Defence against Side-Channel Attacks for Encrypted Network Communication Using Multiple Paths
Abstract
1. Introduction
1.1. Contribution
- A multipath mechanism that prevents analysis by known and unknown side channels due to the underlying behavior being protected, which avoids the overheads associated with other defences, as no artificial delay, junk packets, or padding is added to the packet flow.
- A thorough analysis of protection against privacy attacks based on the use of Hidden Markov Models (HMMs), which are common attacks for (encrypted) traffic based on traffic analysis of a stream of packets—a flow.
- Recommendations that are based on challenges from our analysis for real-world implementation in protocols.
1.2. Paper Structure
2. Traffic Analysis for Network Communication
2.1. Traffic Analysis Techniques
2.2. Use of the Hidden Markov Model (HMM)
2.3. Summary of Existing Countermeasures
- they are application-specific, as they operate at a high level of the stack;
- they require the use of a third party overlay, thus constraining deployability and potentially extending the trust boundary; and
- they are “loud”—that is, an attacker can see that the defence is in use, and may be able to leverage this in further attacks.
3. Evading Traffic Analysis
3.1. Limits of Existing Defences
3.2. Disrupting Interception
3.3. Multipath Evasion and Traffic Splitting
4. Multipath Communication
- Communicating hosts on the Internet have IP addresses, which are included in packets and which serve two key purposes: they provide a global identity for a host and also provide a (topological) location to allow for the correct forwarding of packets. Each packet contains a source address for the sender and a destination address for the receiver.
