SC-DDPL as a Countermeasure against Static Power Side-Channel Attacks
Abstract
:1. Introduction
- We validate the robustness of the TEL protocol to static power analysis, according to Bellizia et al. [14].
- We validate the SC-DDPL as an effective countermeasure to this kind of attacks by means of a full set of experimental results on a reprogrammable device.
2. Review of Attacks Exploiting Static Power
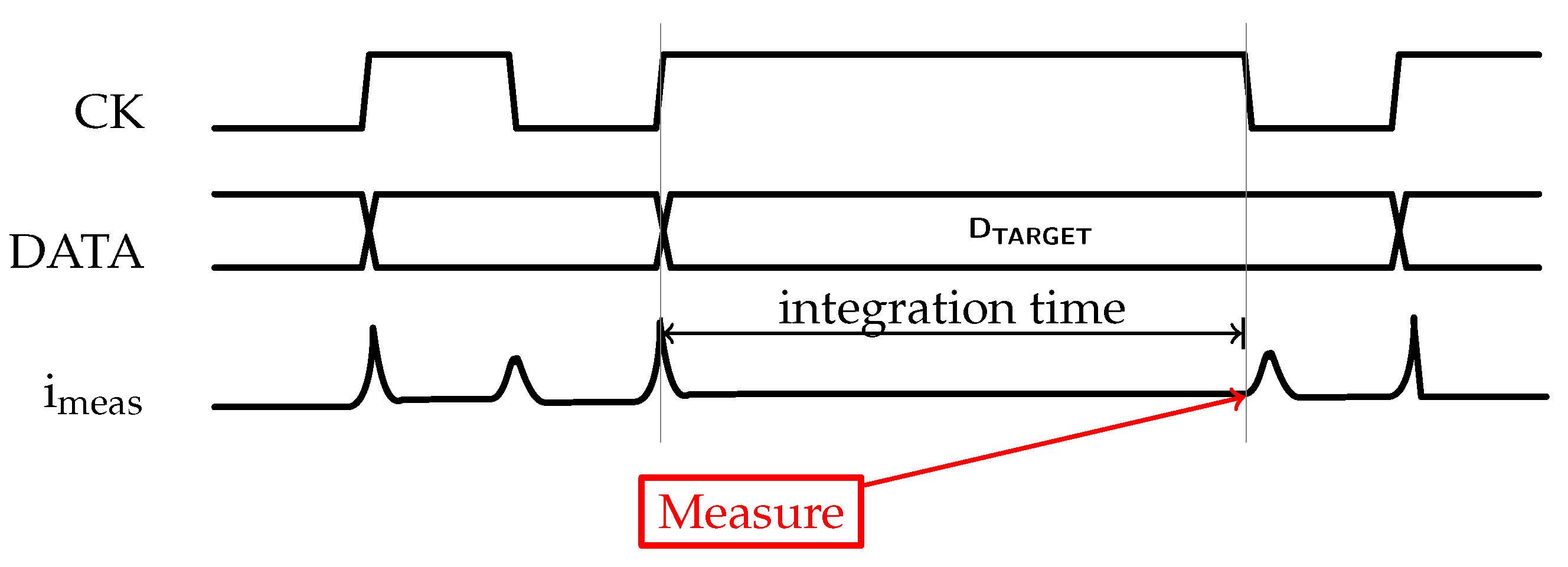
2.1. Threat Model
2.2. Related Works on AESP
2.3. Security Metrics
3. TEL Protocol and SC-DDPL
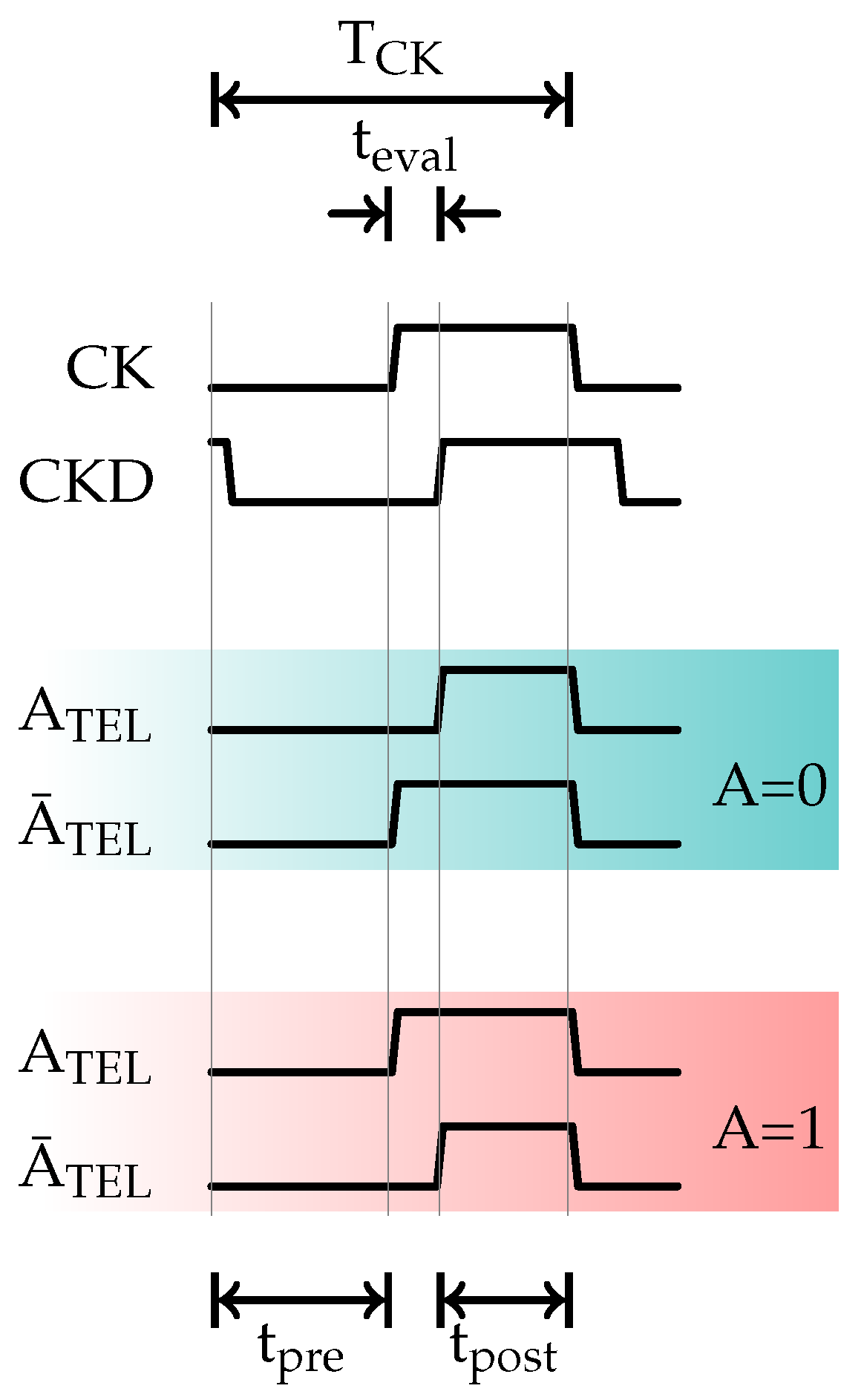
3.1. TEL Protocol
- Pre-charge phase (): Both wires are pre-charged to 0.
- Post-charge phase (): Both wires reach VDD and keep this level to the end of the clock period.
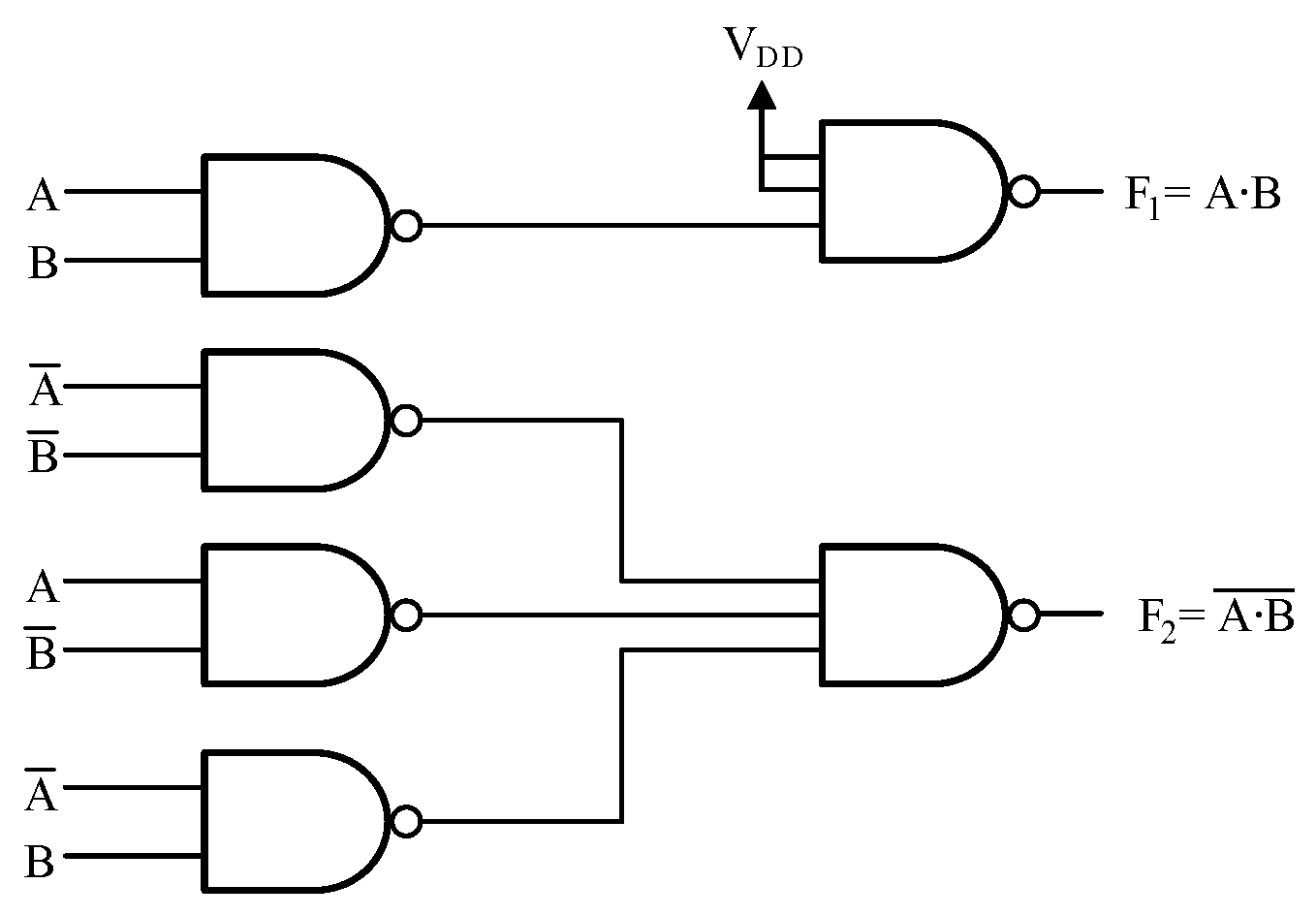
3.2. SC-DDPL Operation
3.3. SC-DDPL Effectiveness against AESP
4. Experimental Results
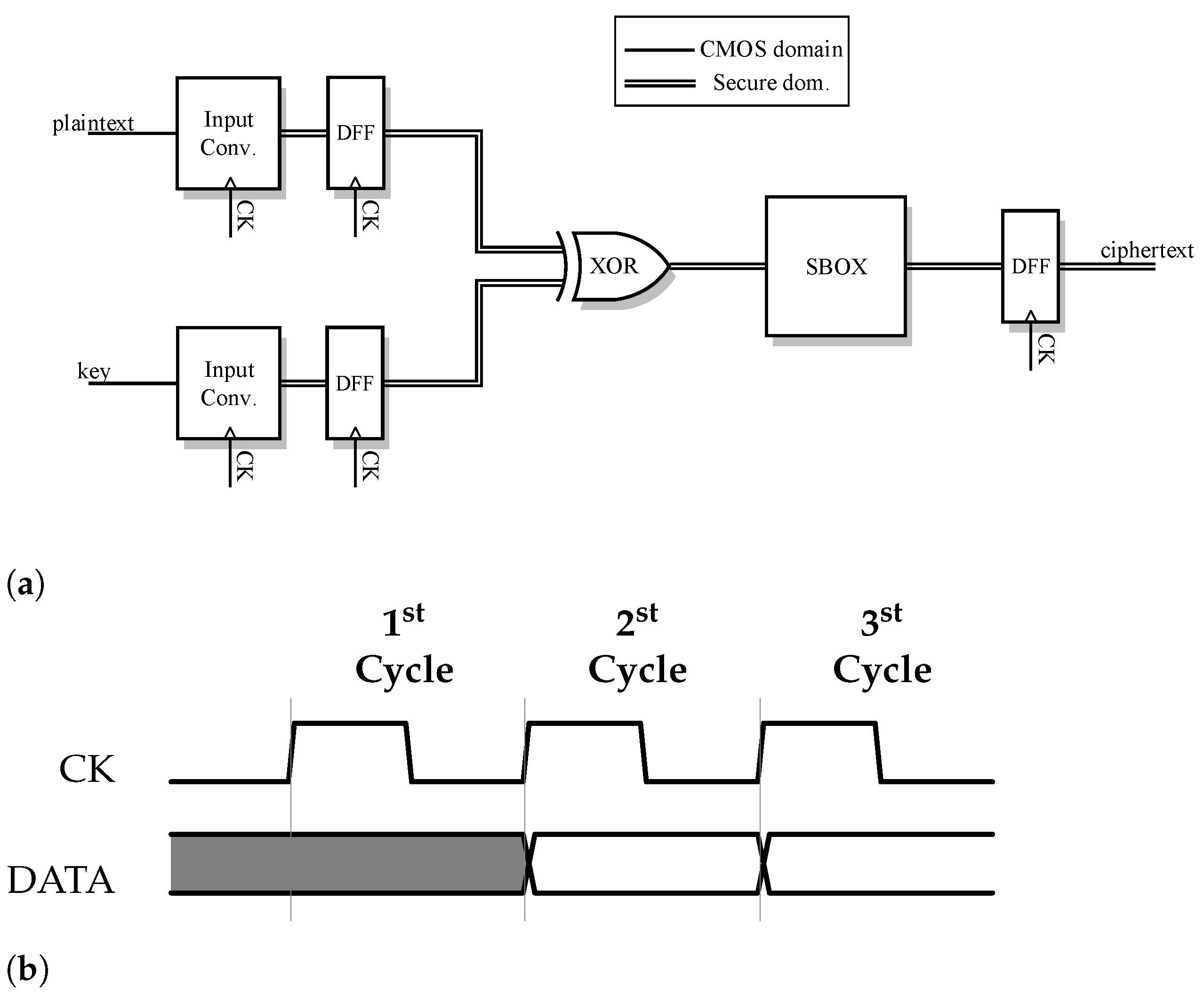
4.1. Case Study — 4-bit PRESENT Crypto-Core
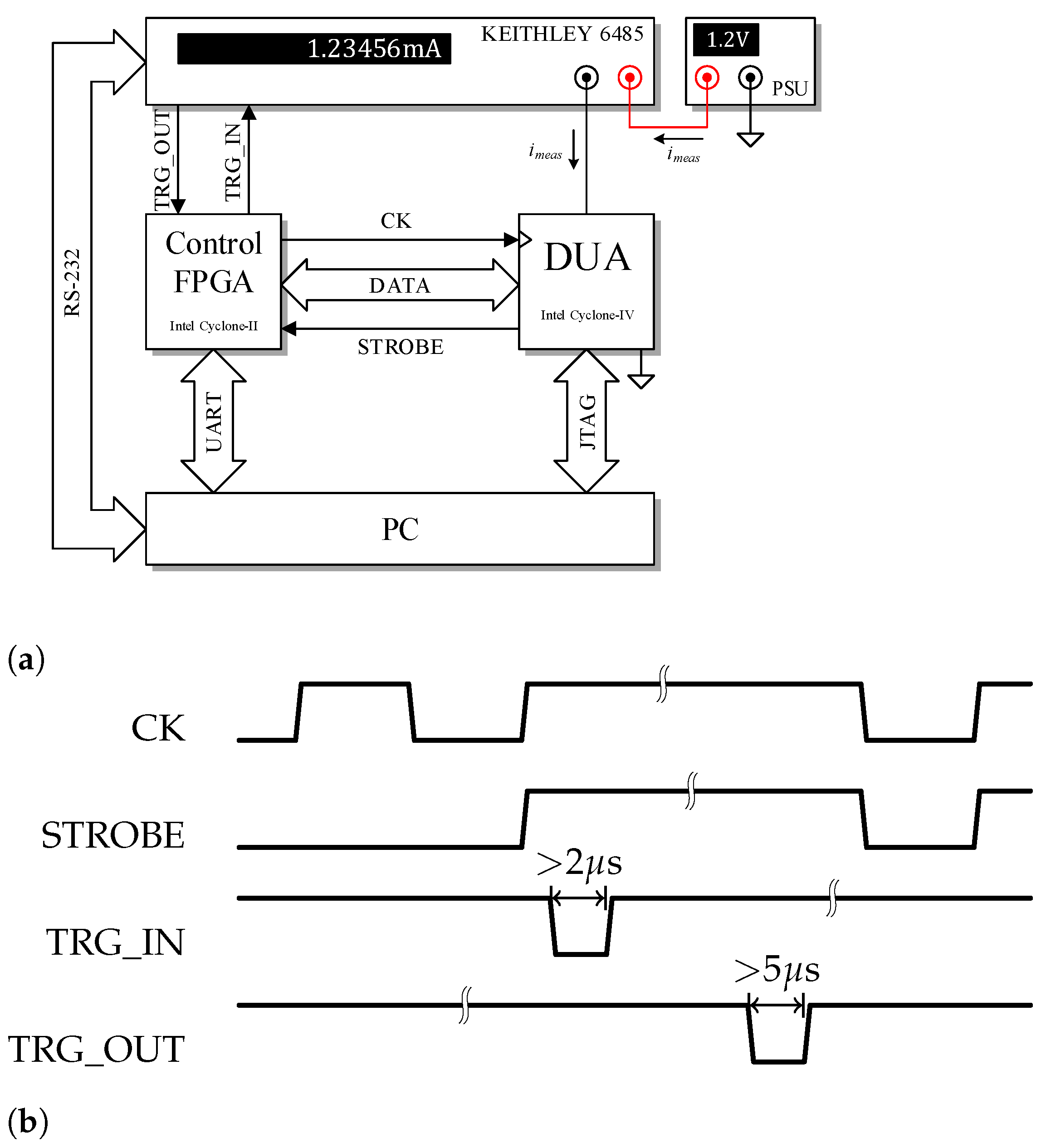
