Enhanced Cyber Attack Detection Process for Internet of Health Things (IoHT) Devices Using Deep Neural Network
Abstract
1. Introduction
- Detection of various types of attacks by applying deep learning approach rather than detection of specific type of attacks [19] in IoHT environment.
- The proposed method uses a new dataset ECU-IoHT in the domain of health care [20] to train and evaluate the model. The reason behind selection of the ECU-IoHT dataset is the fact that many datasets are publicly available, such as, for example, DARPA 98, KDD Cup 99, NSL-KDD, Morre, UNSW-NB15, BOT-IoT, ToN-IoT, ISCX, Kyoto and SCADA, which are inappropriate in the domain of health care.
- The proposed system achieves higher detection accuracy by analyzing an enormous amount of data (ECU-IoHT dataset consist of 111,207 numbers of samples).
2. The Literature Survey
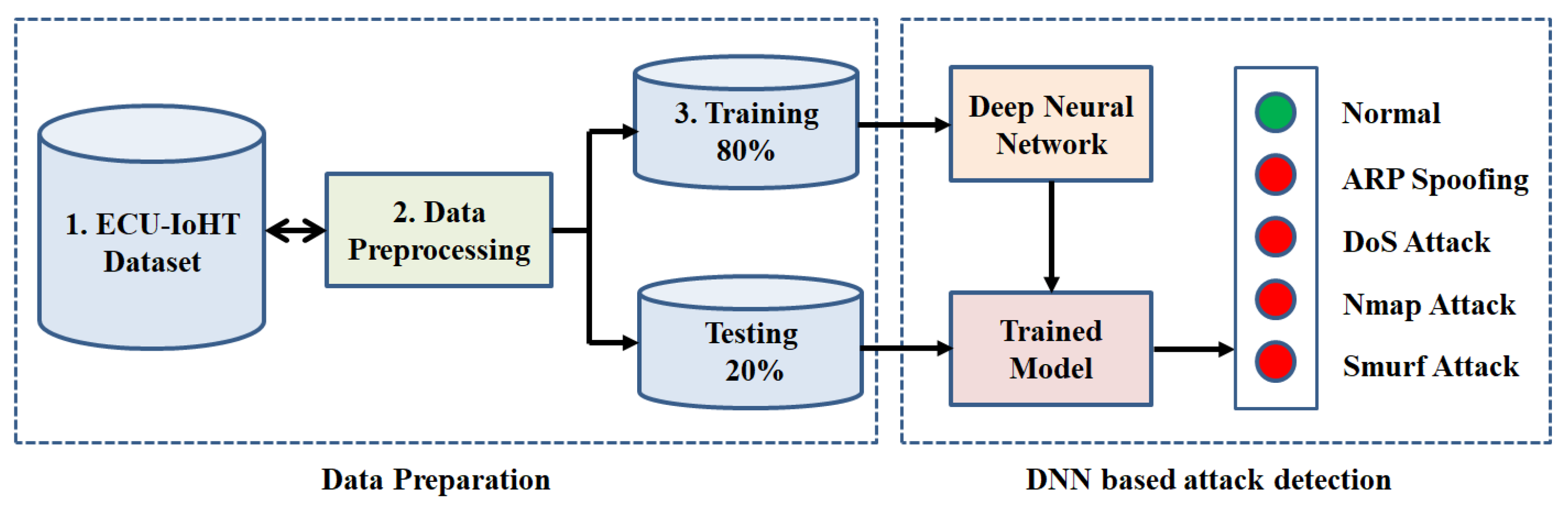
3. Proposed System
3.1. Anomaly Detection
3.2. Deep Nerual Network
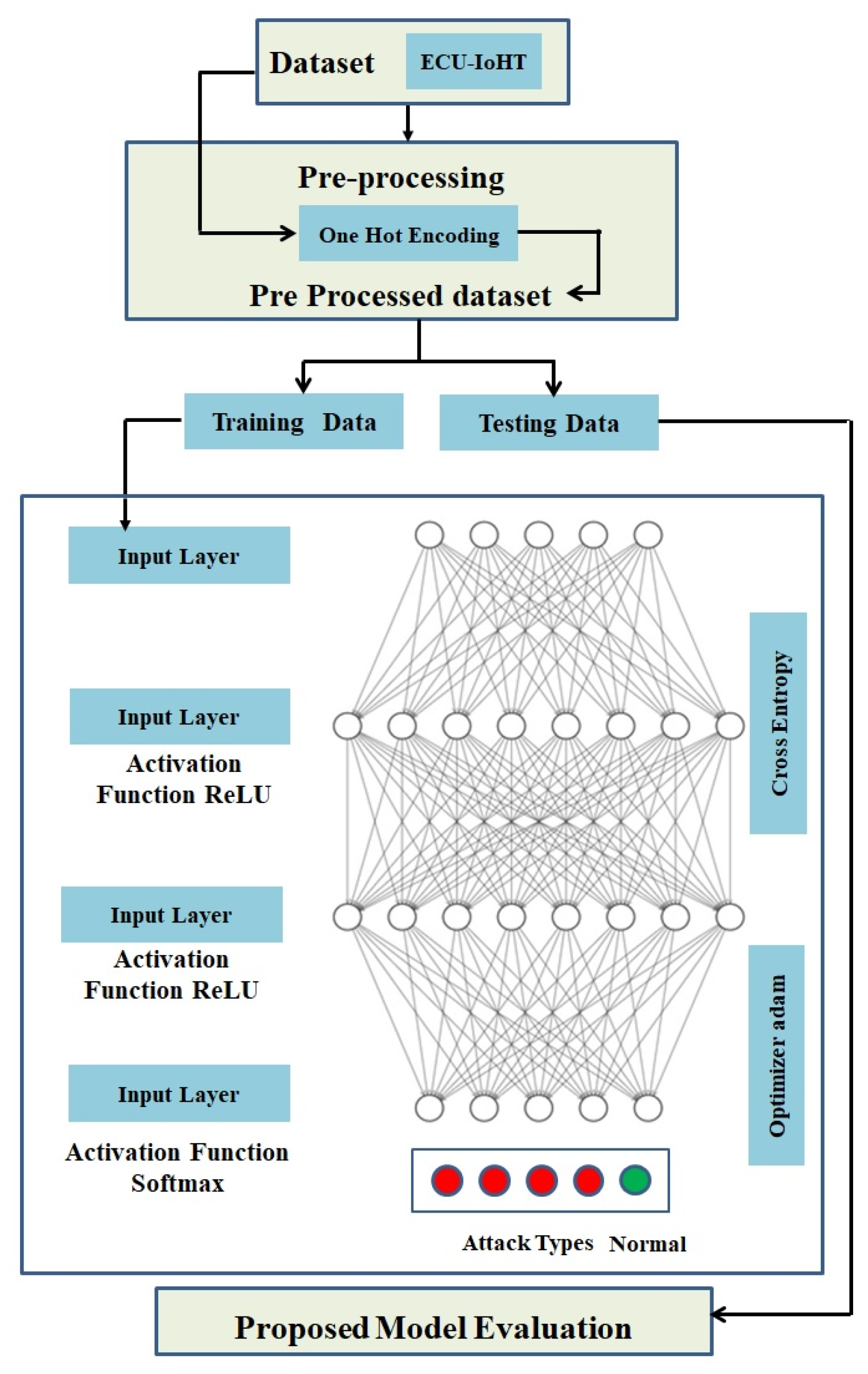
3.3. Methodology
3.3.1. Description of Dataset
