Abstract
With the increasing number of users and the emergence of different types of network services, a multi-server architecture has emerged in recent years. In order to ensure the secure communication of Internet participants in an open network environment, the authentication and key agreement protocol for multi-server architectures were proposed in the past. In 2018, Chatterjee et al. put forward a lightweight three-factor authentication and key agreement protocol for a multi-server environment, and they claimed that all known security features with satisfactory performance could be realized in their protocol. However, it is found that their scheme is vulnerable to user impersonation attacks and cannot achieve user un-traceability and three-factor security through our cryptanalysis. In order to solve these shortcomings, we propose a new lightweight and anonymous three-factor authentication scheme for the multi-server environment in this article. Furthermore, the proposed protocol is proved to be AKE secure theoretically, and we use BAN-logic to prove that our protocol realizes mutual authentication between communication participants. Finally, we show that our proposed scheme is practical and efficient through the comparison of security features and performance.
1. Introduction
In the past two decades, people’s lives have changed significantly because of the development of the Internet. People benefit from a variety of Internet services anytime and anywhere, such as telemedicine services, online shopping, online meetings, online games, and so on. Online life has become the mainstream mode of life, and the virtual network has changed the world [1,2]. With the continuous growth of the online network service business, security and privacy protection has become one of the most important challenges restricting its further development [3,4].
Authentication key agreement protocol is an effective security protocol to realize communication security in a client-server architecture. It can realize mutual authentication between users and servers, ensure that only legitimate users can access the server. At the same time, it can also effectively resist server spoofing attacks. When the user and the server complete mutual authentication, the two sides will negotiate to get their session key, which is used to ensure the security of their future communication. Moreover, the session key is obtained by negotiation between the two parties, and both parties have the same contribution to the generation of the session key, which enhances the security of the session key.
In the traditional single-server network environment, there is a service provider that provides network services for many users. When users access network services, they need to provide legal user identity and authentication factors (passwords, smart cards, biometrics). However, with the strong demand for more types of network services, users need to prepare multiple sets of user identity and authentication factors to register multiple single server network systems in order to access different single server network systems. Obviously, this has caused great inconvenience. If users set the same authentication factor for different systems, when the user password of a system is leaked, it will also affect the security of other systems, which has great security risks. On the other hand, each network service system needs an authentication server to complete the user registration operation, which causes a serious waste of resources.
In order to solve the above drawbacks, the authentication key agreement protocol for a multi-server environment arises at the historic moment. Users can use the same set of identity and authentication factors to complete mutual authentication with different servers in the system so as to obtain the corresponding network services. Generally, the registration center RC needs to complete the initialization of the system. At the same time, it is responsible for the registration of users and service providers into the system and distributes the secret information related to the registrants when the registration is completed. When the registered users want to access the network services, they need to authenticate with the server and establish their session key after the authentication to ensure their future network communication security [5]. The network model of the multi-server environment is shown in Figure 1.

Figure 1.
Network model of multi-server environment.
In 2001, Li et al. [6] proposed the first authentication protocol in a multi-server environment. However, Lin et al. [7] pointed out that the performance of the protocol is poor due to the use of the neural network. Meanwhile, to improve the performance of the protocol, Lin et al. designed an authentication protocol based on a discrete logarithm problem [7]. Unfortunately, their scheme was soon found unable to resist the attack of fake users [8]. At the same time, for the sake of improving the performance, many authentication protocols based on symmetric cryptography primitives [9,10,11,12,13,14,15] have been proposed.
