1. Introduction
With the rapid advancement of technology and the increasing integration of devices, networked cyber–physical systems, particularly those utilizing SCADA (Supervisory Control and Data Acquisition) technology, have become integral components of critical infrastructure across industries, such as energy, water, transportation, and manufacturing. These systems enable efficient monitoring, control, and automation of complex processes, enhancing productivity and operational efficiency. However, the increased connectivity and integration of SCADA systems with corporate networks and the Internet have exposed them to potential cyber threats. A breach or compromise in these systems can have severe consequences, including the disruption of essential services, physical damage, financial losses, and even threats to public safety. Recent advances in cyberattack techniques and the growing sophistication of threat actors have further highlighted the criticality of implementing robust cybersecurity measures.
Various real-world examples underscore the importance of cybersecurity in networked cyber–physical systems and SCADA environments. For instance, the Stuxnet worm, discovered in 2010, specifically targeted SCADA systems in Iranian nuclear facilities. Stuxnet infiltrated Iranian PLCs (Programmable Logic Controllers), gathering data about industrial systems and causing the fast-spinning centrifuges to burn out [
1]. Another notable incident is the Ukrainian power grid cyberattack in 2015, where hackers successfully compromised SCADA systems, leading to widespread power outages affecting thousands of people. In a recent incident in May 2021, the Colonial Pipeline, a major fuel pipeline operator in the United States, fell victim to a ransomware attack. The attackers infiltrated Colonial Pipeline’s network through the DarkSide ransomware. They encrypted the company’s systems and demanded a ransom payment in exchange for the decryption keys. As a result, Colonial Pipeline shut down its operations, leading to disruptions in fuel supply and causing a significant economic impact.
Despite significant advancements in addressing cybersecurity challenges within the information technology (IT) domain, the operational technology (OT) domain is still catching up in terms of progress. IT primarily focuses on the software component of systems, encompassing network infrastructure and data management. In contrast, OT ensures the smooth operation of critical infrastructure, including power grids, smart meters, and distribution systems. Notably, cyberattacks targeting OT systems tend to have more severe and far-reaching consequences compared to those in IT. These attacks can lead to outcomes such as shutdowns, outages, leakages, and even explosions. Consequently, standards development organizations like the National Institute of Standards and Technology (NIST) [
2] have devised essential cybersecurity research roadmaps. These roadmaps serve as frameworks designed to identify and mitigate the impact of cyberattacks, thereby exerting a notable influence on the security protocols adopted across various industries.
While significant research efforts continue to focus on diverse domains, such as the creation of machine learning-based cyberattack detectors [
3,
4,
5,
6], the design of backup controllers in a two-tier safety-performance control architecture [
7], the recovery of process states following a cyberattack [
8], and the development of cyberattack-resilient controllers [
9,
10], one critical and fundamental research issue remains unresolved: the establishment of universally implementable secure data transmission lines in any cyber–physical networked system, without requiring controller modifications, the installation of backup control systems, the development of system-specific detection mechanisms, or tailor-made solutions for individual platforms. A promising solution to address this issue is utilizing an encrypted control system. This approach offers a versatile and effective solution for enhancing data security and confidentiality. It can be easily implemented across various systems without necessitating system-specific modifications, thereby addressing the fundamental challenge of secure data transmission in networked systems.
Regarding encrypted control, extensive research has been conducted in the field of linear control systems, with control computations performed in a fully encrypted space. The fundamental concept behind such systems is multiplicative homomorphism, which enables multiplication operations to be executed in an encrypted medium using complex cryptosystems, like ElGamal [
11]. However, such operations in an encrypted space can be computationally demanding and not applicable to systems governed by complicated nonlinear dynamics where nonlinear controllers may be needed, limiting their widespread adoption. Alternatively, a more viable approach could involve using encryption to secure data transmission lines. The data collected by the sensors can be encrypted, subsequently transferred, and decrypted at the controller, which can be isolated and fortified against potential security breaches. Therefore, within the context of this research, we consider that the edge computer, responsible for executing controller computations within a SCADA architecture, operates within a completely secure cyber–physical setting due to encryption of the sensor-to-controller and controller-to-actuator signals. Specifically, in our formulation, the controller can compute the control action in plaintext, eliminating the need for convoluted calculations in an encrypted space. Subsequently, the control action can undergo encryption before transmission to the actuator, where the encrypted control action is decrypted and executed. This method avoids computationally demanding operations in an encrypted space and is effectively implementable in systems employing advanced process control schemes for nonlinear systems, such as Model Predictive Control (MPC).
Since its inception, the chemical industry has extensively adopted Model Predictive Control (MPC) due to its effectiveness in achieving closed-loop stability and optimizing key performance metrics and its capability to handle multiple inputs and outputs and accommodate constraints on system states and inputs. These benefits arise from employing a mathematical model of the system to predict future behavior and optimize control inputs accordingly. However, implementing MPC necessitates decryption at the controller to obtain the essential information required for prediction and optimization. In an industrial setting, an edge computer, accessible remotely by the sensors and actuators through the network, can perform nonlinear MPC computations. The objective is to utilize encryption techniques to establish secure connections between the sensors–edge computer and edge computer–actuators. The referenced work [
12] provides a comprehensive exploration of the design of an encrypted Model Predictive Control framework, as well as the influence of quantization on system performance. Building upon that foundation, in this work, we go a step further by implementing the encrypted Lyapunov-based Model Predictive Control (LMPC) scheme in a large-scale chemical process network used for Ethylbenzene production, using an Aspen Plus Dynamics-based process model in conjunction with a first-principles-based LMPC to showcase that the influence of quantization can surpass the impact of plant/model mismatch. Moreover, this study conducts a comprehensive and innovative investigation to assess how encryption–decryption affects the computation time required for computing the control action. By thoroughly examining the impact of the quantization parameter selected for encryption on the computation time, this research aims to provide new perspectives and deeper insights into the practical implications of data encryption. To our knowledge, prior investigations have not explored the implications of an encrypted MPC scheme in the aforementioned domains.
