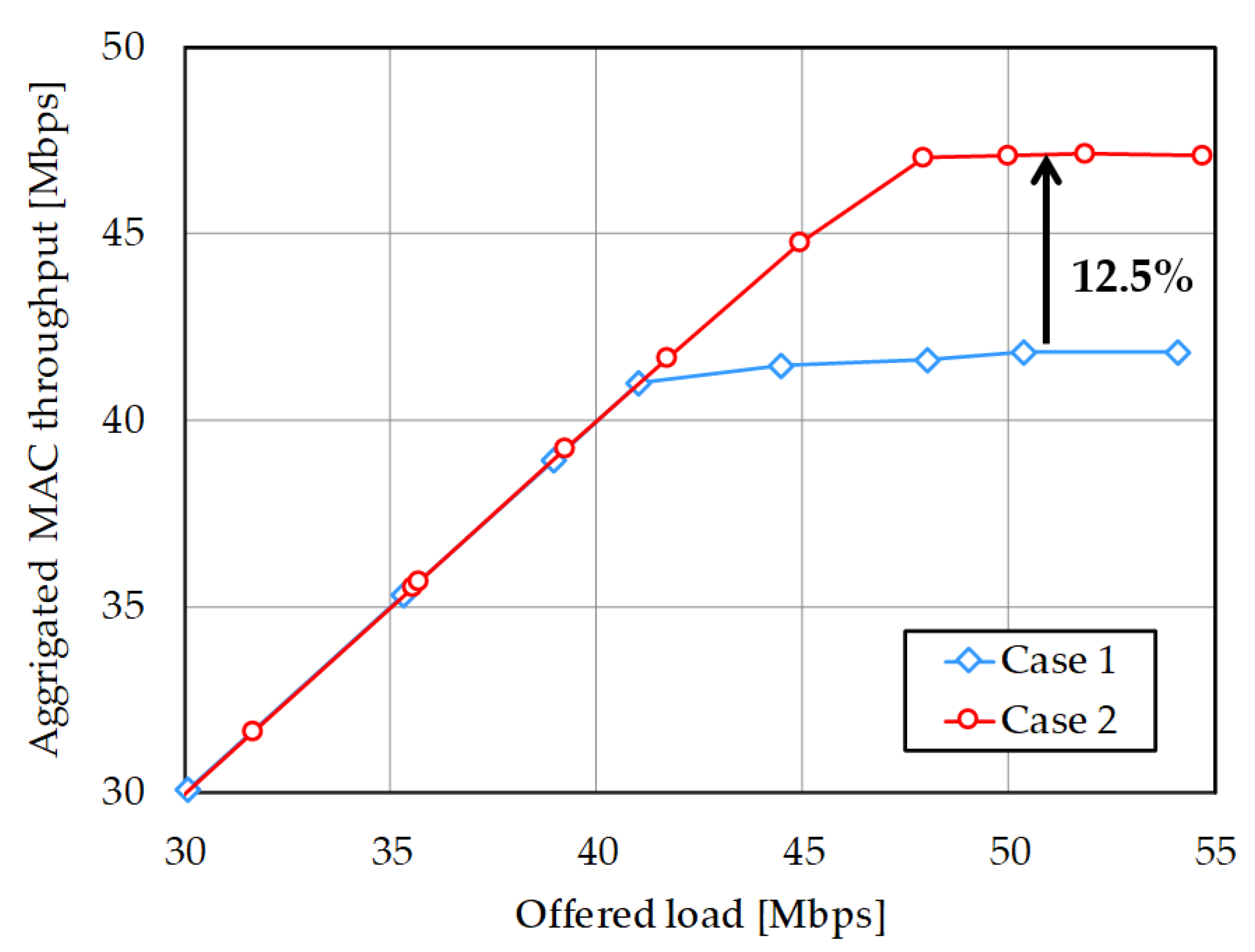
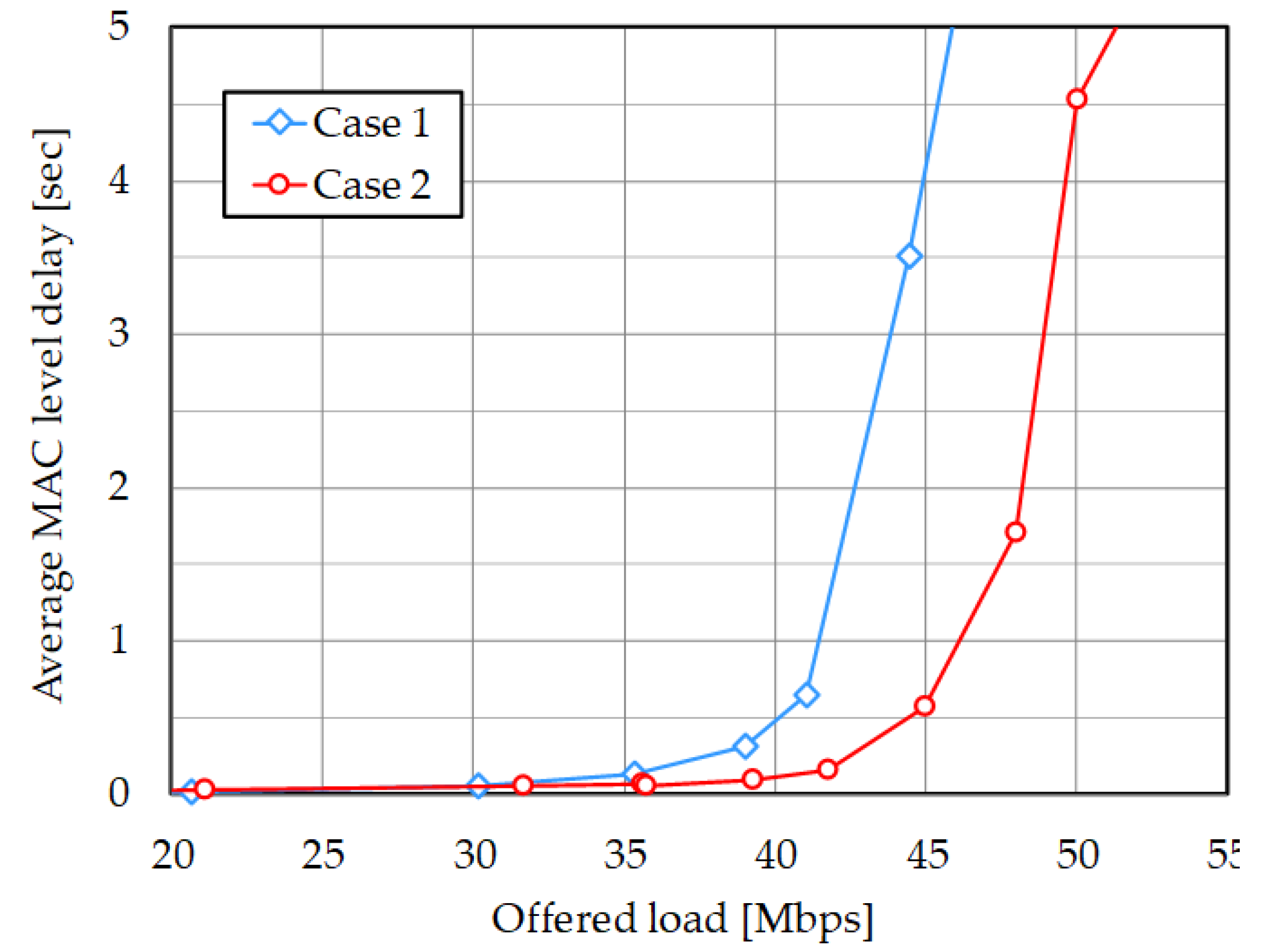
4.2. Simulation Results
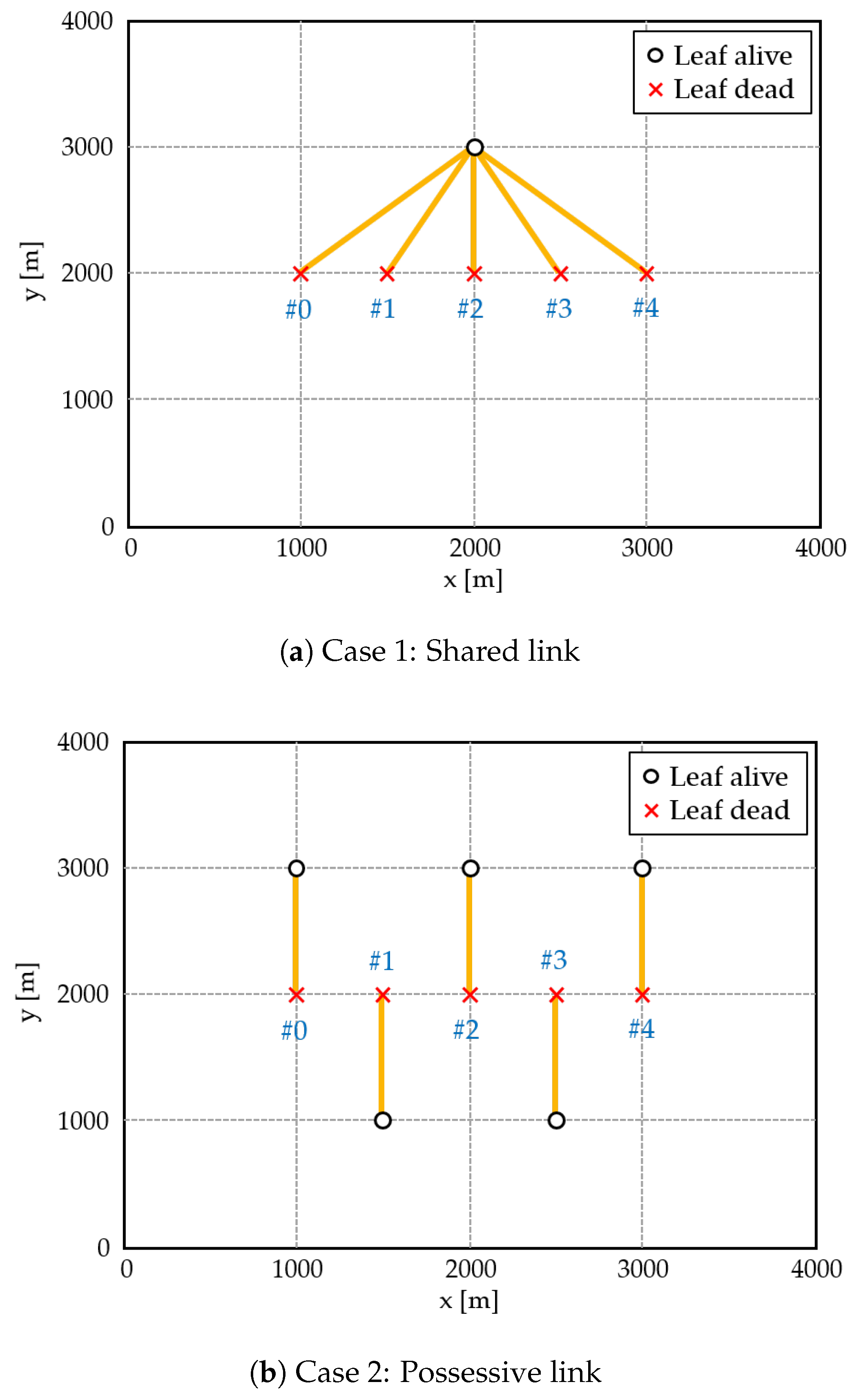
4.2.1. Fundamental Analysis in Simplified Topology
- Case 1: Shared link. All dead nodes are connected to one alive node.
- Case 2: Possessive link. Each node is connected to one alive node.
