Do Patients’ Privacy Concerns Influence Their Intention toward Medical Image Exchange Consent in Taiwan?
Abstract
:1. Introduction
2. Methods
2.1. Methodology of the Study
- The proposed framework was based on prior research studies, most of which utilized a survey design. Furthermore, in this research, we wanted to examine if the model was suitable in the MIEC setting or not. The results of this study, whether they supported previous research or not, would contribute to cumulative knowledge in this field.
- Existing instruments from previous research studies could be adopted.
- The target population is not easy to control. As the dependent variable (intention to sign MIEC consents) varies from person to person, the analysis unit of this study was the individual.
2.2. Research Framework and Hypotheses
2.3. Questionnaire Design
2.4. Sampling
3. Results
3.1. Measurement Model Assessment
3.2. Reliability and Validity Analysis
3.3. Testing of Hypotheses
4. Conclusions
5. Recommendations
5.1. For Government
5.2. For Medical Care Service Providers and Patients
5.3. For Academia
5.4. Limitations
Author Contributions
Funding
Conflicts of Interest
Appendix A
| 1. Gender | 3. Education | ||
 | Male |  | Junior high or less |
 | Female |  | Senior high school |
 | College/University | ||
 | Graduate | ||
| 4. Imaging experiences | |||
| 2. Age (years) |  | No | |
 | Under 20 |  | Yes |
 | 20–29 | 5. Understand MIEC | |
 | 30–39 |  | No |
 | 40–49 |  | Yes |
 | 50–59 | 6. Ever Signed MIEC consent | |
 | 60–69 |  | No |
 | More than 70 |  | Yes |
| Questions | 1 | 2 | 3 | 4 | 5 | 6 | 7 |
|---|---|---|---|---|---|---|---|
| Collection | |||||||
| 1. It usually bothers me when my images information uploads to MIEC. | |||||||
| 2. When medical staff ask me for personal images information in MIEC, I sometimes think twice before providing it. | |||||||
| 3. It bothers me to upload personal images information to MIEC. | |||||||
| 4. I’m concerned that medical staff are collecting too much personal images information about me. | |||||||
| Unauthorized access | |||||||
| 1. Medical staff should devote more time and effort to preventing unauthorized access to personal images information. | |||||||
| 2. IEC that contain personal images information should be protected from unauthorized access –no matter how much it costs. | |||||||
| 3. Medical staff should take more steps to make sure that unauthorized people cannot access personal images information in their computers. | |||||||
| Errors | |||||||
| 1. All the personal images information in MIEC should be double-checked for accuracy—no matter how much this costs. | |||||||
