Privacy Protection in Real Time HEVC Standard Using Chaotic System †
Abstract
1. Introduction
2. Related Works
2.1. HEVC Standard
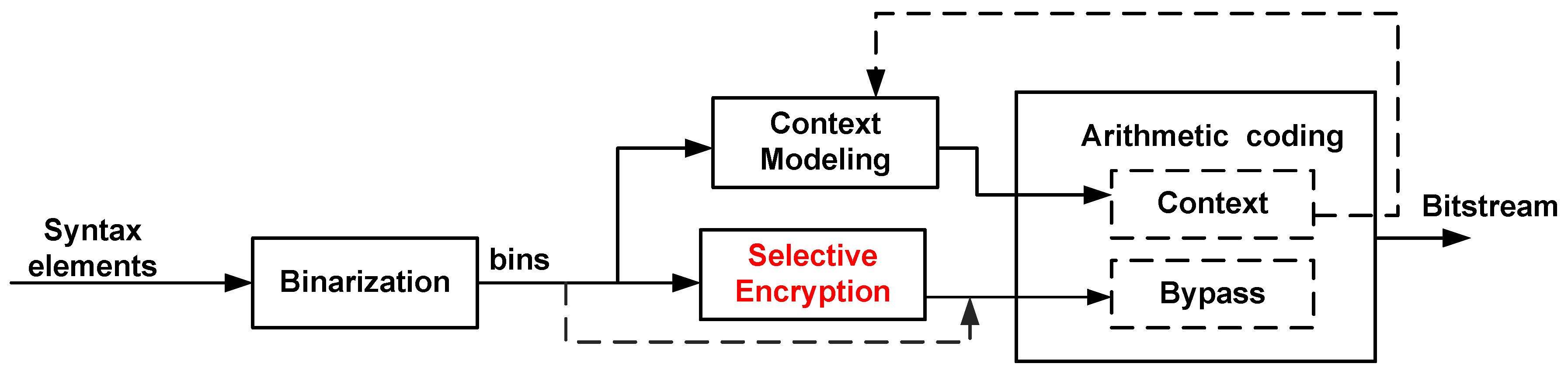
2.1.1. HEVC Entropy Coding
2.1.2. Intra Prediction Modes
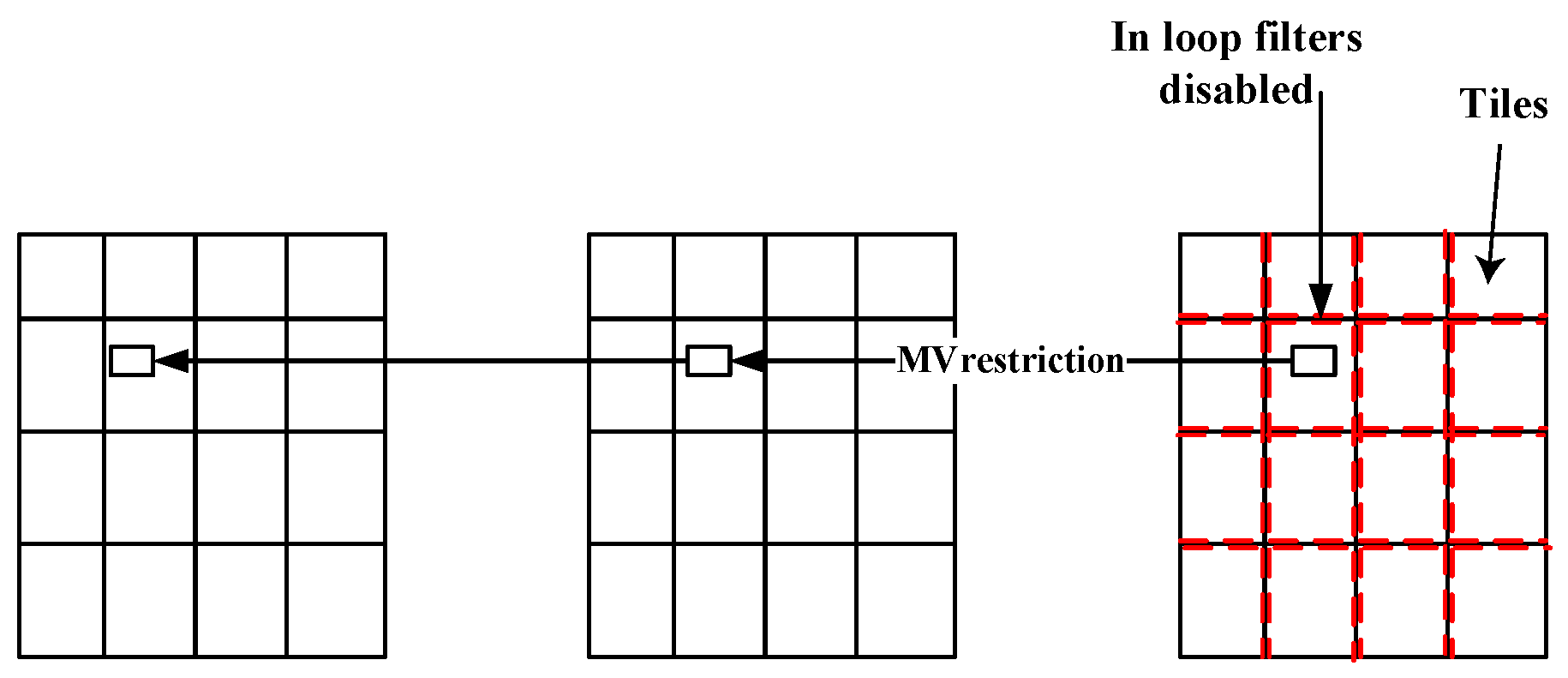
2.1.3. Tiles in HEVC
2.2. Selective Video Encryption
3. Proposed Video Encryption System
3.1. Intra Prediction Parameters Encryption
| Algorithm 1 Encryption of IPMs. |
|
3.2. CABAC Level Encryption