- Traditionally, routing algorithms for IP could discover multiple paths across the Internet between a given source and destination. However, the usual behavior of routing protocols is to select a single path (based on some metric) for communication between a given source and destination based on the destination IP address.
4.1. Using Multiple Paths
- Spreading load across the network: The traffic load is distributed across the network rather than being concentrated on a single path for a given source/destination. This helps to prevent congestion in the network.
- Resilience for the flow: A communication flow (a sequence of packets) has better resilience to loss and delay in the case of disruption or congestion on a single path.
- Perturbing traffic capture: Having the packets within a (logical) communication flow distributed across multiple (physical) paths makes it harder for an attacker to intercept all of the packets in a flow, as the attacker will need to monitor multiple paths.
4.2. Practicalities of Multiple Paths in Networking
4.3. The Identifier Locator Network Protocol (ILNP) and Privacy
5. Analysis of HMMs
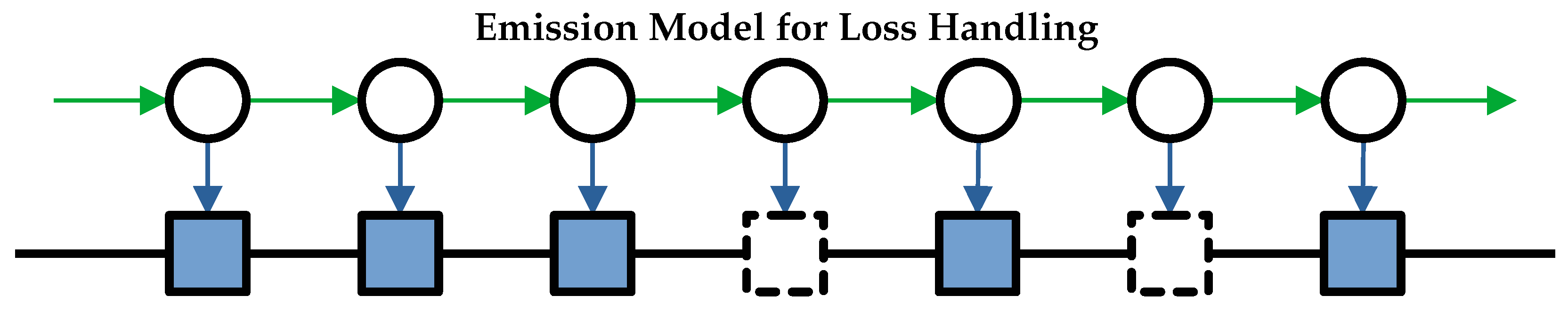
5.1. The Emission Model
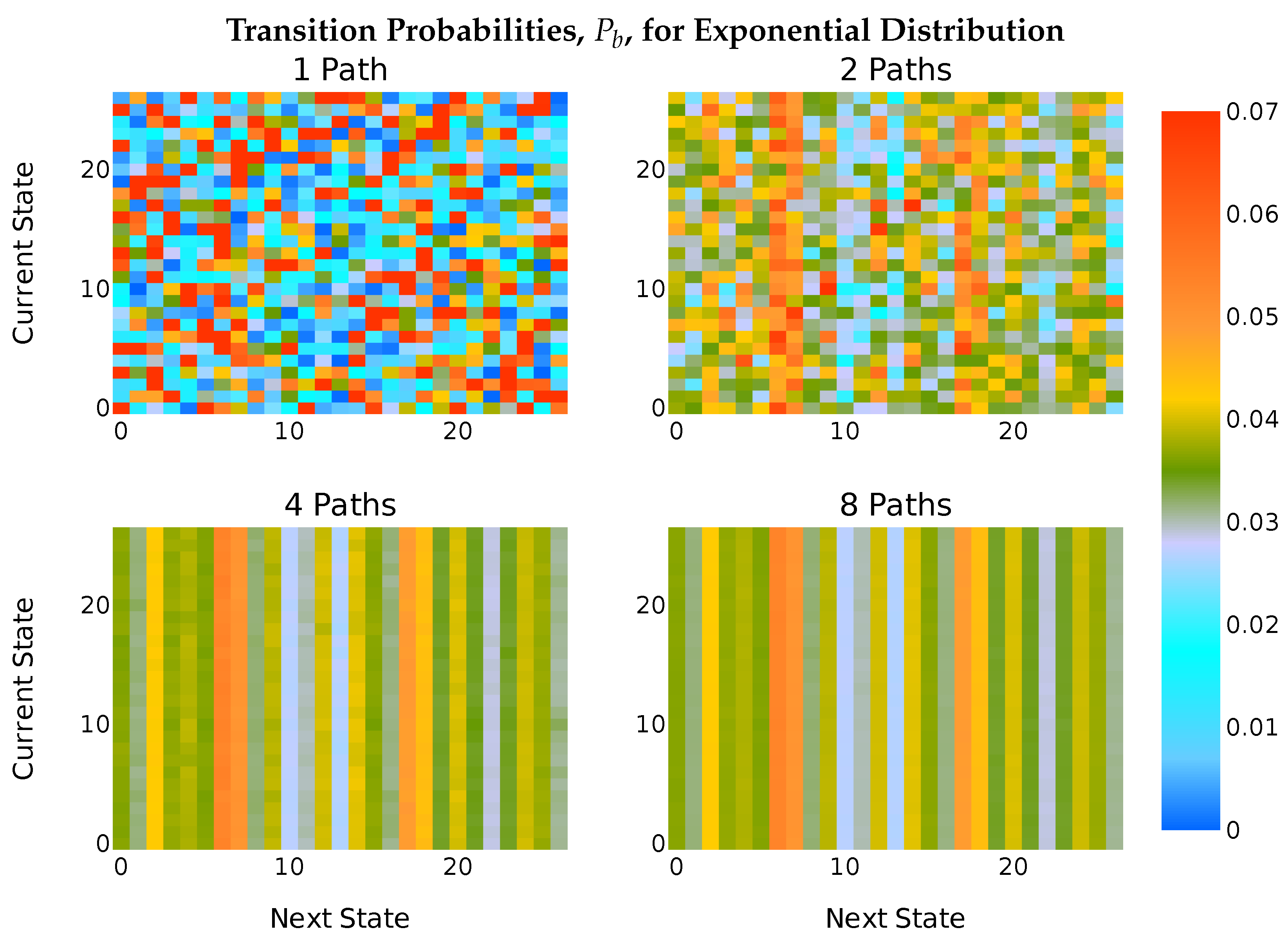
5.2. The Transition Model
Analysis of Loss Models
6. Evaluation
6.1. General Markov Model Simulations
6.2. Methodology
6.2.1. Traffic Distributions and Transition Probabilities
- A uniform random distribution from 0 to 1000;
- A normal distribution with a mean of 250 and standard deviation of 150;
- An exponential distribution with a rate parameter of 1.0;
- The same exponential distribution but with 1 added to each frequency sampled so that all transition probabilities were nonzero.
