Auditable Anonymous Electronic Examination
Abstract
1. Introduction
2. Related Work
3. Preliminaries
3.1. Attribute-Based Credential
3.2. Identity-Based Cryptography
3.3. Attribute-Based Encryption
3.4. Mix Network
Scalix
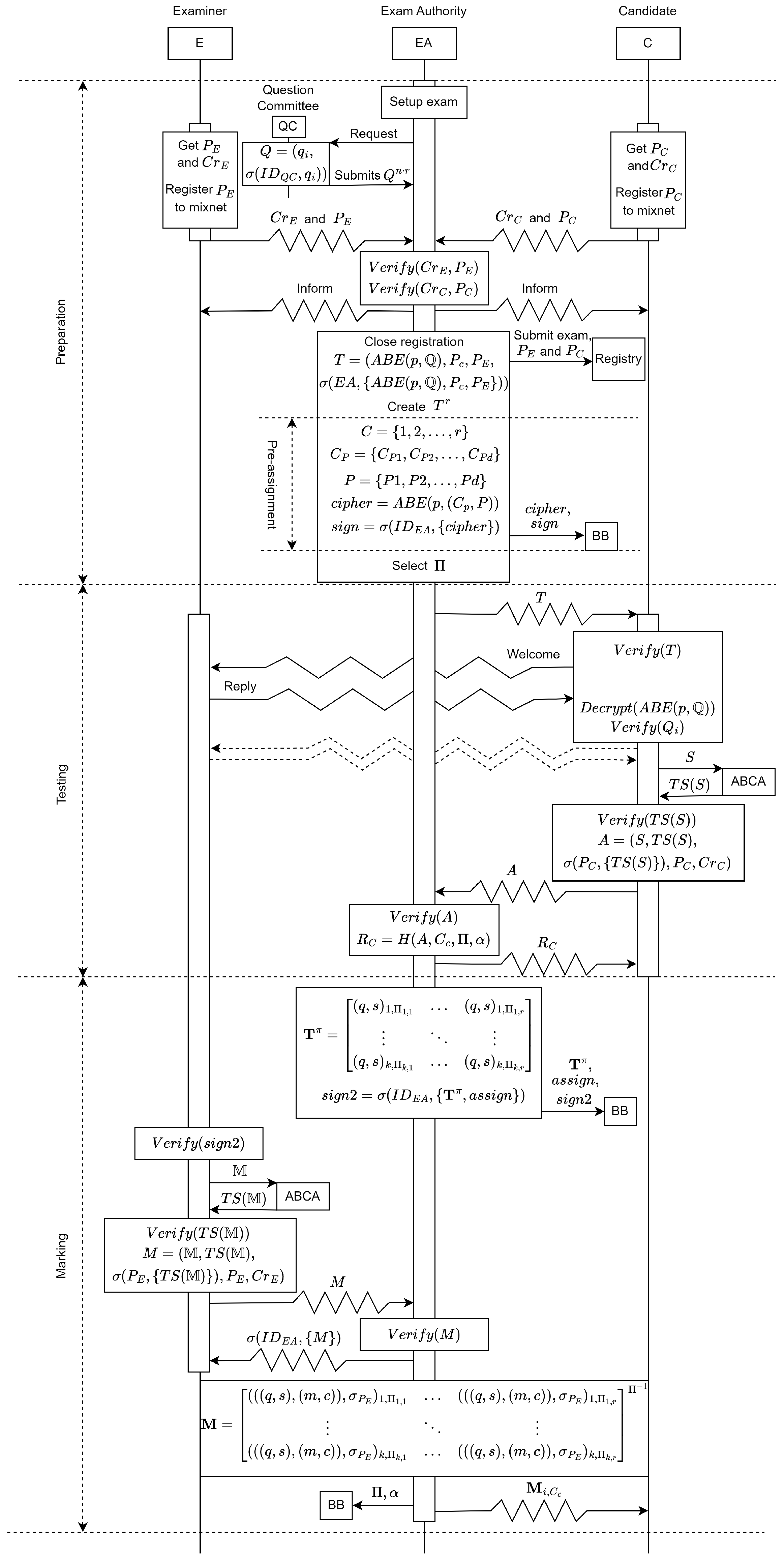
4. Our Protocol
4.1. Roles
- Question Committee (QC): Creates questions for all tests included in exams.
- Attribute-Based Certificate Authority (ABCA): Provides certificate issuance and timestamp generation services. Trusted and honest party in the system.
- Registry: Maintains database of institute regarding examiners and candidates. Trusted and honest party in the system. Also works as an attribute authority for ABC and ABE services.