To apply the encrypted LMPC, we develop two distinct nonlinear dynamical models: one utilizing Aspen Plus Dynamics V12 and the other based on first-principles modeling fundamentals. In
Section 4, we conduct closed-loop simulations for the Aspen Plus Dynamics model, employing the first-principles model-based encrypted LMPC for various quantization parameters. Further, we investigate the impact of these parameters on controller performance and put forth a proposal to mitigate quantization errors and their effects on controller performance. Additionally, in
Section 5, we explore the influence of encryption–decryption on the total control input calculation time. Expanding on the previous recommendation, we provide clear guidance on implementing the encrypted LMPC approach. This implementation ensures a feasible computation time for control action computation (with encryption) while establishing secure communication pathways between the sensor–controller and controller–actuator components, without compromising the performance of the controller.
3. Design of the Encrypted MPC
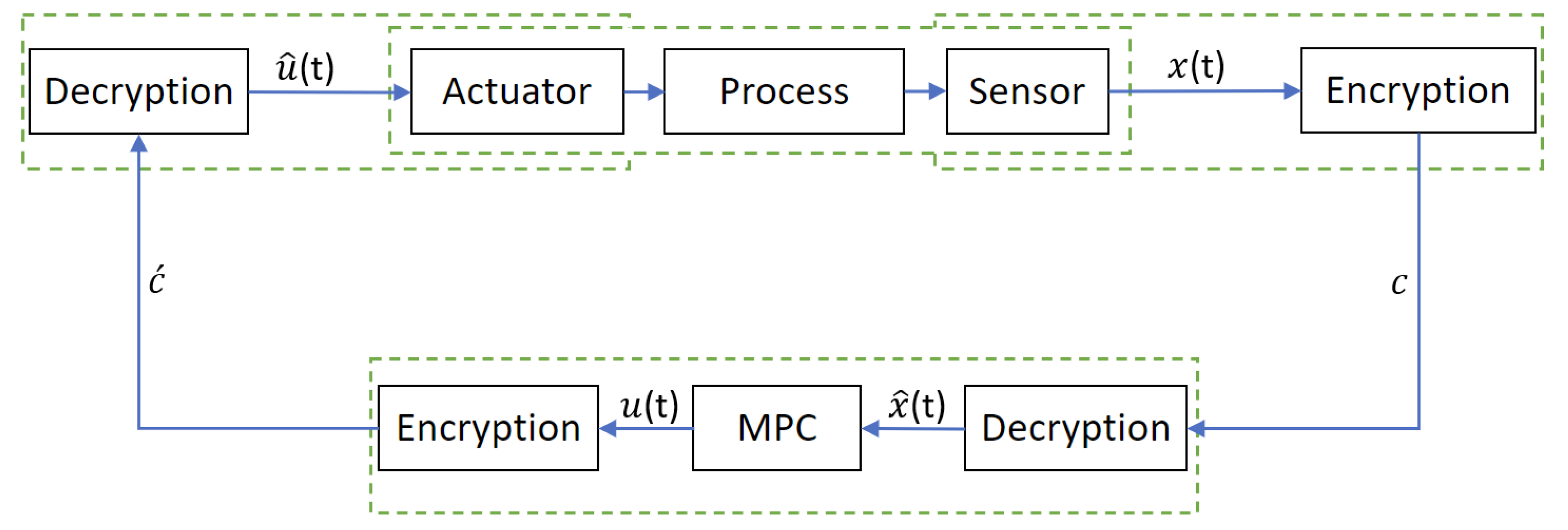
In the envisioned closed-loop architecture of the encrypted MPC, as depicted in
Figure 2, the sensor signals
are subjected to encryption before being sent to the model predictive controller (MPC). After obtaining the encrypted data, it undergoes decryption, resulting in quantized states
. These quantized states serve as the initial values for the plant model within the MPC at time
t. The MPC subsequently computes optimized inputs
, which are encrypted prior to transmission to the actuator. After the actuator receives the encrypted signals as input, the encrypted input is decrypted, leading to a quantized input
that is applied to the process.
The above closed-loop design introduces two sources of errors. Firstly, a quantization error in the sensor-MPC communication link, resulting from the mapping of the state data from
to
. Additionally, the MPC-actuator communication link introduces an input quantization error caused by the conversion of input data from the set of real numbers
to
. These quantization errors are bounded and can be characterized by the mapping equation of Equation (
5), ensuring that
where
d is the quantization parameter used for mapping in Equation (
5). Firstly, taking into account the impact of quantization-induced input errors, the dynamical model of the MPC employs a nonlinear system, represented by Equation (
1), which can be expressed as follows:
where
and
Secondly, an error in the control input,
, will emanate as the MPC receives
instead of the actual state
x. This error will be bounded by the underlying equation, where
:
Reference [
12] discusses and establishes the stability of the proposed control loop with encrypted data transfer, providing assurance for the closed-loop system stability even in the presence of encryption, under certain conditions.