4.2. Measurement Setup
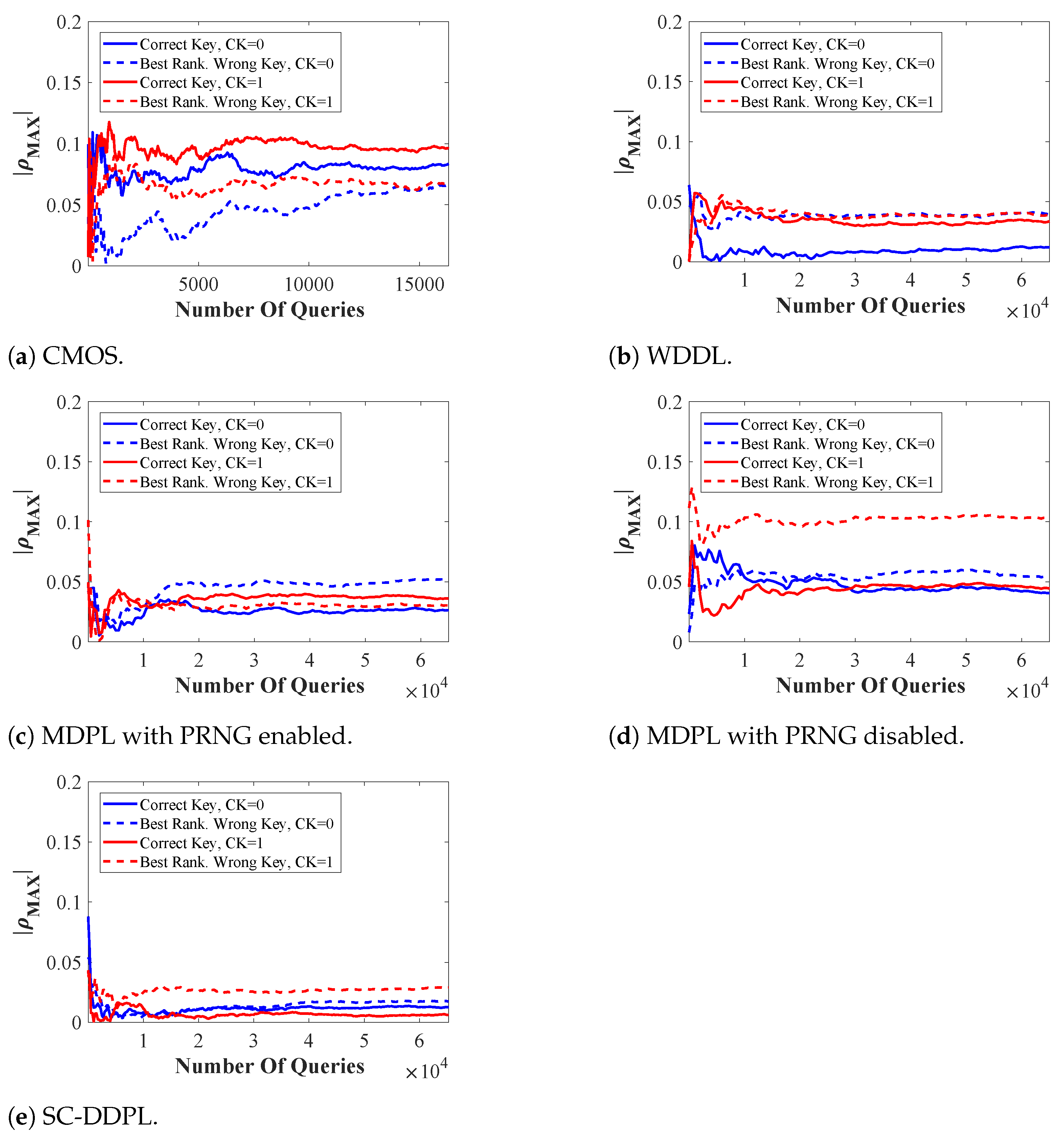
4.3. Leakage Assessment
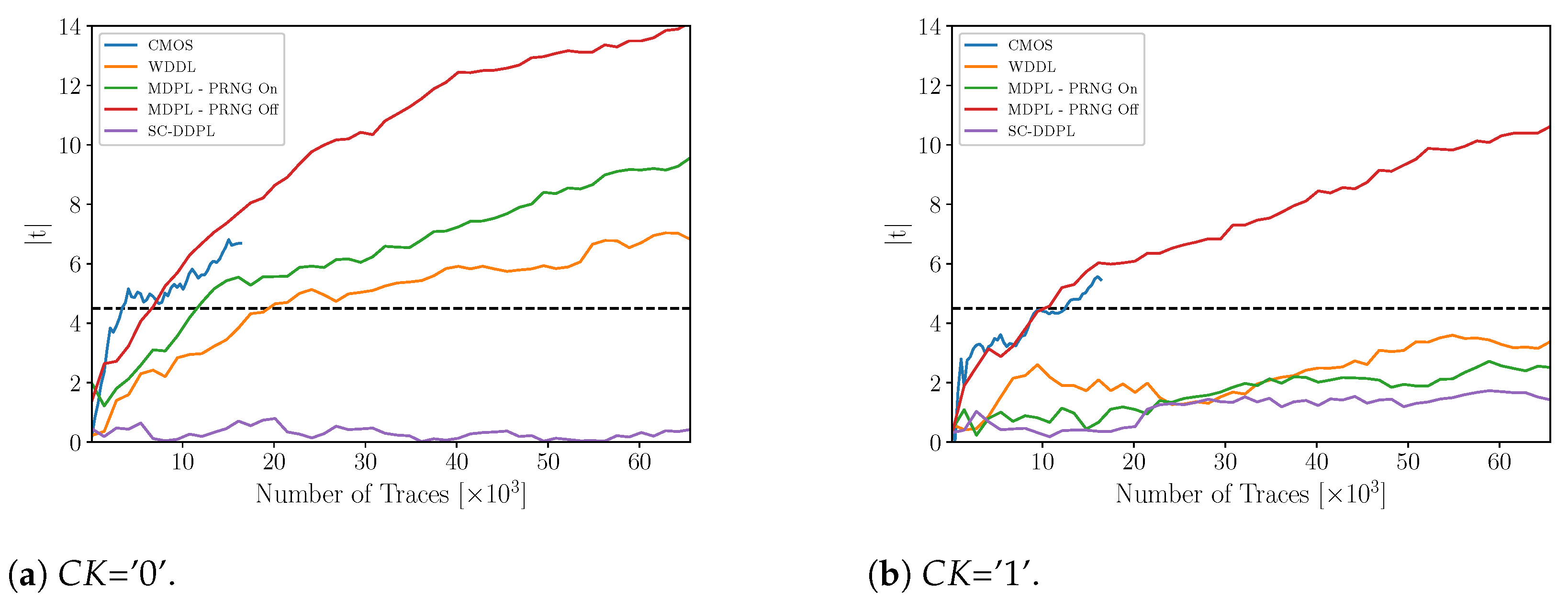
4.4. AESP Results
4.5. Discussion
5. Conclusions
Author Contributions
Funding
Data Availability Statement
Conflicts of Interest
References
- Kocher, P.C. Timing Attacks on Implementations of Diffie-Hellman, RSA, DSS, and Other Systems. In Advances in Cryptology—CRYPTO ’96, Proceedings of the 16th Annual International Cryptology Conference, Santa Barbara, CA, USA, 18–22 August 1996; Lecture Notes in Computer Science; Koblitz, N., Ed.; Springer: Berlin/Heidelberg, Germany, 1996; Volume 1109, pp. 104–113. [Google Scholar]
- Kocher, P.C.; Jaffe, J.; Jun, B. Differential Power Analysis. In Advances in Cryptology—CRYPTO ’99, Proceedings of the 19th Annual International Cryptology Conference, Santa Barbara, CA, USA, 15–19 August 1999; Lecture Notes in Computer Science; Wiener, M.J., Ed.; Springer: Berlin/Heidelberg, Germany, 1999; Volume 1666, pp. 388–397. [Google Scholar]
