1. Introduction
Digital images are the most common multimedia used for both communication and entertainment. In everyday life, people encounter digital information not only on social networks, most of which are based on published images or videos, but also in modern means of communication, such as Zoom, Google Meet, Mesenger, WhatsApp, etc. To a large extent, journalistic and lifestyle publications are presented through digital formats, which significantly increases their audience. And while all these platforms, applications, and sites rely on built-in protections and good intentions on the part of users, the issue of transmitting sensitive digital information through unprotected communicational networks is not so simple.
In communication networks where security is of paramount importance, the secure transmission of sensitive information can be roughly divided into two directions: encryption of the communication channel or encryption of the information itself. The second direction is a more common object of research that considers the encryption of the sensitive information itself and its subsequent transmission over public unprotected communication networks. When this sensitive information is a digital image, the main problem is the implementation of such an encryption scheme that gives satisfactory results not only in terms of encryption level, but also in terms of reliability and speed, with minimal losses throughout recovery.
In the scientific literature of the last decade, a variety of approaches to image encryption have been observed, with researchers combining different techniques and developing new algorithms to enhance encryption security and efficiency. The main categories and commonly used algorithms include the following: Symmetric cryptographic algorithms, including block ciphers such as AES (Advanced Encryption Standard) [
1,
2] and stream ciphers such as Rivest Cipher 4 [
3,
4]; asymmetric cryptographic algorithms, such as ECC (Elliptic Curve Cryptography), which offers shorter keys while maintaining the same level of security, making it attractive for resource-constrained applications [
5,
6]; permutation- and diffusion-based algorithms, which aim to disrupt the statistical structure of the image, making it unrecognizable [
7,
8]; and quantum-resistant algorithms [
9,
10,
11,
12], among others.
Literature Review: Three main directions in the encryption algorithms that are subject to active research and modification can be defined: innovative—such as the encryption algorithms based on artificial neural networks (ANNs); fundamental—the most common among them is the One-Time Pad (OTP) algorithm; and eccentric—which is where chaos-based encryption algorithms fall.
ANN in encryption algorithms: ANN-based encryption algorithms [
13,
14,
15,
16] are an innovative approach that combines the power of machine learning with cryptography. ANNs can be trained to perform cryptographic tasks such as transforming data into ciphertext [
17], are used to generate pseudorandom keys that are difficult to predict [
18], and can create complex cryptographic schemes [
19]. Among the advantages of ANN encryption algorithms are self-adaptability, resistance to traditional attacks, generation of personalized cryptographic schemes for specific applications, and speed of operation (after going through the training process). The disadvantages of this type of encryption methods include the requirement for large volumes of training data, high computational complexity, vulnerability to specific attacks (such as those that exploit their structure), and some difficulties related to security verification.
One-Time Pad based algorithms: One of the fundamental algorithms for image encryption is the One-Time Pad (OTP) algorithm. It is widely used due to its easy implementation and high level of security [
20,
21,
22,
23,
24]. In this case, if the key is completely random, equal in length to the message (or image), and is never reused, OTP provides theoretically perfect security. In image encryption, OTP algorithms are an encryption technique that requires the use of a one-time pre-shared key with a size equal to that of the image or larger. Encryption is performed by applying a bitwise XOR between the data and the key. This technique is one of the most elementary and generally represents pairing the image with the generated secret key. The algorithm is equivalent to the masking method in signal encryption. In this type of algorithm, to achieve a high level of security, the complexity of the generated key is relied on. The advantages of OTP algorithms for image encryption include high security and easy implementation. On the other hand, the following challenges associated with implementing OTP algorithms for image encryption should not be overlooked: the large key size; ensuring secure storage and transmission of the key; and achieving complete randomness of the key.
Chaos in encryption algorithms: There is a growing trend in the application of encryption algorithms based on chaotic systems. What makes chaos attractive for use as a basis for developing cryptosystems is mainly its random behavior, sensitivity to initial conditions and the set of parameters that meet the classical Shannon requirements for confusion and diffusion [
25]. Algorithms based on chaos show some extremely good properties in many aspects in terms of security, complexity, speed, etc. Such algorithms can be based on the use of one-dimensional and two-dimensional chaotic maps—used to generate pseudorandom values that shift and modify pixels [
26,
27,
28,
29]; fractal chaotic maps—use fractal structures generated by chaos [
30,
31,
32]; three-system chaotic maps—generate three chaotic sequences to encrypt the RGB components separately [
33,
34]; and adaptive chaotic algorithms, in which chaotic parameters are tuned based on the histogram or entropy of the input image [
35,
36], among others [
37,
38,
39,
40,
41,
42]. The advantages of chaos-based image encryption algorithms are high security due to the complex dynamics and sensitivity to the initial conditions and parameters of chaotic systems; low computational cost; and flexibility—they are easily adapted for different types of images.
The choice of an appropriate algorithm depends on the specific requirements of the application, including the level of security, computational resources and resistance to various types of attacks. This is precisely what determines the combination of more than one approach to image encryption and the construction of new schemes for the secure transmission of sensitive information via unprotected communicational networks.
Contribution: This article proposes a modification of an image encoding scheme based on a standard OTP algorithm, modified by implementing a multilayer structure with the implementation of a chaotic signal and data from the OTP approximating various encoding functions. By implementing a subsequent chaotic synchronization scheme, the recovery of the transmitted encoded image is achieved. Key points of the proposed modification are the higher degree of reliability achieved by forming a unique encryption key that is not repeated and is not used repeatedly, making the OTP scheme practically unbreakable; the use of chaotic synchronization based on feedback control leads to high quality image recovery; and the used basic structure of the OTP algorithms preserves the efficiency of the subsequent operations of compression, transfer, and storage of images.
The main goals of the developed scheme are to achieve a high degree of security and efficiency in encoding while preserving the quality of the restored images during decoding.
Our main contributions are as follows:
This article proposes an innovative multilayer cryptographic scheme based on the OTP algorithm, integrating static, chaotic, and neural encoding keys with the aim of enhancing security and protection against cryptographic attacks.
The proposed algorithm implements chaotic synchronization of two identical Chua chaotic systems through feedback control, which ensures reliable image encoding and decoding, and enables the concealment of the source of cryptographic information.
An ANN generator has been implemented to provide an additional neural key based on the approximation of time-dependent functions. This reduces the influence of the human factor and adds complex dynamic behavior.
In the encoding process, a scrambling-based encryption of the three-color channels is successfully implemented using the same chaotic signal that was used to generate the chaotic encoding key.
Through simulations and statistical analysis of key metrics, the algorithm has been proven to be highly effective against various types of attacks.
The rest of this article is organized as follows: In
Section 2, the basic method for implementing chaotic synchronization, through feedback control with one-way coupling, the ANN apparatus for approximating temporal functions and classical approaches for analyzing the coding rate and image reconstruction quality are presented. In
Section 3, the proposed modified OTP image coding scheme is described in detail. In
Section 4, analytical and simulation results for coding different images using the proposed approach with the implementation of a synchronization scheme using FFNN for approximating three types of functions are presented. The conclusion and inferences from the obtained results are presented in the last section.
