DeepBlockShield: Blockchain Agent-Based Secured Clinical Data Management Model from the Deep Web Environment
Abstract
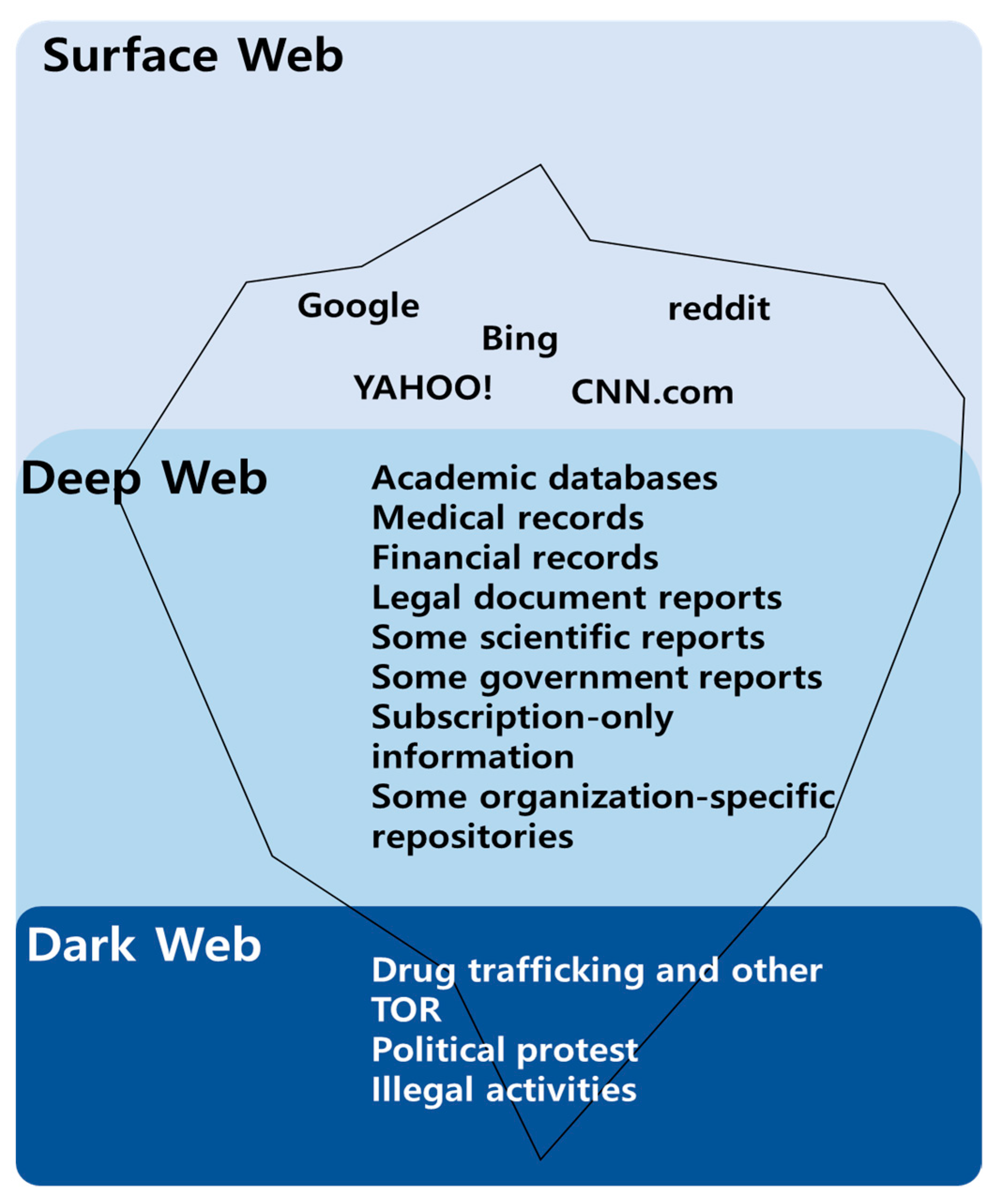
:1. Introduction
2. Related Work
3. Blockchain Agent Based Secured Clinical Data Management Model
3.1. Separated Access Control Module for Data Security
3.2. Authorization Management Module for Role-Based Smart Contract Configuration
- Researcher;The researcher belongs to the hospital. Through the agent, clinical data analysis can be requested based on CDM catalog data. Furthermore, by entering the data analysis request code, the researcher enters information on the analysis method desired by the researcher. Finally, the researcher enters the study period for how long the data will be used.
