A New Hybrid Automated Security Framework to Cloud Storage System
Abstract
1. Introduction
- The problem of CTP as it may convert into a vulnerable point inside the cloud environment.
- The problem of simple keys in the encryption process, which can be readily broken.
- The problem of easier data breaching when using one encryption scheme.
- Curbing the CTP functions and enhancing data privacy.
- Dividing the original data into blocks with random sizes.
- Generating random encryption keys equal to the number of data blocks.
- Encrypting the random encryption keys by both RSA and Twofish algorithms.
- Saving the keys encrypted by the RSA algorithm in a private Mongo DB to be used in the decryption process.
- Using the keys encrypted by the Twofish algorithm as keys to encrypt the original data.
- Encrypting the blocks of data by two novel approaches using AES and DES.
- Improved AES by using a dynamic S-box for each block in the ARC approach.
- Comparing the proposed approaches with other state-of-the-art encryption algorithms, such as DES, 3DES, and RC2.
2. Literature Reviews
- 1-
- Using a single algorithm (non-hybrid methodologies) is insufficient to provide high levels of security because, in symmetric algorithms, only one encryption key is used to encrypt and decrypt data [28].
- 2-
- The non-automated systems that use cloud third parties must ensure that this CTP is trustworthy and not turned into a malicious insider. This issue is challenging to be guaranteed in actual practices.
3. Materials and Methods
3.1. Twofish Algorithm
3.2. Rivest–Shamir–Adleman (RSA) Algorithm
- 1.
- Key generation: Select two separate prime numbers, N and M.
- 2.
- Calculate the value of which is the product of N and M.
- 3.
- Calculate the function of Euler’s totient φ by φ(L) = (N − 1) × (M − 1)
- 4.
- Find the value of , under this condition: φ(L) and (e,φ (L)) = 1
- 5.
- Calculate , where = (mod φ(L))
- 6.
- Use this equation for encryption:
- 7.
- Use this equation for decryption:
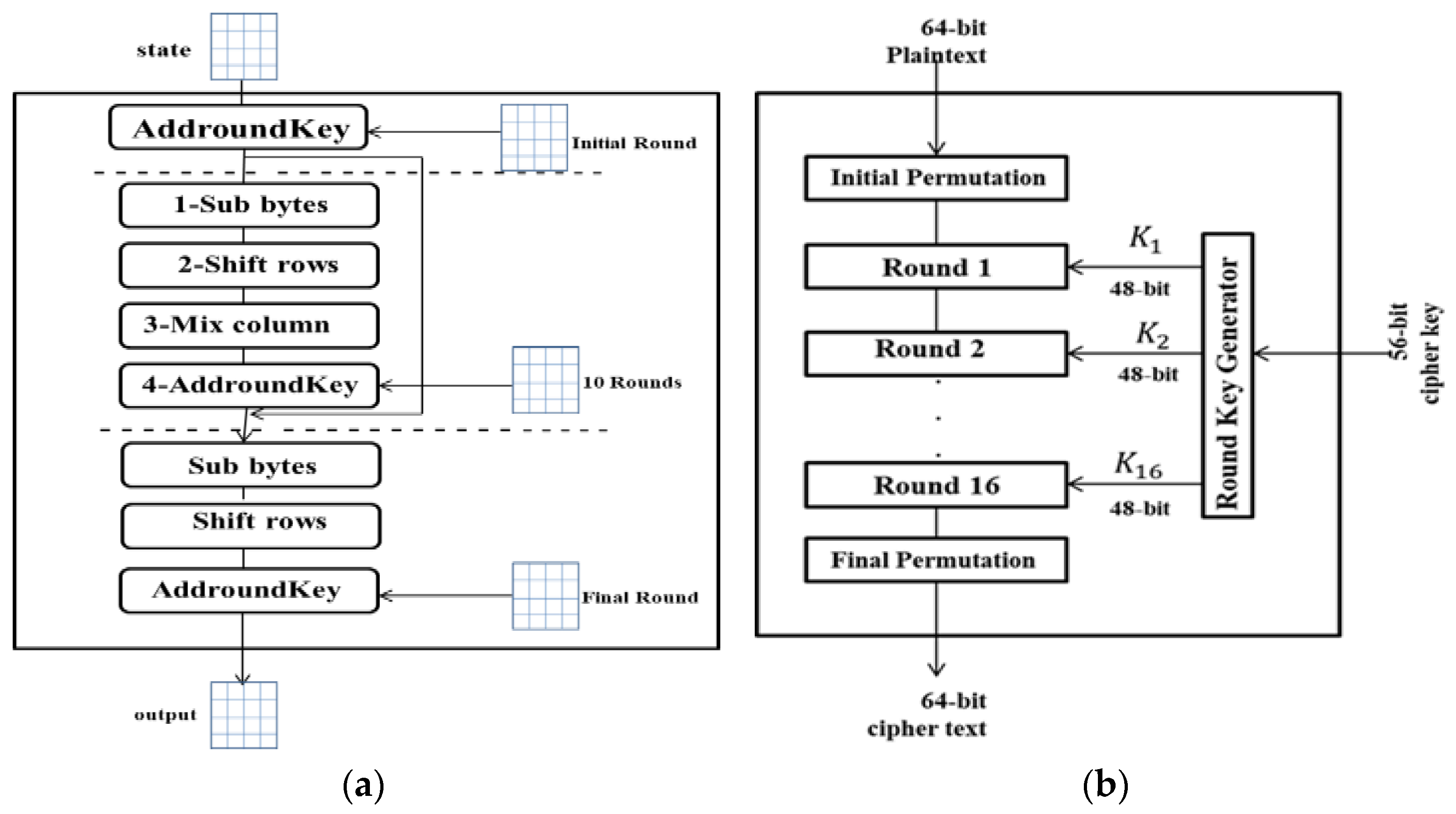
3.3. Advance Encryption Standard (AES) Algorithm
- Byte substitution: These operations are based on a substitution box (S-box) created, particularly for this purpose. This operation results in a four-by-four matrix for data.
- Shift Rows: All of the four rows of the matrix are shifted to the left, and any items dropped are re-inserted to the right side of the row.
- Mix Columns: A particular mathematical function is now used to alter each column of four bytes. This function takes four bytes from one column as input and returns four new bytes that replace the original column. As a result, a new matrix with 16 additional bytes is created. This stage is skipped in the final round.
- Addround Key: The 16 bytes of the four-by-four matrix are now treated as 128 bits, then they are XORed with the round key’s 128 bits. If this round is the last one, the output will be the ciphertext. Otherwise, the 128 bits are transformed into 16 bytes, and another round will begin [26,42]. Figure 1a shows the encryption process of the AES algorithm [43].
3.4. Data Encryption Standard (DES) Algorithm
- The 56-bit key is split into two parts, with 28 bits on the left and 28 on the right. These two parts are merged and compressed. Each half of the key is moved by one or two bits depending on the round. In this round, the plain text block is encrypted with a 48-bit compressed key.
