Fog Computing and the Internet of Things: A Review
Abstract
:1. Introduction
- Discussing recent articles which investigate the integration of fog computing with different IoT applications.
- Investigating IoT challenges and how they will be resolved by integrating the IoT with fog computing.
- Providing various IoT applications that benefit from the integration of the fog with the IoT.
- Discussing the challenges that result from integrating the IoT with fog computing.
- Discussing future research directions regarding fog computing and the IoT.
2. Challenges of the Cloud of Things
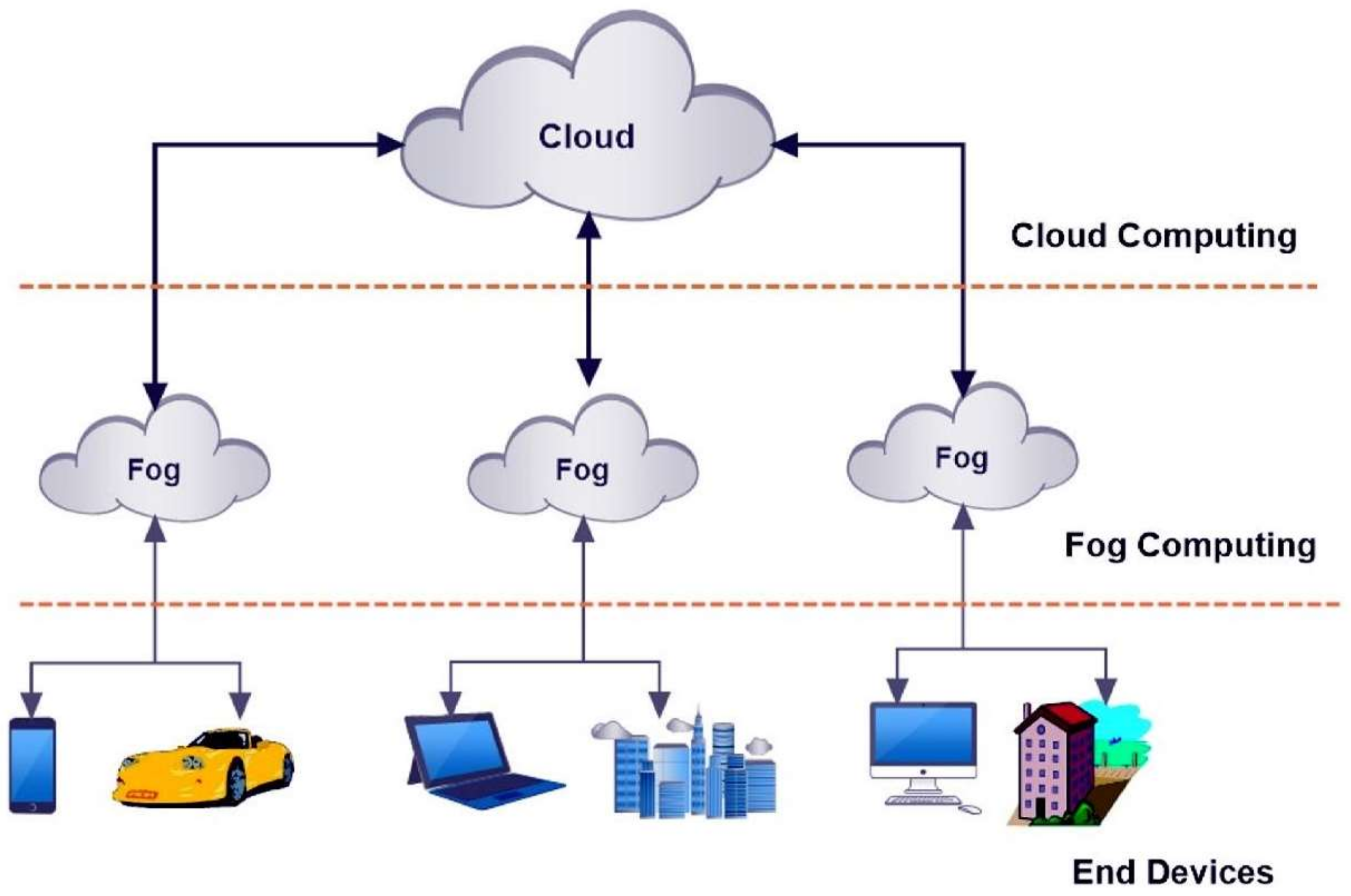
3. Fog Computing
3.1. Definition of Fog Computing
3.2. Characteristics of Fog Computing
- Location awareness and low latency: Fog computing supports location awareness in which fog nodes can be deployed in different locations. In addition, as the fog is closer to end devices, it provides lower latency when processing the data of end devices.
- Geographical distribution: In contrast to the centralized cloud, the services and applications provided by the fog are distributed and can be deployed anywhere.
- Scalability: There are large-scale sensor networks which monitor the surrounding environment. The fog provides distributed computing and storage resources which can work with such large-scale end devices.
- Support for mobility: One of the important aspects of fog applications is the ability to connect directly to mobile devices and therefore enable mobility methods, such as locator ID separation protocol (LISP) which needs a distributed directory system.
- Real-time interactions: Fog computing applications provide real-time interactions between fog nodes rather than the batch processing employed in the cloud.