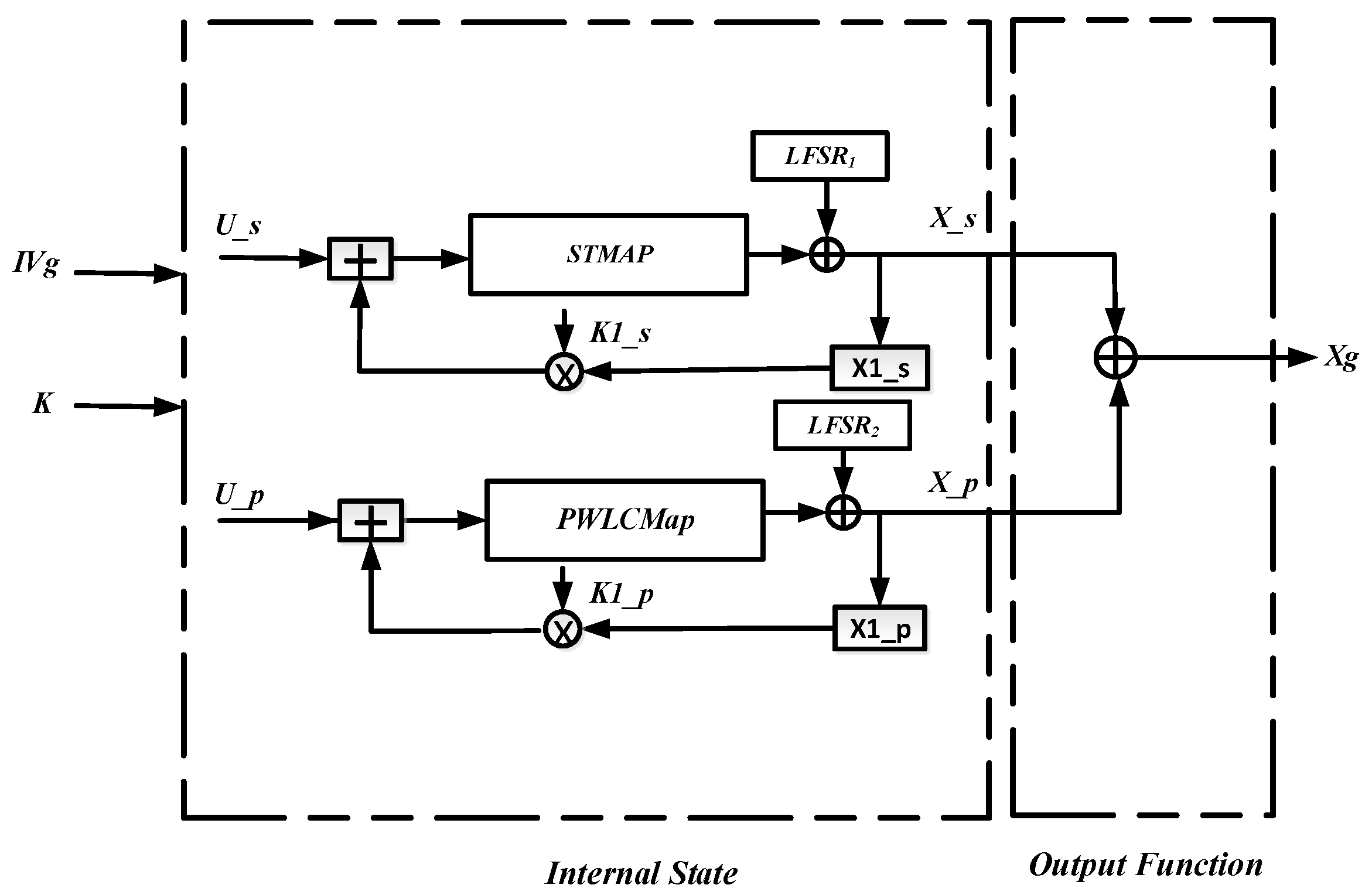
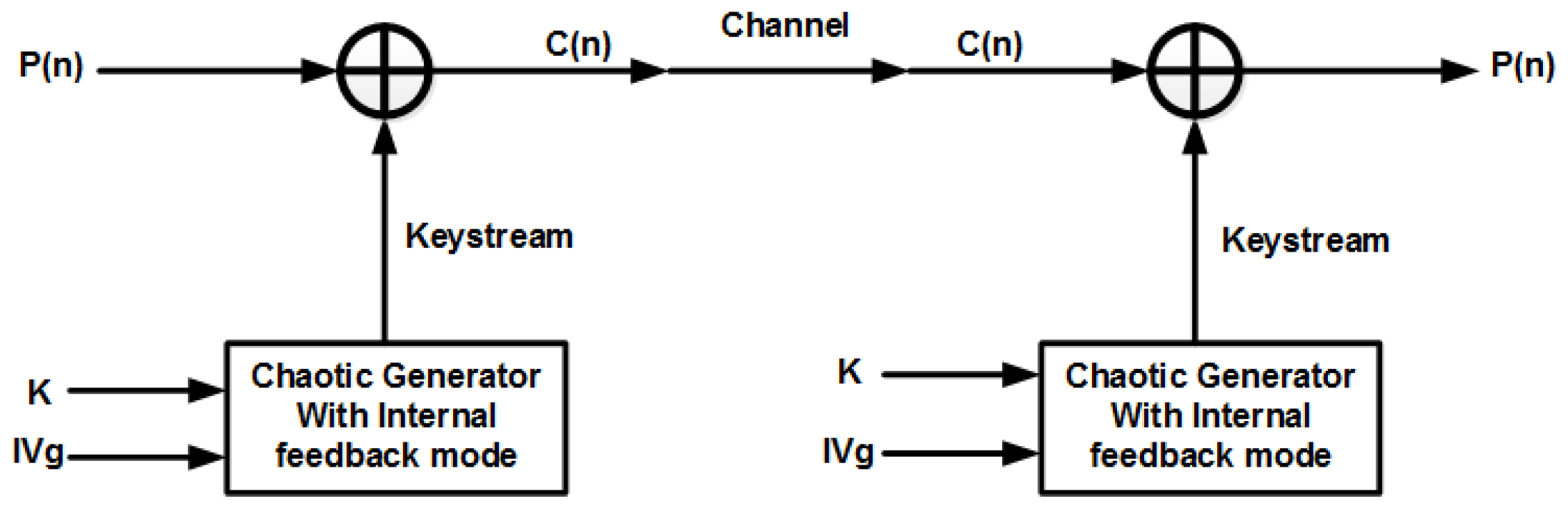
3.3. Encryption System Based on Chaos
4. ROI Encryption Implementation in HEVC Codec
4.1. ROI Encryption System Based on Tiles
4.2. Encryption Propagation in Inter Video Coding
- 1.
- The MVs of the predicted block are restricted to point only to the co-located tile of the reference frame.
- 2.
- The in-loop filters are disabled across the tile boundaries.