Although these protocols use lightweight symmetric cryptography primitives and their performance has been improved, it is difficult for these protocols to achieve strong security attributes, such as perfect forward secrecy. To ensure the security and practicability of the protocol, researchers designed an authentication protocol based on Elliptic Curve Cryptography in a multi-server environment. In 2013, Yoon and Yoo proposed a three-factor authentication protocol based on elliptic curve cryptography [16]. However, the protocol is not secure; malicious users can fake the identity of other users to obtain network services [17]. Subsequently, He and Wang put forward an improved protocol [18] based on Yoon’s protocol [16], but Odelu et al. [19] pointed out that the improved protocol could not achieve user anonymity. In 2015, Tsai proposed a new authentication protocol for multi-server environments [20] and claimed that their protocol could achieve strong security. However, reference [21] claimed that the protocol could not resist server spoofing attacks. Since 2017, Kumari et al. [22] and Wu et al. [23] have proposed relevant authentication protocols for multi-server environments. However, some security problems were found in the proposed scheme by Feng et al. [24] and Wang et al. [25], respectively. Kumari et al.’s scheme [22] has weak user un-traceability and is vulnerable to man-in-the-middle attacks. Wu et al.’s scheme [23] is vulnerable to smart card stolen attacks and temporary information leakage attacks. Based on the previous works, the improved schemes enhance the security and performance step by step. For example, Haq et al. [26] put forward a new, improved protocol based on the work of Ying-Nayak et al. [27] and Kumar-Om et al. [28] in 2021. In recent years, as an effective security mechanism to ensure network security, the authentication protocol in multi-server environments has been paid attention to by scholars, and the related protocols [29] have been proposed one after another. In the research process of authentication and key agreement protocol, these schemes not only need to improve the security (such as introducing biological information as the security factor) but also should have better performance to adapt to the more practical environment, such as wireless sensor network, body area network, and so on.
Through the review of the authentication schemes above, we find that researchers are easy to ignore the user un-traceability and N-factor security of their protocol, and many protocols are also vulnerable to user impersonation attacks. For instance, Chatterjee et al. proposed a three-factor authentication and key agreement protocol based on an extended chaotic map for the multi-server environment in 2018 [30] and claimed that the protocol could achieve all known security features with satisfactory performance. However, it is found that their scheme is vulnerable to user impersonation attacks and cannot achieve user un-traceability and three-factor security through our cryptanalysis.
Based on our analysis of the above protocols, we propose three basic design principles of authentication and key agreement protocol for multi-server environments in this study:
(1) The authentication and key agreement protocol with high-level anonymity cannot be realized only by using symmetric cryptography (such as hash function and XOR operation). In other words, public key technology is a necessary condition to realize user anonymity.
(2) In order to ensure the n-factor security of the authentication protocol, the local verification of the smart card cannot be the deterministic verification method, and the fuzzy authentication technology should be introduced to avoid the offline password guessing attacks initiated by the adversary.
(3) In the login and authentication phase, the requester has a complete set of legal ID, password, smart card, and biological information, which is the necessary condition to generate legal login request information. Only in this way can we ensure the correctness of users’ identity and resist the user impersonation attacks.
Contributions
Our crucial contributions are as follows.
(1) We review and analyze Chatterjee et al.’s three-factor authentication scheme for multi-server environments. Further, we show that their scheme is vulnerable to user impersonation attacks and cannot achieve user un-traceability and three-factor security.
(2) We present a new lightweight anonymous three-factor authentication scheme with perfect forward secrecy for multi-server environments. Our scheme uses an extended chaotic map and achieves strong security.
(3) The proposed protocol is proved to be AKE secure theoretically, and we use BAN-logic to prove that our protocol realizes mutual authentication between communication participants
(4) Through the comparison of security features and performance, it can be found that our proposed scheme is excellent and practical.
2. Preliminaries
2.1. Discrete Logarithm
Given a finite cyclic group G1 and its generator , there is a unique integer x such that . xis the discrete logarithm of a, which is recorded as .
Discrete logarithm problem (DLP): Given a finite cyclic group G1 whose generator is and an element , DLP is to find the integer x such that .
Computational Diffie–Hellman problem (CDHP): Given a finite cyclic group G1 whose generator is and two elements , CDHP is to calculate the value of .
DLP and CDHP are known mathematical problems, which are not computationally feasible; that is, they are not solvable in polynomial time. They are often used in the construction and design of public-key cryptography.
2.2. Chebyshev Chaotic Map
Chebyshev chaotic map satisfies the following iterative relation: , where , , , , . Chebyshev chaotic map has semi-group property, i.e., .