3.3.2. Data Preprocessing
| Algorithm 1: One-hot encoding for encoding categorical data |
| Input: D(f1,f2,…, fn) |
| IOutput: Dencoded(f1encoded,…, fn encoded) |
| For i from 1 to N do |
| If (fi is a categorical input) |
| Encode using one hot encode method |
| End if |
| End for |
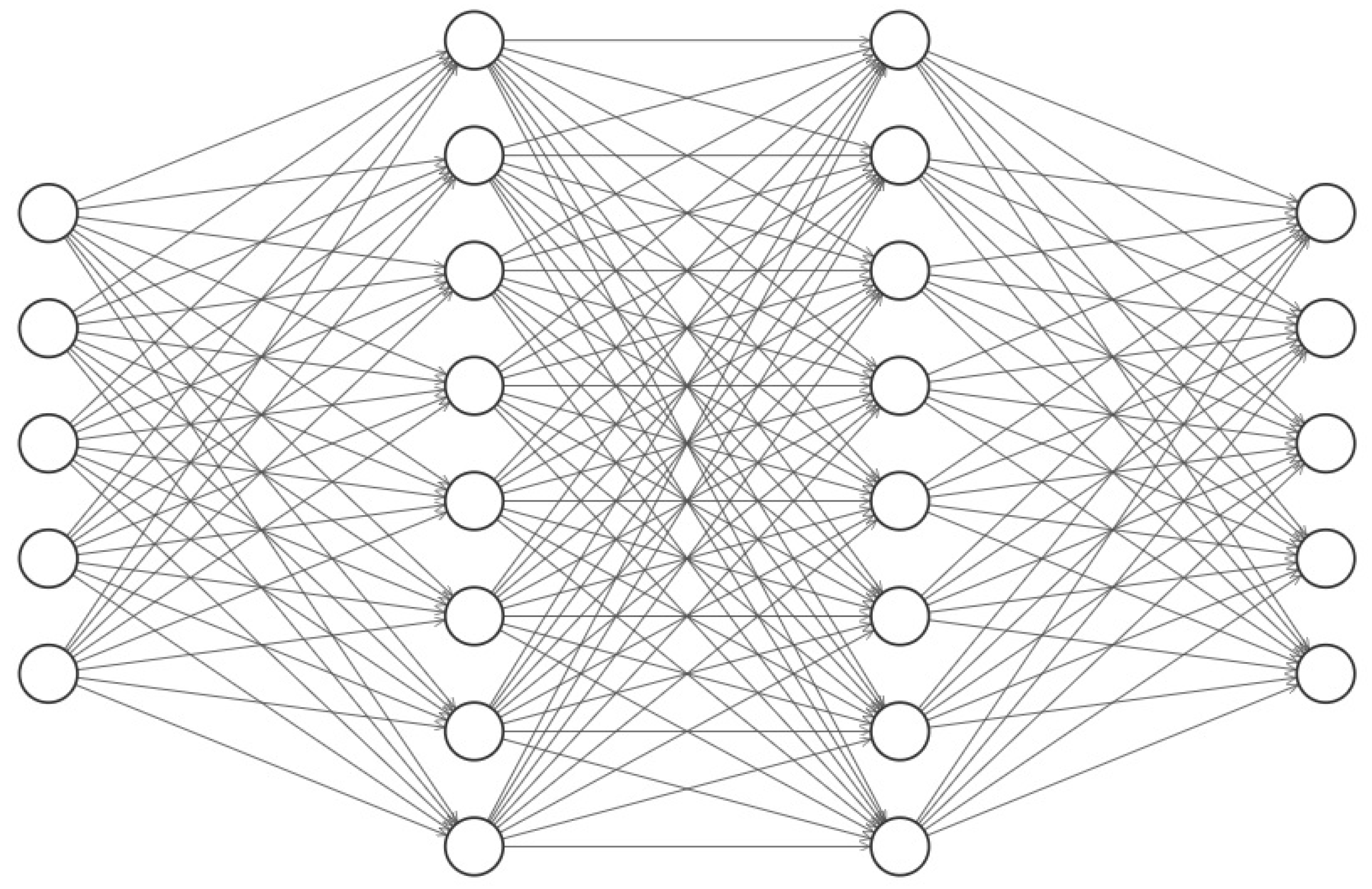
3.3.3. Proposed DNN Structure
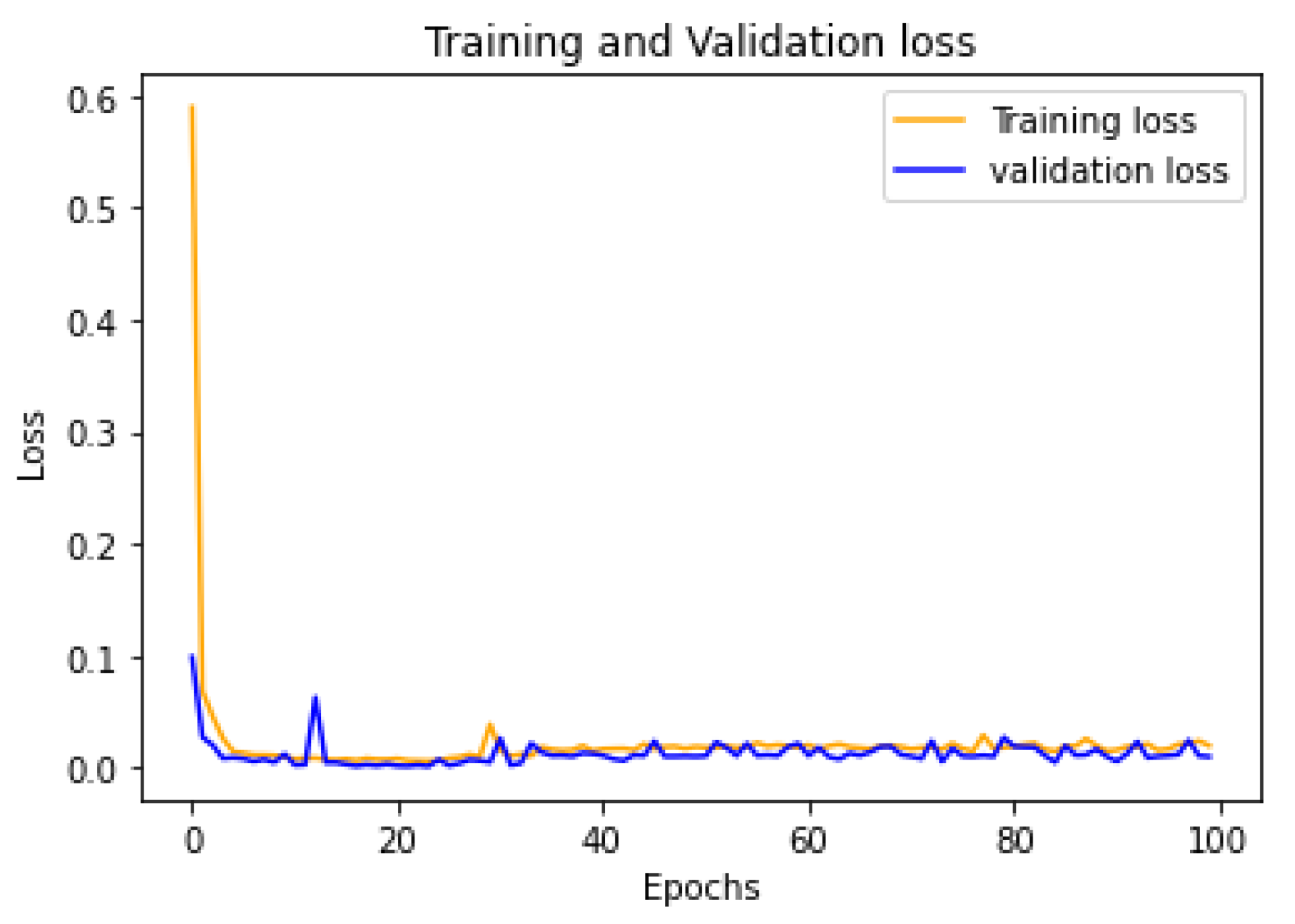
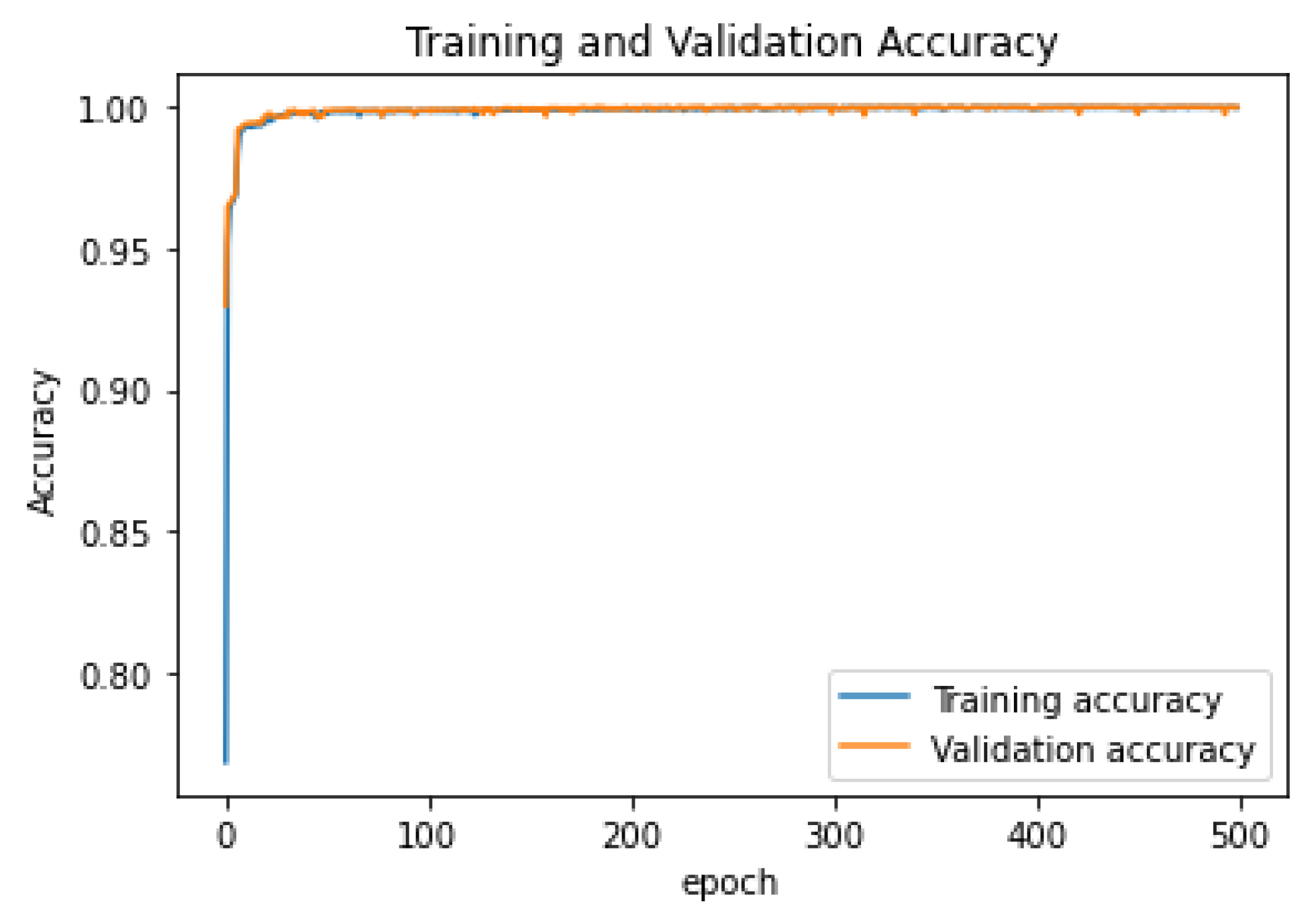
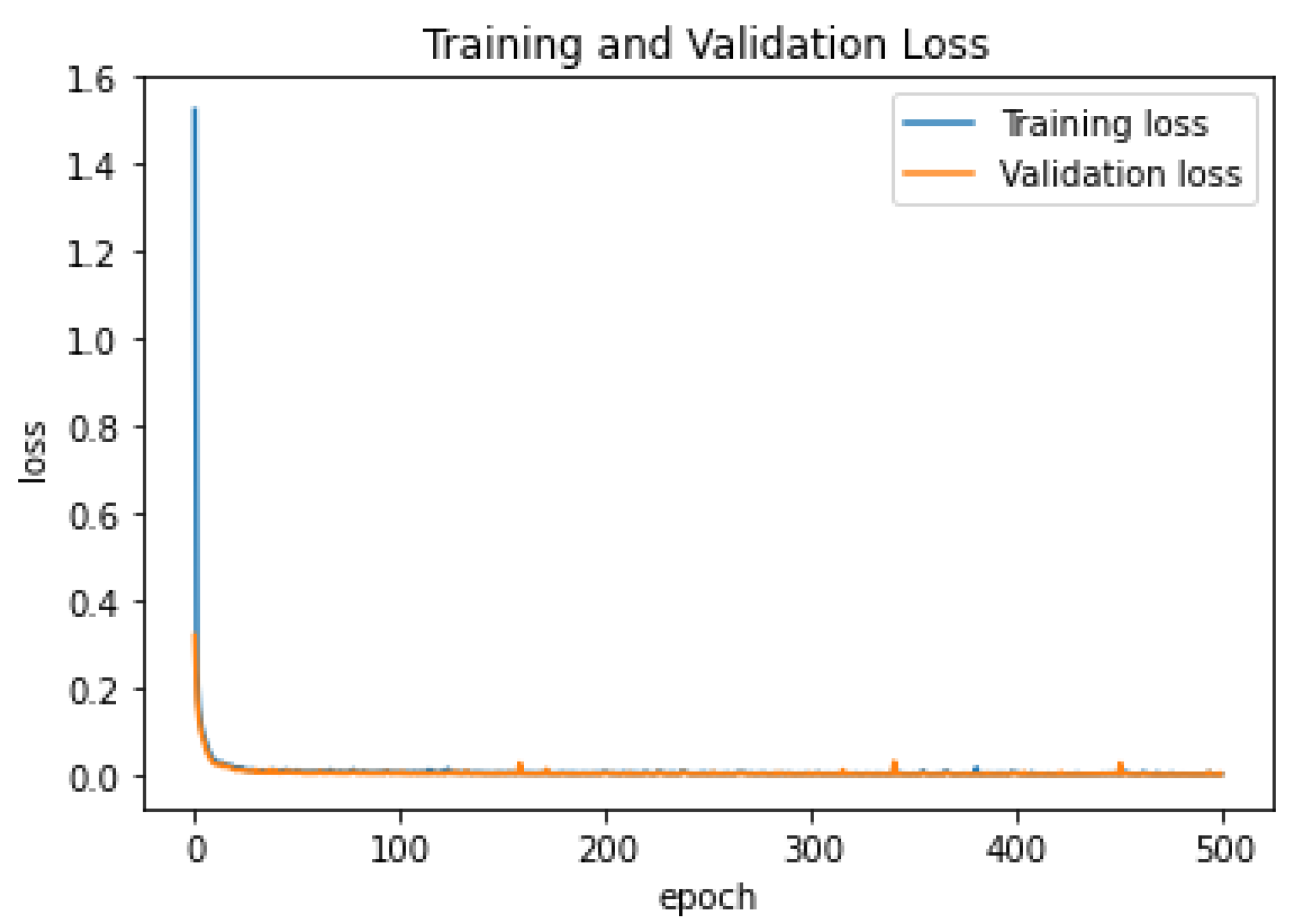
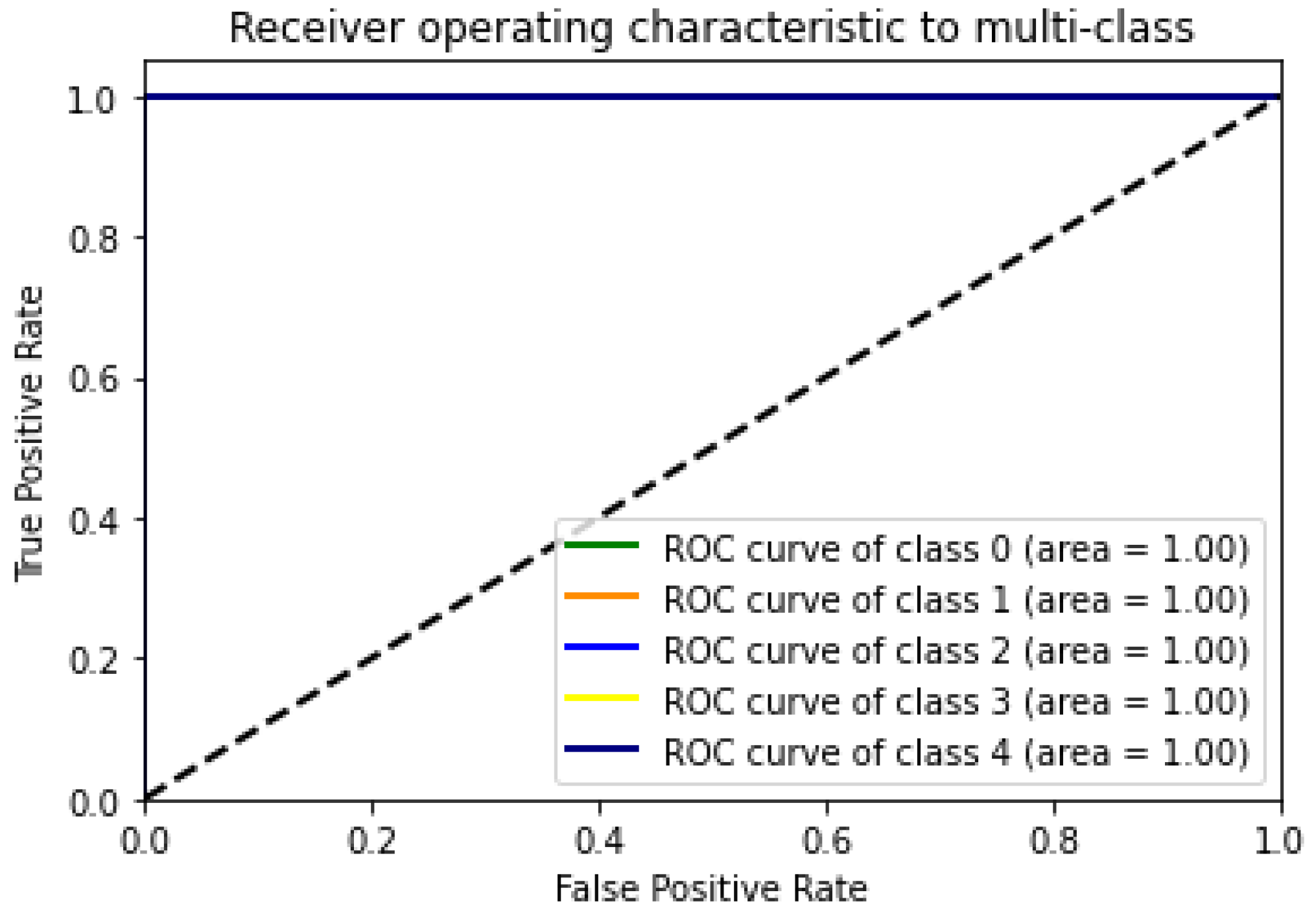
4. Results and Discussions
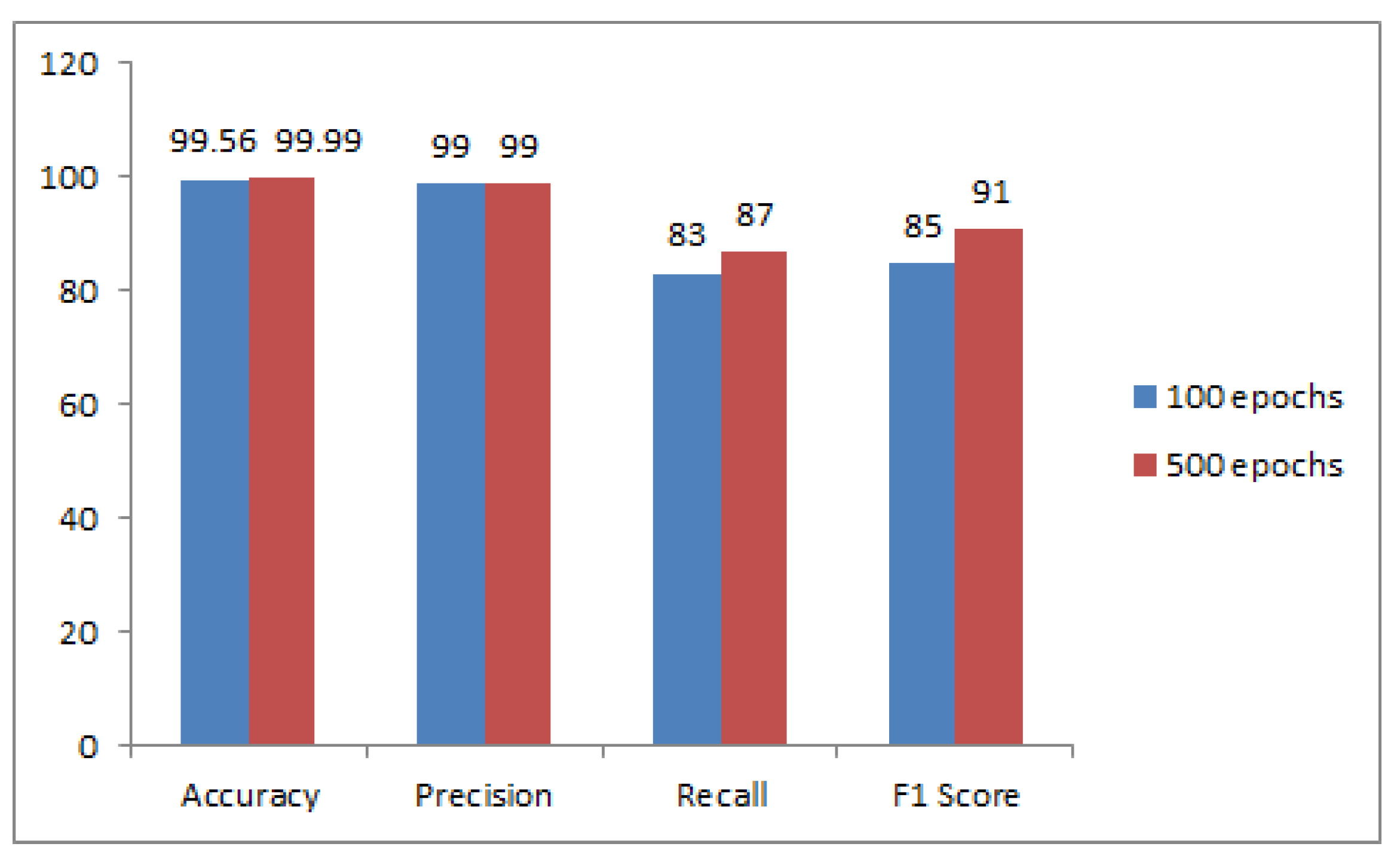
4.1. Evaluation Metrics
4.2. Environmental Setup
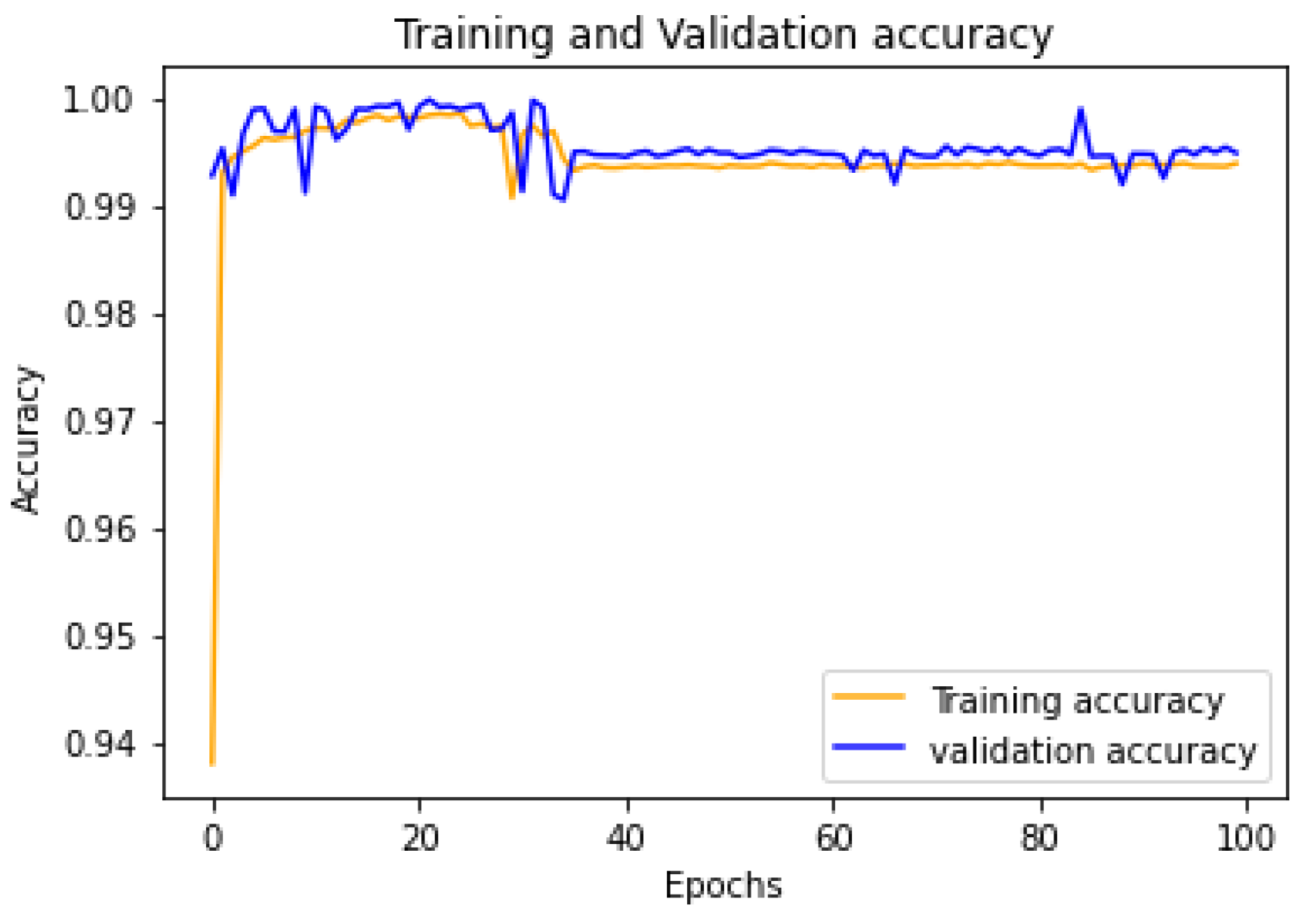
4.3. Discussion
5. Conclusions
Author Contributions
Funding
Data Availability Statement
Conflicts of Interest
References
- Ahmad, Z.; Shahid Khan, A.; Nisar, K.; Haider, I.; Hassan, R.; Haque, M.R.; Tarmizi, S.; Rodrigues, J.J.P.C. Anomaly detection using deep neural network for IoT architecture. Appl. Sci. 2021, 11, 7050. [Google Scholar] [CrossRef]