- Exam Authority (EA): Responsible for organizing exams and maintaining authenticity. The EA is not a trusted party; there is potential for it to be malicious.
- Auditor Authority (AA): All auditing procedures are fulfilled by the AA; in the case of fraudulent behavior, it provides proof for the supervisory board. Not a trusted party; could be malicious.
- Candidate: The exam taker or student. Acts out of self-interest; not trusted; could be malicious.
- Examiner: Marks answers and responds to questions from candidates during the testing phase. Not a trusted party; has potential to be malicious.
- Supervisory Board (SB): A group of people whose task is to examine any complaint and, by majority vote, decide how to respond. Considered to be trusted to a certain level as they make decisions in a distributed manner.
4.2. Goals and Security Requirements
4.2.1. Authentication
- Candidate Authorization: Only registered candidates can take an exam. If a candidate submits an answer, then the candidate was correctly registered for the exam.
- Examiner Authorization: Only registered examiners can mark an exam. If an examiner submits a mark, then the examiner was correctly registered for the exam.
- Answer Authenticity: It states that the exam authority should consider only answers that candidates have actually submitted, and that the contents of all collected answers are not modified after submission. An answer must be bound to a candidate.
- Answer Origin Authentication: The exam authority should accept only answers that originate from registered candidates. In addition, only one answer from each registered candidate is actually collected.
- Answer Authenticity: The examiner only marks the answers intended for them. Moreover, the contents of each answer may not be modified until after the answers are marked by the examiner.
- Mark Authenticity: A mark should be correctly recorded for the corresponding answer and candidate, i.e., the examination authority should store the mark assigned to an answer during marking by the examiner.
- Mark Authentication: The candidate should be notified with the same mark that has been stored by the examination authority.
4.2.2. Privacy
- Question Indistinguishability: The questions should not be revealed until the testing phase begins. Two processes with different questions have to be observationally equivalent until the end of the preparation phase.
- Anonymous Marking: The examiner should mark an answer while ignoring its author, namely an anonymous answer. It is a clear contribution to the fairness of the marking.
- Anonymous Examiner: It concerns all phases of an exam because examiner anonymity could be required to hold forever to prevent bribing or coercion. Thus, it is required that no candidate knows which examiner marked their answers. The examiner should only be de-anonymized in the case of proven fraud.
- Examiner Accountability: If an examiner is found to engage in fraudulent behavior, it is necessary to de-anonymize them and retrieve their identity. This ensures accountability for their actions.
- Anonymous Candidate: A candidate should hold anonymity through all phases of the exam until the grading, before which they should de-anonymize themselves or become de-anonymizable, therefore being able to receive their grade.
- Mark Privacy: The mark ultimately attributed to a candidate is treated as valuable personal information. More specifically, no party learns the marks, besides the examiner, the concerned candidate, and the authority responsible for the notification. This means that the marks cannot be made public.
- Mark Anonymity: No one should learn the association between a mark and the corresponding candidate.
- Candidate–Examiner Communication Anonymity: The exam system should provide a communication channel between candidates and examiners in such a way that the examiners cannot learn anything about the candidates.
4.2.3. Individual Verifiability
- Question Validity: The candidate can check that they have received the questions actually generated by the question committee.
- Marking Correctness: The candidate can verify that the mark received is correctly computed on their answer.
- Answer Integrity: The candidate can check that their answer is accepted and marked as they submitted it.
- Answer Markedness: The candidate can check that the answer submitted is marked without modification.
- Mark Integrity: The candidate can verify that the mark attributed to their answer is assigned to them without any modification.
- Mark Notification Integrity: The candidate can check that they have received the mark assigned to them.
4.2.4. Universal Verifiability
- Registration Universal Verifiability: An auditor can check that all accepted answers are submitted by registered candidates and all accepted marks are submitted by registered examiners. Thus, the exam authority should have considered only answers that originated from eligible candidates and marks that originated from eligible examiners.
- Marking Correctness Universal Verifiability: An auditor can check that all marks attributed by the examiners to the answers are computed correctly.
- Answer Integrity Universal Verifiability: An auditor can verify that all and only accepted answers are marked without any modification. This means that the auditor can be sure that no answer is modified, added, or deleted until the end of marking.
- Mark Integrity Universal Verifiability: An auditor can check that all and only the marks associated to the answers are assigned to the corresponding candidates, with no modifications.
- Communication Universal Verifiability: An auditor can check that, during the communication between candidates and examiners, no rules were violated.