In 2008, Zhang et al. [31] extended the domain of Chebyshev chaotic map to . The extended Chebyshev chaotic map still has the semi-group property, namely , where , , , , and p is a large prime number.
Chaotic map discrete logarithm problem (CMDLP): Given a Chebyshev chaotic map and two random variables: x and , CMDLP is to calculate the value of r.
Computational chaotic maps Diffie–Hellman Problem (CMCDHP): Given a Chebyshev chaotic map and , CMCDHP is to calculate the value of .
2.3. Adversarial Model
Due to the openness of the Internet, the attacker can easily control the information spread in the public channel, tamper, replay, block the information, and then launch a possible malicious attack, as shown in Figure 2. In this paper, the adversary ’s capabilities in a multi-server environment are set as shown in Table 1.
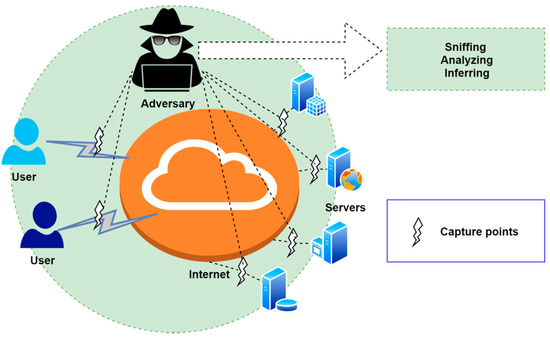
Figure 2.
Security threats.

Table 1.
Attackers’ capabilities.
3. Review of Chatterjee et al.’s Scheme
In the highly cited paper published by Santanu Chatterjee et al., an authentication protocol based on an extended Chebyshev chaotic map for multi-server environments was proposed in 2016 [30]. This section will take Chatterjee’s protocol as an example to analyze and point out the security defects of this kind of authentication protocol.
Chatterjee et al.’s scheme mainly consists of the following phases: system setup phase, user registration phase, server registration phase, login and authentication phase, user password, and biometric update phase. Table 2 lists the symbols used in their scheme.

Table 2.
Notations in Chatterjee et al.’s scheme.
The detailed description of the scheme is as follows:
3.1. System Setup Phase
Step 1: The Registration Center RC randomly selects and from .
Step 2: RC selects a secure hash function , a biological hash function , a Chebyshev polynomial , and a pair of symmetric encryption/decryption algorithms . Then, will be passed onto the public.
3.2. Server Registration Phase
Step 1: The server Sj sends its identity to RC through a secure channel.
Step 2: After receiving the registration information, RC randomly selects xj, calculates , , and sends back to Sj through the secure channel.
3.3. User Registration Setup Phase
Step 1: The user Ui selects his identity , password PWi and enters his biological information Bi. Next, Ui obtains the current timestamp Ti, generates a random number Ri to calculate , , , , , and transmits the registration information to RC through the secure channel.
Step 2: After receiving the registration request from Ui, RC randomly selects xi and and computes the Chebyshev polynomials and . Afterward, RC calculates , , , writes to smart card SCi, and gives it to Ui, where m is the number of servers in the system.
Step 3: After Ui completes registration, RC selects a random number and calculates . Finally, RC transmits to all servers in the system through the secure channel.
3.4. Login and Authentication Phase
Step 1: The user Ui inserts his smart card SCi into the terminal, inputs his identity IDi, password PWi, and collects the biometrics Bi. SCi calculates , , , , , , . The smart card verifies whether is true or not; if not, SCi rejects the login request of Ui; otherwise, SCi obtains the current timestamp TSi, generates a random number RNi, and calculates , , , . Finally, SCi sends the login request information to the server Sj.
Step 2: The server Sj receives M1 and first verifies the validity of the time stamp TSi. If the time stamp TSi is invalid, Sj rejects the login request; otherwise, Sj calculates and decrypts with to get , , , , , , , . Sj uses the decrypted IDi to search for the corresponding and verify whether is true; if not, Sj terminates the session; otherwise, Sj calculates , , and compares the calculated result with the received corresponding value; if not, Sj terminates the session; otherwise, Sj authenticates Ui successfully. Next, Sj obtains the current timestamp TSj and calculates , and the session key . Finally, Sj transmits back to user Ui.