2. Preliminaries
Image encoding mainly aims at a high level of protection, quality preservation, data compression, efficiency preservation during transfer and storage, etc. The use of advanced security mechanisms and intelligent tools is essential to achieve these goals and maintain reliability. The current Section presents a detailed presentation of the methods and techniques used to implement a modified image encoding scheme
2.1. Synchronization of Chaotic Systems Based on Feedback Control
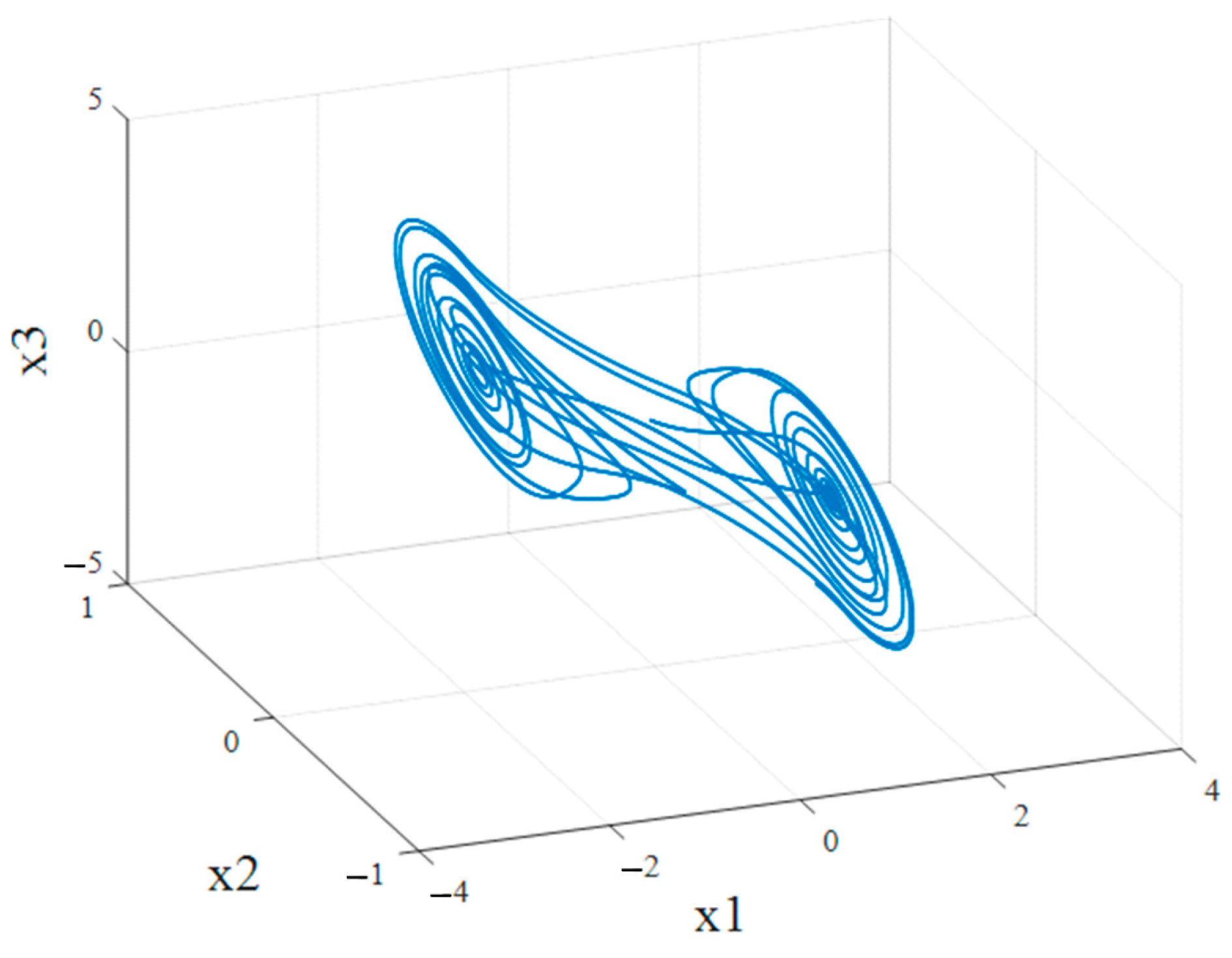
Most of the chaos-based communication systems are based on synchronized chaotic systems. This means that under certain circumstances the complex and highly sensitive nonlinear dynamics of the coupled chaotic systems are synchronized and the resulting synchronous state can be used in the communication scheme in several different ways.
One of the remarkable features of chaotic communication is the possibility of implementation at the physical level. From the point of view of cryptography, chaos has many desirable properties, namely complexity, ergodicity, transitivity, determinism and sensitivity to initial conditions and perturbations [
43]. Cryptography is also the topic that receives the majority of publications in the field of chaos applications.
Chaos is particularly attractive for use as a basis for the development of cryptosystems due to its randomness, strong sensitivity to initial conditions and parameters, which fully satisfy the classical criteria for confusion and diffusion [
44]. Chaos-based algorithms exhibit some exceptionally good properties in many aspects in terms of security, complexity, speed, etc.
Considering that chaotic systems are inherently nonlinear systems, some of the established theories and methods for controlling nonlinear systems can be used in the synchronization of chaotic systems. The chaotic systems under consideration are of a type that allows them to be described by ordinary differential and difference equations.
The synchronization method used is based on feedback control, i.e., an additional signal proportional to the mismatch is fed to one of the systems. Avoiding the strict mathematical description of the method presented in [
45], we choose to refer to the lighter algorithmic interpretation.
Let’s consider a nonlinear SISO system in the following simplified form:
where
is the state vector,
is a vector of inputs, and
is the vector of outputs.
The relative degree of the system r at the point x
0 is determined, if
If the system has relative degree r
n, where n is the order of the system (1), the coordinate transformation functions are formed:
by forming a mapping of the type
If r < n, it is always possible to find n-r additional functions, such that the transforming map (4) has a Jacobian matrix of full rank at x
0, under the additional condition that
, for all r + 1 ≤ i < n and for
in a neighborhood of x
0. In this case, the additional equations to the dynamics of the system are defined by
By means of the transformation z = S(x) from (4) and provided that the system (1) has a relative degree r at x
0, it can be transformed into
At r = n, a(z) ≠ 0, for each
, the new input will be
whereby system (6) will become a linear control system described as
In the synchronization tasks of chaotic systems, a synchronization scheme is most often synthesized between two identical, continuous systems with a one-way connection between them.
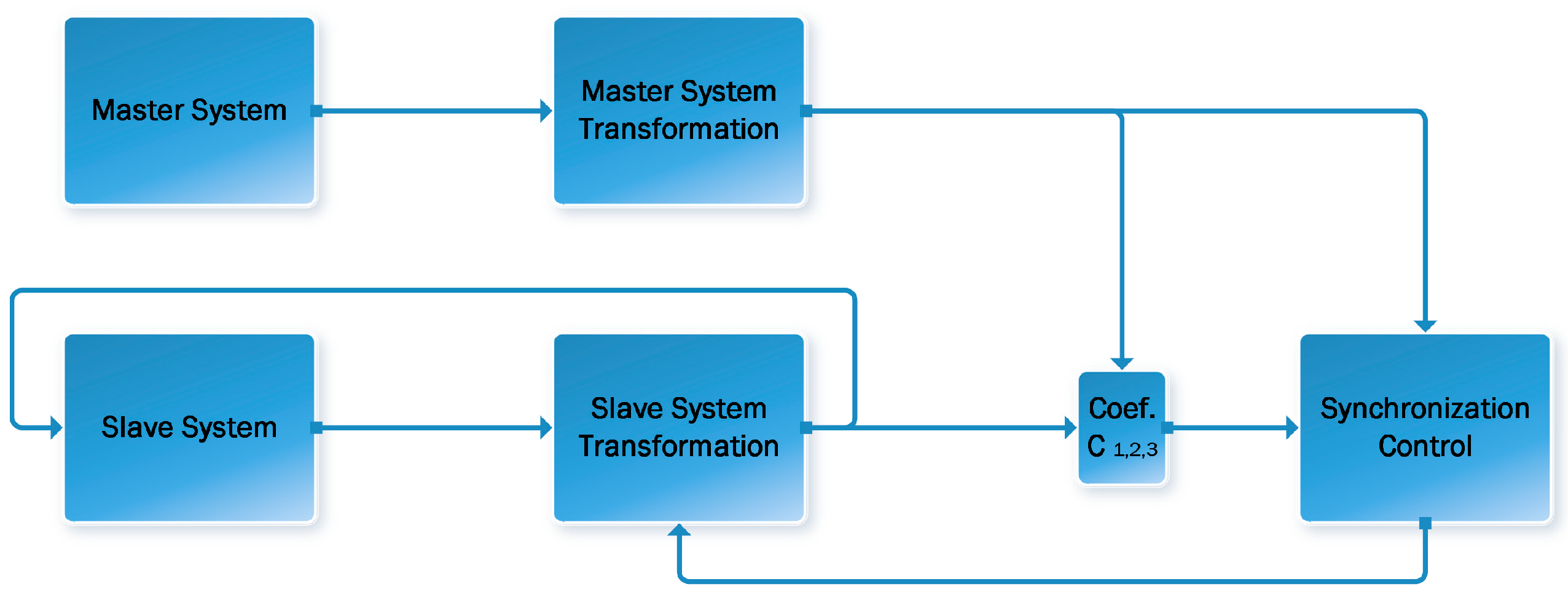
The system that provides the synchronization signal is called the control system (9), and the one that receives this signal and adjusts its dynamics to that of the control system is called the controlled (slave) system (10), generalized block diagram of the synchronization process is presented on
Figure 1. The two can be represented by the following generalized notation:
Setting
defined by (4), if there is a relative degree r (r ≤ n), the system (10) presented in a more compressed form can be transformed into
where A
rxr has the canonical form of Brunowski [
46],
,
and
are smooth mappings that can be determined using (6) and the new input v from (7). System (9) is transformed similarly.