- Heterogeneity: Fog nodes or end devices are designed by different manufacturers and thus come in different forms and need to be deployed according to their platforms. The fog has the ability to work on different platforms.
- Interoperability: Fog components can interoperate and work with different domains and across different service providers.
- Support for on-line analytics and interplay with the cloud: The fog is placed between the cloud and end devices to play an important role in the absorption and processing of the data close to end devices.
3.3. Benefits of Fog Computing
- Greater business agility: With the use of the right tools, fog computing applications can be quickly developed and deployed. In addition, these applications can program the machine to work according to the customer needs [17].
- Low latency: The fog has the ability to support real-time services (e.g., gaming, video streaming) [19].
- Geographical and large-scale distribution: Fog computing can provide distributed computing and storage resources to large and widely distributed applications [19].
- Lower operating expense: Saving network bandwidth by processing selected data locally instead of sending them to the cloud for analysis [17].
- Flexibility and heterogeneity: Fog computing allows the collaboration of different physical environments and infrastructures among multiple services [20].
- Scalability: The closeness of fog computing to end devices enables scaling the number of connected devices and services [19].
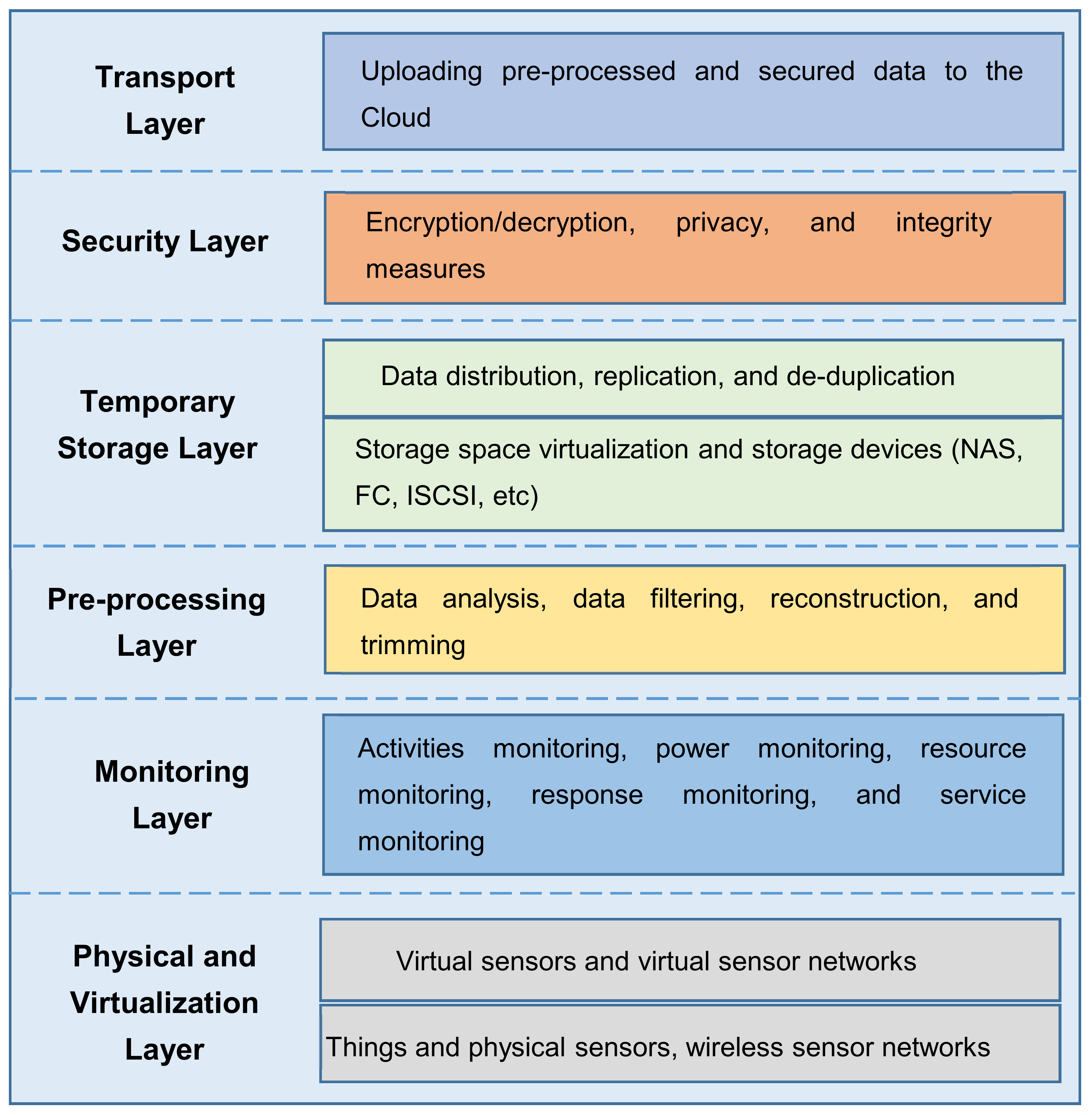
3.4. Architecture of Fog Computing
4. Fog Computing with IoT
5. Applications of Fog with the IoT
5.1. Connected Car
5.2. Smart Traffic Lights
5.3. Smart Home
5.4. Wireless Sensor and Actuator Networks
5.5. Healthcare and Activity Tracking
