An Efficient Tate Pairing Algorithm for a Decentralized Key-Policy Attribute Based Encryption Scheme in Cloud Environments
Abstract
1. Introduction
1.1. Our Contributions
- An efficient Tate pairing algorithm based on multi-base number representation system using point halving (TP-MBNR-PH) with bases 1/2, 3, and 5 has been proposed. This scheme mitigates the cost of bilinear pairing when compared to existing Tate pairing schemes. The efficiency is calculated using the computational costs and pre-computed costs of addition, subtraction, halving, tripling, and quintupling operations.
1.2. Paper Organization
2. Related Work
3. Proposed Work
3.1. Proposed Tate Pairing Algorithm Construction
3.1.1. Bilinear Maps
- Bilinearity: = , where .
- Computability: The bilinear map e is efficiently computable by for any pairs.
- Non-degeneracy: . This means all pairs of the source group do not map to the identity of the target group.
3.1.2. Point Halving (PH)
3.1.3. The Double-Base Number System (DBNS)
3.1.4. Multi-Base Number Representation (MBNR)
3.1.5. Proposed Tate Pairing Algorithm Based on Multi-Base Number Representation System Using Point Halving (TP-MBNR-PH)
| Algorithm 1. TP-MBNR-PH | |
| Input: An integer , , and , , Output: | |
| 1. | |
| 2. | |
| 3. | |
| 4. | |
| 5. | |
| 6. | |
| 7. | |
| 8. | |
| 9. | |
| 10. | |
| 11. | |
| 12. | |
| 13. | |
| 14. | |
| 15. | |
| 16. | |
| 17. | |
| 18. | |
| 19. | |
| 20. | |
| 21. | |
| 22. | |
| 23. | |
| 24. | |
| 25. | |
| 26. | |
| 27. | |
| 28. | |
| 29. | |
| 30. | |
| 31. | |
3.1.6. Experimental Results
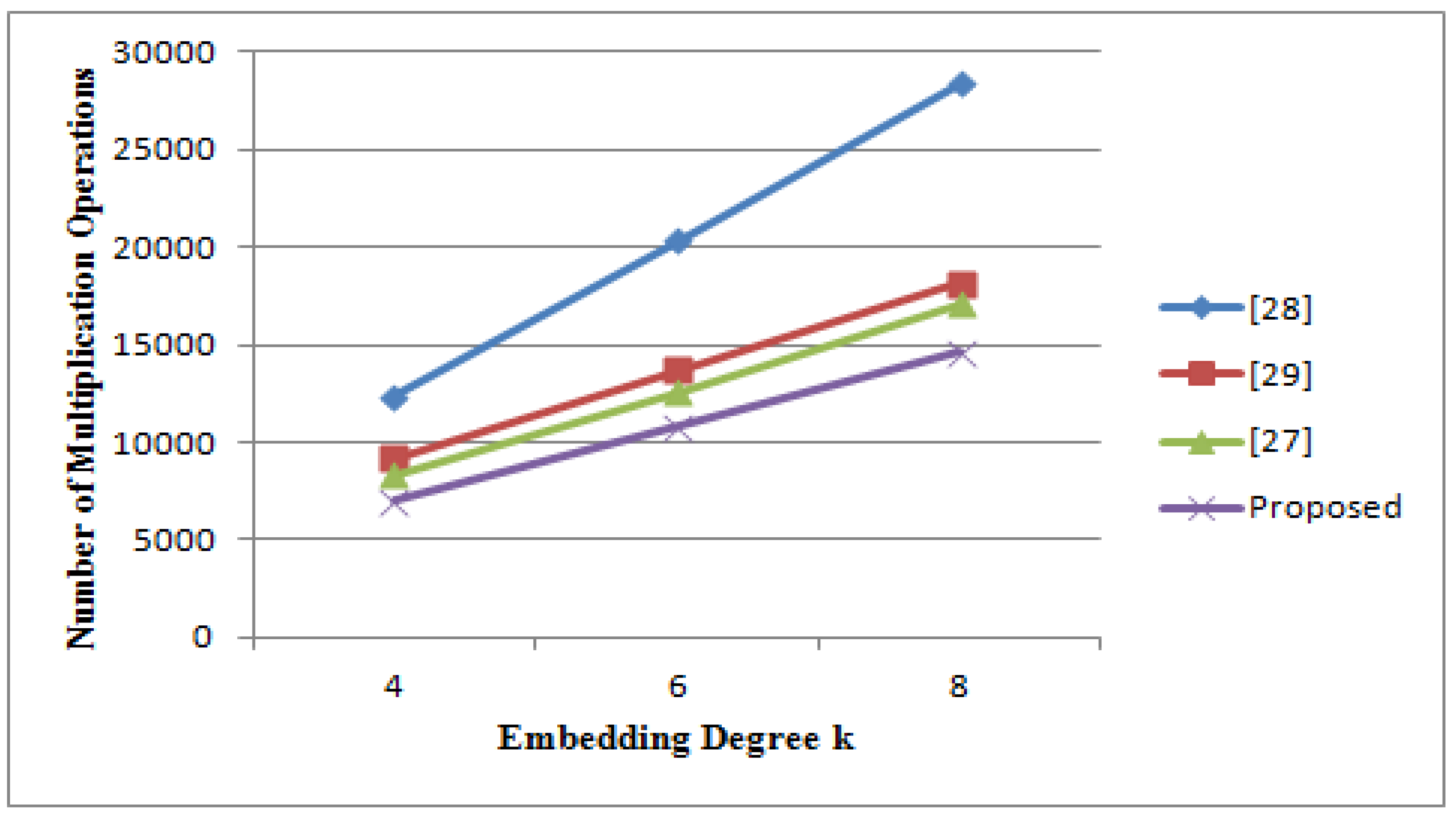
3.1.7. Efficiency of the Proposed Algorithm
3.2. Applying the Proposed TP-MBNR-PH in a Decentralized KP-ABE Scheme
- Take input as a security parameter and it generates the bilinear group with prime order Let be the bilinear map and are generators of the group . The number of authorities are denoted as : monitor attributes i.e., .
