Trusted Time-Based Verification Model for Automatic Man-in-the-Middle Attack Detection in Cybersecurity
Abstract
1. Introduction
2. Related Works
3. Research Background
Can we design an automatic trusted model that adopts an intelligent mechanism to employ time-based verification of sent and received messages to detect MITM attacks?
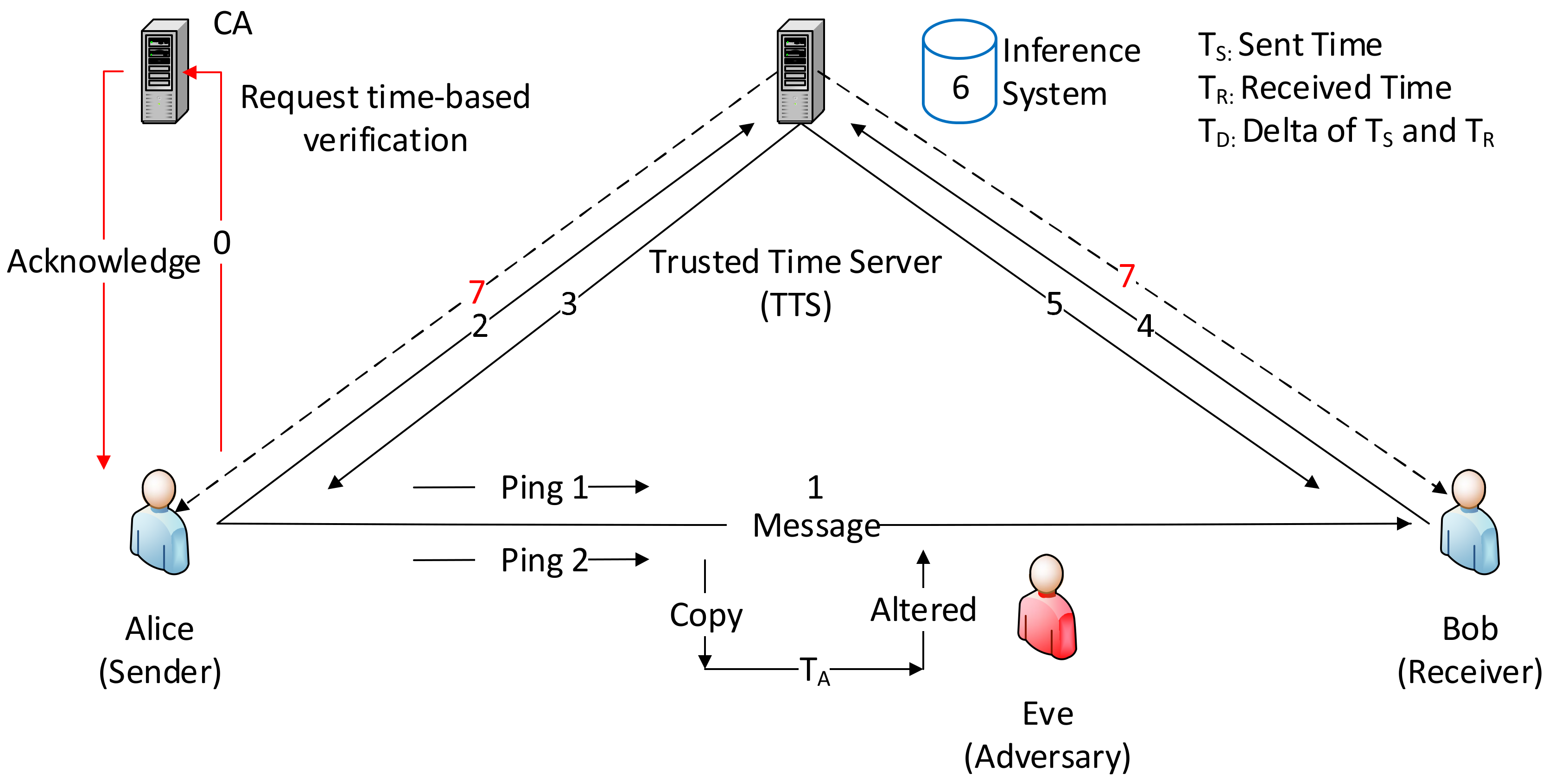
When a user requests the issuance of DC to a CA, the user may select the proposed option of using a timestamp check at a trusted time server (TTS), which will collect and verify the transmission time between when the message is sent and when it is received by the sender and receiver, respectively. The outcome of the verification is to advise the user of any suspicious MITM activity based on the difference between timestamps and preset thresholds, which can be maintained by ongoing updates. The automatic inference scheme is developed using a self-adaptive learning approach.