4.2.5. Our Requirements for ABC Systems
4.3. Structures
- The question is the product of the QC. Based on the security requirements of the system, we distinguish two types of this structure.In the first case, the questions created by the QC are part of a public database; therefore, the QC does not perform encryption, but only provides a signature. Here, the question Q is a pair , where q is a plaintext (the text of the question) and is the digital signature of the QC.The second case is when the QC wishes to keep the questions secret until the candidates start their tests. In this case, the question Q is a pair , where is the digital signature of the QC and is the q question encrypted with ABE, under p policy. In this case, the policy may include useful constraints. If the EA shares some details of the exam that they requested the questions for, the QC can include a candidate eligibility check in the policy. It also has to include a constraint on the decryption key’s freshness, as a timed release (check if generated after the start of the exam) could also add a constraint to ensure that the candidate is registered to the exam. The combination of the latter property and the time constraint would also enable the question to only be usable in the given exam.
- A test is created by the EA. Similarly to the question, we can consider two cases for this structure, based on the security requirements and based on the structure of the question.First, let be a list of questions, and the test , where is the attribute-based encryption of a list of questions, under p policy. Here, p has to include a timed release constraint and may include the same constraints as described in the second case of the question or any other extensions, based on the needs of the implementation. is the pseudonym of a candidate, which is necessary to bound the test to the candidate. is the pseudonym of an examiner, with whom the candidate can communicate through the mixnet during the exam, and is the digital signature of the EA.Second, let be a list of questions, with the test . In this case, the list of questions is not encrypted, assuming that they were already encrypted previously.
- An answer is the product of a candidate. The structure of an answer A is represented as . The solution S is defined as a set of pairs , where, for each , is the question included in and is the candidate’s solution for . is the timestamp generated for S, is the candidate’s digital signature, generated using his pseudonym , and is the required credentials of the candidate.
- A mark is the product of an examiner. A mark , where is a set , where, for each is a question–solution pair originating from a candidate and is the mark and comment given by the examiner. Moreover, the examiner digitally signs each element of the set (denoted as ) with his pseudonym . is the timestamp generated for , following which denotes the digital signature of generated with the examiner’s pseudonym . Finally, denotes the examiner’s required credentials.
4.4. Phases
4.4.1. Preparation
- (P1)
- The EA files the exam in their system, setting all the necessary information, including a deadline for marking. It also establishes eligibility criteria, specifying the required attributes for exam registration. This information, accessible to the public, covers both candidates and examiners. Additionally, a bulletin board (BB) is introduced for each exam, inspired by Remark! [16]. Only the EA can publish information on the BB, while the examiners, candidates, and AA can only read it. In this step, the EA informs the QC to submit questions for the exam.
- (P2)
- The QC submits signed questions to the EA.
- (P3)
- The candidates and examiners create new pseudonyms and submit them to the mix network service provider. The provider accepts them if they are unique pseudonyms and, therefore, maintains the anonymous communication service for them.
- (P4)
- The candidates and examiners register for the exam, providing their attribute-based credentials and pseudonyms to the EA anonymously through a mix network. The EA verifies the authenticity and eligibility of the credentials and pseudonyms. Subsequently, the EA informs the candidates and examiners about the success or failure of their registration through the mix network. The EA submits the pseudonyms of the registered candidates and examiners to the registry, along with information about the exam that they have registered for, essential for the ABE decryption of the test.
- (P5)
- After the registration closes, the EA creates tests from the submitted questions, assigning each test to a candidate. Each candidate is assigned to exactly one test. The questions in the test are encrypted with ABE, using exam eligibility constraints, along with a timed release attribute and an attribute requiring the decryptor to be registered for the exam. The tests are then signed by the EA. For timed release, Ref. [44] provides an overview, which includes this idea in the case of identity-based encryption. However, it is more convenient with attribute-based encryption due to the flexible means of applying attribute constraints. In our case, we require that the decryption key be fresh, created close to the time of the exam. The specific timing can be determined by the system owner or the EA.
- (P6)
- During preparation, a pre-assignment, introduced by Rakeei et al. [20], is implemented to assign examiners to mark a subset/partition of answers without revealing this partition to the public. In their protocol, the distribution of the pre-assignment is handled through secure channels to each examiner. The examiners send back a signature on the pre-assignment, and, as proof that they all received the same pre-assignment, the signatures are redistributed.Rakeei and his colleagues aimed to achieve coercion resistance by permitting examiners to provide false information about the pre-assignment in the event of coercion, as the assignment details are never disclosed, even in encrypted form. They also assumed that a coerced examiner would publish his private keys. Hence, it would be unrealistic to expect the examiner not to reveal all proof signatures confirming the pre-assignment.To simplify this process, we use the BB in combination with ABE for distribution. Assuming r candidates and d examiners registered for the exam, the EA forms a set representing registered candidates. The EA forms d partitions as and labels them as . The EA encrypts and P with ABE using a policy allowing only eligible registered examiners and the AA to decrypt it, resulting in a ciphertext . The EA digitally signs and publishes both the ciphertext and the digital signature on the BB. The examiners and the AA check the signature and, if correct, decrypt .
