Enhancing Privacy in Wearable IoT through a Provenance Architecture
Abstract
:1. Introduction
- Provenance is proposed to generate data trace routes in the wearable IoT economy order to ensure digital audit trail for transparency. The work adopted the broadcast-subscriber IoT architecture to ensure privacy of users’ data such as vitals especially in wearable IoT; a key concern in the generic broadcast IoT architecture.
- Both the hardware and software level data encoding methodologies are proposed based on device meta-data encryption.
2. Background Works
2.1. IoT Applications
2.2. Privacy and Provenance in IoT
2.3. The Open Issues
- How can the personal data shared in wearable IoT be made more secure when devices are broadcasting?
- How can the data be encoded in a way that even if the shared keys are stolen, data privacy will not be breached?
- Can transparency be offered to ensure the determination of who got what information in the wearable IoT?
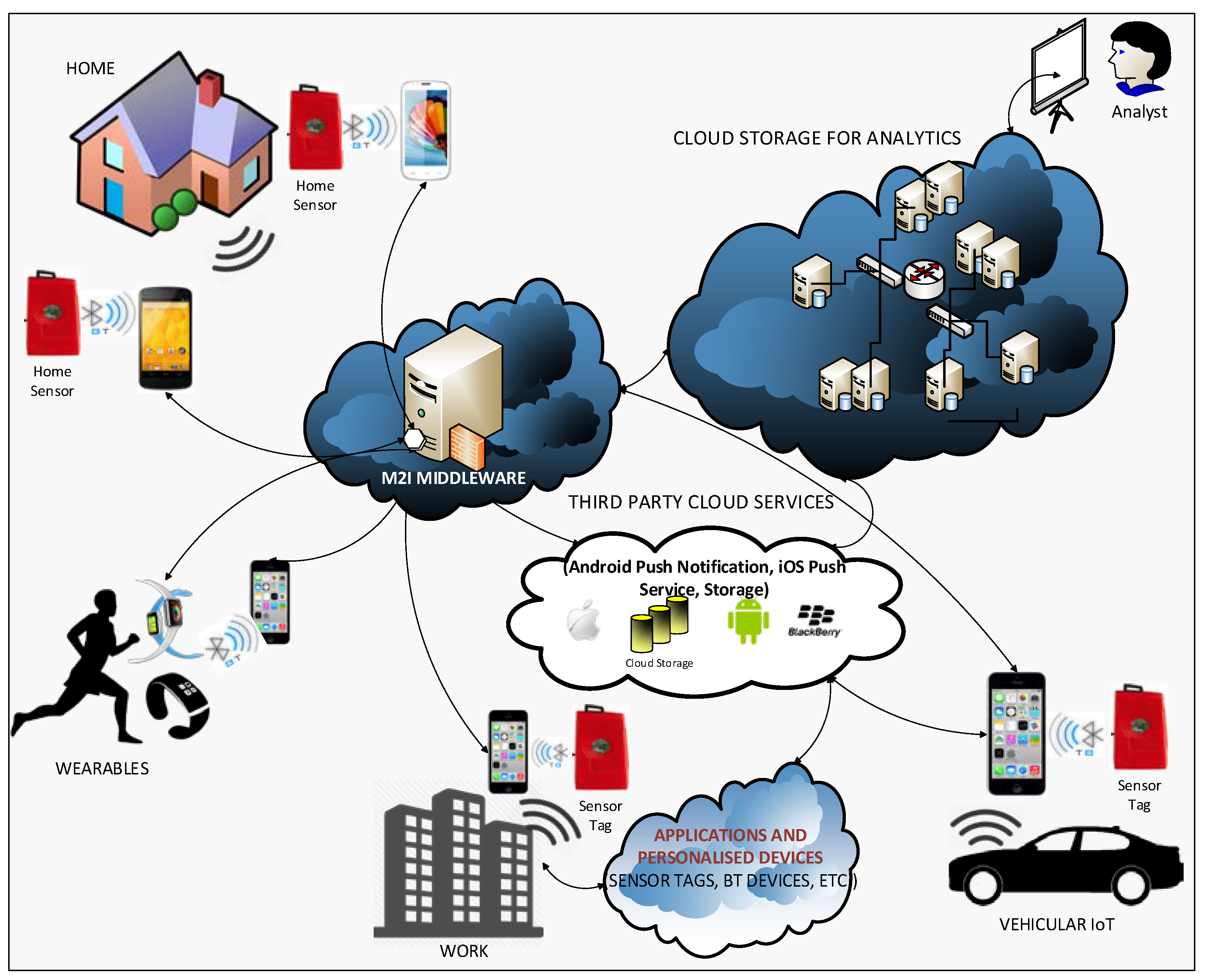
3. The Designed IoT Architecture
3.1. Designing the System
3.2. Provenance and Audit Trail
- Step 1:
- Choose some random numbers , , ,, ,,, and compute
- Step 2:
- Choose the current time stamp and compute the challenge , where
- Step 3:
- Compute
- Step 4:
- Send the timestamp and to the middleware for authentication.
