Natural Language Processing for Hardware Security: Case of Hardware Trojan Detection in FPGAs
Abstract
1. Introduction
- We analyze bitstream architecture and formats, to determine the most effective data preprocessing techniques for RNN analysis.
- We utilize dynamic partial reconfiguration with various optimization subroutines, to create a comprehensive data set containing different circuit profiles of benchmark circuits.
- We develop a special preprocessing algorithm that transforms configuration bitstreams into a format suitable for processing by an RNN.
- We demonstrate the effectiveness of using RNN-based supervised learning methods on preprocessed configuration bitstreams, to identify malicious patterns indicative of HTs.
2. Preliminaries
2.1. Hardware Trojan
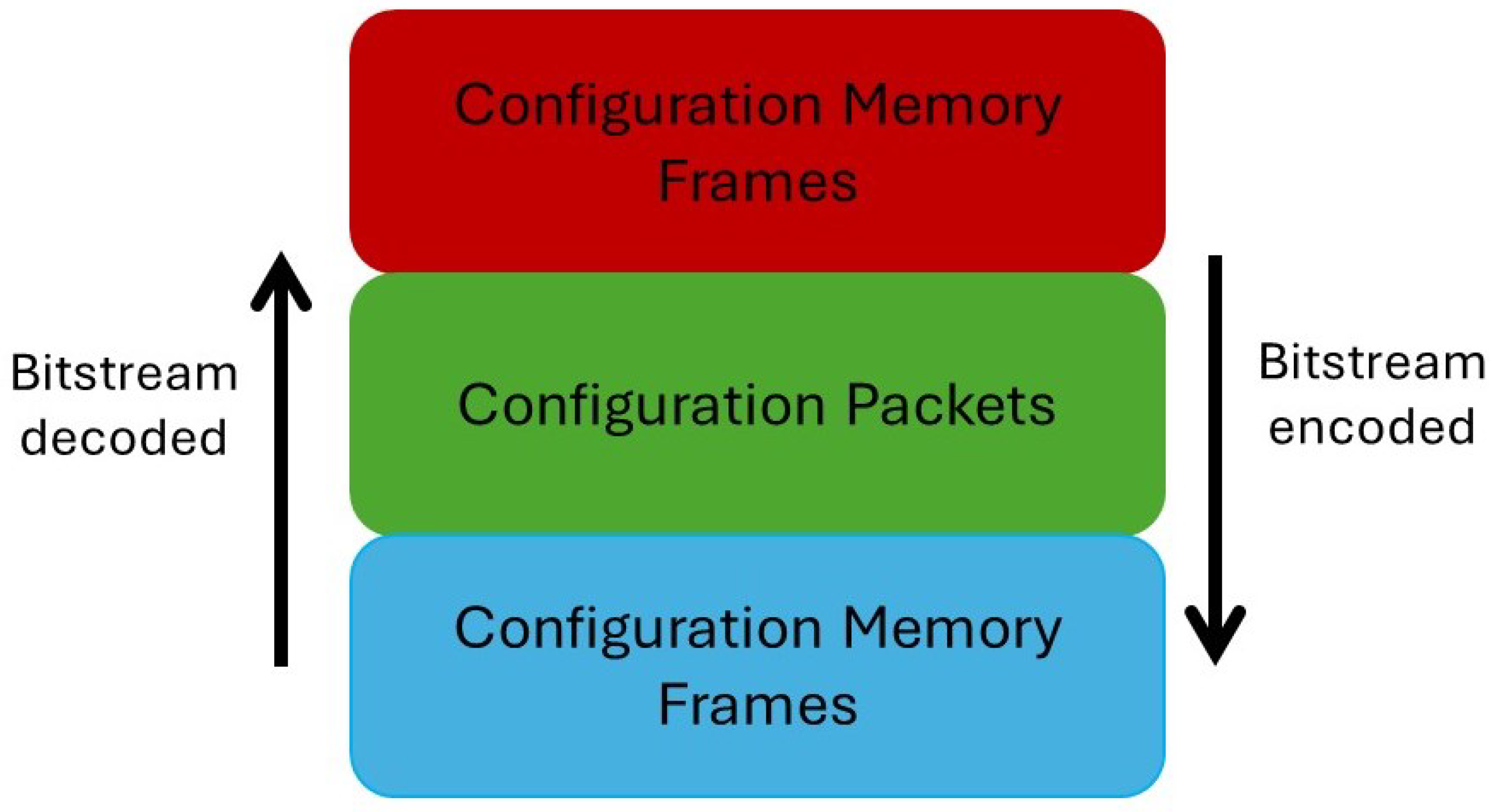
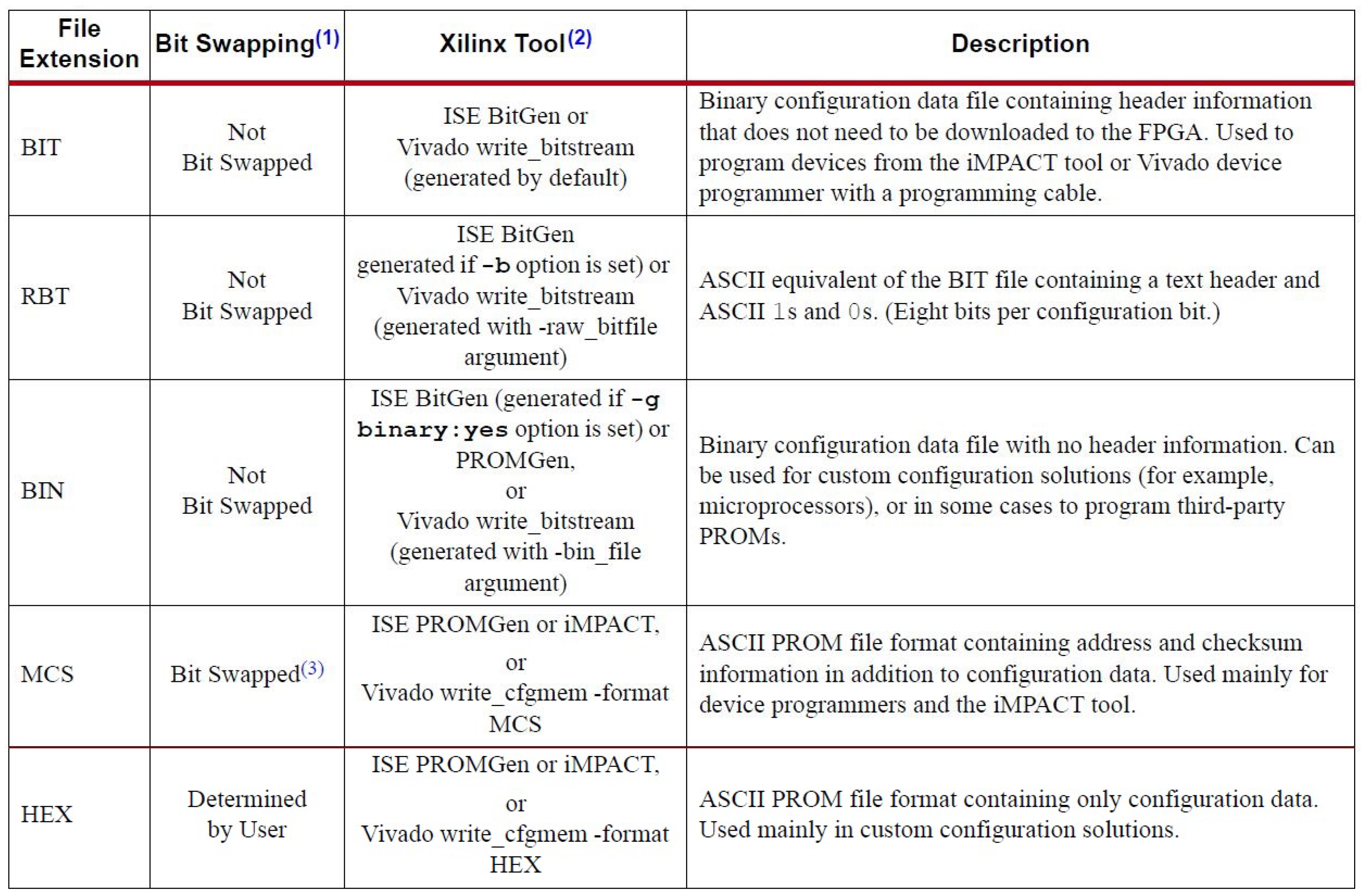
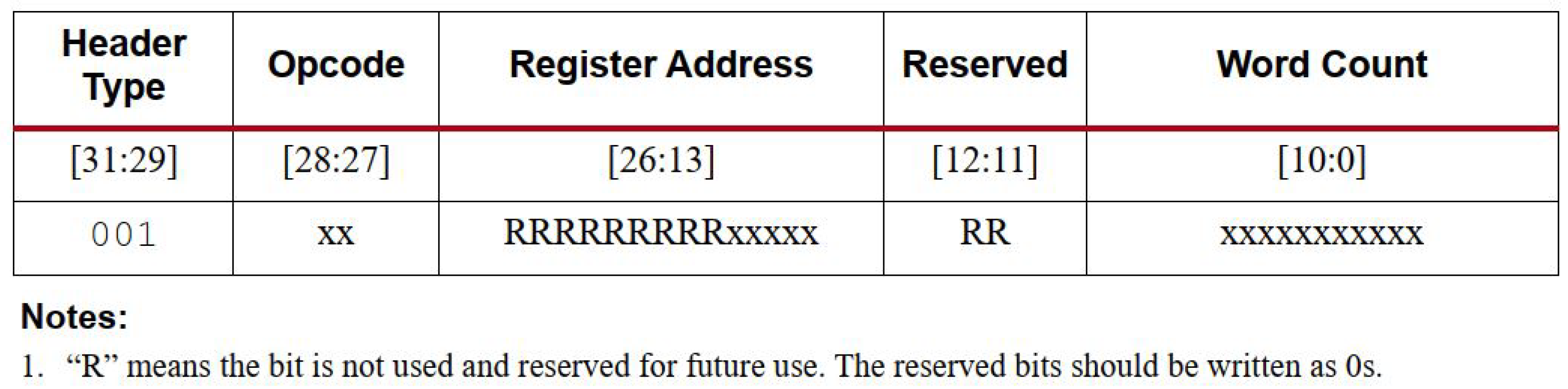
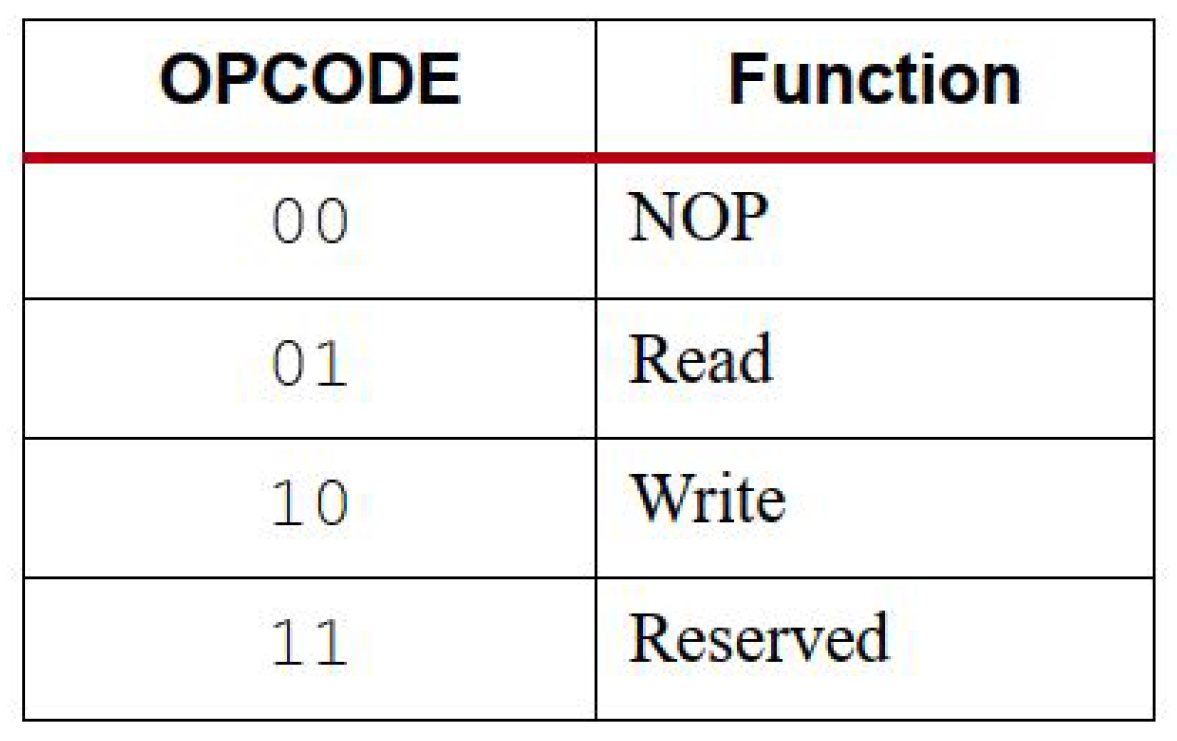
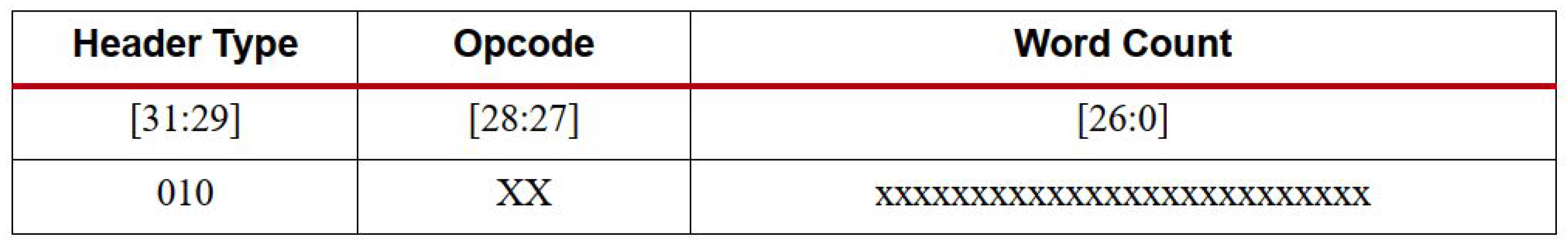
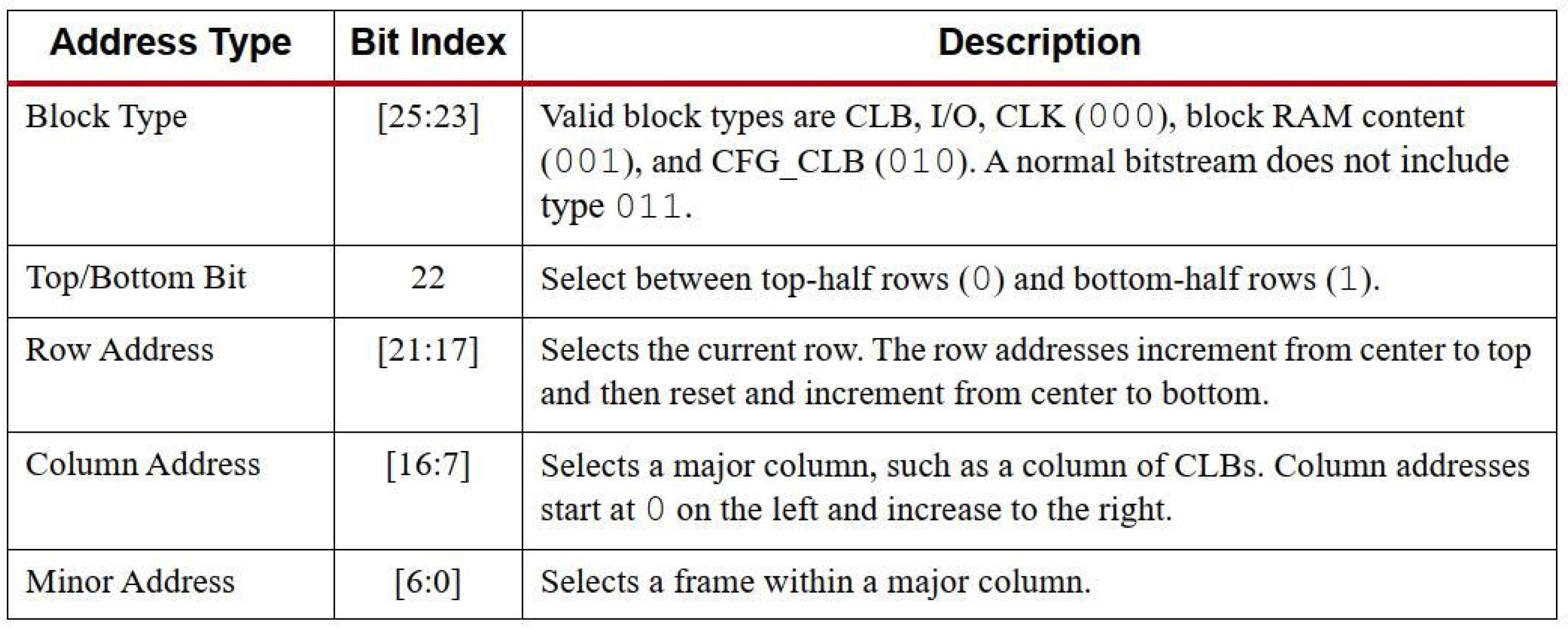
2.2. Bitstream Architecture
- bus width auto-detection;
- sync word;
- FPGA configuration.
2.3. Recurrent Neural Networks (RNN)
3. Related Work
3.1. Machine Learning Techniques in Hardware Trojan Detection
3.2. HT Detection in FPGA Bitstreams Using Machine Learning