6.2.2. Markov Models
6.3. Results
6.4. Convergence on Unigram Probability
6.5. Specific Markov Model Analysis
- Bram Stoker’s Dracula (published in 1897);
- Homer’s The Odyssey (translated in 1897);
- Homer’s The Iliad (translated in 1899).
7. Discussion and Recommendations
7.1. Limitations of the Defence When Applied to the English Corpus
7.2. Implementation Concerns
7.3. Pathological Topology
7.4. Coarse Feature Analysis
7.5. Resilience against Other Attacks
8. Conclusions, Summary, and Future Work
- That the emission and transition properties of an HMM can be transformed to a single transition model for an HMM. This is achieved by combining the loss rate into the transition probabilities, because the loss emission probability can be evaluated as a constant for a communication flow. Also, as Markov models are memoryless, loss events have limited impact on the HMM modeling of a communication flow, especially a flow that is a long-lived flow in time.
- As the Markov models only depend on the current state for computing the probability of the next state, we treat a communication flow, even an encrypted flow, as a set of transitions of states represented by the packets in the flow. If the set of probabilities from current state to next state can be perturbed, then an attack based on observation of those state transitions can also be perturbed.
- A communication system that distributes the packets in a communication flow across multiple paths effectively perturbs the observation of correct state transitions. If an observer only has visibility of one of these paths, the full transition model is perturbed, even for long-lived flows, and an HMM-based attack is perturbed. So, a multipath communication can act as a defence against an HMM-based attack. The overall utility of such a defence improves as the number of paths over which flow is distributed increases. Our simulation results show that there is a significant utility to such a defence with three or more paths. However, in our worst case scenario, where an attacker has full knowledge of the nature of the source, five or more paths are required.
- The use of a protocol such as ILNP at the network layer (layer 3) of the communication stack would enable the distribution of packets in the way described in this paper. This would enable any transport protocol (layer 4), and therefore any application protocol, to benefit from this mechanism. This method of distributing packets below the transport layer will require transport layer mechanisms such as congestion control to be redesigned for optimal performance.