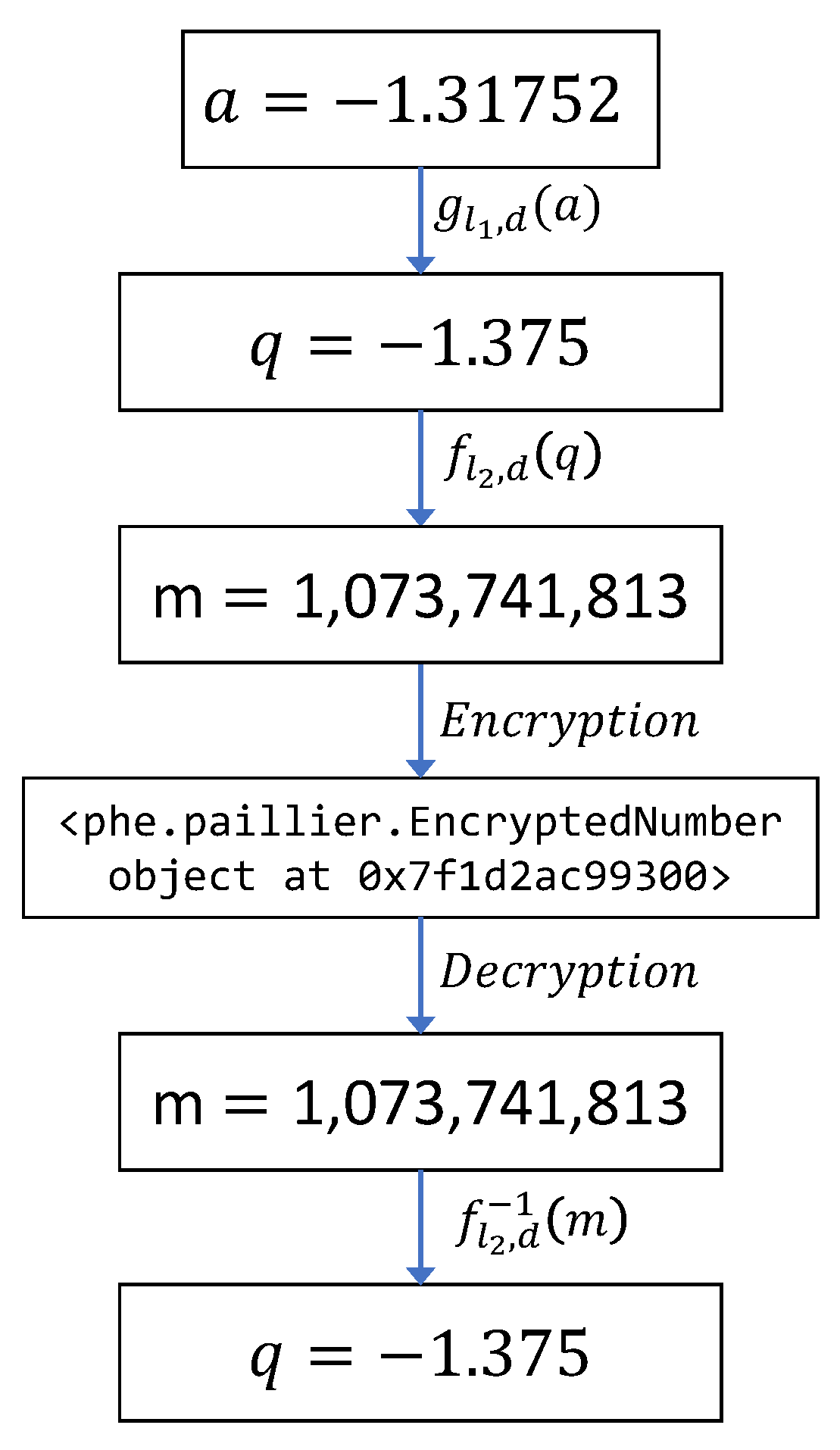
Remark 1. The error in the quantization operation occurs when the target value to be quantized is not found exactly in the set , which consists of quantized values with a certain resolution determined by the quantization parameter, denoted as d. The resolution between elements in this set is given by . To determine the upper bound of the error, let us focus on a specific value, denoted as , that needs to be quantized. We assume that falls within the range of and , where and represent quantized values in the set . The quantization process involves comparing the distance between and with the distance between and . If the distance between and is smaller than the distance between and , then is mapped to . Otherwise, it is mapped to . The error in quantization is then bounded by half the resolution, which is equal to . This implies that the maximum difference between the quantized value , and the actual value , is .
Encrypted Lyapunov-Based MPC
This section presents a formulation of the feedback MPC for the closed-loop design of the nonlinear system described by Equation (
1), considering secure sensor–controller and controller–actuator communication links. Control actions will be applied to the nonlinear system using a sample-and-hold approach with a sampling period of
[
18,
19]. The proposed MPC formulation is outlined as follows:
Within the framework of the Lyapunov-based MPC, referred to as LMPC, the predicted state trajectory is represented as , the sampling time is denoted by , and the prediction horizon encompasses a number of sampling periods indicated by N. The LMPC algorithm computes the optimal input sequence for the entire prediction horizon . The first input of this sequence is subsequently transmitted to the actuator for application to the system within the interval .
In the encrypted LMPC design, the MPC uses quantized states
for predicting the state trajectory, Equation (
13a) integrates the cost function over the entire prediction horizon, and it computes the optimized control inputs for the entire prediction horizon. However, the actuator only applies the control inputs corresponding to the first prediction horizon and repeats this process at each sampling instance. Equation (
13b) represents the dynamic system model used by the LMPC. Equation (
13c) represents the constraints imposed on the control inputs. The constraint in Equation (
13d) initializes the plant model described in Equation (
13b) with quantized states. If the state
at time
lies within the set
, where
represents a level set of
V in proximity to the origin, the Lyapunov constraint outlined in Equation (
13e) steers the closed-loop state
of the nonlinear system presented in Equation (
10) toward the origin. Once the closed-loop state
enters the region
, the constraint specified in Equation (
13f) ensures that this state remains within
throughout the entire prediction horizon.