After transforming the master and slave systems, the disagreement system is defined by
, as
with control that makes (12) asymptotically stable, defined by the following formula:
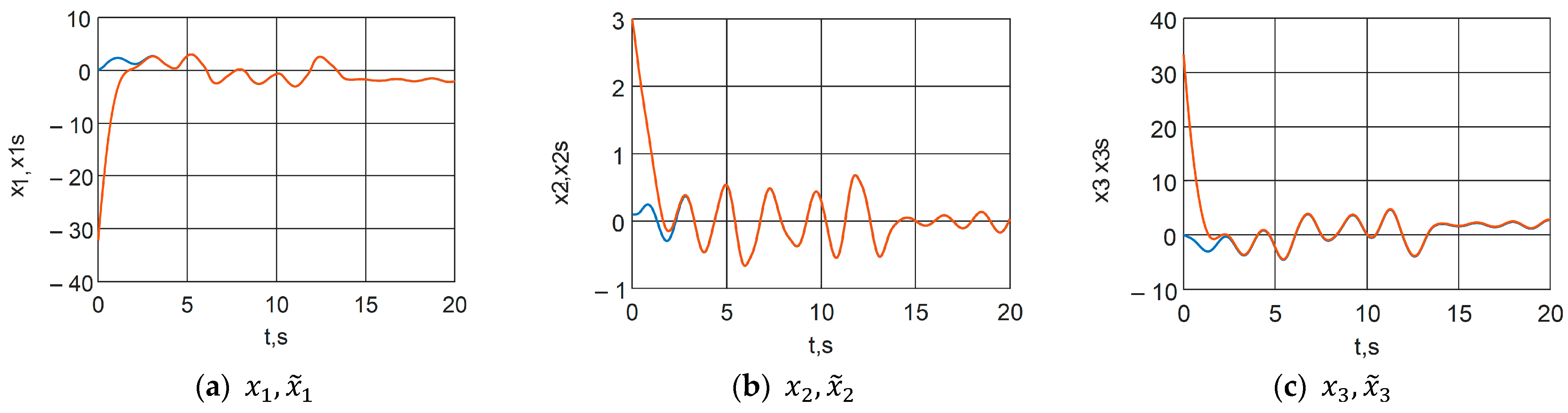
Through the synthesized control, it is guaranteed that systems (9) and (10) can be synchronized asymptotically, i.e., .
2.2. Artificial Neural Network for Time Function Approximation
The second main element in the developed image coding scheme is the integration of the ANN. As already mentioned, the neural network aims at a more complex multilayer coding based on the OTP algorithm. The main idea behind the use of ANNs is to hide the original source of obtaining the coding key. ANNs are applied to solve problems of a diverse nature, such as classifiers, associative memories, simulators, approximators, etc. In the current implementation, the main task of ANNs is the approximation of time functions and subsequent generation of a coding key in the form of an image.
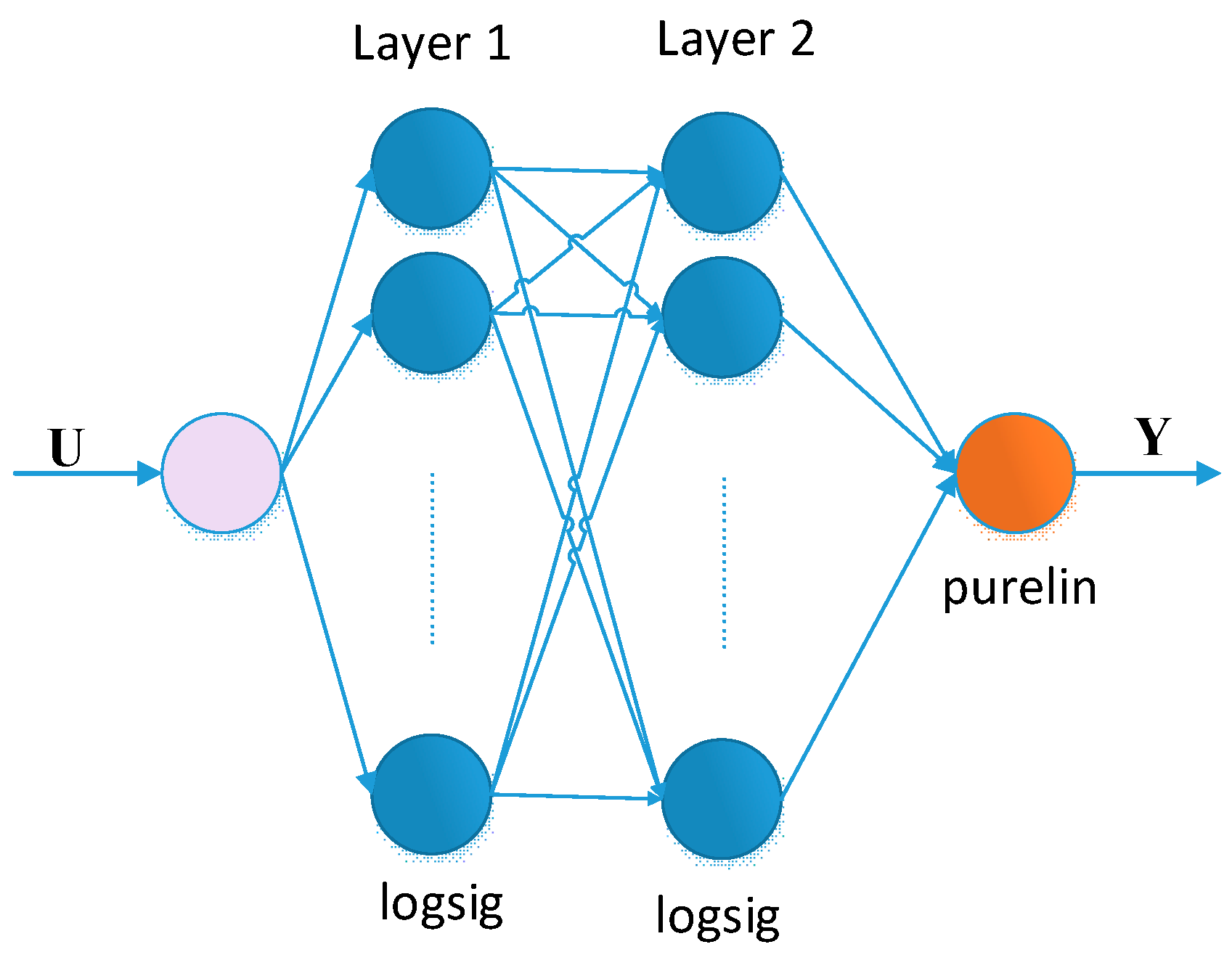
It is known that ANNs give very good results in approximating functions. The submission of values from numerical series as a data set is more inherent to artificial networks of the FFNN type, such as the ANN used in the current case.
The used multilayer neural network has one input and one output, with connections between neurons only in adjacent layers. There are two hidden layers between the input and output of the network, containing computational units, respectively 10 neurons in the first and 20 neurons in the second. The choice of the number of hidden layers and the neurons in them is based on Stone’s theorem and a generalization presented in [
47]. The input-output relationship of each neuron is described by an input x
i, an output y, connection weights w
i, a threshold value θ and a differentiable function ϕ.
Figure 2 shows the architecture of the neural network used in this encrypting scheme.
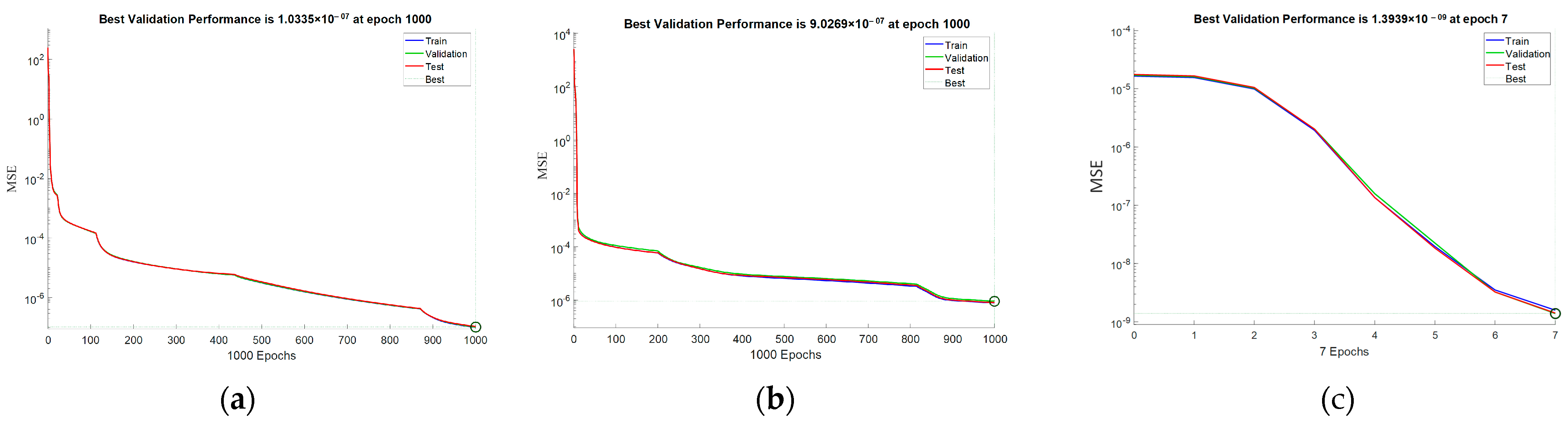
The network is trained using the Levenberg-Marquardt backpropagation method. This method is considered the fastest, since its efficiency is mainly influenced by the rational choice of the regularization factor used to calculate the updated term of the parameter vector wi of the neural network. The regularization factor is functionally related to the gradient of the sum of the mean square errors, which allows us to overcome the limitation of the single-output ANN algorithm and makes it effective for function approximation. In terms of memory, this training algorithm requires memory of the order of O(w2), where w is the number of weight coefficients in the network.