- It is executed by each AA to randomly generate the Security parameter of authority and public parameter of authority :Each specifies as the minimum number of attributes required to satisfy the access structure
- The attribute set of the user is . generates and polynomial for each node (including the leaves) . For each node the degree of the polynomial is where is the threshold value of that node. For the root node , set . For any other node , . Now decryption key for the user is generates as follows:
- Attribute set for the message is Data owner of message randomly chooses and output the ciphertext as follows:where denotes the index set of the authorities.
- In order to decrypt , the user , computes as follows:
3.2.1. Anonymous Key-Issuing Protocol
- The two-party protocol (2PC) is used for the interaction between the user and the attribute authority . The 2PC protocol takes from user from and return and to .
- Once the 2PC protocol gets executed, the user now computes and then sends to .
- Attribute Authority computes , , , and proof of knowledge with the help of and send them to the user:
- User exponentiates the received values by to get the decryption keys.
3.2.2. Proposed Scheme: Proof of Security
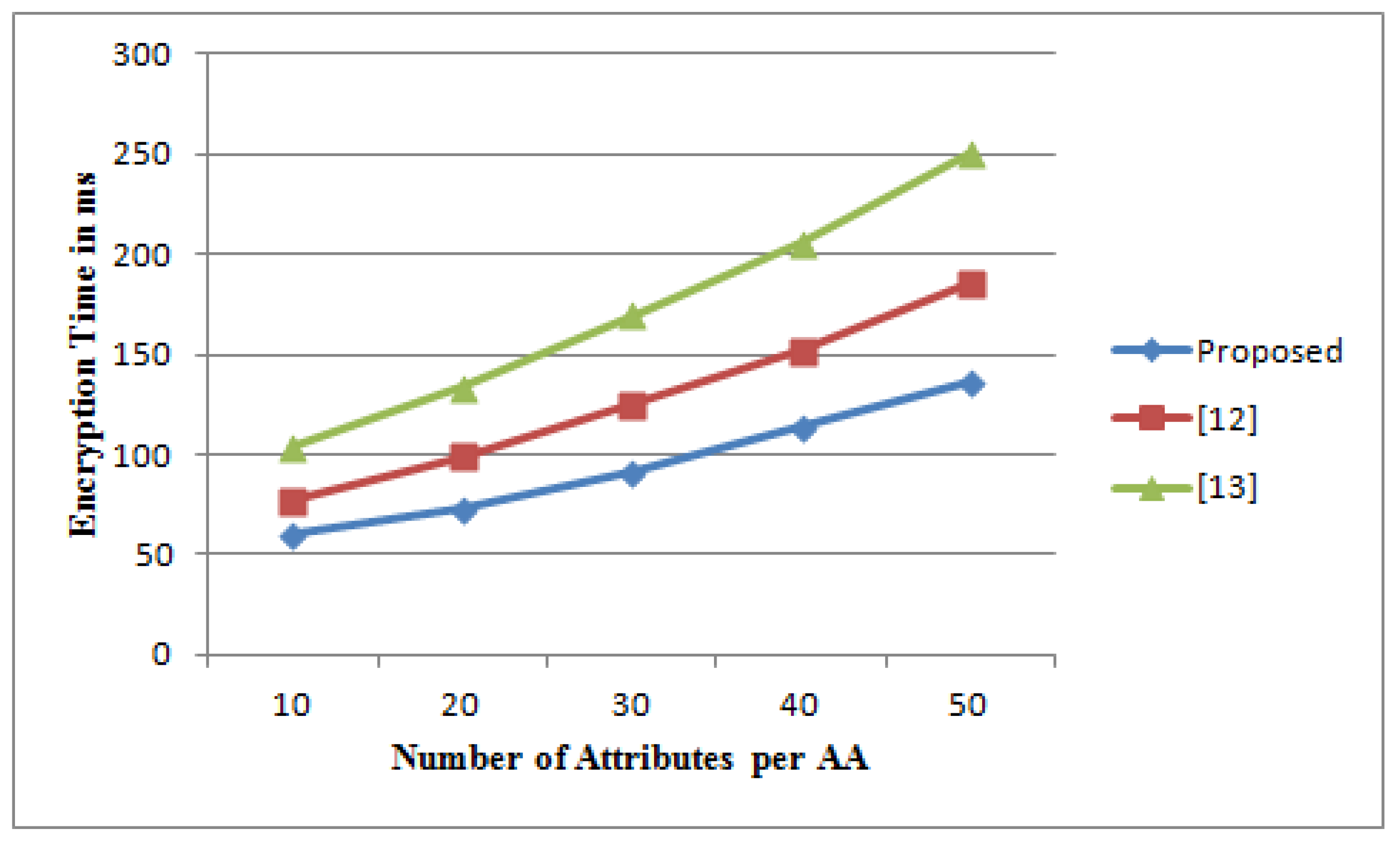
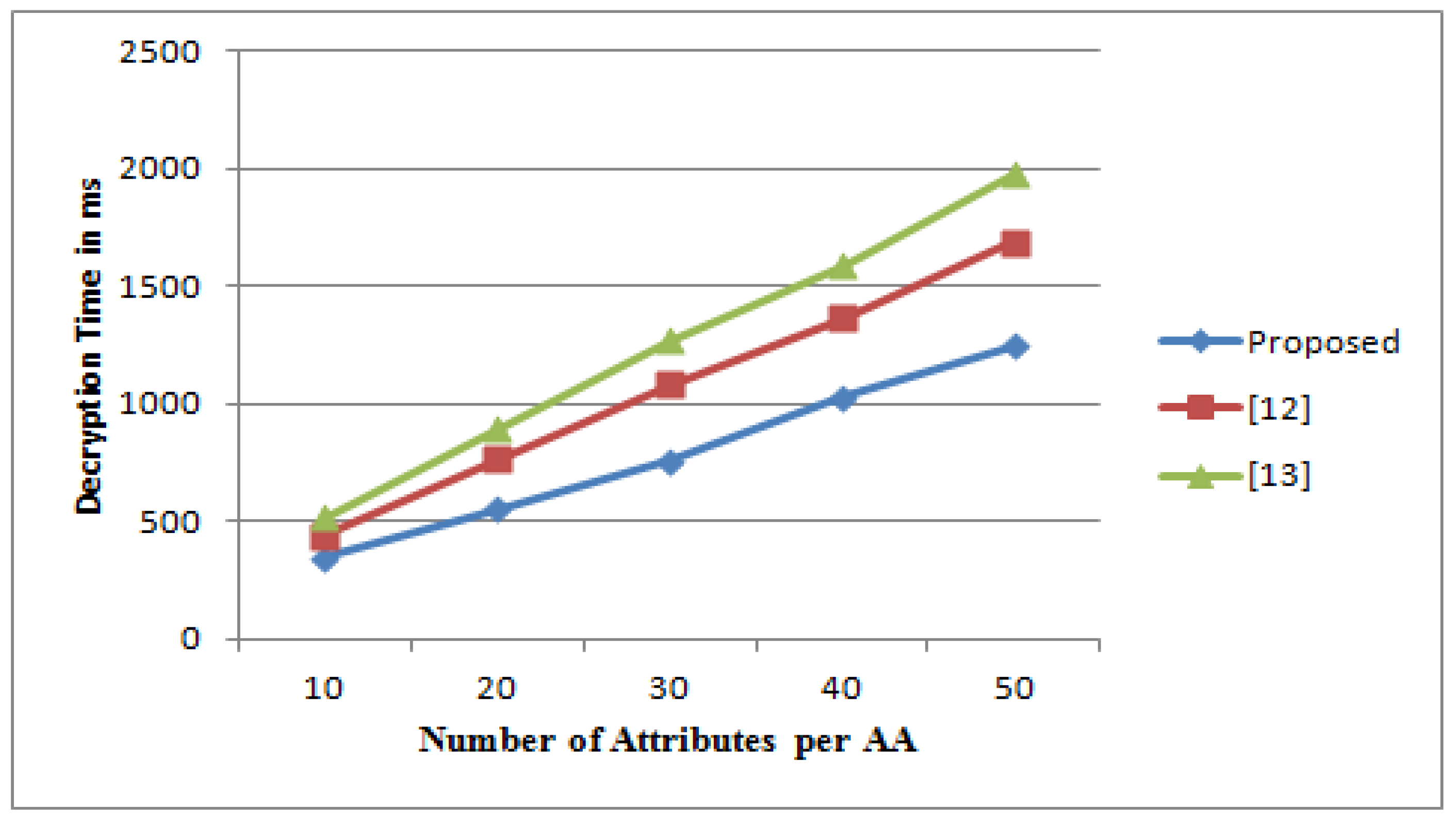
3.2.3. Experimental Results
4. Conclusions
Author Contributions
Funding
Acknowledgments
Conflicts of Interest
References
- Sahai, A.; Waters, B. Fuzzy identity-based encryption. In Advances in Cryptology—EUROCRYPT 2005; Lecture Notes in Computer Science; Springer: Berlin, Germany, 2005; Volume 3494, pp. 457–473. [Google Scholar]
- Nali, D.; Adams, C.; Miri, A. Using threshold attribute based encryption for practical biometric-based access control. Int. J. Netw. Secur. 2005, 1, 173–182. [Google Scholar]