- (P7)
- Finally, the EA selects a secure permutation matrix , which will be relevant during the marking phase.
4.4.2. Testing
- (T1)
- The EA sends the tests to the candidates through the mix network.
- (T2)
- The candidates verify the tests by checking if their pseudonyms are included and by verifying the EA’s signature. Additionally, they confirm the validity of the examiner’s pseudonym with a welcome message sent through the mix network’s anonymous return channel. Eligible candidates decrypt the questions in the test and then verify the QC’s signatures for each question. The candidates can then start their tests.
- (T3)
- During the test, the candidates can communicate with the examiners through the anonymous return channel if necessary. The communication is logged so that, after or even during the exam, the AA can verify that the communication does not involve cheating.
- (T4)
- Upon finishing their work on the test, candidates can request a timestamp from the ABCA. They can verify the correctness of the timestamp and sign it using IBS. Afterward, they submit the answer to the EA through the mix network.
- (T5)
- The EA verifies, for every answer, that the candidate was registered for the exam by confirming their pseudonym and checks their eligibility using their credentials. The EA also checks if this is the candidate’s first time submitting an answer. Following this, the EA verifies the correctness of the signature in the answer and checks if the timestamp is accurate, with the included time falling before the end of the exam. If all the checks are fulfilled, the EA accepts the answer.
- (T6)
- The EA notifies the candidate about the acceptance or rejection of the answer through the mix network. In the case of acceptance, the EA also creates a receipt , where A is the answer submitted by candidate c, is the candidate’s number from the set C, is the permutation matrix from Step P7 of the preparation phase, is a random value generated for the current exam (to prevent candidates from prematurely sharing signatures), and H is a cryptographic hash function. Finally, the EA signs and includes the signature in the notification message.
4.4.3. Marking
- (M1)
- To prevent a malicious EA (collaborating with the AA) from sending the same test to multiple examiners and to prevent malicious examiners from fraudulent marking, we will use the shuffled answers technique [20]. The idea behind the technique is that the EA will share all the question–solution pairs on the BB in such a way that the pairs could form tests; however, they are shuffled, so each pair in the shared tests originates from different candidates.The EA creates a matrix of question–solution pairs and applies to it, forming a new matrix such that . Assuming that there are r candidates who submitted answers, and the tests had k questions, then is the answer of candidate j to question i.In the matrix , each column represents a test submitted by a candidate. In , the columns are tests with each question–solution pair originating from a different candidate. The EA randomly assigns each element of P to an examiner’s pseudonym. Then, the EA signs both and the assignments.If the implementation does not wish to share all the question–solution pairs with all the candidates, as they might be considered sensitive data, the EA encrypts using ABE with a policy allowing only eligible registered examiners and the AA to decrypt it. The EA also creates a new matrix holding the hashed versions of the question–solution pairs using a cryptographic hash function. Finally, the EA digitally signs the cipher of , and the assignments and publishes all of them on the BB, including the signature.Otherwise, they simply publish and the assignments and the signature on the BB.
- (M2)
- The examiner verifies the signature and then decrypts the cipher if was encrypted. Based on the assignments, they mark the correct partitions of the matrix in such a way that, for each column of the matrix partition, they will create a mark, which includes requesting a timestamp from the ABCA. They check if the timestamp is correct and sign it with IBS. Once a mark is created, the examiner sends it to the EA through the mix network.
- (M3)
- The EA verifies, for every mark submission, that the examiner was registered for the exam by confirming their pseudonym and checks their eligibility using their credentials. After this, they check if the signature of the mark is correct and check if the timestamp is correct, with the time included being before the end of the marking deadline. Moreover, they check that the examiner marked the correct partition. If all the checks are fulfilled, they accept the mark. If only the deadline is missed, they still accept the mark but report the delay to the SB. In the case of acceptance, the EA digitally signs the submitted mark and sends the signature to the examiner as a receipt.
- (M4)
- Once all the marks arrive, the EA constructs a matrix of these marks and applies , resulting in the matrix , where each column holds the mark of a candidate.
- (M5)
- The EA notifies the candidates about their marks through the mix network by sending the correct column of . Meanwhile, the EA publishes and on the BB.