5. Results and Discussion
5.1. Experiments
5.2. Objective Measurements
5.2.1. Video Quality Metrics
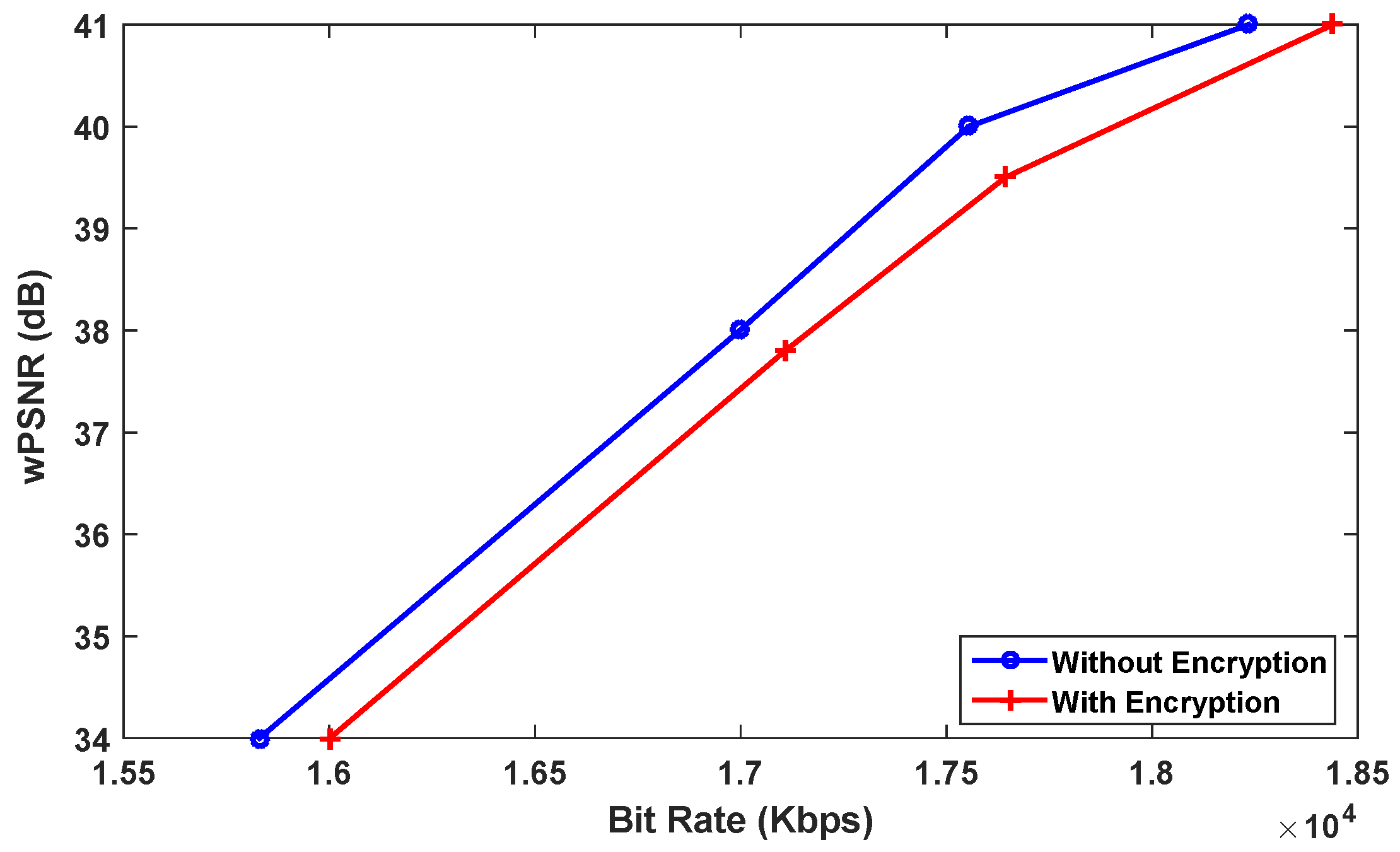
5.2.2. BD-BR Rate Evaluation
5.2.3. Encryption Quality
5.3. Entropy Analysis
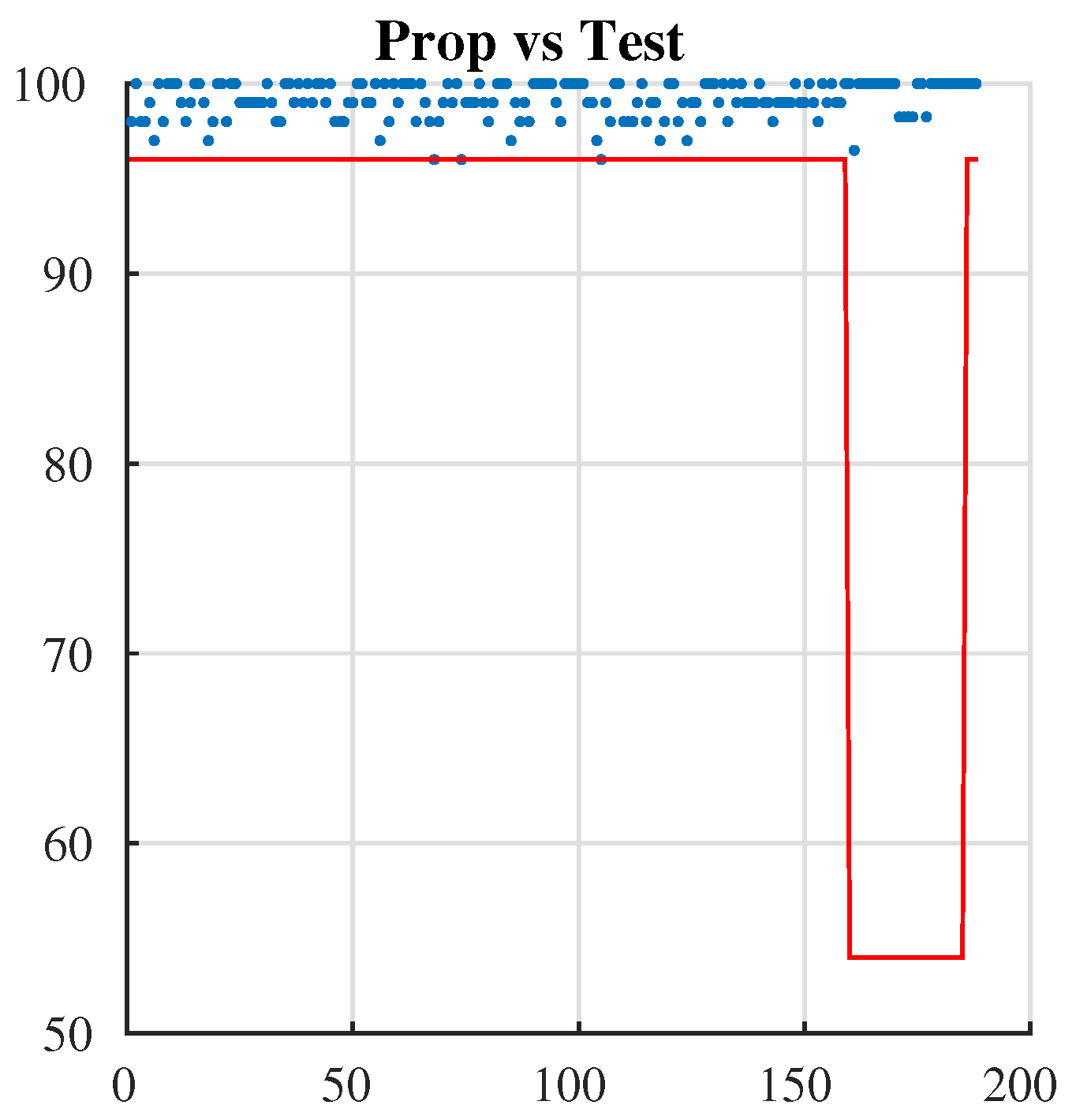
5.3.1. Key Security
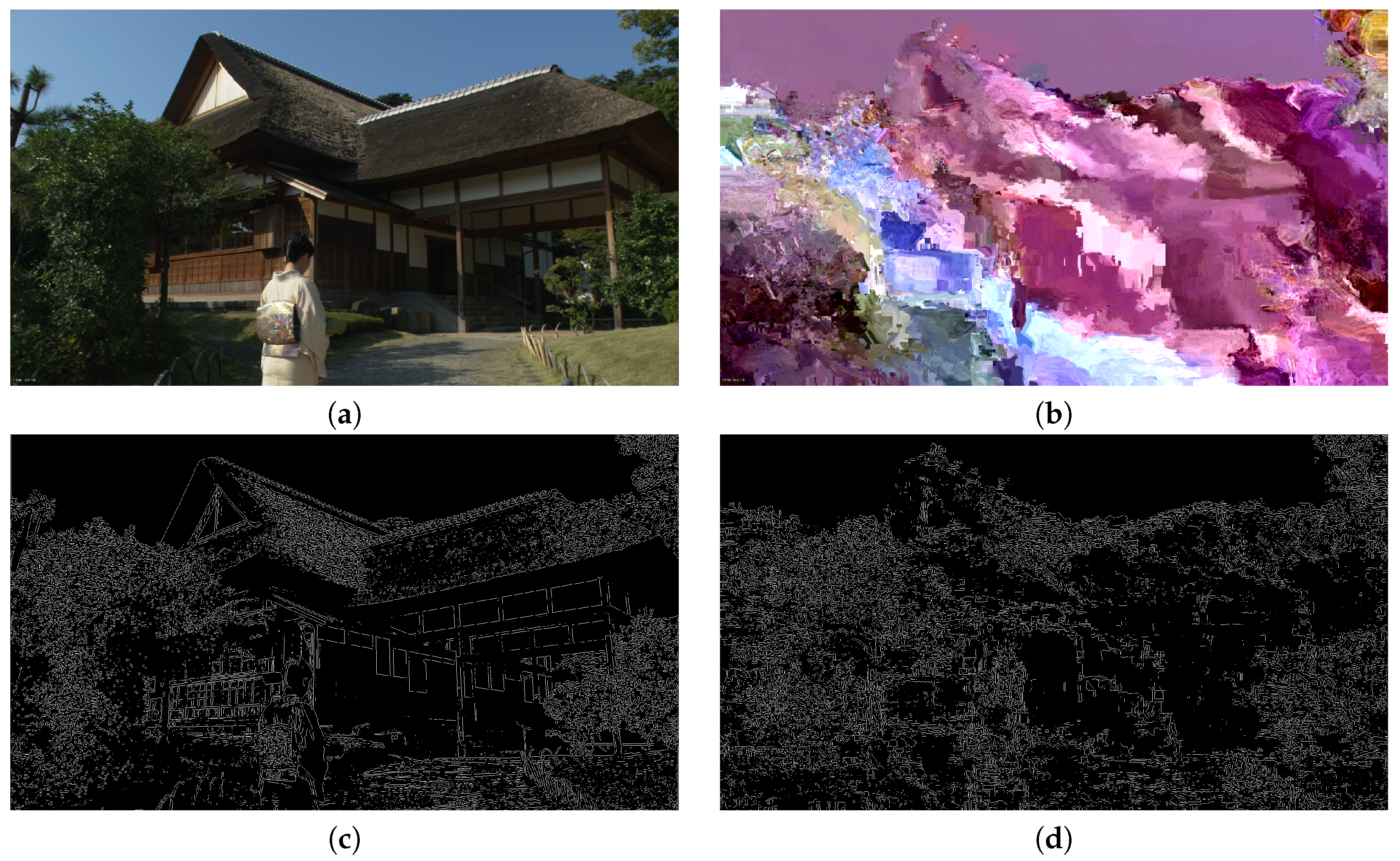
5.3.2. Visual Analysis
5.4. Subjective Evaluations
5.4.1. Design and Procedure
5.4.2. Data Processing
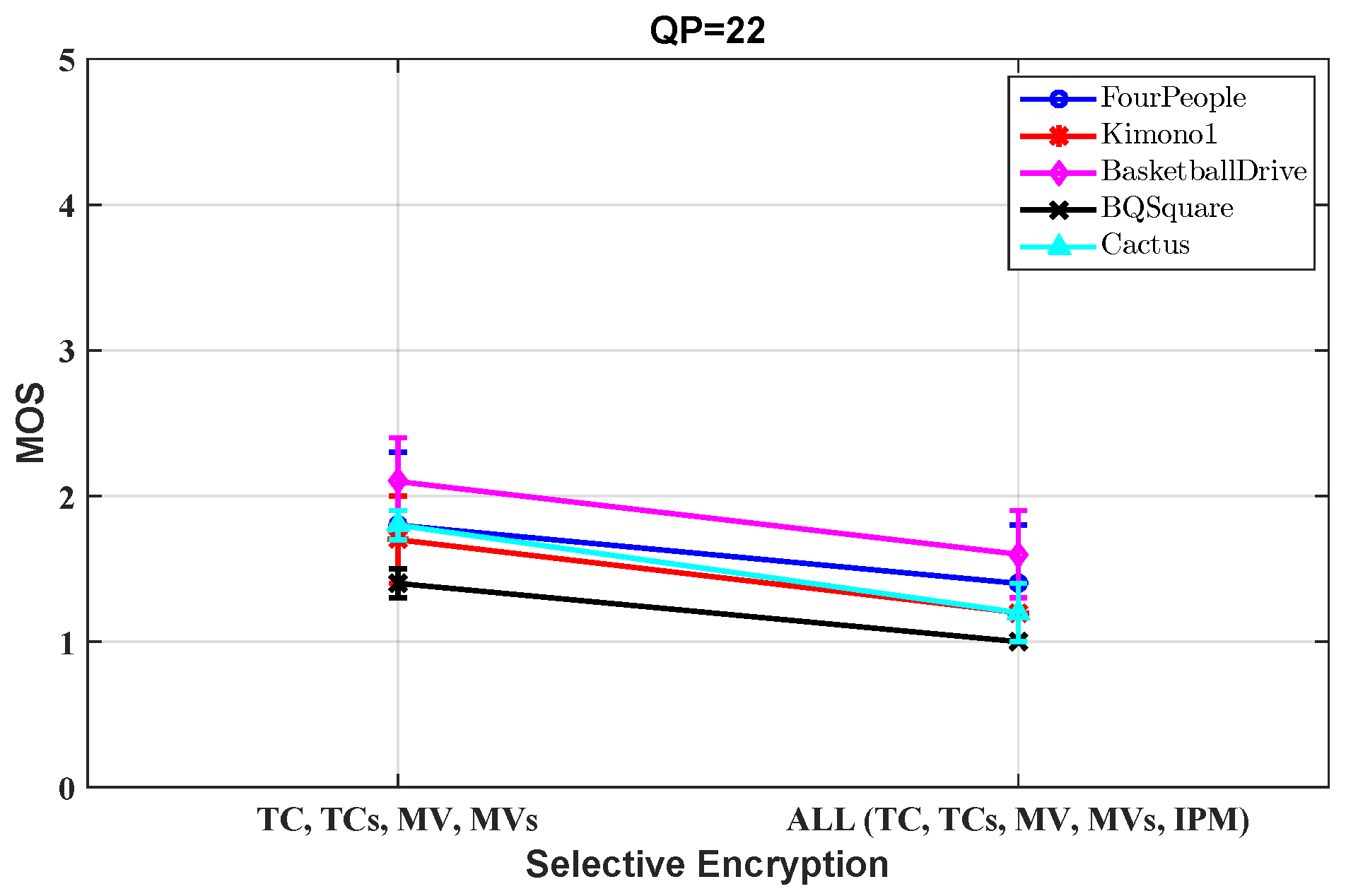
5.4.3. Subjective Scores
5.4.4. Statistical Analysis
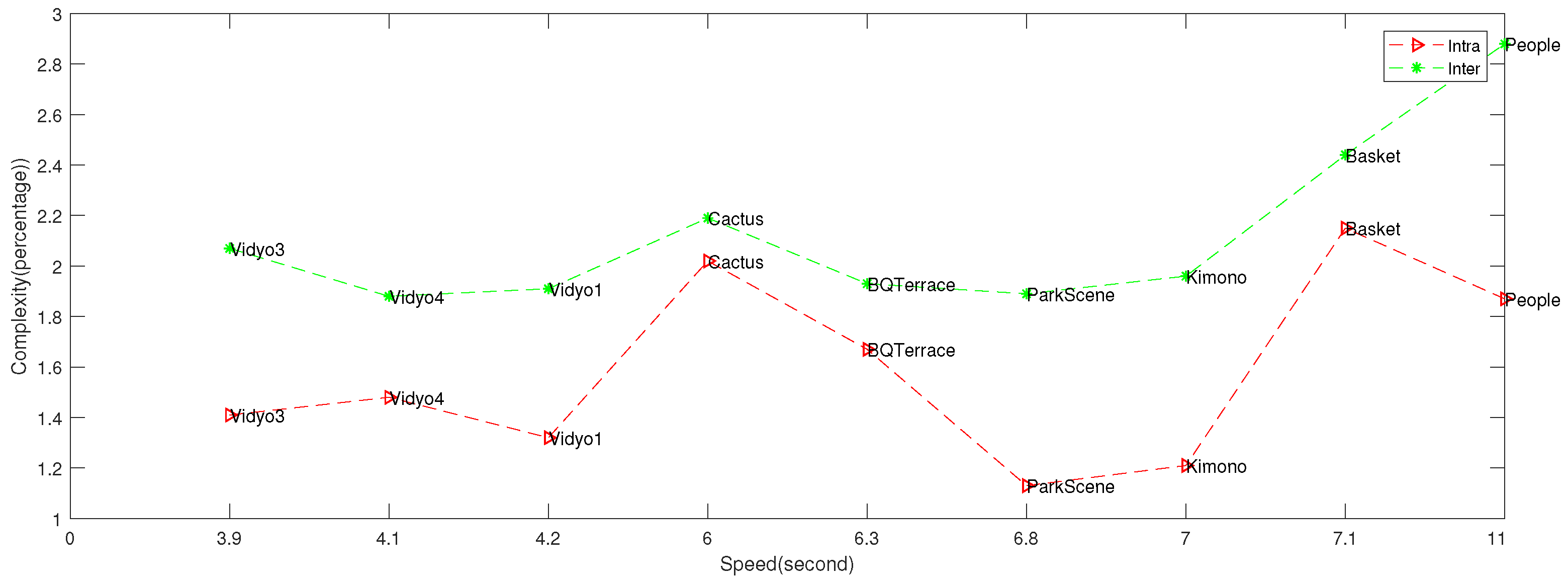
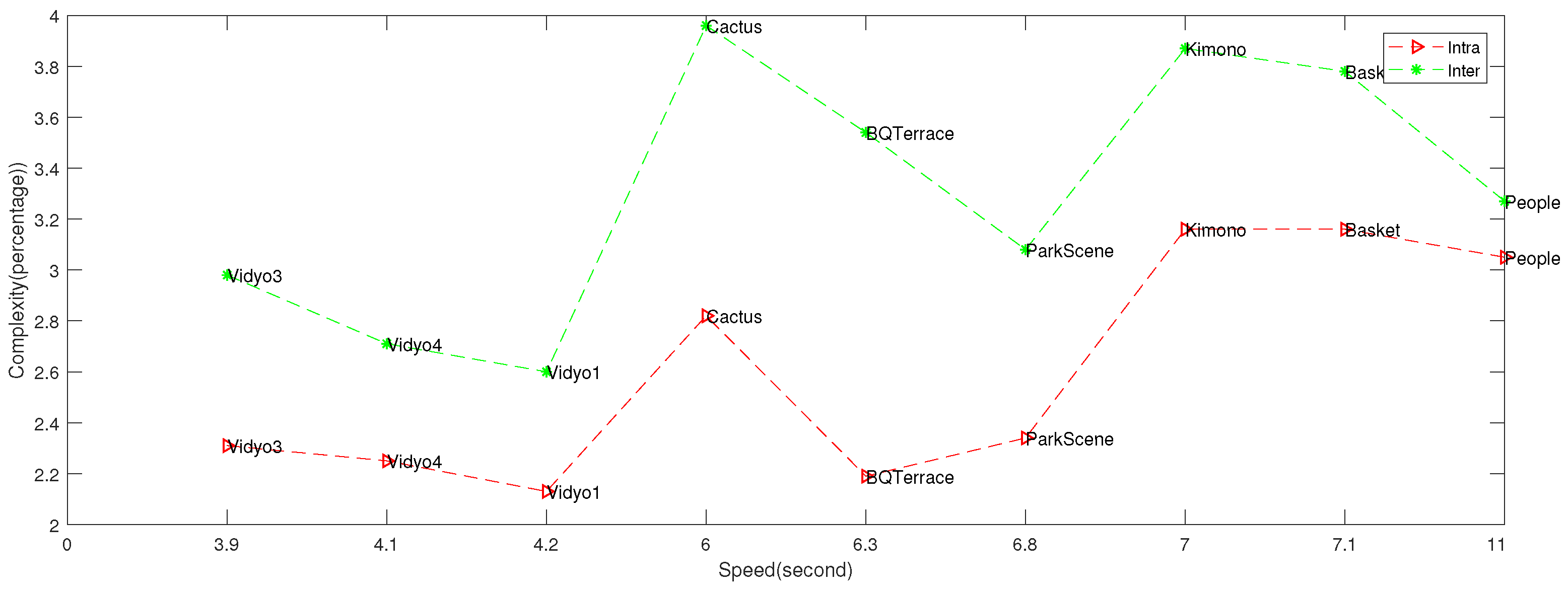
5.5. Complexity Evaluations
6. Conclusions
Author Contributions
Funding
Acknowledgments
Conflicts of Interest
Appendix A
- 1.
- The worst case of the original frame relating to the encryption solution is at low entropy configuration. The whole image has the same color, as an example all pixels are black or blue. Thus, the total number of occurrences of the pixel in the original frame P is , where . In addition, the total number of occurrences of the pixel ( is any pixel except ) in the original (no encrypted) frame P is , where and .
- 2.
- The most secure method should generate a ciphered frame in which all pixels are randomly distributed. Therefore, the total number of occurrences of any pixel Z in the ciphered frame is , where .