- The 64-bit data are split into two halves, each of which is 32 bits long. The size of the block is increased to 48 bits by expanding one-half of the block. Then the output is XOR’ed with the compression key of 48 bits, which is produced in step 1.
- The output is passed to the S-box, which changes key bits and decreases the 48-bit block to 32-bit. The output of the S box is sent into the P-box, which permutes the bits. The two blocks are then switched and become the following round’s input. The key halves that were shifted in step 1 are applied [26]. Figure 1b shows the encryption process in the DES algorithm [44].
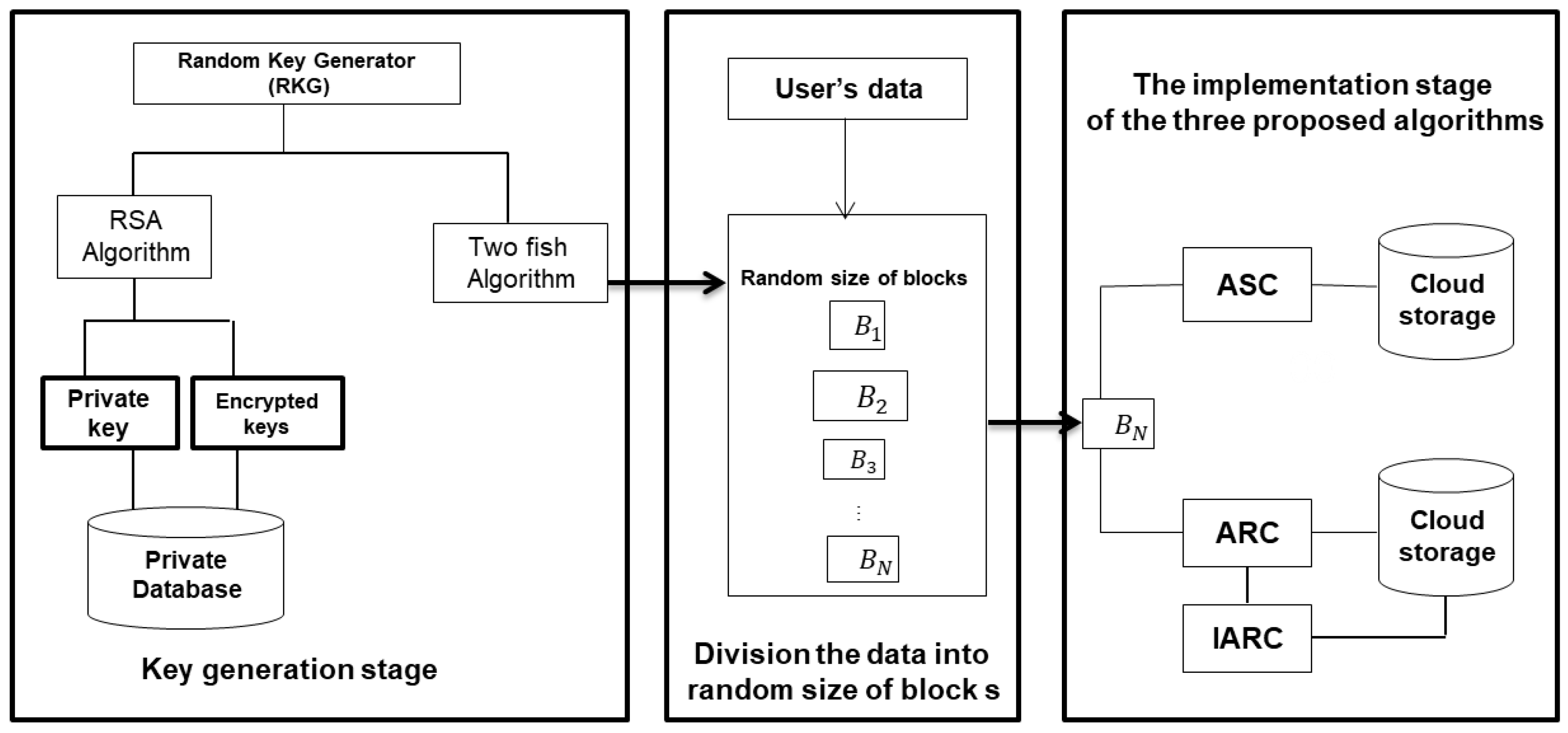
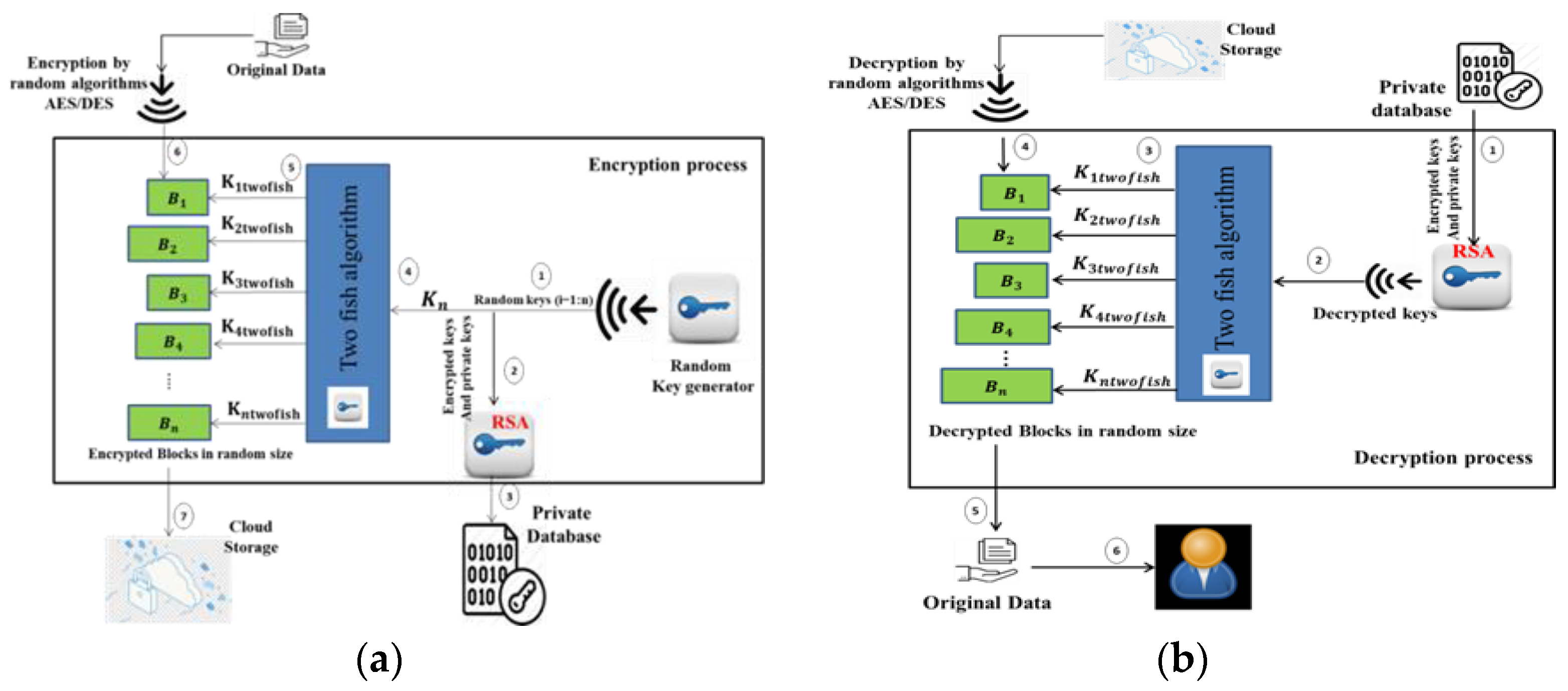
4. The Proposed Automated Encryption/Decryption System for Cloud Data Storage (AEDS)
- (1)
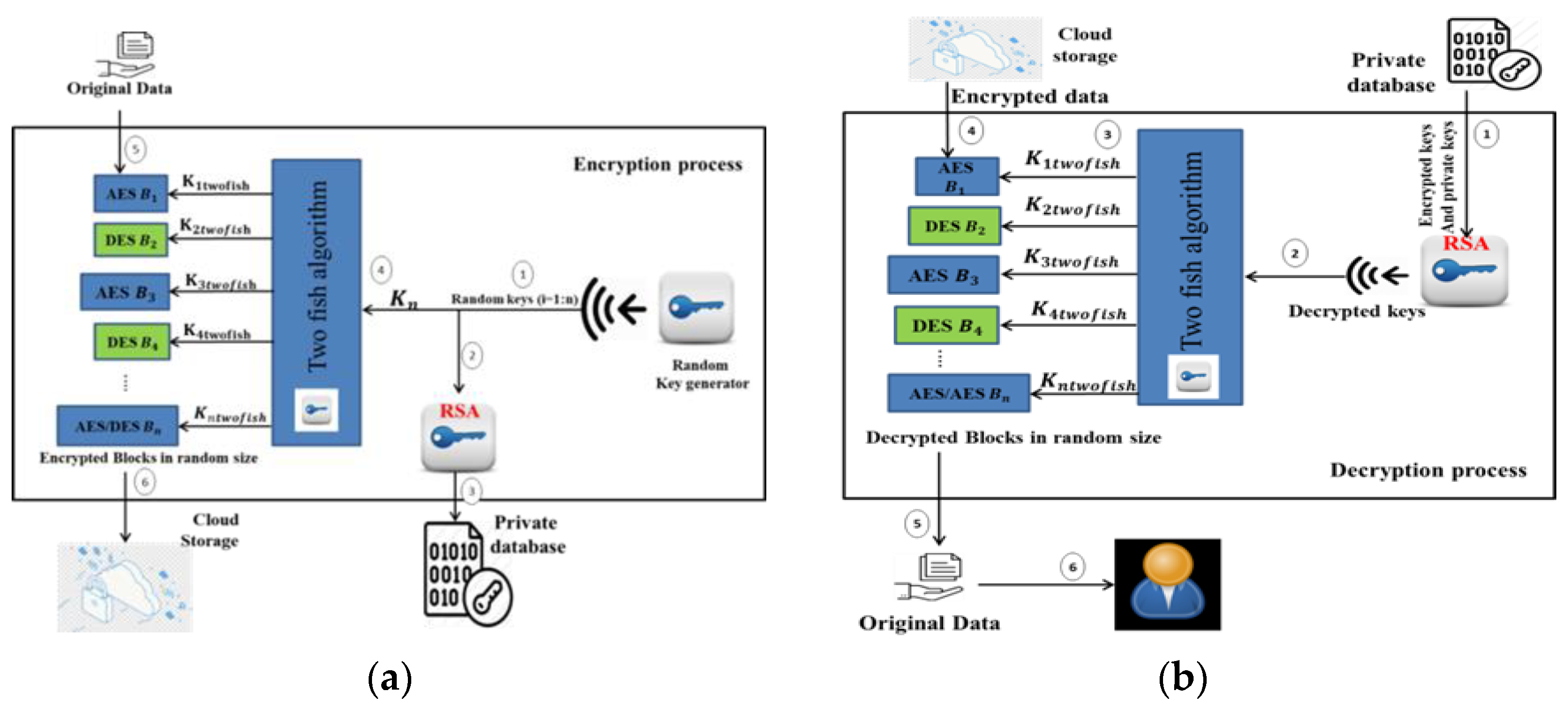
- The RSA algorithm is used to encrypt these generated random keys Ki producing ciphered keys Ki, RSA, and private key (p, L), which will be used latterly to decrypt Ki, RSA. Both the private key and ciphered keys Ki, RSA are stored in a private and secure database.
- (2)
- The Twofish algorithm is also used in encrypting these generated random keys. Still, here, the produced ciphered keys Ki, Twofish are used as encryption keys to encrypt the blocks of original data using the DES and AES algorithms consecutively using the ASC version or randomly in ARC or DARC. The main idea is that the system automatically disposes of the public key used in encrypting the random keys to keep these keys safe and away from unauthorized access. Finally, all the encrypted blocks are sent to the cloud storage, and they are now ready to be stored. Figure 4 displays a brief scenario for the data storage process based on the proposed ADES module. It is worth mentioning that the original data are divided into the random size of blocks by using Equation (1).where S is a random number [2:4], this interval is chosen for the following reasons:Blenght = 64 MB × S.
- If S < 2, the stored data will be much smaller than the usual block size, making the performance suffer drastically.
- If S > 4, the size of data blocks will be substantially larger than the standard block size, and therefore, it will take a long time to upload and process data.
