Abstract
The Collins diffraction transform (CDT) describes the optical wave diffraction from the generic paraxial optical system. The CDT has as special cases the diffraction domains given by the Fourier, Fresnel and fractional Fourier transforms. In this paper, we propose to describe the optical double random phase encoding (DRPE) using a nonlinear joint transform correlator (JTC) and the CDT. This new description of the nonlinear JTC-based encryption system using the CDT covers several optical processing domains, such as Fourier, Fresnel, fractional Fourier, extended fractional Fourier and Gyrator domains, among others. The maximum number of independent design parameters or new security keys of the proposed encryption system using the CDT increases three times in comparison with the same encryption system that uses the Fourier transform. The proposed encryption system using the CDT preserves the shift-invariance property of the JTC-based encryption system in the Fourier domain, with respect to the lateral displacement of both the key random mask in the decryption process and the retrieval of the primary image. The viability of this encryption system is verified and analysed by numerical simulations.
1. Introduction
The double random phase encoding (DRPE) proposed by Réfrégier and Javidi is a well known and highly successful system for optical image encryption [1,2,3,4]. The encrypted image of the DRPE system is a stationary white noise image that it is obtained from an original image, which is the image to encrypt and two random phase masks (RPMs) placed in the input plane and the Fourier plane. The DRPE was extended from the Fourier domain, to the Fresnel domain [5,6] and the fractional Fourier domain [7], in order to improve the security strength of the optical encryption system. The first optical implementation of the DRPE system was carried out using a classical 4f-processor [8]. This classical optical processor is a holographic system that requires a strict optical alignment. Besides, the encrypted image is a complex-valued distribution and, in addition to this, the decryption process needed an exact complex conjugate of one of the phase masks used as a key. In order to overcome this constraints, the use of the joint transform correlator (JTC) architecture to optically implement the DRPE system was proposed in Reference [9]. For the JTC architecture, the encrypted image is an intensity distribution that is captured in the Fourier plane and the decryption system utilizes the same security key previously used in the encryption system.
The security of the DRPE system implemented using a 4f-processor is vulnerable to chosen-plaintext attacks (CPA) [10], known-plaintext attacks (KPA) [10] and ciphertext-only attack (COA) [11]. The DRPE system implemented with a JTC is also vulnerable to CPA [12], KPA [13] and COA [14]. Other modifications of the JTC architecture in different optical processing domains to implement the DRPE system have been proposed by several authors [15,16,17,18,19,20,21,22]. These new proposals simplify the optical setup of the encryption system, increase the security of the encryption system and improve the quality of the decrypted image.
This year, the DRPE system was extended to the Collins diffraction domain (CDD) in order to improve the security of this system and to present a generalized framework theory for the DRPE optical image encryption system [23]. A general volume holographic encryption-decryption system based on the two wave mixing technique and the Collins diffraction transform (CDT), which can be applied to several optical processing domains, was presented in Reference [24]. The CDT describes the optical wave diffraction from the generic paraxial optical system [25,26,27]. In this work, we present a novel extension of the nonlinear JTC-based encryption system [16] to the CDD, with the purpose of increasing the security of the system and representing several optical processing domains, such as Fourier, Fresnel, fractional Fourier, extended fractional Fourier and Gyrator domains, among others, for the encryption and decryption systems by using the CDT formalism. The use of the CDT by the encryption system based on a nonlinear JTC allows the introduction of new security keys which are not present in the same encryption system that uses the Fourier transform. The encrypted image is given by the nonlinear modification of the joint Collins power distribution (JCPD). This nonlinear modification permits a very good quality for the decrypted image and also allows the reproduction of the DRPE system as it was originally formulated by Réfrégier and Javidi [1]. Finally, the additional security keys produced by the use of the CDT over the encryption system and the nonlinear modification of the JCPD for computing the encrypted image increase the security of the proposed optical image encryption and decryption systems in this paper.
The rest of the paper is organized as follows: Section 2 provides the mathematical background related to the CDT. In Section 3, the proposed encryption system based on a nonlinear JTC in the CDD is presented and numerical simulations are performed to illustrate the proposal. The analysis of the proposal along with the provided results lead to outline the conclusions in Section 4.