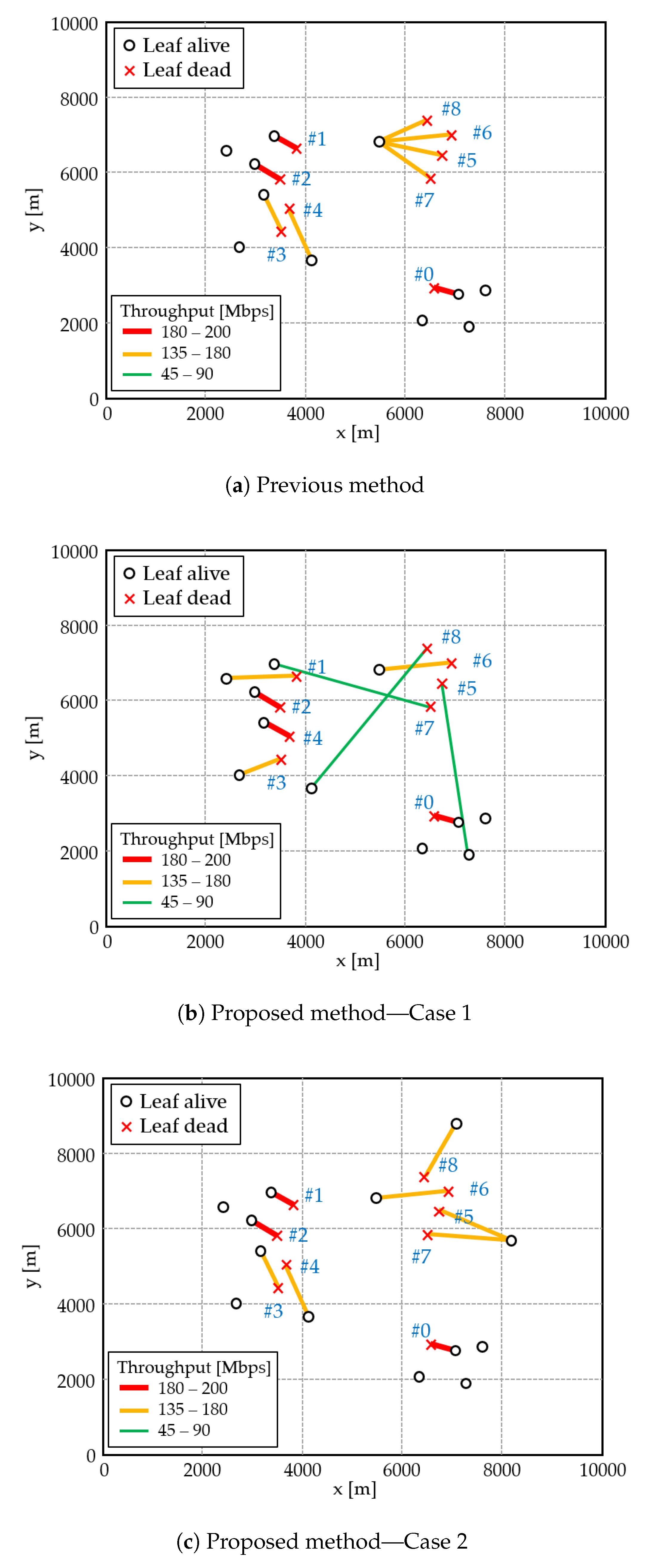
4.2.2. Practical Scenario in Random Topology
- (a)
- Previous method
- (b)
- Proposed nonlinear method—Case 1: sparse alive nodes
- (c)
- Proposed nonlinear method—Case 2: dense alive nodes
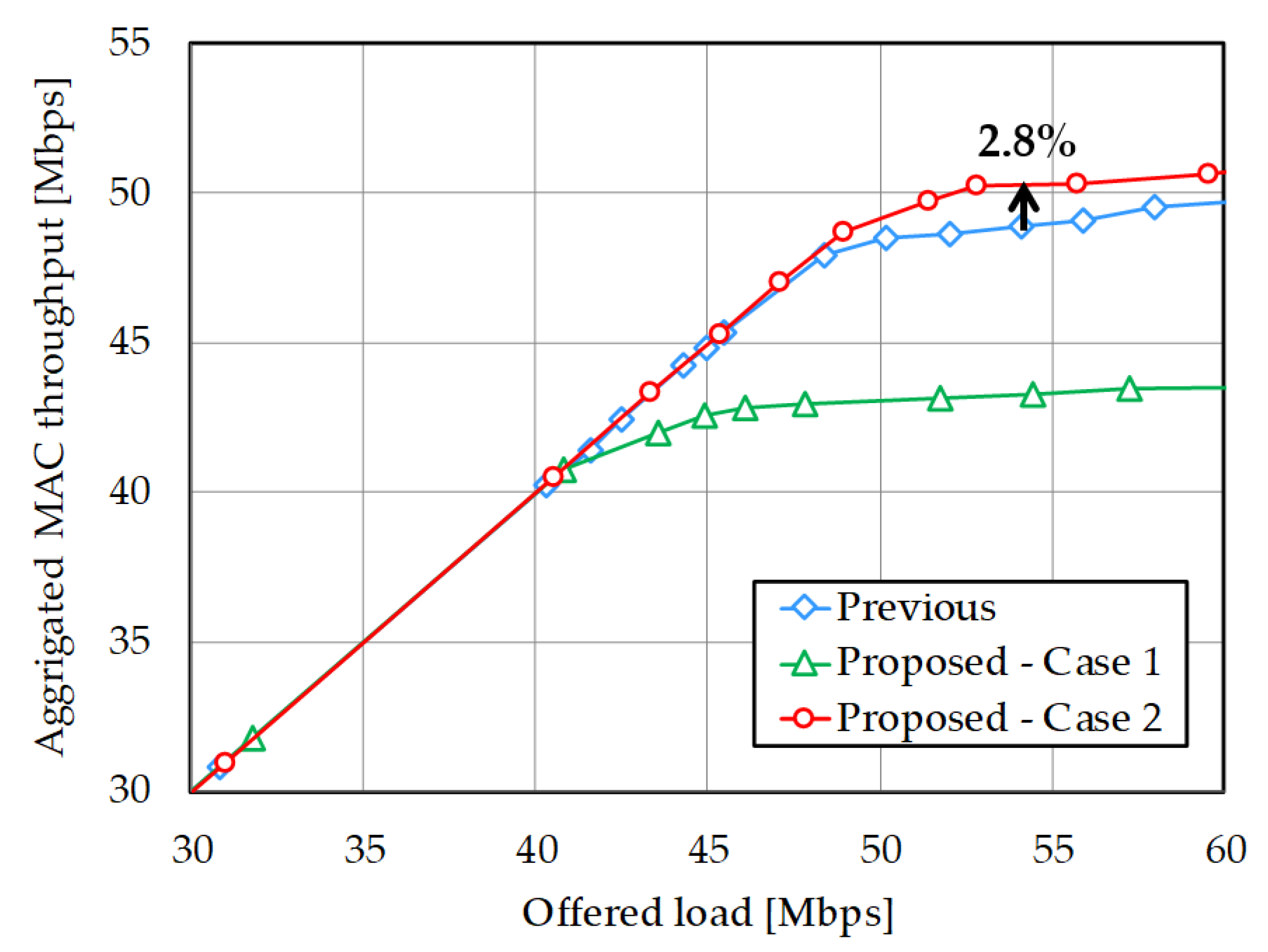
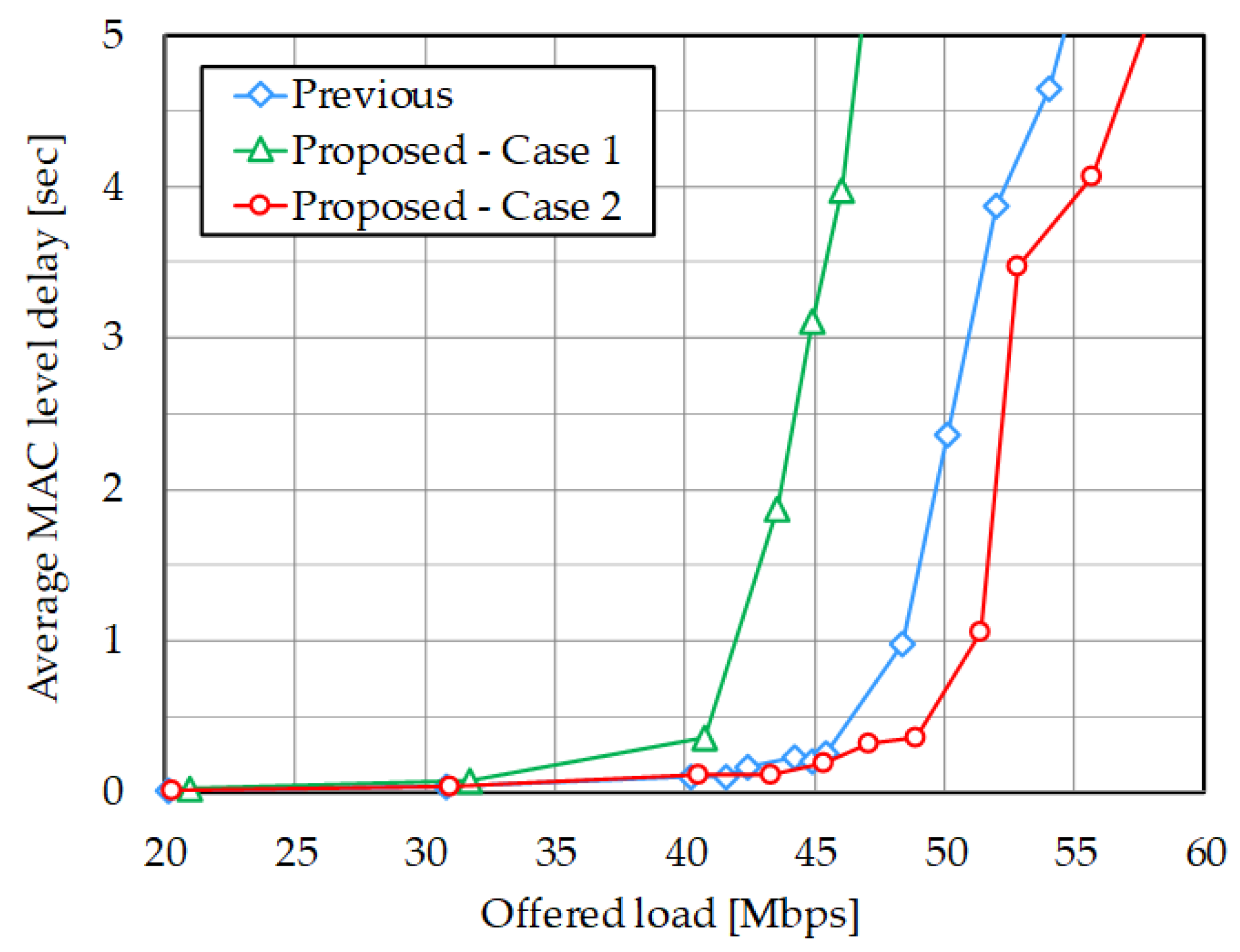
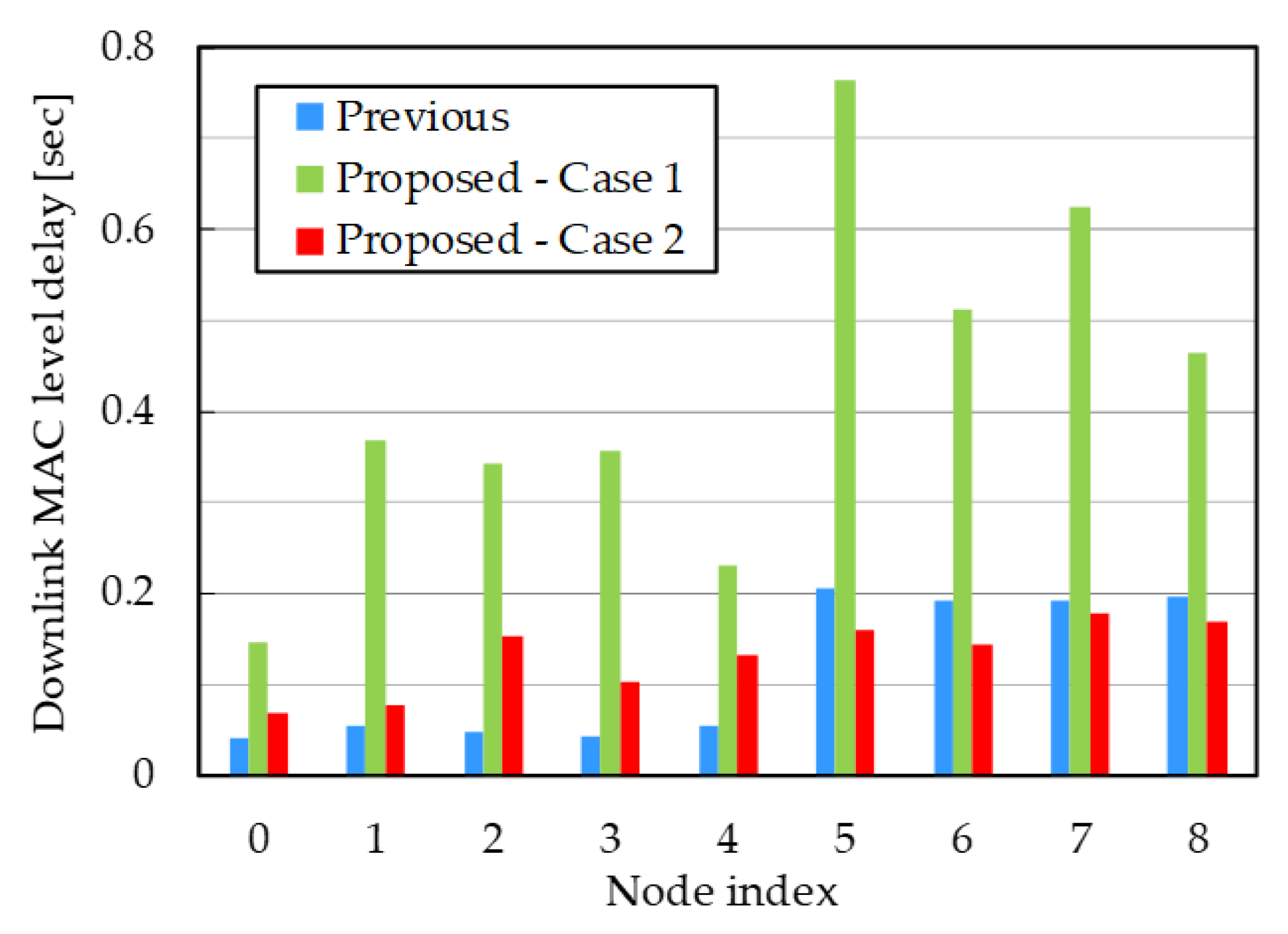
4.3. Discussion
5. Conclusions
Author Contributions
Funding
Conflicts of Interest
Abbreviations
| NeCo | Network Cooperation |
| PON | Passive Optical Network |
| LoS | Line-of-Sight |
| CSMA/CA | Carrier Sense Multiple Access with Collision Avoidance |
| PHY | PHYsical layer |
| GI | Guard Interval |
| LDPC | Low Density Parity Check |
| MCS | Modulation and Coding Scheme |
| RTS | Request-to-Send |
| CTS | Clear-to-Send |
| DL | Downlink |
| UL | Uplink |
| UDP | User Datagram Protocol |
| TCP | Transmission Control Protocol |
| MAC | Medium Access Control |
| FIFO | First-In First-Out |
References
- Thomas, G.; Gene, F.; McCarty, M. Hurricane Katrina: Social-Demographic Characteristics of Impacted Areas; University of North Texas Libraries: Denton, TX, USA, 2005. [Google Scholar]
- Nobuoto, N.; Yoshihisa, M. Comparison of Functional Damage and Restoration Processes of Utility Lifelines in the 2016 Kumamoto Earthquake, Japan with Two Great Earthquake Disasters in 1995 and 2011. JSCE J. Dis. FactSheets 2016, FS2016-L-0005, 1–9. [Google Scholar]
- Habib, M.F.; Tornatore, M.; Dikbiyik, F.; Mukherjee, B. Disaster survivability in optical communication networks. Comput. Commun. 2013, 36, 630–644. [Google Scholar] [CrossRef]
- De La Oliva, A.; Pérez, X.C.; Azcorra, A.; Di Giglio, A.; Cavaliere, F.; Tiegelbekkers, D.; Lessmann, J.; Haustein, T.; Mourad, A.; Iovanna, P. Xhaul: toward an integrated fronthaul/backhaul architecture in 5G networks. IEEE Wirel. Commun. 2015, 22, 32–40. [Google Scholar] [CrossRef]
- Atlam, H.F.; Walters, R.J.; Wills, G.B. Fog Computing and the Internet of Things: A Review. Big Data Cognit. Comput. 2018, 2, 10. [Google Scholar] [CrossRef]