4.1. Automated Sequential Cryptography (ASC) for Data Blocks
4.2. Automated Random Cryptography (ARC) for Data Blocks
| Algorithm 1: Encryption process. |
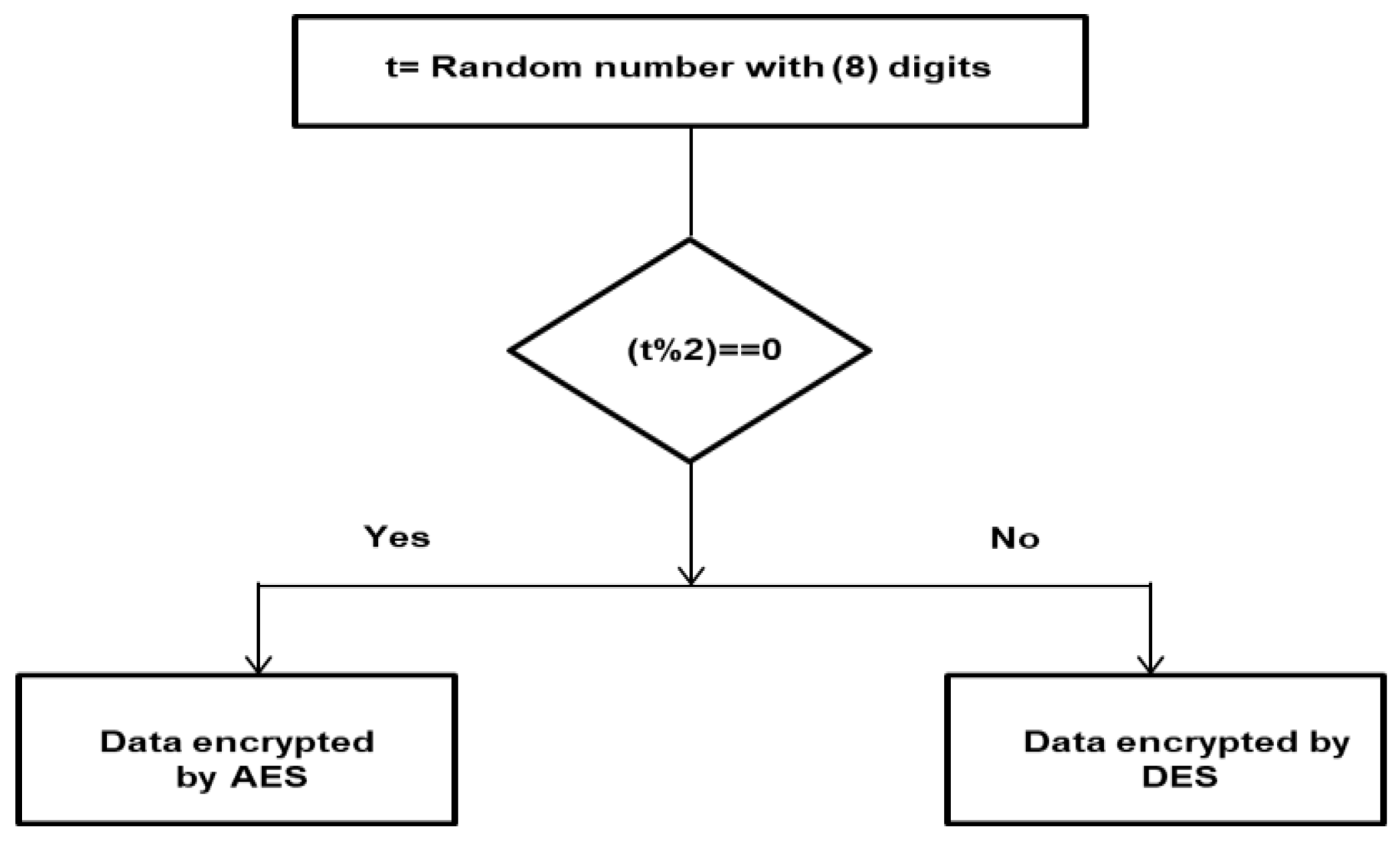
| Input: Plain text F, Random key Output: (encrypted text), private keys of RSA and (encrypted keys using RSA) Set Y = While (Y! = 0) do Set = 0, i = 1 as number of current block, While ( < Y) do Set t =0 /* in case of ASC encryption approach Generate t as a random number /* in case of ARC encryption approach Store t in the private database Generate 16-byte random key according to RKG function Use to encrypt the 16-byte random key Encrypt the same 16-byte random key by Store and the private key in the private database Use the encrypted 16-byte random key to encrypt blocks of data Determine random sizes of blocks according to Equation (1) For i = 1 to n Calculate the = While ( > Y) do = Y Read block data from file start at and end at If (t mod2==0) then Encrypt the block using AES algorithm by the Else Encrypt the block using DES algorithm by the End if t = t + 1 /* in case of ASC encryption approach Generate new t as a random number /* in case of ARC encryption approach Send the cipher block Ei and send it to cloud storage End For Set = End while End while Store the encrypted blocks of data Ei on the cloud storage, and store the private keys p and the encrypted keys by RSA Ki, RSA on a private database. |
| Algorithm 2: Decryption process. |
| Input: Encrypted blocks of data, (encrypted keys) and the private keys by RSA Output: The original file For i = 1 to n /* n is the number of ciphered blocks Select and the private keys p from the private database Decrypt using RSA decryption algorithm Read 16-byte of keys Encrypt the 16-byte keys using the Twofish algorithm Read the block from the cloud storage and read t from the private database If (t mod2==0) then Decrypt the Ei by the inverse of the AES algorithm by its Else Decrypt the ciphertext by the inverse DES algorithm by its Insert the decrypted block of data Bi in a file F End if End for |
4.3. Improved Automated Random Cryptography (IARC) for Data Blocks
| Algorithm 3: S-box without repetition process. |
| Input: S-box (t) value Output: S-box without repetition Set i = 0 countval= S-box.count(S-box (t)) while(countval >= 1)do i = i + 1 S-box (t) = S-box (t) + i while (S-box (t) >= 256) do S-box (t) = abs(S-box(t) − 256) Endwhile countval = S-box.count(S-box (t)) Endwhile |
5. Experiments and Results Analysis
5.1. Configuration of Open Nebula Cloud Simulator
5.2. Performance Evaluation Measures
- Time consumption for upload/retrieving files: is the time the system takes to send data from the user to the server and vice versa. Generally, the server’s speed controls the upload/retrieve time and is calculated by Equation (4) [49].
- Overall Processing time (PT): is the system’s total time for generating random keys and executing the encryption or decryption process. It could be calculated by Equation (5) [27].