- Quisquater, J.; Samyde, D. ElectroMagnetic Analysis (EMA): Measures and Counter-Measures for Smart Cards. In Proceedings of the Smart Card Programming and Security, International Conference on Research in Smart Cards, E-smart 2001, Cannes, France, 19–21 September 2001; Lecture Notes in Computer Science. Attali, I., Jensen, T.P., Eds.; Springer: Berlin/Heidelberg, Germany, 2001; Volume 2140, pp. 200–210. [Google Scholar]
- Alioto, M.; Giancane, L.; Scotti, G.; Trifiletti, A. Leakage Power Analysis Attacks: A Novel Class of Attacks to Nanometer Cryptographic Circuits. IEEE Trans. Circuits Syst. I Regul. Pap. 2010, 57-I, 355–367. [Google Scholar] [CrossRef]
- Tiri, K.; Verbauwhede, I. A Logic Level Design Methodology for a Secure DPA Resistant ASIC or FPGA Implementation. In Proceedings of the 2004 Design, Automation and Test in Europe Conference and Exposition (DATE 2004), Paris, France, 16–20 February 2004; IEEE Computer Society: Washington, DC, USA, 2004; pp. 246–251. [Google Scholar]
- Popp, T.; Mangard, S. Masked Dual-Rail Pre-charge Logic: DPA-Resistance Without Routing Constraints. In Cryptographic Hardware and Embedded Systems—CHES 2005, Proceedings of the 7th International Workshop, Edinburgh, UK, 29 August–1 September 2005; Lecture Notes in Computer Science; Rao, J.R., Sunar, B., Eds.; Springer: Berlin/Heidelberg, Germany, 2005; Volume 3659, pp. 172–186. [Google Scholar]
- Nawaz, K.; Kamel, D.; Standaert, F.; Flandre, D. Scaling Trends for Dual-Rail Logic Styles Against Side-Channel Attacks: A Case-Study. In Proceedings of the Constructive Side-Channel Analysis and Secure Design—8th International Workshop, COSADE 2017, Paris, France, 13–14 April 2017; Revised Selected Papers; Lecture Notes in Computer Science. Guilley, S., Ed.; Springer: Cham, Switzerland, 2017; Volume 10348, pp. 19–33. [Google Scholar]