2. Collins Diffraction Transform (CDT)
The Collins diffraction transform (CDT) of an object , written in one-dimensional notation for the sake of simplicity, for an ABCD-transfer matrix M can be expressed as [25,26,27]
with
where the operator denotes the CDT, the parameter is the wavenumber, is the wavelength, l is the propagation distance from an input plane (x) to an output plane (u) and M is the transfer matrix, characterizing the wave propagation properties in a lossless linear optical system with . Generally, the matrix elements A, B, C and D are real values, A and D are dimensionless, while B has a unit of length and C has a unit of inverse of length but these matrix elements can be defined using complex numbers [28].
The inverse CDT is defined as
with
Some special case of the CDT that represent several important optical transformations are determined by the real or complex values of the elements of the ABCD-transfer matrix M [23,28]. For instance, the following optical transformation are obtained from Equation (1) when
The parameter and denote the fractional order of the fractional Fourier transform and the rotation angle of the Gyrator transform, respectively [29,30]. Some useful properties of the CDT that will be used later in the encryption and decryption systems are
where is a real constant.
3. Optical Image Encryption System Based on a Nonlinear JTC Architecture in the Collins Diffraction Domain
The real-valued image to be encrypted (original image) has its values in the interval [0, 1] and the random phase masks (RPMs) and are given by
where and are normalized positive functions randomly generated, statistically independent and uniformly distributed in the interval [0, 1]. Figure 1 (part I) shows the optical encryption system based on a nonlinear JTC architecture in the Collins diffraction domain (CDD). The input plane of the nonlinear JTC for the encryption system has two non-overlapping data distributions placed side-by-side. The first data distribution is the original image placed against the RPM and modulated by a pure linear phase term
where is a real constant. The second data distribution of the input plane of the JTC is the RPM modulated by another pure linear phase term
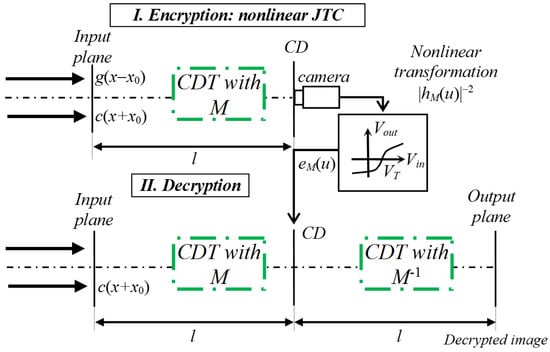
Figure 1.
Schematic representation of the optical setup. The part I is the encryption system based on a nonlinear joint transform correlator (JTC) architecture in the Collins diffraction domain (CDD) and the part II is the decryption system composed by an two successive Collins diffraction transforms (CDTs).
The CDT for an ABCD-transfer matrix M of the functions and are represented by
For the encryption system, and are placed side by side on the input plane of the JTC at coordinates and , respectively. We define the joint Collins power distribution (JCPD) for an ABCD-transfer matrix M as
In order to obtain the encrypted image , we divide the JCPD by the nonlinear term
If is equal to zero for a particular value of u, this intensity value is substituted by a small constant to avoid singularities when computing . The encrypted image is a real-valued function that can be computed using two intensity distribution: JCPD and . The security keys of the encryption and decryption systems are given by the and the elements of the ABCD-transfer matrix M. The possible values of the elements A, B, C and D of the transfer matrix M has three degrees of freedom, because the elements of the transfer matrix M must satisfy . When the proposed encryption system of this work is performed in the Fourier domain, the only security key is given by the RPM . Therefore, the nonlinear JTC-based encryption system using the CDT allows the threefold increase of the number of security keys in comparison with the same encryption system that uses the Fourier transform.
In the decryption system (Figure 1, part II), the data distribution is placed at coordinate in the input plane of the decryption system and, consequently, the encrypted image placed centred in the CDD is illuminated by . Therefore, this initial step of the decryption system is
The fourth term on the right side of Equation (14) retains the information to be decrypted [16]. Therefore, when we perform a inverse CDT with the transfer matrix of that fourth term and then, we take the absolute value, the decrypted image at coordinate is obtained as
The nonlinearity introduced in the computation of the encrypted image of Equation (13) allows the retrieval of the original image at the output plane of the decryption process (Equation (15)). Note that if we use the data distribution shifted to the position of coordinate for the initial step of the decryption system, the decrypted image can be recovered centred at coordinate
The previous equation proves that the encryption-decryption system based on a nonlinear JTC in the CDD preserves the shift-invariance property of the data distribution for decryption and the retrieval of the original image, in the same way as the Fourier domain-JTC encryption system does. The data distribution of Equation (10) is defined in terms of the security key of the encryption and decryption systems given by the RPM .