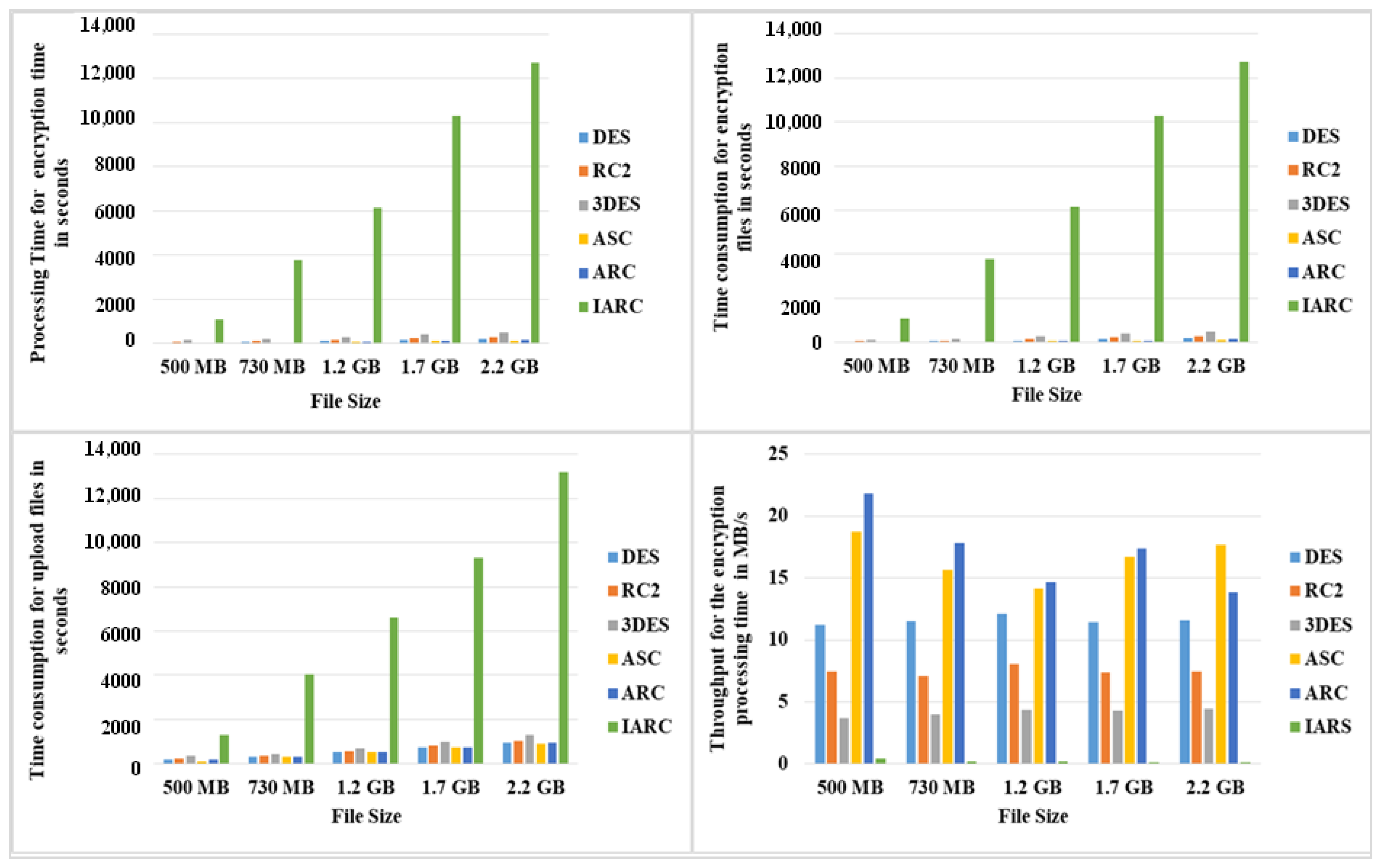
5.3. Discussion and Results Analysis
- Encryption of generated keys: Since the ACS, RCS, and IARC methods use two phases of encrypting the keys, the key generation procedure provides an efficient key generation process that helps resist brute-force assaults. One phase is used to encrypt the keys before encrypting the data, and another algorithm is used to safeguard the keys to be securely stored. Since the key generation technique is utilized in ACS and RCS methods, the security level will be enhanced.
- Hybrid approaches: To improve security, we have combined four algorithms Twofish, RSA, AES, and DES, in different manners according to the adopted approach.
- Improved approach: To increase the security and achieve high confidentiality, we used a dynamic S-box without repeating the AES algorithm in the IARC approach.
- Automated approach: All encryption and storage operations are carried out without intervention from the cloud third party or the user.
- Time complexity: Although the operations are complicated in the proposed approaches, the processing time is still acceptable.
- Storage: The ACS, RCS, and IARC approaches proposed appropriate cloud storage data since they use concealed encryption to secure access against malicious parties.
- Security: ACS, RCS, and IARC approaches are secure algorithms because of the complicated operation and substitution–permutation and Feistel structure.
6. Conclusions and Future Work
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Conflicts of Interest
Appendix A
| Abbreviation | Meaning |
|---|---|
| CTP | Cloud third party |
| AEDS | Automated Encryption/Decryption System for Cloud Data Storage |
| ASC | Automated Sequential Cryptography |
| ARC | Automated Random Cryptography |
| AES | Advance Encryption Standard |
| DES | Data Encryption Standard |
| RSA | Rivest–Shamir–Adleman |
| 3DES | Triple Data Encryption Standard |
| RC2 | ARC2 |
| IaaS | Infrastructure as a Service |
| PaaS | Platform as a Service |
| SaaS | Software as a Service |
| CSP | Cloud Service Provider |
| TTPA | Trusted Third-Party Auditor |
| CSS | Cloud Storage Server |
| TPA | Third-Party Auditor |
| TTP | Trusted Third Parties |
| MDS | Maximum Distance Separable |
| PHT | Pseudo-Hadamard Transform |
| RKG | Random Key Generator |
| EO | Encryption Operator |
| DO | Decryption Operator |
| DFS | Distributed File System |
| Symbol | Meaning |
|---|---|
| N and M | prime numbers as random |
| φ | the function of Euler’s totient |
| cipher data | |
| original data | |
| public key | |
| the private key | |
| Ki | Random key |
| Ki, RSA | Encrypted keys using RSA |
| Ki, Twofish | Encrypted key using Twofish |
| The size of the block | |
| S | random number [2:4] |
| T | Time consumption for encryption/decryption files |
| PT | Overall Processing time |
References
- Mall, S.; Saroj, S.K. A new security framework for cloud data. In Proceedings of the International Conference on Advances in Computing and Communications, Kochi, India, 19–22 September 2018; Volume 143, pp. 765–775. [Google Scholar] [CrossRef]
- Dhanapal, R.; Tharageswari, K.; Karthik, S. A decentralized accountability framework for enhancing secure data sharing through ICM in cloud. Innov. Technol. Explor. Eng. 2019, 8, 1505–1511, ISSN 2278-3075. [Google Scholar] [CrossRef]
- Shahzadi, S.; Iqbal, M.; Qayyum, Z.U.; Dagiuklas, T. Infrastructure as a service (IaaS): A comparative performance analysis of open-source cloud platforms. In Proceedings of the International Workshop on Computer Aided Modeling and Design of Communication Links and Networks, Lund, Sweden, 19–21 June 2017; pp. 1–6. [Google Scholar] [CrossRef]
- Jathanna, R.; Jagli, D. Cloud Computing and security issues. Int. J. Eng. Res. Appl. 2017, 7, 31–38, ISSN 2248-9622. [Google Scholar] [CrossRef]
- Kulkarni, G.; Waghmare, R.; Palwe, R.; Waykule, V.; Bankar, H. Cloud storage architecture. In Proceedings of the International Conference on Telecommunication Systems, Services, and Applications, Denpasar-Bali, Indonesia, 30–31 October 2012; pp. 76–81. [Google Scholar] [CrossRef]
- Vurukonda, N.; Rao, B.T. A Study on data storage security issues in cloud computing. In Proceedings of the Inernational Conference on Intelligent Computing, Communications & Convergence, Odisha, India, 24–25 January 2016; Volume 92, pp. 128–135. [Google Scholar] [CrossRef]
- Bentajer, A.; Hedabou, M.; Abouelmehdi, K.; Elfezazi, S. CS-IBE: A data confidentiality system in a public cloud storage system. Procedia Comput. Sci. 2018, 141, 559–564. [Google Scholar] [CrossRef]
- Tawalbeh, L.A.; Saldamli, G. Reconsidering big data security and privacy in cloud and mobile cloud systems. Comput. Inf. Sci. 2019, 33, 810–819. [Google Scholar] [CrossRef]
- Das, D. Secure cloud computing algorithm using homomorphic encryption and multi-party computation. In Proceedings of the International Conference on Information Networking, Chiang Mai, Thailand, 10–12 January 2018; Volume 1, pp. 391–396. [Google Scholar] [CrossRef]
- Mohta, A.; Awasthi, L.K. Cloud data security while using third-party auditor. Sci. Eng. Res. 2012, 3, 1–9, ISSN 2229-5518. [Google Scholar]
- Yusop, Z.M.; Abawajy, J.H. Analysis of insiders attack mitigation strategies. Procedia-Soc. Behav. Sci. 2014, 129, 611–618. [Google Scholar] [CrossRef]
