Abstract
Background: In relevant research, blockchain technology (BCT) is credited with great potential for supply chain management (SCM). However, even after more than 10 years of the technology’s existence, it is barely used for any self-sustaining applications. This raises the question of why BC cannot prevail against its alternatives. With this paper we want to identify criteria by which the added value of BCT can be measured. Furthermore, we want to evaluate how well the different supply chains (SC) exploit the added values of BCT. Methods: For this, we identified real-world examples and case studies for luxury, food, and healthcare SCs. These examples are described in detail and then analyzed for their added value compared to possible alternatives. Results: The results show that in the clusters of food and healthcare SCs, no general added value of BC over current best-practice solutions could be verified. Luxury SCs manage valuable products that are typically traded in small quantities. It is within this cluster that the implementation of BC can be justified best. Conclusions: In conclusion, this study shows that the application of BCT is especially beneficial for goods with a high value and low trade volume. In addition, the interface between reality and the digital twin should be as secure as the database or BC solution itself. Furthermore, the demand for transparency and immutability of data should be more important than the need to protect sensitive data. Finally, SC participants, especially the end customer, must also be able to appreciate the advantages of BCT.
1. Introduction
In 2021, the most successful application of blockchain technology (BCT) is still in the field of cryptocurrencies, but researchers have recognized the potential of BCT and are trying to apply it to other areas of research, such as supply chain management (SCM). Many different areas of academia have explored BCT in terms of the distributed storage of data, peer-to-peer networks, cryptography, Smart Contracts, and consensus algorithms [1] (p. 1). By design, BC is a very secure database structure where information, such as transactions or programs, is stored in chained blocks [2] (p. 5). BC is designed to be storable in a decentralized manner while functioning without a central controlling system. Moreover, BC is transparent, in order to allow decentralized storage so that older blocks become unchangeable and a high level of trust in the data set can be established.
Supply chain management is defined as the cross-company coordination and optimization of the flow of materials, information, and value along the entire value chain, from resource extraction to the end customer. The aim is to optimize SC holistically in terms of costs and time. SCM must contend with several challenges, such as globalization, increasing customer demand, shortened product life cycles, and developing information technology. To maintain or gain competitive advantages, Supply Chain (SC) companies must face these challenges. Thus, increasingly complex systems must be coordinated. As a result of globalization, the SC of many products extends across different countries of the world, each with different currencies and laws. From the source to the delivery to the end consumer, goods pass through different companies in different countries, such as manufacturing plants, warehouses, wholesalers, or retailers. SCM could benefit from a transparent, tamper-proof database and automated contracts, which is why Xu et al. (2019) recommend that any SCM company should consider BCT [1] (p. 11).
Current research on BCT, especially in the context of cryptocurrencies, is available in abundance, but published case studies and concrete examples in an industrial context are lacking at present. There are still only a few applications of BCT in SCM with commercial success and the chances of a successful implementation are currently low. According to Browne (2017), on average, only 8% of BC projects were still active within one year of starting [3]. Moreover, there is little research on the actual added value of BCT. This paper therefore aims to fill this gap. Our achievement is to classify and evaluate the value proposition of BCT for the three clusters on the basis of preliminary work. In doing so, we aim to answer the following two questions: (a) What criteria can be used to measure the added value of BCT? (b) How do different SCs exploit the properties of BCT?
Therefore, this paper aims to identify possible reasons for the few real implementations of BCT in the industrial context. For this purpose, the three clusters of Luxury, Food and Healthcare SC are analyzed in detail for the potential application of BCT to each. In a previous systematic literature review, we found that these three clusters are credited the greatest potential for BC adoption [4]. Therefore, it is evaluated whether the technology is currently mature enough for practical use in some areas.
2. Blockchain Technology in Supply Chain Management
2.1. Fundamentals of BCT in SCM
BCT is a form of data storage in the so-called blocks of the BC. These blocks are arranged chronologically and are inseparably connected to each other, hence the name BC. The data within the blocks cannot be changed without destroying the BC. A desired change, e.g., a transfer from A to B, is executed in the form of a transaction in a new block. Thus, a BC is a constantly growing chain of data blocks that are cryptographically linked to each other.
BCT was developed for the secure, worldwide transfer of virtual values without intermediaries; BCT fulfills this functionality very effectively and successfully [2] (p. 49). However, other functions of BCT, for which it was not originally designed, are needed in SCM. The practical applications of BCT go far beyond cryptocurrencies, as any type of valuable information can be digitized and tracked and traced via a BC [5]. Customers are demanding more and more origin-related data. In 2016, for example, an E. coli virus outbreak at Chipotle Mexican Grill led to 55 cases of infection, shutdowns, and investigations. As a result, the company’s reputation was damaged, sales dropped, and there was a 42% drop in the value of its stock [6]. The desire of many consumers was to be able to track food with confidence, which BCT can principally enable.
Hinckeldeyn (2019) states that BC is always worthwhile when high levels of trust between multiple actors are needed. The exploration of BCT in the field of food SC is an attempt to gain the trust of customers through greater transparency. BCT can generate or secure a competitive advantage for companies if customers trust the BC solution and if this trust is of value to the customer [2] (p. 47). For this reason, after this event at Chipotle Mexican Grill, several large food companies, such as Dole, Unilever, and Walmart, approached the problem by working together with IBM, since IBM already demonstrated competence in the use of BCT. Thus, food SCs in particular began to recognize the relevance of strategic partnerships, because only when SC works as an integrated whole can the confidence of consumers in the products of the SC be strengthened [7] (p. 5).
However, BCT can not only support SCM by means of reliable provenance knowledge. According to Roeck et al. (2020), BCT introduces transparency, trust, and disintermediation as key value propositions in SCM [8] (p. 2125). Colaka et al. (2020) cite the main value proposition of BCT in SCM as creating transparency for the customer, simplifying the tracking process, reducing costs and errors, minimizing inventory, minimizing transportation costs, reducing delays, and identifying problems faster [9] (p. 937). Ideally, SCM controls SCs by means of cross-company software systems. This software must enable SC activities to be planned, scheduled, coordinated, monitored, and validated. Al-Jaroodi and Mohamed (2019) state that with the help of BCT, this software could be enabled [10] (p. 36504).
Consequently, the possible applications of BCT are very diverse. However, for meaningful economic use, this technology must solve existing problems of SCs or lead to process improvements. In the literature review conducted in a previously published paper, two major clusters were identified. The first cluster presents an overview of BCT in SCM and the second cluster shows possible concrete applications of BCT. In that second cluster, six papers each on luxury and food SC were found, as well as five papers on health SC [4]. The conducted literature review [4] (p. 7) was able to identify two functionalities of BCT that are very promising for SCM. These are, firstly, the functionality as a secure, transparent database and, secondly, the application of Smart Contracts written on the BC.
2.2. Features of a BC That Are Beneficial for the SCM
One way to categorize the influence of BCT on SCM is provided by Litke et al. 2019, who identified the following possible positive influences of BCT on SCM: Scalability, Performance, Consensus, Privacy, Location and Cost. They state that SCs scale better and that the SC performance could increase due to BCT. This is because modern SCs are becoming more complex and a significant amount of data needs to be exchanged between many actors. The data from these SCs is currently managed very inefficiently, as each company uses its own solution and when necessary, data must be exchanged with another company that relies on a different approach. No common database has yet been implemented in an SC; BCT could unite all SC participants for such an endeavor. Furthermore, BCT can provide unity within the SC through consensus and protect privacy effectively through permissioned access and by making private transactions invisible but properly verified. A significant amount of money could be saved by payments with cryptocurrencies, as well as by better detection of potential savings. However, one of the most potentially important elements of BCT is the ability to document the location of products over time in a trustworthy manner [11] (p. 7).
