Federated Learning-Driven Cybersecurity Framework for IoT Networks with Privacy Preserving and Real-Time Threat Detection Capabilities
Abstract
1. Introduction
- Data Heterogeneity: IoT devices generate a wide range of data types that vary in quality, volume, and format. Machine learning models must be designed to handle this heterogeneity without compromising performance [6].
- Resource Constraints: Many IoT devices have limited computational power, memory, and energy resources. Ensuring the efficient operation of FL algorithms under these constraints remains a significant challenge [7].
- Real-Time Threat Detection: Timely detection and response to cyber threats in IoT networks are crucial to minimizing damage. Achieving real-time performance while maintaining high accuracy is still an open problem [8].
- Security and Privacy Risks: Although FL reduces the need to share raw data, the transmission of model updates poses potential risks. Techniques such as secure aggregation and encryption are essential to mitigate these vulnerabilities [9].
- The development of a novel threat detection algorithm based on GRU-based recurrent neural networks (RNNs), optimized for analyzing time-series data generated by IoT devices.
- The integration of homomorphic encryption to secure the aggregation of model updates, ensuring robust privacy preservation.
- An energy-efficient architecture tailored to the resource constraints of IoT devices, reducing computational overhead.
- A comprehensive evaluation of the framework’s performance in identifying cyber threats, including DDoS attacks, malware, and unauthorized access attempts.
2. Related Work and Contribution
- Scalability: Current FL frameworks face difficulties in scaling to IoT networks with a large number of heterogeneous devices [15].
- Energy Efficiency: The high computational requirements of privacy-preserving techniques and complex ML models are a bottleneck for resource-constrained IoT devices [16].
- Real-Time Detection: Many existing approaches are unable to provide the real-time responsiveness required to mitigate cyber threats effectively in IoT systems [17].
- Privacy Risks: Although FL reduces the need to share raw data, the security of model updates remains vulnerable to adversarial attacks, necessitating robust encryption and secure aggregation methods [18].
3. Materials and Methods
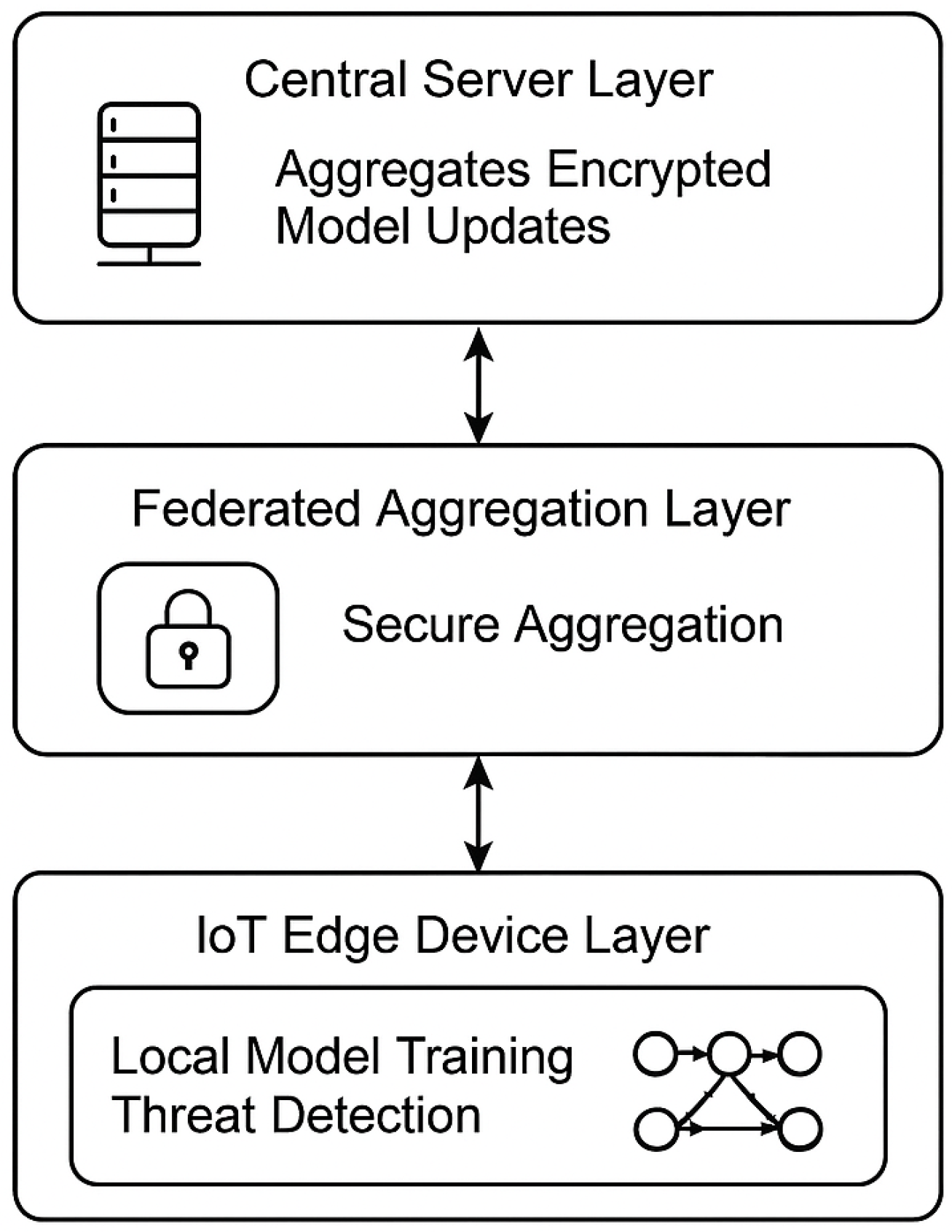
- IoT Edge Device Layer: Hosts local model training and threat detection using GRU-based recurrent neural networks (RNNs) optimized for time-series data generated by IoT devices.
