Reptile Search Algorithm (RSA)-Based Selective Harmonic Elimination Technique in Packed E-Cell (PEC-9) Inverter
Abstract
:1. Introduction
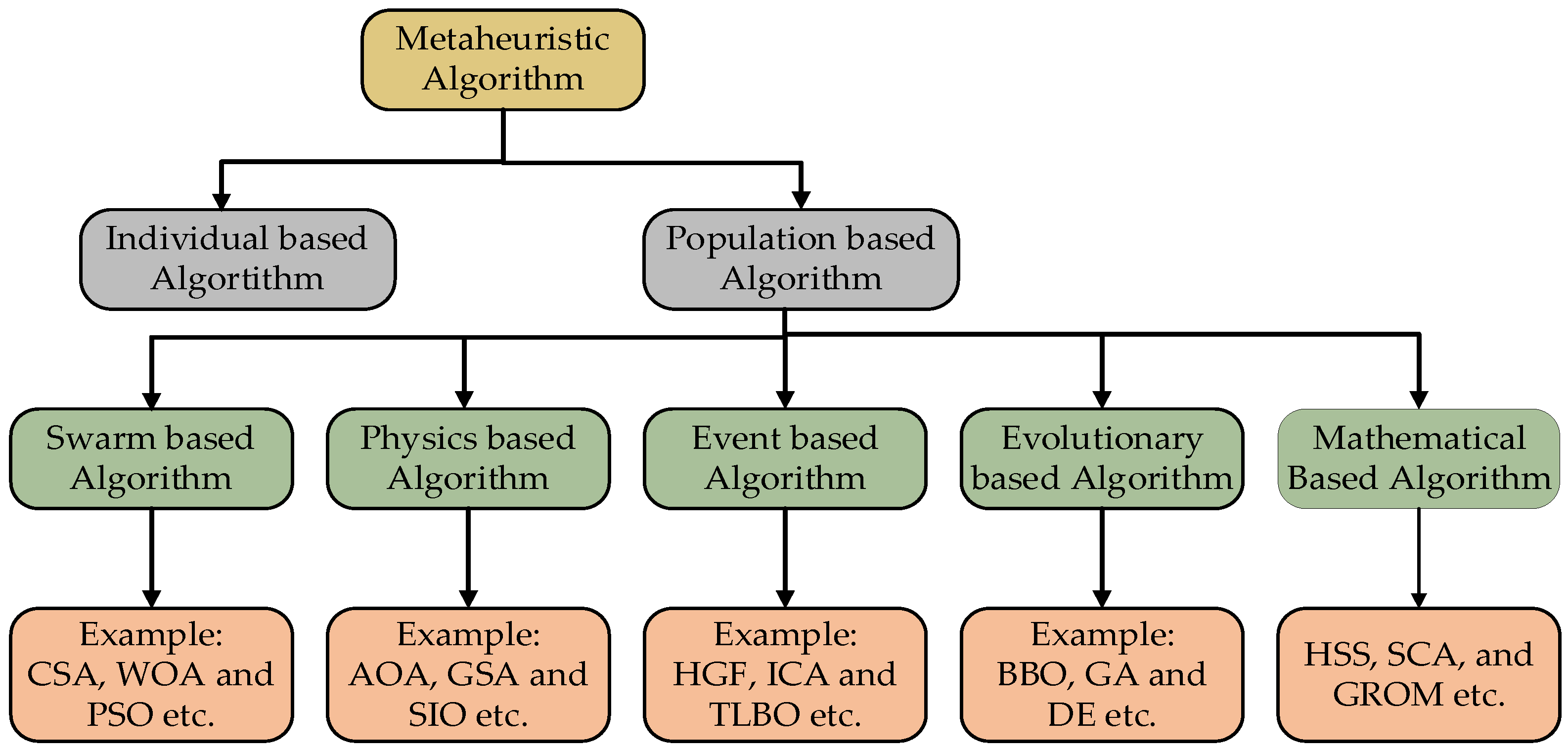
2. Metaheuristic Algorithm
3. Reptile Search Algorithm
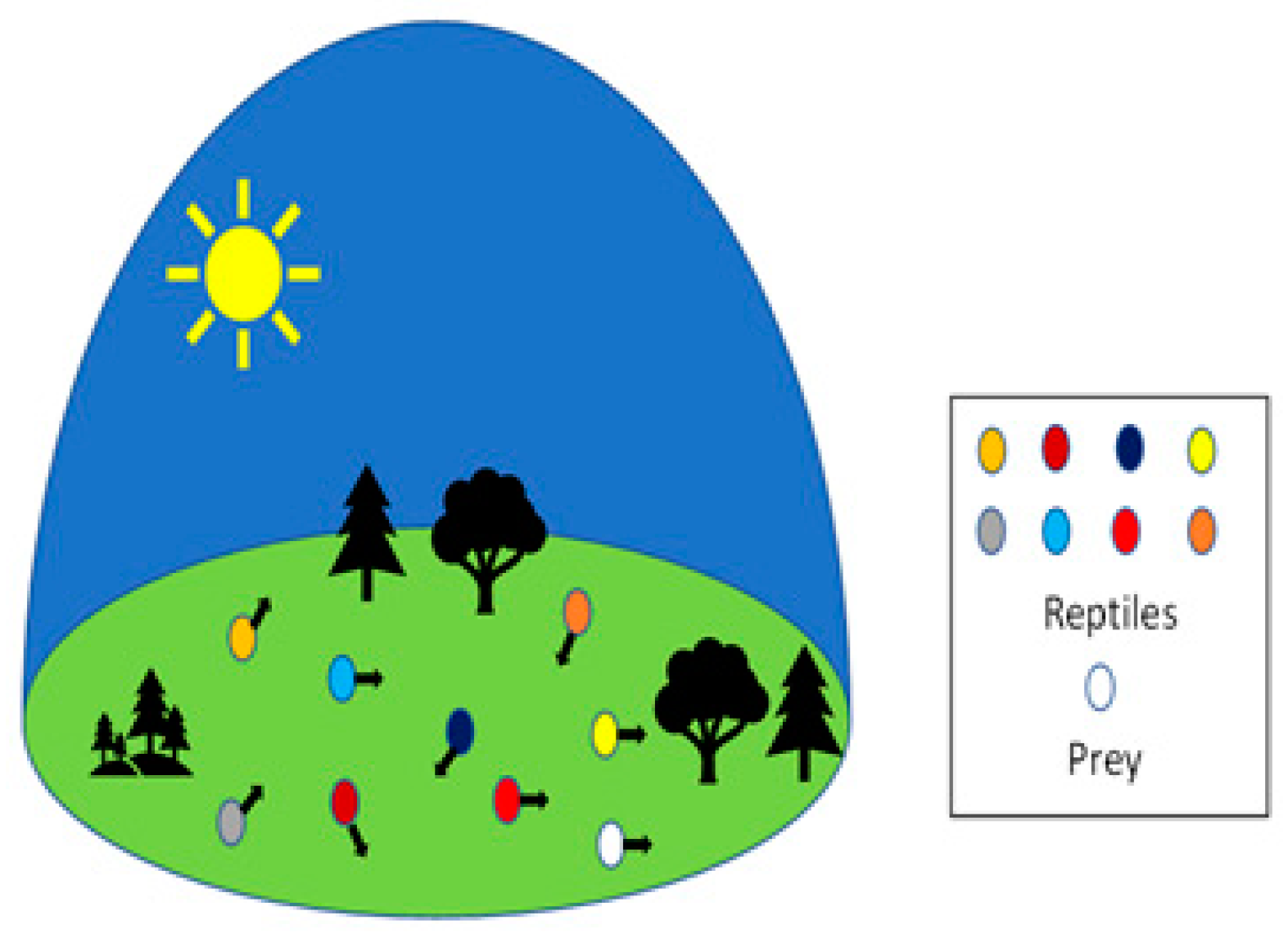
3.1. Crocodile Biology and Behavior
3.2. Initialization Phase
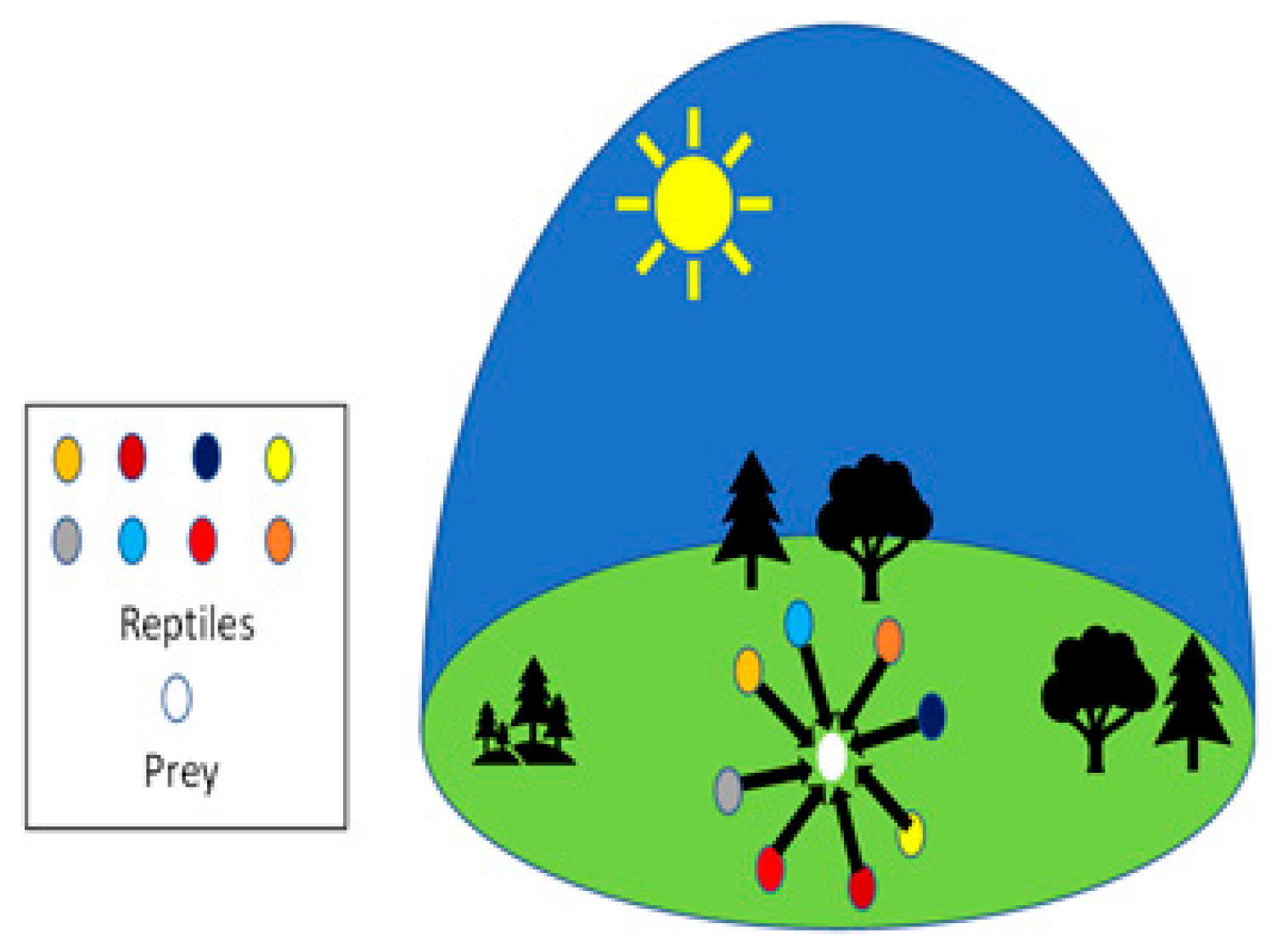
3.3. Exploration (Encircling Phase)
3.4. Exploitation (Hunting Phase)
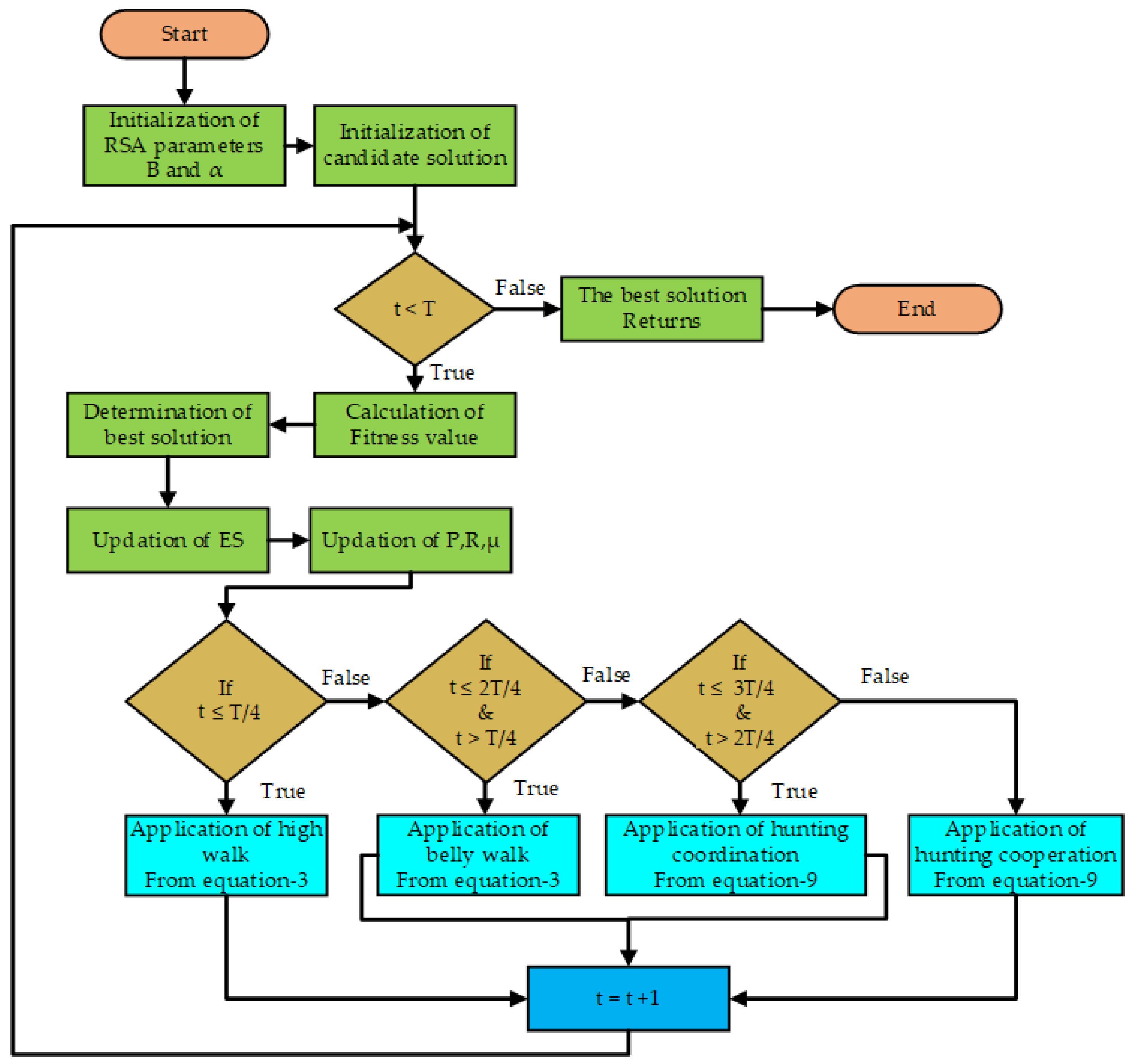
3.5. Modeling
3.6. Time Complexity
4. Nine–Level Packed E–Cell (PEC–9)
4.1. PEC–9 Topology
4.2. Switching State Topology
4.3. Fault–Tolerant Capability in PEC–9 Topology
5. Implementation of the Reptile Search Algorithm in Selective Harmonic Elimination
Switching Angle Calculation
6. Simulation Results
7. Experimental Verification
8. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Acknowledgments
Conflicts of Interest
References
- Sharifzadeh, M.; Mehrasa, M.; Babaie, M.; Al-Haddad, K. Stable Frequency Response for Multi-Terminal MMC-HVDC System with DC Voltage Fluctuations. In Proceedings of the IECON 2019—45th Annual Conference of the IEEE Industrial Electronics Society, Lisbon, Portugal, 14–17 October 2019; pp. 3577–3582. [Google Scholar] [CrossRef]
- Noghani, K.A.; Sharifzadeh, M.; Ounejjar, Y.; Al-Haddad, K. Current Based Model Predictive Control for DC Capacitor Optimization in Grid-Connected and Stand-Alone Nine-Level Packed U-Cell Inverter. In Proceedings of the 2019 IEEE 28th International Symposium on Industrial Electronics (ISIE), Vancouver, BC, Canada, 12–14 June 2019; pp. 787–792. [Google Scholar] [CrossRef]