- Singh, S.; Thokchom, S. Public integrity auditing for shared dynamic cloud data. In Proceedings of the International Conference on Smart Computing and Communications, Kurukshetra, India, 7–8 December 2018; Volume 125, pp. 698–708. [Google Scholar] [CrossRef]
- Potey, M.M.; Dhote, C.A.; Sharma, D.H. Homomorphic encryption for security of cloud data. In Proceedings of the International Conference on Communication, Computing and Virtualization, Mumbai, India, 26–27 February 2016; Volume 79, pp. 175–181. [Google Scholar] [CrossRef]
- El-Attar, N.E.; Awad, W.A.; Omara, F.A. Empirical assessment for security risk and availability in public cloud frameworks. In Proceedings of the International Conference on Computer Engineering & Systems, Cairo, Egypt, 20–21 December 2016; pp. 17–25. [Google Scholar] [CrossRef]
- El Makkaoui, K.; Ezzati, A.; Beni-Hssane, A.; Ouhmad, S. A swift Cloud-Paillier scheme to protect sensitive data confidentiality in cloud computing. In Proceedings of the International Conference on Mobile Systems and Pervasive Computing, Gran Canaria, Spain, 13–15 August 2018; Volume 134, pp. 83–90. [Google Scholar] [CrossRef]
- Chakraborty, S.; Singh, S.; Thokchom, S. Integrity Checking using third party auditor in cloud storage. In Proceedings of the International Conference on Contemporary Computing, Noida, India, 2–4 August 2018; pp. 1–6. [Google Scholar] [CrossRef]
- Nadlamani, G.F.; Shaikh, S. Preserving privacy using TPA for cloud storage based on regenerating code. In Proceedings of the International Conference on Recent Trends in Information Technology, Chennai, India, 8–9 April 2016; pp. 1–5. [Google Scholar] [CrossRef]
- More, S.; Chaudhari, S. Third party public auditing scheme for cloud storage. In Proceedings of the International Conference on Communication, Computing and Virtualization, Mumbai, India, 26–27 February 2016; Volume 79, pp. 69–76. [Google Scholar] [CrossRef]
- Singh, A.P.; Pasupuleti, S.K. Optimized Public auditing and data dynamics for data storage security in cloud computing. In Proceedings of the International Conference on Advances In Computing & Communications, Cochin, India, 6–8 September 2016; Volume 93, pp. 751–759. [Google Scholar] [CrossRef]
- Ferhat, O.C.; Ahmet, F.M. CPP-ELM: Cryptographically Privacy-Preserving Extreme Learning Machine for Cloud Systems. Int. J. Comput. Intell. Syst. 2018, 11, 33–44. [Google Scholar] [CrossRef]
- Saxena, R.; Dey, S. Cloud Audit: A Data Integrity verification approach for cloud computing. Procedia Comput. Sci. 2016, 89, 142–151. [Google Scholar] [CrossRef][Green Version]
- Adokshaja, B.L.; Saritha, S.J. Third-party public auditing on cloud storage using the cryptographic algorithm. In Proceedings of the International Conference on Energy, Communication, Data Analytics and Soft Computing, Chennai, India, 1–2 August 2017; pp. 3635–3638. [Google Scholar] [CrossRef]
- Akhil, K.M.; Kumar, M.P.; Pushpa, B.R. Enhanced cloud data security using AES algorithm. In Proceedings of the International Conference on Intelligent Computing and Control, Coimbatore, India, 14–15 June 2018; pp. 1–5. [Google Scholar] [CrossRef]
- Sivakumar, P.; NandhaKumar, M.; Jayaraj, R.; Kumaran, A.S. Securing Data and Reducing the Time Traffic Using AES Encryption with Dual Cloud. In Proceedings of the International Conference on System, Computation, Automation and Networking, Pondicherry, India, 29–30 March 2019; pp. 1–5. [Google Scholar] [CrossRef]
- Orobosade, A.; Favour-Bethy, T.A.; Kayode, A.B.; Gabriel, A.J. Cloud Application Security using Hybrid Encryption. Commun. Appl. Electron. 2020, 7, 25–31, ISSN 2394-4714. [Google Scholar] [CrossRef]
- Sohal, M.; Sharma, S. BDNA-A DNA inspired symmetric key cryptographic technique to secure cloud computing. Comput. Inf. Sci. 2018, 1–8. [Google Scholar] [CrossRef]
- Thabit, F.; Alhomdy, S.; Al-Ahdal, H.A.; Jagtap, S. A new lightweight cryptographic algorithm for enhancing data security in cloud computing. Glob. Transit. Proc. 2021, 2, 91–99. [Google Scholar] [CrossRef]
- Maitri, P.V.; Verma, A. Secure file storage in cloud computing using hybrid cryptography algorithm. In Proceedings of the International Conference on Wireless Communications, Signal Processing and Networking, Chennai, India, 23–25 March 2016; pp. 1635–1638. [Google Scholar] [CrossRef]
- Hoomod, H.K.; Hussein, A.M. New Modified Twofish for Data Protection Using Salsa20 and Lü system. In Proceedings of the International Conference on Intelligent Computing and Control Systems, Madurai, India, 15–17 May 2019; pp. 1189–1195. [Google Scholar] [CrossRef]
- Zodpe, H.; Sapkal, A. An efficient AES implementation using FPGA with enhanced security features. Eng. Sci. 2020, 32, 115–122. [Google Scholar] [CrossRef]
- Xu, X.; Tian, N. The search and improvement of DES algorithm for data transmission security in SCADA. In Proceedings of the International Conference on Intelligent Computing, Automation and Systems, Chongqing, China, 29–31 December 2019; pp. 275–279. [Google Scholar] [CrossRef]
- Malgari, V.; Dugyala, R.; Kumar, A. A Novel Data Security Framework in Distributed Cloud Computing. In Proceedings of the International Conference on Image Information Processing, Shimla, India, 15–17 November 2019; pp. 373–378. [Google Scholar] [CrossRef]
- Gupta, P.; Kumar, D.; Kumar Singh, A. Improving RSA Algorithm Using Multi-Threading Model for Outsourced Data Security in Cloud Storage. In Proceedings of the International Conference on Cloud Computing, Data Science & Engineering, Noida, India, 11–12 January 2018; pp. 14–15. [Google Scholar] [CrossRef]