- Federated Aggregation Layer: Implements a secure aggregation mechanism using homomorphic encryption, enabling decentralized model updates without exposing sensitive data.
- Central Server Layer: Aggregates encrypted model updates, constructs a global model, and disseminates it back to IoT devices.
3.1. Problem Formulation
3.2. Federated Learning Architecture
3.3. Anomaly Detection Using GRU-Based Recurrent Neural Networks
3.4. Privacy-Preserving Mechanisms
3.5. Energy-Efficient Design
3.6. Implementation and Scientific Innovation
- Integration of FL and GRU-based RNNs: Combines the decentralized learning capabilities of FL with the sequential data analysis strength of GRU-based RNNs for enhanced anomaly detection.
- Advanced Privacy Mechanisms: Employs homomorphic encryption, differential privacy, and secure multi-party computation (SMPC) to address multi-layered security and privacy concerns.
- Energy-Efficient Design: Optimizes computational resources through model compression and adaptive learning strategies, ensuring compatibility with IoT devices.
- Real-Time Threat Detection: Enables fast and accurate anomaly detection, critical to mitigate cyber threats from the IoT in real time.
4. Analysis and Results
4.1. Experimental Setup
- Framework Implementation: The proposed framework was implemented using Python, leveraging TensorFlow for model development and PySyft for federated learning and privacy-preserving techniques.
- Hardware Setup: The experimental setup consisted of a distributed architecture, with edge nodes equipped with NVIDIA Jetson Nano devices for local model training, and a central server featuring an NVIDIA RTX 3080 GPU for federated aggregation and global model construction.
- Dataset: The evaluation utilized a combination of synthetic IoT traffic datasets alongside real-world datasets, including the CICIDS2017 dataset [19], widely recognized for network intrusion detection benchmarking. The dataset has been extensively described in the paper [20], which provides more details about the dataset and its fundamental principles. However, a brief description and a table of the variables contained in the dataset are provided in the Appendix A at the end of this paper.
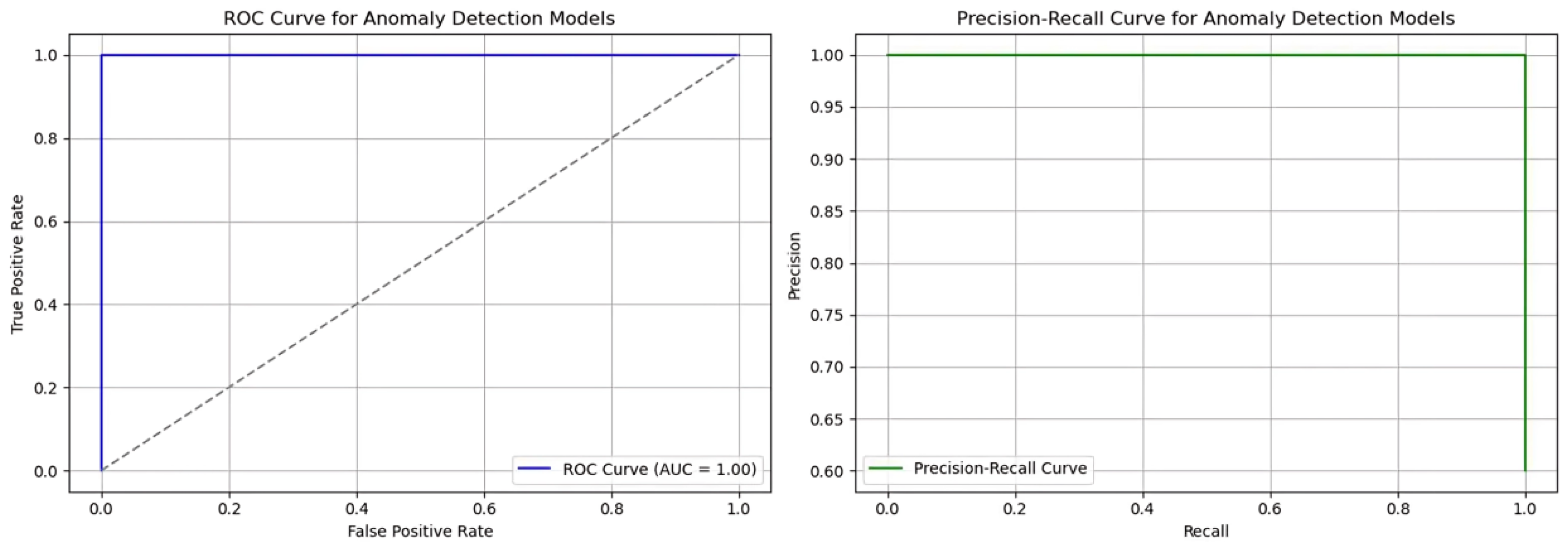
4.2. Anomaly Detection Performance
- Accuracy: Proportion of correctly identified benign and malicious instances.