8.1. Summary of This Paper
8.2. Future Work
Author Contributions
Funding
Data Availability Statement
Conflicts of Interest
Abbreviations
| HMM | Hidden Markov Model |
| HTTP | HyperText Transfer Protocol |
| ILNP | Identifier Locator Network Protocol |
| IPAT | Interpacket Arrival Time |
| IPv6 | Internet Protocol version 6 |
| L64 | ILNP Locator |
| LRR | Locator Rewriting Relay |
| QUIC | now considered a name, but formerly Quick UDP Internet Connections |
| NID | Node Identifier. |
| SCTP | Stream Control Transmission Protocol |
| TCP | Transmission Control Protocol |
| UDP | User Datagram Protocol |
| VoIP | Voice over Internet Protocol |
References
- Dyer, K.P.; Coull, S.E.; Ristenpart, T.; Shrimpton, T. Peek-a-Boo, I Still See You: Why Efficient Traffic Analysis Countermeasures Fail. In Proceedings of the 2012 IEEE Symposium on Security and Privacy, San Francisco, CA, USA, 20–23 May 2012; pp. 332–346. [Google Scholar] [CrossRef]
- Hall, J.L.; Aaron, M.D.; Andersdotter, A.; Jones, B.; Feamster, N.; Knodel, M. A Survey of Worldwide Censorship Techniques. RFC 9505, 2023. Available online: https://www.rfc-editor.org/info/rfc9505 (accessed on 10 May 2024). [CrossRef]
- Trammell, B.; Kühlewind, M. The Wire Image of a Network Protocol. RFC 8546, 2019. Available online: https://www.rfc-editor.org/info/rfc8546 (accessed on 10 May 2024). [CrossRef]
- Song, D.X.; Wagner, D.; Tian, X. Timing Analysis of Keystrokes and Timing Attacks on SSH. In Proceedings of the 10th USENIX Security Symposium (USENIX Security 01), Washington, DC, USA, 13–17 August 2001. [Google Scholar]
- Wright, C.V.; Ballard, L.; Coull, S.E.; Monrose, F.; Masson, G.M. Spot Me if You Can: Uncovering Spoken Phrases in Encrypted VoIP Conversations. In Proceedings of the 2008 IEEE Symposium on Security and Privacy (sp 2008), Oakland, CA, USA, 18–21 May 2008; IEEE: New York, NY, USA, 2008. [Google Scholar] [CrossRef]
- Wright, C.V.; Ballard, L.; Monrose, F.; Masson, G.M. Language Identification of Encrypted VoIP Traffic: Alejandra y Roberto or Alice and Bob? In Proceedings of the USENIX Security Symposium, Boston, MA, USA, 6–10 August 2007. [Google Scholar]
- Abbasi, M.; Shahraki, A.; Taherkordi, A. Deep Learning for Network Traffic Monitoring and Analysis (NTMA): A Survey. Comput. Commun. 2021, 170, 19–41. [Google Scholar] [CrossRef]
- Alqudah, N.; Yaseen, Q. Machine Learning for Traffic Analysis: A Review. Procedia Comput. Sci. 2020, 170, 911–916. [Google Scholar] [CrossRef]
- Almutiri, T.; Nadeem, F. Markov models applications in natural language processing: A survey. Int. J. Inf. Technol. Comput. Sci 2022, 2, 1–16. [Google Scholar] [CrossRef]
- Forney, G. The viterbi algorithm. Proc. IEEE 1973, 61, 268–278. [Google Scholar] [CrossRef]
- Baum, L.E.; Petrie, T.; Soules, G.; Weiss, N. A Maximization Technique Occurring in the Statistical Analysis of Probabilistic Functions of Markov Chains. Ann. Math. Stat. 1970, 41, 164–171. [Google Scholar] [CrossRef]
- Dingledine, R.; Mathewson, N.; Syverson, P. Tor: The Second-Generation Onion Router. In Proceedings of the 13th USENIX Security Symposium (USENIX Security 04), San Diego, CA, USA, 9–13 August 2004. [Google Scholar]
- Abusnaina, A.; Jang, R.; Khormali, A.; Nyang, D.; Mohaisen, D. DFD: Adversarial Learning-based Approach to Defend Against Website Fingerprinting. In Proceedings of the IEEE INFOCOM 2020—IEEE Conference on Computer Communications, Toronto, ON, Canada, 6–9 July 2020; pp. 2459–2468. [Google Scholar] [CrossRef]