- Huang, Z. Analysis of IoT-based smart home applications. In Proceedings of the IEEE International Conference on Computer Science, Artificial Intelligence and Electronic Engineering (CSAIEE), SC, USA, 20–22 August 2021. [Google Scholar]
- Ma, L.; Li, Z.; Zheng, M. A research on IoT based smart home. In Proceedings of the 11th International Conference on Measuring Technology and Mechatronics Automation (ICMTMA), Qiqihar, China, 28–29 April 2019. [Google Scholar]
- Tabaa, M.; Monteiro, F.; Bensag, H.; Dandache, A. Green industrial internet of things from a smart industry perspectives. Energy Rep. 2020, 6, 430–446. [Google Scholar] [CrossRef]
- Brincat, A.A.; Pacifici, F.; Martinaglia, S.; Mazzola, F. The internet of things for intelligent transportation systems in real smart cities scenarios. In Proceedings of the IEEE 5th World Forum on Internet of Things (WF-IoT), Limerick, Ireland, 15–18 April 2019. [Google Scholar]
- Alluhaidan, A.S.; Alluhaidan, M.S.; Basheer, S. Internet of things based intelligent transportation of food products during COVID. Wirel. Pers. Commun. 2021, 127, 27. [Google Scholar] [CrossRef]
- Harb, H.; Mansour, A.; Nasser, A.; Cruz, E.M.; de la Torre Díez, I. A sensor-based data analytics for patient monitoring in connected healthcare applications. IEEE Sens. J. 2021, 21, 974–984. [Google Scholar] [CrossRef]
- Centenaro, M.; Costa, C.E.; Granelli, F.; Sacchi, C.; Vangelista, L. A survey on technologies, standards and open challenges in satellite IoT. IEEE Commun. Surv. Tutor. 2021, 23, 1693–1720. [Google Scholar] [CrossRef]
- Deb, S.; Islam, S.M.R.; RobaiatMou, J.; Islam, M.T. Design and implementation of low cost ECG monitoring system for the patient using smart device. In Proceedings of the International Conference on Electrical, Computer and Communication Engineering (ECCE), Cox’s Bazar, Bangladesh, 16–18 February 2017. [Google Scholar]
- Li, C.; Hu, X.; Zhang, L. The IoT-based heart disease monitoring system for pervasive healthcare service. Proc. Comput. Sci. 2017, 112, 2328–2334. [Google Scholar] [CrossRef]