- Kang, K.D.; Chen, L.; Yi, H.; Wang, B.; Sha, M. Real-Time Information Derivation from Big Sensor Data via Edge Computing. Big Data Cognit. Comput. 2017, 1, 5. [Google Scholar] [CrossRef]
- Nakayama, Y.; Sezaki, K. Per-Flow Throughput Fairness in Ring Aggregation Network with Multiple Edge Routers. Big Data Cognit. Comput. 2018, 2, 17. [Google Scholar] [CrossRef]
- Mitsui, T.; Sakamoto, T.; Hara, K.; Yoshimoto, N. Flexible and scalable PON protection architecture using N: M redundancy toward next generation access network. In Proceedings of the 17th Asia-Pacific Conference on Communications, Sabah, Malaysia, 2–5 October 2011; pp. 224–229. [Google Scholar]
- Tsutsumi, T.; Sakamoto, T.; Sakai, Y.; Fujiwara, T.; Ou, H.; Kimura, Y.; Suzuki, K.I. Long-reach and high-splitting-ratio 10G-EPON system with semiconductor optical amplifier and N: 1 OSU protection. J. Lightwave Technol. 2015, 33, 1660–1665. [Google Scholar] [CrossRef]
- Tsutsumi, T.; Sakai, Y.; Sakamoto, T.; Kubota, M.; Otaka, A. Field Trial and Analysis of N: 1 Redundant 10G-EPON Using Boost-type Semiconductor Optical Amplifier. In Proceedings of the 2015 Optical Fiber Communications Conference and Exhibition, Los Angeles, CA, USA, 22–26 March 2015. [Google Scholar]
- Manoj, B.S.; Baker, A.H. Communication challenges in emergency response. Commun. ACM 2007, 50, 51–53. [Google Scholar] [CrossRef]
- Portmann, M.; Pirzada, A.A. Wireless mesh networks for public safety and crisis management applications. IEEE Int. Comput. 2008, 12, 18–25. [Google Scholar] [CrossRef]
- Lien, Y.N.; Chi, L.C.; Huang, C.C. A multi-hop walkie-talkie-like emergency communication system for catastrophic natural disasters. In Proceedings of the 39th International Conference on Parallel Processing Workshops, San Diego, CA, USA, 13–16 September 2010. [Google Scholar]
- Ueda, Y. Vehicle-mounted Transportable Mobile Base Station and Backhaul Link for Disaster Relief Operation. New Breeze 2014 Summer 2014, 26, 2–3. [Google Scholar]
- Baldo, N.; Dini, P.; Mangues-Bafalluy, J.; Miozzo, M.; Núñez Martínez, J. Small cells, wireless backhaul and renewable energy: A solution for disaster aftermath communications. In Proceedings of the 4th International Conference on Cognitive Radio and Advanced Spectrum Management, Barcelona, Spain, 26–29 October 2011. [Google Scholar]