4.4.4. Revising and Grading
- (G1)
- The candidate reviews the marks and comments received from the examiners. If a mistake is identified, they contact the EA by sending through the mix network, where e is a plaintext describing the found mistake, and is the candidate’s digital signature signing all the elements listed before it, with their pseudonym . The EA will then contact an examiner who did not mark the problematic answer through the mix network. The examiner reviews , makes remarks if necessary, and sends the new mark to the EA thorugh the mix network. The EA replaces the old mark with the new one and notifies the candidate again through the mix network.
- (G2)
- The candidate identifies themselves verifiably using the ABC’s de-anonymization (identification) method and also sends a digital signature of the received mark. If a candidate refuses to identify themselves, the EA should contact the SB by sending the candidate’s final mark as proof of the end of the exam. The SB will then use the ABC’s anonymity revocation method to identify the candidate for the EA and also sends a digital signature of the mark.
- (G3)
- The EA registers the grading to the registry by providing, for each candidate, the candidate’s identity in a verifiable form, the mark and a final grade, the candidate’s or the SB’s signature, and also the EA’s signature on this package.
4.4.5. Auditing
- (A1)
- Starting at the preparation phase, the AA obtains public information about the new exam and receives registrations as a log through the mix network. Since the EA responds to registration attempts with success or failure messages, the AA can verify that only eligible candidates and examiners were accepted for the exam. Additionally, if necessary, the AA can verify the EA’s honesty by checking the recipients of the sent-out tests.
- (A2)
- Following the registration phase, similarly using the logs, the AA can verify that the accepted answers are associated with the pseudonyms of registered candidates, ensuring registration universal verifiability.
- (A3)
- Furthermore, by utilizing the mix network logs, the AA receives all the marks, enabling compliance with the requirements of marking correctness universal verifiability and answer integrity universal verifiability.
- (A4)
- However, to achieve mark integrity universal verifiability, the AA should have access to the marks registered in the registry to compare the marks suggested by the examiners with those registered by the EA. Since the registry is a trusted party, the AA can assume that the data provided by it are equivalent to the data that the EA provided to the registry.
- (A5)
- Finally, communication universal verifiability is attained since all communication through the mix network is logged.
5. Identity-Based Proof of Correct Decryption
5.1. Zero-Knowledge Proof of Equality of Identity-Based Private Key
5.1.1. -Protocols
- A sends a commitment a;
- B sends a challenge c;
- A sends a response k, and B accepts or rejects it.
- The protocol is of the above 3-move form.
- The protocol has completeness. If both parties follow the protocol and , then the verifier always accepts.
- The protocol has the special soundness property. For any given Y and any pair of accepting transcripts on Y, , where , w is efficiently computable such that .
- The protocol has the special honest-verifier zero-knowledge property. There exists an efficient simulator that, when receiving Y and c as input, outputs an accepting transcript with the same distribution as an accepting protocol conversation between honest parties.
5.1.2. Our Protocol
- The prover chooses a random and computes . The prover sends to the verifier.
- The verifier chooses a random challenge and sends it to the prover.
- The prover computes and sends it to the verifier. Finally, the verifier accepts the proof; if , then and hold; otherwise, they reject it.
6. Auditable Mix Network
6.1. Scalix’s Packet
Achieving Auditability with Scalix
6.2. Scalix’s Anonymous Return Channel
7. Fraudulent Behavior or Unreadable Log
7.1. Decision-Making
7.2. De-Anonymization
7.3. Punishment
8. Security Analysis
Non-Cryptographic Threat
9. Conclusions
Author Contributions
Funding
Data Availability Statement
Acknowledgments
Conflicts of Interest
References
- Huszti, A.; Pethő, A. A secure electronic exam system. Publ. Math. Debr. 2010, 77, 299–312. [Google Scholar] [CrossRef]
- Watson, R. Student visa system fraud exposed in BBC investigation. BBC News. 10 February 2014. Available online: https://www.bbc.com/news/uk-26024375 (accessed on 30 April 2024).
- Liptak, K. US Navy discloses nuclear exam cheating. CNN. 4 February 2014. Available online: https://edition.cnn.com/2014/02/04/us/navy-cheating-investigation/index.html (accessed on 30 April 2024).
- Biswas, S. Vyapam: India’s deadly medical school exam scandal. BBC News. 8 July 2015. Available online: https://www.bbc.com/news/world-asia-india-33421572 (accessed on 30 April 2024).
- Strauss, V. Remember the Atlanta schools’ cheating scandal? It isn’t over. The Washington Post. 1 February 2022. Available online: https://www.washingtonpost.com/education/2022/02/01/atlanta-cheating-schools-scandal-teachers/ (accessed on 30 April 2024).