4. Methodology
4.1. Data Set Generation
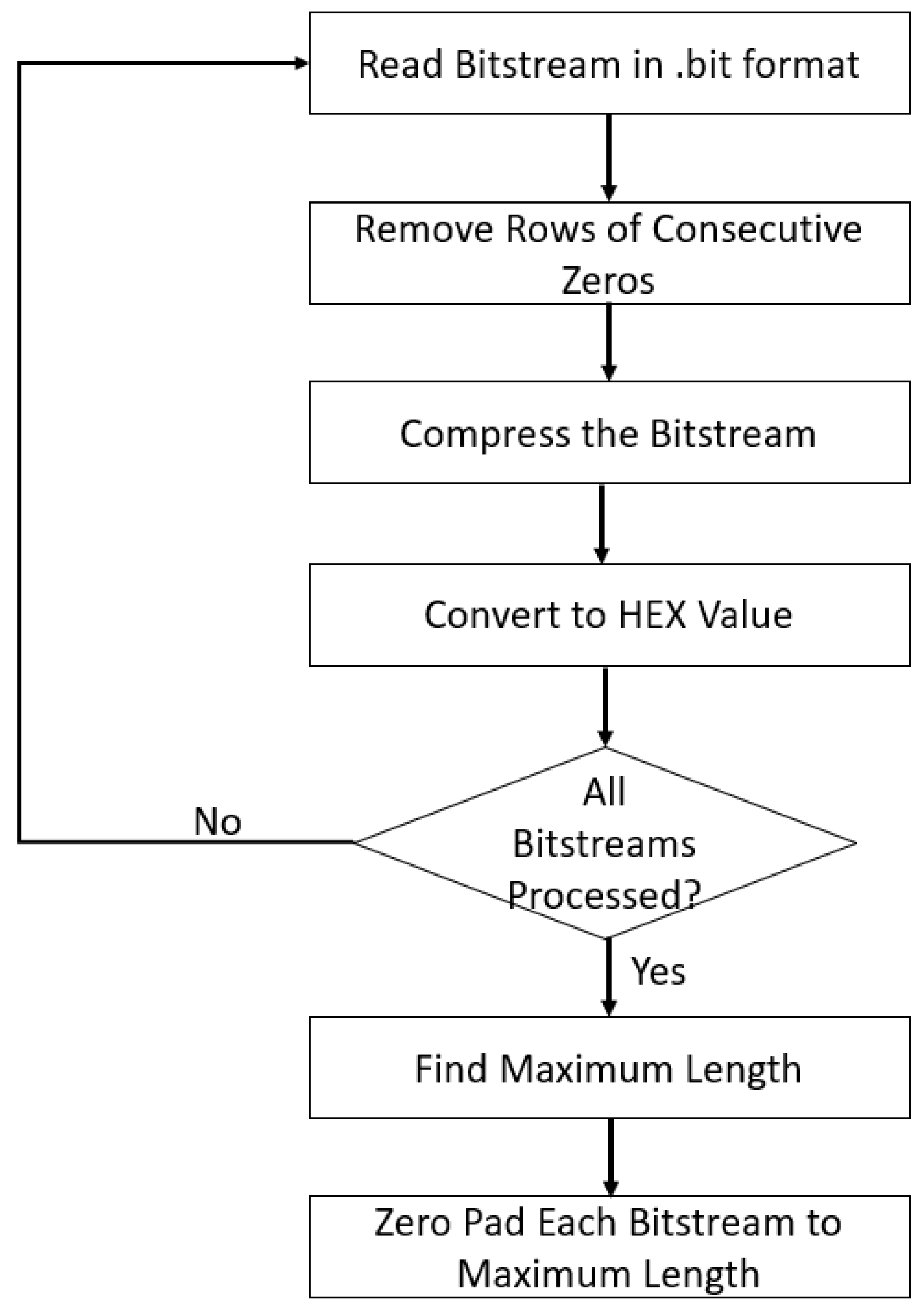
4.2. Preprocessing FPGA Bitstream for RNN and LSTM Models
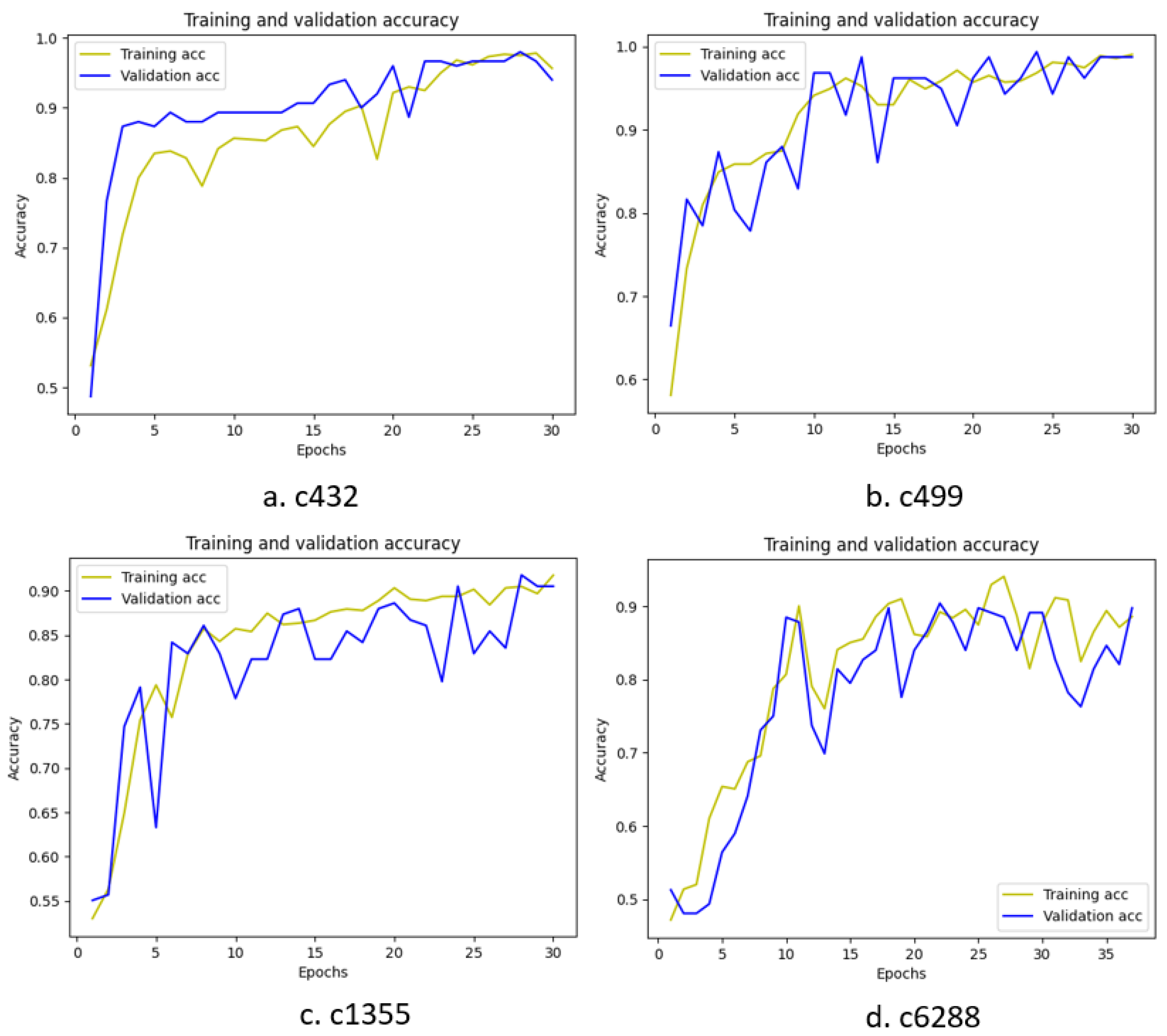
5. Results
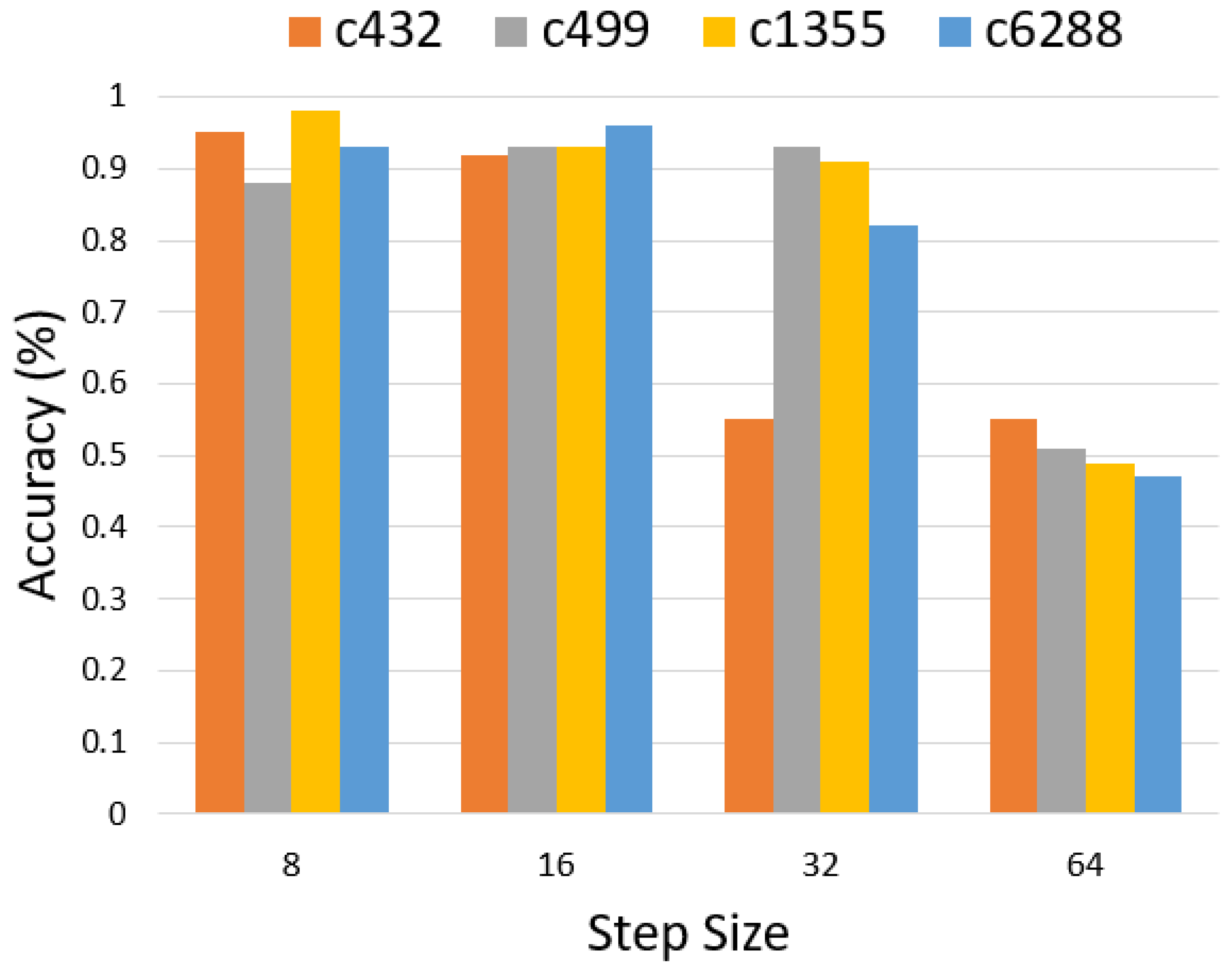
5.1. Combinational Trojan Detection
- Two bidirectional SimpleRNN layers with 64 and 32 units, respectively, where the first layer processed input sequences bidirectionally, while the second layer processed output sequences bidirectionally.
- Dropout layers with a dropout rate of 0.5 after each SimpleRNN layer, to prevent overfitting.
- A dense output layer with a sigmoid activation function that facilitated binary classification.
- A bidirectional LSTM layer with 64 units/nodes along with a dropout layer with a rate = 0.5;
- A bidirectional LSTM layer with 32 units/nodes along with a dropout layer with a rate = 0.5;
- A dense layer with 1 unit/node and a ’sigmoid’ activation function.
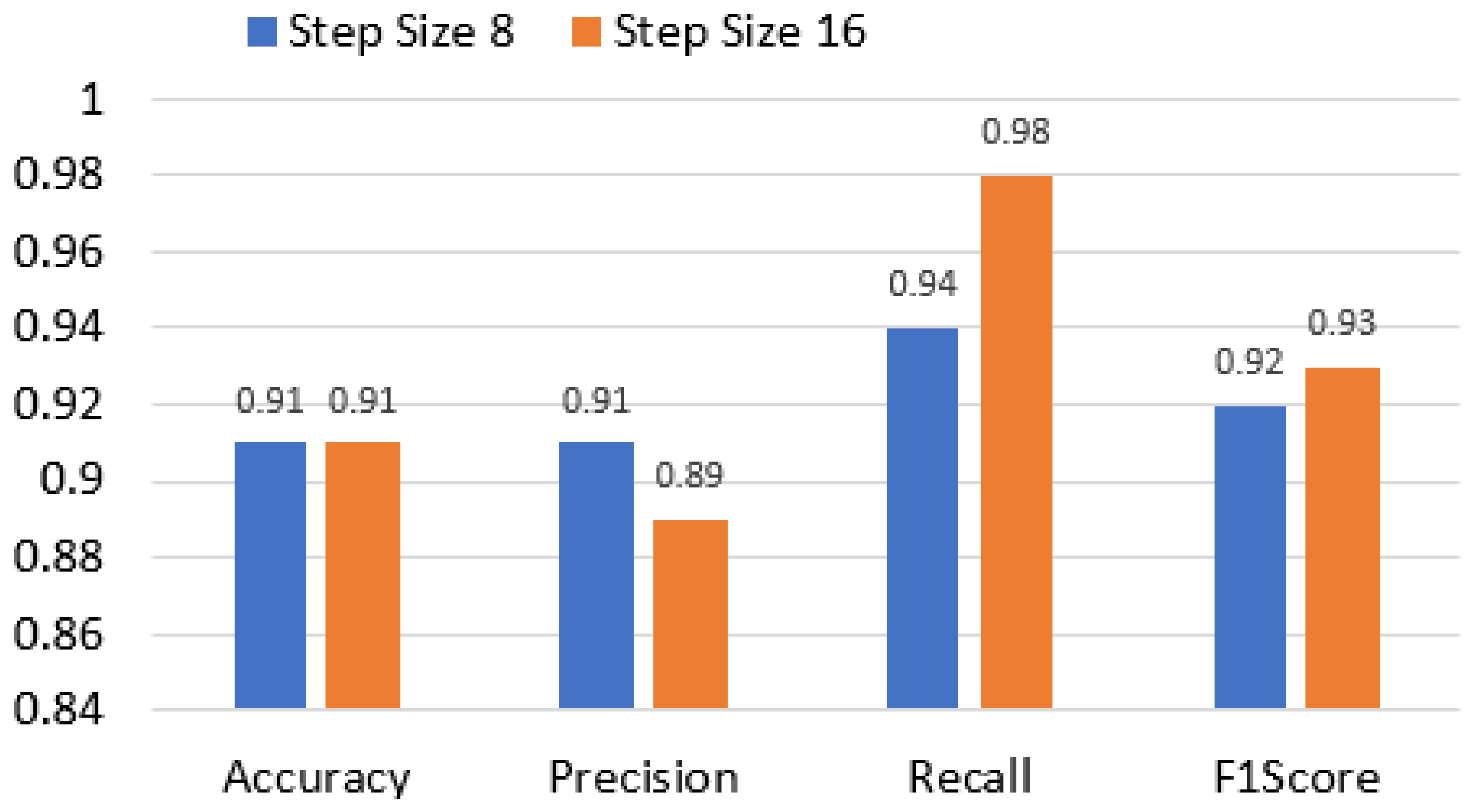
5.2. Case Study: Multi-Tenant FPGA Ring Oscillator-Based Trojan
5.3. Comparison with Relevant Work
6. Conclusions
Author Contributions
Funding
Data Availability Statement
Conflicts of Interest
References