- Vergara, P.M.; de la Cal, E.; Villar, J.R.; González, V.M.; Sedano, J. An IoT platform for epilepsy monitoring and supervising. J. Sens. 2017, 2017, 6043069. [Google Scholar] [CrossRef]
- Deshkar, S.; Thanseeh, R.A.; Menon, V.G. A review on IoT based m-health systems for diabetes. Int. J. Comput. Sci. Telecommun. 2017, 8, 13–18. [Google Scholar]
- Catarinucci, L.; de Donno, D.; Mainetti, L.; Palano, L.; Patrono, L.; Stefanizzi, M.L.; Tarricone, L. An IoT-aware architecture for smart healthcare systems. IEEE Internet Things 2015, 2, 515–526. [Google Scholar] [CrossRef]
- Yin, Y.; Zeng, Y.; Chen, X.; Fan, Y. The internet of things in healthcare: An overview. J. Ind. Inf. Integr. 2016, 1, 3–13. [Google Scholar] [CrossRef]
- Alsubaei, F.; Abuhussein, A.; Shiva, S. Security and privacy in the internet of medical things: Taxonomy and risk assessment. In Proceedings of the IEEE 42nd Conference on Local Computer Networks Workshops (LCN Workshops), Singapore, 9 October 2017. [Google Scholar]