5.6. IoT and Cyber–Physical Systems
5.7. Augmented Reality
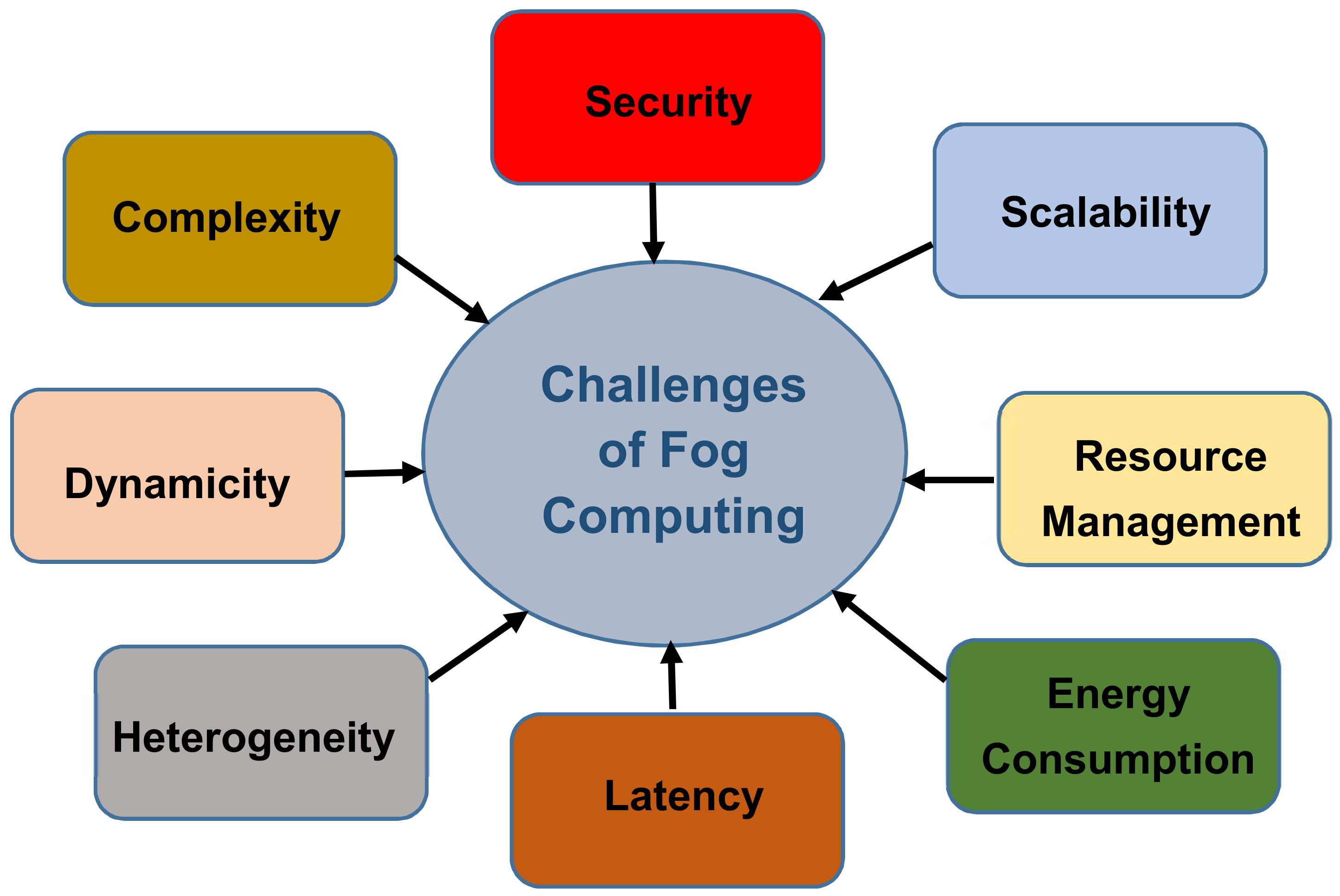
6. Challenges of Fog with the IoT
- (1)
- Scalability: The number of IoT devices is in the order of billions, which generates a huge amount of data and requires a huge amount of resources such as processing power and storage. Therefore, fog servers should be able to support all these devices with adequate resources. The real challenge will be the capability to respond to the rapid growth of IoT devices and applications [53,54].
- (2)
- Complexity: Since there are many IoT devices and sensors designed by different manufacturers, choosing the optimal components is becoming very complicated, especially with different software and hardware configurations and personal requirements. In addition, in some cases, applications with high-security requirements require specific hardware and protocols to function, which increases the difficulty of the operation [53].
- (3)
- Dynamicity: One of the important features of IoT devices is the ability to evolve and dynamically change their workflow composition. This challenge will alter the internal properties and performance of IoT devices. In addition, handheld devices suffer from software and hardware aging, which will result in changing workflow behaviour and device properties. Therefore, fog nodes will need automatic and intelligent reconfiguration of the topological structure and assigned resources [53].
- (4)
- Heterogeneity: There are many IoT devices and sensors which are designed by different manufacturers. These devices have various capabilities in communication radios, sensors, computing powers, storage, etc. The management and coordination of networks such heterogeneous IoT devices and the selection of the appropriate resources will become a big challenge [14].
