Key Management Systems at the Cloud Scale
Abstract
:1. Introduction
1.1. Related Work
1.2. Our Contribution
- We describe the challenges and considerations that need to be addressed by any design of a . We explain why current modes (such as AES-GCM) are not a suitable solution to the problem and a tailored mode is required. Nevertheless, a for the public cloud should adhere to well established cryptographic standards in order to be trusted by cloud users. This restricts the flexibility of the choices that the tailored mode may have.
- We define and analyze a mode of operation () that is suitable for multi-user-multi-key large scale usages, and has nonce-misuse-independence. It builds on top of a nonce respecting mode (AES-GCM). To the best of our knowledge, this is the first multi-user-multi-key mode that is being deployed in a real cloud system.
2. Preliminaries and Notation
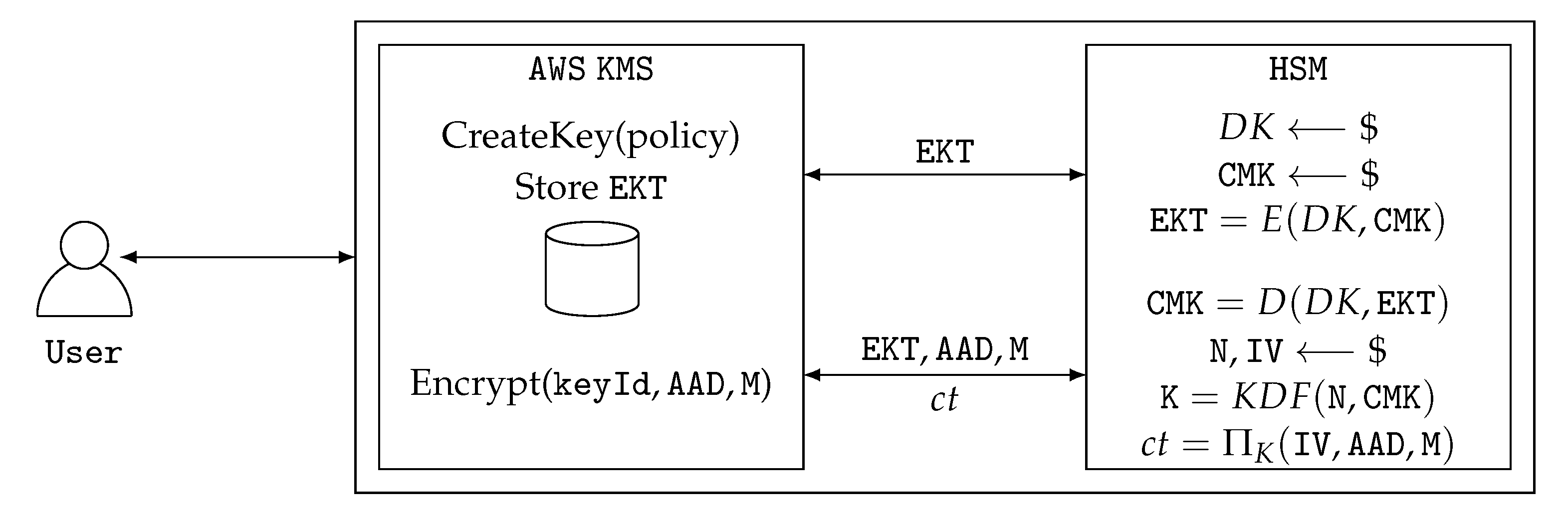
3. A Cloud-Based Key Management Service
3.1. Requirements
- Copious: must support many s. Customers want to reason about use cases.
- FIPS: s can only be accessed within a FIPS 140-2 certified security module.
- Low-latency: generate, encrypt and decrypt of data keys under a must have low-latency.
- Simultaneous use: A can be used simultaneously within the system.
- Durability: s must be at least as durable as the data that they protect.
- High volume: each must be able to encrypt a large number of objects.
- Scalability: a should be able to support a large volume of calls across many customers.
- Distributive: a should be able to distribute the role of key generation and bulk data encryption.
3.2. Desired Properties of a CES
3.3. Requirement Driven Design
“The probability that the authenticated encryption function ever will be invoked with the same and the same key on two (or more) distinct sets of input data shall be no greater than .”