- Nagarajan, S.M.; Deverajan, G.G.; Kumaran, U.; Thirunavukkarasan, M.; Alshehri, M.D.; Alkhalaf, S. Secure data transmission in internet of medical things using RES-256 algorithm. IEEE Trans. Ind. Inform. 2021, 18, 8876–8884. [Google Scholar] [CrossRef]
- Bosri, R.; Uzzal, A.R.; Al Omar, A.; Bhuiyan, M.Z.A.; Rahman, M.S. HIDEchain: A user-centric secure edge computing architecture for healthcare IoT devices. In Proceedings of the IEEE Conference on Computer Communications Workshops (INFOCOM WKSHPS), Toronto, ON, Canada, 6–9 July 2020. [Google Scholar]
- Li, Y.; Liu, Q. A comprehensive review study of cyber-attacks and cyber security. Emerging trends and recent developments. Energy Rep. 2021, 7, 8176–8186. [Google Scholar] [CrossRef]
- Ahmed, M.; Byreddy, S.; Nutakki, A.; Sikos, L.F.; Haskell-Dowland, P. ECU-IoHT: A dataset for analyzing cyberattacks in internet of health things. Ad Hoc Netw. 2021, 122, 102621. [Google Scholar] [CrossRef]
- Ahmed, M.; Byreddy, S.; Nutakki, A.; Sikos, L.; Haskell-Dowland, P. ECU-IoHT, 2020. Available online: https://doi.org/10.25958/5f1f97b837aca (accessed on 10 January 2023).