- Goldstein, M. Ernst & Young to Pay $100 Million Fine After Auditors Cheated on Ethics Exams. The New York Times. 28 June 2022. Available online: https://www.nytimes.com/2022/06/28/business/ernst-young-sec-cheating.html (accessed on 30 April 2024).
- Brands, S. Rethinking Public Key Infrastructures and Digital Certificates: Building in Privacy (The MIT Press); The MIT Press: Cambridge, MA, USA, 2000; p. 340. [Google Scholar]
- Camenisch, J.; Lysyanskaya, A. An Efficient System for Non-Transferable Anonymous Credentials with Optional Anonymity Revocation; Lecture Notes in Computer Science; Springer: Berlin/Heidelberg, Germany, 2001; pp. 93–118. [Google Scholar] [CrossRef]
- Bethencourt, J.; Sahai, A.; Waters, B. Ciphertext-Policy Attribute-Based Encryption. In Proceedings of the 2007 IEEE Symposium on Security and Privacy (SP ’07), Oakland, CA, USA, 20–23 May 2007. [Google Scholar] [CrossRef]
- Hess, F. Efficient Identity Based Signature Schemes Based on Pairings. In Selected Areas in Cryptography; Springer: Berlin/Heidelberg, Germany, 2003; pp. 310–324. [Google Scholar] [CrossRef]
- Vécsi, Á.; Pethő, A. Scalix Mix Network. Acta Cybernetica, to Appear.
- Castella-Roca, J.; Herrera-Joancomarti, J.; Dorca-Josa, A. A secure e-exam management system. In Proceedings of the First International Conference on Availability, Reliability and Security (ARES’06), Vienna, Austria, 20–22 April 2006; IEEE: Piscataway, NJ, USA, 2006. [Google Scholar] [CrossRef]
- Bella, G.; Costantino, G.; Riccobene, S. WATA—A System for Written Authenticated though Anonymous Exams. In Proceedings of the 2nd International Conference on Computer Supported Education—Volume 1: CSEDU, Valencia, Spain, 7–10 April 2010; INSTICC, SciTePress: Setúbal, Portugal, 2010; pp. 132–137. [Google Scholar] [CrossRef]
- Bella, G.; Costantino, G.; Coles-Kemp, L.; Riccobene, S. Remote management of face-to-face written authenticated though anonymous exams. In Proceedings of the 3rd International Conference on Computer Supported Education (CSEDU 2011)—Volume 2: ATTeL, Noordwijkerhout, The Netherlands, 6–8 May 2011; INSTICC, SciTePress: Setúbal, Portugal, 2011; pp. 431–437. [Google Scholar] [CrossRef]
- Bella, G.; Giustolisi, R.; Lenzini, G. Secure exams despite malicious management. In Proceedings of the 2014 Twelfth Annual International Conference on Privacy, Security and Trust, Toronto, ON, Canada, 23–24 July 2014; IEEE: Piscataway, NJ, USA, 2014. [Google Scholar] [CrossRef]
- Giustolisi, R.; Lenzini, G.; Ryan, P.Y.A. Remark!: A Secure Protocol for Remote Exams; Lecture Notes in Computer Science; Springer International Publishing: Berlin/Heidelberg, Germany, 2014; pp. 38–48. [Google Scholar] [CrossRef]
- Bella, G.; Giustolisi, R.; Lenzini, G.; Ryan, P.Y.A. A Secure Exam Protocol Without Trusted Parties. In IFIP Advances in Information and Communication Technology; Springer International Publishing: Berlin/Heidelberg, Germany, 2015; pp. 495–509. [Google Scholar] [CrossRef]
- Bella, G.; Giustolisi, R.; Lenzini, G.; Ryan, P.Y. Trustworthy exams without trusted parties. Comput. Secur. 2017, 67, 291–307. [Google Scholar] [CrossRef]
- Küppers, B.; Politze, M.; Zameitat, R.; Kerber, F.; Schroeder, U. Practical Security for Electronic Examinations on Students’ Devices. In Intelligent Computing; Springer International Publishing: Berlin/Heidelberg, Germany, 2018; pp. 290–306. [Google Scholar] [CrossRef]
- Rakeei, M.; Giustolisi, R.; Lenzini, G. Secure Internet Exams Despite Coercion. In Data Privacy Management, Cryptocurrencies and Blockchain Technology; Springer International Publishing: Berlin/Heidelberg, Germany, 2023; pp. 85–100. [Google Scholar] [CrossRef]
- Chaum, D. Security without identification: Transaction systems to make big brother obsolete. Commun. ACM 1985, 28, 1030–1044. [Google Scholar] [CrossRef]
- Christian Paquin, G.Z. U-Prove Cryptographic Specification V1.1 (Revision 5); Technical Report; Microsoft Corporation: Redmond, WA, USA, 2023. [Google Scholar]