- (5)
- Latency: One of the main reasons to replace the cloud with fog computing is providing low latency, especially for time-sensitive applications. However, there are many factors presenting a high latency of application or service performance on fog computing platforms. The fog with high latency will lead to user dissatisfaction [54].
- (6)
- Security: Although fog nodes will need to be protected by using the same policy, controls and procedures and use the same physical security and cybersecurity solutions [17], the fog environment itself is vulnerable and less secure than cloud computing. Existing security and privacy measurements of cloud computing cannot be directly applied to the fog due to its mobility, heterogeneity and large-scale geo-distribution [55]. Many research studies focus on cryptography and authentication to improve network security to protect against cyber-attacks in fog computing [14,53].
- (7)
- Resource management: Fog end devices are often network devices equipped with additional storage and computing power. However, it is difficult for such devices to match the resource capacity of traditional servers, let alone the cloud. Therefore, sensible management of fog resources is required for efficient operation of the fog computing environment [27,35].
- (8)
- Energy consumption: The fog environment involves a large number of fog end devices; the computation is distributed and can be less energy-efficient than the centralized cloud model of computation. Therefore, reducing energy consumed in fog computing is an important challenge that needs to be addressed [56].
7. Open Issues of Fog with the IoT
7.1. Communications between the Fog and the Cloud
7.2. Communications between Fog Servers
7.3. Fog Computing Deployment
7.4. Parallel Computation Algorithm
7.5. Security
7.6. End User Privacy
8. Conclusions
Acknowledgments
Conflicts of Interest
References
- Atlam, H.F.; Alenezi, A.; Walters, R.J.; Wills, G.B. An Overview of Risk Estimation Techniques in Risk-based Access Control for the Internet of Things. In Proceedings of the 2nd International Conference on Internet of Things, Big Data and Security (IoTBDS 2017), Porto, Portugal, 24–26 April 2017; pp. 254–260. [Google Scholar]
- Giang, N.; Kim, S.; Kim, D.; Jung, M.; Kastner, W. Extending the EPCIS with Building Automation Systems: A New Information System for the Internet of Things. In Proceedings of the 2014 Eighth International Conference on Innovative Mobile and Internet Services in Ubiquitous Computing, Birmingham, UK, 2–4 July 2014; pp. 364–369. [Google Scholar]
- Atlam, H.F.; Alenezi, A.; Hussein, R.K.; Wills, G.B. Validation of an Adaptive Risk-Based Access Control Model for the Internet of Things. Int. J. Comput. Netw. Inf. Secur. 2018, 10, 26–35. [Google Scholar] [CrossRef]
- Atlam, H.F.; Alenezi, A.; Alharthi, A.; Walters, R.; Wills, G. Integration of cloud computing with internet of things: challenges and open issues. In Proceedings of the 2017 IEEE International Conference on Internet of Things (iThings) and IEEE Green Computing and Communications (GreenCom) and IEEE Cyber, Physical and Social Computing (CPSCom) and IEEE Smart Data (SmartData), Exeter, UK, 21–23 June 2017; pp. 670–675. [Google Scholar]
- Ai, Y.; Peng, M.; Zhang, K. Edge cloud computing technologies for internet of things: A primer. Digit. Commun. Netw. 2017, in press. [Google Scholar] [CrossRef]
- Bonomi, F.; Milito, R.; Zhu, J.; Addepalli, S. Fog computing and its role in the internet of things. In Proceedings of the First Edition of the MCC Workshop on Mobile Cloud Computing-MCC ’12, Helsinki, Finland, 17 August 2012; pp. 13–15. [Google Scholar]
- Peter, N. FOG Computing and Its Real Time Applications. Int. J. Emerg. Technol. Adv. Eng. 2015, 5, 266–269. [Google Scholar]
- Wen, Z.; Yang, R.; Garraghan, P.; Lin, T.; Xu, J.; Rovatsos, M. Fog orchestration for internet of things services. IEEE Internet Comput. 2017, 21, 16–24. [Google Scholar] [CrossRef]
- Yang, Y. FA2ST: Fog as a Service Technology. In Proceedings of the 2017 IEEE 41st IEEE Annual Computer Software and Applications Conference, Turin, Italy, 4–8 July 2017; p. 708. [Google Scholar]
- Chiang, M.; Zhang, T. Fog and IoT: An Overview of Research Opportunities. IEEE Internet Things J. 2016, 3, 854–864. [Google Scholar] [CrossRef]
- Aazam, M.; Huh, E.N. Fog computing and smart gateway based communication for cloud of things. In Proceedings of the 2014 International Conference on Future Internet of Things Cloud, FiCloud 2014, Barcelona, Spain, 27–29 August 2014; pp. 464–470. [Google Scholar]
- Atlam, H.F.; Alenezi, A.; Walters, R.J.; Wills, G.B.; Daniel, J. Developing an adaptive Risk-based access control model for the Internet of Things. In Proceedings of the 2017 IEEE International Conference on Internet of Things (iThings) and IEEE Green Computing and Communications (GreenCom) and IEEE Cyber, Physical and Social Computing (CPSCom) and IEEE Smart Data (SmartData), Exeter, UK, 21–23 June 2017; pp. 655–661. [Google Scholar]
- Verma, M.; Bhardwaj, N.; Yadav, A.K. Real Time Efficient Scheduling Algorithm for Load Balancing in Fog Computing Environment. Int. J. Inf. Technol. Comput. Sci. 2016, 8, 1–10. [Google Scholar] [CrossRef]
- Yi, S.; Hao, Z.; Qin, Z.; Li, Q. Fog computing: Platform and applications. In Proceedings of the 3rd Workshop on Hot Topics in Web Systems and Technologies, HotWeb 2015, Washington, DC, USA, 24–25 October 2016; pp. 73–78. [Google Scholar]
- Vaquero, L.M.; Rodero-Merino, L. Finding Your Way in the Fog: Towards a Comprehensive Definition of Fog Computing. ACM SIGCOMM Comput. Commun. Rev. 2014, 44, 27–32. [Google Scholar] [CrossRef]
- Definition of Fog Computing. Available online: https://www.openfogconsortium.org/#definition-of-fog-computing (accessed on 24 March 2018).