4. Proposed MITM Detection Model
4.1. Modeling the Problem Scenario
4.2. Model Intelligence to Counter Evasive MITM Attacks
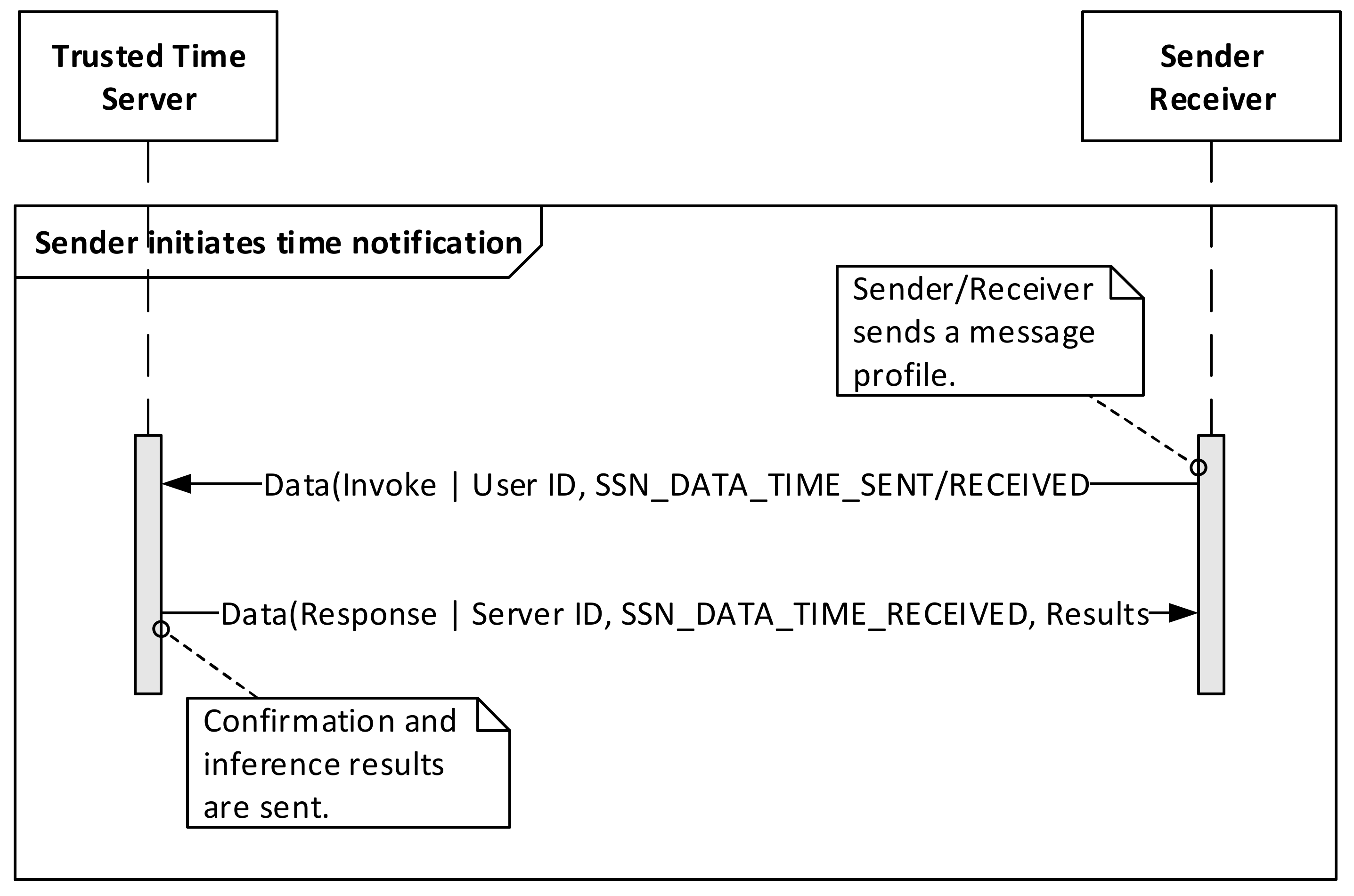
5. Implementation of Time-Based Verification Model
5.1. Model Implementation
5.2. Inference Engine Using Threshold Table
- Ping results to and from A and B;
- Previous data and learning experiences;
- Network types (local, national, international, wired, wireless, cellular, metro, wide area network, etc.), which can be determined by source and destination IP that relates to geographic location;
- Current network status, e.g., normal, congested, abnormal etc.