- Sajadi, R.; Iman-Eini, H.; Bakhshizadeh, M.K.; Neyshabouri, Y.; Farhangi, S. Selective harmonic elimination technique with control of capacitive DC-link voltages in an asymmetric cascaded H-bridge inverter for STATCOM application. IEEE Trans. Ind. Electron. 2018, 65, 8788–8796. [Google Scholar] [CrossRef]
- el Gadari, A.; el Ouardi, H.; Alibou, S.; Ounejjar, Y.; Bejjit, L.; Sharifzadeh, M. New Nine-Level SPUC Inverter Using Single DC Source. In Proceedings of the IECON 2019—45th Annual Conference of the IEEE Industrial Electronics Society, Lisbon, Portugal, 14–17 October 2019; pp. 1892–1897. [Google Scholar] [CrossRef]
- Sharifzadeh, M.; Babaie, M.; Sebaaly, F.; Mehrasa, M.; Chouinard, G.; Al-Haddad, K. Low Switching Frequency Operation of PEC9 Multilevel Inverter Using Modified SHM-PWM. In Proceedings of the IECON 2020 the 46th Annual Conference of the IEEE Industrial Electronics Society, Singapore, 18–21 October 2020; pp. 4215–4220. [Google Scholar] [CrossRef]
- Sharifzadeh, M.; Vahedi, H.; Al-Haddad, K. SHM-PWM applied on single DC source CHB with self-regulation of capacitors voltages. In Proceedings of the 2018 IEEE International Conference on Industrial Technology (ICIT), Lyon, France, 20–22 February 2018; pp. 1893–1897. [Google Scholar] [CrossRef]