- Precision: Ratio of true positives to the total predicted positives.
- Recall: Ratio of true positives to the total actual positives.
- F1-Score: Harmonic mean of precision and recall, providing a balanced measure.
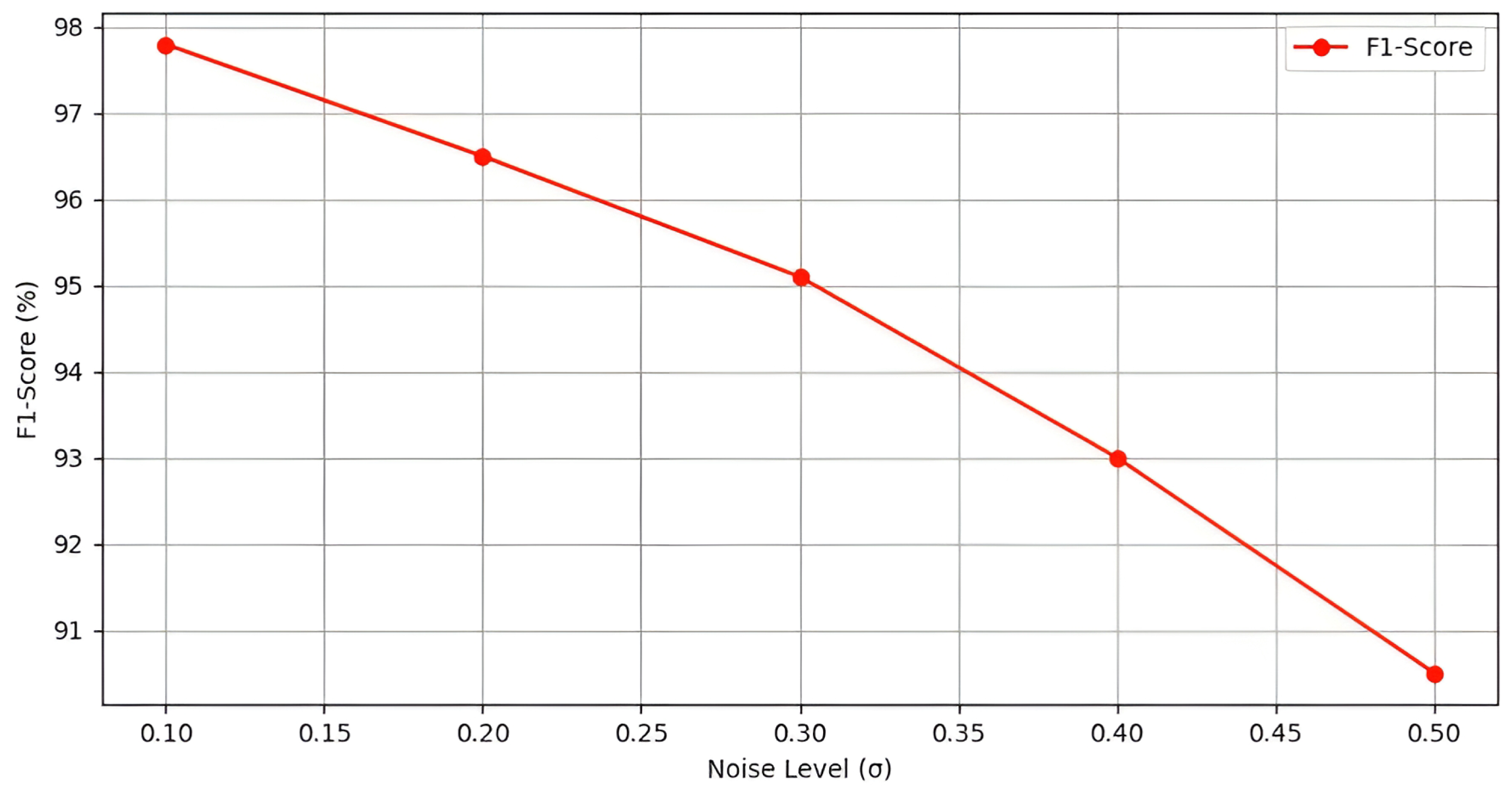
4.3. Privacy Preservation Evaluation
4.4. Energy Efficiency
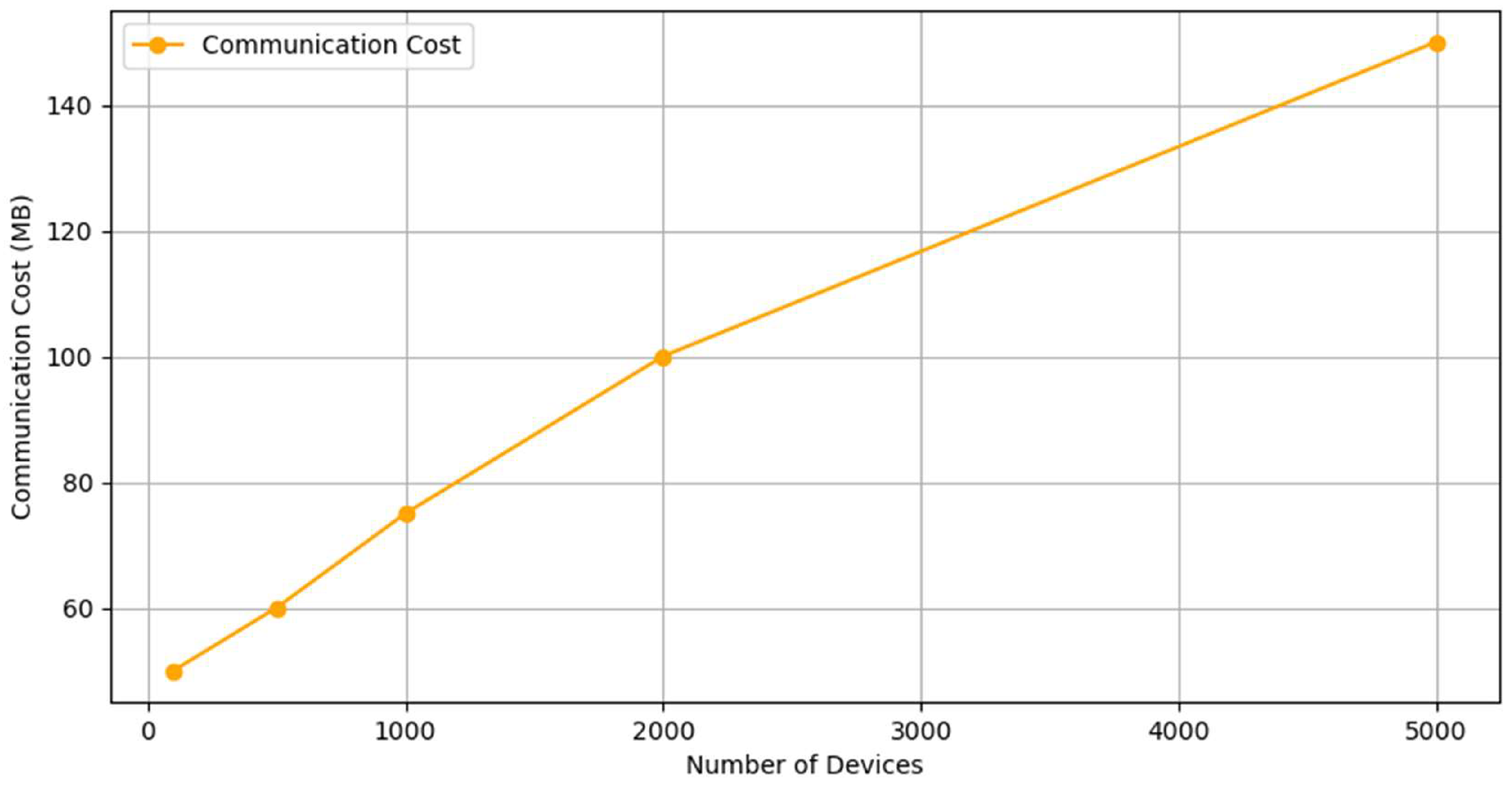
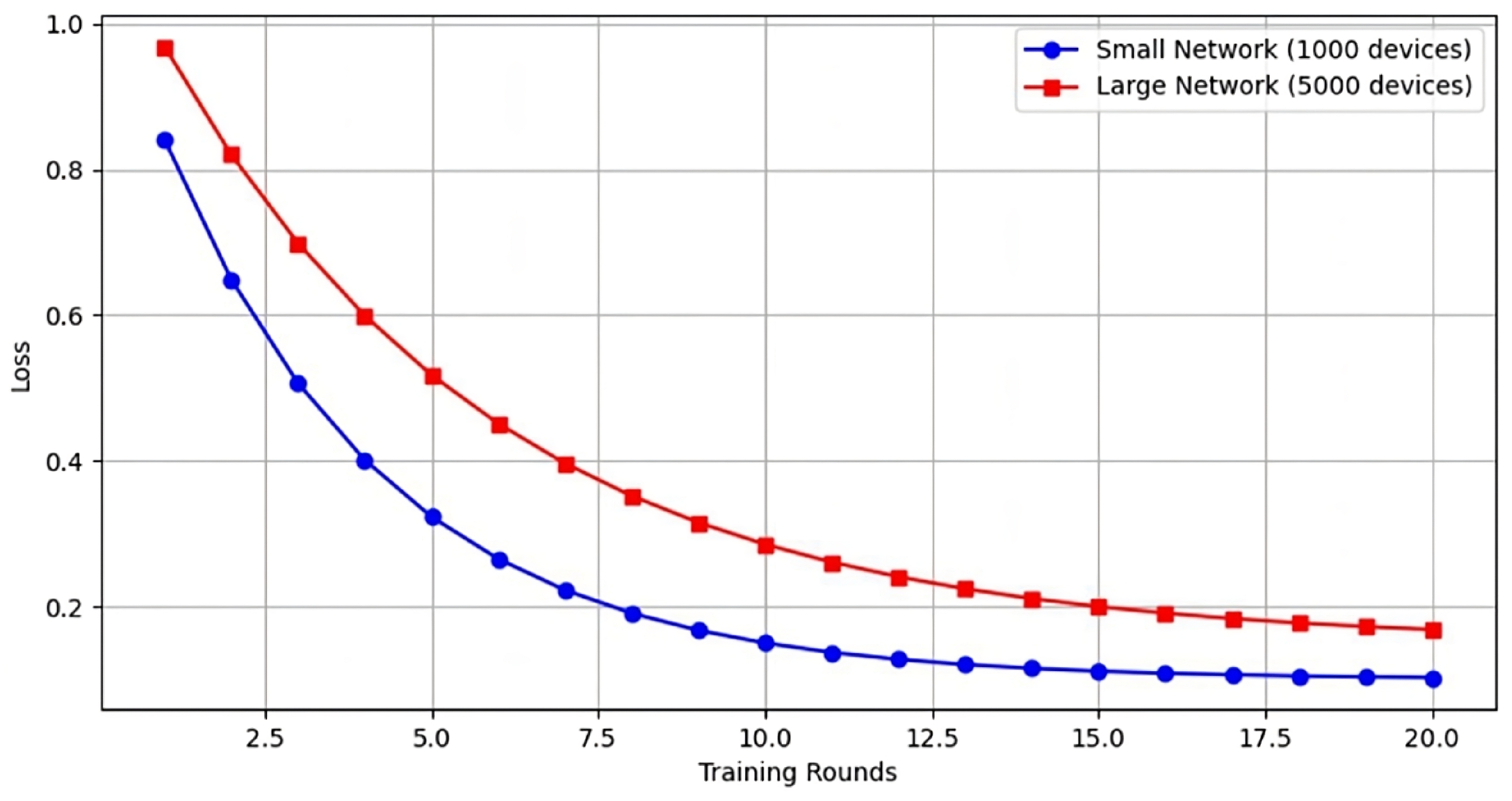
4.5. Scalability Analysis
5. Discussion
5.1. Key Findings and Their Implications
5.2. Comparative Evaluation with Existing Approaches
5.3. Potential Limitations
5.4. Future Directions
6. Conclusions
Author Contributions
Funding
Data Availability Statement
Conflicts of Interest
Appendix A
| Column Number | Column Name | Data Type |
| 0 | Destination Port | object |
| 1 | Flow Duration | float64 |
| 2 | Total Fwd Packets | float64 |
| 3 | Total Backward Packets | float64 |
| 4 | Total Length of Fwd Packets | float64 |
| 5 | Total Length of Bwd Packets | float64 |
| 6 | Fwd Packet Length Max | float64 |
| 7 | Fwd Packet Length Min | float64 |
| 8 | Fwd Packet Length Mean | float64 |
| 9 | Fwd Packet Length Std | float64 |
| 10 | Bwd Packet Length Max | float64 |
| 11 | Bwd Packet Length Min | float64 |
| 12 | Bwd Packet Length Mean | float64 |
| 13 | Bwd Packet Length Std | float64 |
| 14 | Flow Bytes/s | float64 |
| 15 | Flow Packets/s | float64 |
| 16 | Flow IAT Mean | float64 |
| 17 | Flow IAT Std | float64 |
| 18 | Flow IAT Max | float64 |
| 19 | Flow IAT Min | float64 |
| 20 | Fwd IAT Total | float64 |
| 21 | Fwd IAT Mean | float64 |
| 22 | Fwd IAT Std | float64 |
| 23 | Fwd IAT Max | float64 |
| 24 | Fwd IAT Min | float64 |
| 25 | Bwd IAT Total | float64 |
| 26 | Bwd IAT Mean | float64 |
| 27 | Bwd IAT Std | float64 |
| 28 | Bwd IAT Max | float64 |
| 29 | Bwd IAT Min | float64 |
| 30 | Fwd PSH Flags | float64 |
| 31 | Bwd PSH Flags | float64 |
| 32 | Fwd URG Flags | float64 |
| 33 | Bwd URG Flags | float64 |
| 34 | Fwd Header Length | float64 |
| 35 | Bwd Header Length | float64 |
| 36 | Fwd Packets/s | float64 |
| 37 | Bwd Packets/s | float64 |
| 38 | Min Packet Length | float64 |
| 39 | Max Packet Length | float64 |
| 40 | Packet Length Mean | float64 |
| 41 | Packet Length Std | float64 |
| 42 | Packet Length Variance | float64 |