4. Application to a Chemical Process Operating at an Unstable Steady State Using Aspen Plus Simulator
In this section, we demonstrate the application of the proposed encrypted LMPC to a large-scale chemical process. To begin, we construct two dynamic models for a chemical process. We develop the first dynamic model using Aspen Plus Dynamics V12, while the second model is based on first-principles modeling fundamentals. Aspen Plus Dynamics is a high-fidelity software that can be used for the detailed dynamic simulation of chemical processes in an operating region around a stable or unstable steady state, which is not possible in steady-state simulation software for chemical processes, and hence, can be considered as the closest representation of the actual process dynamic behavior. Furthermore, first-principles-based MPC computations can be performed on a computer in SCADA systems using Python. As a first-principles model can be derived for most processes even in the absence of data and can be simulated readily with available solvers, the Aspen Plus Dynamics model and first-principles-based Python code can be considered as a “standard metric” to quantify and analyze specific aspects of MPC. In this work, we use a distinct model to simulate the chemical process from the model incorporated into the LMPC to demonstrate the impact of quantization and compare it with the plant/model mismatch. We design both models without any input or state delays. Subsequently, closed-loop simulations are performed in the Aspen Plus Dynamics model using the first-principles model-based LMPC. Finally, we replace the LMPC with an encrypted LMPC, and closed-loop simulations are conducted and discussed.
4.1. Process Description
The process considered is the production of Ethylbenzene (EB) from Ethylene (E) and Benzene (B) as reactive raw materials. The main reaction, labeled as “primary”, is a second-order, exothermic, and irreversible reaction that occurs alongside two additional side reactions. This reaction scheme is illustrated in Equation (14) and takes place in two non-isothermal, well-mixed continuous stirred tank reactors (CSTR). The chemical reactions involved are as follows:
The state variables are the concentrations of Ethylene, Benzene, Ethylbenzene and Di-Ethylbenzene and the reactor temperature, for each , respectively, which in deviation terms is:
The subscript “s” denotes the steady-state value. The rate of heat removal for each reactor is the manipulated inputs to our process, which are bounded by the closed sets and , respectively.
The control objective is to maintain the operation of both the CSTRs at their unstable steady state under the encrypted LMPC using the quantized states and inputs in computation and actuation. Because the rate of heat removal for each CSTR is the manipulated input, the reactor temperature state variables are directly affected by it. However, the manipulated inputs do not directly influence the concentration states. Instead, they follow open-loop trajectories, gradually converging to their respective steady-state values as the reactor temperatures approach their steady-state values.
To identify the stability condition of the operating steady state, we conducted an open-loop simulation in Aspen Plus Dynamics. We initiated the simulation using the steady-state values as initial conditions, and the control inputs were held constant at their respective steady-state values (0 in deviation form) throughout the simulation. After running the simulation for 10 h of process time, the system states converged to a distinct stable steady state, providing clear evidence that the selected operating condition is an unstable steady state. The main reason behind choosing this unstable steady state as the operating condition was its ability to yield the highest amount of Ethylbenzene, our desired product, at steady state, at the outlet of the second CSTR.
4.2. Dynamic Model in Aspen Plus Dynamics
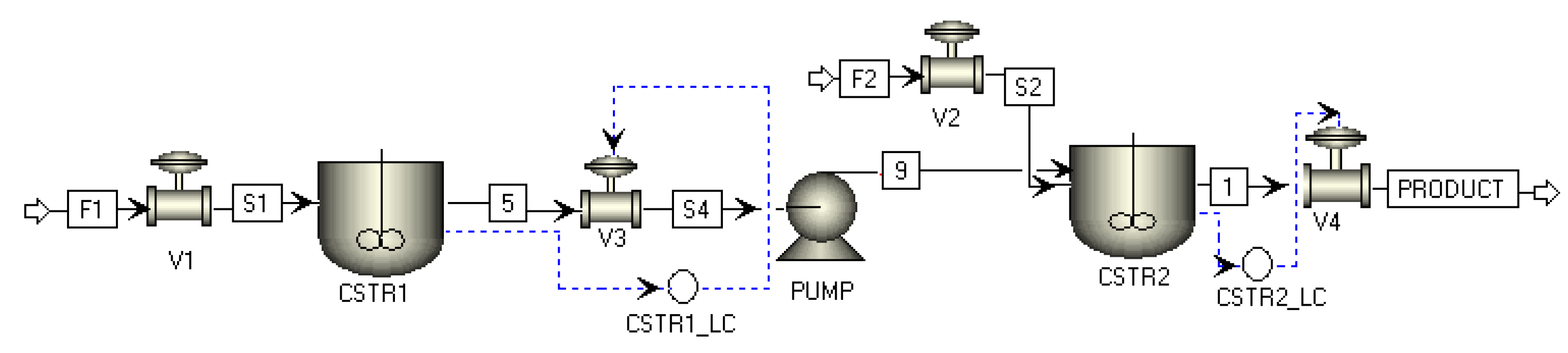
We develop the process model for this system using Aspen Plus and Aspen Plus Dynamics V12. These are high-fidelity simulators used for complex chemical process modeling. The two CSTRs are connected in series, such that the output of the first reactor affects the second reactor but not vice versa. Initially, the process model is created in Aspen Plus, and a steady-state simulation is performed and validated by examining material and energy balances. Subsequently, dynamic simulations of the process are conducted in Aspen Plus Dynamics, enabling a thorough analysis and control of its dynamic behavior. The construction of both the steady-state and dynamic models follows the following procedure in detail:
Inlet stream configuration: We enter the inlet stream components, concentrations, and temperatures into Aspen Plus and supply it to each reactor through Hexane solutions with flow rates
and
. Using Hexane ensures the inlet flows remain in the liquid phase at the feeding temperature.