- Fog Computing and the Internet of Things: Extend the Cloud to Where the Things Are. White Paper. 2016. Available online: http://www.cisco.com/c/dam/en_us/solutions/trends/iot/docs/computing-overview.pdf (accessed on 8 April 2018).
- Liu, Y.; Fieldsend, J.E.; Min, G. A Framework of Fog Computing: Architecture, Challenges and Optimization. IEEE Access 2017, 4, 1–10. [Google Scholar] [CrossRef]
- Peralta, G.; Iglesias-Urkia, M.; Barcelo, M.; Gomez, R.; Moran, A.; Bilbao, J. Fog computing based efficient IoT scheme for the Industry 4.0. In Proceedings of the 2017 IEEE International Workshop of Electronics, Control, Measurement, Signals and their application to Mechatronics, San Sebastian, Spain, 24–26 May 2017; pp. 1–6. [Google Scholar]
- Bonomi, F.; Milito, R.; Natarajan, P.; Zhu, J. Fog Computing: A Platform for Internet of Things and Analytics. In Big Data and Internet of Things: A Roadmap for Smart Environments; Studies in Computational Intelligence; Springer: Cham, Switzerland, 2014; Volume 546, pp. 169–186. [Google Scholar]
- Shi, Y.; Ding, G.; Wang, H.; Roman, H.E.; Lu, S. The fog computing service for healthcare. In Proceedings of the 2015 2nd International Symposium on Future Information and Communication Technologies for Ubiquitous HealthCare (Ubi-HealthTech), Beijing, China, 28–30 May 2015; pp. 1–5. [Google Scholar]
- Mukherjee, M.; Shu, L.; Wang, D. Survey of Fog Computing: Fundamental, Network Applications, and Research Challenges. IEEE Commun. Surv. Tutor. 2018, PP. [Google Scholar] [CrossRef]
- Aazam, M.; Huh, E.N. Fog computing micro datacenter based dynamic resource estimation and pricing model for IoT. Proc. Int. Conf. Adv. Inf. Netw. Appl. AINA 2015, 2015, 687–694. [Google Scholar]
- Muntjir, M.; Rahul, M.; Alhumyani, H.A. An Analysis of Internet of Things (IoT): Novel Architectures, Modern Applications, Security Aspects and Future Scope with Latest Case Studies. Int. J. Eng. Res. Technol. 2017, 6, 422–447. [Google Scholar]
- Aazam, M.; Hung, P.P.; Huh, E. Smart Gateway Based Communication for Cloud of Things. In Proceedings of the 2014 IEEE Ninth International Conference on Intelligent Sensors, Sensor Networks and Information Processing, Singapore, 21–24 April 2014; pp. 1–6. [Google Scholar]
- Marques, B.; Machado, I.; Sena, A.; Castro, M.C. A Communication Protocol for Fog Computing Based on Network Coding Applied to Wireless Sensors. In Proceedings of the 2017 IEEE International Symposium on High Performance Computer Architecture, Vosendorf, Austria, 24–28 February 2017; pp. 109–114. [Google Scholar]
- Mouradian, C.; Naboulsi, D.; Yangui, S.; Glitho, R.H.; Morrow, M.J.; Polakos, P.A. A Comprehensive Survey on Fog Computing: State-of-the-art and Research Challenges. IEEE Commun. Surv. Tutor. 2017, 20, 416–464. [Google Scholar] [CrossRef]
- Agarwal, S.; Yadav, S.; Yadav, A.K. An Efficient Architecture and Algorithm for Resource Provisioning in Fog Computing. Int. J. Inf. Eng. Electron. Bus. 2016, 8, 48–61. [Google Scholar] [CrossRef]
- Atlam, H.F.; Alassafi, M.O.; Alenezi, A.; Walters, R.J.; Wills, G.B. XACML for Building Access Control Policies in Internet of Things. In Proceedings of the 3rd International Conference on Internet of Things, Big Data and Security (IoTBDS 2018), Setúbal, Portugal, 19–21 March 2018; pp. 253–260. [Google Scholar]
- Ketel, M. Fog-Cloud Services for IoT. In Proceedings of the SouthEast Conference, Kennesaw, GA, USA, 13–15 April 2017; pp. 262–264. [Google Scholar]
- Skarlat, O.; Schulte, S.; Borkowski, M.; Leitner, P. Resource provisioning for IoT services in the fog. In Proceedings of the 2016 IEEE 9th International Conference on Service-Oriented Computing and Applications, SOCA 2016, Macau, China, 4–6 November 2016; pp. 32–39. [Google Scholar]
- Saharan, K.P.; Kumar, A. Fog in Comparison to Cloud: A Survey. Int. J. Comput. Appl. 2015, 122, 10–12. [Google Scholar]
- Yi, S.; Li, C.; Li, Q. A Survey of Fog Computing. In Proceedings of the 2015 Workshop on Mobile Big Data-Mobidata ’15, Hangzhou, China, 21 June 2015; pp. 37–42. [Google Scholar]
- Puliafito, C.; Mingozzi, E.; Anastasi, G. Fog Computing for the Internet of Mobile Things: Issues and Challenges. In Proceedings of the 2017 International Conference on Smart Computing (SMARTCOMP), Hong Kong, China, 29–31 May 2017; pp. 1–6. [Google Scholar]