References
- Sullivan, G.J.; Ohm, J.R.; Han, W.J.; Wiegand, T. Overview of the High Efficiency Video Coding (HEVC) Standard. IEEE Trans. Circuits Syst. Video Technol. 2012, 22, 1649–1668. [Google Scholar] [CrossRef]
- Ohm, J.R.; Sullivan, G.J.; Schwarz, H.; Tan, T.K.; Wiegand, T. Comparison of the Coding Efficiency of Video Coding Standards— Including High Efficiency Video Coding (HEVC). IEEE Trans. Circuits Syst. Video Technol. 2012, 22, 1669–1684. [Google Scholar] [CrossRef]
- 1: Advanced Video Coding for Generic Audiovisual Services, ITU-T Rec. Available online: https://www.itu.int/rec/T-REC-H.264-201906-I/en (accessed on 6 January 2020).
- Shahid, Z.; Puech, W. Visual Protection of HEVC Video by Selective Encryption of CABAC Binstrings. IEEE Trans. Multimed. 2014, 16, 24–36. [Google Scholar] [CrossRef]
- Van Wallendael, G.; Boho, A.; De Cock, J.; Munteanu, A.; Van de Walle, R. Encryption for High Efficiency Video Coding with Video Adaptation Capabilities. IEEE Trans. Consum. Electron. 2013, 59, 634–642. [Google Scholar] [CrossRef]
- Shifa, A.; Asghar, M.N.; Noor, S.; Gohar, N.; Fleury, M. Lightweight Cipher for H. 264 Videos in the Internet of Multimedia Things with Encryption Space Ratio Diagnostics. Sensors 2019, 19, 1228. [Google Scholar] [CrossRef]