- Step 1:
- Compute ,, , and :
- Step 2:
- Check the following equation
- Step 1:
- The IoT device or the middleware first takes a version of the provenance record and sends the provenance information to an independent trusted authority, which is part of the middleware but a detached component.
- Step 2:
- The trusted authority, say uses its master key to compute and based on the outcome return to the middleware .
- Step 3:
- The middleware then looks up the tracking list with 𝐴. If an entry is found with , the IoT device which created the questionable version is tracked. The correctness is that, if the version is really generated by , we will have
4. Evaluation
4.1. The IoT Device Resource Utilization Cost
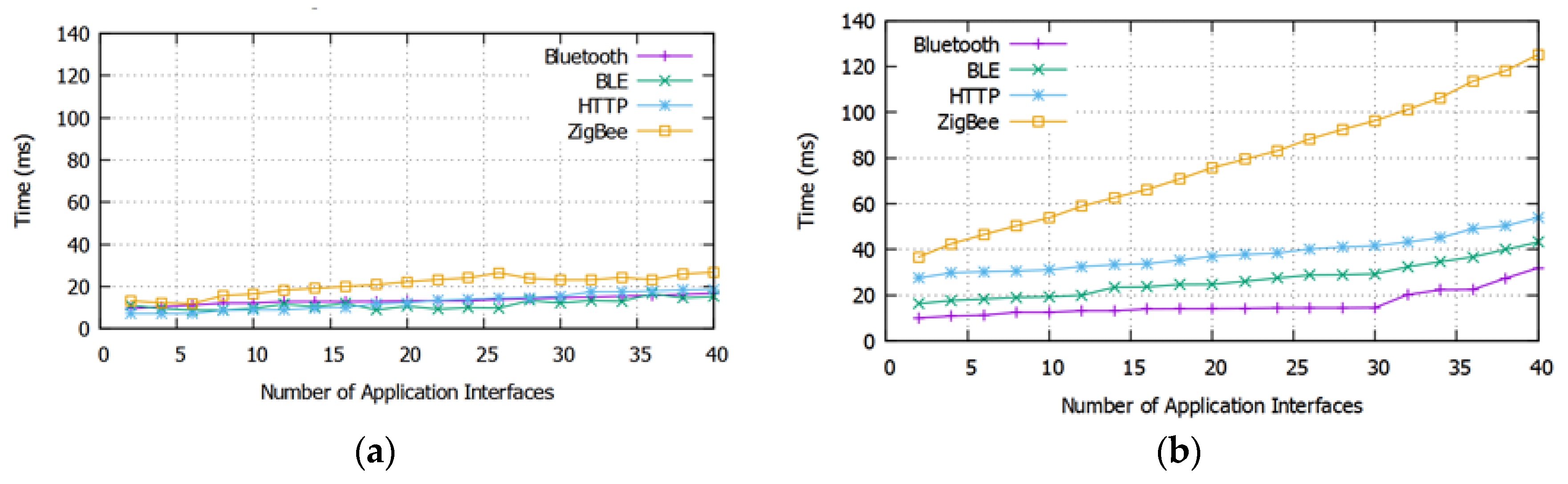
4.2. Sensor Data Propagation
4.3. Fault Injection Analysis
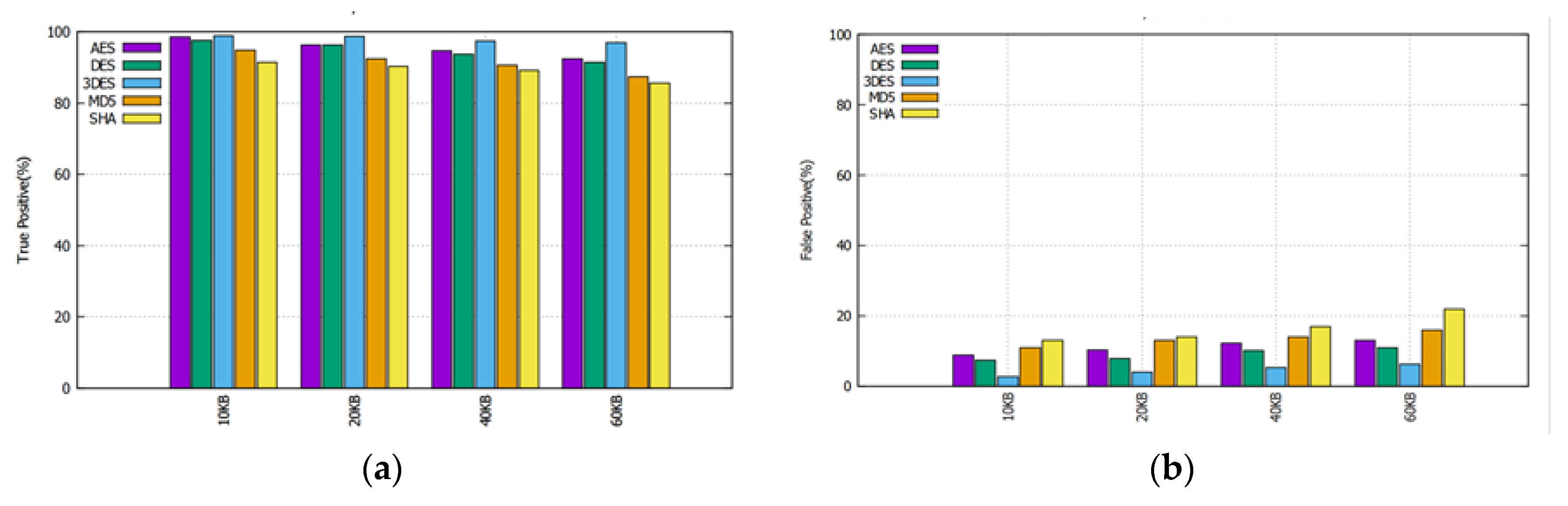
4.4. Visual Analytics from the Provenance Data
5. Conclusions
- Provenance is proposed to generate data trace routes in the wearable IoT economy order to ensure digital audit trail for transparency. The work adopted the broadcast-subscriber IoT architecture to ensure privacy of users’ data such as vitals especially in wearable IoT; a key concern in the generic broadcast IoT architecture.
- Both the hardware and software level data encoding methodologies are proposed based on device meta-data encryption.
Acknowledgments
Author Contributions
Conflicts of Interest
References
- Sicari, S.; Cappiello, C.; De Pellegrini, F.; Miorandi, D.; Coen-Porisini, A. A security-and quality-aware system architecture for Internet of Things. Inf. Syst. Front. 2016, 18, 665–677. [Google Scholar] [CrossRef] [Green Version]