- Rajput, S.; Dofe, J.; Danesh, W. Automating Hardware Trojan Detection Using Unsupervised Learning: A Case Study of FPGA. In Proceedings of the 2023 24th International Symposium on Quality Electronic Design (ISQED), San Francisco, CA, USA, 5–7 April 2023; pp. 1–6. [Google Scholar] [CrossRef]
- Elnawawy, M.; Farhan, A.; Nabulsi, A.A.; Al-Ali, A.; Sagahyroon, A. Role of FPGA in Internet of Things Applications. In Proceedings of the 2019 IEEE International Symposium on Signal Processing and Information Technology (ISSPIT), Ajman, United Arab Emirates, 10–12 December 2019; pp. 1–6. [Google Scholar] [CrossRef]
- Fahmy, S.A.; Vipin, K.; Shreejith, S. Virtualized FPGA Accelerators for Efficient Cloud Computing. In Proceedings of the 2015 IEEE 7th International Conference on Cloud Computing Technology and Science (CloudCom), Vancouver, BC, Canada, 30 November–3 December 2015; pp. 430–435. [Google Scholar] [CrossRef]
- Zeitouni, S.; Vliegen, J.; Frassetto, T.; Koch, D.; Sadeghi, A.R.; Mentens, N. Trusted Configuration in Cloud FPGAs. In Proceedings of the 2021 IEEE 29th Annual International Symposium on Field-Programmable Custom Computing Machines (FCCM), Orlando, FL, USA, 9–12 May 2021; pp. 233–241. [Google Scholar] [CrossRef]
- Monmasson, E.; Hilairet, M.; Spagnuolo, G.; Cirstea, M.N. System-on-Chip FPGA Devices for Complex Electrical Energy Systems Control. IEEE Ind. Electron. Mag. 2022, 16, 53–64. [Google Scholar] [CrossRef]