- Chung, Y.; Lee, S.; Jeon, T.; Park, D. Fast video encryption using the H. 264 error propagation property for smart mobile devices. Sensors 2015, 15, 7953–7968. [Google Scholar] [CrossRef]
- Misra, K.; Segall, A.; Horowitz, M.; Xu, S.; Fuldseth, A.; Zhou, M. An Overview of Tiles in HEVC. IEEE J. Sel. Top. Signal Process. 2013, 7, 969–977. [Google Scholar] [CrossRef]
- Hamidouche, W.; Farajallah, M.; Sidaty, N.; Assad, S.E.; Deforges, O. Real-time Selective Video Encryption based on the Chaos System in Scalable HEVC Extension. Signal Process. Image Commun. 2017, 58, 73–86. [Google Scholar] [CrossRef]
- Taha, M.A.; El Assad, S.; Queudet, A.; Déforges, O. Design and Efficient Implementation of a Chaos-based Stream Cipher. Int. J. Internet Technol. Secured Trans. 2017, 7, 89–114. [Google Scholar] [CrossRef]
- Taha, M.A.; El Assad, S.; Jallouli, O.; Queudet, A.; Déforges, O. Design of a Pseudo-Chaotic Number Generator as a Random Number Generator. In Proceedings of the 11th International Conference on Communications, Bucharest, Romania, 21 October 2016; pp. 401–404. [Google Scholar]
- Kvazaar. Kvazaar HEVC Encoder. Available online: https://github.com/ultravideo/kvazaar (accessed on 4 December 2019).