- Goyal, V.; Pandey, O.; Sahai, A.; Waters, B. Attribute based encryption for fine-grained access control of encrypted data. In Proceedings of the 13th ACM Conference on Computer and Communications Security (CCS ’06), Alexandria, VA, USA, 30 October–3 November 2006; pp. 89–98. [Google Scholar]
- Ostrovsky, R.; Sahai, A.; Waters, B. Attribute-based encryption with non-monotonic access structures. In Proceedings of the 14th ACM Conference on Computer and Communications Security (CCS ’07), Alexandria, VA, USA, 29 October–2 November 2007; pp. 195–203. [Google Scholar]
- Attrapadung, N.; Libert, B.; de Panafieu, E. Expressive key policy attribute-based encryption with constant-size ciphertexts. In Public Key Cryptography—PKC 2011; Springer: Berlin, Germany, 2011; Volume 6571, pp. 90–108. [Google Scholar]
- Bethencourt, J.; Sahai, A.; Waters, B. Ciphertext-policy attribute-based encryption. In Proceedings of the IEEE Symposium on Security and Privacy (SP ’07), Oakland, CA, USA, 20–23 May 2007; pp. 321–334. [Google Scholar]
- Cheung, L.; Newport, C. Provably secure ciphertext policy ABE. In Proceedings of the 14th ACM Conference on Computer and Communications Security (CCS ’07), Alexandria, VA, USA, 29 October–2 November 2007; pp. 456–465. [Google Scholar]
- Nishide, T.; Yoneyama, K.; Ohta, K. Attribute-based encryption with partially hidden encryptor-specified access structures. In Applied Cryptography and Network Security (ACNS 2008); Springer: Berlin, Germany, 2008; pp. 111–129. [Google Scholar]
- Emura, K.; Miyaji, A.; Omote, K.; Nomura, A.; Soshi, M. A ciphertext-policy attribute-based encryption scheme with constant ciphertext length. Int. J. Appl. Cryptogr. 2010, 2, 46–59. [Google Scholar] [CrossRef]
- Liang, X.; Cao, Z.; Lin, H.; Xing, D. Provably secure and efficient bounded ciphertext policy attribute based encryption. In Proceedings of the 4th International Symposium on ACM Symposium on Information, Computer and Communications Security (ASIACCS ’09), Sydney, Australia, 10–12 March 2009; pp. 343–352. [Google Scholar]