- Wang, P.; Valerdi, R.; Zhou, S.; Li, L. Introduction: Advances in IoT research and applications. Inf. Syst. Front. 2015, 17, 239–241. [Google Scholar] [CrossRef]
- Li, N.; Sun, M.; Bi, Z.; Su, Z.; Wang, C. A new methodology to support group decision-making for IoT-based emergency response systems. Inf. Syst. Front. 2014, 16, 953–977. [Google Scholar] [CrossRef]
- Zhang, Q.; Yang, L.T.; Chen, Z.; Li, P. High-order possibilistic c-means algorithms based on tensor decompositions for big data in IoT. Inf. Fusion 2018, 39, 72–80. [Google Scholar] [CrossRef]
- Lomotey, R.K.; Nilson, J.; Mulder, K.; Wittmeier, K.; Schachter, C.; Deters, R. Mobile Medical Data Synchronization on Cloud-Powered Middleware Platform. IEEE Trans. Serv. Comput. 2016, 9, 757–770. [Google Scholar] [CrossRef]
- Pencheva, E.; Atanasov, I. Engineering of web services for internet of things applications. Inf. Syst. Front. 2016, 18, 277–292. [Google Scholar] [CrossRef]
- Atzori, L.; Iera, A.; Morabito, G. The Internet of Things: A survey. Comput. Netw. 2010, 54, 2787–2805. [Google Scholar] [CrossRef]
- March, S.T.; Scudder, G.D. Predictive maintenance: Strategic use of IT in manufacturing organizations. Inf. Syst. Front. 2017. [Google Scholar] [CrossRef]
- Whitmore, A.; Agarwal, A.; Da Xu, L. The Internet of Things—A survey of topics and trends. Inf. Syst. Front. 2015, 17, 261–274. [Google Scholar] [CrossRef]
- Lomotey, R.K.; Deters, R. Middleware for mobile medical data management with minimal latency. Inf. Syst. Front. 2016, 1–16. [Google Scholar] [CrossRef]
- Namboodiri, M. M2M and IoT—Security and Privacy Thoughts for 2015. Available online: https://www.linkedin.com/pulse/m2m-iot-security-privacy-thoughts-2015-manu-namboodiri (accessed on 1 August 2016).