- Khan, S.A. Performance Analysis of Nine-Level Packed E Cell Inverter for Different Carrier Wave PWM Techniques. In AI and Machine Learning Paradigms for Health Monitoring System; Springer: Singapore, 2021; pp. 419–427. [Google Scholar] [CrossRef]
- Sharifzadeh, M.; Vahedi, H.; Al-Haddad, K. New Constraint in SHE-PWM for Single-Phase Inverter Applications. IEEE Trans. Ind. Appl. 2018, 54, 4554–4562. [Google Scholar] [CrossRef]
- Jana, A.-S.; Liu, H.-D.; Lu, S.-D.; Lin, C.-H. New Control Scheme for Solar Power Systems under Varying Solar Radiation and Partial Shading Conditions. Processes 2021, 9, 1359. [Google Scholar] [CrossRef]
- Siddique, M.D.; Mekhilef, S.; Padmanaban, S.; Memon, M.A.; Kumar, C. Single-Phase Step-Up Switched-Capacitor-Based Multilevel Inverter Topology with SHEPWM. IEEE Trans. Ind. Appl. 2021, 57, 3107–3119. [Google Scholar] [CrossRef]
- Lu, S.-D.; Lin, C.-H.; Huang, L.-Y.; Lee, Y.-L.; Liu, H.-D.; Liao, P.-C.; Gao, G.-J.; Hsu, C.-M. Novel Global-MPPT Control Strategy Considering the Variation in the Photovoltaic Module Output Power and Loads for Solar Power Systems. Processes 2022, 10, 367. [Google Scholar] [CrossRef]
- Liu, H.-D.; Lu, S.-D.; Lee, Y.-L.; Lin, C.-H. A Novel Photovoltaic Module Quick Regulate MPPT Algorithm for Uniform Irradiation and Partial Shading Conditions. Processes 2021, 9, 2213. [Google Scholar] [CrossRef]
- Fahad, M. A Dual Source Switched-Capacitor Multilevel Inverter with Reduced Device Count. Electronics 2021, 11, 67. [Google Scholar] [CrossRef]