- Abdelfattah, M.S.; Bitar, A.; Betz, V. Design and Applications for Embedded Networks-on-Chip on FPGAs. IEEE Trans. Comput. 2017, 66, 1008–1021. [Google Scholar] [CrossRef]
- Mattioli, M. FPGAs in Client Compute Hardware: Despite Certain Challenges, FPGAs Provide Security and Performance Benefits over ASICs. Queue 2022, 19, 66–88. [Google Scholar] [CrossRef]
- Koch, D.; Ziener, D.; Hannig, F. FPGA Versus Software Programming: Why, When, and How? In FPGAs for Software Programmers; Koch, D., Hannig, F., Ziener, D., Eds.; Springer International Publishing: Cham, Switzerland, 2016; pp. 1–21. [Google Scholar] [CrossRef]
- Deep Dive into Alibaba Cloud F3 FPGA as a Service Instances. 2018. Available online: https://www.alibabacloud.com/blog/deep-dive-into-alibaba-cloud-f3-fpga-as-a-service-instances_594057 (accessed on 22 March 2024).
- Amazon EC2 F1 Instances. 2024. Available online: https://aws.amazon.com/ec2/instance-types/f1 (accessed on 20 March 2024).
- Magyari, A.; Chen, Y. Review of state-of-the-art FPGA applications in IoT Networks. Sensors 2022, 22, 7496. [Google Scholar] [CrossRef]