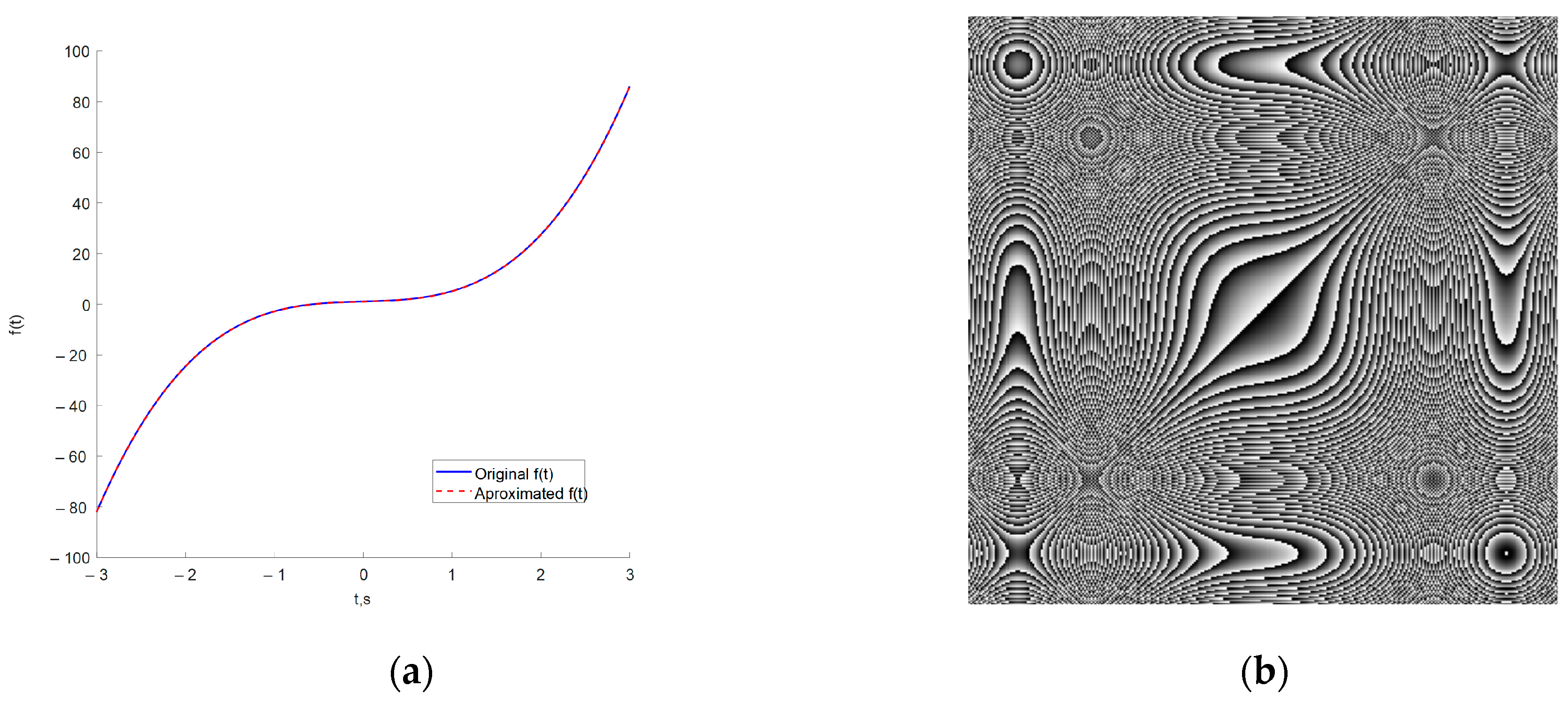
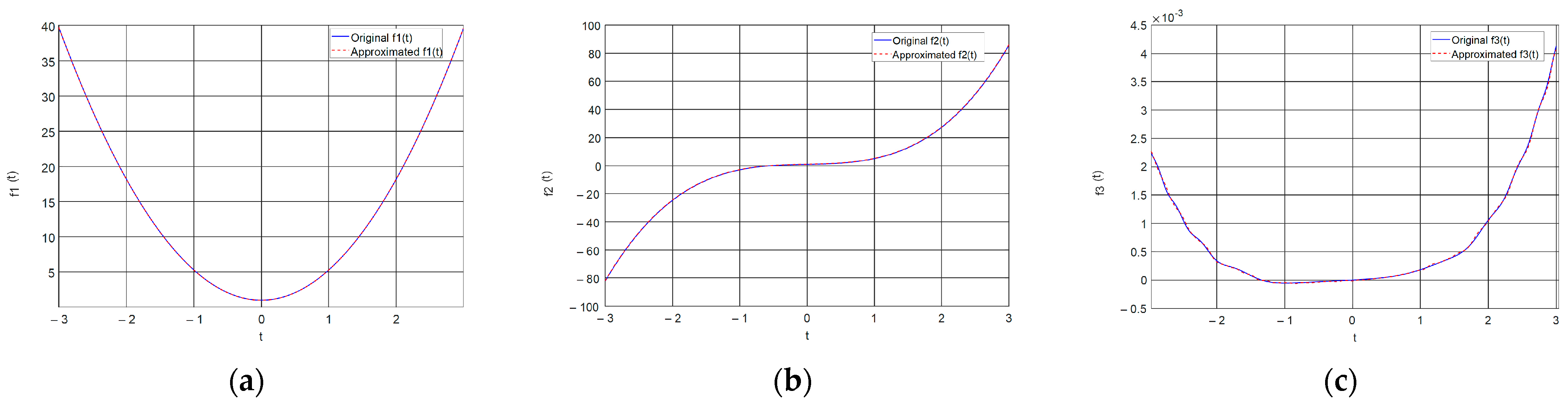
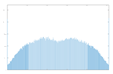
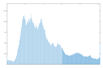
The graphical results of approximating the function
and the resulting image, which will be used to form an encryption key are shown in
Figure 3.
From the images shown in
Figure 3, it can be seen that the used ANN copes with the task of approximating complex time characteristics, as the achieved mean square error (MSE) is of the order of 1 × 10
−7.
2.3. Methods for Statistical Analysis in Image Encryption
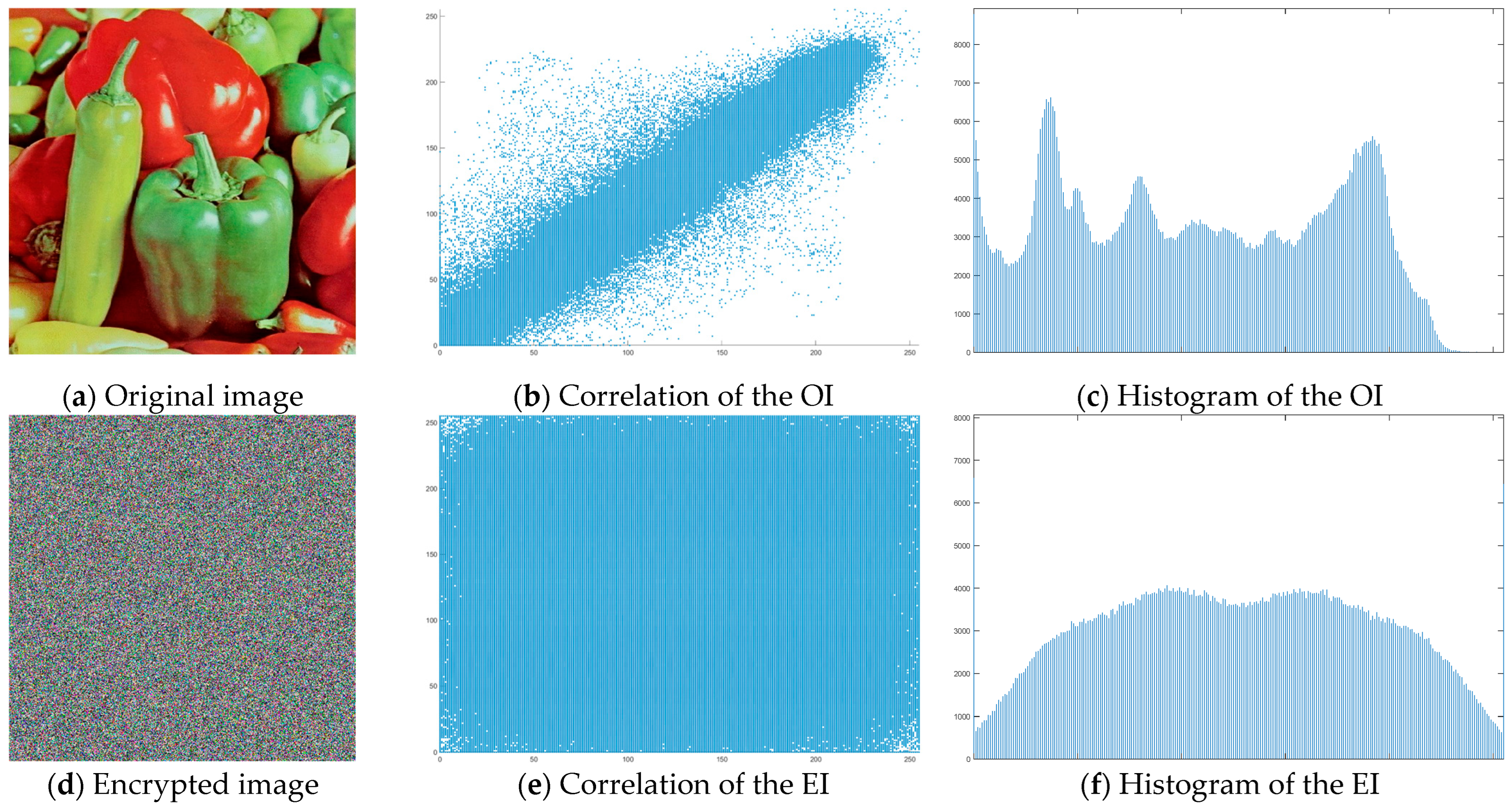
Regardless of the chosen image encryption and recovery process, the final assessment of whether a given image is highly encrypted or of good quality after recovery is based on the subjective judgment of the person. This is an essential and key point in the process of encoding/decoding digital images. For this reason, the analysis of the results of the decryption process is carried out based on three main methods, widely used in publications on the subject, namely histograms, correlations and information entropy.