- Admin;The admin manages the network and assigns a unique ID to hospitals that have joined the blockchain network through an agent. Research can be approved, modified, or canceled based on the information requested by the researcher. In addition, the information analyzed by the data scientist is finally confirmed and the analysis results are provided to the user through the agent.
- Data scientist;Data scientists have direct access to medical data and check and analyze the data the researcher wants based on the research request information approved by the admin.
3.3. Management of Smart Contract-Based Clinical Data Analysis Request and Role-Based Feature Control
| Algorithm 1. Pseudo-Code of User Validation |
| Input: Previous Hash, Time Stamp, User Information |
| Output: Granting Admin or Research authority depending on whether or not to subscribe to the service |
| U = userType |
| A = AdminAccount |
| B = ResearcherAccount |
| function getUserExist(U) public constant returns(bool) |
| if U is Admin, then return A |
| if A is not Null, then exist is true |
| else if U is Researcher, return B |
| if B is not Null, then exist is true |
| return exist; |
4. Experimental Results
4.1. Experiment Setup
4.2. Contract Execution
4.3. Blockchain-Based Information Distribution Management Delay Time Analysis
4.4. Discussions for Security Review with Blockchain Agent
- ConfidentialityIn authority nodes, information is requested to the database configured in an off-chain format, using the data keys requested through user validation. Then, the results are verified with the ID given by the authority node. Then, the encrypted analysis results of the requested data can be checked through the web interface. If data are hacked, encrypted results are only leaked. Unless the encrypted private key granted through the agent is available, analysis results cannot be read. In addition, they are deleted from the database after the elapse of a certain period of time, enhancing confidentiality.
- AvailabilityThe proposed model stores user information in the agent and blockchain as well as through the web interface, allowing authorized members only to access it. In fact, an unauthorized user is not permitted to join the agent and blockchain. In the proposed model, information sharing on a closed network is performed through the blockchain. In the blockchain, validation nodes in which identity is guaranteed through the PoA consensus algorithm are only authorized to create and validate blocks. Even if malicious users attack the services, data cannot be forged or modified because they have no authority of data validation. Therefore, actual network damage is minor. In all nodes, furthermore, authorized validators are only able to validate and extend transactions in a quick and easy fashion.
- Non-repudiationIn the proposed model, concerning the use of clinical data, related information (who, when, what, how) is stored in blocks when a transaction is requested. Then, a validator checks the transaction, and the transaction information is shared through the ledger owned by the network members. In other words, the history of access to personal information is clarified, allowing the information provider, hospitals, or governmental institutes to check the details.
5. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Conflicts of Interest
References
- Bilogrevic, I. A machine-learning based approach to privacy-aware information-sharing in mobile social networks. Pervasive Mob. Comput. 2016, 25, 125–142. [Google Scholar] [CrossRef] [Green Version]
- Kim, M.; Sang, O.P. Group affinity based social trust model for an intelligent movie recommender system. Multimed. Tools Appl. 2013, 64, 505–516. [Google Scholar] [CrossRef]
- Kim, M. Identity management-based social trust model for mediating information sharing and privacy enhancement. Secur. Commun. Netw. 2012, 5, 887–897. [Google Scholar] [CrossRef]
- Alba, A. Accessing the deep web: When good ideas go bad. In Proceedings of the Companion to the 23rd ACM SIGPLAN Conference on Object-Oriented Programming Systems Languages and Applications, Nashville, TN, USA, 19–23 October 2008; pp. 815–818. [Google Scholar]
- Bergman, M.K. White paper: The deep web: Surfacing hidden value. J. Electron. Publ. 2001, 7. [Google Scholar] [CrossRef]
- He, B. Accessing the deep web. Commun. ACM 2007, 50, 94–101. [Google Scholar] [CrossRef]
- Hu, V.C. Attribute-based access control. Computer 2015, 48, 85–88. [Google Scholar] [CrossRef]
- Kim, Y.-Y.; Seung-soo, S. A study on reliable electronic medical record systems. J. Digit. Converg. 2012, 10, 193–200. [Google Scholar]
- Barcelo, J. User Privacy in the Public Bitcoin Blockchain. 2014. Available online: http://www.dtic.upf.edu/jbarcelo/papers/20140704UserPrivacyinthePublicBitcoinBlockchain/paper.pdf (accessed on 9 May 2016).