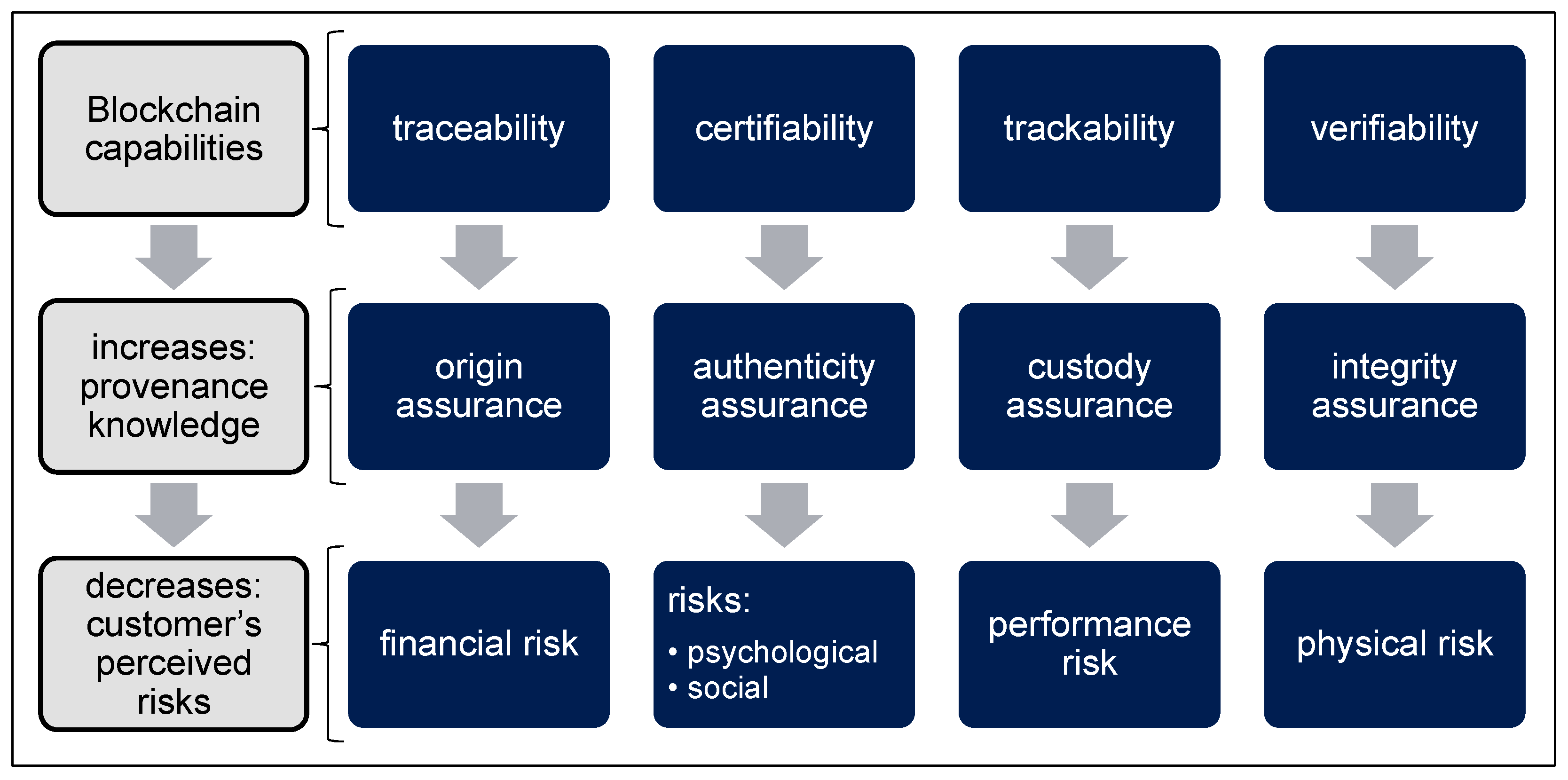
BCT offers traceability, certifiability, trackability, and verifiability for determining the origin of a product. By improving knowledge about the origin of a product, the perceived risks of customers can be reduced (see Figure 1). Traceability leads to increased certainty about the origin. This reduces potential financial risk because the customer can verify that the source materials are those the manufacturer advertises. For example, the customer could trace source materials such as cashmere or high-value leather. The certainty about the authenticity strengthens the customer’s confidence not to behave unethically and, for example, to purchase counterfeits or products with undignified production conditions. This reduces the customer’s psychological risk and the social impact when other people find out about the purchase, known as the social risk. Trackability through the different stages of SC enables subsequent control and thus increases trust in the product. For example, in the case of a high-quality wine, the storage conditions, such as temperature and humidity, could be documented. This lowers the risk for the customer of the performance or function of the product being inadequate. Verifiability ensures data integrity. This can dramatically reduce the risk of counterfeit products, especially for critical products such as medicine. This security can in turn reduce the risk of physical damage to the customer [12] (pp. 286–291). An example of a BC provider is Provenance, which connects consumers and suppliers for different logistical activities to enable provenance knowledge [10] (p. 36504). The most important prerequisite for such a service is the unambiguous assignability of products with their image in the BC. Ideally, the products are inseparably linked with the BC. However, the BC solution can only be as secure as the link between the physical products and the BC [13] (p. 42).
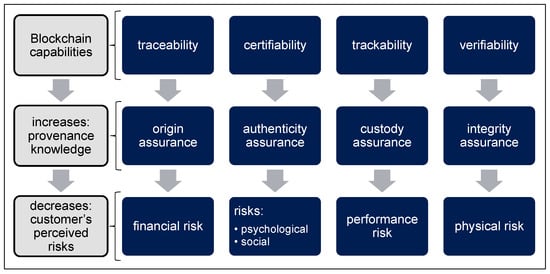
Figure 1.
Impacts of Blockchain-activated origin knowledge on the customer [12].
3. Value Proposition Analysis
The authors of this paper conducted a systematic literature review on the applications of BCT in logistics and SCM. Three clusters were identified in which the application of BCT is particularly promising: Luxury, Food, and Healthcare SCs. In what remains of this paper, real-world examples are used to analyze the added value of BCT for each respective cluster. The examples identified in the conducted literature analysis serve as a basis [4] (pp. 10–13).
In this chapter, applications of BCT in SCM are introduced and validated. For the Luxury SC, the Food SC, and the Health SC, the value proposition of BCT is worked out in each case using the example of a specific application. Here, the BCT, with its limitations, must be measured against alternative solutions. The structure of the subchapters starts with a summary of the actual problem of that cluster, followed by a description of how BCT can help, i.e., what its value is. Subsequently, the limitations and challenges of the BC solution are considered, before being compared with alternatives. Finally, a summary and assessment are provided.
3.1. Luxury Supply Chain
3.1.1. Examples of Applications and Case Studies
In the relevant research there are various possibilities as to how BCT can support Luxury SC. A current application is the authentication and certification of diamonds. On the one hand, this is important in order to prevent “blood” diamonds; on the other hand, conventional certificates can be faked, or a real certificate can be used for a fake diamond. Furthermore, BC certificates are permanent [14] (p. 17).
Two major providers have established themselves for BCT in SCM: Everledger and the open source project Hyperledger, which has been supported by IBM, SAP, and Intel, among others [5]. The platform Everledger offers a unique digital thumbprint for high value and hard-to-replace goods, such as diamonds, wine, etc. [15] (p. 9). This thumbprint is unalterably stored in the BC and consists “of 40 metadata points, the laser inscription on the girdle, and the stone’s four Cs—color, clarity, cut, and carat weight” [16]. Since the diamond is uniquely digitally assignable, Everledger can create a digital twin for each diamond. The website states: “By combining blockchain technology with AI, IoT and nanotechnology, we create a digital twin of every diamond, enabling traceability in a secure, unalterable and private platform” [17].
In addition to the already existing BC-certificates [14] (p. 27), the transport of the diamond can be documented completely by means of the BCT (tracked and traced). As soon as the recipient of the package confirms that the package has been delivered, a transaction can be triggered by means of a Smart Contract. The advantage of using the BCT is that it is suitable for use across different companies, which means that the transportation means of different companies can be used, if they agree to use this BC. No one can change the data in the BC retrospectively. As the BC is law, the person currently responsible for the diamond is always visible to all parties; the person currently responsible is always liable for any damage or loss. The responsible persons can individually insure themselves. In the case of a public block certificate, there is a risk that criminals could gain access to the current location of the valuable diamond, which makes private, permissioned BCs more suitable [15] (p. 6). However, a residual risk remains because all companies along the SC have access to the BC.