- Lomotey, R.K.; Sriramoju, S.; Deters, R. Middleware platform for the synchronisation of mobile medical data. Int. J. Bus. Process Integr. Manag. 2017, 8, 136–144. [Google Scholar] [CrossRef]
- Pignotti, E.; Edwards, P. Trusted tiny things: Making the internet of things more transparent to users. In Proceedings of the International Workshop on Adaptive Security, Zurich, Switzerland, 8–12 September 2013. [Google Scholar]
- Ziegeldorf, J.H.; Morchon, O.G.; Wehrle, K. Privacy in the Internet of Things: Threats and challenges. Secur. Commun. Netw. 2014, 7, 2728–2742. [Google Scholar] [CrossRef]
- Bertino, E. Data Security and Privacy in the IoT. EDBT 2016, 2016, 1–3. [Google Scholar]
- Shebaro, B.; Oluwatimi, O.; Midi, D.; Bertino, E. Identidroid: Android can finally wear its anonymous suit. Trans. Data Priv. 2014, 7, 27–50. [Google Scholar]
- Singh, J.; Pasquier, T.; Bacon, J.; Ko, H.; Eyers, D. Twenty security considerations for cloud-supported Internet of Things. IEEE Internet Things J. 2016, 3, 269–284. [Google Scholar] [CrossRef]
- Devi, K.N.; Muthuselvi, R. Secret Sharing of IoT Healthcare Data Using cryptographic algorithm. Int. J. Eng. Res. 2016, 5. [Google Scholar]
- Lomotey, R.K.; Pry, J.; Sriramoju, S. Wearable IoT data stream traceability in a distributed health information system. Pervasive Mob. Comput. 2017, 40, 692–707. [Google Scholar] [CrossRef]
- SensorTag. Available online: http://www.ti.com/tool/cc2650stk#0 (accessed on 20 April 2018).
- Xamarin. Available online: https://www.xamarin.com/ (accessed on 20 April 2018).
- CouchDB. Available online: http://www.couchdb.com (accessed on 20 April 2018).
- Kura Open Source for IoT. Available online: http://www.eclipse.org/kura/ (accessed on 20 April 2018).
- Alharbi, K.; Lin, X. PDP: A Privacy-Preserving Data Provenance Scheme. In Proceedings of the 2012 32nd International Conference on Distributed Computing Systems Workshops, Macau, China, 18–21 June 2012; pp. 500–505. [Google Scholar] [CrossRef]




| Property | Definition |
|---|---|
| Resource Utilization | The percentage of resources taken by the encryption schemes. |
| Network Types | Different communication protocols such as ZigBee, HTTP, Bluetooth, and BLE. |
| Encryption/Decryption Schemes | AES (aes_128_cfb), DES (des_cfb), 3DES. |
| Hashing Schemes | MD5, and SHA (SHA-256). |
| Soft-Real Time | Acceptable window within which data should be synchronized. |
| Fault Injection | Attempts to hack the proposed broadcast-subscriber system for the purpose of testing. |
| Resource | Utilization | |||
|---|---|---|---|---|
| Min (%) | Avg (%) | Max (%) | ||
| CPU | AES | 6.75 | 11.15 | 16.75 |
| DES | 10.44 | 16.51 | 20.44 | |
| 3DES | 11.89 | 17.10 | 23.96 | |
| MD5 | 16.02 | 18.84 | 23.00 | |
| SHA | 15.65 | 18.68 | 22.66 | |
| RAM | AES | 4.25 | 5.66 | 8.96 |
| DES | 5.23 | 7.82 | 10.95 | |
| 3DES | 5.87 | 9.00 | 12.44 | |
| MD5 | 7.33 | 10.50 | 14.56 | |
| SHA | 8.22 | 12.67 | 19.22 | |
© 2018 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Lomotey, R.K.; Sofranko, K.; Orji, R. Enhancing Privacy in Wearable IoT through a Provenance Architecture. Multimodal Technol. Interact. 2018, 2, 18. https://doi.org/10.3390/mti2020018
Lomotey RK, Sofranko K, Orji R. Enhancing Privacy in Wearable IoT through a Provenance Architecture. Multimodal Technologies and Interaction. 2018; 2(2):18. https://doi.org/10.3390/mti2020018
Chicago/Turabian StyleLomotey, Richard K., Kenneth Sofranko, and Rita Orji. 2018. "Enhancing Privacy in Wearable IoT through a Provenance Architecture" Multimodal Technologies and Interaction 2, no. 2: 18. https://doi.org/10.3390/mti2020018
APA StyleLomotey, R. K., Sofranko, K., & Orji, R. (2018). Enhancing Privacy in Wearable IoT through a Provenance Architecture. Multimodal Technologies and Interaction, 2(2), 18. https://doi.org/10.3390/mti2020018