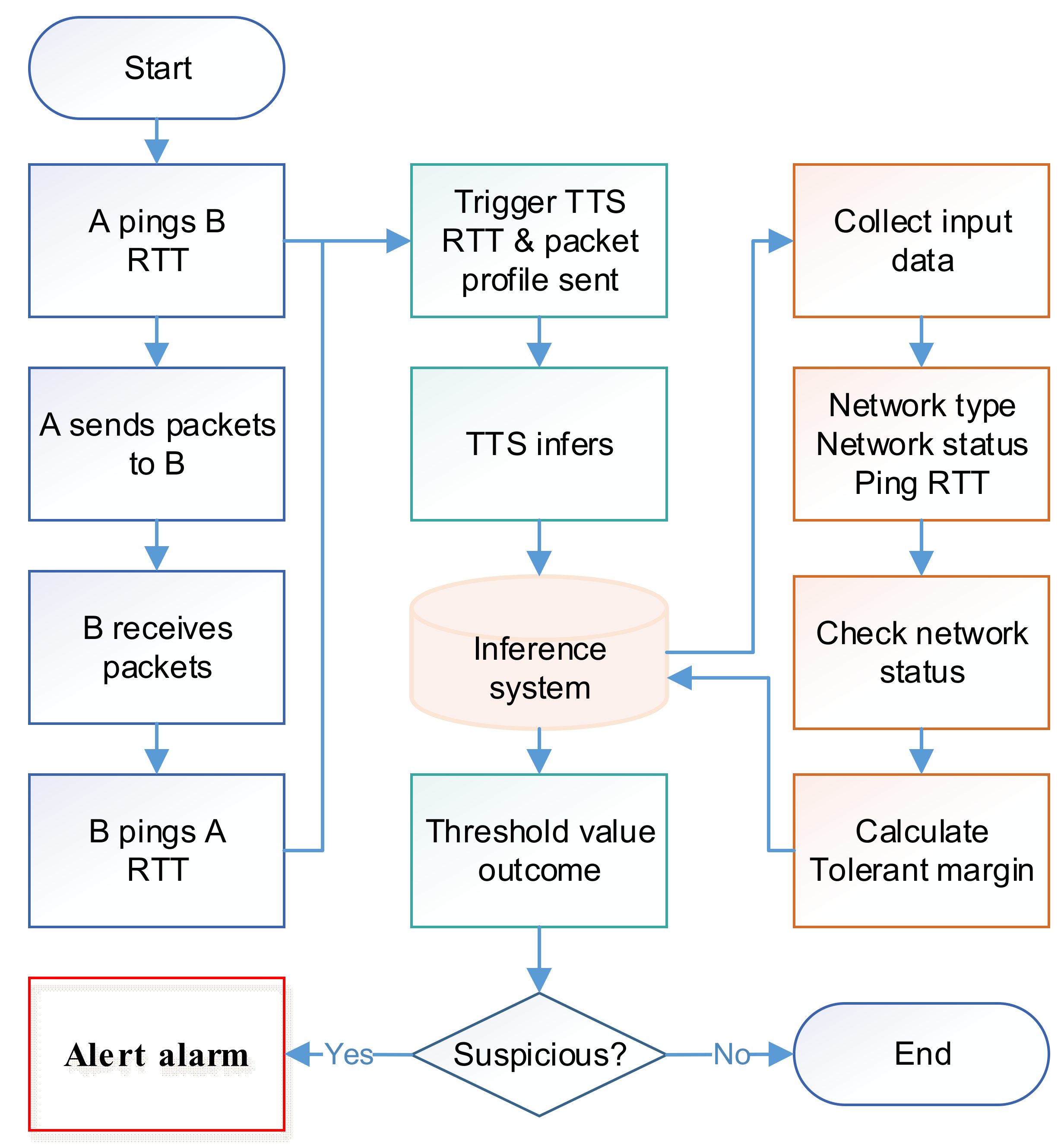
5.3. Time-Based Verification and MITM Detection Algorithm
| Algorithm 1. MITM detection algorithm. |
| 1. Initialize: TP1 = 0, TP2 = 0, TD = 0 |
| 2. function createSentTimeStamp(MID,TP1) |
| 3. TS ← sent timestamp generated |
| 4. record MID, TP, TS in dbI database |
| 5. end function |
| 6. function updateReceivedTimeStamp(MID,TP2) |
| 7. TR ← received timestamp generated |
| 8. update the TR value based on MID in dbI database |
| 9. end function |
| 10. function calculatetimeDifference(TS,TR) |
| 11. TD ← TR − TS |
| 12. return TD |
| 13. end function |
| 14. function findThresholdValue(NT) |
| 15. find the threshold time for NT |
| 16. TH ←Avg(TH) of Physical distance—DV and Logical distance—LS |
| 17. TM ← Avg(TM) of Physical distance—DV and Logical distance—LS |
| 18. Ns ← 0.25(N),0.5(LC),0.75(MC),1(A) |
| 19. return TH, TM, NS |
| 20. end function |
| 21. function findStandarddeviation(NT) |
| 22. μ(mean) ← ((Tp) x (a%) + Tth x (b%) + Ns)/3 |
| 23. n←subtract the μ and square the result |
| 24. m← |