Breitling was identified as another example within Luxury SC. Breitling includes a digital passport and a certificate of ownership with a QR code, with new watches. The data of the owner of a Breitling watch and the certificate can be stored in the BC using an app. Each Breitling watch features a serial number on the back of its case, and as of 2021, older watches can also be registered. Breitling cites traceability, transparency, and tradability as its advantages [18].
In terms of traceability, information such as the warranty or the full history of the watch can be viewed. It is easier to engage in anonymous conversations with Breitling customer services; for example, ordering an additional bracelet can become easier. Breitling tries to motivate its customers to use its service by offering an extended warranty. A significant advantage, however, is that the current owner of a Breitling is stored in the BC. In the event of a sale, ownership can be proven and transferred very easily using the app. For this purpose, a transaction is stored in the BC in a new block. This has a potentially positive effect on the resale value of the watch. On the one hand, the buyer can be sure that it is an original and that the seller is the rightful owner. On the other hand, general information, such as the number of previous owners or whether maintenance has been complied with, can be retrieved.
It is very likely that the BC used by Breitling is a private BC; whether Breitling developed the BC solution itself, or uses a vendor is not known (note: an inquiry to Breitling on this matter was not answered).
3.1.2. Current Problems of the Respective Area
In the following section, the value creation of BCs will be examined primarily using the example of the digital twin of a diamond. However, most of this also applies to the Breitling example or goods of other Luxury SCs. In the example, clearly marked diamonds were linked to the BC. Since the diamonds are very valuable, there is a trust problem.
On the one hand, the diamond should be traceable to be able to determine its origin with certainty and to ensure that it is not a “blood” diamond. Many consumers actively try to avoid illegally mined elements [2] (p. 47). Consumers thereby try to avoid the social and psychological risks described in Section 2.2. On the other hand, with such an expensive commodity, there is always the risk of counterfeiting. The customer wants to be sure that the information about the diamond is correct. This is important because non-professionals find it difficult to determine the value of a diamond.
3.1.3. Possible Value BCT Could Provide (+)—Pros of Implementing a BC
Everledger states that the origin of a diamond is stored thanks to AI, nanotechnology, and BCT. Thanks to nanotechnology, the diamonds can be clearly assigned and a digital twin can be created. Should the technology with the marking of diamonds become accepted worldwide, the resale value of stolen diamonds would be reduced. This digital twin must be stored as securely as possible, as diamonds are often very valuable; trust must be established.
The BCT is designed to create trust. In a public BC with many participants, the BC can provide trust very effectively. However, the data around the diamond is too sensitive for a public BC. Everledger therefore relies on a private BC. Everledger’s website states: “The lifetime story of a diamond, colored gemstone or fine bottle of wine is valuable information. It’s a story you must increasingly be able to tell with clarity and confidence, to meet your customer’s call for responsible and verifiable sourcing” [19]. In the case of Everledger, the life history of the diamond consists of entries in different blocks of Everledger’s own BC. When a change is made, the old record is not overwritten; instead, the change is recorded in a new block. This ensures maximum transparency. The benefit of the BCT is that changes to the data set are made transparent and traceable, and therefore unchangeable.
3.1.4. Limitations and Challenges of BCT (−)—Cons of Implementing a BC
Everledger uses a private BC, so the decentralized component of the BC is lost. With the private BC, old blocks could be changed. However, all the subsequent blocks would have to be recalculated. If no requirements are placed on the hash, in contrast to the PoW algorithm, recalculation is possible quickly. However, if the clients have access to the hash, they may notice that a previous block has been modified. Since Everledger is the main node, all new information must be verified by Everledger itself, which requires trust from all parties involved towards Everledger. It comes down to this: the customer must trust Everledger. Therefore, it must be questioned what value proposition the BC has to offer over storing the data of the uniquely marked diamonds on a normal database of a trusted third party, which could also be Everledger.
3.1.5. Alternative Solutions without the Use of BCT
Since the customer must trust Everledger, Everledger could also store the data in a conventional database. Furthermore, in the conventional database, changes to the data set, such as the current location of the diamond, could be stored and made traceable. Everledger must guarantee that they do not manipulate old data, and that the data cannot be manipulated from the outside. However, Everledger must provide this guarantee independently of the database’s structure, i.e., also when using a BC.
Conclusion and assessment—Compared with a conventional database structure, the BC can offer the advantage that customers could more easily check whether older data have been manipulated. The cost of storing data in a BC is also reasonable. Everledger only needs to keep the old data and, if it changes, it does not have to change the data but link a block with the change to the BC. In this case, the value proposition of BCT is relatively small. Storing digital twins in a BC is more of an incremental innovation than a revolution. Nevertheless, the value proposition could cover the low costs relative to the high value of the diamonds.
3.2. Food Supply Chain
3.2.1. Examples of Applications and Case Studies
Food SC were the largest cluster found in the literature analysis; nevertheless, no case was found in which a company actively uses the BCT to earn money and gain a competitive advantage [4] (p. 11). Many feasibility studies have been found, but only few have tested their prototypes in the real world; this finding matches the findings of Hinckeldeyn (2019) [2] (p. 32). Demestichas et al. (2020) also identified many ideas, models, and case studies in a recent comprehensive literature review, as well as a growing interest in research. However, they could not find this growth in commercial applications of BCT [20] (pp. 10–14). Instead, they found companies and websites promoting BC solutions in Food SCs (see Table 1). Below, some projects are briefly mentioned as examples, followed by more detailed descriptions of selected applications.

Table 1.
Companies which promote BCT for the food SC [20] (p. 15).
Firstly, there is the cooperation of Walmart and Hyperledger Fabric, a BC platform for companies, which is intensively supported by IBM [2] (p. 24) and has been found numerous times [21]. In a field test, Walmart and IBM were able to demonstrate that the origin of mangoes and pork could be determined via BC within a short time [2] (p. 32). The IBM Trustchain can track tomatoes from the farm to the pot, to the jar, to the table, but is not yet in use, instead is a working prototype [22]. Bumble Bee Foods cooperates with SAP to document tuna fish products from Indonesia. The size of the fish, fishing location and time, freshness during its processing, and the company’s certificate of production are stored within the BC [23]. Other examples deal with the traceability and certification of Extra Virgin Olive Oil [24] (p. 173) or describe how eggs could be traced in the USA using BCT [25].
On the one hand, these examples demonstrate the increased interest of food manufacturers in the trustworthy documentation of their products in the BC. Many companies are already trying to gain the trust of consumers with the help of seals, such as the Fairtrade label, which is awarded by a Fairtrade organization under certain conditions. On the other hand, the examples also show the interest of large IT groups. Whether the interest comes from the Research and Development department or the Marketing department is not always identifiable. Food scandals have led to manufacturers generating competitive advantages by providing reliable proof of the origin and processing of goods. The BCT might be able to strengthen the confidence of the consumer [2] (p. 32).
Below, a prototype that has been tested in the field is discussed. Zhang et al. (2020) developed a new system architecture along the entire Grain SC based on the BCT. Compared to traditional methods of the SCM, their system is characterized by high data security, real-time exchange of relevant information, such as hazardous material information, and trustworthy grain tracing along the entire SC [26] (p. 36398). The Grain SC starts with grain cultivation and production, primary grain processing, grain product cycles, and deep grain processing, and ends with transport to the consumer. Zhang et al. (2020) identified five typical links in the traditional Grain SC: the link of grain production, the link of grain storage, the link of grain processing, the link of grain logistics and transport, and the link of grain marketing [26] (p. 36400).
Smart Contracts define the conditions for the execution of transactions in advance. The system collects data on the grain, which is then stored within the BC. The data is collected mainly by electronic tags and various sensors, such as code-scan guns, cameras, smoke detectors, humidity sensors, light sensors, etc. When the parameters of the grain meet the requirements and, in addition, all other requirements are met, the transaction is automatically triggered [26] (p. 36404). A special use case was applied to validate the proposed system: an Information Management System for the Grain SC was established with grain companies in the province of Shandong. This field test was conducted on the BC platform, Hyperledger Fabric with the cloud database, MySQL. The system was able to provide reliable information in the SC for participants, consumers and third parties, and the data provided a good basis for the assessment, prediction, and early warning of hazards [26] (p. 36407).