- Islam, N.; Mohammad, K.; Khan, R.A.; Sarwer, Z.; Sarwar, A. Symmetrical and Asymmetrical Multilevel Inverter Topologies with Reduced Device Count: A Review. In Proceedings of the 2021 2nd International Conference for Emerging Technology (INCET), Belagavi, India, 21–23 May 2021; pp. 1–6. [Google Scholar] [CrossRef]
- Sarwar, M.I.; Alam, M.S.; Ahmad, S.; Tariq, M. A Nine-Level Cascaded Multilevel Inverter with Reduced Switch Count and Lower Harmonics. In Applications of Computing, Automation and Wireless Systems in Electrical Engineering; Lecture Notes in Electrical Engineering; Springer: Singapore, 2019; p. 553. [Google Scholar] [CrossRef]
- Sarwar, M.I.; Alam, M.S.; Sarwar, A.; M Zaid, A.R.; Sarfraz, M. PSO based Optimal Operation of a Cascaded Grid Connected Three Phase Solar PV Inverter. In Proceedings of the 2021 International Conference on Advances in Electrical, Computing, Communication and Sustainable Technologies (ICAECT), Bhilai, India, 19–20 February 2021; pp. 1–7. [Google Scholar] [CrossRef]
- Fahad, M. Asymmetric Multilevel Inverter Topology and Its Fault Management Strategy for High-Reliability Applications. Energies 2021, 14, 4302. [Google Scholar] [CrossRef]
- Khan, S.A.; Upadhyay, D.; Ali, M.; Rahman, K.; Tariq, M.; Sarwar, A.; Anees, A. Integration of Distributed PV System with Grid Using Nine-Level PEC Inverter. In International Conference on Modelling, Simulation and Intelligent Computing; Springer: Singapore, 2021; pp. 555–562. [Google Scholar] [CrossRef]