- openHEVC. HEVC Decoder. Available online: http://openhevc.insa-rennes.fr (accessed on 5 December 2019).
- Lainema, J.; Bossen, F.; Han, W.J.; Min, J.; Ugur, K. Intra Coding of the HEVC Standard. IEEE Trans. Circuits Syst. Video Technol. 2012, 22, 1792–1801. [Google Scholar] [CrossRef]
- Sze, V.; Budagavi, M.; Sullivan, G.J. High Efficiency Video Coding (HEVC). In Integrated Circuit and Systems, Algorithms and Architectures; Springer: Berlin, Germany, 2014. [Google Scholar]
- Bossen, F.; Bross, B.; Suhring, K.; Flynn, D. HEVC Complexity and Implementation Analysis. IEEE Trans. Circuits Syst. Video Technol. 2012, 22, 1685–1696. [Google Scholar] [CrossRef]
- Chi, C.C.; Alvarez-Mesa, M.; Juurlink, B.; Clare, G.; Henry, F.; Pateux, S.; Schierl, T. Parallel Scalability and Efficiency of HEVC Parallelization Approaches. IEEE Trans. Circuits Syst. Video Technol. 2012, 22, 1827–1838. [Google Scholar]
- Ryu, E.K.; Nam, J.H.; Lee, S.O.; Jo, H.H.; Sim, D.G. Sample Adaptive Offset Parallelism in HEVC. In Multimedia and Ubiquitous Engineering; Springer: Berlin, Germany, 2013; pp. 1113–1119. [Google Scholar]
- Shahid, Z.; Chaumont, M.; Puech, W. Fast Protection of H. 264/AVC by Selective Encryption of CAVLC and CABAC for I and P Frames. IEEE Trans. Circuits Syst. Video Technol. 2011, 21, 565–576. [Google Scholar] [CrossRef]
- Hamidouche, W.; Farajallah, M.; Raulet, M.; Deforges, O.; El Assad, S. Selective video Encryption using Chaotic System in the SHVC Extension. In Proceedings of the 2015 IEEE International Conference on Acoustics, Speech and Signal Processing (ICASSP), Brisbane, QLD, Australia, 19–24 April 2015; pp. 1762–1766. [Google Scholar]
- Boyce, J.M.; Ye, Y.; Chen, J.; Ramasubramonian, A.K. Overview of SHVC: Scalable Extensions of the High Efficiency Video Coding Standard. IEEE Trans. Circuits Syst. Video Technol. 2016, 26, 20–34. [Google Scholar] [CrossRef]
- Boyadjis, B.; Bergeron, C.; Pesquet-Popescu, B.; Dufaux, F. Extended Selective Encryption of H. 264/AVC (CABAC) and HEVC Encoded Video Streams. IEEE Trans. Circuits Syst. Video Technol. 2015, 1–15. [Google Scholar] [CrossRef]
- Peng, F.; Zhu, X.W.; Long, M. An ROI Privacy Protection Scheme for H. 264 Video based on FMO and Chaos. IEEE Trans. Inf. Forensics Secur. 2013, 8, 1688–1699. [Google Scholar] [CrossRef]
- Dufaux, F.; Ebrahimi, T. Scrambling for Privacy Protection in Video Surveillance Systems. IEEE Trans. Circuits Syst. Video Technol. 2008, 18, 1168–1174. [Google Scholar] [CrossRef]
- Newton, E.M.; Sweeney, L.; Malin, B. Preserving Privacy by De-identifying Face Images. IEEE Trans. Knowl. Data Eng. 2005, 17, 232–243. [Google Scholar] [CrossRef]
- Sohn, H.; AnzaKu, E.T.; De Neve, W.; Ro, Y.M.; Plataniotis, K.N. Privacy Protection in Video Surveillance Systems using Scalable Video Coding. In Proceedings of the Sixth IEEE International Conference on Advanced Video and Signal Based Surveillance, Genova, Italy, 2–4 September 2009; pp. 424–429. [Google Scholar]
- Schwarz, H.; Marpe, D.; Wiegand, T. Overview of the Scalable Video Coding Extension of the H.264/AVC Standard. IEEE Trans. Circuits Syst. Video Technol. 2007, 17, 1103–1120. [Google Scholar] [CrossRef]
- Elaine, B.; John, K. Recommendation for Random Number Generation Using Deterministic Random Bit Generators; Technical Report; National Institute of Standards and Technology: Gaithersburg, MD, USA, 2012.
- Institute, F.H.H. Reference Software Model (hm). Available online: https://mpeg.chiariglione.org/tags/hm (accessed on 10 October 2019).
- Bjøntegaard, G. VCEG-M33: Calculation of Average PSNR Differences Between RD-Curves. Available online: https://www.mathworks.com/matlabcentral/mlc-downloads/downloads/submissions/41749/versions/1/previews/bjontegaard2.m/index.html (accessed on 3 January 2020).