- Tiri, K.; Akmal, M.; Verbauwhede, I. A dynamic and differential CMOS logic with signal independent power consumption to withstand differential power analysis on smart cards. In Proceedings of the 28th European Solid-State Circuits Conference, Florence, Italy, 24–26 September 2002; pp. 403–406. [Google Scholar]
- He, W.; Otero, A.; de la Torre, E.; Riesgo, T. Automatic generation of identical routing pairs for FPGA implemented DPL logic. In Proceedings of the 2012 International Conference on Reconfigurable Computing and FPGAs, ReConFig 2012, Cancun, Mexico, 5–7 December 2012; pp. 1–6. [Google Scholar]
- Bucci, M.; Giancane, L.; Luzzi, R.; Scotti, G.; Trifiletti, A. Delay-Based Dual-Rail Precharge Logic. IEEE Trans. Very Large Scale Integr. Syst. 2011, 19, 1147–1153. [Google Scholar] [CrossRef]
- Bongiovanni, S.; Centurelli, F.; Scotti, G.; Trifiletti, A. Design and validation through a frequency-based metric of a new countermeasure to protect nanometer ICs from side-channel attacks. J. Cryptogr. Eng. 2015, 5, 269–288. [Google Scholar] [CrossRef]
- Bellizia, D.; Scotti, G.; Trifiletti, A. TEL Logic Style as a Countermeasure Against Side-Channel Attacks: Secure Cells Library in 65 nm CMOS and Experimental Results. IEEE Trans. Circuits Syst. I Regul. Pap. 2018, 65-I, 3874–3884. [Google Scholar] [CrossRef]
- Bellizia, D.; Bongiovanni, S.; Olivieri, M.; Scotti, G. SC-DDPL: A Novel Standard-Cell Based Approach for Counteracting Power Analysis Attacks in the Presence of Unbalanced Routing. IEEE Trans. Circuits Syst. I Regul. Pap. 2020, 67-I, 2317–2330. [Google Scholar] [CrossRef]
- Bellizia, D.; Bongiovanni, S.; Monsurrò, P.; Scotti, G.; Trifiletti, A. Univariate Power Analysis Attacks Exploiting Static Dissipation of Nanometer CMOS VLSI Circuits for Cryptographic Applications. IEEE Trans. Emerg. Top. Comput. 2017, 5, 329–339. [Google Scholar] [CrossRef]
- Bellizia, D. Design Methodologies for Cryptographic Hardware with Countermeasures against Side Channel Attacks. Ph.D. Thesis, Sapienza Università di Roma, DIET, Rome, Italy, 2018. Available online: http://hdl.handle.net/11573/1094643 (accessed on 27 May 2021).