The results of the numerical simulations for the encryption and decryption systems, following the description of these systems above, are presented in Figure 2 and Figure 3, respectively. The images utilized in the security system have a resolution of pixels in grayscale. The original image to encrypt and the random distribution image of the RPM are shown in Figure 2a,b, respectively. The random distribution image of the RPM has different values but the same appearance of the image presented in Figure 2b. The elements of the ABCD-transfer matrix M for the encryption and decryption systems are defined as: , , and . For these elements of the ABCD-transfer matrix M, the CDT reduces to a Fresnel transform
where the operator denotes the Fresnel transform at parameters and l. The optical transform or processing domain depends on the values of the elements of the ABCD-transfer matrix M, just as it was presented in Equation (5). For this numerical simulation of the encryption and decryption systems, we use the wavelength = 543 nm and the propagation distance l = 50 mm. Therefore, the values of the wavelength and the propagation distance l are two security keys for the encryption and decryption systems. The encrypted image for the security keys = 543 nm, l = 50 mm and the RPM is depicted in Figure 2c.
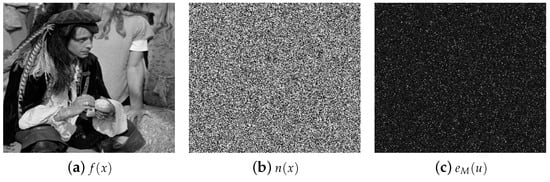
Figure 2.
(a) Original image to encrypt . (b) Random distribution image of the random phase mask (RPM) . (c) Encrypted image for the security keys nm, mm and the RPM .
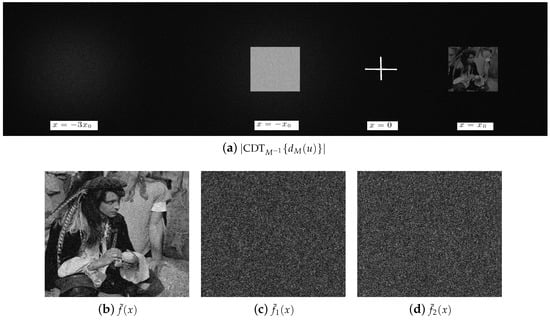
Figure 3.
(a) Absolute value of the output plane for the decryption system with the right values of the security keys , l and the RPM . (b) Magnified region of Figure 3a centred at coordinate which is the decrypted image . Decrypted images when: (c) the security key of the decryption system given by the RPM is different from the RPM used in the encryption system and (d) an incorrect wavelength of = 575 nm is used in the decryption system.
Figure 3a shows the absolute value of the output plane for the decryption system with the same values of the security keys , l and the RPM that were used in the encryption system. The decrypted image presented in Figure 3b is the magnified region and centred at position of the Figure 3a. We use the root mean square error (RMSE) in order to evaluate the quality of the decrypted image. The RMSE is defined by [16]
where , and denote the original image and the decrypted image, respectively. The values of the RMSE metric to evaluate the quality of the image are values between 0 and 1; when the value of the RMSE metric is near or equal to 0, this metric indicates an excellent quality of the image for the retrieval of the decrypted image at the output of the decryption system, whereas the values of the RMSE metric near or equal to 1 represent a worse quality of the decrypted image. The RMSE between the original image of Figure 2a and the decrypted image of Figure 3b is 0.17. Using a typical modern office computer, the computing time for the proposed encryption and decryption systems are 0.37 and 0.35 seconds, respectively. The time to compute the encrypted and decrypted images is almost the same because the encryption and decryption systems perform two numerical Fresnel transforms.
Finally, we test the influence of the right values of the security keys on the decrypted image resulting in the decryption system by numerical simulations. The decrypted images presented in Figure 3c,d are noisy images that were obtained at the output plane of the decryption system when a wrong RPM or an incorrect wavelength were provided to the decryption system, respectively, whenever l = 50 mm. These decrypted images have a noisy appearance without any information of the original image. The RMSE between the original image of Figure 2a and the decrypted image of Figure 3c,d are 0.81 and 0.79, respectively. If an incorrect distance of propagation l is used in the decryption process, the obtained decrypted image is a noisy image similar to the one shown in Figure 3c. The right retrieval of the original image at the output of the decryption system, only is possible when the all security keys with their correct values are used in the decryption system.