- Paquin, C. U-Prove Technology Overview V1.1 (Revision 3); Technical Report; Microsoft Corporation: Redmond, WA, USA, 2023. [Google Scholar]
- Camenisch, J.; Herreweghen, E.V. Design and implementation of the idemix anonymous credential system. In Proceedings of the 9th ACM conference on Computer and Communications Security, Washington, DC, USA, 18–22 November 2002; ACM: New York, NY, USA, 2002. [Google Scholar] [CrossRef]
- Camenisch, J. Specification of the Identity Mixer Cryptographic Library Version 2.3.0; Technical Report; IBM Research: Zurich, Switzerland, 2010. [Google Scholar]
- Rannenberg, K.; Camenisch, J.; Sabouri, A. (Eds.) Attribute-Based Credentials for Trust; Springer International Publishing: Berlin/Heidelberg, Germany, 2015. [Google Scholar] [CrossRef]
- Hampiholi, B.; Alpár, G.; van den Broek, F.; Jacobs, B.; Lueks, W.; Ringers, S. IRMA: Practical, decentralized and privacy-friendly identity management using smartphones. In Proceedings of the 10th Workshop on Hot Topics in Privacy Enhancing Technologies, Minneapolis, MA, USA, 18–21 July 2017; HotPETs: Minneapolis, MA, USA, 2017. [Google Scholar]
- Sanchez, J.L.C.; Bernabe, J.B.; Skarmeta, A.F. Integration of Anonymous Credential Systems in IoT Constrained Environments. IEEE Access 2018, 6, 4767–4778. [Google Scholar] [CrossRef]
- Sene, I.; Ciss, A.A.; Niang, O. I2PA: An Efficient ABC for IoT. Cryptography 2019, 3, 16. [Google Scholar] [CrossRef]
- Shamir, A. Identity-based cryptosystems and signature schemes. Advances in Cryptology. In Proceedings of the CRYPTO 84 4, Santa Barbara, CA, USA, 19–22 August 1984; Springer: Berlin/Heidelberg, Germany, 1985; pp. 47–53. [Google Scholar]
- Boneh, D.; Franklin, M. Identity-Based Encryption from the Weil Pairing. In Advances in Cryptology—CRYPTO 2001; Springer: Berlin/Heidelberg, Germany, 2001; pp. 213–229. [Google Scholar] [CrossRef]
- Vécsi, Á.; Pethő, A. Formal Language Identity-based Cryptography. Rad Hrvat. Akad. Znan. Umjet. Mat. Znan. 2021, 25, 143–159. [Google Scholar] [CrossRef]
- Vécsi, Á.; Bagossy, A.; Pethő, A. Cross-platform Identity-based Cryptography using WebAssembly. Infocommun. J. 2019, 11, 31–38. [Google Scholar] [CrossRef]
- Sahai, A.; Waters, B. Fuzzy Identity-Based Encryption. In Advances in Cryptology—EUROCRYPT 2005; Springer: Berlin/Heidelberg, Germany, 2005; pp. 457–473. [Google Scholar] [CrossRef]
- Goyal, V.; Pandey, O.; Sahai, A.; Waters, B. Attribute-based encryption for fine-grained access control of encrypted data. In Proceedings of the 13th ACM conference on Computer and Communications Security, Alexandria, VA, USA, 30 October–3 November 2006; ACM: New York, NY, USA, 2006. [Google Scholar] [CrossRef]
- Chase, M. Multi-authority attribute based encryption. In Proceedings of the Theory of Cryptography: 4th Theory of Cryptography Conference, Amsterdam, The Netherlands, 21–24 February 2007; Springer: Berlin/Heidelberg, Germany, 2007; pp. 515–534. [Google Scholar] [CrossRef]
- Chaum, D.L. Untraceable electronic mail, return addresses, and digital pseudonyms. Commun. ACM 1981, 24, 84–90. [Google Scholar] [CrossRef]
- Dingledine, R.; Mathewson, N.; Syverson, P.F. Tor: The second-generation onion router. In Proceedings of the USENIX Security Symposium, San Diego, CA, USA, 9–13 August 2004; Volume 4, pp. 303–320. [Google Scholar] [CrossRef]
- Kesdogan, D.; Egner, J.; Büschkes, R. Stop-and-Go-MIXes Providing Probabilistic Anonymity in an Open System. In Lecture Notes in Computer Science; Springer: Berlin/Heidelberg, Germany, 1998; pp. 83–98. [Google Scholar] [CrossRef]
- Piotrowska, A.M.; Hayes, J.; Elahi, T.; Meiser, S.; Danezis, G. The loopix anonymity system. In Proceedings of the 26th Usenix Security Symposium (Usenix Security 17), Vancouver, BC, Canada, 19–18 August 2017; pp. 1199–1216. [Google Scholar]