- Todd, T.D.; Sayegh, A.A.; Smadi, M.N.; Zhao, D. The need for access point power saving in solar powered WLAN mesh networks. IEEE Netw. 2008, 22, 4–10. [Google Scholar] [CrossRef]
- Li, J.; Blake, C.; De Couto, D.S.; Lee, H.I.; Morris, R. Capacity of Ad Hoc Wireless Networks. In Proceedings of the 7th Annual International Conference on Mobile Computing and Networking, Rome, Italy, 16–21 July 2001; pp. 61–69. [Google Scholar]
- Thota, S.; Bhaumik, P.; Chowdhury, P.; Mukherjee, B.; Sarkar, S. Exploiting wireless connectivity for robustness in WOBAN. IEEE Netw. 2013, 27, 72–79. [Google Scholar] [CrossRef]
- Sarkar, S.; Dixit, S.; Mukherjee, B. Hybrid wireless-optical broadband-access network (WOBAN): A review of relevant challenges. J. Lightwave Technol. 2007, 25, 3329–3340. [Google Scholar] [CrossRef]
- Yinpeng, Y.; Ranaweera, C.; Lim, C.; Wong, E.; Guo, L.; Liu, Y.; Nirmalathas, A. Optimization Framework for Deployment of Hybrid Fiber Wireless Networks with Survivability Constraints. In Proceedings of the Asia Communications and Photonics Conference 2015, Hong Kong, 19–23 November 2015. [Google Scholar]
- Maier, M. Survivability techniques for NG-PONs and FiWi access networks. In Proceedings of the 2012 IEEE International Conference on Communications (ICC), Ottawa, ON, Canada, 10–15 June 2012; pp. 6214–6219. [Google Scholar]
- Nakayama, Y.; Maruta, K.; Tsutsumi, T.; Sezaki, K. Wired and wireless network cooperation for quick recovery. In Proceedings of the IEEE International Conference on Communications (ICC), Kuala Lumpur, Malaysia, 22–27 May 2016; pp. 1–6. [Google Scholar]
- Nakayama, Y.; Maruta, K.; Tsutsumi, T.; Sezaki, K. Wired and Wireless Network Cooperation for Wide-Area Quick Disaster Recovery. IEEE Access 2018, 6, 2410–2424. [Google Scholar] [CrossRef]