| 2. Medical staff should take more steps to make sure that the personal images information in their files is accurate. | |||||||
| 3. Medical staff should have better procedure to correct errors in personal images information. | |||||||
| 4. Medical staff should devote more time and effort to verifying the accuracy of the personal images information in MIEC. | |||||||
| Secondary Use | |||||||
| 1. Medical staff should not use personal images information for any purpose unless it has been authorized by the individuals who provided the images information. | |||||||
| 2. When people give personal images information to medical staff for some reason, the medical staff should never use the information for any other reason. | |||||||
| 3. Medical staff should never sell the personal images information in MIEC to other medical staff. | |||||||
| 4. Medical staff should never share personal images information with other medical staff unless it has been authorized by the individuals who provided the images information. | |||||||
| Trust | |||||||
| 1. I generally trust other people. | |||||||
| 2. I generally have faith in humanity. | |||||||
| 3. I feel that people are generally reliable. | |||||||
| 4. I tend to count upon other people. | |||||||
| Intention to use MIEC | |||||||
| 1. I intend to use MIEC at every opportunity over the next year. | |||||||
| 2. I plan to increase my use of MIEC over the next year. | |||||||
References
- Sahama, T.; Simpson, L.; Lane, B. Security and Privacy in Ehealth: Is It Possible? Presented at the 2013 IEEE 15th International Conference on e-Health Networking, Applications and Services (Healthcom 2013), Lisbon, Portugal, 9–12 October 2013. [Google Scholar]
- Walker, D.M.; Johnson, T.; Ford, E.W.; Huerta, T.R. Trust Me, I’m a Doctor: Examining Changes in How Privacy Concerns Affect Patient Withholding Behavior. J. Med Internet Res. 2017, 19, e2. [Google Scholar] [CrossRef] [Green Version]
- Bender, J.L.; Cyr, A.B.; Arbuckle, L.; Ferris, L.E. Ethics and Privacy Implications of Using the Internet and Social Media to Recruit Participants for Health Research: A Privacy-by-Design Framework for Online Recruitment. J. Med Internet Res. 2017, 19, e104. [Google Scholar] [CrossRef]
- Li, Y.-C.J.; Yen, J.-C.; Chiu, W.-T.; Jian, W.-S.; Syed-Abdul, S.; Hsu, M.-H. Building a National Electronic Medical Record Exchange System–Experiences in Taiwan. Comput. Methods Programs Biomed. 2015, 121, 14–20. [Google Scholar] [CrossRef]
- Dimitropoulos, L.; Rizk, S. A State-Based Approach to Privacy and Security for Interoperable Health Information Exchange. Health Aff. 2009, 28, 428–434. [Google Scholar] [CrossRef]