, and
represent the concentrations of Ethylene, Benzene, Ethylbenzene, and Di-Ethylbenzene in the inlet stream, respectively.
are the temperature, liquid density, and volume of
,
.
represents the mass-specific heat capacity of the liquid mixture and is assumed to remain constant throughout the process in both reactors.
Table 1 specifies the process parameters used. The subscript “o” denotes the state in the inlet stream, and “s” indicates the steady-state conditions.
Pressure drop selection: Valves play a crucial role in establishing a dynamic model for Aspen Plus Dynamics, as they serve as connectors between components and regulate fluid flow by controlling the pressure drop across the system. A suitable pressure drop specifies the flow direction, ensuring a smooth simulation run. In our model, valves , and are assigned pressure drops of 5, 5, 2, and 14 bars, respectively.
Reaction and reactor specification: We define the reaction parameters and stoichiometry in Aspen Plus. All reactions mentioned in Equation (14) are selected in the kinetic specifications of both the CSTRs. We set the initial pressure of each CSTR to 15 bar and equip them with a heating/cooling jacket to provide or remove heat at a rate denoted by , where i represents the reactor number. The initial temperatures of the first and second CSTRs are 350 K and 400 K, respectively. These settings ensure that the reactants and products remain in the liquid phase throughout the process. After completing the reaction specification for both reactors, we carry out a steady-state simulation.
Reactor geometry: Before exporting the steady-state model from Aspen Plus to Aspen Plus Dynamics, it is necessary to define the reactor geometry. In our model, the vessels are of the vertical type with flat heads, and each CSTR has a length of ten meters.
Pressure verification: To ensure the accuracy of the dynamic model, perform a pressure check using the integrated Aspen Plus pressure checker. This step verifies that no errors arise during the dynamic process. Once the steady-state model successfully passes the pressure check, we export it to Aspen Plus Dynamics for further analysis and simulation.
Dynamic model initialization: Level controllers are added to each reactor to maintain them at the desired capacity. We perform a steady-state simulation to determine the steady-state values of the dynamic model. The values obtained are listed in Equation (14). Further, we specify the initial values of the states in both reactors for the dynamic simulation. Through an initialization run, we ensure the values entered are thermo-kinetically consistent with the model specifications.
Manipulated input configuration: For external control of the manipulated variables
and
(heat duty of reactor 1 and 2, respectively) during the dynamic simulation, the heating type of the reactors is switched to constant heat duty. With these adjustments, the dynamical process model is now fully established.
Figure 3 depicts the corresponding model flow sheet.
4.3. First-Principles Model Development
By applying the concepts of mass and energy balances, the first-principles model for the CSTRs is developed. Specifically, the dynamic model of the first CSTR is represented by the following ODEs:
where
. The dynamic model of the second CSTR is represented by the following ODEs:
where
, and the reaction rates are calculated by the following expressions:
Remark 2. When constructing a dynamic model based on first-principles fundamentals involving multiple ordinary differential equations (ODEs), there may be multiple potential steady states. It is crucial to design the dynamic model in a manner that ensures convergence to the desired steady state. It should be noted that the steady states obtained from the first-principles model may differ from those obtained using the Aspen model. Therefore, our approach involves expressing the first-principles dynamic model equations in the form . Here, and correspond to the steady-state values of the state variables and control inputs, respectively. These values are determined by the Aspen model through simulation. Writing the equations in this form guarantees that the first-principles model will converge to the desired steady states obtained from the Aspen model, particularly when dealing with multiple distinct steady states.
4.4. Linking the Dynamic Models
To establish a seamless data transfer between the Aspen model (Aspen Plus Dynamics V12) and the first-principles model-based LMPC (Python code), we program a script in Aspen Plus Dynamics. This script reads the calculated control inputs, exported as text files by the Python code responsible for computing the control inputs. Additionally, it facilitates the export of the state variable values from Aspen Plus Dynamics as text files read by the Python code. This data exchange occurs at each sampling time, establishing a robust data transfer link between the Aspen model and the first-principles-based LMPC.
Remark 3. As discussed in Section 4.1, the MPC model (first-principles based) used for predicting future states and optimizing control inputs differs from the Aspen dynamic model, where we apply the controller. To address this model mismatch, we analyze the combined and relative effects of the quantization errors, which arise from encryption–decryption and can further amplify the model mismatch error. Our analysis reveals that the quantization error is bounded by half the resolution (resolution/2). For instance, when the quantization parameter chosen is , the resolution is 0.5, and the upper bound of the error between the actual and quantized values is resolution/2 or 0.25. Hence, for higher quantization parameters, the impact of the quantization error on the overall model mismatch error is negligible. It is important to note that quantization introduces a bounded error in the states, thereby limiting the extent of the model mismatch error. 4.5. Implementing the Encrypted LMPC
Before implementing encryption–decryption in a process, it is crucial to carefully choose the values: , , and . After closely examining the maximum and minimum permissible values of the states and inputs, we determine the number of integer bits, . The largest value in the set is obtained using the formula , while the smallest value is . The quantization parameter should be selected based on factors, such as the desired accuracy and the range of the state and input values. Additionally, a value for should be selected such that is greater than . These steps complete the hyperparameter selection process.