- Nakayama, Y.; Maruta, K.; Tsutsumi, T.; Yasunaga, R.; Honda, K.; Sezaki, K. Recovery Node Layout Planning for Wired and Wireless Network Cooperation for Disaster Response. In Proceedings of the 2018 IEEE International Conference on Communications Workshops, Kansas City, MO, USA, 20–24 May 2018. [Google Scholar]
- Maruta, K.; Nakayama, Y.; Tsutsumi, T. Throughput Performance Evaluation on Wired and Wireless Network Cooperation Quick Recovery System Employing IEEE 802.11 DCF. In Proceedings of the Fifth International Conference on Network, Communication and Computing, Kyoto, Japan, 17–21 December 2016; pp. 267–271. [Google Scholar]
- IEEE. Wireless LAN Medium Access Control (MAC) and Physical Layer (PHY) Specifications. IEICE Tech. Rep. 2013, 108, 67–72. (In Japanese) [Google Scholar]
- 5 GHz Wireless Access System. 2006. (In Japanese). Available online: http://www.soumu.go.jp/main_sosiki/joho_tsusin/policyreports/joho_tsusin/pdf/tosin_061221_4.pdf (accessed on 29 August 2018).
- Mitsunaga, K.; Maruta, K.; Higa, Y.; Furukawa, H. Application of directional antenna to wireless multihop network enabled by IPT forwarding. In Proceedings of the 2008 2nd International Conference on Signal Processing and Communication Systems, Gold Coast, QLD, Australia, 15–17 December 2008; pp. 1–6. [Google Scholar] [CrossRef]
- Maruta, K.; Furukawa, H. Highly Efficient Multi Channel Packet Forwarding with Round Robin Intermittent Periodic Transmit for Multihop Wireless Backhaul Networks. Sensors 2017, 17, 2609. [Google Scholar] [CrossRef] [PubMed]
- Bruno, R.; Conti, M.; Gregori, E. IEEE 802.11 optimal performances: RTS/CTS mechanism vs. basic access. In Proceedings of the 13th IEEE International Symposium on Personal, Indoor and Mobile Radio Communications, Lisboa, Portugal, 18 September 2002; pp. 1747–1751. [Google Scholar] [CrossRef]
- Abrams, M.; Williams, S.; Abdulla, G.; Patel, S.; Ribler, R.; Fox, E.A. Multimedia Traffic Analysis Using CHITRA95. In Proceedings of the Third ACM International Conference on Multimedia, San Francisco, CA, USA, 5–9 November 1995; pp. 267–276. [Google Scholar]
- ISP Backbone Traffic in Japan. Available online: http://www.hongo.wide.ad.jp/InternetTraffic/data/ (accessed on 29 August 2018).