- Park, S.C.; Finnell, J.T. Indianapolis Emergency Medical Service and the Indiana Network for Patient Care: Evaluating the Patient Match Algorithm. Presented at the AMIA Annual Symposium, Chicago, IL, USA, 3–7 November 2012. [Google Scholar]
- Adler-Milstein, J.; Bates, D.W.; Jha, A.K. Us Regional Health Information Organizations: Progress and Challenges. Health Aff. 2009, 28, 483–492. [Google Scholar] [CrossRef] [PubMed] [Green Version]
- Protti, D. Us Regional Health Information Organizations and the Nationwide Health Information Network: Any Lessons for Canadians? Healthc. Q. 2008, 11, 96–101. [Google Scholar] [PubMed]
- Maffei, R.; Burciago, D.; Dunn, K. Determining Business Models for Financial Sustainability in Regional Health Information Organizations (Rhios): A Review. Popul. Health Manag. 2009, 12, 273–278. [Google Scholar] [CrossRef] [PubMed]
- Jha, A.K.; Doolan, D.; Grandt, D.; Scott, T.; Bates, D.W. The Use of Health Information Technology in Seven Nations. Int. J. Med. Inform. 2008, 77, 848–854. [Google Scholar] [CrossRef] [PubMed]
- McGraw, D.; Dempsey, J.X.; Harris, L.; Goldman, J. Privacy as an Enabler, Not an Impediment: Building Trust into Health Information Exchange. Health Aff. 2009, 28, 416–427. [Google Scholar] [CrossRef] [PubMed]
- Birnbaum, D. Revisiting Public Health Informatics: Patient Privacy Concerns. Int. J. Health Gov. 2018, 23, 149–159. [Google Scholar] [CrossRef] [Green Version]
- Romanou, A. The Necessity of the Implementation of Privacy by Design in Sectors Where Data Protection Concerns Arise. Comput. Law Secur. Rev. 2018, 34, 99–110. [Google Scholar] [CrossRef]
- Entzeridou, E.; Markopoulou, E.; Mollaki, V. Public and Physician’s Expectations and Ethical Concerns About Electronic Health Record: Benefits Outweigh Risks except for Information Security. Int. J. Med. Inf. 2018, 110, 98–107. [Google Scholar] [CrossRef] [PubMed]
- Blobel, B.; López, D.; Gonzalez, C. Patient Privacy and Security Concerns on Big Data for Personalized Medicine. Health Technol. 2016, 6, 75–81. [Google Scholar] [CrossRef]
- Ghazi-asgar, M.; Peikari, H.; Ehteshami, A. Health Information Management: Psychological Factors Influencing Information Privacy Concerns in Psychiatric Hospitals. Bali Med. J. 2018, 7, 120. [Google Scholar] [CrossRef]
- Torous, J.; Wisniewski, H.; Liu, G.; Keshavan, M. Mental Health Mobile Phone App Usage, Concerns, and Benefits among Psychiatric Outpatients: Comparative Survey Study. JMIR Ment. Health 2018, 5, e11715. [Google Scholar] [CrossRef] [Green Version]
- McDonald, C. Protecting Patients in Health Information Exchange: A Defense of the Hipaa Privacy Rule. Health Aff. 2009, 28, 447–449. [Google Scholar] [CrossRef] [Green Version]