- Jintcharadze, E.; Iavich, M. Hybrid implementation of twofish, AES, ElGamal, and RSA cryptosystems. In Proceedings of the IEEE East-West Design & Test Symposium, Varna, Bulgaria, 4–7 September 2020; pp. 1–5. [Google Scholar] [CrossRef]
- Ramtri, G.; Patel, C. Secure banking transactions using RSA and two fish algorithms. In Proceedings of the International Conference on Emerging Trends in Information Technology and Engineering, Vellore, India, 24–25 February 2020; pp. 1–5. [Google Scholar] [CrossRef]
- Hemanth, P.N.; Abhinay Raj, N.; Yadav, N. Secure message transfer using RSA algorithm and improved Playfair cipher in cloud computing. In Proceedings of the International Conference for Convergence in Technology, Mumbai, India, 7–9 April 2017; pp. 931–936. [Google Scholar] [CrossRef]
- Mehmood, M.S.; Shahid, M.R.; Jamil, A.; Ashraf, R.; Mahmood, T. A comprehensive literature review of data encryption techniques in cloud computing and IoT environment. In Proceedings of the International Conference on Information and Communication Technologies, Karachi, Pakistan, 16–17 November 2019; pp. 54–59. [Google Scholar] [CrossRef]
- Mittal, S.; Arora, S.; Jain, R. PData security using RSA encryption combined with image steganography. In Proceedings of the International Conference on Information Processing, Delhi, India, 21–23 December 2017; pp. 1–5. [Google Scholar] [CrossRef]
- Panda, M. Performance analysis of encryption algorithms for security. In Proceedings of the International Conference on Signal Processing, Communication, Power and Embedded System, Paralakhemundi, India, 3–5 October 2016; pp. 278–284. [Google Scholar] [CrossRef]
- Rani, K.; Sagar, R.K. Enhanced data storage security in cloud environment using encryption, compression asplitting technique. In Proceedings of the International Conference on Telecommunication and Networks, Noida, India, 10–11 August 2017; pp. 1–5. [Google Scholar] [CrossRef]
- Jayant, B.; Swapnaja, U.; Subhash, P.; Kailash, K.; Sulabha, A. Developing secure cloud storage system by applying AES and RSA cryptography algorithms with role-based access control model. Comput. Appl. 2015, 118, 46–52. [Google Scholar] [CrossRef][Green Version]
- Ametepe, A.F.; Ahouandjinou, S.A.; Ezin, E.C. Secure encryption by combining asymmetric and symmetric cryptographic method for data collection WSN in smart agriculture. In Proceedings of the International Smart Cities Conference, Casablanca, Morocco, 14–17 October 2019; pp. 93–99. [Google Scholar] [CrossRef]
- Fauziah, N.A.; Rachmawanto, E.H.; Moses Setiadi, D.; Sari, C.A. Design and implementation of AES and SHA-256 cryptography for securing multimedia file over android chat application. In Proceedings of the International Seminar on Research of Information Technology and Intelligent Systems, Yogyakarta, Indonesia, 21–22 November 2018; pp. 146–151. [Google Scholar] [CrossRef]
- Shivhare, R.; Shrivastava, R.; Gupta, C. An enhanced image encryption technique using DES algorithm with random image overlapping and random key generation. In Proceedings of the International Conference on Advanced Computation and Telecommunication, Bhopal, India, 28–29 December 2018; pp. 1–9. [Google Scholar] [CrossRef]
- Yassein, M.B.; Aljawarneh, S.; Qawasmeh, E.; Mardini, W.; Khamayseh, Y. Comprehensive study of symmetric key and asymmetric key encryption algorithms. In Proceedings of the International Conference on Engineering and Technology, Antalya, Turkey, 21–23 August 2017; pp. 1–7. [Google Scholar] [CrossRef]
- Subandri, M.A.; Cyclomatic, R.S. Complexity for Determining Product Complexity Level in COCOMO II. In Proceedings of the Information Systems International Conference, Denpasar-Bali, Indonesia, 6–8 November 2017; Volume 124, pp. 478–486. [Google Scholar] [CrossRef]
- Reddy, I.R.; Murali, G. A novel triple DES to enhance e-governance security. In Proceedings of the International Conference on Energy, Communication, Data Analytics and Soft Computing, Chennai, India, 1–2 August 2017; pp. 2443–2446. [Google Scholar] [CrossRef]
- Charbathia, S.; Sharma, S. A comparative study of rivest cipher algorithms. Inf. Comput. Technol. 2014, 4, 1831–1838, ISSN 0974-2239. [Google Scholar]
- Malviya, S.; Dave, S. Secure data sharing scheme using cryptographic algorithm for cloud storage. Appl. Eng. Res. 2018, 13, 14799–14805, ISSN 0973-4562. [Google Scholar]
- Srilaya, S.; Velampalli, S. Performance Evaluation for DES and AES Algorithms—An Comprehensive Overview. In Proceedings of the International Conference on Recent Trends in Electronics, Information & Communication Technology, Bangalore, India, 18–19 May 2018. [Google Scholar] [CrossRef]

| Ref. | Algorithms Used | Hybrid Approach | Automated Approach | CTP | Calculate Processing Time | Lightweight | Split the Data | Calculate Throughput | |
|---|---|---|---|---|---|---|---|---|---|
| Equal Size | Random Size | ||||||||
| [16] | AES | √ | √ | ||||||
| [17] | AES | √ | √ | ||||||
| [18] | AES, RSA digital signature and SHA-2 | √ | √ | √ | |||||
| [19] | Chameleon Authentication Tree and Homomorphic Linear Authenticators | √ | √ | √ | |||||
| [20] | Paillier Homomorphic Encryption | √ | √ | ||||||
| [21] | Paillier Homomorphic Cryptography | √ | √ | √ | |||||