| 25. σ = √m |
| 26. return μ, σ |
| 27. end function |
| 28. for each message send do |
| 29. A pings B |
| 30. TP1 ← ping response time |
| 31. TP1 = Tp1/2 |
| 32. createSentTimeStamp(MID,TP1) |
| 33. B pings A |
| 34. TP2 ← ping response time |
| 35. TP2 = Tp2/2 |
| 36. updateReceivedTimeStamp(MID,TP2) |
| 37. calculatetimeDifference(TS,TR) |
| 38. TH,TM ← findThresholdValue(NT) |
| 39. TP = (Tp1 + Tp2)/2 |
| 40. update the threshold of tolerant response time table for Ping time |
| 41. findStandarddeviation |
| 42. σ = μ+ σ |
| 43. if ((TD > TP) AND (TD > (TP + TP * Tm/100))) |
| 44. if ((TD > μ) AND (TD > σ)) AND (TD > (σ + σ * Tm/100))) |
| 45. mark as a suspicious case |
| 46. Mwarn → sends a notification to A and B |
| 47. end if |
| 48. end if |
| 49. end for |
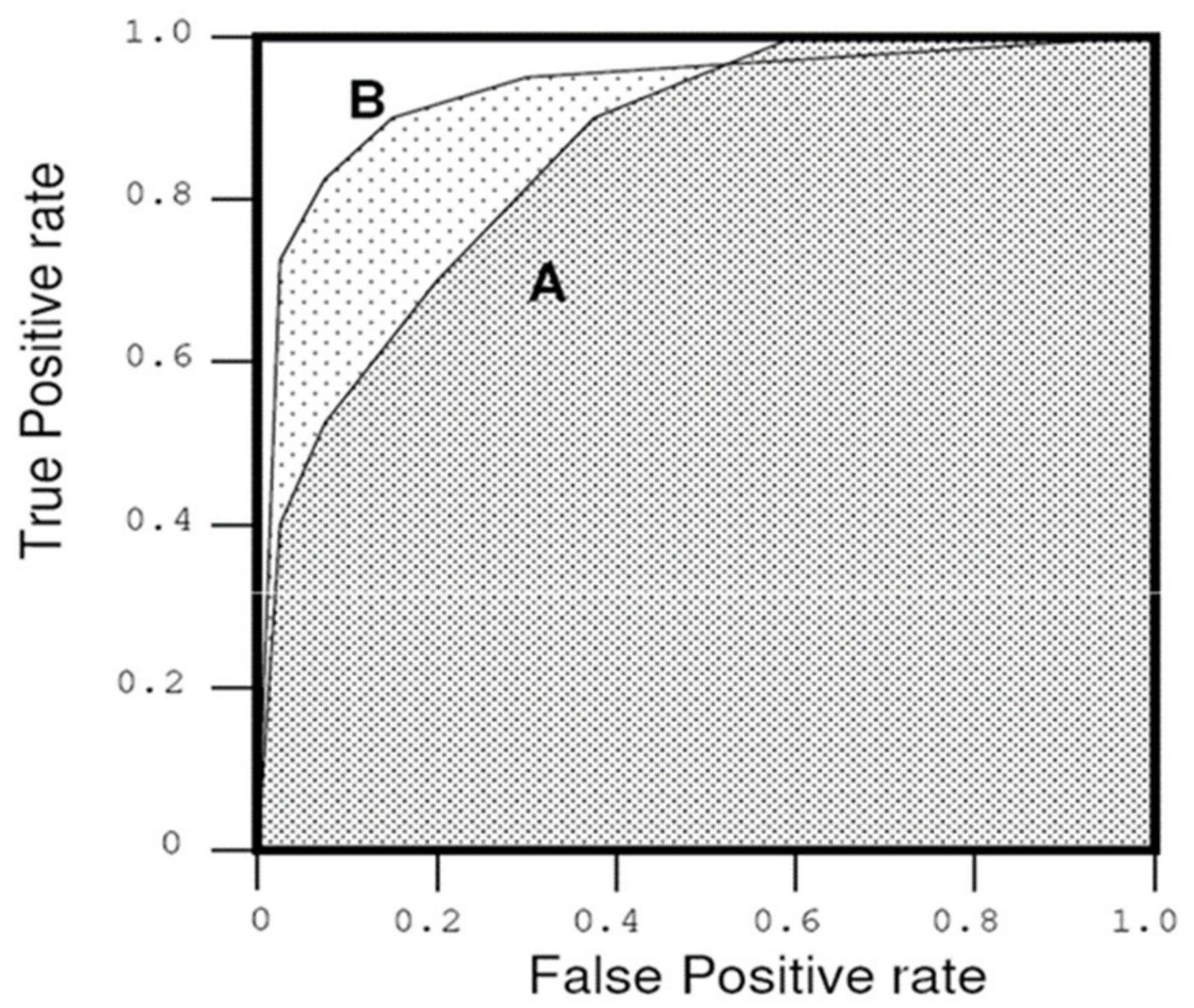
5.4. Results and Analysis
5.5. Performance Measures
- True Positive (TP): Number of instances of correct inferences of an MITM attack possibility when an MITM attack is actually expected to happen;
- False Negative (FN): Number of instances of non-detection when an MITM attack has actually happened;
- False Positive (FP): Number of instances of wrong inferences of an MITM attack possibility when there is no MITM attack;
- True Negative (TN): Number of instances of correct inferences of no MITM attack possibility when there is no MITM attack happening;
- True Positive Rate (TP Rate): Percentage of correct inferences made. The TP rate is calculated as follows:
- False Positive Rate (FP Rate): Percentage of wrong inferences made. The FP rate is calculated as follows:
- Overall Accuracy: Percentage of correct inferences made. The overall accuracy is calculated as follows:
6. Conclusions and Future Works
Author Contributions
Funding
Conflicts of Interest
Appendix A. Detailed Workflow for the Detection of MITM Attacks

Appendix B. Detailed Algorithm Implementation Using Java for Detection of MITM Attacks
References
- Bright, P. Independent Iranian hacker Claims Responsibility for Comodo Hack. Available online: http://www. wired. com/threatlevel/2011/03/comodo_hack (accessed on 11 October 2018).