- Smith, H.J.; Milberg, S.J.; Burke, S.J. Information Privacy: Measuring Individuals’ Concerns About Organizational Practices. MIS Q. 1996, 20, 167–196. [Google Scholar] [CrossRef]
- Bellman, S.; Johnson, E.J.; Kobrin, S.J.; Lohse, G.L. International Differences in Information Privacy Concerns: A Global Survey of Consumers. Inf. Soc. 2004, 20, 313–324. [Google Scholar] [CrossRef]
- Earp, J.B.; Antón, A.I.; Aiman-Smith, L.; Stufflebeam, W.H. Examining Internet Privacy Policies within the Context of User Privacy Values. IEEE Trans. Eng. Manag. 2005, 52, 227–237. [Google Scholar] [CrossRef]
- Rose, E.A. An Examination of the Concern for Information Privacy in the New Zealand Regulatory Context. Inf. Manag. 2006, 43, 322–335. [Google Scholar] [CrossRef]
- Stewart, K.A.; Segars, A.H. An Empirical Examination of the Concern for Information Privacy Instrument. Inf. Syst. Res. 2002, 13, 36–49. [Google Scholar] [CrossRef]
- Milne, G.R.; Boza, M.E. Trust and Concern in Consumers’ Perceptions of Marketing Information Management Practices. J. Interact. Mark. 1999, 13, 5–24. [Google Scholar] [CrossRef]
- Rohm, A.J.; Milne, G.R. Just What the Doctor Ordered: The Role of Information Sensitivity and Trust in Reducing Medical Information Privacy Concern. J. Bus. Res. 2004, 57, 1000–1011. [Google Scholar] [CrossRef]
- Chellappa, R.K.; Sin, R.G. Personalization Versus Privacy: An Empirical Examination of the Online Consumer’s Dilemma. Inf. Technol. Manag. 2005, 6, 181–202. [Google Scholar] [CrossRef]
- Dinev, T.; Hart, P. Internet Privacy Concerns and Their Antecedents-Measurement Validity and a Regression Model. Behav. Inf. Technol. 2004, 23, 413–422. [Google Scholar] [CrossRef]
- Stone, E.F.; Gueutal, H.G.; Gardner, D.G.; McClure, S. A Field Experiment Comparing Information-Privacy Values, Beliefs, and Attitudes across Several Types of Organizations. J. Appl. Psychol. 1983, 68, 459. [Google Scholar] [CrossRef]
- Zhang, X.; Liu, S.; Chen, X.; Wang, L.; Gao, B.; Zhu, Q. Health Information Privacy Concerns, Antecedents, and Information Disclosure Intention in Online Health Communities. Inf. Manag. 2018, 55, 482–493. [Google Scholar] [CrossRef]
- Mayer, R.C.; Davis, J.H.; Schoorman, F.D. An Integrative Model of Organizational Trust. Acad. Manag. Rev. 1995, 20, 709–734. [Google Scholar] [CrossRef]
- Gefen, D.; Karahanna, E.; Straub, D.W. Trust and Tam in Online Shopping: An Integrated Model. MIS Q. 2003, 27, 51–90. [Google Scholar] [CrossRef]
- Tabachnick, B.G.; Fidell, L.S.; Ullman, J.B. Using Multivariate Statistics; Pearson: Boston, MA, USA, 2007; Volume 5. [Google Scholar]
- Cooper, D.R.; Schindler, P.S.; Sun, J. Business Research Methods; McGraw-Hill Irwin: New York, NY, USA, 2006; Volume 9. [Google Scholar]