| 43 | FIN Flag Count | float64 |
| 44 | SYN Flag Count | float64 |
| 45 | RST Flag Count | float64 |
| 46 | PSH Flag Count | float64 |
| 47 | ACK Flag Count | float64 |
| 48 | URG Flag Count | float64 |
| 49 | CWE Flag Count | float64 |
| 50 | ECE Flag Count | float64 |
| 51 | Down/Up Ratio | float64 |
| 52 | Average Packet Size | float64 |
| 53 | Avg Fwd Segment Size | float64 |
| 54 | Avg Bwd Segment Size | float64 |
| 55 | Fwd Header Length.1 | float64 |
| 56 | Fwd Avg Bytes/Bulk | float64 |
| 57 | Fwd Avg Packets/Bulk | float64 |
| 58 | Fwd Avg Bulk Rate | float64 |
| 59 | Bwd Avg Bytes/Bulk | float64 |
| 60 | Bwd Avg Packets/Bulk | float64 |
| 61 | Bwd Avg Bulk Rate | float64 |
| 62 | Subflow Fwd Packets | float64 |
| 63 | Subflow Fwd Bytes | float64 |
| 64 | Subflow Bwd Packets | float64 |
| 65 | Subflow Bwd Bytes | float64 |
| 66 | Init_Win_bytes_forward | float64 |
| 67 | Init_Win_bytes_backward | float64 |
| 68 | act_data_pkt_fwd | float64 |
| 69 | min_seg_size_forward | float64 |
| 70 | Active Mean | float64 |
| 71 | Active Std | float64 |
| 72 | Active Max | float64 |
| 73 | Active Min | float64 |
| 74 | Idle Mean | float64 |
| 75 | Idle Std | float64 |
| 76 | Idle Max | float64 |
| 77 | Idle Min | float64 |
| 78 | Label | object |
References
- IoT Analytics. The State of IoT: 2021 Edition. IoT Analytics Report. 2021. Available online: https://iot-analytics.com/product/state-of-iot-summer-2021/ (accessed on 1 July 2025).
- Ahmed, S.F.; Sharmin, S.; Kuldeep, S.A.; Lameesa, A.; Alam, M.S.B.; Liu, G.; Gandomi, A.H. Transformative Impacts of the Internet of Medical Things on Modern Healthcare. Results Eng. 2024, 25, 103787. [Google Scholar] [CrossRef]
- McMahan, B.; Moore, E.; Ramage, D.; Hampson, S.; Arcas, B.A. Communication-Efficient Learning of Deep Networks from Decentralized Data. In Proceedings of the Artificial Intelligence and Statistics, Fort Lauderdale, FL, USA, 20–22 April 2017. [Google Scholar]
- Bonawitz, K.; Ivanov, V.; Kreuter, B.; Marcedone, A.; McMahan, H.B.; Patel, S.; Ramage, D.; Segal, A.; Seth, K. Practical Secure Aggregation for Privacy-Preserving Machine Learning. In Proceedings of the 2017 ACM SIGSAC Conference on Computer and Communications Security, London, UK, 11–15 November 2019. [Google Scholar]