- Comodo Hacker, A Message from Comodo Hacker. Available online: https://pastebin.com/74KXCaEZ. (accessed on 11 October 2018).
- Scarfone, K.; Mell, P. Guide to Intrusion Detection and Prevention Systems (IDPS). NIST Spec. Publ. 2007, 800, 94. [Google Scholar]
- Agarwal, N.; Hussain, S.Z. A Closer Look at Intrusion Detection System for Web Applications. arXiv, arXiv:1803.06153.
- Brainard, J.G.; Kaliski, B.S., Jr.; Rivest, R.L. Method and apparatus for performing enhanced time-based authentication. U.S. Patent No. US7363494B2, 22 April 2008. [Google Scholar]
- M’Raihi, D.; Machani, S.; Pei, M.; Rydell, J. Totp: Time-Based One-Time Password Algorithm. Available online: https://www.rfc-editor.org/rfc/rfc6238.txt (accessed on 11 October 2018).
- Uymatiao, M.L.T.; Yu, W.E.S. Time-based OTP authentication via secure tunnel (TOAST): A mobile TOTP scheme using TLS seed exchange and encrypted offline keystore. In Proceedings of the 4th IEEE International Conference on Information Science and Technology (ICIST), Shenzhen, China, 26–28 April 2014; pp. 225–229. [Google Scholar]
- Hsieh, W.-B.; Leu, J.-S. Design of a time and location based One-Time Password authentication scheme. In Proceedings of the 7th International Wireless Communications and Mobile Computing Conference (IWCMC), Istanbul, Turkey, 2011; pp. 201–206. [Google Scholar]
- Kemshall, A.C. Time-based authentication. U.S. Patent US9363077B2, 7 June 2016. [Google Scholar]
- Oberheide, J.; Goodman, A.; Czub, C.; Garrity, P. System and method for converting one-time passcodes to app-based authentication. U.S. Patent US20160197914A1, 22 May 2018. [Google Scholar]
- O’Donoghue, K. A New Security Mechanism for the Network Time Protocol. IETF J. Internet Secur. Available online: https://www.ietfjournal.org/a-new-security-mechanism-for-the-network-time-protocol/ (accessed on 31 October 2017).
- NTP Working Group. Network Time Security for the Network Time Protocol. Internet Engineering Task Force, 2017. Available online: https://tools.ietf.org/id/draft-ietf-ntp-using-nts-for-ntp-10.html (accessed on 11 October 2018).
- Bi, Y.; Gaillardon, P.; Hu, X.S.; Niemier, M.; Yuan, J.; Jin, Y. Leveraging Emerging Technology for Hardware Security—Case Study on Silicon Nanowire FETs and Graphene SymFETs. In Proceedings of the 2014 IEEE 23rd Asian Test Symposium, Hangzhou, China, 16–19 November 2014; pp. 342–347. [Google Scholar] [CrossRef]
- Lowe, G. Casper: A compiler for the analysis of security protocols. J. Comput. Secur. 1998, 6, 53–84. [Google Scholar] [CrossRef]
- Panday, K.K. Various SSL/TLS Certificate File Types/Extensions. Available online: https://blogs.msdn.microsoft.com/kaushal/2010/11/04/various-ssltls-certificate-file-typesextensions/ (accessed on 11 October 2018).