As mentioned briefly above, Walmart and IBM are working on a BC to increase the transparency of the SC by tracking goods efficiently. Walmart faces the challenge of tracking and identifying a large number of products through a complex SC. If there is a problem with a product, such as contamination, Walmart needs to be able to locate and remove affected products from the shelves or contact affected customers as quickly as possible. The solution from Walmart and IBM is based on a private BC and is intended to be used to identify products very quickly. At the time of writing, a localization takes 6 days, while new solution products should be identified and localized within 2 s [27] (p. 14). Although many papers have mentioned this example, no technical details are identified. Who verifies the data entered, how false data is handled, and who pays for the transactions remains unclear.
Three papers were found in the Food Cluster that addressed the tracking and tracing of meat (see: [12,28,29]). Barge et al. (2020) focus on methods to better mark and identify meat, as they identified the problem of the interface between the physical meat and the digital information. According to Barge et al. (2020), increased consumer confidence in food and producer reputation, especially for meat, have been shown to provide increased sales. In the area of meat, there have already been several food scandals, e.g., concerning diseases, which is why there are already laws regarding this in the EU. Manufacturers must keep traceability data on meat, but do not necessarily have to share this data with customers. In Italy, the consumer even has the right to view part of the stored information about the meat, via a website from which the information can be accessed. This information includes the date of birth, sex, breed, farm code and slaughter date of the meat source animal. For this purpose, the customer needs a 14 digit code, which is written on each package. This information is provided without the BCT [28].
In addition to these obligations, the SC can also store further tracking and tracing information. High-quality meat producers can provide customers with further information. To be able to assign a piece of meat to a cow, the meat and the cow must be clearly identifiable. In the EU, electronic tagging is mandatory for sheep, goats, and cattle. The unique ID of the animal is stored in a passive tag, which is also stored in the national animal register [28]. In summary, producers already possess the relevant information, but rarely share it with their customers.
Ferdousi et al. (2020) identified the problem that many farmers view data about their meat as confidential and its disclosure as a threat. As a solution to this problem, Ferdousi et al. (2020) propagate a Smart Contract-enabled private BC with the goal of preserving the anonymity of users. To establish consensus among the participants of the network, Proof of Authority (PoA) is used. This is an evolution of the Proof of Stake (PoS) consensus mechanism [29]. In PoA, unlike PoS, no assets in a cryptocurrency ensure trustworthiness; instead, participants with a good reputation ensure consensus by vouching for the correctness of the transaction with their name. However, this requires the identification of the user. Therefore, this system requires a central administration, which takes over the registration of the farm owners and assesses their trustworthiness and reputation. The main advantage of this method is that neither computing power is needed, nor a large amount of cryptocurrency.
Transactions or Smart Contracts are stored in the approved blocks, as before. This form of consensus building allows more data and more complex Smart Contracts to be stored in the BC. The propagated system can be hosted on any SQL DBMS (database management system) and the Smart Contracts can be executed using Ethereum. In the field of Smart Contracts, anonymity can be guaranteed in the proposed system. The special feature of the system is that data protection, data ownership, and security are guaranteed. Therefore, farmers can share data relevant to the customer anonymously [29] (p. 154841).
3.2.2. Current Problems of the Respective Area
Some applications of BCT in Food SCs were introduced. A model for grain SC, the cooperation of Walmart with IBM and the tracking and tracing of meat were presented in detail. Most approaches in food deal with improving traceability. The goal is either to offer the customer added value through trustworthy, in-depth information, so that the willingness to pay increases, or it is for companies to make recalls more efficient.
3.2.3. Possible Value BCT Could Provide (+)—Pros of Implementing a BC
The BC can function as a database and provide trustworthy traceability data. As described earlier, in meat and fish, traceability is mandatory in many countries. However, these data often do not have to be shared with the customer. Producers often do not want to share this data because the data is considered trustworthy. The BC could help to share the data in an anonymous but trustworthy manner with the customers.
3.2.4. Limitations and Challenges of BCT (−)—Cons of Implementing a BC
Food is produced in large quantities and there are many different types of food. Thus, it is a very high -volume productive process; by contrast BCT is not designed for high volumes, but rather for high values. Furthermore, BCT can provide trust, but it provides trust through transparency. Since this transparency is not desired by many manufacturers, approaches are being pursued in which transparency is widely restricted. In this case, much of the manufacturer’s data is anonymous to the customer. The lower level of transparency automatically reduces the customer’s trust in the data, meaning that a higher level of basic trust on the customers’ side is assumed. Another critical point of BC solutions is that a secure interface between the food and the BC is often difficult to implement. Ideally, the interface and the BC itself should be similarly secure and ensure a well-balanced system without vulnerabilities. For example, Walmart’s mangoes could simply be exchanged. The customer cannot be sure that the presented secure BC-based data also belong to the product at hand.
3.2.5. Alternative Solutions without the Use of BCT
Alternative solutions to BCT include a write-only database or a trusted third party. If food data must be stored according to the law, then these data are already trustworthy, since there is a threat of penalties in the case of false information. The trust in mandatory data is therefore comparatively high, which is why a BC is not required. In addition, companies usually do not want to hand over the data voluntarily and, therefore, they try to minimize the costs.
In the example of Walmart, there is already a great deal of trust between the SC participants due to often intensive cooperation. In the area of product recalls, there is often no trust problem in a data set. Rather, the problem is that the data are not available at all and must be investigated manually by employees. Accordingly, BCT is not necessarily needed for this use case from a technical point of view. However, customers may feel more secure if the traceability system is based on BCT.
In the case of fish, origin information is already mandatory in Europe. The company followfood or followfish has made the complete traceability of food, mainly fish, its business model [30]. Using a code, the traceability data for salmon, for example, can be retrieved, such as: “Bred by the Salmar company in Frøya, Norway, processed in Lithuania, packaged in Holland and stored in Bocholt, Germany” [31]. The company guarantees the correctness of the data and does not use BCT for this purpose. Other companies or SCs could follow the example of followfood and make transparent traceability of food a part of their business model.
In the food sector, however, the customer is often not provided with the option of traceability at all. Customers are often not provided with tracking data, which is why the problem of a lack of trust in tracking data cannot arise in the first place. The ability to track products without BCT offers a great value proposition. Should customers embrace tracking and tracing and increasingly access the data, then for exclusive products this tracking and tracing solution could be run on a BC. However, this is only worthwhile if customers can appreciate the benefits of BCT.
Conclusion and assessment—Verhoeven et al. (2018) critically discuss the cooperation between Walmart and IBM. According to them, Walmart’s disclosures suggest relatively little engagement with BCT. Walmart does not specify how and where the BC is stored and seems to store the data centrally. Further, Walmart does not address the costs and procedure of writing on the BC, nor how secure and trusted data sources are created. As mentioned above, Walmart claims to have reduced the tracking time of the respective products from 6 days to 2 s. How Walmart arrives at these numbers is not known, especially in comparison to alternatives to BCT. According to Verhoeven et al. (2018), Walmart does not seem to validate the data written to the BC. With a central database with regulated write permissions, for example, a write-only database, even faster traceability times could be achieved. Walmart also does not address who has access to the data. Some companies do not want competitors to obtain access to such data. Based on all the identified requirements from Walmart and the manufacturers of the products, no need for a BC solution could be identified [27] (pp. 14–18). In conclusion, it remains unclear whether a BC is the best solution for Walmart; however, marketing strategies were not included in the analysis.
In the area of meat SCs, there could be a great value proposition to the customer in the form of traceability. The entire tracking is possible with a central data bank; the only advantage that BCT could offer to the customer is an increased trust in the data, provided that the customer values the BCT. However, this is only worth striving for if the interface between food and BC is improved. This is because, especially in the case of food, the interface between the food, such as a steak, and the BC is very difficult, since food is often processed in very high numbers [28] (p. 2). If the customer trusts the stored data because of the BCT, the problem remains that the customer must ensure that he has also received the steak that matches the data in the BC. For example, the same QR code from a high-quality steak could have been used on other steaks of poorer quality. The customer must also trust that the data entered is correct. Currently, BCT in the Food SC sector only seems to be worthwhile for those who do provide a high-quality service with a higher-priced product and want to prove this transparently to the customer. In this case, the benefits must outweigh the disadvantages of disclosing the information to the competition.