After following the aforementioned steps, we determine that, for the example discussed in this section,
is calculated to be 15. The values of
and
d need to be selected accordingly. In the set
, rational numbers are separated by a resolution of
, meaning that a higher value of
d leads to lower quantization errors. For simulation purposes, we vary the values of
d from 1 to 8, resulting in
ranging from 16 to 23. It is important to ensure that
for the bijective mapping, so we choose
. After determining all the quantization-related parameters, we proceed to quantize the states and inputs. Subsequently, we encrypt them using the Paillier Encryption algorithm. The implementation of Paillier Encryption is carried out using the “phe” module in Python, specifically PythonPaillier [
20]. The first-principles model, described by Equations (15) and (16), serves as the process model in the LMPC framework. To solve the optimization problem, we utilize the Python module of the IPOPT software, version: ASL (20190605) [
21].
Remark 4. IPOPT, Interior Point OPTimizer, is a software tool designed specifically for solving nonlinear optimization problems. It employs an iterative method known as the interior point method, which focuses on finding the optimal solution by gradually moving toward the interior of the feasible region. To solve the optimization problem, IPOPT employs a series of iterations. In each iteration, it updates a sequence of points that satisfy the given constraints and improve the value of the objective function. This process involves calculating descent directions based on the gradient and Hessian of both the objective function and the constraints. IPOPT considers both the feasibility and optimality of the solution, striving to find a point that not only satisfies the constraints but also optimizes the objective function. Throughout the iterations, IPOPT utilizes a barrier function to handle inequality constraints and a penalty function to handle equality constraints. It also incorporates a line search procedure to determine the appropriate step length and employs backtracking techniques to ensure convergence toward the optimal solution. In our study, the nature of the MPC formulation leads to a non-convex optimization problem. This signifies that the optimum achieved through the IPOPT optimizer is a local optimum, rather than a global one. The optimization process begins with a designated starting input trajectory based on predicted values for the extended horizon (beyond the first input trajectory calculation) from the prior iteration. Furthermore, the optimizer is guided by a prescribed tolerance error and an upper limit on the number of iterations. The optimizer will persist in its pursuit of an improved solution until either of these conditions is met. If the optimizer is unable to calculate an optimal solution, the computed solution from the backup controller (P-controller) will be substituted for that specific sampling instance.
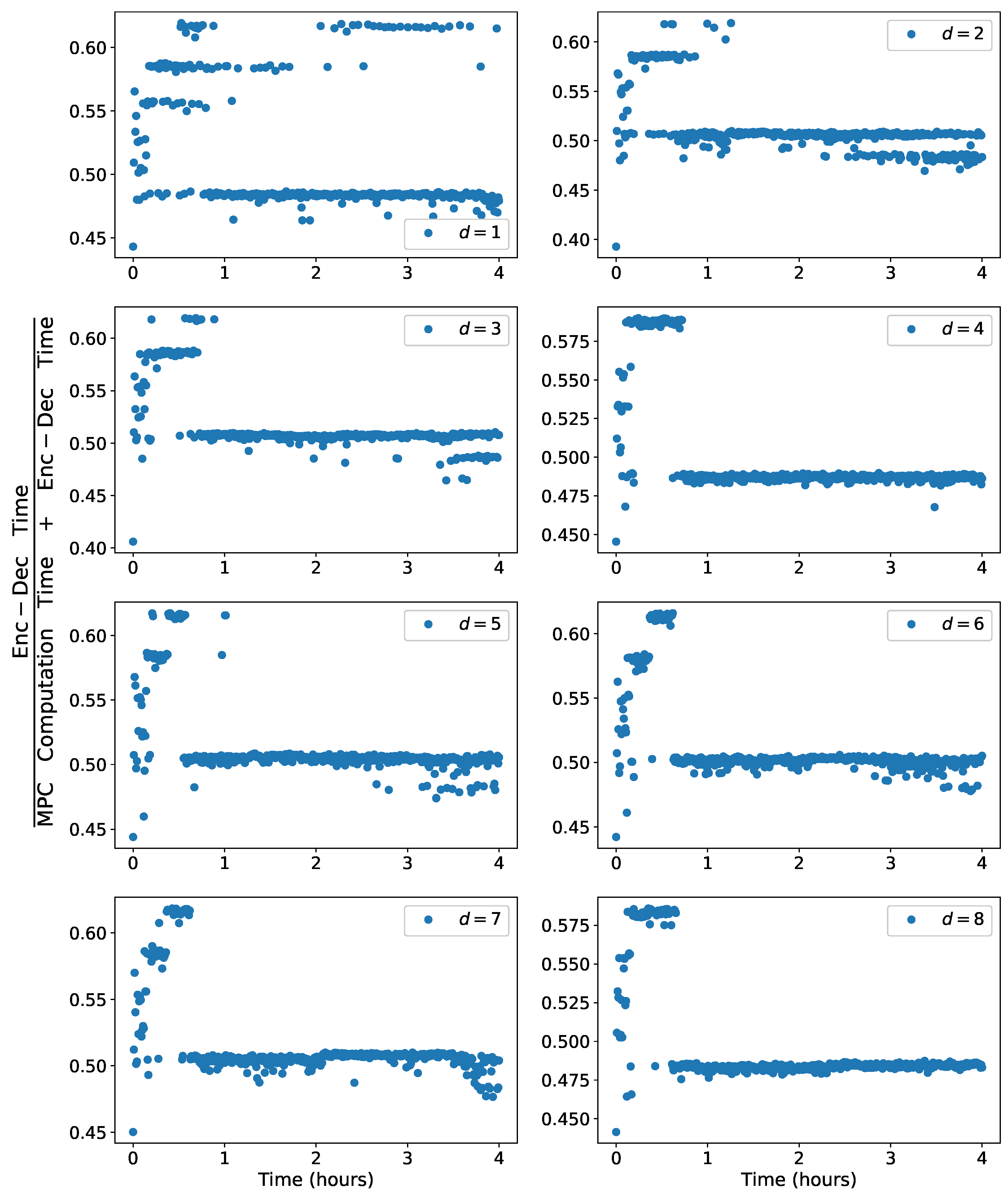
To implement encryption in a practical setting, it is crucial to ensure that the sampling time
exceeds the combined maximum of the encryption–decryption time required for all the states and control inputs, as well as the maximum time needed for computing the control action at each sampling instance for all the considered quantization parameters, denoted as
d. This requirement can be expressed by the following equation:
During the implementation of the encrypted MPC design in the SCADA systems, where encrypted sensor measurements and control actions are transmitted through the network, the time spent on signal transmission is generally not substantial due to the rapid and efficient nature of networked communication. However, this efficiency comes at the risk of susceptibility to cyberattacks. To mitigate this potential vulnerability, this study encrypts these communication channels and assesses the repercussions of encryption. Consequently, the formula provided above does not incorporate the factor of signal transmission time as well as issues with asynchronous, delayed measurements that have been studied in past works [