- Krautter, J.; Gnad, D.R.E.; Tahoori, M.B. Mitigating Electrical-Level Attacks towards Secure Multi-Tenant FPGAs in the Cloud. ACM Trans. Reconfig. Technol. Syst. 2019, 12, 1–26. [Google Scholar] [CrossRef]
- Sunkavilli, S.; Zhang, Z.; Yu, Q. New Security Threats on FPGAs: From FPGA Design Tools Perspective. In Proceedings of the 2021 IEEE Computer Society Annual Symposium on VLSI (ISVLSI), Tampa, FL, USA, 7–9 July 2021; pp. 278–283. [Google Scholar] [CrossRef]
- Zhang, T.; Wang, J.; Guo, S.; Chen, Z. A Comprehensive FPGA Reverse Engineering Tool-Chain: From Bitstream to RTL Code. IEEE Access 2019, 7, 38379–38389. [Google Scholar] [CrossRef]
- Trimberger, S.; McNeil, S. Security of FPGAs in data centers. In Proceedings of the 2017 IEEE 2nd International Verification and Security Workshop (IVSW), Rhodes Island, Greece, 3–5 July 2017; pp. 117–122. [Google Scholar] [CrossRef]
- Cho, M.; Jang, J.; Seo, Y.; Jeong, S.; Chung, S.; Kwon, T. Towards Bidirectional LUT-level Detection of Hardware Trojans. Comput. Secur. 2021, 104, 102223. [Google Scholar] [CrossRef]
- Krieg, C.; Wolf, C.; Jantsch, A. Malicious LUT: A stealthy FPGA Trojan injected and triggered by the design flow. In Proceedings of the 2016 IEEE/ACM International Conference on Computer-Aided Design (ICCAD), Austin, TX, USA, 7–10 November 2016; pp. 1–8. [Google Scholar] [CrossRef]