- De Angelis, S. Assessing security and performances of consensus algorithms for permissioned blockchains. arXiv 2018, arXiv:1805.03490. [Google Scholar]
- Eyal, I. Bitcoin-ng: A scalable blockchain protocol. In Proceedings of the 13th {USENIX} Symposium on Networked Systems Design and Implementation ({NSDI} 16), Santa Clara, CA, USA, 16–18 March 2016. [Google Scholar]
- Mercer, R. Privacy on the blockchain: Unique ring signatures. arXiv 2016, arXiv:1612.01188. [Google Scholar]
- Buterin, V. A Next-Generation Smart Contract and Decentralized Application Platform. White Paper 3.37 (2014). Available online: https://ethereum.org/en/whitepaper/ (accessed on 12 November 2020).
- Guadamuz, A.; Christopher, M. Blockchains and Bitcoin: Regulatory responses to cryptocurrencies. First Monday 2015, 20. [Google Scholar] [CrossRef] [Green Version]
- Kosba, A. Hawk: The blockchain model of cryptography and privacy-preserving smart contracts. In Proceedings of the 2016 IEEE Symposium on Security and Privacy (SP), San Jose, CA, USA, 22–26 May 2016; pp. 839–858. [Google Scholar]
- Zyskind, G.; Oz, N. Decentralizing privacy: Using blockchain to protect personal data. In Proceedings of the 2015 IEEE Security and Privacy Workshops, San Jose, CA, USA, 21–22 May 2015. [Google Scholar]
- Fatokun, T.; Nag, A.; Sharma, S. Towards a Blockchain Assisted Patient Owned System for Electronic Health Records. Electronics 2021, 10, 580. [Google Scholar] [CrossRef]
- Jabarulla, M.Y.; Lee, H.-N. Blockchain-Based Distributed Patient-Centric Image Management System. Appl. Sci. 2021, 11, 196. [Google Scholar] [CrossRef]
- Wehbe, Y.; Zaabi, M.A.; Svetinovic, D. Blockchain AI Framework for Healthcare Records Management: Constrained Goal Model. In Proceedings of the 2018 26th Telecommunications Forum (TELFOR), Belgrade, Serbia, 20—21 November 2018; pp. 420–425. [Google Scholar]
- Kaaniche, N.; Maryline, L. A blockchain-based data usage auditing architecture with enhanced privacy and availability. In Proceedings of the 2017 IEEE 16th International Symposium on Network Computing and Applications (NCA), Cambridge, MA, USA, 30 October–1 November 2017. [Google Scholar]
- Maymounkov, P.; David, M. Kademlia: A peer-to-peer information system based on the xor metric. In International Workshop on Peer-to-Peer Systems; Springer: Berlin/Heidelberg, Germany, 2002. [Google Scholar]
- Passant, A.; Laublet, P.; Breslin, J.G.; Decker, S. A uri is worth a thousand tags: From tagging to linked data with moat. Int. J. Semant. Web Inf. Syst. (IJSWIS) 2009, 5, 71–94. [Google Scholar] [CrossRef]
- Teutsch, J.; Christian, R. A scalable verification solution for blockchains. arXiv 2019, arXiv:1908.04756. [Google Scholar]
- Liang, X. Provchain: A blockchain-based data provenance architecture in cloud environment with enhanced privacy and availability. In Proceedings of the 2017 17th IEEE/ACM International Symposium on Cluster, Cloud and Grid Computing (CCGRID), Madrid, Spain, 14–17 May 2017. [Google Scholar]
- Rantos, K.; Drosatos, G.; Demertzis, K.; Ilioudis, C.; Papanikolaou, A. Blockchain-based Consents Management for Personal Data Processing in the IoT Ecosystem. ICETE 2018, 2, 572–577. [Google Scholar]









| Purpose | List | Summary |
|---|---|---|
| Privacy Protection | [12,15,16,17,18,19] | Personal data management platform focused on personal information protection |
| Access Control | [18,19,20,21,22,23] | Address data protection and privacy access control issues |
| Blockchain Architecture | [15,17,18,24,25] | Guaranteed data integrity and non-repudiation through public verification based on blockchain technology |
| Category | Information | Description |
|---|---|---|
| Common | Previous Hash | The hash value of the block positioned right before the blockchain. |
| Time Stamp | Stores data at the time when a contract is generated, and access permission is approved. | |
| Research ID | Allocates a unique ID on the researcher joining a blockchain network. | |
| Researcher | Research Period | Stores a period on the researcher’s request information. |
| Target clinical data | Saves the diagnosis code. | |
| Variable | Saves a data variable name requested by the researcher based on the CDM catalogue data. | |
| Free-Text | Stores information on analysis methods by supporting a composite data type, e.g., data analysis request code, other information being generated at analysis request. | |