- Zachos, G.; Essop, I.; Mantas, G.; Porfyrakis, K.; Ribeiro, J.C.; Rodriguez, J. An anomaly-based intrusion detection system for internet of medical things networks. Electronics 2021, 10, 2562. [Google Scholar] [CrossRef]
- Ahmad, Z.; Shahid Khan, A.; Wai Shiang, C.; Abdullah, J.; Ahmad, J.F. Network intrusion detection system: A systematic study of machine learning and deep learning approaches. Trans. Emerg. Telecommun. Technol. 2021, 32, e4150. [Google Scholar] [CrossRef]
- Kuzlu, M.; Fair, C.; Guler, O. Role of artificial intelligence in the internet of things (IoT) cyber security. Discov. Internet Things 2021, 1, 7. [Google Scholar] [CrossRef]
- Sarker, I.H.; Abushark, A.I. Internet of Things (IoT) security intelligence: A comprehensive overview, machine learning solutions and research directions. Mob. Netw. Appl. 2022, 1–17. [Google Scholar] [CrossRef]
- Esteva, A.; Kuprel, B.; Novoa, R.A.; Justin, Ko.; Sweeter, S.M.; Blau, H.M.; Thrun, S. Dermatologist-level classification of skin cancer with deep neural networks. Nature 2017, 542, 115–118. [Google Scholar] [CrossRef]
- Sze, V.; Chen, Y.H.; Yang, T.J.; Emer, J.S. Efficient processing of deep neural networks: A tutorial and survey. Proc. IEEE 2017, 105, 2295–2329. [Google Scholar] [CrossRef]
- Manimurugan, S.; Al-Mutairi, S.; Aborokbah, M.M.; Chilamkurti, N.; Ganesan, S.; Patan, R. Effective attack detection in internet of medical things smart environment using a deep belief neural network. IEEE Access 2020, 8, 77396–77404. [Google Scholar] [CrossRef]
- Diro, A.A.; Chilamkurti, N. Distributed attack detection scheme using deep learning approach for internet of things. Future Gener. Comput. Syst. 2018, 82, 761–768. [Google Scholar] [CrossRef]
- Anthi, E.; Williams, L.; Burnap, P. Pulse: An adaptive intrusion detection for the internet of things. In Proceedings of the Conference on Living in the Internet of Things: Cyber Security of the IoT, London, UK, 28–29 March 2018. [Google Scholar]
- Thamilarasu, G.; Odesile, A.; Hoang, A. An intrusion detection system for internet of medical things. IEEE Access 2020, 8, 181560–181576. [Google Scholar] [CrossRef]
- Radanliev, P.; De Roure, D. Disease X vaccine production and supply chains: Risk assessing healthcare systems operating with artificial intelligence and industry 4.0. Health Technol. 2023, 13, 11–15. [Google Scholar] [CrossRef]
- Radanliev, P.; De Roure, D. Advancing the cyber security of the healthcare system with self-optimising and self-adaptive artificial intelligence (part 2). Health Technol. 2022, 12, 923–929. [Google Scholar] [CrossRef]
- Eliash, C.; Lazar, I.; Nissim, N. SEC-C-U: The Security of Intensive Care Unit Medical Devices and Their Ecosystems. IEEE Access 2020, 8, 64193–64224. [Google Scholar] [CrossRef]
- Syed, M.; Syed, S.; Sexton, K.; Syeda, H.B.; Garza, M.; Zozus, M.; Syed, F.; Begum, S.; Syed, A.U.; Sanford, J.; et al. Application of Machine Learning in Intensive Care Unit (ICU) Settings Using MIMIC Dataset: Systematic Review. Informatics 2021, 8, 16. [Google Scholar] [CrossRef] [PubMed]
- Ahmed, M.; Mahmood, A.N.; Hu, J. A survey of network anomaly detection techniques. J. Netw. Comput. Appl. 2016, 60, 19–31. [Google Scholar] [CrossRef]
- Fernandes, G.; Rodrigues, J.J.P.C.; Carvalho, L.F.; AI-Muhtadi, J.F.; Proenca, M.L., Jr. A comprehensive survey on network anomaly detection. Telecommun. Syst. 2019, 70, 447–489. [Google Scholar] [CrossRef]
- Hijazi, S.; Obaidat, M.S. A new detection and prevention system for ARP attacks using static entry. IEEE Syst. J. 2019, 13, 2732–2738. [Google Scholar] [CrossRef]