- Chase, M.; Chow, S.S. Improving privacy and security in multi-authority attribute-based encryption. In Proceedings of the 16th ACM Conference on Computer and Communications Security, New York, NY, USA, 9–13 November 2009; pp. 121–130. [Google Scholar]
- Rahulamathavan, Y.; Veluru, S.; Han, J.; Li, F.; Rajarajan, M.; Lu, R. User Collusion Avoidance Scheme for Privacy-Preserving Decentralized Key-Policy Attribute-Based Encryption. IEEE Trans. Comput. 2016, 65, 2939–2946. [Google Scholar] [CrossRef]
- Yang, Y.; Chen, X.; Chen, H.; Du, X. Improving Privacy and Security in Decentralizing Multi-Authority Attribute-Based Encryption in Cloud Computing. IEEE Access 2018, 6, 18009–18021. [Google Scholar] [CrossRef]
- Chase, M. Multi-authority attribute based encryption. In Theory of Cryptography; Springer: Berlin, Germany, 2007; pp. 515–534. [Google Scholar]
- Lin, H.; Cao, Z.; Liang, X.; Shao, J. Secure threshold multi authority attribute based encryption without a central authority. Inf. Sci. 2010, 180, 2618–2632. [Google Scholar] [CrossRef]
- Lewko, A.; Waters, B. Decentralizing attribute-based encryption. In Annual International Conference on the Theory and Applications of Cryptographic Techniques; Springer: Berlin/Heidelberg, Germany, 2011; pp. 568–588. [Google Scholar]
- Waters, B. Ciphertext-policy attribute-based encryption: An expressive, efficient, and provably secure realization. In International Workshop on Public Key Cryptography; Springer: Berlin/Heidelberg, Germany, 2011; pp. 53–70. [Google Scholar]
- Han, J.; Susilo, W.; Mu, Y.; Yan, J. Privacy-preserving decentralized key-policy attribute-based encryption. IEEE Trans. Parallel Distrib. Syst. 2012, 23, 2150–2162. [Google Scholar] [CrossRef]
- Ge, A.; Zhang, J.; Zhang, R.; Ma, C.; Zhang, Z. Security analysis of a privacy—preserving decentralized key-policy attribute-based encryption scheme. IEEE Trans. Parallel Distrib. Syst. 2013, 24, 2319–2321. [Google Scholar] [CrossRef]