- Dastjerdi, A.V.; Gupta, H.; Calheiros, R.N.; Ghosh, S.K.; Buyya, R. Fog Computing: Principles, architectures, and applications. In Internet of Things: Principles and Paradigms; Morgan Kaufmann Publishers Inc.: San Francisco, CA, USA, 2016; pp. 61–75. [Google Scholar]
- Suárez-Albela, M.; Fernández-Caramés, T.M.; Fraga-Lamas, P.; Castedo, L. A practical evaluation of a high-security energy-efficient gateway for IoT fog computing applications. Sensors 2017, 17, 1–39. [Google Scholar] [CrossRef] [PubMed]
- Hong, K.; Lillethun, D.; Ramachandran, U.; Ottenwälder, B.; Koldehofe, B. Mobile Fog: A Programming Model for Large–Scale Applications on the Internet of Things. In Proceedings of the Second ACM SIGCOMM Workshop on Mobile Cloud Computing, Hong Kong, China, 16 August 2003; p. 15. [Google Scholar]
- Yousefpour, A.; Ishigaki, G.; Jue, J.P. Fog Computing: Towards Minimizing Delay in the Internet of Things. In Proceedings of the 2017 IEEE 1st International Conference on Edge Computing, Honolulu, HI, USA, 25–30 June 2017; pp. 17–24. [Google Scholar]
- Gazis, V.; Leonardi, A.; Mathioudakis, K.; Sasloglou, K.; Kikiras, P.; Sudhaakar, R. Components of fog computing in an industrial internet of things context. In Proceedings of the 12th Annual IEEE International Conference on Sensing, Communication, and Networking-Workshops, SECON Workshops 2015, Seattle, WA, USA, 22–25 June 2015; pp. 37–42. [Google Scholar]
- Alrawais, A.; Alhothaily, A.; Hu, C.; Cheng, X. Fog Computing for the Internet of Things: Security and Privacy Issues. IEEE Internet Comput. 2017, 21, 34–42. [Google Scholar] [CrossRef]
- Lee, K.; Kim, D.; Ha, D.; Rajput, U.; Oh, H. On security and privacy issues of fog computing supported Internet of Things environment. In Proceedings of the 6th International Conference on the Network of the Future (NOF), Montreal, QC, USA; 2015; pp. 1–3. [Google Scholar] [CrossRef]
- Hou, X.; Li, Y.; Chen, M.; Wu, D.; Jin, D.; Chen, S. Vehicular Fog Computing: A Viewpoint of Vehicles as the Infrastructures. IEEE Trans. Veh. Technol. 2016, 65, 3860–3873. [Google Scholar] [CrossRef]
- Sookhak, M.; Yu, F.R.; He, Y.; Talebian, H.; Safa, N.S.; Zhao, N.; Khan, M.K.; Kumar, N. Fog Vehicular Computing: Augmentation of Fog Computing Using Vehicular Cloud Computing. IEEE Veh. Technol. Mag. 2017, 12, 55–64. [Google Scholar] [CrossRef]
- Khan, S.; Parkinson, S.; Qin, Y. Fog computing security: A review of current applications and security solutions. J. Cloud Comput. 2017, 6, 19. [Google Scholar] [CrossRef]
- Stojmenovic, I.; Wen, S. The Fog Computing Paradigm: Scenarios and Security Issues. In Proceedings of the 2014 Federated Conference on Computer Science and Information Systems, Warsaw, Poland, 7–10 September 2014; Volume 2, pp. 1–8. [Google Scholar]
- Mahmud, R.; Kotagiri, R.; Buyya, R. Fog Computing: A Taxonomy, Survey and Future Directions. In Internet of Everything: Internet of Things (Technology, Communications and Computing); Springer: Singapore, 2016; pp. 103–130. [Google Scholar]
- Adhatarao, S.S.; Arumaithurai, M.; Fu, X. FOGG: A Fog Computing Based Gateway to Integrate Sensor Networks to Internet. In Proceedings of the 29th International Teletraffic Congress, Genoa, Italy, 5–7 September 2017; Volume 2, pp. 42–47. [Google Scholar]
- Atlam, H.F.; Attiya, G.; El-Fishawy, N. Integration of Color and Texture Features in CBIR System. Int. J. Comput. Appl. 2017, 164, 23–28. [Google Scholar]
- Nikoloudakis, Y.; Markakis, E.; Mastorakis, G.; Pallis, E.; Skianis, C. An NF V-powered emergency system for smart enhanced living environments. In Proceedings of the 2017 IEEE Conference on Network Function Virtualization and Software Defined Networks (NFV-SDN), Berlin, Germany, 6–8 November 2017; pp. 258–263. [Google Scholar]
- Dastjerdi, A.V.; Buyya, R. Fog Computing: Helping the Internet of Things Realize Its Potential. IEEE Comput. Soc. 2016, 112–116. [Google Scholar] [CrossRef]
- Kim, S.J.J. A user study trends in augmented reality and virtual reality research: A qualitative study with the past three years of the ISMAR and IEEE VR conference papers. In Proceedings of the 2012 International Symposium on Ubiquitous Virtual Reality, ISUVR 2012, Daejeon, Korea, 22–25 August 2012; pp. 1–5. [Google Scholar]
- Zao, J.K.; Gan, T.T.; You, C.K.; Méndez, S.J.R.; Chung, C.E.; Wang, Y.T.; Mullen, T. Augmented brain computer interaction based on fog computing and linked data. In Proceedings of the 2014 International Conference on Intelligent Environments, IE 2014, Shanghai, China, 2–4 July 2014; pp. 374–377. [Google Scholar]