- Hair, J.F., Jr.; Page, M.; Brunsveld, N. Essentials of Business Research Methods; Routledge: New York, NY, USA, 2019. [Google Scholar]
- Hair, J.F.; Black, W.C.; Babin, B.J.; Anderson, R.E. Multivariate Data Analysis: Pearson New International Edition; Pearson Higher Education: New York, NY, USA, 2013. [Google Scholar]
- Weiming, T.U. Confucianism: Humanism and the Enlightenment. In Encyclopedia of Chinese Philosophy; Taylor & Francis Group: Milton Park, UK, 2013. [Google Scholar]
- Szasz, T.S.; Hollender, M.H. A Contribution to the Philosophy of Medicine: The Basic Models of the Doctor-Patient Relationship. AMA Arch. Intern. Med. 1956, 97, 585–592. [Google Scholar] [CrossRef]

| Variable | Description | Frequency | % | F-Value | |||||
|---|---|---|---|---|---|---|---|---|---|
| C | U | E | S | T | I | ||||
| Gender | Male | 158 | 48.9 | 7.910 | 0.979 | 0.328 | 0.120 | 1.189 | 7.178 |
| Female | 165 | 51.1 | |||||||
| Age Group | Younger than 20 | 15 | 4.6 | 2.780 | 0.731 | 1.520 | 2.522 | 3.234 | 4.830 * |
| 20–29 | 111 | 34.4 | |||||||
| 30–39 | 100 | 31.0 | |||||||
| 40–49 | 54 | 16.7 | |||||||
| 50–59 | 22 | 6.8 | |||||||
| 60–69 | 8 | 2.5 | |||||||
| 70 or older | 13 | 4.0 | |||||||
| Education | Junior High or below | 44 | 13.6 | 3.377 * | 3.736 * | 4.531 * | 4.732 * | 6.336 * | 3.678 * |
| Senior High | 53 | 16.4 | |||||||
| University/College | 119 | 36.8 | |||||||
| Masters or above | 107 | 33.1 | |||||||
| Medical Image Experience | No | 129 | 39.9 | 2.170 | 0.609 * | 7.021 * | 9.423 * | 0.459 | 1.151 * |
| Yes | 194 | 60.1 | |||||||
| Knew of MIEC in advance | No | 191 | 59.1 | 0.042 | 0.357 | 2.806 | 1.438 | 1.444 | 1.676 |
| Yes | 132 | 40.9 | |||||||
| Ever signed consent for MIEC | No | 292 | 90.4 | 0.827 * | 0.567 | 0.069 | 0.690 * | 0.553 | 0.954 |
| Yes | 31 | 9.6 | |||||||
| Concern for Information Privacy Items (1, Strongly Agree; 4, So-So; 7, Strongly Disagree) | Mean | S.D. |
|---|---|---|
| Average collection | 3.91 | 1.26 |
| Average unauthorized access | 2.44 | 1.23 |
| Average errors | 2.41 | 1.23 |
| Average secondary use | 2.21 | 1.22 |
| Average CFIP | 2.75 | 1.01 |
| Constructs | Cronbach’s α |
|---|---|
| Collection | 0.861 |
| Unauthorized Access | 0.813 |
| Errors | 0.896 |
| Secondary Use | 0.879 |
| Trust | 0.730 |
| Intention to Sign MIEC Consents | 0.909 |
| Factor Analysis Items | Value | |
|---|---|---|
| Kaiser–Meyer–Olkin Measure of Sampling Adequacy | 0.912 | |
| Bartlett’s Test of Sphericity | Approx. Chi-Square | 3237.004 |
| df | 105 | |
| Sig. | 0.000 * | |
| Component | Component | |||
|---|---|---|---|---|
| 1 | 2 | 1 | 2 | |