- Elnaggar, R.; Chaudhuri, J.; Karri, R.; Chakrabarty, K. Learning Malicious Circuits in FPGA Bitstreams. IEEE Trans. Comput.-Aided Des. Integr. Circuits Syst. 2022, 42, 726–739. [Google Scholar] [CrossRef]
- Bhunia, S.; Abramovici, M.; Agrawal, D.; Bradley, P.; Hsiao, M.S.; Plusquellic, J.; Tehranipoor, M. Protection Against Hardware Trojan Attacks: Towards a Comprehensive Solution. IEEE Des. Test 2013, 30, 6–17. [Google Scholar] [CrossRef]
- Mal-Sarkar, S.; Krishna, A.; Ghosh, A.; Bhunia, S. Hardware trojan attacks in FPGA devices: Threat analysis and effective counter measures. In Proceedings of the 24th Edition of the Great Lakes Symposium on VLSI, Houston, TX, USA, 21–23 May 2014. [Google Scholar] [CrossRef]
- Altherr, R. Unpacking Xilinx 7-Series Bitstreams: Part 1. 2018. Available online: https://www.kc8apf.net/2018/05/unpacking-xilinx-7-series-bitstreams-part-1 (accessed on 30 December 2023).
- AMD Adaptive Computing Documentation Portal—docs.xilinx.com. Available online: https://docs.xilinx.com/r/en-US/ug470_7Series_Config (accessed on 30 October 2023).
- Afshine Amidi, S.A. Recurrent Neural Networks Cheatsheet. Available online: https://stanford.edu/~shervine/teaching/cs-230/cheatsheet-recurrent-neural-networks (accessed on 10 November 2023).