- Himdi, T. A Blockchain and AI-Driven Security Framework for Cognitive Cities. Adv. Artif. Intell. Mach. Learn. 2024, 4, 2908–2925. [Google Scholar]
- Altherwi, A.; Ahmad, M.T.; Alam, M.M.; Mirza, H.; Sultana, N.; Pasha, A.A.; Sultana, N.; Khan, A.I.; Alam, M.M.; Azim, R. A Hybrid Optimization Approach for Securing Cloud-Based E-Health Systems. Multimed. Tools Appl. 2024, 84, 16525–16560. [Google Scholar] [CrossRef]
- Shafique, M.; Marchisio, A.; Putra, R.V.W.; Hanif, M.A. Towards energy-efficient and secure edge AI: A cross-layer framework. ICCAD special session paper. In Proceedings of the 2021 IEEE/ACM International Conference On Computer Aided Design (ICCAD), IEEE, Virtual, 1 November–4 November 2021; pp. 1–9. [Google Scholar]
- Sinha, A.; Sharma, N.; Kumar, S.; Lande, A.; Iqbal, M.I. AI-Enhanced Living: The Future of Smart Homes. In Proceedings of the 2023 International Conference on Smart Devices (ICSD), Dehradun, India, 2–3 May 2024. [Google Scholar]
- Mehta, S.; Khurana, M.; Dogra, A.; Hariharan, S. Advancing IoT Security through Federated Learning: A Comprehensive Approach. In Proceedings of the 2024 3rd International Conference on Applied Artificial Intelligence and Computing (ICAAIC), IEEE, Salem, India, 5–7 June 2024; pp. 561–566. [Google Scholar]
- Awosika, T.; Shukla, R.M.; Pranggono, B. Transparency and privacy: The role of explainable ai and federated learning in financial fraud detection. IEEE Access 2024, 12, 64551–64560. [Google Scholar] [CrossRef]
- Iacob, A.; Sani, L.; Marino, B.; Aleksandrov, P.; Shen, W.F.; Lane, N.D. Worldwide federated training of language models. arXiv 2024, arXiv:2405.14446. [Google Scholar]
- Wei, K.; Li, J.; Ding, M.; Ma, C.; Su, H.; Zhang, B.; Poor, H.V. User-level privacy-preserving federated learning: Analysis and performance optimization. IEEE Trans. Mob. Comput. 2021, 21, 3388–3401. [Google Scholar] [CrossRef]
- Anelli, V.W.; Deldjoo, Y.; Di Noia, T.; Ferrara, A. Towards effective device-aware federated learning. In Proceedings of the AI* IA 2019–Advances in Artificial Intelligence: XVIIIth International Conference of the Italian Association for Artificial Intelligence, Rende, Italy, 19–22 November 2019; Proceedings 18. Springer: Berlin/Heidelberg, Germany, 2019; pp. 477–491. [Google Scholar]