- Dinitz, Y.; Itzhak, R. Hybrid Bellman–Ford–Dijkstra algorithm. J. Discret. Algorithms 2017, 42, 35–44. [Google Scholar] [CrossRef]
- Waleed, S.; Faizan, M.; Iqbal, M.; Anis, M.I. Demonstration of single link failure recovery using Bellman Ford and Dijikstra algorithm in SDN. In Proceedings of the 2017 International Conference on Innovations in Electrical Engineering and Computational Technologies (ICIEECT), Karachi, Pakistan, 5–7 April 2017; pp. 1–4. [Google Scholar]
| Input Variables | Physical Distance: Pd (ms)—DV Based | Logical Distance: Ld (ms)—LS Based | ||||||
|---|---|---|---|---|---|---|---|---|
| Network Type | A | B | C | D | A | B | C | D |
| Previous | 100 | 200 | 350 | 500 | 50 | 300 | 400 | 600 |
| Ping | 50 | 150 | 400 | 700 | 20 | 200 | 360 | 550 |
| Status | N | N | A | A | N | N | A | N |
| Margin (%) | 5 | 10 | 15 | 17 | 5 | 7 | 9 | 15 |
| SD Outcome | 90 | 160 | 420 | 540 | 45 | 320 | 390 | 570 |
| dbI | Inference Database at the trusted time server (TTS) |
| NS | Network Status—Current network status |
| NT | Network Type—Current network type; network types include local, national, international, wired, wireless, cellular, metro, wide area network |
| MID | Message ID—Unique message identifier |
| Mwarn | Warning Message sent to A and B |
| TD | Time—Difference between TS and TR |
| TP1 | Ping Time—Response time when machine A pings machine B before sending the message to B |
| TP2 | Ping Time—Response time when machine B pings machine A after receiving the message from A |
| TR | Received Time—Timestamp recorded by the TTS when machine B receives a message from machine A |
| TS | Sent Time—Timestamp recorded by the TTS when machine A sends a message to machine B |
| TTH | Threshold time—A threshold value that is decided based on the table of thresholds of tolerant response time, with the level of margin and network status based on the network type |
| TM | Time margin—Level of margin which will be compared with the timestamp difference value TD percentage; it is determined by averaged data learned previously. |
| Network Type A | |
|---|---|
networkTypevalue:
| Networkstatus: Network status = N
|
Thresholdvalue:
| marginValue:
|
PingRTT:
| mean:
|
standardDev:
| Mean + Standard deviation:
|
| Case 1—Nonsuspicious Outcome | Case 2—Suspicious Outcome |
|---|---|
| Timedifference → 50 | Timedifference → 100 |
|
|
|
|
| Verification: As the above Boolean comparison returns a false, that means that the time difference is within the time limits based on the standard deviation of the average Ping RTT and Threshold time of Network type A. The time difference does not lead to the inference of an anomaly. | Verification: As the above Boolean comparison returns a true, that means that the time difference is outside the time limits based on the standard deviation of the average Ping RTT and Threshold time of Network type A. The time difference does lead to the inference of an anomaly. |
| Result: The TTS will mark this message as not suspicious and not send any notification to A and B. | Result: The TTS will mark this message as suspicious and send necessary notifications to A and B. |
© 2018 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Kang, J.J.; Fahd, K.; Venkatraman, S. Trusted Time-Based Verification Model for Automatic Man-in-the-Middle Attack Detection in Cybersecurity. Cryptography 2018, 2, 38. https://doi.org/10.3390/cryptography2040038
Kang JJ, Fahd K, Venkatraman S. Trusted Time-Based Verification Model for Automatic Man-in-the-Middle Attack Detection in Cybersecurity. Cryptography. 2018; 2(4):38. https://doi.org/10.3390/cryptography2040038
Chicago/Turabian StyleKang, James Jin, Kiran Fahd, and Sitalakshmi Venkatraman. 2018. "Trusted Time-Based Verification Model for Automatic Man-in-the-Middle Attack Detection in Cybersecurity" Cryptography 2, no. 4: 38. https://doi.org/10.3390/cryptography2040038
APA StyleKang, J. J., Fahd, K., & Venkatraman, S. (2018). Trusted Time-Based Verification Model for Automatic Man-in-the-Middle Attack Detection in Cybersecurity. Cryptography, 2(4), 38. https://doi.org/10.3390/cryptography2040038