- Torrance, R.; James, D. The state-of-the-art in semiconductor reverse engineering. In Proceedings of the 2011 48th ACM/EDAC/IEEE Design Automation Conference (DAC), San Diego, CA, USA, 5–9 June 2011; pp. 333–338. [Google Scholar]
- Shiyanovskii, Y.; Wolff, F.; Rajendran, A.; Papachristou, C.; Weyer, D.; Clay, W. Process reliability based trojans through NBTI and HCI effects. In Proceedings of the 2010 NASA/ESA Conference on Adaptive Hardware and Systems, Anaheim, CA, USA, 15–18 June 2010; pp. 215–222. [Google Scholar] [CrossRef]
- Bao, C.; Forte, D.; Srivastava, A. On Reverse Engineering-Based Hardware Trojan Detection. IEEE Trans. Comput.-Aided Des. Integr. Circuits Syst. 2016, 35, 49–57. [Google Scholar] [CrossRef]
- Hoque, T.; Cruz, J.; Chakraborty, P.; Bhunia, S. Hardware IP Trust Validation: Learn (the Untrustworthy), and Verify. In Proceedings of the 2018 IEEE International Test Conference (ITC), Harbin, China, 15–17 August 2018; pp. 1–10. [Google Scholar] [CrossRef]
- Nguyen, L.N.; Cheng, C.L.; Prvulovic, M.; Zajić, A. Creating a Backscattering Side Channel to Enable Detection of Dormant Hardware Trojans. IEEE Trans. Very Large Scale Integr. (VLSI) Syst. 2019, 27, 1561–1574. [Google Scholar] [CrossRef]
- Bao, C.; Forte, D.; Srivastava, A. On application of one-class SVM to reverse engineering-based hardware Trojan detection. In Proceedings of the Fifteenth International Symposium on Quality Electronic Design, Santa Clara, CA, USA, 3–5 March 2014; pp. 47–54. [Google Scholar] [CrossRef]
- Bao, C.; Xie, Y.; Liu, Y.; Srivastava, A. Reverse Engineering-Based Hardware Trojan Detection. In The Hardware Trojan War: Attacks, Myths, and Defenses; Bhunia, S., Tehranipoor, M.M., Eds.; Springer International Publishing: Cham, Switzerland, 2018; pp. 269–288. [Google Scholar] [CrossRef]
- Zhou, E.R.; Li, S.Q.; Chen, J.H.; Ni, L.; Zhao, Z.X.; Li, J. A Novel Detection Method for Hardware Trojan in Third Party IP Cores. In Proceedings of the 2016 International Conference on Information System and Artificial Intelligence (ISAI), Hong Kong, China, 24–26 June 2016; pp. 528–532. [Google Scholar] [CrossRef]
- Lodhi, F.K.; Hasan, S.R.; Hasan, O.; Awwadl, F. Power profiling of microcontroller’s instruction set for runtime hardware Trojans detection without golden circuit models. In Proceedings of the Design, Automation & Test in Europe Conference & Exhibition (DATE), Lausanne, Switzerland, 27–31 March 2017; pp. 294–297. [Google Scholar] [CrossRef]
- Huang, Z.; Wang, Q.; Chen, Y.; Jiang, X. A Survey on Machine Learning Against Hardware Trojan Attacks: Recent Advances and Challenges. IEEE Access 2020, 8, 10796–10826. [Google Scholar] [CrossRef]
- Vakil, A.; Behnia, F.; Mirzaeian, A.; Homayoun, H.; Karimi, N.; Sasan, A. LASCA: Learning Assisted Side Channel Delay Analysis for Hardware Trojan Detection. In Proceedings of the 2020 21st International Symposium on Quality Electronic Design (ISQED), Santa Clara, CA, USA, 25–26 March 2020; pp. 40–45. [Google Scholar] [CrossRef]
- Sumarsono, A.; Masters, Z. Application of LSTM Auto Encoder in Hardware Trojan Detection. In Proceedings of the 2023 IEEE 13th Annual Computing and Communication Workshop and Conference (CCWC), Las Vegas, NV, USA, 8–11 March 2023; pp. 566–571. [Google Scholar] [CrossRef]
- Kataria, J.; Housley, R.; Pantoga, J.; Cui, A. Defeating Cisco Trust Anchor: A Case-Study of Recent Advancements in Direct FPGA Bitstream Manipulation. In Proceedings of the 13th USENIX Conference on Offensive Technologies, Santa Clara, CA, USA, 12–13 August 2019; WOOT’19. p. 5. [Google Scholar]
- Chakraborty, R.S. ProTro: A Probabilistic Counter Based Hardware Trojan Attack on FPGA Based MACSec Enabled Ethernet Switch. In Proceedings of the Security, Privacy, and Applied Cryptography Engineering: 9th International Conference SPACE 2019, Gandhinagar, India, 3–7 December 2019; Springer: Berlin/Heidelberg, Germany, 2019; Volume 11947, p. 159. [Google Scholar]
- Krautter, J.; Gnad, D.R.; Tahoori, M.B. FPGAhammer: Remote voltage fault attacks on shared FPGAs, suitable for DFA on AES. IACR Trans. Cryptogr. Hardw. Embed. Syst. 2018, 2018, 44–68. [Google Scholar] [CrossRef]
- Johnson, A.P.; Patranabis, S.; Chakraborty, R.S.; Mukhopadhyay, D. Remote dynamic partial reconfiguration: A threat to Internet-of-Things and embedded security applications. Microprocess. Microsyst. 2017, 52, 131–144. [Google Scholar] [CrossRef][Green Version]
- Chakraborty, R.S.; Saha, I.; Palchaudhuri, A.; Naik, G.K. Hardware Trojan insertion by direct modification of FPGA configuration bitstream. IEEE Des. Test 2013, 30, 45–54. [Google Scholar] [CrossRef]
- Swierczynski, P.; Fyrbiak, M.; Koppe, P.; Paar, C. FPGA Trojans through detecting and weakening of cryptographic primitives. IEEE Trans. Comput.-Aided Des. Integr. Circuits Syst. 2015, 34, 1236–1249. [Google Scholar] [CrossRef]
- Swierczynski, P.; Fyrbiak, M.; Koppe, P.; Moradi, A.; Paar, C. Interdiction in practice—Hardware Trojan against a high-security USB flash drive. J. Cryptogr. Eng. 2017, 7, 199–211. [Google Scholar] [CrossRef]
- Heiner, J.; Sellers, B.; Wirthlin, M.; Kalb, J. FPGA partial reconfiguration via configuration scrubbing. In Proceedings of the 2009 International Conference on Field Programmable Logic and Applications, Prague, Czech Republic, 31 August–2 September 2009; pp. 99–104. [Google Scholar] [CrossRef]