Step 3: Ui receives M2 and verifies the validity of time stamp TSj. If TSj is invalid, Ui terminates the session; otherwise, Ui computes and decrypts to get , , , , , and then Ui computes , . If holds, Ui authenticates Sj successfully and calculates session key .
The process of login and authentication phase is shown in Figure 3.
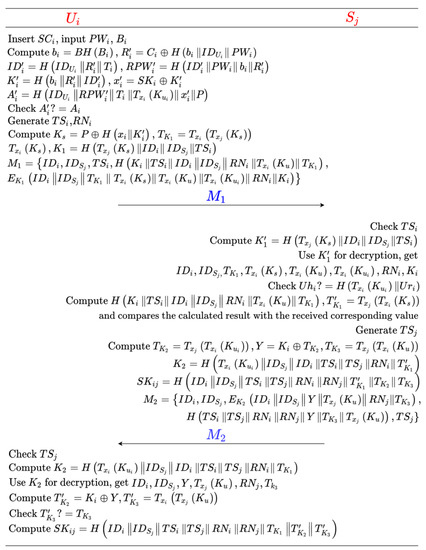
Figure 3.
Login and authentication phase of Chatterjee et al.’s scheme.
3.5. User Password and Biometric Update Phase
Step 1: The user Ui inserts his smart card SCi into the terminal, inputs his identity and password PWi, and collects his biometric Bi. SCi calculates , , , , , , . SCi verifies whether is established; if not, the smart card rejects the login request of Ui; otherwise, SCi makes Ui enter a new password and new biological information.
Step 2: Ui enters the new password and new biometric . Then, the smart card computes , , , .
Step 3: SCi replaces , with Ai and Ci.
4. Cryptanalysis of Chatterjee et al.’s Scheme
4.1. User Un-Traceability
The adversary can intercept the information transmitted between the user and the server in the public channel. Due to the protection of hash function, the adversary cannot directly extract the user’s identity. However, in the login request information of user u, , where Ti is the time stamp obtained when Ui registers. It can be found that the IDi generated by the same user in each login request is fixed. Therefore, it is easy for adversaries to determine whether two sessions are initiated by the same user through IDi, so as to track the user’s behavior. Therefore, the protocol proposed by Chatterjee et al. cannot achieve user un-traceability.
4.2. Three-Factor Security
Chatterjee et al.’s protocol involves three security factors: user password, smart card, and user’s biometrics. Suppose that the adversary accidentally obtains the smart card and biometric of user , the adversary can obtain the password of through the following operations:
Step 1: The adversary uses the side-channel attack technology [32] to extract the secret information stored in the smart card of , and calculates .
Step 2: guesses that the identity and password of Ui are , where and are generated from user identity space and password space , respectively.
Step 3: calculates , , , , , .
Step 4: The smart card verifies whether is true; if it is true, are correct; otherwise, go to Step 2.
According to the above steps, it takes to complete the offline password guessing attack, where Th is the time-consuming of hash function running once, and XOR operation can be ignored due to its small time-consuming. According to reference [33], . Using the computing processor intel-i7-5500 3.6 g Hz in reference [34], , the adversary can complete the above attack within 33 days. If a high-performance cloud platform launches the attack, the user’s password can be guessed within a few hours.
4.3. User Impersonation Attack
Since is stored in each user’s smart card, malicious users can intercept the login request information of user Ui to initiate login request as user Ui and pass the authentication of server Sj. The specific operations are as follows:
Step 1: The malicious user intercepts
transmitted in the public channel.
Step 2: calculates , where is extracted from the smart card of , , , is obtained from M1. Then, uses K1 to decrypt to get , , ,, , , , .