- Luan, T.H.; Gao, L.; Li, Z.; Xiang, Y.; Wei, G.; Sun, L. Fog Computing: Focusing on Mobile Users at the Edge. arXiv, 2015; arXiv:1502.01815. [Google Scholar]
- Choi, N.; Kim, D.; Lee, S.; Yi, Y. Fog Operating System for User-Oriented IoT Services: Challenges and Research Directions. IEEE Commun. Mag. 2017, 55, 2–9. [Google Scholar] [CrossRef]
- Mukherjee, M.; Matam, R.; Shu, L.; Maglaras, L.; Ferrag, M.A.; Choudhury, N. Security and Privacy in Fog Computing: Challenges. IEEE Access 2017, 5, 19293–19304. [Google Scholar] [CrossRef]
- Ni, J.; Zhang, K.; Lin, X.; Shen, X. Securing Fog Computing for Internet of Things Applications: Challenges and Solutions. IEEE Commun. Surv. Tutor. 2017, 20, 601–628. [Google Scholar] [CrossRef]
- Giang, N.K.; Blackstock, M.; Lea, R.; Leung, V.C.M. Developing IoT applications in the Fog: A Distributed Dataflow approach. In Proceedings of the 5th International Conference Internet Things, IoT 2015, Seoul, Korea, 26–28 October 2015; pp. 155–162. [Google Scholar]
- Alenezi, A.; Zulkipli, N.H.N.; Atlam, H.F.; Walters, R.J.; Wills, G.B. The Impact of Cloud Forensic Readiness on Security. In Proceedings of the 7th International Conference on Cloud Computing and Services Science (CLOSER 2017), Porto, Portugal, 24–26 April 2017; pp. 511–517. [Google Scholar]
- Yin, B.; Shen, W.; Cheng, Y.; Cai, L.X.; Li, Q. Distributed resource sharing in fog-assisted big data streaming. In Proceedings of the 2017 IEEE International Conference on Communications, Chengdu, China, 27–30 October 2017; pp. 1–6. [Google Scholar]
- Hung, C.L.; Yan, R.Y.; Wang, H.H. Parallel image dehazing algorithm based on GPU using fuzzy system and hybird evolution algorithm. In Proceedings of the 2016 IEEE/ACIS International Conference on Software Engineering, Artificial Intelligence, Networking and Parallel/Distributed Computing (SNPD), Shanghai, China, 30 May–1 June 2016; pp. 581–583. [Google Scholar]
- Hu, P.; Ning, H.; Qiu, T.; Song, H.; Wang, Y.; Yao, X. Security and Privacy Preservation Scheme of Face Identification and Resolution Framework Using Fog Computing in Internet of Things. IEEE Internet Things J. 2017, 4, 1143–1155. [Google Scholar] [CrossRef]
- Wang, L.; Liu, G.; Sun, L. A secure and privacy-preserving navigation scheme using spatial crowdsourcing in fog-based VANETs. Sensors 2017, 17, 668. [Google Scholar] [CrossRef] [PubMed]
- Al Hamid, H.A.; Rahman, S.M.M.; Hossain, M.S.; Almogren, A.; Alamri, A. A Security Model for Preserving the Privacy of Medical Big Data in a Healthcare Cloud Using a Fog Computing Facility with Pairing-Based Cryptography. IEEE Access 2017, 5, 22313–22328. [Google Scholar] [CrossRef]
| Items | Cloud Computing | Fog Computing |
|---|---|---|
| Latency | High | Low |
| Hardware | Scalable storage and computing power | Limited storage and computing power |
| Location of server nodes | Within the Internet | At the edge of the local network |
| Distance between client and server | Multiple hops | One hop |
| Working environment | Warehouse-size building with air conditioning systems | Outdoor (e.g., Streets, gardens) or indoor (e.g., Restaurants) |
| Security measures | Defined | Hard to define |
| Attack on data | Less probability | High probability |
| Deployment | Centralized | Distributed |
| Location awareness | No | Yes |
| IoT Challenge | How the Fog Can Solve the Challenge |
|---|---|
| Latency constraints | The fog performs all computation operation such as managing and analyzing data and other time-sensitive actions close to end users, which is the ideal solution to meet latency constraints of some of IoT applications. |
| Network bandwidth constraints | Fog computing enables hierarchical data processing along the cloud to IoT devices. This allows data processing to be carried out depending on application demands, available networking and computing resources. This, in turn, reduces the amount of data required to be uploaded to the cloud, which will save network bandwidth. |
| Resource-constrained devices | Fog computing can be used to perform operations that need huge resources on behalf of resource-constrained devices when such operations cannot be uploaded to the cloud. Therefore, this allows reducing devices’ complexity, lifecycle costs and power consumption. |
| Uninterrupted services | Fog computing can run independently to ensure continuous services even when it has irregular network connectivity to the cloud. |