- Nayak, J.; Naik, B.; Vimal, S.; Favorskaya, M. Machine Learning for Cyber-Physical Systems: Advances and Challenges; Springer: Berlin/Heidelberg, Germany, 2024. [Google Scholar]
- Campos, E.M.; Saura, P.F.; González-Vidal, A.; Hernández-Ramos, J.L.; Bernabé, J.B.; Baldini, G.; Skarmeta, A. Evaluating Federated Learning for intrusion detection in Internet of Things: Review and challenges. Comput. Netw. 2022, 203, 108661. [Google Scholar] [CrossRef]
- Demelius, L.; Kern, R.; Trügler, A. Recent advances of differential privacy in centralized deep learning: A systematic survey. ACM Comput. Surv. 2025, 57, 1–28. [Google Scholar] [CrossRef]
- Baqer, M. Energy-Efficient Federated Learning for Internet of Things: Leveraging In-Network Processing and Hierarchical Clustering. Future Internet 2024, 17, 4. [Google Scholar] [CrossRef]
- Li, S.; Ngai, E.; Voigt, T. Byzantine-Robust Aggregation in Federated Learning. In IEEE Transactions on Industrial Informatics; IEEE: New York, NY, USA, 2024. [Google Scholar]
- Canadian Institute for Cybersecurity. CICIDS2017 Dataset. 2017. Available online: https://www.unb.ca/cic/datasets/ids-2017.html (accessed on 30 March 2025).
- Sharafaldin, I.; Lashkari, A.H.; Ghorbani, A.A. Toward generating a new intrusion detection dataset and intrusion traffic characterization. ICISSp 2018, 1, 108–116. [Google Scholar]
- Khan, M.M.; Alkhathami, M. Anomaly detection in IoT-based healthcare: Machine learning for enhanced security. Sci. Rep. 2024, 14, 5872. [Google Scholar] [CrossRef] [PubMed]
- Khan, R.; Taj, S.; Ma, X.; Noor, A.; Zhu, H.; Khan, J.; Khan, Z.U.; Khan, S.U. Advanced federated ensemble internet of learning approach for cloud based medical healthcare monitoring system. Sci. Rep. 2024, 14, 26068. [Google Scholar] [CrossRef] [PubMed]
- Ghadi, Y.Y.; Mazhar, T.; Shah, S.F.A.; Haq, I.; Ahmad, W.; Ouahada, K.; Hamam, H. Integration of federated learning with IoT for smart cities applications, challenges, and solutions. PeerJ Comput. Sci. 2023, 9, e1657. [Google Scholar] [CrossRef]
- Priyadarshini, I. Anomaly detection of iot cyberattacks in smart cities using federated learning and split learning. Big Data Cogn. Comput. 2024, 8, 21. [Google Scholar] [CrossRef]