3.3. Healthcare Supply Chain
3.3.1. Examples of Applications and Case Studies
The SC in Healthcare was the second largest cluster found in the application of BCT. The company Modum, a Swiss start-up, is as an example for this category. Modum has initiated several studies and developed and tested prototypes and offers its services in the field of BCT in SCM. The goal of the company is the secure tracking and tracing of pharmaceutical products. To this end, the company relies on a public BC, the Ethereum BC. For tracking, IoT sensor devices, QR codes, and barcodes are used to clearly identify the items handled.
The Good Distribution Practice Regulation (GDP 2013/C 343/01) requires proof that the transport conditions (in particular the temperature) do not affect the quality of the pharmaceutical products transported [32]. Modum enables other companies to meet the GDP requirements with the help of the BCT. At the same time, it should be possible to generate significant cost savings for the transport of pharmaceuticals that do not require active cooling [33] (p. 5).
To monitor the temperature during the transport of medicines, a calibrated temperature sensor in the package stores a measured value every 10 min. When receiving the package, the customer can scan the ID number on the package and then request the temperature data via Bluetooth, without having to open the package [33] (p. 5). The customer then sends the data to the Smart Contract. The data is stored in PostgreSQL because the collected data is too large or too sensitive to be stored in the Ethereum BC [34] (p. 588).
Other suggestions we found in the relevant research h on how the cold chain of medicines can be monitored transparently, e.g., using RFID systems [35], and how the risk of counterfeit drugs [36] can be reduced. For this purpose, Singh et al. (2020) proposed an IoT- and BC-based model for SCM in healthcare, where consensus is established by the Raft algorithm. The Raft algorithm builds on the Paxos algorithm but is intended to be more comprehensible (see: https://raft.github.io—last accessed on 15 September 2021). In these algorithms, a changing leader is elected, and each node must agree to the changes. The algorithm is suitable for a network with few participants, allows high data throughput and does not require high computing power to do so. The authors refined their model to improve privacy, security and show a full implementation, including an analysis of the performance and security of the network [37] (p. 20).
Another way in which BCT can support SCM in healthcare is through process improvements. One example is IBM’s Hyperledger Fabric, which can connect all parties to the vaccine SC, such as manufacturers, government agencies, participating companies, and others. Each of these participants can view relevant information about the vaccine, such as its production and storage conditions, and related data [38] (p. 16). In this context, a vaccine SC monitoring model was proposed by Yong et al. (2020). In the model, vaccine tracking data is based on Ethereum Smart Contracts, enabling functions such as the notification of soon-to-expire vaccines. By analyzing the available trusted data, for example, the need for vaccines can be predicted [39] (p. 10). BC could also support SCM in pharmacy; since more trustworthy data are available through a BC, better and more meaningful analyses could be performed, such as in the discovery of trends [10] (p. 36503). Jayaraman et al. (2018) are considering a BC-based drug recall system because product recalls have increased in recent years [40].
Another application of BCT in healthcare that we found several times is the storage of patient data, so-called Electronic Medical Record (EMR) in a BC. Only if the treating physician possesses all the relevant information about his patient can they make the best possible decision between all treatment options. Various models for implementation have been promoted in research, including MedRec by Azaria et al., Healthcare Data Gateway (HGD) by Yue et al., MediBchain by AlOmar et al., or MeDShare by Xia et al. All of these models deal with the storage of patient data in a BC, but differ in their implementation, such as the BC type [41] (p. 1420). The main advantage resulting from this is that all parties involved have the current version of the patient data stored. If the data changes, it is stored between the doctors, the insurance company, and the patients as a transaction [7] (p. 4).
3.3.2. Current Problems of the Respective Areas
In healthcare, most data are critical because, in the worst case, health or human lives depend on it. On the one hand, patient data must be stored and made available to all concerned, and on the other hand, data about medications or vaccines must be stored. For these critical goods, the storage of production data, tracking and tracing data or data on storage conditions such as temperature could lead to a new quality. Currently, patients’ medical records are stored in multiple locations and are rarely merged, which in the worst case could lead to treatment errors due to missing information.
3.3.3. Possible Value BCT Could Provide (+)—Pros of Implementing a BC
BCT can support SCM through data immutability, storing critical data in a very secure and immutable way. Immutable datasets could enable automated payments via Smart Contracts by sharing data with the insurer. The insurer might have an interest in this to prevent various types of fraud by preventing the critical data from being manipulated [7] (p. 4).
Palas and Bunduchi (2020) investigated the value of BCT for SCM by conducting an extensive literature review and combining the findings with an expert survey. As a result, for the value proposition of BCT, they identified improvements in the following: privacy and security; value capture, especially cost savings; and the value network, especially in data accessibility and the reduction of intermediation [42] (p. 1). Furthermore, BCs should generate a value proposition for healthcare by “enhancing privacy and security, offering more efficient management of health data, and, to a lesser extent, enhancing accountability, thus offering better services to patients” [42] (p. 34).
As a result of their expert survey, Palas/Bunduchi (2020) add the following points to these value propositions of BCT for healthcare that are already often mentioned in other studies. First, BCT should improve the quality of healthcare service delivery. Second, patients could be granted the opportunity to earn money with their data, through data sharing with studies. Third, social value can also be generated by reducing opportunities for fraud and supporting honesty and ethical behavior when sharing data [42] (p. 35).
3.3.4. Limitations and Challenges of BCT (−)—Cons of Implementing a BC
The general limitations and challenges of BCT such as the conflict between transparency, security, and privacy, also apply to the healthcare sector. The data to be managed are not only critical in terms of their correctness, but also very sensitive and must not be made public. In addition to the general limitations, the main problem in the healthcare sector is that BC is still at a very early stage in this area. There are no commercial applications of BCT so far and very few large studies. The actual value proposition of BCT can only be predicted in theory, as well as the actual total costs and disadvantages [42] (p. 3). The expected value proposition of BCT is therefore based on the expectations of actors and not on experience [42] (p. 13).
In healthcare, there are few very large and powerful players that would need to collaborate for a secure BC. Most of the anticipated benefits will only come to bear with a full implementation. Errors the storage of patient data must be eliminated from an implementation because, in the worst case, patients could be harmed. In addition, all existing patient data would first have to be transferred to the BC securely and without the possibility of manipulation.
3.3.5. Alternative Solutions without the Use of BCT
Patients’ medical records are often distributed across several systems provided by different players. Merging and digitizing all patient data offers significant value in itself, which should not be directly credited to BCT. However, the merged data must be viewed and processed by many different healthcare providers, physicians, hospitals, insurers, and others, which creates many problems, including security and privacy [10] (p. 36503). In this area, a large, trusted provider that can guarantee data correctness and be held liable for errors could establish itself. The large provider could also make changes to the data set traceable without the BCT.
In Germany, for example, the elektronische Patientenakte (electronic patient file) was introduced in 2021. Since a large volume of relevant data is currently only stored in one place and often not even digitally, such as in file folders in doctors’ offices, examinations often must be repeated. All 70 million people with public health insurance will soon be able to store important data, such as their vaccination record or allergy report, in this secure database. The insured person can decide whether and which of his or her data he or she would like to have stored digitally and can then determine who may access this data and for how long [43].
The elektronische Patientenakte (electronic patient file) is not based on BCT but on a central database in which access rights are restricted and the data is encrypted. With 70 million insured people, very large amounts of data are generated, which cannot be stored in a reasonable way with BCT.
Conclusion and assessment—BCT could theoretically solve some of the problems of the healthcare system. However, no case could be identified in which BCT is without alternatives, so it must compete with alternative solutions that do not include a BC. Furthermore, some participants demonstrate no interest in implementing a BC and the greatest value only exists with a very broad implementation of BCT. For example, the very high level of information in the medical field, such as diagnoses or prescriptions, could lead to resistance from some physicians because they may feel controlled or threatened in their autonomy [44] (p. 49653). In Germany, doctors are bound by a duty of confidentiality, and any solution must comply with this legal requirement, which could pose a challenge to the implementation of transparent BCs. In the healthcare sector, there is already a high level of trust among most participants, which speaks against a BC solution in tracking and tracing. In addition, many drugs are monopolized due to patents and manufacturer guarantees of quality.