22,
23]. The sampling time
is carefully selected as 30 s, considering the aforementioned condition to ensure proper implementation. The integration step
is chosen as
to evaluate the cost function of the LMPC through the first-principles model. The positive definite matrix
P in the control Lyapunov function
for this system is taken as
based on extensive simulations. A prediction horizon of
is employed in the LMPC framework. To ensure stability in the LMPC, we set the criterion
to determine when the states have reached stability. Additionally, a contractive constraint of the form
is utilized for Equation (
13f), where the value of
k is chosen as
. The weight matrices
and
in the LMPC cost function are chosen as
and
, respectively. The cost function is defined as
.
4.6. Utilizing MPC over Traditional Control
In this section, we substantiate the utilization of Model Predictive Control (MPC) by conducting a comparative analysis between the MPC and the simpler p-control strategy. P-control allows control actions to be computed directly in encrypted states, eliminating the requirement for decryption at the controller through complex multiplicative homomorphic algorithms, such as the ElGamal cryptosystem. The MPC strategy is a more advanced control method that uses a mathematical model of the system to predict future behavior and optimize control actions accordingly. It requires decryption at the controller to obtain the necessary information for prediction and multi-constrained, nonlinear optimization, which cannot be performed in an encrypted space.
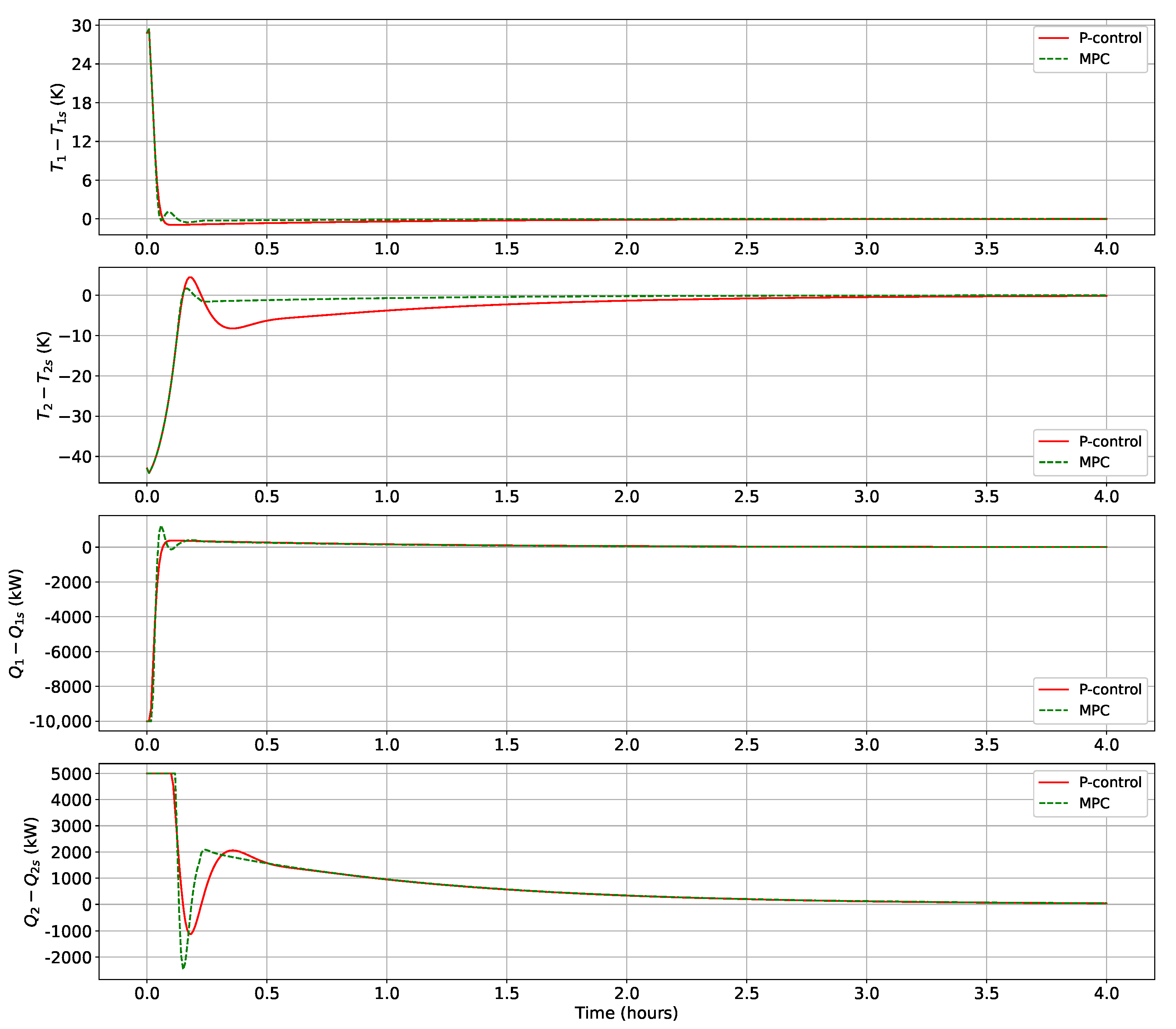
Figure 4 showcases its enhanced performance, with lower undershoot and faster settling time observed for the temperature of CSTR 1. Further, the temperature of CSTR 2 exhibits a significant reduction in overshoot by almost
and converges over 1 h before the p-control, within a settling limit of
. Moreover, the evaluation of the normalized sum of the controller cost function (
) over the closed-loop simulation reinforces the advantage of MPC over p-control, by the respective values of 0.86 and 1. These findings underscore the necessity of adopting MPC, as it offers reduced overshoot and undershoot, a faster settling time of state variables, and enhanced cost efficiency.
Remark 5. As mentioned earlier in Section 2.4, the Paillier cryptosystem is a partially homomorphic encryption scheme that does not support multiplication operations in an encrypted space. Therefore, in the above section, we mention using the ElGamal cryptosystem, which supports multiplicative homomorphism. Although the Paillier cryptosystem supports addition operations in an encrypted space, we do not utilize this property in our study. The Paillier cryptosystem is primarily selected for encryption due to its lower computational complexity compared to the ElGamal cryptosystem. This choice reduces the time and computational effort required for encryption–decryption processes. 4.7. Simulation Results of the Encrypted LMPC
We apply the encrypted LMPC to the Aspen dynamic model, initialized from the following point:
We then observe the closed-loop simulation results for
. A process time of 4 h allows both the states and control inputs to reach their respective steady-state values.
Figure 5,
Figure 6 and
Figure 7 display the temperature state and input profiles.