- Maruta, K.; Ohta, A.; Kurosaki, S.; Arai, T.; Iizuka, M. Experimental Investigation of Space Division Multiplexing on Massive Antenna Systems for Wireless Entrance. IEICE Trans. Commun. 2017, 100, 1436–1448. [Google Scholar] [CrossRef]
| Item | Value |
|---|---|
| Carrier frequency | GHz |
| System bandwidth | 40 MHz |
| Wireless interface | IEEE802.11ac [26] |
| RTS/CTS | Off |
| Number of antenna | 1, Omni-directional |
| Number of channel | 1 |
| Number of spatial stream | 1 |
| Guard interval length | Short: 400 nsec |
| Transmission power | 23 dBm |
| Antenna gain | 13 dBi |
| Channel model | Free space propagation |
| Poisson origination, | |
| Log-normal distribution | |
| Traffic model | UDP Packet: 1500 bytes, |
| Average: DL: 20, UL: 3 [31] | |
| Load ratio DL:UL = 6:1 [32] |
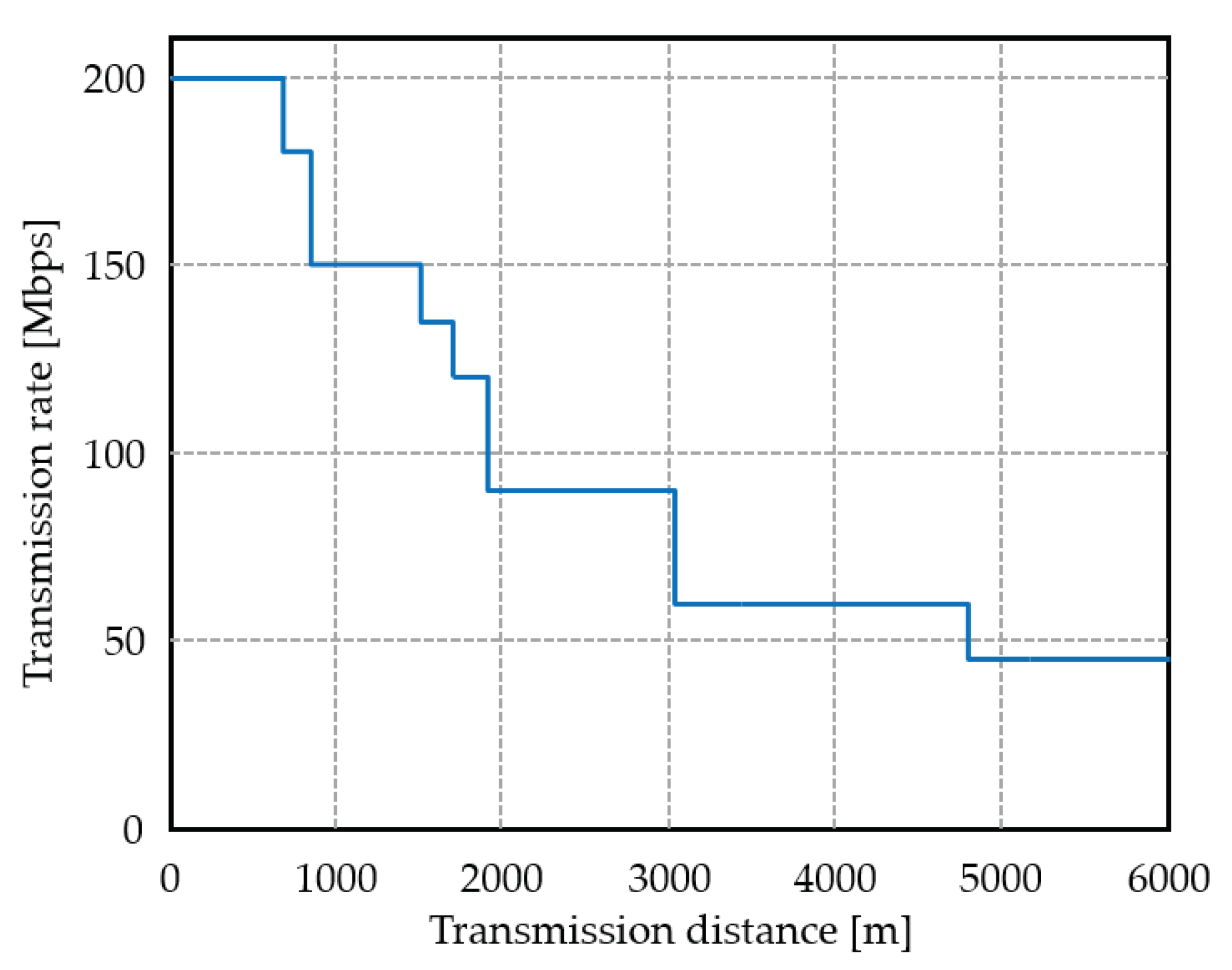
| MCS Index | Rx Level [dBm] | Tx Rate [Mbps] | Mod. Order | Coding Rate | [sec] |
|---|---|---|---|---|---|
| 0 | 15 | BPSK | 844 | ||
| 1 | 30 | QPSK | 444 | ||
| 2 | 45 | QPSK | 312 | ||
| 3 | 60 | 16QAM | 244 | ||
| 4 | 90 | 16QAM | 180 | ||
| 5 | 120 | 64QAM | 144 | ||
| 6 | 135 | 64QAM | 132 | ||
| 7 | 150 | 64QAM | 124 | ||
| 8 | 180 | 256QAM | 112 | ||
| 9 | 200 | 256QAM | 104 |
| Case 1 | Case 2 | |
|---|---|---|
| Saturated throughput value [Mbps] | 41.85 | 47.09 |
| Improvement | —- | 12.5% |
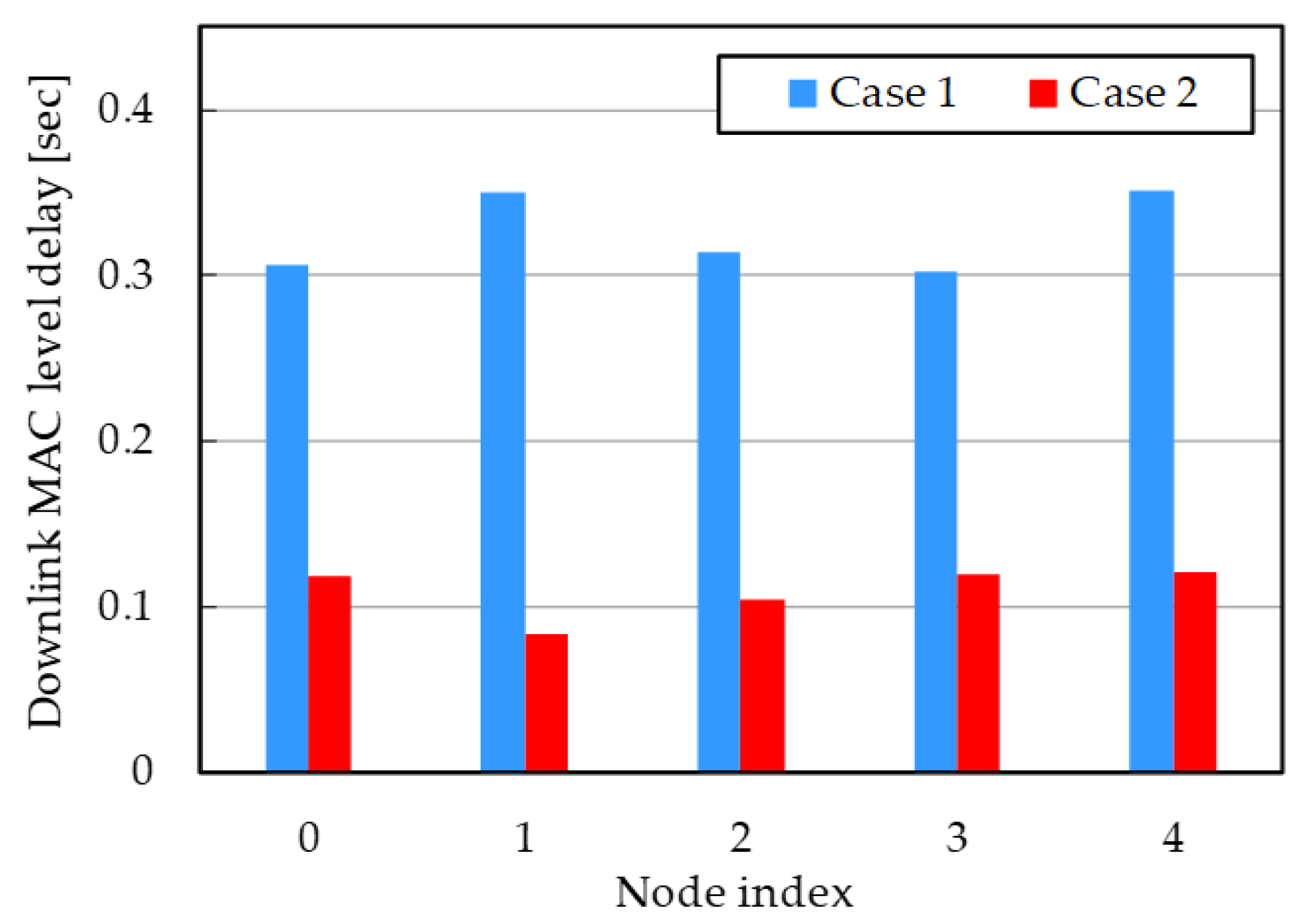
| Node index | 0 | 1 | 2 | 3 | 4 | |
|---|---|---|---|---|---|---|