- Fong, K.; Hankerson, D.; Lopez, J.; Menezes, A. Field Inversion and Point Halving Revisited. IEEE Trans. Comput. 2004, 53, 1047–1059. [Google Scholar] [CrossRef]
- Ciet, M.; Joye, M.; Lauter, K.; Montgomery, P.L. Trading Inversions for Multiplications in Elliptic Curve Cryptography. Des. Codes Cryptogr. 2006, 39, 189–206. [Google Scholar] [CrossRef]
- Dimitrov, V.S.; Imbert, L.; Mishra, P.K. Fast Elliptic Curve Point Multiplication using Double-Base Chains. Cryptol. Epr. Arch. 2005, 2005, 69. [Google Scholar]
- Dimitrov, V.; Imbert, L.; Mishra, P. The double-base number system and its application to elliptic curve cryptography. Math. Comput. 2008, 77, 1075–1104. [Google Scholar] [CrossRef]
- Wong, K.W.; Edward, C.W.; Lee, L.M.; Liao, X. Fast elliptic scalar multiplication using new double-base chain and point halving. Appl. Math. Comput. 2006, 183, 1000–1007. [Google Scholar] [CrossRef]
- Mishra, P.K.; Dimitrov, V. Efficient quintuple formulas for elliptic curves and efficient scalar multiplication using multibase number representation. In International Conference on Information Security; Springer: Berlin/Heidelberg, Germany, 2007; pp. 390–406. [Google Scholar]
- Ismail, A.M.; Said, M.R.M.; Atan, K.M.; Rakhimov, I.S. An Algorithm to enhance Elliptic Curves scalar Multiplication Combining MBNR with point halving. Appl. Math. Sci. 2010, 4, 259–261. [Google Scholar]
- Zhao, C.; Zhang, F.; Huang, J. Efficient Tate Pairing Computation Using Double-Base Chains. Sci. China Ser. F Inf. Sci. 2008, 51, 1096–1105. [Google Scholar] [CrossRef]
- Izu, T.; Takagi, T. Efficient computations of the Tate pairing for the large MOV degrees. In International Conference on Information Security and Cryptology; Springer: Berlin/Heidelberg, Germany, 2003; pp. 283–297. [Google Scholar]
- Kobayashi, T.; Aoki, K.; Imai, H. Efficient algorithms for Tate pairing. IEICE Trans. Fundam. Electron. Commun. Comput. Sci. 2006, 1, 134–143. [Google Scholar] [CrossRef]