- Chaudhuri, J.; Chakrabarty, K. Diagnosis of Malicious Bitstreams in Cloud Computing FPGAs. IEEE Trans. Comput.-Aided Des. Integr. Circuits Syst. 2023, 42, 3651–3664. [Google Scholar] [CrossRef]
- Zhao, M.; Suh, G.E. FPGA-Based Remote Power Side-Channel Attacks. In Proceedings of the 2018 IEEE Symposium on Security and Privacy (SP), San Francisco, CA, USA, 21–23 May 2018; pp. 229–244. [Google Scholar] [CrossRef]
- Gnad, D.R.E.; Oboril, F.; Tahoori, M.B. Voltage drop-based fault attacks on FPGAs using valid bitstreams. In Proceedings of the 2017 27th International Conference on Field Programmable Logic and Applications (FPL), Ghent, Belgium, 4–8 September 2017; pp. 1–7. [Google Scholar] [CrossRef]
- Sugawara, T.; Sakiyama, K.; Nashimoto, S.; Suzuki, D.; Nagatsuka, T. Oscillator without a Combinatorial Loop and its Threat to FPGA in Data Center. Electron. Lett. 2019, 55, 640–642. [Google Scholar] [CrossRef]
- Yu, S.; Gu, C.; Liu, W.; O’Neill, M. Deep Learning-Based Hardware Trojan Detection With Block-Based Netlist Information Extraction. IEEE Trans. Emerg. Top. Comput. 2022, 10, 1837–1853. [Google Scholar] [CrossRef]
- Kumar, R.; Jovanovic, P.; Burleson, W.; Polian, I. Parametric Trojans for Fault-Injection Attacks on Cryptographic Hardware. In Proceedings of the 2014 Workshop on Fault Diagnosis and Tolerance in Cryptography, Busan, Republic of Korea, 23 September 2014; pp. 18–28. [Google Scholar] [CrossRef]









| Steps | Description |
|---|---|
| 1. Input Verilog and XDC file. | Provide the Verilog hardware description language (HDL) file describing the FPGA design and the XDC file containing timing constraints. |
| 2. Synthesize design. | Convert the Verilog code into a netlist, a low-level representation of the circuit. |
| 3. Enable dynamic function exchange. | Configure the FPGA to allow for partial reconfiguration. |
| 4. Perform partial reconfiguration in selected floorplan. | Define the area of the FPGA where the reconfiguration will occur and implement the desired changes. |
| 5. Generate full bitstream in .bit format. | Create a complete configuration file containing instructions for the entire FPGA, including both static and reconfigured areas. |
| Benchmarks | Accuracy | Precision | Recall | F1Score | ||||
|---|---|---|---|---|---|---|---|---|
| RNN | LSTM | RNN | LSTM | RNN | LSTM | RNN | LSTM | |
| c432 | 0.52 | 0.95 | 0.48 | 0.97 | 0.66 | 0.92 | 0.56 | 0.95 |
| c499 | 0.49 | 0.88 | 1.00 | 0.81 | 0.74 | 0.98 | 0.85 | 0.88 |
| c1355 | 0.64 | 0.98 | 0.71 | 0.96 | 0.49 | 1.0 | 0.58 | 0.98 |
| c6288 | 0.44 | 0.93 | 0.00 | 0.96 | 0.00 | 0.92 | 0.00 | 0.94 |
| Benchmark | Accuracy | Precision | Recall | F1Score | ||||
|---|---|---|---|---|---|---|---|---|
| RNN | LSTM | RNN | LSTM | RNN | LSTM | RNN | LSTM | |
| c432 | 0.46 | 0.92 | 0.45 | 0.97 | 0.84 | 0.84 | 0.59 | 0.90 |
| c499 | 0.49 | 0.93 | 0.49 | 0.97 | 1.0 | 0.88 | 0.66 | 0.93 |
| c1355 | 0.60 | 0.93 | 0.61 | 0.93 | 0.60 | 0.93 | 0.61 | 0.93 |
| c6288 | 0.41 | 0.96 | 0.39 | 0.94 | 0.20 | 0.91 | 0.26 | 0.92 |
| Benchmark | Accuracy | Precision | Recall | F1Score | ||||
|---|---|---|---|---|---|---|---|---|
| RNN | LSTM | RNN | LSTM | RNN | LSTM | RNN | LSTM | |
| c432 | 0.55 | 0.55 | 0.00 | 0.00 | 0.00 | 0.00 | 0.00 | 0.00 |
| c499 | 0.56 | 0.93 | 0.54 | 0.97 | 0.60 | 0.88 | 0.57 | 0.93 |
| c1355 | 0.49 | 0.91 | 0.00 | 0.93 | 0.00 | 0.89 | 0.00 | 0.91 |
| c6288 | 0.44 | 0.82 | 0.00 | 0.94 | 0.00 | 0.80 | 0.00 | 0.70 |
| Benchmark | Accuracy | Precision | Recall | F1Score | ||||
|---|---|---|---|---|---|---|---|---|
| RNN | LSTM | RNN | LSTM | RNN | LSTM | RNN | LSTM | |
| c432 | 0.55 | 0.55 | 0.00 | 0.00 | 0.00 | 0.00 | 0.00 | 0.00 |
| c499 | 0.51 | 0.51 | 0.00 | 0.00 | 0.00 | 0.00 | 0.00 | 0.00 |
| c1355 | 0.49 | 0.49 | 0.00 | 0.00 | 0.00 | 0.00 | 0.00 | 0.00 |
| c6288 | 0.47 | 0.47 | 0.00 | 0.00 | 0.00 | 0.00 | 0.00 | 0.00 |
| Reference Article | Type of IC Used | Feature Selection Needed | Feature Selection | HT Type | Learning Model | Evaluation Metric |
|---|---|---|---|---|---|---|
| [48] | ASIC | ✓ | Circuit path information | Combinational | LSTM | TPR: 84.00% |
| Proposed Method | FPGA | X | Not needed | Combinational | LSTM | Accuracy: 93.50% |
| [48] | ASIC | ✓ | Circuit path information | Sequential | LSTM | TPR-99.00% |
| Proposed Method | FPGA | X | Not needed | Sequential | LSTM | Accuracy: 91.00% |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2024 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Dofe, J.; Danesh, W.; More, V.; Chaudhari, A. Natural Language Processing for Hardware Security: Case of Hardware Trojan Detection in FPGAs. Cryptography 2024, 8, 36. https://doi.org/10.3390/cryptography8030036
Dofe J, Danesh W, More V, Chaudhari A. Natural Language Processing for Hardware Security: Case of Hardware Trojan Detection in FPGAs. Cryptography. 2024; 8(3):36. https://doi.org/10.3390/cryptography8030036
Chicago/Turabian StyleDofe, Jaya, Wafi Danesh, Vaishnavi More, and Aaditya Chaudhari. 2024. "Natural Language Processing for Hardware Security: Case of Hardware Trojan Detection in FPGAs" Cryptography 8, no. 3: 36. https://doi.org/10.3390/cryptography8030036
APA StyleDofe, J., Danesh, W., More, V., & Chaudhari, A. (2024). Natural Language Processing for Hardware Security: Case of Hardware Trojan Detection in FPGAs. Cryptography, 8(3), 36. https://doi.org/10.3390/cryptography8030036