4. Security Bounds for Mode Of Operation
4.1. Abstraction of an Idealized AWS KMS Mode CES-GCM(i)
4.2. Security Definitions for CES-GCM(i)
4.2.1. A Oracle
- (a)
- a bit b.
- (b)
- U keys , each one of bits.
- (c)
- a random function .
- Select, uniformly at random,
- (a)
- a string of bits,
- (b)
- a string of bits,
- (c)
- a string of length blocks.
- Compute .
- E-GCM encrypt M, with , under the key , obtaining the ciphertext and the authentication tag .
- Output: , , , if , and , , , , if .
- Compute .
- E-GCM decrypt , , , using , under the key , obtaining the plaintext of , and determining if the authentication passed or failed.
- Output: if then: (plaintext) if authentication passed and ⊥ if it failed.If then: ⊥.
4.2.2. Adversary against
4.3. Security Bounds for
4.3.1. Events That May Occur during Encryption Queries
- () There are two identifiers , such that .
- () All the ’s are distinct, and there are identifiers , and indexes , such that .
- () There is an identifier , such that contains a value that is repeated 3 or more times.
- () There is an identifier , and indexes i, j, , such that and .
- () The combined list includes a value that is repeated more than times.
- c1.
- All the CMK’s are distinct.
- c2.
- For every , the usage of E-GCM by was proper. Furthermore, can be split to disjoint sub-lists: keys that were used for encrypting a single message, and keys that were used for encrypting two messages. These satisfy the relation , and .
- c3.
- Across all the encryptions, every counter block is encrypted under at most distinct keys.
Interpreting Theorem 2
Accounting for Real Primitives
Accounting for an Active (Forging) Adversary
5. Discussion
Author Contributions
Funding
Conflicts of Interest
References
- Services, A.W. AWS Identity and Access Management. 2016. Available online: https://aws.amazon.com/kms/ (accessed on 31 August 2017).
- McGrew, D.A.; Viega, J. The Security and Performance of the Galois/Counter Mode (GCM) of Operation. In Progress in Cryptology—INDOCRYPT 2004; Canteaut, A., Viswanathan, K., Eds.; Springer: Berlin/Heidelberg, Germany, 2005; pp. 343–355. [Google Scholar]
- Abdalla, M.; Bellare, M. Increasing the Lifetime of a Key: A Comparative Analysis of the Security of Re-keying Techniques. In Proceedings of the 6th International Conference on the Theory and Application of Cryptology and Information Security: Advances in Cryptology, Kyoto, Japan, 3–7 December 2000; Springer-Verlag: London, UK, 2000; pp. 546–559. [Google Scholar] [Green Version]
- Smyshlyaev, S.V. Re-Keying Mechanisms for Symmetric Keys; Internet-Draft draft-irtf-cfrg-re-keying-11; Internet Engineering Task Force: Fremont, CA, USA, 2019. [Google Scholar]
- Chatterjee, S.; Menezes, A.; Sarkar, P. Another Look at Tightness. In Selected Areas in Cryptography; Miri, A., Vaudenay, S., Eds.; Springer: Berlin/Heidelberg, Germany, 2012; pp. 293–319. [Google Scholar]
- Mouha, N.; Luykx, A. Multi-key Security: The Even-Mansour Construction Revisited. In Proceedings of the Advances in Cryptology—CRYPTO 2015—35th Annual Cryptology Conference, Santa Barbara, CA, USA, 16–20 August 2015; pp. 209–223. [Google Scholar]
- Bellare, M.; Tackmann, B. The Multi-user Security of Authenticated Encryption: AES-GCM in TLS 1.3. In Advances in Cryptology—CRYPTO 2016; Robshaw, M., Katz, J., Eds.; Springer Berlin/Heidelberg: Berlin/Heidelberg, Germany, 2016; pp. 247–276. [Google Scholar]
- Luykx, A.; Mennink, B.; Paterson, K.G. Analyzing Multi-key Security Degradation. In Proceedings of the Advances in Cryptology—ASIACRYPT 2017—23rd International Conference on the Theory and Applications of Cryptology and Information Security, Hong Kong, China, 3–7 December 2017; pp. 575–605. [Google Scholar]
- Gueron, S.; Langley, A.; Lindell, Y. AES-GCM-SIV: Specification and Analysis. Cryptology ePrint Archive, Report 2017/168. 2017. Available online: https://eprint.iacr.org/2017/168 (accessed on 31 July 2019).