- Chandrakasan, A.P.; Bowhill, W.J.; Fox, F. Design of High-Performance Microprocessor Circuits, 1st ed.; Wiley-IEEE Press: Hoboken, NJ, USA, 2000. [Google Scholar]
- Narendra, S.G.; Chandrakasan, A. Leakage in Nanometer CMOS Technologies; Series on Integrated Circuits and Systems; Springer: Berlin/Heidelberg, Germany, 2005. [Google Scholar]
- Moos, T.; Moradi, A.; Richter, B. Static Power Side-Channel Analysis—An Investigation of Measurement Factors. IEEE Trans. Very Large Scale Integr. Syst. 2020, 28, 376–389. [Google Scholar] [CrossRef]
- Karimi, N.; Moos, T.; Moradi, A. Exploring the Effect of Device Aging on Static Power Analysis Attacks. IACR Trans. Cryptogr. Hardw. Embed. Syst. 2019, 2019, 233–256. [Google Scholar] [CrossRef]
- Moos, T. Static Power SCA of Sub-100 nm CMOS ASICs and the Insecurity of Masking Schemes in Low-Noise Environments. IACR Trans. Cryptogr. Hardw. Embed. Syst. 2019, 2019, 202–232. [Google Scholar] [CrossRef]
- Djukanovic, M.; Bellizia, D.; Scotti, G.; Trifiletti, A. Multivariate Analysis Exploiting Static Power on Nanoscale CMOS Circuits for Cryptographic Applications. In Proceedings of the Progress in Cryptology—AFRICACRYPT 2017—9th International Conference on Cryptology in Africa, Dakar, Senegal, 24–26 May 2017; Lecture Notes in Computer Science. Joye, M., Nitaj, A., Eds.; Springer: Cham, Switzerland, 2017; Volume 10239, pp. 79–94. [Google Scholar]
- Moradi, A. Side-Channel Leakage through Static Power—Should We Care about in Practice? In Proceedings of the Cryptographic Hardware and Embedded Systems—CHES 2014—16th International Workshop, Busan, South Korea, 23–26 September 2014; Lecture Notes in Computer Science. Batina, L., Robshaw, M., Eds.; Springer: Berlin/Heidelberg, Germany, 2014; Volume 8731, pp. 562–579. [Google Scholar]
- Bellizia, D.; Scotti, G.; Trifiletti, A. Implementation of the PRESENT-80 block cipher and analysis of its vulnerability to Side Channel Attacks Exploiting Static Power. In Proceedings of the 2016 MIXDES—23rd International Conference Mixed Design of Integrated Circuits and Systems, Lodz, Poland, 23–25 June 2016; pp. 211–216. [Google Scholar]
- Pozo, S.M.D.; Standaert, F.; Kamel, D.; Moradi, A. Side-channel attacks from static power: When should we care? In Proceedings of the 2015 Design, Automation & Test in Europe Conference & Exhibition, DATE 2015, Grenoble, France, 9–13 March 2015; Nebel, W., Atienza, D., Eds.; ACM: New York, NY, USA, 2015; pp. 145–150. [Google Scholar]
- Mangard, S. Hardware Countermeasures against DPA? A Statistical Analysis of Their Effectiveness. In Proceedings of the Topics in Cryptology—CT-RSA 2004, The Cryptographers’ Track at the RSA Conference 2004, San Francisco, CA, USA, 23–27 February 2004; Lecture Notes in Computer Science. Okamoto, T., Ed.; Springer: Berlin/Heidelberg, Germany, 2004; Volume 2964, pp. 222–235. [Google Scholar]
- Macé, F.; Standaert, F.; Quisquater, J. Information Theoretic Evaluation of Side-Channel Resistant Logic Styles. In Proceedings of the Cryptographic Hardware and Embedded Systems—CHES 2007, 9th International Workshop, Vienna, Austria, 10–13 September 2007; Lecture Notes in Computer Science. Paillier, P., Verbauwhede, I., Eds.; Springer: Berlin/Heidelberg, Germany, 2007; Volume 4727, pp. 427–442. [Google Scholar]
- Becker, G.; Cooper, J.; DeMulder, E.; Goodwill, G.; Jaffe, J.; Kenworthy, G.; Kouzminov, T.; Leiserson, A.; Marson, M.; Rohatgi, P.; et al. Test Vector Leakage Assessment (TVLA) Methodology in Practice. In Proceedings of the International Cryptographic Module Conference 2013, Gaithersburg, MD, USA, 24–26 September 2013. [Google Scholar]
- Durvaux, F.; Standaert, F. From Improved Leakage Detection to the Detection of Points of Interests in Leakage Traces. In Proceedings of the Advances in Cryptology—EUROCRYPT 2016—35th Annual International Conference on the Theory and Applications of Cryptographic Techniques, Vienna, Austria, 8–12 May 2016; Proceedings, Part I; Lecture Notes in Computer Science. Fischlin, M., Coron, J., Eds.; Springer: Berlin/Heidelberg, Germany, 2016; Volume 9665, pp. 240–262. [Google Scholar]
- Fant, K.M.; Brandt, S.A. NULL Convention Logic/sup TM/: A Complete And Consistent Logic For Asynchronous Digital Circuit Synthesis. In Proceedings of the 1996 International Conference on Application-Specific Systems, Architectures, and Processors (ASAP ’96), Chicago, IL, USA, 19–23 August 1996; IEEE Computer Society: Washington, DC, USA, 1996; pp. 261–273. [Google Scholar]
- Bogdanov, A.; Knudsen, L.R.; Leander, G.; Paar, C.; Poschmann, A.; Robshaw, M.J.B.; Seurin, Y.; Vikkelsoe, C. PRESENT: An Ultra-Lightweight Block Cipher. In Proceedings of the Cryptographic Hardware and Embedded Systems—CHES 2007, 9th International Workshop, Vienna, Austria, 10–13 September 2007; Lecture Notes in Computer Science. Paillier, P., Verbauwhede, I., Eds.; Springer: Berlin/Heidelberg, Germany, 2007; Volume 4727, pp. 450–466. [Google Scholar]