- Dantas, B.; Carvalho, P.; Lima, S.R.; Silva, J.M.C. Detection of Anonymised Traffic: Tor as Case Study. In Proceedings of the Internet of Things, Smart Spaces, and Next Generation Networks and Systems, 20th International Conference, NEW2AN 2020, and 13th Conference, ruSMART 2020, St. Petersburg, Russia, 26–28 August 2020; Galinina, O., Andreev, S., Balandin, S., Koucheryavy, Y., Eds.; Springer: Cham, Switzerland, 2020; pp. 95–109. [Google Scholar]
- Winter, P.; Crandall, J.R. The Great Firewall of China: How it blocks Tor and why it is hard to pinpoint. Login Usenix Mag. 2012, 37, 42–50. [Google Scholar]
- Wright, C.V.; Coull, S.E.; Monrose, F. Traffic Morphing: An Efficient Defense Against Statistical Traffic Analysis. In Proceedings of the Network and Distributed System Security Symposium, San Diego, CA, USA, 8–11 February 2009. [Google Scholar]
- Wang, T.; Goldberg, I. Walkie-Talkie: An Efficient Defense Against Passive Website Fingerprinting Attacks. In Proceedings of the 26th USENIX Security Symposium (USENIX Security 17), Vancouver, BC, Canada, 16–18 August 2017; pp. 1375–1390. [Google Scholar]
- Gong, J.; Wang, T. Zero-delay Lightweight Defenses against Website Fingerprinting. In Proceedings of the 29th USENIX Security Symposium (USENIX Security 20), Boston, MA, USA, 12–14 August 2020; USENIX Association: Berkeley, CA, USA, 2020; pp. 717–734. [Google Scholar]
- Wang, Y.; Wang, Y.; Huang, J.J.; Chen, Y. TBP: Tree structure Burst-sequence Padding Defense Against Website Fingerprinting. In Proceedings of the 2023 IEEE International Performance, Computing, and Communications Conference (IPCCC), Anaheim, CA, USA, 17–19 November 2023; pp. 99–108. [Google Scholar] [CrossRef]
- Al-Naami, K.; El-Ghamry, A.; Islam, M.S.; Khan, L.; Thuraisingham, B.; Hamlen, K.W.; Alrahmawy, M.; Rashad, M.Z. BiMorphing: A Bi-Directional Bursting Defense against Website Fingerprinting Attacks. IEEE Trans. Dependable Secur. Comput. 2021, 18, 505–517. [Google Scholar] [CrossRef]
- Gong, J.; Zhang, W.; Zhang, C.; Wang, T. WFDefProxy: Real World Implementation and Evaluation of Website Fingerprinting Defenses. IEEE Trans. Inf. Forensics Secur. 2024, 19, 1357–1371. [Google Scholar] [CrossRef]
- Nasr, M.; Bahramali, A.; Houmansadr, A. Defeating DNN-Based Traffic Analysis Systems in Real-Time With Blind Adversarial Perturbations. In Proceedings of the 30th USENIX Security Symposium (USENIX Security 21). USENIX Association, Vancouver, BC, Canada, 11–13 August 2021; pp. 2705–2722. [Google Scholar]
- Bhat, S.; Lu, D.; Kwon, A.; Devadas, S. Var-CNN: A Data-Efficient Website Fingerprinting Attack Based on Deep Learning. Proc. Priv. Enhancing Technol. 2019, 2019, 292–310. [Google Scholar] [CrossRef]
- Oh, S.E.; Sunkam, S.; Hopper, N. pFP: Extraction, Classification, and Prediction of Website Fingerprints with Deep Learning. arXiv 2019, arXiv:1711.03656. [Google Scholar]
- Iyengar, J.; Thomson, M. QUIC: A UDP-Based Multiplexed and Secure Transport. RFC 9000(PS), IETF, 2021. Available online: https://www.rfc-editor.org/info/rfc9000 (accessed on 20 May 2024). [CrossRef]
- Ford, A.; Raiciu, C.; Handley, M.; Bonaventure, O.; Paasch, C. TCP Extensions for Multipath Operation with Multiple Addresses. RFC 8684(PS), IETF, 2020. Available online: https://www.rfc-editor.org/info/rfc8684 (accessed on 10 May 2024). [CrossRef]
- Abolfathi, M.; Shomorony, I.; Vahid, A.; Jafarian, J.H. A Game-Theoretically Optimal Defense Paradigm against Traffic Analysis Attacks Using Multipath Routing and Deception. In Proceedings of the 27th ACM on Symposium on Access Control Models and Technologies, New York, NY, USA, 8–10 June 2022; SACMAT ’22. pp. 67–78. [Google Scholar] [CrossRef]