- Rogaway, P.; Shrimpton, T. A Provable-Security Treatment of the Key-Wrap Problem. In Advances in Cryptology—EUROCRYPT 2006; Vaudenay, S., Ed.; Springer: Berlin/Heidelberg, Germany, 2006; pp. 373–390. [Google Scholar] [Green Version]
- Gueron, S.; Langley, A.; Lindell, Y. AES-GCM-SIV: Nonce Misuse-Resistant Authenticated Encryption. RFC 2019, 8452, 1–42. [Google Scholar] [CrossRef]
- Iyengar, J.; Thomson, M. QUIC: A UDP-Based Multiplexed and Secure Transport; Internet-Draft Draft-Ietf-Quic-Transport-20; Internet Engineering Task Force: Fremont, CA, USA, 2019. [Google Scholar]
- Gueron, S.; Lindell, Y. Better Bounds for Block Cipher Modes of Operation via Nonce-Based Key Derivation. In Proceedings of the 2017 ACM SIGSAC Conference on Computer and Communications Security, CCS 2017, Dallas, TX, USA, 30 October–3 November 2017; pp. 1019–1036. [Google Scholar] [CrossRef]
- Bose, P.; Hoang, V.T.; Tessaro, S. Revisiting AES-GCM-SIV: Multi-user Security, Faster Key Derivation, and Better Bounds. In Proceedings of the Advances in Cryptology—EUROCRYPT 2018—37th Annual International Conference on the Theory and Applications of Cryptographic Techniques, Tel Aviv, Israel, 39 April–3 May 2018; pp. 468–499. [Google Scholar]
- Dworkin, M. SP 800-38D, Recommendation for Block Cipher Modes of Operation: Galois/Counter Mode (GCM) and GMAC; Technical Report; National Institute of Standards and Technology: Gaithersburg, MD, USA, 2007. [Google Scholar]
- Suzuki, K.; Tonien, D.; Kurosawa, K.; Toyota, K. Birthday Paradox for Multi-collisions. In Proceedings of the 9th International Conference on Information Security and Cryptology, Busan, Korea, 30 November–1 December 2006; Springer-Verlag: Berlin/Heidelberg, Germany, 2006; pp. 29–40. [Google Scholar] [CrossRef]
- Services, A.W. AWS Key Management Service (KMS). 2019. Available online: https://docs.aws.amazon.com/IAM/latest/UserGuide/iam-ug.pdf#access_policies (accessed on 31 August 2017).
- Ramaswamy Chandramouli, M.I.; Chokhani, S. Cryptographic Key Management Issues & Challenges in Cloud Services; Technical Report; National Institute of Standards and Technology: Gaithersburg, MD, USA, 2013. [Google Scholar]
- Chen, L. SP 800-108. Recommendation for Key Derivation Using Pseudorandom Functions (Revised); Technical Report; National Institute of Standards and Technology: Gaithersburg, MD, USA, 2009. [Google Scholar]
- Campagna, M. AWS Key Management Service Cryptographic Details. 2016. Available online: https://d0.awsstatic.com/whitepapers/KMS-Cryptographic-Details.pdf (accessed on 31 August 2018).

© 2019 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Campagna, M.; Gueron, S. Key Management Systems at the Cloud Scale. Cryptography 2019, 3, 23. https://doi.org/10.3390/cryptography3030023
Campagna M, Gueron S. Key Management Systems at the Cloud Scale. Cryptography. 2019; 3(3):23. https://doi.org/10.3390/cryptography3030023
Chicago/Turabian StyleCampagna, Matthew, and Shay Gueron. 2019. "Key Management Systems at the Cloud Scale" Cryptography 3, no. 3: 23. https://doi.org/10.3390/cryptography3030023
APA StyleCampagna, M., & Gueron, S. (2019). Key Management Systems at the Cloud Scale. Cryptography, 3(3), 23. https://doi.org/10.3390/cryptography3030023