- Ahmed, H.E.d.H.; Kalash, H.M.; Allah, O.F. Encryption Efficiency Analysis and Security Evaluation of RC6 Block Cipher for Digital Images. In Proceedings of the 2007 International Conference on Electrical Engineering, Lahore, Pakistan, 11–12 April 2007; pp. 1–7. [Google Scholar]
- Farajallah, M. Chaos Based Crypto and Joint Crypto-Compression Systems for Images and Videos. Ph.D. Thesis, University of Nantes, Nantes, France, 2015. [Google Scholar]
- Sallam, A.I.; El-Rabaie, E.S.M.; Faragallah, O.S. Efficient HEVC selective stream encryption using chaotic logistic map. Multimed. Syst. 2018, 24, 419–437. [Google Scholar] [CrossRef]
- Taneja, N.; Raman, B.; Gupta, I. Selective Image Encryption in Fractional Wavelet Domain. AEU-Int. J. Electron. Commun. 2011, 65, 338–344. [Google Scholar] [CrossRef]
- Joshi, R.L.; Fischer, T.R. Comparison of Generalized Gaussian and Laplacian Modeling in DCT Image Coding. IEEE Signal Process. Lett. 1995, 2, 81–82. [Google Scholar] [CrossRef]
- Qi, M.; Chen, X.; Jiang, J.; Zhan, S. Face Protection of H. 264 video based on Detecting and Tracking. In Proceedings of the 8th International Conference on Electronic Measurement and Instruments, Xi’an, China, 16–18 August 2007; pp. 2–172. [Google Scholar]
- Xu, H.; Tong, X.; Meng, X. An efficient chaos pseudo-random number generator applied to video encryption. Optik 2016, 127, 9305–9319. [Google Scholar] [CrossRef]
- Abomhara, M.; Zakaria, O.; Khalifa, O.O.; Zaidan, A.; Zaidan, B. Enhancing Selective Encryption for H. 264/AVCUsing Advanced Encryption Standard. Int. J. Comput. Electr. Eng. 2010, 2, 223. [Google Scholar] [CrossRef]
- Hong, S.S.; Han, M.M. The study of selective encryption of motion vector based on the S-Box for the security improvement in the process of video. Multimed. Tools Appl. 2014, 71, 1577–1597. [Google Scholar] [CrossRef]
- Wei, Z.; Wu, Y.; Ding, X.; Deng, R.H. A scalable and format-compliant encryption scheme for H. 264/SVC bitstreams. Signal Process. Image Commun. 2012, 27, 1011–1024. [Google Scholar] [CrossRef]
- Wang, X.; Zheng, N.; Tian, L. Hash key-based video encryption scheme for H. 264/AVC. Signal Process. Image Commun. 2010, 25, 427–437. [Google Scholar] [CrossRef]
- Cheng, S.; Wang, L.; Ao, N.; Han, Q. A Selective Video Encryption Scheme Based on Coding Characteristics. Symmetry 2020, 12, 332. [Google Scholar] [CrossRef]
- ITU Radiocommunication Assembly. Methodology for the Subjective Assessment of the Quality of Television Pictures; International Telecommunication Union: Geneva, Switzerland, 2003. [Google Scholar]
- Sidaty, N.; Hamidouche, W.; Deforges, O. A New Perceptual Assessment Methodology for Selective HEVC Video Encryption. In Proceedings of the 2017 IEEE International Conference on Acoustics, Speech and Signal Processing (ICASSP), New Orleans, LA, USA, 5–9 March 2017. [Google Scholar]
- Gamst, G.; Meyers, L.S.; Guarino, A. Analysis of Vvariance Designs: A Conceptual and Computational Approach with SPSS and SAS; Cambridge University Press: Cambridge, UK, 2008. [Google Scholar]

| Number of Bits | Code | Coded Mode |
|---|---|---|
| 2 | 10 | IPM0 |
| 3 | 110 | IPM1 |
| 3 | 111 | IPM2 |
| 000000 | ||
| 6 | ⋮ | 32 remaining IPMs |
| 011111 |
| Chroma IPM | Luma IPM | |||
|---|---|---|---|---|
| 0 | 26 | 10 | 1 | |
| Planar (mode 0) | 34 | 0 | 0 | 0 |
| Angular (mode 26) | 26 | 34 | 26 | 26 |
| Angular (mode 10) | 10 | 10 | 34 | 10 |
| DC (mode 1) | 1 | 1 | 1 | 34 |
| Derived (luma mode) | 0 | 26 | 10 | 1 |
| Test | P_Value | Proportion |
|---|---|---|
| Frequency test | 0.637 | 100.000 |
| Block-frequency test | 0.956 | 98.000 |
| Cumulative-sums test | 0.715 | 99.500 |
| Runs test | 0.720 | 98.000 |
| Longest-run test | 0.055 | 98.000 |
| Rank test | 0.554 | 99.000 |
| FFT test | 0.109 | 100.000 |
| nonperiodic-templates | 0.546 | 98.973 |
| overlapping-templates | 0.2256 | 99.000 |
| universal | 0.994 | 99.000 |
| approximty entropie | 0.575 | 99.000 |
| random-excursions | 0.428 | 97.581 |
| random-excursions-variant | 0.428 | 98.925 |
| serial test | 0.519 | 99.000 |
| linear-complexity | 0.740 | 98.000 |
| Sequence | Class | Resolution | Frame Rate |
|---|---|---|---|
| PeopleOnStreet | A | 30 | |
| Kimono | B | 24 | |
| ParkScene | B | 24 | |
| BasketballDrive | B | 50 | |
| Cactus | B | 50 | |
| BQTerrace | B | 60 | |
| Vidyo1 | E | 60 | |
| Vidyo3 | E | 60 | |
| Vidyo4 | E | 60 |
| Sequence | Original | Encrypted ROI | ||
|---|---|---|---|---|
| PSNR | SSIM | PSNR | SSIM | |
| PeopleOnStreet | 42.7 | 0.92 | 11.1 | 0.22 |
| Kimono1 | 42.1 | 0.95 | 9.8 | 0.22 |
| ParkScene | 42.2 | 0.90 | 10.76 | 0.21 |
| Cactus | 42.4 | 0.93 | 10.3 | 0.21 |
| BQTerrace | 41.7 | 0.90 | 10.7 | 0.22 |
| BasketballDrive | 41.4 | 0.95 | 10.0 | 0.22 |
| Vidyo1 | 45.3 | 0.91 | 11.2 | 0.20 |
| Vidyo3 | 44.5 | 0.93 | 10.8 | 0.20 |
| Vidyo4 | 44.7 | 0.90 | 11.0 | 0.21 |
| Sequence | QP | Original-PSNR | SE-PSNR | Original-SSIM | SE-SSIM | ||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| Y | U | V | Y | U | V | Y | U | V | Y | U | V | ||
| BasketballDrive (B) | 22 | 42.1 | 43.5 | 44.9 | 10.2 | 10.8 | 11.1 | 0.92 | 0.94 | 0.94 | 0.21 | 0.22 | 0.24 |
| 27 | 41.3 | 42.2 | 43.6 | 10.1 | 10.7 | 11.0 | 0.89 | 0.91 | 0.93 | 0.2 | 0.21 | 0.21 | |
| 32 | 37.5 | 38.8 | 39.1 | 9.8 | 10.5 | 10.9 | 0.76 | 0.72 | 0.88 | 0.16 | 0.18 | 0.22 | |
| 37 | 36.7 | 37.9 | 38.1 | 8.1 | 8.9 | 10.1 | 0.74 | 0.78 | 0.81 | 012 | 0.16 | 0.18 | |
| Kimono1 (B) | 22 | 43.7 | 44.1 | 45.1 | 9.5 | 10.1 | 10.3 | 0.96 | 0.96 | 0.99 | 0.17 | 0.18 | 0.19 |