4. Implications on the Added Value of BCT for Respective SCs
Within the literature analysis, the following clusters were analyzed in possible applications of BCT in SCM: Food SC, Health SC, logistical process, Luxury SC and other applications. Within the cluster of food SCs, a model for grain SC, the cooperation of Walmart with IBM, and the traceability of meat were presented in detail. The main objective found in this area was a need for traceability, either by making this data available to customers or allowing companies to make recalls more efficient. The study showed that a BC solution can help this area by providing the traceability data of companies anonymously while allowing the customer to enjoy high confidence in the data. However, it was concluded that BC is only suitable for this area in exceptional cases, especially in comparison to alternatives, because the trading volumes are very large and the value of most items is comparatively low. In addition, the interface between BCs and physical foodstuffs was identified as a problem, as it is often difficult to produce this type of interface. As an ideal case, we suggest that the interface should be as secure as the database itself to create a well-balanced system. In conclusion, no general need for a BC solution could be identified in the field of food SCs, due to the interface problem, high volumes, and low values. On the other hand, the customer must be able to appreciate the advantages of BCT, which would require an understanding of the complex technology.
Healthcare SCs were the second largest cluster found; in this case, there is a lot of critical data to be stored. A major concern in this area is to ensure the immutability, completeness, and correctness of the stored data. For healthcare in particular, the paradox of the trade-off between security resulting from transparency and the resulting lower level of data protection found by this thesis applies. Since data protection is a high priority in healthcare, trade-offs in BC security must be accepted. A major problem of BCT in this cluster is that like the network effect, the benefits of BCT are not evident until it is fully implemented. Until then, the impact of BCT can only be predicted in theory. Since some participants are not interested in joining the network or would like to be the last to join, full implementation is very unlikely unless legislation introduces an obligation. Further, especially when storing patient data, the amount of data is simply too large for BCT. When storing tracking data to verify the authenticity of a drug, no need for a BC solution could be identified. In the case of drugs, trust in the manufacturer is already assumed, so creating trust does not generate any additional benefits here. The verification of authenticity via a central solution or the manufacturer’s own solution has a similar effect to a BC solution. In summary, no general need for a BC could be verified in the healthcare sector.
Luxury SCs manage valuable products, which are usually traded in relatively small quantities; thus, the advantages of BCT can be exploited effectively, according to the guideline of high value, low volume. With valuable products, trust is often a challenge, and laymen cannot verify the authenticity of many products. BCT can store traceability data securely so that the end customer can enjoy a high level of confidence in the data. In the area of luxury goods, a certain level of privacy is desired, as tracking data must not fall into the wrong hands. For this reason, permissioned BCs are also suitable in this area, where access is strictly limited. In the case of luxury goods, a secure interface with the BC can usually be created by clearly marking the goods. The additional costs for the interface are relatively low compared to the often-high total costs. In this area, most BC solutions are implemented in-house or, alternatively, trusted third parties are established. Nevertheless, most of the value proposition comes from the storage of the data by a trusted third party and not from the BCT. However, the customer could enjoy the advantage of greater security with a BC solution because it would ensure that older data could not be manipulated.
The identified clusters, Luxury, Food, and Health SC, can be analyzed according to strategic considerations in order to compare them with other possible fields of application. The strategic trade-offs can be evaluated in terms of the following needs and strategies: immutability of data, Smart Contracts, digital currency, traceability, visibility and transparency, privacy, value to be transferred, volume to be transferred, trust level, and cost sensitivity (See Table 2).

Table 2.
General determination of the value of BCT for selected SC [45] (p. 28) (greatly modified).
Although BCT offers a value proposition that could theoretically offset the costs in many examples, successful implementations still do not exist, apart from cryptocurrencies. Bitcoin has now existed for 12 years and has thus demonstrated a very successful application of BCT. Therefore, parts of the research material are very critical towards a transfer of BCT to areas other than Bitcoin. Ammous (2016) summarizes that the only commercially successful application of BCT is digital cash, specifically Bitcoin. According to him, other applications have not made it out of prototype status because they cannot compete with the best practices currently available. He concludes from this observation that the redundancies in storing transactions and the expense of consensus algorithms can only be justified with digital money. With digital money, no interface with the outside world is necessary, because the money cannot exist without the BCT and, on the other hand, the amounts of data are very small. There is no application that exploits BCT as well as digital money because BCT was developed specifically for this purpose, according to Ammous (2016) there is no reason to expect that this very specific technology can be successfully implemented in other areas [46] (p. 5).
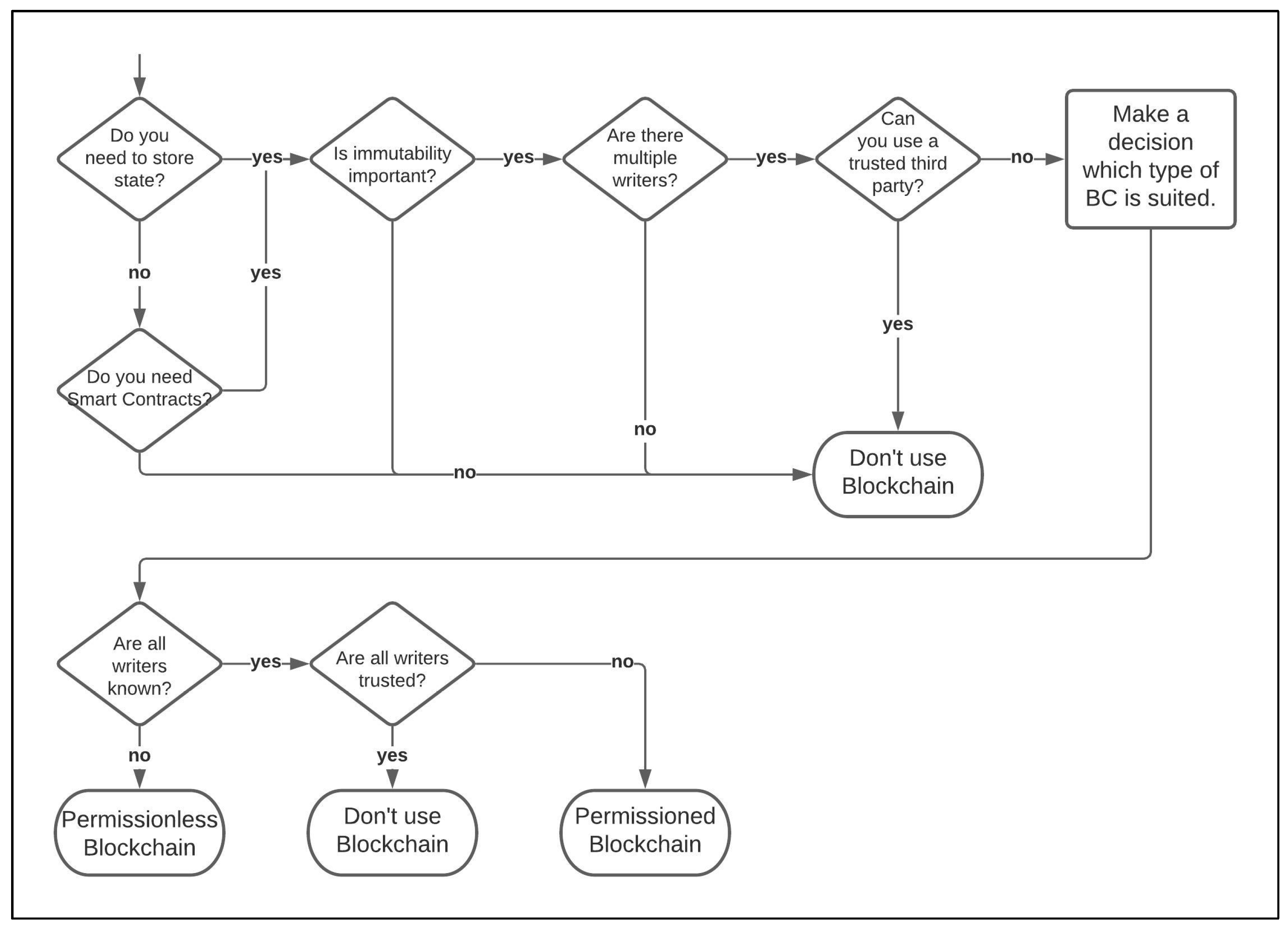
However, the authors of this paper are not as critical about the BCT because some use cases exist in which a low-cost implementation could have a benefit. Nevertheless, some identified BC solutions are so far away from the actual concept of BCT that the term BC, in the sense of a proof of work-based BC, such as Bitcoin’s BC, no longer applies. For example, if a Trusted Third Party stores a BC centrally and no other participant stores the BC for cost reasons, this system relies on trust towards the Trusted Third Party. Older blocks could be changed without any problems, so the advantages of BCT are omitted in this example. The following decision tree (see Figure 2) can be used to assess whether a BC could be a potential solution for a specific application, although cost and marketing effects are not considered. If there is the potential for a successful implementation of a BC solution, the lower part of the diagram can be used to estimate which type of BC might be the right choice.