2.3.1. Histogram
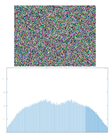
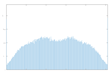
The histogram measures the quality of encryption in terms of how it maximizes the difference between the original and encrypted images.
An image histogram uses a bar chart that shows the distribution of pixel brightness values. For greyscale images, the horizontal axis represents the grey level value, starting from zero and going up to 255. Each vertical column represents the number of occurrences of the corresponding grey level in the image. For image encryption algorithms, the histogram of the encrypted image must have two properties: it must be completely different from the histogram of the original image; it must have a uniform distribution, meaning that the probability of occurrence of any value in the grey scale is approximately the same.
A high level of image encryption is evidenced by a stable and smooth histogram of the encrypted image, while the number of occurrences of the corresponding grey level in the original image is unstable. This means that the resulting encrypted image does not provide any statistical information about the corresponding grey level.
2.3.2. Correlation
Correlation analysis is a statistical data processing method used to study the coefficients (correlations) between variables. The analysis compares the correlation coefficients between one or more pairs of variables to establish statistical interdependencies between them. A useful indicator for assessing the quality of encryption of a given image is the correlation coefficient between pixels at the same indices in the original and encrypted images. This indicator can be calculated as follows:
where x и y are the original and encrypted images. In numerical calculations, the following discrete formulas can be used:
where L is the number of pixels involved in the calculations. The closer the value of
is to zero, the lower the information dependence between two neighboring pixels, and therefore, the better the quality of the encryption algorithm will be.
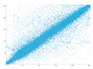
The graphical interpretation of the correlation of the encoded image should show a significant elimination of correlated pixels in the original image, which are usually located in the diagonal, vertical or horizontal direction. The purpose of the correlation pattern analysis is to identify the degree of connectivity between the original and encrypted images.
2.3.3. Entropy
Entropy is a physical quantity that is a measure of disorder. Information entropy, originally proposed by Shannon, is one of the key measures for quantifying the degree of uncertainty (randomness) of a system with respect to information [
25]. It can be applied to measure randomness in an image encryption system. Given an 8-bit grayscale level that has 256 possible pixel values, i.e., 0, 1, …, 255, the information entropy—H, can be formulated as the following equation:
where
is the probability with which the i-th gray value
appears in image
. For an encrypted image, when each gray value
appears with equal probability, i.e.,
, the information entropy reaches a maximum of—8. Therefore, an ideal approach to encrypt images should have an information entropy close to 8.
3. Modified OTP Scheme for Image Encryption
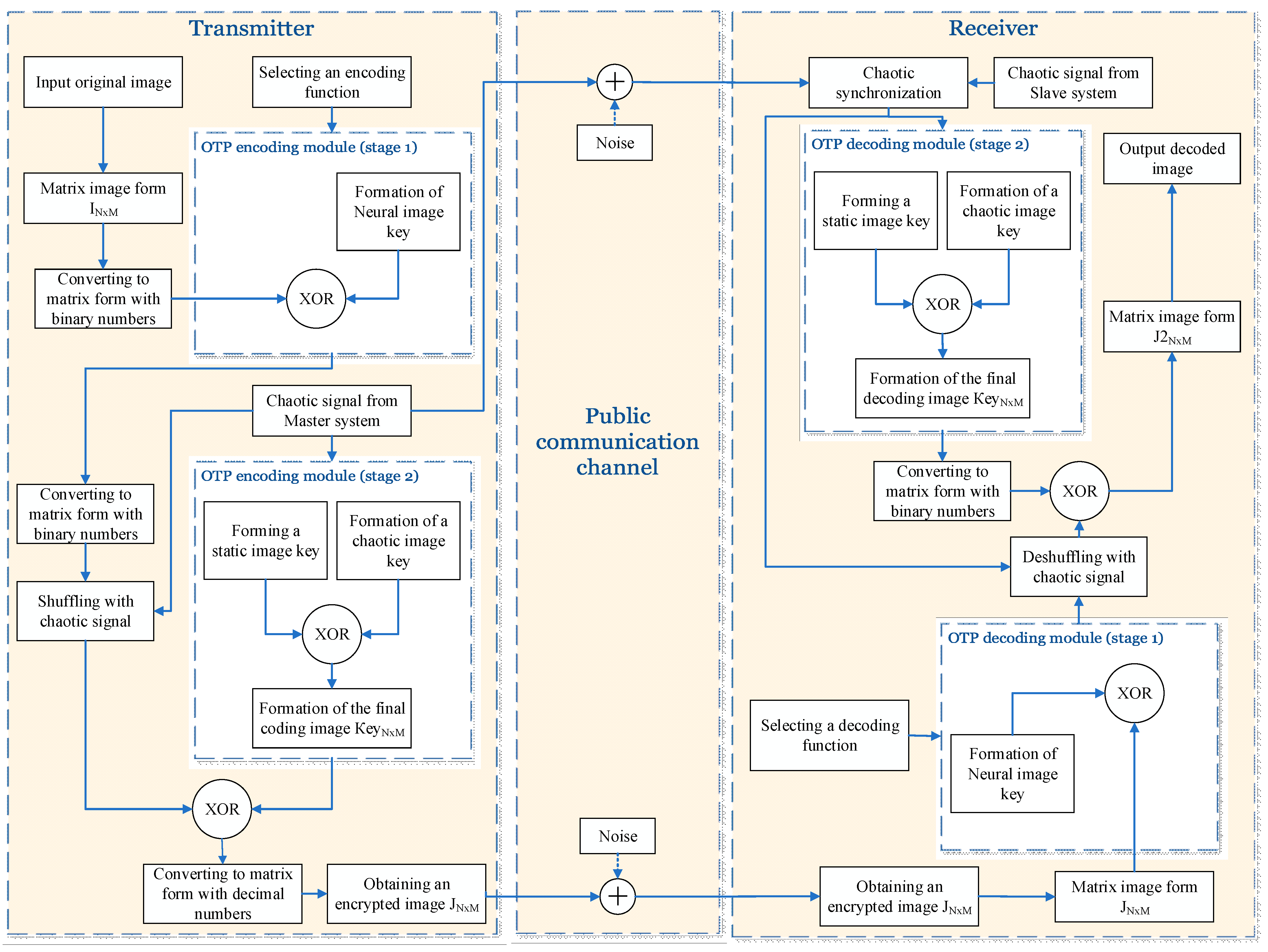
When encoding an image, OTP algorithms are an encoding technique that must be based on a one-time pre-shared key with a size equal to or larger than that image. This technique is one of the most elementary and, in general, represents pairing the image with the created secret key, which provides great opportunities for implementing and exploring various additions and modifications. The algorithm is equivalent to the masking method in signal encoding. In this type of algorithms, to achieve a high level of protection, the complexity of the generated key is relied on. For this reason, the use of a chaotic signal and the implementation of chaotic synchronized schemes is very appropriate, the essence of the method. In the current implementation, the chaotic signal from the control system is used to increase a second additional key, which is combined with a pre-increased primary key of a pseudo-random nature. In addition, the chaotic signal is used to implement the scrambling process, individual for each of the color channels.
The use of chaotic signals in this type of algorithms is very valuable, since it achieves a condition for a one-time increase in the key, as well as achieving its high degree of complexity. In view of the international trends in improving ANNs and AI, an opportunity opens up to achieve even more complex coding by implementing a multilayer scheme. This multilayer is achieved by solving the fundamental task for the ANN apparatus—namely, approximating functions or signals. These functions are used to generate an additional coding key, which will be called a neural key from now on. The main idea of using ANNs is to hide the original source for obtaining the neural key.
To implement the modified OTP (One-time path) image encryption scheme, a chaotic synchronization scheme between two identical Chua chaotic systems is used according to the method shown in point 2.1.
When implementing the scheme, the following steps are followed:
Step 1: Representation of the input image (
Figure 4)—A matrix interpretation of the input image is obtained by calculating its dimensions (rows and columns) and number of pixels.