- Bellizia, D.; Cellucci, D.; Stefano, V.D.; Scotti, G.; Trifiletti, A. Novel measurements setup for attacks exploiting static power using DC pico-ammeter. In Proceedings of the 2017 European Conference on Circuit Theory and Design, ECCTD 2017, Catania, Italy, 4–6 September 2017; pp. 1–4. [Google Scholar]
Short Biography of Authors
 | Davide Bellizia was born on 20 June 1989. He received the M.S. degree (summa cum laude) and Ph.D. degree in Electronics Engineering from University “La Sapienza” of Rome (Italy), respectively in 2014 and 2018. In 2014 he received the “Laureato Eccellente” award for the best graduate student of the year. In 2017, he joined to the Crypto Group of Université Catholique de Louvain (UCLouvain), Louvain-la-Neuve, Belgium, as postdoc researcher. His main research interests include the design and evaluation of circuits for hardware security, with particular attention to development of countermeasures against side-channel attacks, PUFs and RNGs. |
 | Riccardo Della Sala was born on 23 April 1996. In 2020 he received the M.S. degree (summa cum laude) in Electronics Engineering from the University of Rome “La Sapienza” (Italy). His main research interests include the design and development of analog and digital PUFs for hardware security. Furthermore, in the context of analog design, his research activity is focused on ultra-low voltage ultra-low power topology for IOT and biomedical applications. |
 | Giuseppe Scotti received the M.S. and Ph.D. degrees in electronic engineering from the University of Rome “La Sapienza”, Italy, in 1999 and 2003, respectively. In 2010, he became a Researcher (Assistant Professor) at the DIET department of the University of Rome "La Sapienza" and in 2015 he was appointed Associate Professor in the same department. His research activity was mainly concerned with integrated circuits design and focused on design methodologies able to guarantee robustness with respect to parameter variations in both analog circuits and digital VLSI circuits. In the context of cryptographic hardware his focus has been on novel PAAs methodologies and countermeasures. He has coauthored more than 60 publications in international Journals, about 70 contributions in conference proceedings and is the co-inventor of 2 international patents. |
| RTZ Protocol | TEL Protocol | ||||
|---|---|---|---|---|---|
| Log.Value | Pre-Charge | Evaluation | Pre-Charge | Evaluation | Post-Charge |
| A | (ARTZ,ARTZ) | (ARTZ,ARTZ) | (ATEL,ATEL) | (ATEL,ATEL) | (ATEL,ATEL) |
| 0 | (0,0) | (0,VDD) | (0,0) | (0,VDD) | (VDD,VDD) |
| 1 | (0,0) | (VDD,0) | (0,0) | (VDD,0) | (VDD,VDD) |
| NULL | (0,0) | (0/VDD,0/VDD) | (0,0) | (0/VDD,0/VDD) | (VDD,VDD) |
| Impl. | CK = ’0’ | CK = ’1’ | ||||
|---|---|---|---|---|---|---|
| SNR [dB] | MI(X;L) [×] | data [nA] | SNR [dB] | MI(X;L) [×] | data [nA] | |
| CMOS | 416 | 537 | ||||
| WDDL | 259 | 260 | ||||
| MDPL-PRNGon | 416 | 302 | ||||
| MDPL-PRNGoff | 493 | 568 | ||||
| SC-DDPL | 184 | 199 | ||||
| Impl. | CK = ’0’ | CK = ’1’ | ||||||
|---|---|---|---|---|---|---|---|---|
| MTD | |MAX| | SVI | SVI% | MTD | |MAX| | SVI | SVI% | |
| CMOS | 2060 | 411 | ||||||
| WDDL | >64k | >64k | ||||||
| MDPL-PRNGon | >64k | |||||||
| MDPL-PRNGoff | >64k | >64k | ||||||
| SC-DDPL | >64k | >64k | ||||||
| Impl. | CMOS | WDDL | MDPL * | SC-DDPL |
|---|---|---|---|---|
| RTZ | - | ✓ | ✓ | ✓ |
| TEL | - | ✗ | ✗ | ✓ |
| Need Randomness | - | ✗ | ✓ | ✗ |
| Tolerance Cap. Unbalance | - | ✗ | ✗ | ✓ |
| LUTs | 30 | 154 | 784 | 486 |
| Regs | 6 | 0 | 34 | 0 |
| LUT-Reg Pair | 13 | 30 | 62 | 6 |
| (@1.2 V, 2 MHz) | 81.25 | 85.85 | 268.74 | 228.68 |
| (@1.2 V, °C) | 11.89 | 11.74 | 12.01 | 13.49 |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2021 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Bellizia, D.; Della Sala, R.; Scotti, G. SC-DDPL as a Countermeasure against Static Power Side-Channel Attacks. Cryptography 2021, 5, 16. https://doi.org/10.3390/cryptography5030016
Bellizia D, Della Sala R, Scotti G. SC-DDPL as a Countermeasure against Static Power Side-Channel Attacks. Cryptography. 2021; 5(3):16. https://doi.org/10.3390/cryptography5030016
Chicago/Turabian StyleBellizia, Davide, Riccardo Della Sala, and Giuseppe Scotti. 2021. "SC-DDPL as a Countermeasure against Static Power Side-Channel Attacks" Cryptography 5, no. 3: 16. https://doi.org/10.3390/cryptography5030016
APA StyleBellizia, D., Della Sala, R., & Scotti, G. (2021). SC-DDPL as a Countermeasure against Static Power Side-Channel Attacks. Cryptography, 5(3), 16. https://doi.org/10.3390/cryptography5030016