- Khan, A.I. Artificial Neural Network-Based Maximum Power Point Tracking Method with the Improved Effectiveness of Standalone Photovoltaic System. In AI and Machine Learning Paradigms for Health Monitoring System; Springer: Singapore, 2021; pp. 459–470. [Google Scholar] [CrossRef]
- Abualigah, L. Reptile Search Algorithm (RSA): A nature-inspired meta-heuristic optimizer. Expert Syst. Appl. 2022, 191, 116158. [Google Scholar] [CrossRef]
- Farooqui, S.A. Crystal Structure Algorithm (CryStAl) Based Selective Harmonic Elimination Modulation in a Cascaded H-Bridge Multilevel Inverter. Electronics 2021, 10, 3070. [Google Scholar] [CrossRef]
- Khan, R.A. Archimedes Optimization Algorithm Based Selective Harmonic Elimination in a Cascaded H-Bridge Multilevel Inverter. Sustainability 2021, 14, 310. [Google Scholar] [CrossRef]
- Hussan, M.R. Aquila Optimization Based Harmonic Elimination in a Modified H-Bridge Inverter. Sustainability 2022, 14, 929. [Google Scholar] [CrossRef]
- Khan, S.A. M-Type and CD-Type Carrier Based PWM Methods and Bat Algorithm-Based SHE and SHM for Compact Nine-Level Switched Capacitor Inverter. IEEE Access 2021, 9, 87731–87748. [Google Scholar] [CrossRef]
- Farooqui, S.A.; Khan, R.A.; Islam, N.; Ahmed, N. Cuckoo Search Algorithm and Artificial Neural Network-based MPPT: A Comparative Analysis. In Proceedings of the 2021 IEEE 8th Uttar Pradesh Section International Conference on Electrical, Electronics and Computer Engineering (UPCON), Dehradun, India, 11–13 November 2021; pp. 1–5. [Google Scholar] [CrossRef]