- Aljunaid, S.K.; Almheiri, S.J.; Dawood, H.; Khan, M.A. Secure and Transparent Banking: Explainable AI-Driven Federated Learning Model for Financial Fraud Detection. J. Risk Financ. Manag. 2025, 18, 179. [Google Scholar] [CrossRef]
- Arora, S.; Beams, A.; Chatzigiannis, P.; Meiser, S.; Patel, K.; Raghuraman, S.; Rindal, P.; Shah, H.; Wang, Y.; Wu, Y.; et al. Privacy-preserving financial anomaly detection via federated learning & multi-party computation. In Proceedings of the 2024 Annual Computer Security Applications Conference Workshops (ACSAC Workshops), Honolulu, HI, USA, 9–13 December 2024; pp. 270–279. [Google Scholar]
- Dritsas, E.; Trigka, M. Federated Learning for IoT: A Survey of Techniques, Challenges, and Applications. J. Sens. Actuator Netw. 2025, 14, 9. [Google Scholar] [CrossRef]
- Mohammadi, S.; Balador, A.; Sinaei, S.; Flammini, F. Balancing privacy and performance in federated learning: A systematic literature review on methods and metrics. J. Parallel Distrib. Comput. 2024, 192, 104918. [Google Scholar] [CrossRef]
- Himeur, Y.; Sayed, A.N.; Alsalemi, A.; Bensaali, F.; Amira, A. Edge AI for Internet of Energy: Challenges and perspectives. Internet Things 2024, 25, 101035. [Google Scholar] [CrossRef]
- Ramírez-Gordillo, T.; Maciá-Lillo, A.; Pujol, F.A.; García-D’Urso, N.; Azorín-López, J.; Mora, H. Decentralized Identity Management for Internet of Things (IoT) Devices Using IOTA Blockchain Technology. Future Internet 2025, 17, 49. [Google Scholar] [CrossRef]
- Agarkar, A.A.; Karyakarte, M.; Chavhan, G.; Patil, M.; Talware, R.; Kulkarni, L. Blockchain aware decentralized identity management and access control system. Meas. Sens. 2024, 31, 101032. [Google Scholar] [CrossRef]
- Kumar, M. Post-quantum cryptography Algorithm’s standardization and performance analysis. Array 2022, 15, 100242. [Google Scholar] [CrossRef]
- Amirkhanova, D.S.; Iavich, M.; Mamyrbayev, O. Lattice-Based Post-Quantum Public Key Encryption Scheme Using ElGamal’s Principles. Cryptography 2024, 8, 31. [Google Scholar] [CrossRef]
- Sibanda, I. The Rise of Quantum-Resistant Cryptography. IEEE Comput. Soc. 2024. Available online: https://www.computer.org/publications/tech-news/trends/quantum-resistant-cryptography/ (accessed on 1 July 2025).