4. Conclusions
In this paper, we have presented a novel extension of the image encryption system based on a nonlinear JTC architecture to the CDD. The proposed encryption system is a generalized optical security system which can represent several optical processing domain, such as the Fourier, Fresnel, fraction Fourier, extended fractional Fourier and Gyrator domains, among others. The selected optical processing domain depends on the values of the elements of the ABCD-transfer matrix M. The extension of the JTC-based encryption system to the CDD introduces additional security keys to the security system proposed in this work. These additional security keys correspond to the three degrees of freedom of the CDT given by the values the elements of the ABCD-transfer matrix M and the condition . The nonlinear modification of JCPD when the encrypted image is computed along with the additional security keys allow the improvement of the security of the encryption and decryption systems against the brute force and plaintext attacks. Finally, the presented security system preserves the shift-invariance property of the RPM for the decryption system and the retrieval of the original image.
Author Contributions
The work described in this article is the collaborative development of all authors. Conceptualization, J.M.V.O., R.A.P. and C.O.T.M.; Methodology, J.M.V.O., R.A.P. and C.O.T.M.; Software, J.M.V.O. and R.A.P.; Validation, C.O.T.M.; Investigation, J.M.V.O., R.A.P. and C.O.T.M.; Writing—original draft preparation, J.M.V.O. and R.A.P.; Writing—review and editing, J.M.V.O. and C.O.T.M.; Supervision, C.O.T.M.
Funding
This research has been funded by the Universidad de La Guajira (Riohacha) and the Universidad Popular del Cesar from Valledupar (Cesar).
Conflicts of Interest
The authors declare no conflict of interest.
References
- Réfrégier, P.; Javidi, B. Optical image encryption based on input plane and Fourier plane random encoding. Opt. Lett. 1995, 20, 767–769. [Google Scholar] [CrossRef] [PubMed]
- Millán, M.S.; Pérez-Cabré, E. Optical data encryption. In Optical and Digital Image Processing: Fundamentals and Applications; Cristóbal, G., Schelkens, P., Thienpont, H., Eds.; Wiley-VCH Verlag GmbH & Co.: Hoboken, NJ, USA, 2011; pp. 739–767. [Google Scholar]
- Javidi, B.; Carnicer, A.; Yamaguchi, M.; Nomura, T.; Pérez-Cabré, E.; Millán, M.; Nishchal, N.; Torroba, R.; Barrera, J.; He, W.; et al. Roadmap on optical security. J. Opt. 2016, 18, 083001. [Google Scholar] [CrossRef]
- Millán, M.S.; Pérez-Cabré, E.; Vilardy, J.M. Nonlinear techniques for secure optical encryption and multifactor authentication. In Advanced Secure Optical Image Processing for Communications; Al Falou, A., Ed.; IOP Publishing: Bristol, UK, 2018; pp. 8-1–8-33. [Google Scholar]
- Matoba, O.; Javidi, B. Encrypted optical memory system using three-dimensional keys in the Fresnel domain. Opt. Lett. 1999, 24, 762–764. [Google Scholar] [CrossRef] [PubMed]
- Situ, G.; Zhang, J. Double random phase encoding in the Fresnel domain. Opt. Lett. 2004, 29, 1584–1586. [Google Scholar] [CrossRef] [PubMed]
- Unnikrishnan, G.; Joseph, J.; Singh, K. Optical encryption by double-random phase encoding in the fractional Fourier domain. Opt. Lett. 2000, 25, 887–889. [Google Scholar] [CrossRef] [PubMed]
- Goodman, J.W. Introduction to Fourier Optics; McGraw-Hill: New York, NY, USA, 1996. [Google Scholar]
- Nomura, T.; Javidi, B. Optical encryption using a joint transform correlator architecture. Opt. Eng. 2000, 39, 2031–2035. [Google Scholar]
- Frauel, Y.; Castro, A.; Naughton, T.J.; Javidi, B. Resistance of the double random phase encryption against various attacks. Opt. Express 2007, 15, 10253–10265. [Google Scholar] [CrossRef]