| [22] | AES | √ | √ | ||||||
| [23] | AES | √ | |||||||
| [24] | AES | √ | |||||||
| [25] | AES and ECC | √ | √ | ||||||
| [26] | DNA | √ | √ | √ | √ | ||||
| [27] | NLCA | √ | √ | ||||||
| The current work | RSA, AES, DES, and Twofish | √ | √ | √ | √ | √ | √ | ||
| Parameter | Description |
|---|---|
| Blocks of data | |
| Random key | |
| F | Plain text file |
| The size of the file | |
| the start of each block | |
| the end of each block | |
| Encrypted key using Twofish | |
| Ki, RSA | Encrypted key using RSA |
| Encrypted block | |
| Number of checks of repetition | |
| Countval | Number of repetitions |
| S-box (t) | The value of each place |
| Algorithm | NLOC | Avg. NLOC | Avg. Token | Function Count | AvgCCN |
|---|---|---|---|---|---|
| ARC | 826 | 22.9 | 185.2 | 33 | 1.5 |
| ASC | 805 | 22.4 | 180.9 | 33 | 1.4 |
| IARC | 822 | 22.8 | 183.1 | 33 | 1.5 |
| Hostname | Master. Hadoop. Lan | Node1 | Node2 |
|---|---|---|---|
| Decommission Status | Normal | Normal | Normal |
| Configured capacity | 30.19 GB | 25.19 GB | 25.09 GB |
| DFS Used | 15.9 GB | 15.9 GB | 15.9 GB |
| Non DFS Used | 8.48 GB | 7.04 GB | 7.08 GB |
| DFS Remaining | 5.81 GB | 2.25 GB | 2.11 GB |
| DFS Remaining% | 19.24% | 8.93% | 8.41% |
| DFS used% | 52.67% | 63.12% | 63.37% |
| Cache used% | 100% | 100% | 100% |
| File Size | The Overall Time of Encryption Process/s | The Overall Time Decryption Process/s | ||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|
| DES | RC2 | 3DES | ASC | ARC | IARC | DES | RC2 | 3DES | ASC | ARC | IARC | |
| 500 MB | 44.69 | 67.27 | 136.18 | 26.70 | 22.90 | 1092.41 | 115.22 | 139.43 | 243.04 | 103.26 | 101.27 | 1162.13 |
| 730 MB | 63.24 | 102.81 | 182.84 | 46.72 | 40.99 | 3782.78 | 175.37 | 210.81 | 303.29 | 161.20 | 158.45 | 3972.41 |
| 1.2 GB | 101.68 | 152.53 | 279.97 | 86.91 | 83.79 | 6157.41 | 285.36 | 325.95 | 469.01 | 264.63 | 267.36 | 6484.52 |
| 1.7 GB | 152.50 | 236.39 | 406.76 | 104.05 | 100.24 | 1029.16 | 406.74 | 487.70 | 668.14 | 379.95 | 425.32 | 11,320.09 |
| 2.2 GB | 194.00 | 302.07 | 509.57 | 127.37 | 162.76 | 12,702.62 | 521.86 | 620.32 | 831.47 | 465.63 | 486.22 | 14,195.37 |
| File Size | Time for Encrypting a File/s | Time for Decryption a File/s | ||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|
| DES | RC2 | 3DES | ASC | ARC | IARC | DES | RC2 | 3DES | ASC | ARC | IARC | |
| 500 MB | 44.43 | 66.91 | 135.65 | 26.41 | 22.58 | 1092.10 | 42.84 | 63.55 | 139.93 | 25.86 | 21.27 | 1082.47 |
| 730 MB | 63.11 | 102.62 | 182.33 | 46.29 | 40.47 | 3783.11 | 61.26 | 98.39 | 178.10 | 45.13 | 39.55 | 3637.41 |
| 1.2 GB | 101.30 | 151.84 | 279.41 | 86.48 | 83.17 | 6157.113 | 103.17 | 151.88 | 284.64 | 74.83 | 82.73 | 6057.11 |
| 1.7 GB | 151.68 | 235.78 | 406.10 | 103.20 | 99.70 | 10,293.96 | 148.07 | 229.56 | 397.59 | 102.45 | 94.40 | 10,211.38 |
| 2.2 GB | 193.30 | 301.02 | 508.65 | 126.81 | 161.43 | 12,702.17 | 185.38 | 293.27 | 504.15 | 120.35 | 156.60 | 11,801.31 |
| File Size | Time for Uploading a File/s | Time for Retrieving a File/s | ||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|
| DES | RC2 | 3DES | ASC | ARC | IARC | DES | RC2 | 3DES | ASC | ARC | IARC | |
| 500 MB | 220.09 | 247.90 | 359.62 | 137.14 | 208.97 | 1285.33 | 115.56 | 139.79 | 243.78 | 103.65 | 101.41 | 1163.57 |
| 730 MB | 324.31 | 364.12 | 463.90 | 316.50 | 326.18 | 4053.67 | 175.90 | 211.30 | 303.84 | 161.67 | 159.07 | 3297.32 |
| 1.2 GB | 528.33 | 575.33 | 718.65 | 566.50 | 534.48 | 6601.83 | 286.38 | 327.29 | 469.96 | 265.65 | 266.33 | 5229.31 |
| 1.7 GB | 768.27 | 850.46 | 1026.68 | 745.61 | 747.32 | 9318.29 | 408.43 | 489.39 | 669.88 | 387.36 | 427.82 | 8030.57 |
| 2.2 GB | 977.90 | 1066.20 | 1291.87 | 937.36 | 966.01 | 13,195.55 | 524.35 | 622.51 | 831.47 | 468.13 | 488.45 | 11,059.28 |
| File Size | Throughput for the Encryption Process | Throughput for the Decryption Process | ||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|
| DES | RC2 | 3DES | ASC | ARC | IARC | DES | RC2 | 3DES | ASC | ARC | IARC | |
| 500 MB | 11.19 | 7.43 | 3.67 | 18.72 | 21.83 | 0.46 | 4.33 | 3.59 | 2.06 | 4.84 | 4.94 | 0.43 |
| 730 MB | 11.54 | 7.10 | 3.99 | 15.62 | 17.81 | 0.19 | 4.16 | 3.46 | 2.40 | 4.52 | 4.61 | 0.18 |
| 1.2 GB | 12.08 | 8.06 | 4.39 | 14.14 | 14.67 | 0.20 | 4.31 | 3.77 | 2.62 | 4.64 | 4.6 | 0.11 |
| 1.7 GB | 11.42 | 7.36 | 4.28 | 16.73 | 17.37 | 0.17 | 4.28 | 3.57 | 2.61 | 4.58 | 4.09 | 0.15 |
| 2.2 GB | 11.61 | 7.46 | 4.42 | 17.69 | 13.84 | 0.18 | 4.32 | 3.63 | 2.71 | 4.84 | 4.63 | 0.16 |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2021 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
El-Attar, N.E.; El-Morshedy, D.S.; Awad, W.A. A New Hybrid Automated Security Framework to Cloud Storage System. Cryptography 2021, 5, 37. https://doi.org/10.3390/cryptography5040037
El-Attar NE, El-Morshedy DS, Awad WA. A New Hybrid Automated Security Framework to Cloud Storage System. Cryptography. 2021; 5(4):37. https://doi.org/10.3390/cryptography5040037
Chicago/Turabian StyleEl-Attar, Noha E., Doaa S. El-Morshedy, and Wael A. Awad. 2021. "A New Hybrid Automated Security Framework to Cloud Storage System" Cryptography 5, no. 4: 37. https://doi.org/10.3390/cryptography5040037
APA StyleEl-Attar, N. E., El-Morshedy, D. S., & Awad, W. A. (2021). A New Hybrid Automated Security Framework to Cloud Storage System. Cryptography, 5(4), 37. https://doi.org/10.3390/cryptography5040037