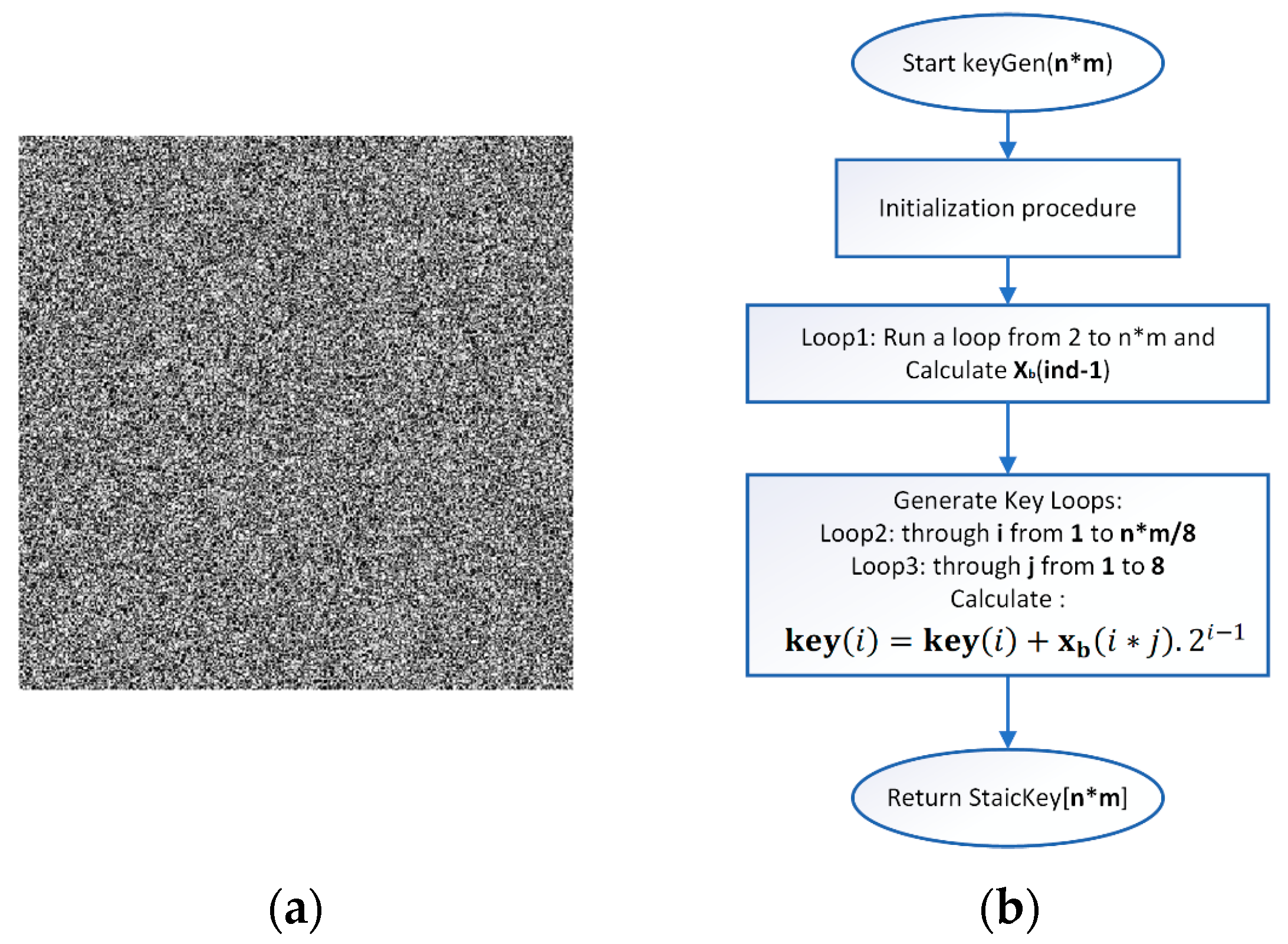
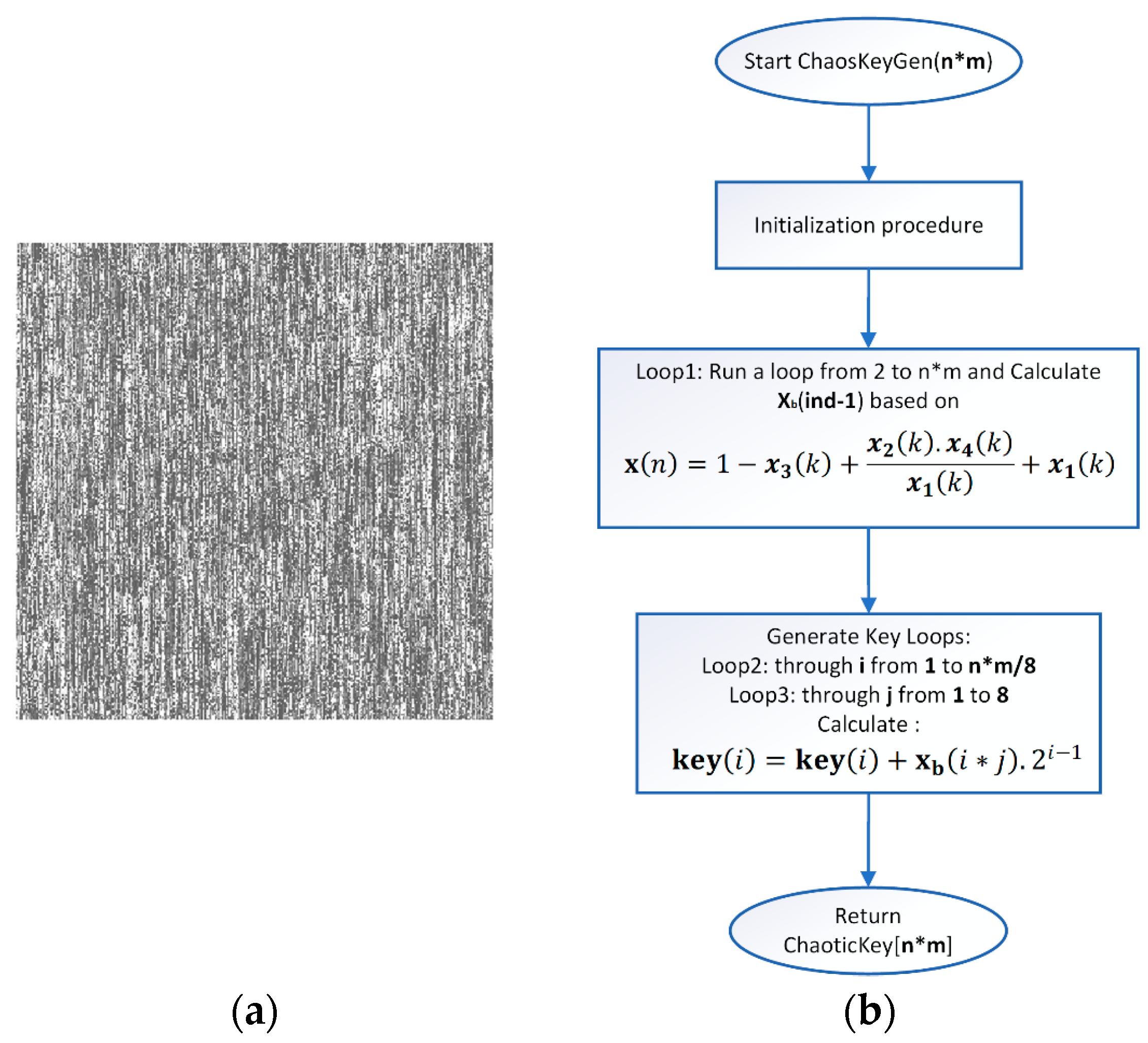
Step 2: Static key generation—The static key generation process is iterative, with the maximum number of iterations being n*m*8, where n and m describe the dimensions of the input image. A recursive algorithm is used to generate an array of numbers in the binary number system. The resulting array is converted to numbers in the decimal number system, reducing the size of the array by eight times. The extraction of each value from the key is performed using the following formula:
where
key is the array of the newly generated key with dimension n*m,
is the array of binary numbers generated in the previous step, i varies in the ranges
, j varies in the range
.
Figure 5a presents the generated static key in the form of an image.
Figure 5b presents a simple block diagram for the process of generating the Static key.