| 27 | 42.3 | 42.9 | 43.1 | 9.1 | 10.0 | 10.1 | 0.95 | 0.98 | 0.98 | 0.17 | 0.17 | 0.19 | |
| 32 | 38.8 | 38.9 | 39.9 | 8.5 | 9.9 | 10.3 | 0.82 | 0.83 | 0.88 | 0.14 | 0.16 | 0.18 | |
| 37 | 37.8 | 38.6 | 38.9 | 7.5 | 8.4 | 9.9 | 0.77 | 0.78 | 0.80 | 0.12 | 0.14 | 0.17 | |
| PeopleOnStreet (A) | 22 | 38.6 | 41.4 | 43.4 | 10.2 | 10.6 | 11.3 | 0.95 | 0.95 | 0.97 | 0.19 | 0.19 | 0.22 |
| 27 | 38.3 | 39.8 | 41.2 | 9.5 | 9.9 | 10.3 | 0.91 | 0.93 | 0.94 | 0.17 | 0.20 | 0.22 | |
| 32 | 37.0 | 38.1 | 40.6 | 8.9 | 9.3 | 10.1 | 0.88 | 0.90 | 0.92 | 0.18 | 0.19 | 0.21 | |
| 37 | 35.4 | 37.6 | 38.9 | 8.1 | 9.0 | 9.8 | 0.78 | 0.83 | 0.88 | 0.15 | 0.15 | 0.19 | |
| Sequence | Wallendael et al. [5] | Boyadjis et al. [22] | Proposed SE | |||
|---|---|---|---|---|---|---|
| PSNR | SSIM | PSNR | SSIM | PSNR | SSIM | |
| BasketballDrive | 11.4 | 0.40 | 10.4 | 0.43 | 9.9 | 0.17 |
| Kimono1 | 10.1 | 0.32 | 6.6 | 0.27 | 8.9 | 0.14 |
| Vidyo1 | 12.9 | 0.61 | 11.2 | 0.55 | 10.1 | 0.18 |
| Class | Main Intra | Random Access | ||
|---|---|---|---|---|
| TC, TCs, MV and MVs | All | TC, TCs, MV and MVs | All | |
| B | 11.1 | 10.2 | 10.4 | 10.2 |
| D | 9.3 | 8.9 | 8.7 | 8.4 |
| E | 10.2 | 9.6 | 9.7 | 9.1 |
| Class | Main Intra | Random Access | ||
|---|---|---|---|---|
| TC, TCs, MV and MVs | All | TC, TCs, MV and MVs | All | |
| B | 0.33 | 0.25 | 0.30 | 0.21 |
| D | 0.26 | 0.20 | 0.23 | 0.18 |
| E | 0.22 | 0.19 | 0.20 | 0.17 |
| Resolution | Sequence | Intra Coding ( Tiles) | Inter Coding ( Tiles) | ||||
|---|---|---|---|---|---|---|---|
| Bit Rate Loss (%) | Complexity Increase (%) | Bit Rate Loss (%) | Complexity Increase (%) | ||||
| BD-Rate | Encoding | Decoding | BD-Rate | Encoding | Decoding | ||
| PeopleOnStreet | 3.67 | 3.05 | 1.87 | 5.13 | 3.27 | 2.88 | |
| Kimono1 | 5.16 | 3.16 | 1.21 | 13.19 | 3.87 | 1.96 | |
| ParkScene | 4.09 | 2.34 | 1.13 | 9.81 | 3.08 | 1.89 | |
| Cactus | 5.43 | 2.82 | 2.02 | 7.65 | 3.96 | 2.19 | |
| BQTerrace | 7.18 | 2.19 | 1.67 | 18.23 | 3.54 | 1.93 | |
| BasketballDrive | 6.34 | 3.16 | 2.15 | 17.11 | 3.78 | 2.44 | |
| Vidyo1 | 4.21 | 2.13 | 1.32 | 13.87 | 2.60 | 1.91 | |
| Vidyo3 | 6.17 | 2.31 | 1.41 | 10.08 | 2.98 | 2.07 | |
| Vidyo4 | 6.01 | 2.25 | 1.48 | 15.91 | 2.71 | 1.88 | |
| Average | 5.36 | 2.60 | 1.58 | 12.33 | 3.31 | 2.12 | |
| Resolution | Sequence | Intra Coding ( Tiles) | Inter Coding ( Tiles) | ||||
|---|---|---|---|---|---|---|---|
| Bit Rate Loss (%) | Complexity Increase (%) | Bit Rate Loss (%) | Complexity Increase (%) | ||||
| BD-Rate | Encoding | Decoding | BD-Rate | Encoding | Decoding | ||
| PeopleOnStreet | 2.14 | 2.11 | 1.12 | 3.42 | 2.16 | 1.71 | |
| Kimono1 | 4.13 | 2.13 | 1.01 | 11.65 | 2.48 | 1.63 | |
| ParkScene | 3.68 | 1.98 | 1.06 | 8.55 | 2.18 | 1.12 | |
| Cactus | 3.14 | 1.68 | 1.22 | 5.12 | 2.56 | 1.67 | |
| BQTerrace | 4.32 | 1.67 | 1.10 | 12.56 | 2.14 | 1.73 | |
| BasketballDrive | 4.74 | 1.36 | 1.17 | 13.49 | 2.68 | 1.41 | |
| Vidyo1 | 2.08 | 1.43 | 1.15 | 9.19 | 1.93 | 1.43 | |
| Vidyo3 | 4.65 | 1.21 | 1.08 | 7.81 | 1.68 | 1.47 | |
| Vidyo4 | 4.79 | 1.64 | 1.33 | 11.02 | 1.98 | 1.39 | |
| Average | 3.74 | 1.69 | 1.13 | 9.20 | 2.19 | 1.50 | |
| Sequence | EQ in [32] | EQ of Proposed SE |
|---|---|---|
| Kimono1 | 8996 | |
| PeopleOnStreet | 14884 | |
| Vidyo1 | − | |
| Vidyo3 | − | |
| Vidyo4 | − |
| Sequence | Information Entropy |
|---|---|
| PeopleOnStreet | 7.10 |
| Kimono | 7.23 |
| ParkScene | 7.50 |
| BasketballDrive | 7.44 |
| Cactus | 7.35 |
| BQTerrace | 7.21 |
| Vidyo1 | 7.01 |
| Vidyo3 | 7.34 |
| Vidyo4 | 7.21 |
| Algorithm | Encrypted Elements | Format Compliant | Bit Increase | Encryption Algorithm |
|---|---|---|---|---|
| Xu [37] | IPM, MVDs, T1s, signs of the NZ coefficients | yes | no | Chaos |
| Abomhara [38] | I frame | no | no | AES |
| Shahid [19] | T1s, NZ level | yes | no | AES |
| Fei [23] | IPM, MVD, Signs of residual | yes | yes | Chaos |
| Sung [39] | Motion vector | yes | yes | RC4 |
| Wei [40] | NALUs | yes | yes | RC4 |
| Wang [41] | IPM, MVD, Quantization coefficients | yes | yes | Hash and AES |
| Shuli [42] | IPM, MVDs, Signs of residual, delta QP | yes | yes | Chaos and AES |
| Proposed algorithm | IPM, MV, MVS, TC, TCS | yes | IPM | Chaos |
| Source | DF | F-Value | P-Value |
|---|---|---|---|
| Class | 2 | 1.0121 | 0.4001 |
| Content | 4 | 0.9871 | 0.5501 |
| QP | 3 | 0.1281 | 0.128 |
| SE Scheme | 1 | 97.754 | <0.0001 |
© 2020 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Abu Taha, M.; Hamidouche, W.; Sidaty, N.; Viitanen, M.; Vanne, J.; El Assad, S.; Deforges, O. Privacy Protection in Real Time HEVC Standard Using Chaotic System. Cryptography 2020, 4, 18. https://doi.org/10.3390/cryptography4020018
Abu Taha M, Hamidouche W, Sidaty N, Viitanen M, Vanne J, El Assad S, Deforges O. Privacy Protection in Real Time HEVC Standard Using Chaotic System. Cryptography. 2020; 4(2):18. https://doi.org/10.3390/cryptography4020018
Chicago/Turabian StyleAbu Taha, Mohammed, Wassim Hamidouche, Naty Sidaty, Marko Viitanen, Jarno Vanne, Safwan El Assad, and Olivier Deforges. 2020. "Privacy Protection in Real Time HEVC Standard Using Chaotic System" Cryptography 4, no. 2: 18. https://doi.org/10.3390/cryptography4020018
APA StyleAbu Taha, M., Hamidouche, W., Sidaty, N., Viitanen, M., Vanne, J., El Assad, S., & Deforges, O. (2020). Privacy Protection in Real Time HEVC Standard Using Chaotic System. Cryptography, 4(2), 18. https://doi.org/10.3390/cryptography4020018