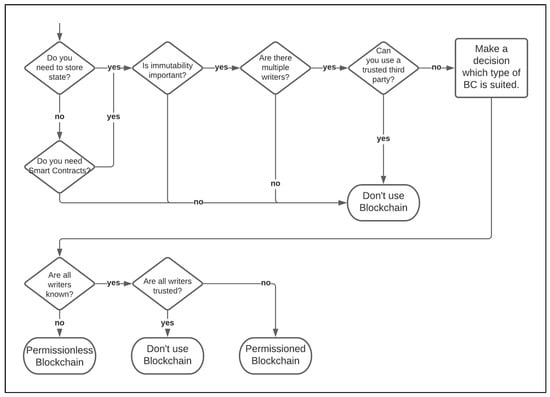
Figure 2.
Decision tree on whether a BC is an appropriate technology for a use case [47] (p. 47) (greatly modified).
The implementation of a BC is a complex procedure, in which many individual aspects must be considered. The decision tree is intended to serve as a potential assessment, especially for companies that possess no expertise in BCT. The management of a SC should implement BCT not because the technology works in cryptocurrencies, is revolutionary and exerts a marketing effect but, rather, because it is more effective than its alternatives. According to Verhoeven et al. (2018), the best and most efficient technology should always be selected regarding a concrete problem, which requires a comprehensive understanding of the problem and the available technologies. In the case of BCT, however, it is often the other way around: some organizations seem to first choose a solution based on BCT and then to tune the problem with BC [27] (p. 18). This may be one reason for the low success rate of BC projects, as after one year, only 8% of started projects are still active [3].
5. Summary, Findings and Outlook
In summary, the study has shown that the application of BCT is especially beneficial for goods with a high value. The advantages of BCT are further augmented if, in addition, the trade volume of the goods is low. At the same time, SCs should be affected as little as possible by the following three key problems found with BCT. First, the interface between reality and the digital twin should be as secure as the database or BC solution. If a secure interface cannot be implemented with reasonable effort, a BC solution is not advisable, which is the case for many products. Second, the primary conflicting goals of BCT must not pose a significant problem; the demand for transparency and the immutability of data must be more important than the need to protect sensitive data. Third, SC participants must also be able to perceive and appreciate the benefits of BCT. Often, the end customer is the main beneficiary of an implemented BC. Understanding BCT is necessary for an increased willingness to pay, which must cover the increased costs. This knowledge cannot be taken for granted, especially in the mass market, and educating customers is often not profitable. In conclusion, the management of an SC should implement BCT not because the technology works in cryptocurrencies, is revolutionary, and exerts a marketing effect, but only if it is more effective than its alternatives.
No paper is without limitations. Due to space limitations, the much-described topic of BCT cannot be fully discussed, and this paper is no exception. Future research could follow up on the decision tree presented and add more decisions regarding the needs of the business, although this would be at the expense of clarity. In addition, further research could analyze how customers’ knowledge of BCT affects the technology’s value proposition, as only customers with a basic understanding of BCT can appreciate its benefits.
Author Contributions
Conceptualization, M.B. and H.W.; methodology, M.B.; validation, M.B. and H.W.; formal analysis, M.B.; investigation, M.B.; writing—original draft preparation, M.B.; writing—review and editing, M.B. and H.W.; visualization, M.B.; supervision, H.W. All authors have read and agreed to the published version of the manuscript.
Funding
This research received no external funding.
Institutional Review Board Statement
Not applicable.
Informed Consent Statement
Not applicable.
Data Availability Statement
Data sharing not applicable.
Acknowledgments
The authors thank the anonymous reviewers for their constructive support. The comments helped to improve the quality of the paper.
Conflicts of Interest
The authors declare no conflict of interest.
References
- Xu, M.; Chen, X.; Kou, G. A systematic review of blockchain. Financ. Innov. 2019, 5, 27. [Google Scholar] [CrossRef] [Green Version]
- Hinckeldeyn, J. Blockchain-Technologie in der Supply Chain: Einführung und Anwendungsbeispiele; Springer Fachmedien Wiesbaden: Wiesbaden, Germany, 2019. [Google Scholar]
- Browne, R. There Were More than 26,000 New Blockchain Projects Last Year—Only 8% Are Still Active. CNBC, 9 November 2017. Available online: https://www.cnbc.com/2017/11/09/just-8-percent-of-open-source-blockchain-projects-are-still-active.html (accessed on 16 November 2021).
- Berneis, M.; Winkler, H. Applications of Blockchain Technology in Logistics and Supply Chain Management—Insights from a Systematic Literature Review. Logistics 2021, 5, 43. [Google Scholar] [CrossRef]
- Catalini, C.; How Blockchain Applications Will Move Beyond Finance. Harvard Business Review, 2 March 2017. Available online: https://hbr.org/2017/03/how-blockchain-applications-will-move-beyond-finance (accessed on 16 November 2021).
- Cacey, M.J.; Wong, P. Global Supply Chains Are about to Get Better. Thanks to Blockchain. Harvard Business Review, 13 March 2017. Available online: https://hbr.org/2017/03/global-supply-chains-are-about-to-get-better-thanks-to-blockchain (accessed on 10 December 2020).
- Kim, J.-S.; Shin, N. The Impact of Blockchain Technology Application on Supply Chain Partnership and Performance. Sustainability 2019, 11, 6181. [Google Scholar] [CrossRef] [Green Version]
- Roeck, D.; Sternberg, H.; Hofmann, E. Distributed ledger technology in supply chains: A transaction cost perspective. Int. J. Prod. Res. 2020, 58, 2124–2141. [Google Scholar] [CrossRef] [Green Version]
- Colaka, M.; Kaya, I.; Ozkan, B.; Budakc, A.; Karasan, A. A multi-criteria evaluation model based on hesitant fuzzy sets for blockchain technology in supply chain management. J. Intell. Fuzzy Syst. 2020, 38, 935–946. [Google Scholar] [CrossRef]
- Al-Jaroodi, J.; Mohamed, N. Blockchain in Industries: A Survey. IEEE Access 2019, 7, 36500–36515. [Google Scholar] [CrossRef]
- Litke, A.; Anagnostopoulos, D.; Varvarigou, T. Blockchains for Supply Chain Management: Architectural Elements and Challenges Towards a Global Scale Deployment. Logistics 2019, 3, 5. [Google Scholar] [CrossRef] [Green Version]
- Montecchi, M.; Plangger, K.; Etter, M. It’s real, trust me! Establishing supply chain provenance using blockchain. Bus. Horiz. 2019, 62, 283–293. [Google Scholar] [CrossRef] [Green Version]
- Min, H. Blockchain technology for enhancing supply chain resilience. Bus. Horiz. 2019, 62, 35–45. [Google Scholar] [CrossRef]
- Choi, T.-M. Blockchain-technology-supported platforms for diamond authentication and certification in luxury supply chains. Transp. Res. Part E Logist. Transp. Rev. 2019, 128, 17–29. [Google Scholar] [CrossRef]
- Chung, G.; González-Peralta, J.; Turner, K.; Gockel, B. Blockchain in Logistics—Perspectives on the upcoming impact of blockchain technology and use cases for the logistics industry. DHL Cust. Solut. Innov. 2018, 1, 1–28. [Google Scholar]
- Altoros. A Close Look at Everledger—How Blockchain Secures Luxury Goods. 2017. Available online: https://www.altoros.com/blog/a-close-look-at-everledger-how-blockchain-secures-luxury-goods/ (accessed on 15 September 2021).