| Delay [sec] | Case 1 | 0.31 | 0.35 | 0.31 | 0.30 | 0.35 |
| Case 2 | 0.12 | 0.08 | 0.10 | 0.12 | 0.12 | |
| Improvement | 61.6% | 75.9% | 66.8% | 60.3% | 65.5% | |
| Previous | Proposed—Case 1 | Proposed–Case 2 | |
|---|---|---|---|
| Saturated throughput value [Mbps] | 48.89 | 50.24 | 43.31 |
| Improvement/Degradation | —- | 2.8% | % |
| Node Index | 5 | 6 | 7 | 8 | |
|---|---|---|---|---|---|
| Delay [sec] | Previous | 0.21 | 0.19 | 0.19 | 0.20 |
| Proposed—Case 2 | 0.16 | 0.14 | 0.18 | 0.17 | |
| Improvement | 22.3% | 25.3% | 6.5% | 14.0% | |
© 2018 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Nakayama, Y.; Maruta, K. Analysis of Nonlinear Bypass Route Computation for Wired and Wireless Network Cooperation Recovery System. Big Data Cogn. Comput. 2018, 2, 28. https://doi.org/10.3390/bdcc2030028
Nakayama Y, Maruta K. Analysis of Nonlinear Bypass Route Computation for Wired and Wireless Network Cooperation Recovery System. Big Data and Cognitive Computing. 2018; 2(3):28. https://doi.org/10.3390/bdcc2030028
Chicago/Turabian StyleNakayama, Yu, and Kazuki Maruta. 2018. "Analysis of Nonlinear Bypass Route Computation for Wired and Wireless Network Cooperation Recovery System" Big Data and Cognitive Computing 2, no. 3: 28. https://doi.org/10.3390/bdcc2030028
APA StyleNakayama, Y., & Maruta, K. (2018). Analysis of Nonlinear Bypass Route Computation for Wired and Wireless Network Cooperation Recovery System. Big Data and Cognitive Computing, 2(3), 28. https://doi.org/10.3390/bdcc2030028