- Vijayakumar, K.P.; Pradeep, M.K.K.; Kottilingam, K.; Karthick, T.; Ganeshkumar, P. An adaptive neuro-fuzzy logic based jamming detection system in WSN. Soft Comput. 2019, 23, 2655–2667. [Google Scholar] [CrossRef]
- Liao, S.; Zu, C.; Zhao, Y.; Zhang, Z.; Zhang, C.; Gao, Y.; Zhong, G. A comprehensive detection approach of Nmap: Principles, rules and experiments. In Proceedings of the 2020 International Conference on Cyber-Enabled Distributed Computing and Knowledge Discovery (CyberC), Chongqing, China, 29–30 October 2020; 30 October 2020. [Google Scholar]
- Zhang, Q.; Han, R.; Xin, G.; Liu, C.H.; Wang, G.; Chen, L.Y. Lightweight and accurate DNN-based anomaly detection at edge. IEEE Trans. Parallel Distrib. Syst. 2021, 33, 2927–2942. [Google Scholar] [CrossRef]
- Nicolazzo, S.; Nocera, A.; Ursino, D.; Virgili, L. A privacy-preserving approach to prevent feature disclosure in an IoT scenario. Future Gener. Comput. Syst. 2020, 15, 502–519. [Google Scholar] [CrossRef]
- Cauteruccio, F.; Cinelli, L.; Corradini, E.; Terracina, G.; Ursino, D.; Virgili, L.; Savaglio, C.; Liotta, A.; Fortino, G. A framework for anomaly detection and classification in Multiple IoT scenarios. Future Gener. Comput. Syst. 2021, 114, 322–335. [Google Scholar] [CrossRef]

| Category | ECU-IoHT | ECU-IoHT in Proposed System | ||
|---|---|---|---|---|
| Counts | Counts | Training (80%) | Training (20%) | |
| No Attack/Normal | 23,453 | 23,453 | 18,780 | 4673 |
| ARP Spoofing | 2359 | 2359 | 18,780 | 4673 |
| DoS Attack | 639 | 639 | 525 | 114 |
| Nmap PortScan | 6836 | 6836 | 5510 | 1326 |
| Smurf Attack | 77,920 | 77,920 | 62,218 | 15,642 |
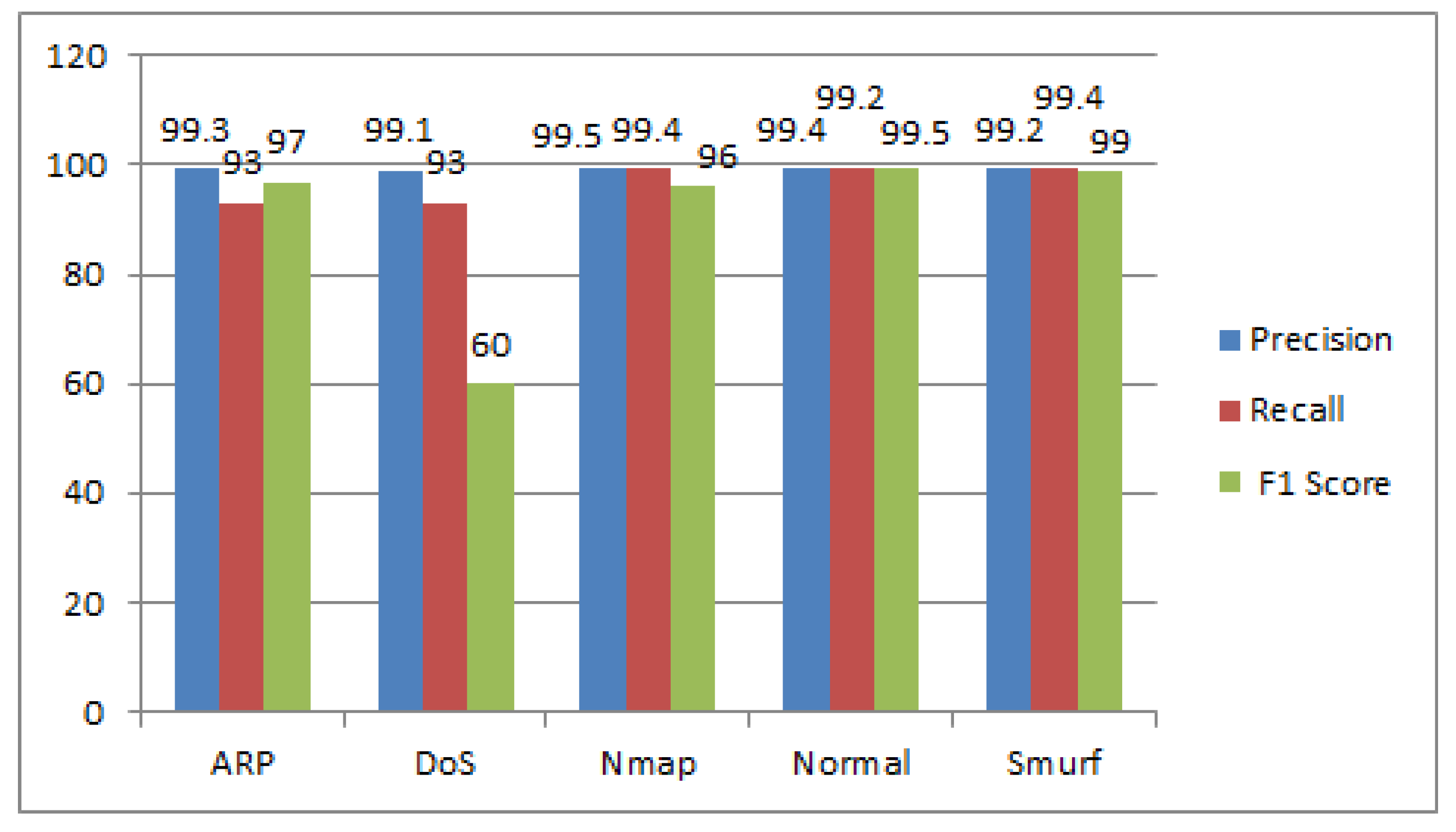
| Systems/ Attacks | ARP | DoS | Nmap | Normal | Smurf | |
|---|---|---|---|---|---|---|
| Proposed System (%) | Precision | 99.3 | 99.1 | 99.5 | 99.4 | 99.2 |
| Recall | 93 | 93 | 99.4 | 99.2 | 99.4 | |
| F1 Score | 97 | 60 | 96 | 99.5 | 99 | |
| Existing System [27] % | Precision | 96.12 | 96.21 | |||
| Recall | 96.24 | 98.34 | ||||
| F1 Score | 97 | 97 | ||||
| Existing DM System [28] % | Precision | 97 | 98.56 | 99.52 | ||
| Recall | 99.5 | 99 | 97.43 | |||
| F1 Score | 98.47 | 98.78 | 98.47 | |||
| Existing SM System [28] % | Precision | 96.55 | 87.44 | 99.35 | ||
| Recall | 99 | 99.48 | 95 | |||
| F1 Score | 93 | |||||
| Existing SM System [29] % | Precision | 97.7 | ||||
| Recall | 97.7 | |||||
| F1 Score | 97.7 |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2023 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Vijayakumar, K.P.; Pradeep, K.; Balasundaram, A.; Prusty, M.R. Enhanced Cyber Attack Detection Process for Internet of Health Things (IoHT) Devices Using Deep Neural Network. Processes 2023, 11, 1072. https://doi.org/10.3390/pr11041072
Vijayakumar KP, Pradeep K, Balasundaram A, Prusty MR. Enhanced Cyber Attack Detection Process for Internet of Health Things (IoHT) Devices Using Deep Neural Network. Processes. 2023; 11(4):1072. https://doi.org/10.3390/pr11041072
Chicago/Turabian StyleVijayakumar, Kedalu Poornachary, Krishnadoss Pradeep, Ananthakrishnan Balasundaram, and Manas Ranjan Prusty. 2023. "Enhanced Cyber Attack Detection Process for Internet of Health Things (IoHT) Devices Using Deep Neural Network" Processes 11, no. 4: 1072. https://doi.org/10.3390/pr11041072
APA StyleVijayakumar, K. P., Pradeep, K., Balasundaram, A., & Prusty, M. R. (2023). Enhanced Cyber Attack Detection Process for Internet of Health Things (IoHT) Devices Using Deep Neural Network. Processes, 11(4), 1072. https://doi.org/10.3390/pr11041072