- Upadhyay, M.; Ali, M.; Tariq, M.; Khan, S.A.; Alamri, B.; Alahmadi, A. Thirteen-level UXE-type inverter with 12-band hysteresis current control employing PSO based PI controller. IEEE Access 2022, 10, 29890–29902. [Google Scholar] [CrossRef]
- Sharifzadeh, M.; Al-Haddad, K. Packed E-Cell (PEC) Converter Topology Operation and Experimental Validation. IEEE Access 2019, 7, 93049–93061. [Google Scholar] [CrossRef]














| States | T1 | T2 | T3 | T4 | T5 | T6 | T7 | IOutput | VOutput |
|---|---|---|---|---|---|---|---|---|---|
| 1 | 1 | 0 | 0 | 0 | 1 | 1 | 0 | +I | +V |
| 2 | 1 | 0 | 0 | 0 | 1 | 0 | 1 | +I | +3V/4 |
| 3 | 1 | 0 | 1 | 0 | 1 | 0 | 0 | +I | +V/2 |
| 4 | 1 | 1 | 0 | 0 | 0 | 1 | 0 | +I | +V/4 |
| 5 | 1 | 1 | 0 | 0 | 0 | 0 | 0 | -- | 0 |
| 6 | 0 | 0 | 0 | 1 | 1 | 1 | 0 | −I | −V/4 |
| 7 | 0 | 0 | 0 | 1 | 1 | 0 | 1 | −I | −V/2 |
| 8 | 0 | 1 | 0 | 1 | 0 | 0 | 0 | −I | −3V/4 |
| 9 | 0 | 1 | 1 | 1 | 0 | 0 | 0 | −I | −V |
| Parameters | Selection |
|---|---|
| No. of runs | 25 |
| No. of iterations | 500 |
| No. of crocodile (Space search) | 30 |
| No. of function evaluation | 1500 |
| α | 0.1 |
| β | 0.1 |
| Sr. No. | Component/ Parameter | Specification | Quantity/ Component No. |
|---|---|---|---|
| 1. | DC voltage source | 600 V | 1 |
| 2. | Power frequency | 50 Hz | 1 |
| 3. | IGBT | IKW40N65ES5 | 8 |