- Golle, P.; Jakobsson, M. Reusable anonymous return channels. In Proceedings of the 2003 ACM Workshop on Privacy in the Electronic Society, Washington, DC, USA, 30 October 2003; ACM: New York, NY, USA, 2003. [Google Scholar] [CrossRef]
- Giustolisi, R. Modelling and Verification of Secure Exams; Springer International Publishing: Berlin/Heidelberg, Germany, 2018. [Google Scholar] [CrossRef]
- Zaverucha, G. U-Prove ID Escrow Extension; Technical Report MSR-TR-2013-86; Microsoft Corporation: Redmond, WA, USA, 2013. [Google Scholar]
- Takács, P. Kriptográfiai Protokollok formális Vizsgálata a CSN Logikai Rendszer Bővítésével. Ph.D. Thesis, University of Debrecen, Debrecen, Hungary, 2010. [Google Scholar]
- Chaum, D.; Pedersen, T.P. Wallet Databases with Observers. In Lecture Notes in Computer Science; Springer: Berlin/Heidelberg, Germany, 1992; pp. 89–105. [Google Scholar] [CrossRef]
- Cramer, R. Modular Design of Secure, yet Practical Cryptographic Protocols. Ph.D. Thesis, University of Amsterdam, Amsterdam, The Netherlands, 1996. [Google Scholar]
- Krenn, S.; Orrù, M. Proposal: Σ-Protocols. 2021. Available online: https://docs.zkproof.org/pages/standards/accepted-workshop4/proposal-sigma.pdf (accessed on 30 April 2024).
- Baek, J.; Zheng, Y. Identity-based threshold signature scheme from the bilinear pairings (extended abstract). In Proceedings of the International Conference on Information Technology: Coding and Computing, 2004 Proceedings, ITCC 2004, Las Vegas, NV, USA, 5–7 April 2004. [Google Scholar] [CrossRef]
- Cheng, X.; Liu, J.; Wang, X. An identity-based signature and its threshold version. In Proceedings of the 19th International Conference on Advanced Information Networking and Applications (AINA’05) Volume 1 (AINA Papers), Taipei, Taiwan, 28–30 March 2005; Volume 1, pp. 973–977. [Google Scholar] [CrossRef]
- Liu, J.; Huang, S. Identity-Based Threshold Proxy Signature from Bilinear Pairings. Informatica 2010, 21, 41–56. [Google Scholar] [CrossRef]
- Blanchet, B. An efficient cryptographic protocol verifier based on prolog rules. In Proceedings of the 14th IEEE Computer Security Foundations Workshop, Cape Breton, NS, Canada, 11–13 June 2001. [Google Scholar] [CrossRef]
- Han, S.; Nikou, S.; Yilma Ayele, W. Digital proctoring in higher education: A systematic literature review. Int. J. Educ. Manag. 2023, 38, 265–285. [Google Scholar] [CrossRef]

| Symbol | Description |
|---|---|
| A question plaintext | |
| A digital signature created by the user X, signing the listed data | |
| A digital signature created by the user X, signing all data listed before the signature | |
| A question package, which is a pair | |
| An attribute-based encryption of some plaintext with policy p | |
| A pseudonym of the user X | |
| T | A test created by the EA |
| A candidate’s solution to | |
| S | A candidate’s solution to T, built as a list of pairs |
| A timestamp created by the ABCA to the data | |
| An attribute-based credential of the user X | |
| A | An answer created by a candidate |
| A mark given by an examiner to | |
| A comment given by an examiner to | |
| A set of signed marks and comments to questions and solutions | |
| M | A mark package created by an examiner |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2024 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Vécsi, Á.; Pethő, A. Auditable Anonymous Electronic Examination. Cryptography 2024, 8, 19. https://doi.org/10.3390/cryptography8020019
Vécsi Á, Pethő A. Auditable Anonymous Electronic Examination. Cryptography. 2024; 8(2):19. https://doi.org/10.3390/cryptography8020019
Chicago/Turabian StyleVécsi, Ádám, and Attila Pethő. 2024. "Auditable Anonymous Electronic Examination" Cryptography 8, no. 2: 19. https://doi.org/10.3390/cryptography8020019
APA StyleVécsi, Á., & Pethő, A. (2024). Auditable Anonymous Electronic Examination. Cryptography, 8(2), 19. https://doi.org/10.3390/cryptography8020019