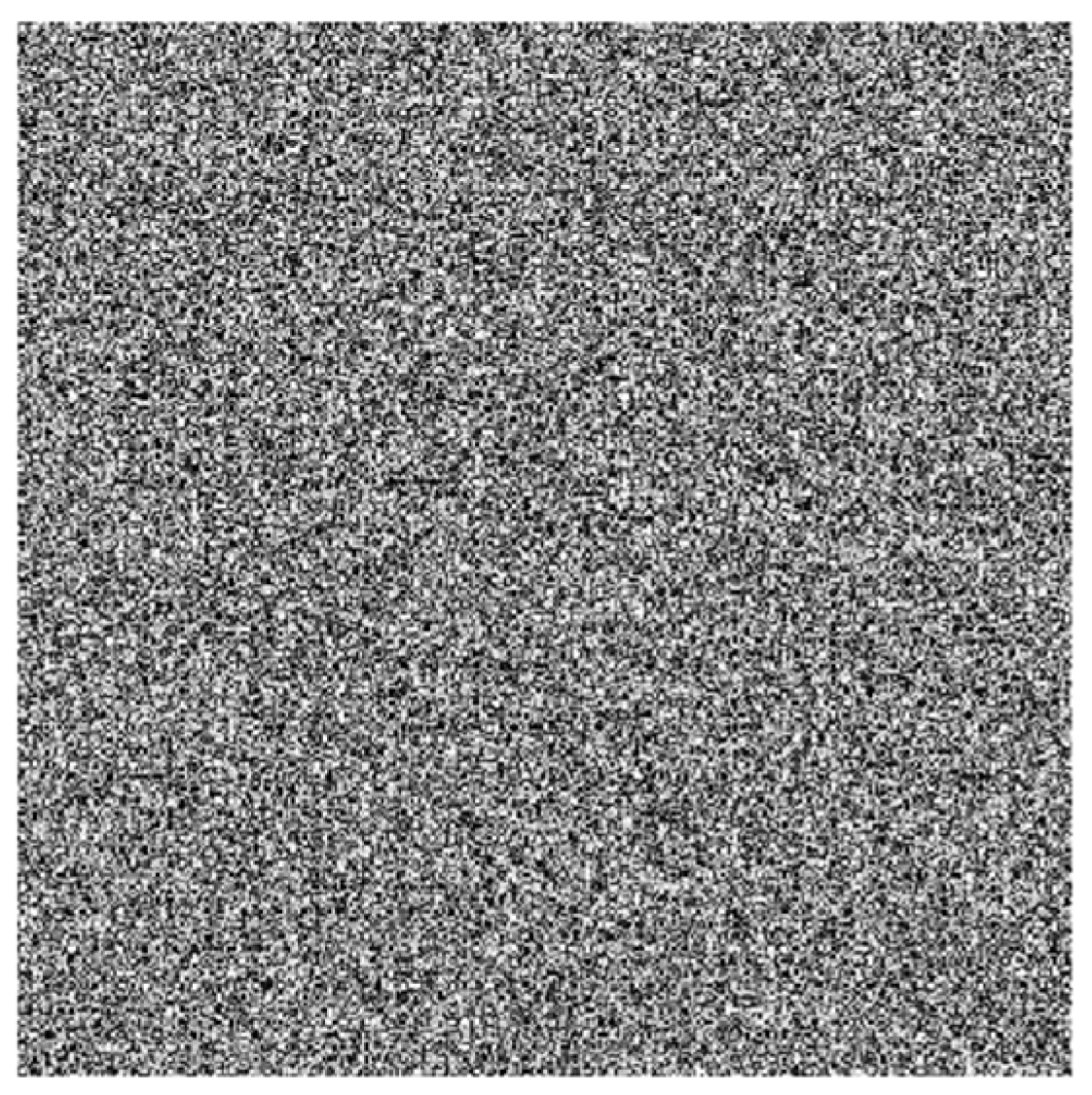
Step 3: Generate a chaotic (dynamic) key—The process of generating the second key is similar to the generation of the primary key described in the previous step. The difference occurs in the generation of the initial array, where each value is a function of the chaotic signal from the state vector of the chaotic control system and is calculated using the following formula:
where n and k are index variables, with k reflecting values of the chaotic signal after passing the transient process. In Formula (21) the use of
is intended to provide for the possibility of the algorithm to work with hyperchaotic systems of the 4th order. Since in the current implementation the system is of the third order, for the chaotic signal of the fourth state variable it is chosen to repeat that of
. After obtaining the primary array, the final one is obtained in an analogous way, i.e., by using Formula (21).
Figure 6a shows the generated chaotic key in the form of an image. The chaotic key generation block diagram is presented in
Figure 6b.
Step 4: Generation of a neural key—A similar iterative algorithm is used to generate the neural key, with the array of binary numbers being formed when generating a value of the function approximated by the ANN. The initial value can be chosen arbitrarily, but must be within the range of the function variation with which the training was conducted. When generating the encoding key, the x and y coordinates are generated, after which the image matrix is initialized. Each pixel of the generated image is formed using the following relationship:
where key is the matrix of the encoding image,
a value from the ANN approximating a given function, i and j—index variables, x(j) and y(i) are the horizontal and vertical coordinates of the matrix. The type of image obtained from a given function can be seen in
Figure 3b in
Section 2.2. Simple block diagram of the Neural key generation process is presented in
Figure 7.
Step 5: Deriving the encryption key, the final encryption key is obtained by iteratively applying an XOR operation with the static and chaotic primary keys.
Figure 8 shows the resulting encryption key.
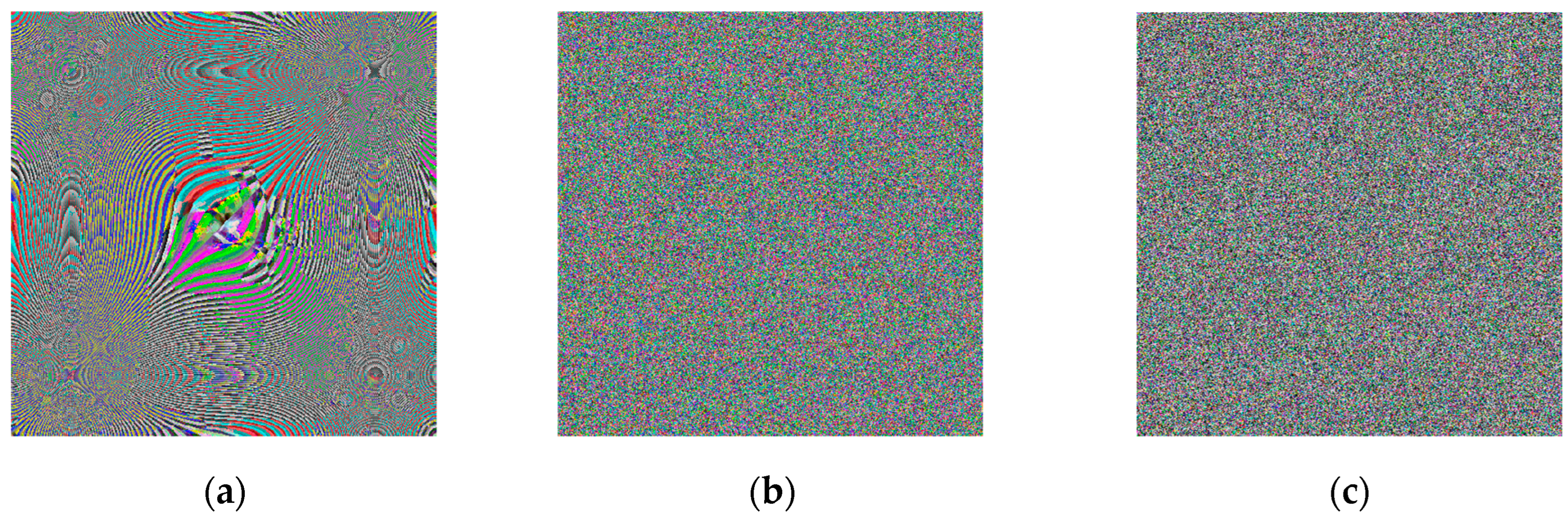
Step 6: Image encoding—As with most encoding methods, here, the encoding key (image) is paired with the input image using an XOR operation, thus obtaining a kind of masking of the image. Here, the process is carried out in two stages—initially the image is paired with the neural key, and then with the general chaotic key. Between the two steps, the image already encoded with the neural key is subjected to a shuffling process. Shuffling begins with dividing the image into the three-color channels. Each of the new images obtained is shuffled by using the chaotic signal to obtain a numerical sequence with a length equal to the size of the image. The indices of this sequence are used for shuffling. The three images thus obtained are combined again for pairing with the chaotic key.
Figure 9a shows the encoded image at the first stage,
Figure 9b shows the encoded image after the scrambling process, and
Figure 9c shows the final encoded image. A simple block diagram for the final process of image encoding via the general chaotic encryption key is presented in
Figure 10.