- Chandrasekaran, B.; Balakrishnan, R.; Nogami, Y. Secure Data Communication using File Hierarchy Attribute Based Encryption in Wireless Body Area Networks. J. Commun. Softw. Syst. 2018, 14, 75–81. [Google Scholar] [CrossRef]
| N | B = {2, 3} | B = {2, 3, 5} | B = {2, 3, 5, 7} |
|---|---|---|---|
| 10 | 5 | 8 | 10 |
| 20 | 12 | 32 | 48 |
| 50 | 72 | 489 | 1266 |
| 100 | 402 | 8425 | 43,777 |
| 150 | 1296 | 63,446 | 586,862 |
| 200 | 3027 | 316,557 | 4,827,147 |
| 300 | 11,820 | 4,016,749 | 142,196,718 |
| Operation | Cost | Pre-Computed Cost | |||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|
| TADD | 1 | - | 2.5 | 1 | 1 | 3 | 2 | - | - | 7 | 1 |
| TSUB | 1 | - | - | 1 | 1 | 2+3 | 2 | - | 1 | - | - |
| THAL | 1 | 1 | 3.5 | - | - | 4 | 2 | - | - | - | - |
| TTRL | 3 | 1 | 2 | 1 | 4 | 9 | - | 1 | - | - | - |
| TQNT | 4 | 1 | 5 | 1 | 4 | 12 | - | 2 | - | - | - |
© 2018 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Chandrasekaran, B.; Balakrishnan, R. An Efficient Tate Pairing Algorithm for a Decentralized Key-Policy Attribute Based Encryption Scheme in Cloud Environments. Cryptography 2018, 2, 14. https://doi.org/10.3390/cryptography2030014
Chandrasekaran B, Balakrishnan R. An Efficient Tate Pairing Algorithm for a Decentralized Key-Policy Attribute Based Encryption Scheme in Cloud Environments. Cryptography. 2018; 2(3):14. https://doi.org/10.3390/cryptography2030014
Chicago/Turabian StyleChandrasekaran, Balaji, and Ramadoss Balakrishnan. 2018. "An Efficient Tate Pairing Algorithm for a Decentralized Key-Policy Attribute Based Encryption Scheme in Cloud Environments" Cryptography 2, no. 3: 14. https://doi.org/10.3390/cryptography2030014
APA StyleChandrasekaran, B., & Balakrishnan, R. (2018). An Efficient Tate Pairing Algorithm for a Decentralized Key-Policy Attribute Based Encryption Scheme in Cloud Environments. Cryptography, 2(3), 14. https://doi.org/10.3390/cryptography2030014