Remark 6. As indicated in Section 4.1, the concentration states in the reactors exhibit open-loop trajectories as the reactor temperature converges to its steady-state value. Consequently, the presence or absence of encryption does not significantly affect these states because the manipulated input, i.e., the heat removed from the reactors, has no direct influence on the concentration states. Therefore, in this section, we focus solely on displaying the temperature states and control inputs, as encryption noticeably influences them. For a quantization parameter of , it is evident that the state does not precisely converge to its steady-state value, instead exhibiting small oscillations around it throughout the 4 h process time. Also, the state demonstrates nearly double the overshoot with encryption and oscillates around the steady-state values, similar to the previous state. Further, quantized control inputs and experience significant oscillations under the encrypted MPC, rendering it incapable of effectively stabilizing the closed-loop system within a small neighborhood around the origin. Although, it does stabilize the system within the larger neighborhood . This behavior can be attributed to the quantization error resulting from the quantization of the state measurements. Thus, we establish that errors due to quantization can be more significant than plant/model mismatch errors as the MPC without encryption and with a higher quantization parameter, , is stabilized within the small neighborhood around the origin. As indicated in Remark 7, the quantization error associated with the quantized control input can be deemed negligible. However, the quantization error emanating from the quantized states is significant given the range in which they lie during the closed-loop simulation. For , the quantized states are separated by a resolution of or 0.5, leading to a high quantization error. When running simulations with the quantization parameter , we no longer observe oscillatory motions in the temperature states, and the magnitude of oscillations for the quantized inputs is much smaller compared to the case where . Furthermore, the amplitude of overshoot observed in the state variable remains nearly unchanged when encryption is applied, and the system also reaches the steady state more rapidly.
It is important to note that as the quantization parameter increases, resulting in a lower resolution, the states and inputs converge more quickly and exhibit reduced oscillations. Therefore, a higher quantization parameter improves the convergence behavior and decreases fluctuations in the state and control input profiles. Specifically, when , the closed-loop trajectories of the temperature states and control inputs become nearly identical between the cases with encryption and without encryption. In other words, the impact of encryption on the system’s behavior diminishes significantly as the quantization parameter increases, ultimately resulting in almost indistinguishable closed-loop trajectories for both scenarios.
Remark 7. The total quantization error can be attributed to the state quantization rather than the control input quantization, because the magnitudes of the quantized control inputs generally fall within the order of magnitude three. For the case , representing the lowest quantization, the maximum permissible error in the control input calculated by the MPC (before encryption) and applied by the actuator (after decryption) is 0.25, corresponding to half of the resolution. This error is considered negligible compared to the overall control input. As a result, the error arising from the quantization of control inputs is insignificant, particularly for the specific example considered. However, it is crucial to acknowledge that if the control inputs have smaller magnitudes, the error resulting from the quantized control inputs would significantly impact the controller’s performance.