- De la Cadena, W.; Mitseva, A.; Hiller, J.; Pennekamp, J.; Reuter, S.; Filter, J.; Engel, T.; Wehrle, K.; Panchenko, A. TrafficSliver: Fighting Website Fingerprinting Attacks with Traffic Splitting. In Proceedings of the 2020 ACM SIGSAC Conference on Computer and Communications Security, New York, NY, USA, 9–13 November 2020; CCS ’20. pp. 1971–1985. [Google Scholar] [CrossRef]
- Liu, L.; Hu, N.; Shan, C.; Jiang, Y.; Liu, X. SMART: A Lightweight and Reliable Multi-Path Transmission Model against Website Fingerprinting Attacks. Electronics 2023, 12, 1668. [Google Scholar] [CrossRef]
- Moon, T.; Park, J.; Kim, S. BlueFMCW: Random frequency hopping radar for mitigation of interference and spoofing. EURASIP J. Adv. Signal Process. 2022, 2022, 4. [Google Scholar] [CrossRef]
- Wang, T.; Cai, X.; Nithyanand, R.; Johnson, R.; Goldberg, I. Effective Attacks and Provable Defenses for Website Fingerprinting. In Proceedings of the 23rd USENIX Security Symposium (USENIX Security 14), San Diego, CA, USA, 20–22 August 2014; pp. 143–157. [Google Scholar]
- Hayes, J.; Danezis, G. k-fingerprinting: A Robust Scalable Website Fingerprinting Technique. In Proceedings of the 25th USENIX Security Symposium (USENIX Security 16), Austin, TX, USA, 10–12 August 2016; pp. 1187–1203. [Google Scholar]
- Sirinam, P.; Imani, M.; Juarez, M.; Wright, M. Deep Fingerprinting: Undermining Website Fingerprinting Defenses with Deep Learning. In Proceedings of the 2018 ACM SIGSAC Conference on Computer and Communications Security, CCS’ 18, New York, NY, USA, 15–19 October 2018; pp. 1928–1943. [Google Scholar] [CrossRef]
- Stewart, R.; Tuxen, M.; Nielsen, K. Stream Control Transmission Protocol. RFC 9260(PS), IETF, 2022. Available online: https://www.rfc-editor.org/info/rfc9260 (accessed on 10 May 2024). [CrossRef]
- Deering, S.; Hinden, R. Internet Protocol, Version 6 (IPv6) Specification. RFC 8200(S), IETF, 2017. Available online: https://www.rfc-editor.org/info/rfc8200 (accessed on 10 May 2024). [CrossRef]
- Gont, F.; Krishnan, S.; Narten, T.; Draves, R. Temporary Address Extensions for Stateless Address Autoconfiguration in IPv6. RFC 8981(PS), IETF, 2021. Available online: https://www.rfc-editor.org/info/rfc8981 (accessed on 10 May 2024). [CrossRef]
- Yanagida, R.; Bhatti, S.N. Seamless Internet connectivity for ubiquitous communication. In Proceedings of the PURBA2019, Pervasive Urban Applications Workshop, London, UK, 9–13 September 2019; p. 12. [Google Scholar] [CrossRef]
- Bhatti, S.N.; Haywood, G.; Yanagida, R. End-to-End Privacy for Identity & Location with IP. In Proceedings of the NIPAA-21—2nd Workshop on New Internetworking Protocols, Architecture and Algorithms (ICNP 2021), Online, 1 November 2021; p. 6. [Google Scholar] [CrossRef]
- Haywood, G.T.; Bhatti, S.N.; Yanagida, R. ILNP—Identifier-Locator Network Protocol: FreeBSD 14.0 @ IETF118/Prague (Dataset). Available online: https://research-portal.st-andrews.ac.uk/en/datasets/ilnp-identifier-locator-network-protocol-freebsd-140-ietf118pragu (accessed on 10 May 2024). [CrossRef]
- Markov, A.A. Theory of Algorithms; Academy of Sciences of the USSR: Moscow, Russia, 1954. [Google Scholar]
- Haywood, G.T.; Bhatti, S.N. Cryptography2024-Data: Data and Source Files for Paper, “Defence against Side-Channel Attacks for Encrypted Network Communication Using Multiple Paths”, from Cryptography 2024. Available online: https://doi.org/10.17630/bf2ffcc2-8663-42a8-b019-ca18005236ba (accessed on 20 May 2024).