- EVERLEDGER. A Marketplace for Blockchain Diamonds with Verified Provenance and Sustainability Claims. Available online: https://www.everledger.io/industry-solutions/diamonds/ (accessed on 15 September 2021).
- Breitling. Digital Passport on Breitling Blockchain. Available online: https://www.breitling.com/de-en/service/blockchain/ (accessed on 15 September 2021).
- EVERLEDGER. The Story of Everledger. Available online: https://www.everledger.io/about/ (accessed on 15 September 2021).
- Demestichas, K.; Peppes, N.; Alexakis, T.; Adamopoulou, E. Blockchain in Agriculture Traceability Systems: A Review. Appl. Sci. 2020, 10, 4113. [Google Scholar] [CrossRef]
- Hackett, R. Walmart and 9 Food Giants Team Up on IBM Blockchain Plans FORTUNE, 22 August 2017. Available online: https://fortune.com/2017/08/22/walmart-blockchain-ibm-food-nestle-unilever-tyson-dole/ (accessed on 15 September 2021).
- The TrustChainTM Initiativ. TrustChain. 2018. Available online: https://www.trustchainjewelry.com (accessed on 15 September 2021).
- Partz, H. US Seafood Giant Bumble Bee Foods to Use SAP Blockchain Tech in Supply Chain. TrustChain, 8 March 2019. Available online: https://cointelegraph.com/news/north-american-seafood-firm-to-use-blockchain-tech-in-supply-chain/amp (accessed on 15 September 2021).
- Arena, A.; Bianchini, A.; Perazzo, P.; Vallati, C.; Dini, G. Bruschetta: An IoT Blockchain-Based Framework for Certifying Extra Virgin Olive Oil Supply Chain; IEEE: New York, NY, USA, 2019. [Google Scholar]
- Bumblauskas, D.; Mann, A.; Dugan, B.; Rittmer, J. A blockchain use case in food distribution: Do you know where your food has been? Int. J. Inf. Manag. 2020, 52, 102008. [Google Scholar] [CrossRef]
- Zhang, X.; Sun, P.; Xu, J.; Wang, X.; Yu, J.; Zhao, Z.; Dong, Y. Blockchain-Based Safety Management System for the Grain Supply Chain. IEEE Access 2020, 8, 36398–36410. [Google Scholar] [CrossRef]
- Verhoeven, P.; Sinn, F.; Herden, T. Examples from Blockchain Implementations in Logistics and Supply Chain Management: Exploring the Mindful Use of a New Technology. Logistics 2018, 2, 20. [Google Scholar] [CrossRef] [Green Version]
- Barge, P.; Biglia, A.; Comba, L.; Aimonino, D.R.; Tortia, C.; Gay, P. Radio Frequency IDentification for Meat Supply-Chain Digitalisation. Sensors 2020, 20, 4957. [Google Scholar] [CrossRef] [PubMed]
- Ferdousi, T.; Gruenbacher, D.; Scoglio, C.M. A Permissioned Distributed Ledger for the US Beef Cattle Supply Chain. IEEE Access 2020, 8, 154833–154847. [Google Scholar] [CrossRef]
- Followfood. Available online: http://followfood.de (accessed on 15 September 2021).
- Stiftung Warentest. How to Crack Fish Codes. Stiftung Warentest, 13 December 2012. Available online: https://www.test.de/Rueckverfolgbarkeit-von-Fisch-So-knacken-Sie-Fischcodes-4471489-0/ (accessed on 15 September 2021).
- European Union. Guidelines of 5 November 2013 on Good Distribution Practice of Medicinal Products for Human Usetext with EEA Relevance; European Union: Brussels, Belgium, 2013; p. 14. [Google Scholar]
- Modum. Data Integrity for Supply Chain Operations Powered by Blockchain Technology. 2017. Available online: https://modum.io/wp-content/uploads/2017/08/modum-whitepaper-v.-1.0.pdf (accessed on 19 June 2020).
- Azzi, R.; Chamoun, R.K.; Sokhn, M. The power of a blockchain-based supply chain. Comput. Ind. Eng. 2019, 135, 582–592. [Google Scholar] [CrossRef]
- Figueroa, S.; Anorga, J.; Arrizabalaga, S. An Attribute-Based Access Control Model in RFID Systems Based on Blockchain Decentralized Applications for Healthcare Environments. Computers 2019, 8, 57. [Google Scholar] [CrossRef] [Green Version]
- Sylim, P.; Liu, F.; Marcelo, A.; Fontelo, P. Blockchain Technology for Detecting Falsified and Substandard Drugs in Distribution: Pharmaceutical Supply Chain Intervention. JMIR Res. Protoc. 2018, 7, e10163. [Google Scholar] [CrossRef]
- Singh, R.; Dwivedi, A.D.; Srivastava, G. Internet of Things Based Blockchain for Temperature Monitoring and Counterfeit Pharmaceutical Prevention. Sensors 2020, 20, 3951. [Google Scholar] [CrossRef]
- Issaoui, Y.; Khiat, A.; Bahnasse, A.; Ouajji, H. Toward Smart Logistics: Engineering Insights and Emerging Trends. Arch. Comput. Methods Eng. 2021, 28, 3183–3210. [Google Scholar] [CrossRef]
- Yong, B.; Shen, J.; Liu, X.; Li, F.; Chen, H.; Zhou, Q. An intelligent blockchain-based system for safe vaccine supply and supervision. Int. J. Inf. Manag. 2020, 52, 102024. [Google Scholar] [CrossRef]
- Jayaraman, R.; AlHammadi, F.; Simsekler, M.C.E. Managing Product Recalls in Healthcare Supply Chain. In Proceedings of the 2018 IEEE International Conference on Industrial Engineering and Engineering Management (IEEM), Bangkok, Thailand, 16–19 December 2018; pp. 293–297. [Google Scholar]
- Al-Megren, S.; Alsalamah, S.; Altoaimy, L.; Alsalamah, H.; Soltanisehat, L.; Almutairi, E.; Pentland, A. Blockchain Use Cases in Digital Sectors: A Review of the Literature. In Proceedings of the 2018 IEEE International Conference on Internet of Things (iThings) and IEEE Green Computing and Communications (GreenCom) and IEEE Cyber, Physical and Social Computing (CPSCom) and IEEE Smart Data (SmartData), Halifax, NS, Canada, 30 July–3 August 2018. [Google Scholar]
- Palas, M.J.U.; Bunduchi, R. Exploring interpretations of blockchain’s value in healthcare: A multi-stakeholder approach. Inf. Technol. People 2020. [Google Scholar] [CrossRef]
- Federal Ministry of Health. Die Elektronische Patientenakte (ePA); Federal Ministry of Health: Bonn, Germany, 2021. Available online: https://www.bundesgesundheitsministerium.de/elektronische-patientenakte.html (accessed on 15 September 2021).
- Wan, P.K.; Huang, L.; Holtskog, H. Blockchain-Enabled Information Sharing Within a Supply Chain: A Systematic Literature Review. IEEE Access 2020, 8, 49645–49656. [Google Scholar] [CrossRef]
- Kumar, A.; Liu, R.; Shan, Z. Is Blockchain a Silver Bullet for Supply Chain Management? Technical Challenges and Research Opportunities. Decis. Sci. 2020, 51, 8–37. [Google Scholar] [CrossRef]
- Ammous, S.H. Blockchain Technology: What is it Good for? SSRN J. 2016. [Google Scholar] [CrossRef] [Green Version]
- Wust, K.; Gervais, A. Do you need a Blockchain? In Proceedings of the 2018 Crypto Valley Conference on Blockchain Technology (CVCBT), Zug, Switzerland, 20–22 June 2018. [Google Scholar]
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2021 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).