- Guo, C.; Liu, S.; Sheridan, J.T. Iterative phase retrieval algorithms. Part II: Attacking optical encryption systems. Appl. Opt. 2015, 54, 4709–4719. [Google Scholar] [CrossRef]
- Barrera, J.F.; Vargas, C.; Tebaldi, M.; Torroba, R. Chosen-plaintext attack on a joint transform correlator encrypting system. Opt. Commun. 2010, 283, 3917–3921. [Google Scholar] [CrossRef]
- Barrera, J.F.; Vargas, C.; Tebaldi, M.; Torroba, R.; Bolognini, N. Known-plaintext attack on a joint transform correlator encrypting system. Opt. Lett. 2010, 35, 3553–3555. [Google Scholar] [CrossRef]
- Zhang, C.; Liao, M.; He, W.; Peng, X. Ciphertext-only attack on a joint transform correlator encryption system. Opt. Express 2013, 21, 28523–28530. [Google Scholar] [CrossRef] [PubMed]
- Rueda, E.; Barrera, J.F.; Henao, R.; Torroba, R. Optical encryption with a reference wave in a joint transform correlator architecture. Opt. Commun. 2009, 282, 3243–3249. [Google Scholar] [CrossRef]
- Vilardy, J.M.; Millán, M.S.; Pérez-Cabré, E. Improved decryption quality and security of a joint transform correlator-based encryption system. J. Opt. 2013, 15, 025401. [Google Scholar] [CrossRef]
- Vilardy, J.M.; Millán, M.S.; Pérez-Cabré, E. Nonlinear optical security system based on a joint transform correlator in the Fresnel domain. Appl. Opt. 2014, 53, 1674–1682. [Google Scholar] [CrossRef] [PubMed]
- Barrera, J.F.; Jaramillo, A.; Vélez, A.; Torroba, R. Experimental analysis of a joint free space cryptosystem. Opt. Lasers Eng. 2016, 83, 126–130. [Google Scholar]
- Vilardy, J.M.; Torres, Y.; Millán, M.S.; Pérez-Cabré, E. Generalized formulation of an encryption system based on a joint transform correlator and fractional Fourier transform. J. Opt. 2014, 16, 125405. [Google Scholar] [CrossRef]
- Vilardy, J.M.; Millán, M.S.; Pérez-Cabré, E. Sistema de cifrado de imágenes basado en un correlador de transformadas conjuntas fraccionario y filtrado no lineal. Ópt. Pura Apl. 2014, 47, 35–41. [Google Scholar] [CrossRef]
- Jaramillo, A.; Barrera, J.F.; Vélez, A.; Torroba, R. Fractional optical cryptographic protocol for data containers in a noise-free multiuser environment. Opt. Lasers Eng. 2018, 102, 119–125. [Google Scholar] [CrossRef]
- Vilardy, J.M.; Millán, M.S.; Pérez-Cabré, E. Nonlinear image encryption using a fully phase nonzero-order joint transform correlator in the Gyrator domain. Opt. Lasers Eng. 2017, 89, 88–94. [Google Scholar] [CrossRef]
- Kwak, C.H.; Javidi, B. Generalized description of double random phase encoding by Collins diffraction transformation. J. Opt. 2019, 21, 015703. [Google Scholar] [CrossRef]
- Kwak, C.H.; Kim, G.Y.; Javidi, B. Volume holographic optical encryption and decryption in photorefractive LiNbO3:Fe crystal. Opt. Commun. 2019, 437, 95–103. [Google Scholar] [CrossRef]
- Collins, S.A. Lens-system diffraction integral written in terms of matrix optics. J. Opt. Soc. Am. 1970, 60, 1168–1177. [Google Scholar] [CrossRef]
- Alieva, T.; Bastiaans, M.J. Properties of the linear canonical integral transformation. J. Opt. Soc. A 2007, 24, 3658–3665. [Google Scholar] [CrossRef] [PubMed]
- Bernardo, L.M. ABCD matrix formalism of fractional Fourier optics. Opt. Eng. 1996, 35, 732–740. [Google Scholar] [CrossRef]
- Healy, J.J.; Kutay, M.A.; Ozaktas, H.M.; Sheridan, J.T. Linear Canonical Transforms: Theory and Applications; Springer: Berlin/Heidelberg, Germany, 2015. [Google Scholar]
- Ozaktas, H.M.; Zalevsky, Z.; Kutay, M.A. The Fractional Fourier Transform: With Applications in Optics and Signal Processing; Wiley: Hoboken, NJ, USA, 2001. [Google Scholar]
- Rodrigo, J.A.; Alieva, T.; Calvo, M.L. Gyrator transform: Properties and applications. Opt. Express 2007, 15, 2190–2203. [Google Scholar] [CrossRef]
© 2019 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).