- Alalhareth, M.; Hong, S.C. Enhancing the internet of medical things (IoMT) security with meta-learning: A performance-driven approach for ensemble intrusion detection systems. Sensors 2024, 24, 3519. [Google Scholar] [CrossRef]
- Rihan, S.D.A.; Anbar, M.; Alabsi, B.A. Meta-learner-based approach for detecting attacks on internet of things networks. Sensors 2023, 23, 8191. [Google Scholar] [CrossRef]
- Prantl, T.; Bauer, A.; Engel, S.; Horn, L.; Krupitzer, C.; Iffländer, L.; Kounev, S. Benchmarking of Secure Group Communication schemes with focus on IoT. Discov. Data 2024, 2, 5. [Google Scholar] [CrossRef]



| Reference | Privacy Techniques | Trade-Off Management | Model Training |
|---|---|---|---|
| Awosika et al. [10] | Federated Learning | Privacy Guarantees | Decentralized Model Training |
| Iacob et al. [11] | Differential Privacy | Privacy Guarantees | Federated Learning |
| Wei et al. [12] | Differential Privacy | Privacy Budget Allocation | Local Training |
| Anelli et al. [13] | Federated Learning | Accuracy Losses | Federated Learning |
| Proposed Method | Hierarchical integration | Energy-Efficient Privacy Optimization | Local Model Training |
| Attack Type | Accuracy (%) | Precision (%) | Recall (%) | F1-Score (%) |
|---|---|---|---|---|
| DDoS | 98.6 | 97.4 | 96.9 | 97.2 |
| Port Scanning | 97.2 | 95.8 | 96.1 | 96.0 |
| Malware Propagation | 98.9 | 98.1 | 97.8 | 97.9 |
| Metric | Value | Description |
|---|---|---|
| Average F1-Score (50% shared classes) | 94.6% | Model performance under class imbalance and limited data overlap |
| Matthews Correlation Coefficient (MCC) | 0.89 | Strong correlation between predicted and true labels |
| Inference Latency (per device) | 21 ms | Time required for local GRU model to process a new data sequence |
| Model Size (compressed) | 1.2 MB | Final GRU model size after quantization and pruning |
| Update Size (encrypted) | 2.4 MB | Homomorphically encrypted update per training round |
| Resilience to MIA (Privacy Test) | <15% success rate | Indicates high privacy protection under Membership Inference Attack |
| Metric | Centralized Approaches | Non-FL Decentralized Methods | Proposed Framework |
|---|---|---|---|
| Privacy Level | Low | Medium | High |
| Detection Accuracy | 92% | 94% | 98% |
| Energy Efficiency | Low | Medium | High |
| Framework | Accuracy | Energy (J) | Communication (MB) | Privacy Method |
|---|---|---|---|---|
| Baseline A | 96.5% | 270 | 110 | DP + HE |
| Baseline B | 95.2% | 310 | 125 | Differential Privacy |
| Baseline C | 94.0% | 320 | 130 | Homomorphic Encryption |
| Proposed | 98.2% | 200 | 85 | DP + HE + SMPC |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Rahmati, M.; Pagano, A. Federated Learning-Driven Cybersecurity Framework for IoT Networks with Privacy Preserving and Real-Time Threat Detection Capabilities. Informatics 2025, 12, 62. https://doi.org/10.3390/informatics12030062
Rahmati M, Pagano A. Federated Learning-Driven Cybersecurity Framework for IoT Networks with Privacy Preserving and Real-Time Threat Detection Capabilities. Informatics. 2025; 12(3):62. https://doi.org/10.3390/informatics12030062
Chicago/Turabian StyleRahmati, Milad, and Antonino Pagano. 2025. "Federated Learning-Driven Cybersecurity Framework for IoT Networks with Privacy Preserving and Real-Time Threat Detection Capabilities" Informatics 12, no. 3: 62. https://doi.org/10.3390/informatics12030062
APA StyleRahmati, M., & Pagano, A. (2025). Federated Learning-Driven Cybersecurity Framework for IoT Networks with Privacy Preserving and Real-Time Threat Detection Capabilities. Informatics, 12(3), 62. https://doi.org/10.3390/informatics12030062