| Admin | Approval Authority | Allocates a unique ID on the hospitals joining a blockchain network. Expresses information in the institutions holding information on data field names. Allocates institution IDs in sequence when joining a network. |
| Analysis Results | A URL revealing analysis results. An access to the site prohibited after an elapse of certain time even though information is leaked. |
| Category | Description |
|---|---|
| A_ID | Issued through authentication when first joining the network. |
| Block creation and authentication permission. | |
| Creates a transaction using A_ID. | |
| Ledger | All authorities share the same contents. |
| History of smart contracts related to the use of personal information by all nodes. | |
| Database | Stores information for database connection. |
| ID and authentication key to access DB provided by institutions | |
| Smart Contract | The management and provision of personal information through smart contract |
| Creates new smart contracts as needed |
| Category | Description |
|---|---|
| U_ID | Issued through personal information authentication when joining the network |
| Blockchain registration and identifier role when sending personal information. | |
| Signing with U_ID when requesting smart contract privacy. | |
| R.I | The R.I contains the researcher information in Table 2 requested by the user |
| Enters the variable name requested by using the variable used. | |
| Data analysis request code, other information generated when requesting analysis | |
| Smart Contract | The ability to manage personal information |
| Registration, correction, reading, deletion |
| Category | Description | Input | Output |
|---|---|---|---|
| Request | Registers clinical data to be requested | U_ID, time stamp, Catalog, organization information, Researcher information | Request information |
| View | Views requested information | U_ID, time stamp | Catalog information requested |
| Modify | Information correction | U_ID, time stamp, Catalog | Modified information |
| Cancellation | Cancels analysis request | U_ID, time stamp | Canceled history information |
| Category | Description | Input | Output |
|---|---|---|---|
| Approve | Approval of analysis request | A_ID, time stamp, Catalog, organization information, Researcher information | Requested analysis result information |
| Delete | Deleted requested information | A_ID, time stamp | Deleted history information |
| Re-request | Cancels analysis request | A_ID, time stamp | Catalog data re-request information |
| Preferences | Content |
|---|---|
| OS | Ubuntu 16.04 |
| GO | Go1.12.9 |
| RAM | 8GB |
| Geth | 1.9.3-stable |
| DB | PostgreSQL |
| Node.js | 10.16.3 |
| Block Generation Cycle (ms) | 50 | 100 | 250 | 500 | 1000 | 2000 |
|---|---|---|---|---|---|---|
| TPS | 289 | 294 | 275 | 288 | 284 | 291 |
| Latency(sec) | 0.30 | 0331 | 0.420 | 0.612 | 0.802 | 0.89 |
| Block Size (MB) | Network Delay (s) |
|---|---|
| 0.1 | 2 |
| 0.5 | 6 |
| 1 | 11 |
| 4 | 59 |
| 8 | 108 |
| Consensus | TPS | Block Generation Cycle | Confirmation Frequency | Confirmation Time (sec) | |
|---|---|---|---|---|---|
| EOS | DPoS | 1,000,000 | 3 | 15 | 45 |
| Bitshare | DPoS | 100,000 | 3 | 15 | 45 |
| Neo | dBFT | 10,000 | 15–20 | 1 | 15–20 |
| Ethereum | PoW | 15 | 14 | 12 | 180 |
| Bitcoin | PoW | 7 | 600 | 6 | 3600 |
| Proposed | PoA | 300 | 5 | 2 | 11 |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2021 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Kim, J.; Kim, M. DeepBlockShield: Blockchain Agent-Based Secured Clinical Data Management Model from the Deep Web Environment. Mathematics 2021, 9, 1069. https://doi.org/10.3390/math9091069
Kim J, Kim M. DeepBlockShield: Blockchain Agent-Based Secured Clinical Data Management Model from the Deep Web Environment. Mathematics. 2021; 9(9):1069. https://doi.org/10.3390/math9091069
Chicago/Turabian StyleKim, Junho, and Mucheol Kim. 2021. "DeepBlockShield: Blockchain Agent-Based Secured Clinical Data Management Model from the Deep Web Environment" Mathematics 9, no. 9: 1069. https://doi.org/10.3390/math9091069
APA StyleKim, J., & Kim, M. (2021). DeepBlockShield: Blockchain Agent-Based Secured Clinical Data Management Model from the Deep Web Environment. Mathematics, 9(9), 1069. https://doi.org/10.3390/math9091069