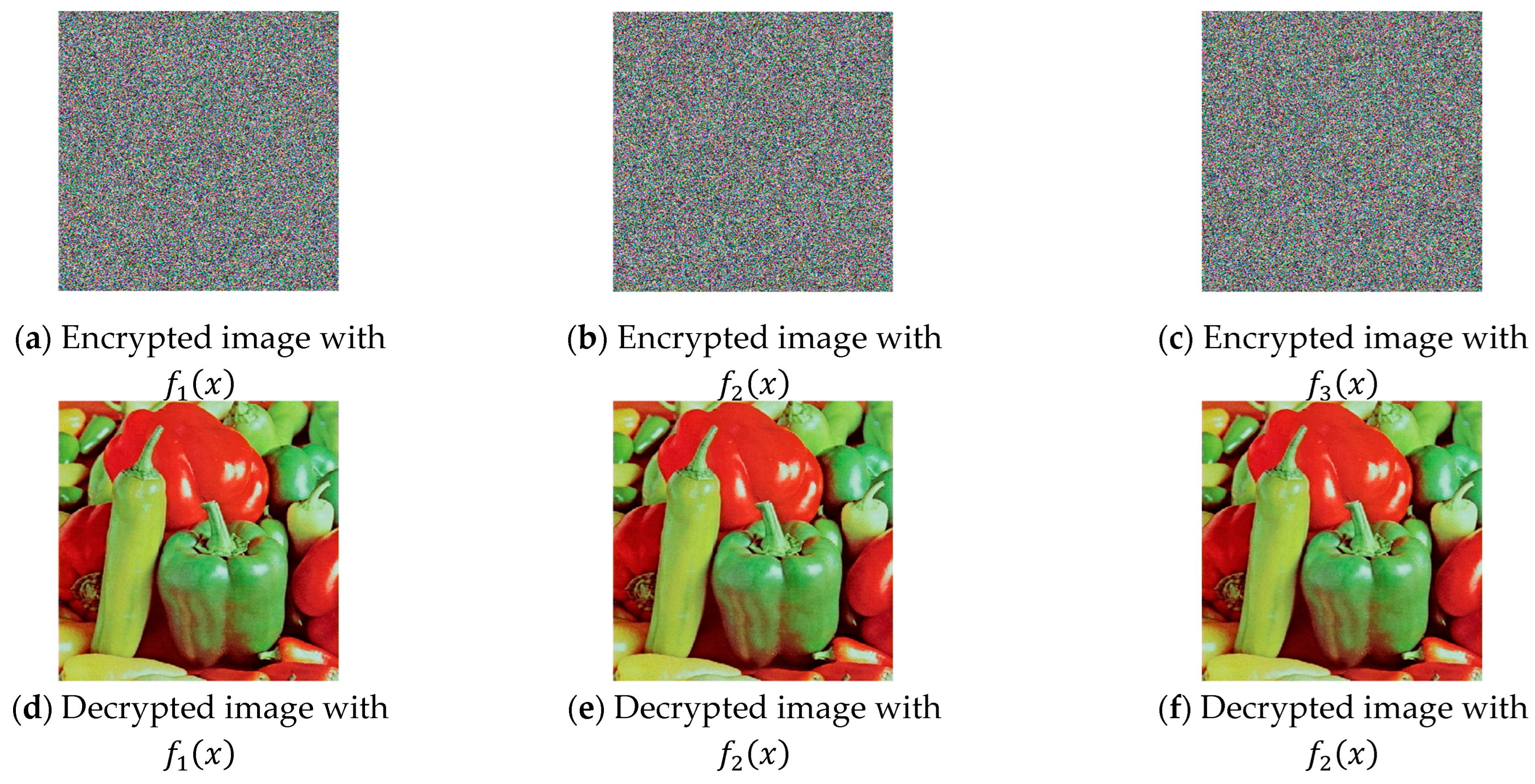
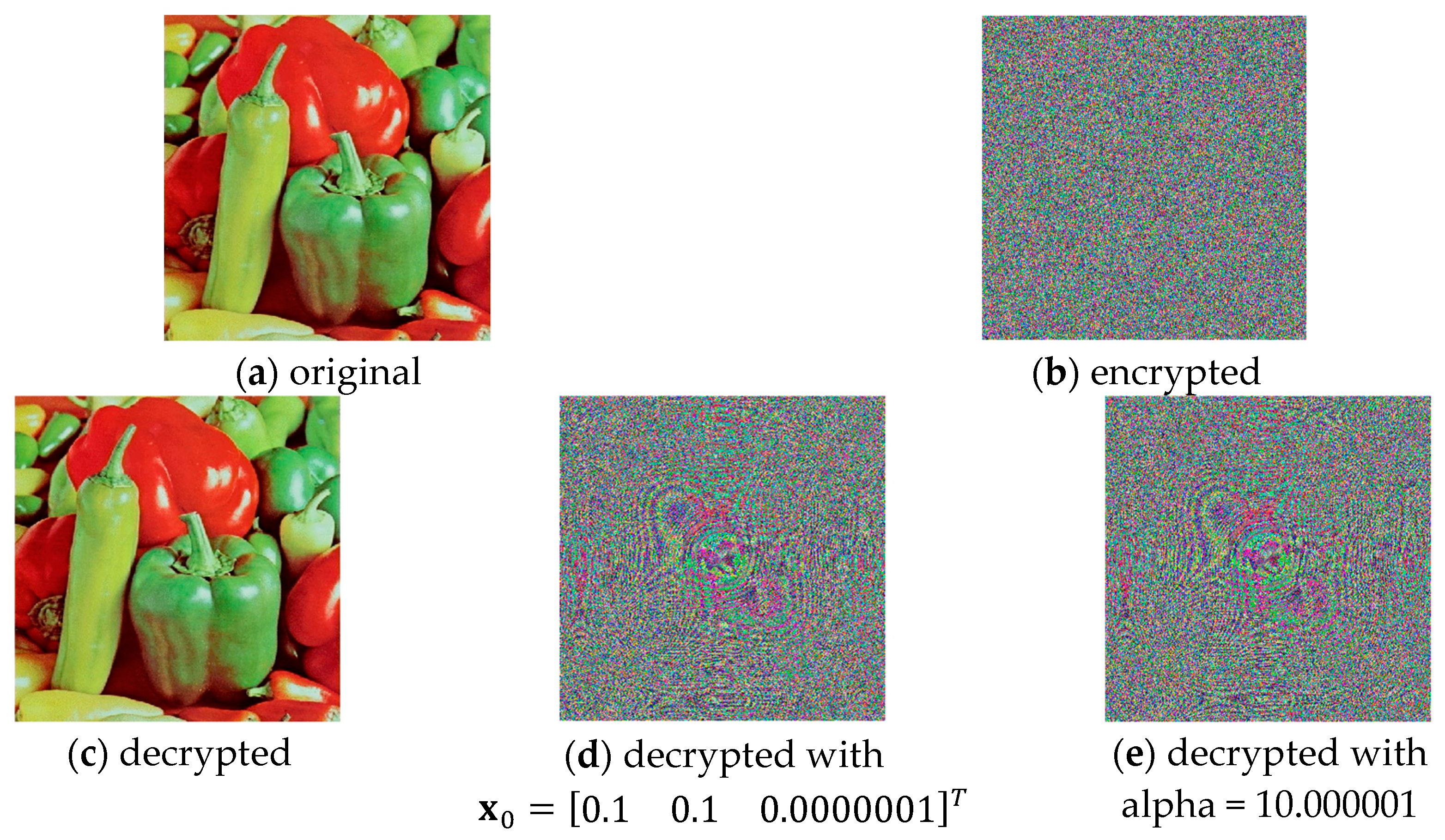
Step 7: Unlike traditional OTP methods, here, the process of chaotic synchronization is of primary importance and is executed first. Through the functional dependencies described above, the decoding static, chaotic, and neural keys are obtained, followed by the final main decoding key. The decryption procedure is carried out by generating the same chaotic sequence used during encoding, through the synchronized chaotic generator. A reverse index array of the chaotic sequence is formed to restore the original arrangement of the pixels across the three-color channels. Inverse shuffling is applied based on these indices. The actual decoding is again performed using an XOR operation, meaning that at its core, the technique represents a one-to-one encryption-decryption algorithm, and no loss of information or quality of the decoded image is expected. The presented scheme can operate either with key exchange or in a hybrid mode, where only part of the information required for generating the decoding keys (for the static and neural keys) is shared.
Figure 11 shows the resulting decoded image.
A generalized block diagram is shown in
Figure 12.
5. Conclusions
This article considers the problem of image protection. A modified image encryption scheme is that combines the classical OTP algorithm, the advantages of chaotic synchronization schemes, and the integration of ANNs is presented. The proposed approach differs from the traditional one by implementing multilayering provided by the formation and combination of a static, chaotic, and neural key, which is an innovative approach in the field of image encryption. This multilayer approach is achieved by implementing ANNs to conceal the original source of obtaining the encoding key, in the context of the classical function approximation task.
The results obtained and the tests and analyses performed are based on generalizations of numerical and graphical data for histograms, information entropy (7.9975 ÷ 7.9994), NPCR (99.6200 ÷ 99.8631), UACI (32.8354 ÷ 34.9938), and correlation coefficients (−0.0057 ÷ 0.0012), as well as an analysis of the resistance to various cryptographic attacks. The results obtained prove they achieved a high level of protection tending to the theoretical maximum.
The proposed modified image encryption scheme successfully integrates innovative approaches and classical methods, achieving high stability and flexibility. The flexibility of the proposed approach lies in the choice of chaotic systems, coding functions, neural network architectures, etc., which provide the possibility of customizing the algorithm to the specific requirements of the application. The testing results confirm the successful implementation of the approach for the secure transmission of sensitive information in real applications.