| 4. | load | 50 Ω + 120 mH, 100 + 240 mH, 50 Ω, 100 Ω | R and RL type |
| 5. | Capacitor | 24,000 µF | 2 |
| Sr. No. | Components | Specification |
|---|---|---|
| 1. | IGBT | IKW40N65ES5 |
| 2. | Driver Circuit for IGBTs | TLP 250, 1 A |
| 3. | DSP | TMS320F28335 |
| 4. | Input DC Source | 200 V |
| 5. | Load | R = 30 Ω, L = 30 mH |
| 6 | Fundamental frequency | 50 Hz |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2022 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Khan, R.A.; Sabir, B.; Sarwar, A.; Liu, H.-D.; Lin, C.-H. Reptile Search Algorithm (RSA)-Based Selective Harmonic Elimination Technique in Packed E-Cell (PEC-9) Inverter. Processes 2022, 10, 1615. https://doi.org/10.3390/pr10081615
Khan RA, Sabir B, Sarwar A, Liu H-D, Lin C-H. Reptile Search Algorithm (RSA)-Based Selective Harmonic Elimination Technique in Packed E-Cell (PEC-9) Inverter. Processes. 2022; 10(8):1615. https://doi.org/10.3390/pr10081615
Chicago/Turabian StyleKhan, Rashid Ahmed, Bushra Sabir, Adil Sarwar, Hwa-Dong Liu, and Chang-Hua Lin. 2022. "Reptile Search Algorithm (RSA)-Based Selective Harmonic Elimination Technique in Packed E-Cell (PEC-9) Inverter" Processes 10, no. 8: 1615. https://doi.org/10.3390/pr10081615
APA StyleKhan, R. A., Sabir, B., Sarwar, A., Liu, H.-D., & Lin, C.-H. (2022). Reptile Search Algorithm (RSA)-Based Selective Harmonic Elimination Technique in Packed E-Cell (PEC-9) Inverter. Processes, 10(8), 1615. https://doi.org/10.3390/pr10081615