| C_1 | 0.813 | 0.860 | ||
| C_2 | 0.701 | 0.758 | ||
| C_3 | 0.791 | 0.841 | ||
| C_4 | 0.836 | 0.874 | ||
| U_1 | 0.697 | 0.653 | ||
| U_2 | 0.791 | 0.779 | ||
| U_3 | 0.814 | 0.813 | ||
| E_1 | 0.758 | 0.779 | ||
| E_2 | 0.831 | 0.837 | ||
| E_3 | 0.835 | 0.841 | ||
| E_4 | 0.790 | 0.801 | ||
| S_1 | 0.750 | 0.769 | ||
| S_2 | 0.809 | 0.819 | ||
| S_3 | 0.798 | 0.797 | ||
| S_4 | 0.745 | 0.745 | ||
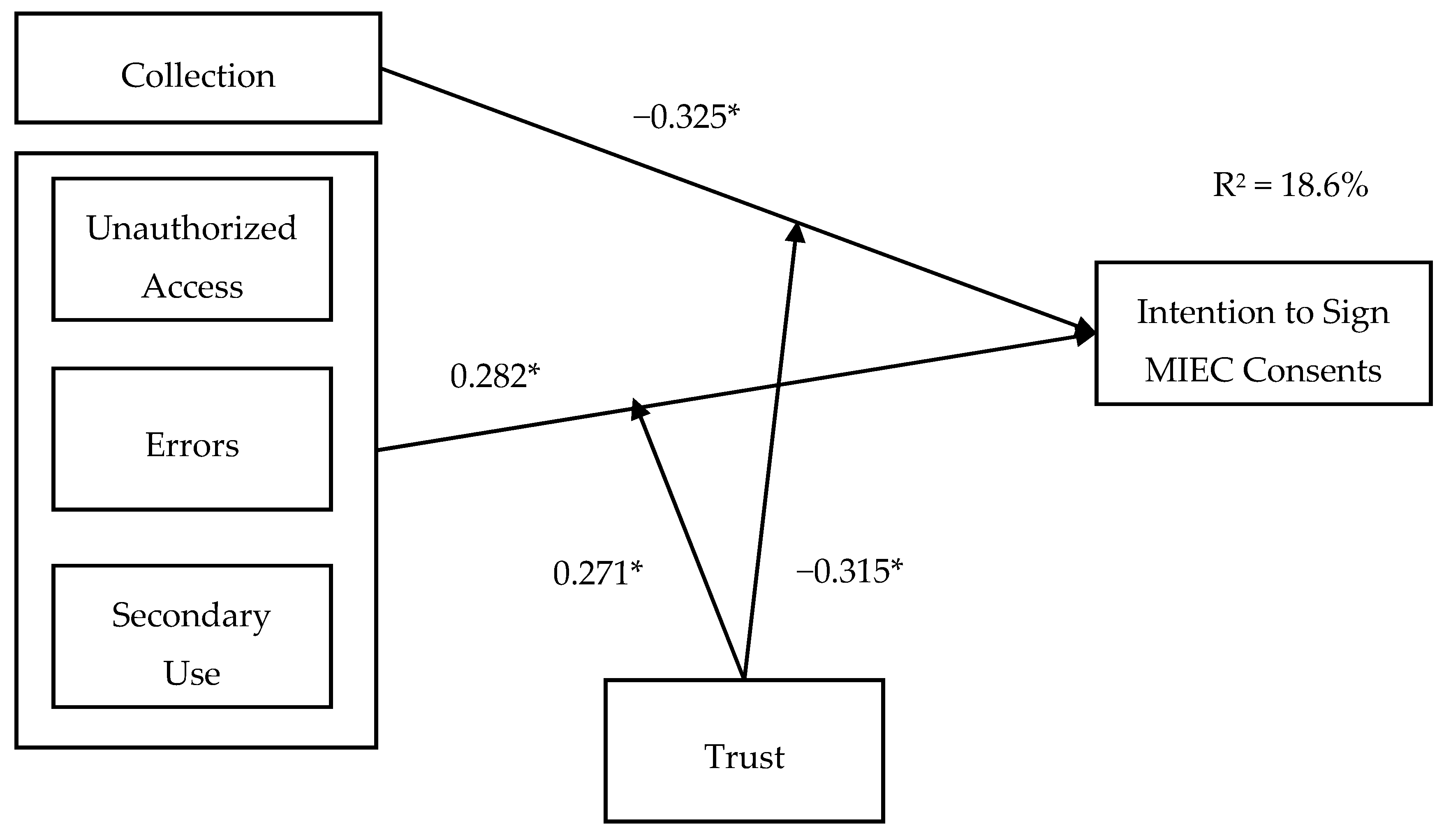
| Title | Relationship | Std. Beta Coefficient | t-Value (Sig. t) | R2 Changed (Sig F) | Total of R2 | Hypothesis Confirmed? |
|---|---|---|---|---|---|---|
| H1 | CFIP→I | 0.074 | 1.322 | 0.005 | 0.005 | No |
| H2 | +Trust | 0.185 | 3.375 * (0.001) | 0.034 * (0.001) | 0.040 | Yes (pure Moderator) |
| +Trust*CFIP | −0.250 | −1.333 (0.184) | 0.005 (0.184) | 0.045 | ||
| H1a | C→I | −0.262 | −4.871 * | 0.069 | 0.069 | Yes |
| H2a | +Trust | 0.174 | 3.269 * (0.001) | 0.030 * (0.001) | 0.099 | Yes (pure Moderator) |
| +Trust*C | −0.231 | −0.231 (0.181) | 0.005 (0.181) | 0.104 | ||
| H1b | U→I | 0.157 | 2.856 * | 0.025 | 0.025 | Yes |
| H2b | +Trust | 0.185 | 3.412 * (0.001) | 0.034 * (0.001) | 0.059 | Yes (pure Moderator) |
| +Trust*U | −0.222 | −1.657 (0.099) | 0.008 (0.099) | 0.067 | ||
| H1c | E→I | 0.233 | 4.289 * | 0.054 | 0.054 | Yes |
| H2c | +Trust | 0.169 | 3.142 * (0.002) | 0.028 * (0.002) | 0.083 | Yes (pure Moderator) |
| +Trust*E | −0.199 | −1.381 (0.168) | 0.005 (0.168) | 0.088 | ||
| H1d | S→I | 0.178 | 3.234 | 0.032 | 0.032 | Yes |
| H2d | +Trust | 0.177 | 3.271 * (0.001) | 0.031 * (0.001) | 0.063 | Yes (pure Moderator) |
| +Trust*S | −0.257 | −1.922 (0.055) | 0.011 (0.055) | 0.074 |
© 2020 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Tseng, H.-T.; Hung, W.-F.; Hwang, H.-G.; Chang, I.-C. Do Patients’ Privacy Concerns Influence Their Intention toward Medical Image Exchange Consent in Taiwan? Healthcare 2020, 8, 14. https://doi.org/10.3390/healthcare8010014
Tseng H-T, Hung W-F, Hwang H-G, Chang I-C. Do Patients’ Privacy Concerns Influence Their Intention toward Medical Image Exchange Consent in Taiwan? Healthcare. 2020; 8(1):14. https://doi.org/10.3390/healthcare8010014
Chicago/Turabian StyleTseng, Hsiao-Ting, Won-Fu Hung, Hsin-Ginn Hwang, and I-Chiu Chang. 2020. "Do Patients’ Privacy Concerns Influence Their Intention toward Medical Image Exchange Consent in Taiwan?" Healthcare 8, no. 1: 14. https://doi.org/10.3390/healthcare8010014
APA StyleTseng, H.-T., Hung, W.-F., Hwang, H.-G., & Chang, I.-C. (2020). Do Patients’ Privacy Concerns Influence Their Intention toward Medical Image Exchange Consent in Taiwan? Healthcare, 8(1), 14. https://doi.org/10.3390/healthcare8010014