| IoT security challenges | Resource-constrained devices have limited security functions; therefore, fog computing acts as the proxy for these devices to update the software of these devices and security credentials. The fog can also be used to monitor the security status of nearby devices. |
| Author | Year | Summary of Contribution |
|---|---|---|
| F. Bonomi et al. [6] | 2012 | Propose a fog computing platform to support resource-constrained IoT devices |
| Hong et al. [37] | 2013 | Propose mobile fog (MF) that allows IoT applications to aggregate and process data locally and support load balancing |
| F. Bonomi et al. [20] | 2014 | Propose a hierarchical distributed architecture for the fog and provide use cases of smart traffic light system and wind farm to demonstrate the key features of the proposed architecture |
| Stojmenovic and Wen [45] | 2014 | Provide security and privacy issues of the current fog computing paradigm with an example of the man-in-the-middle attack |
| K. Lee et al. [41] | 2015 | Investigate security and privacy issues resulting from integrating fog computing |
| K. Saharan and A. Kumar [32] | 2015 | Provide an overview of fog computing as an extension of cloud computing |
| N. Peter [7] | 2015 | Provide a summary of opportunities for fog computing in real-time applications and how to resolve problems related to congestion and latency |
| M. Aazam and E. Huh [23] | 2015 | Propose a model for management of resources through fog computing. This model provides a dynamic way to manage resources and can adapt to different requirements of cloud service providers |
| S. Yi et al. [33] | 2015 | Provide a survey of fog computing and challenges that might arise while implementing fog computing systems |
| V. Gazis et al. [39] | 2015 | Propose an adaptive operations platform (AOP) to provide end-to-end manageability for fog computing regarding the operational demands of the industrial process |
| Y. Shi et al. [21] | 2015 | Provide essential characteristics of fog computing in the healthcare system |
| Dastjerdi et al. [35] | 2016 | Propose a reference architecture for fog computing which serves IoT requests in the local fog rather than involving the cloud |
| M. Chiang and T. Zhang [10] | 2016 | Provide a summary of the opportunities and challenges of fog computing focusing primarily on the networking context of the IoT |
| O. Skarlat et al. [31] | 2016 | Propose a framework for fog resource provisioning to provide delay-sensitive utilization of available fog-based computational resources |
| X. Hou et al. [42] | 2016 | Propose VFC architecture to facilitate collaboration between end users to perform communication and computation based on resources of each vehicle |
| A. Alrawais et al. [40] | 2017 | Propose a mechanism that employs the fog to improve the distribution of certificate revocation information among IoT devices for security enhancement |
| A. Yousefpour et al. [38] | 2017 | Propose a framework to understand, evaluate and model service delay in IoT–fog–cloud application scenarios |
| C. Puliafito et al. [34] | 2017 | Discuss mobility support in a fog environment and investigate the main challenges of mobility support with presenting three scenarios |
| M. Sookhak et al. [43] | 2017 | Propose a cross-layer architecture of VFC to explain the procedures of the decision-making process and how different types of services are distributed among vehicles |
| S. Khan et al. [44] | 2017 | Provide a review of fog computing applications to identify common security issues |
| Mahmud et al. [46] | 2018 | Provide a taxonomy of fog computing according to challenges and features of fog computing |
© 2018 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Atlam, H.F.; Walters, R.J.; Wills, G.B. Fog Computing and the Internet of Things: A Review. Big Data Cogn. Comput. 2018, 2, 10. https://doi.org/10.3390/bdcc2020010
Atlam HF, Walters RJ, Wills GB. Fog Computing and the Internet of Things: A Review. Big Data and Cognitive Computing. 2018; 2(2):10. https://doi.org/10.3390/bdcc2020010
Chicago/Turabian StyleAtlam, Hany F., Robert J. Walters, and Gary B. Wills. 2018. "Fog Computing and the Internet of Things: A Review" Big Data and Cognitive Computing 2, no. 2: 10. https://doi.org/10.3390/bdcc2020010
APA StyleAtlam, H. F., Walters, R. J., & Wills, G. B. (2018). Fog Computing and the Internet of Things: A Review. Big Data and Cognitive Computing, 2(2), 10. https://doi.org/10.3390/bdcc2020010