- Bizzocchi, A. How Many Phonemes Does the English Language Have? Int. J. Stud. Engl. Lang. Lit. 2017, 5, 36–46. [Google Scholar] [CrossRef]
- Atkinson, R.; Bhatti, S.N. Optional Advanced Deployment Scenarios for the Identifier-Locator Network Protocol (ILNP). RFC 6748(E), IRTF, 2012. Available online: https://www.rfc-editor.org/info/rfc6748 (accessed on 10 May 2024). [CrossRef]





| Parameter | Value | Description |
|---|---|---|
| Types () | 5 | Normal, Uniform, Exponential, Nonzero Exponential |
| English Corpus (worst case, model known by attacker). | ||
| States | 28 | Letters in English alphabet, plus a space character and a starting state. |
| Chain size () | Representing, for example, a document or a long-lived interactive communication. | |
| Chains per model (Nc) | Representing multiple communications per model use. | |
| Each chain is different but follows the same model. | ||
| Transitions per model | , giving a possible attacker a large number of transitions for a successful attack. | |
| Models () | 250 | Randomized Markov models of each type to reduce random error due to possible outliers. |
| (Number of runs to evaluate for each path.) |
| Distribution | 1 | 2 | 3 | 4 | 5 | 6 | 7 | 8 |
|---|---|---|---|---|---|---|---|---|
| Unigram Only | 1.0 | 1.0 | 1.0 | 1.0 | 1.0 | 1.0 | 1.0 | 1.0 |
| Normal | 0.67 | 0.73 | 1.0 | 1.0 | 1.0 | 1.0 | 1.0 | 1.0 |
| Uniform | 0.52 | 0.95 | 0.99 | 1.0 | 1.0 | 1.0 | 1.0 | 1.0 |
| Exponential | 0.29 | 0.86 | 0.98 | 1.0 | 1.0 | 1.0 | 1.0 | 1.0 |
| Nonzero Exponential | 0.65 | 0.97 | 1.0 | 1.0 | 1.0 | 1.0 | 1.0 | 1.0 |
| English Corpus | 0.25 | 0.45 | 0.74 | 0.82 | 0.88 | 0.91 | 0.94 | 0.96 |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2024 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Haywood, G.T.; Bhatti, S.N. Defence against Side-Channel Attacks for Encrypted Network Communication Using Multiple Paths. Cryptography 2024, 8, 22. https://doi.org/10.3390/cryptography8020022
Haywood GT, Bhatti SN. Defence against Side-Channel Attacks for Encrypted Network Communication Using Multiple Paths. Cryptography. 2024; 8(2):22. https://doi.org/10.3390/cryptography8020022
Chicago/Turabian StyleHaywood, Gregor Tamati, and Saleem Noel Bhatti. 2024. "Defence against Side-Channel Attacks for Encrypted Network Communication Using Multiple Paths" Cryptography 8, no. 2: 22. https://doi.org/10.3390/cryptography8020022
APA StyleHaywood, G. T., & Bhatti, S. N. (2024). Defence against Side-Channel Attacks for Encrypted Network Communication Using Multiple Paths. Cryptography, 8(2), 22. https://doi.org/10.3390/cryptography8020022