Step 3: Through the information obtained in Step 2, can generate a new timestamp and construct the legitimate request information m of user Ui requesting to log in to server Sj:
5. The Proposed Scheme
The proposed protocol includes the following phases: system setup phase, server registration phase, login and authentication phase, user registration phase, user password, and biometric update phase. The symbols used in the proposed protocol are shown in Table 3.

Table 3.
Notations in Chatterjee et al.’s scheme.
The detailed description of the agreement is as follows:
5.1. System Setup Phase
The registration center RC randomly selects x, y as the system master keys in . Next, RC selects a secure hash function h(·).
5.2. Server Registration Phase
Step 1: The server Sj selects its identity SIDj and passes it to RC through a secure channel.
Step 2: After receiving SIDj, RC calculates and publishes information . Next, RC sends Kj back to Sj through the secure channel.
Step 3: Sj receives Kj and keeps it in secret.
5.3. User Registration Setup Phase
Step 1: The user Ui selects his identity IDi and password PWi and enters his biometric Bioi. Then, Ui uses the biological hash function BH(.) to get bi and calculates , . Finally, Ui transmits the registration information to RC through a secure channel.
Step 2: After receiving Ui ‘s registration information, RC computes , , , where . Next, RC calculates , , where and m is the number of servers in the systems. At last, are written into the smart card SCi, and SCi is transmitted to Ui via the secure channel.
Step 3: Ui keeps SCi properly.
The process of the registration phase is shown in Figure 4.
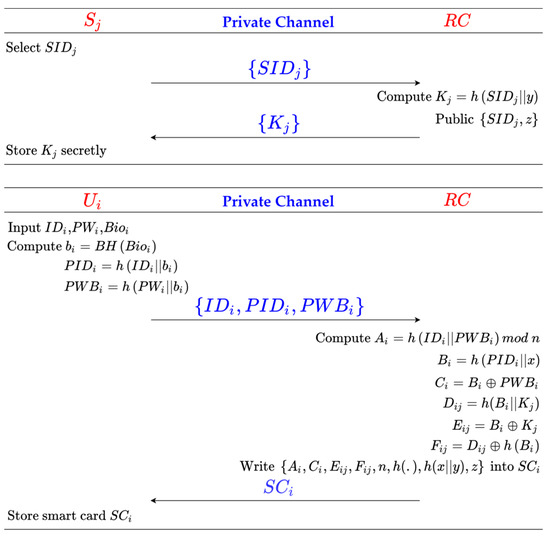
Figure 4.
Registration phase of proposed scheme.
5.4. Login and Authentication Phase
Step 1: The user Ui inserts his smart card SCi into the terminal and inputs his identity IDi, password PWi, and biometric Bioi. SCi calculates , , and verifies whether is established; if not, SCi terminates the session; otherwise, SCi generates a random number ni, selects the identity of the server to be accessed SIDj, and calculates , , , , , . Finally, Ui sends to server Sj.
Step 2: Upon the receipt of login request from Ui, Sj computes , , , , , and verifies that M1 and match. If not, Sj terminates the session. Otherwise, Sj generates a random number nj and calculates , , , . Afterward, Sj sends to Ui.
Step 3: Ui receives and calculates . Ui verifies whether is established; if not, Ui terminates the session; otherwise, Ui identifies Sj as legal. After that, Ui computes , , and gets the session key . Ultimately, is delivered to Sj.
Step 4: Sj receives and verifies whether holds; if not, Sj terminates the session; otherwise, Sj certifies that the identity of Ui is legal. Furthermore, Sj computes and reaches the same session key with Ui: .
The process of login and authentication phase is shown in Figure 5.

Figure 5.
Login and authentication phase of the proposed scheme.
5.5. User Password and Biometric Update Phase
Step 1: The user Ui inserts his smart card SCi into the terminal, inputs his identity and password PWi, and collects his biometric Bi. SCi calculates , , and verifies whether is established; if not, SCi terminates the session; otherwise, SCi makes Ui enter a new password and new biological information.
Step 2: Ui enters the new password and new biometric . Then, SCi computes , , , , .
Step 3: SCi replaces , with Ai and Ci.
6. Security Analysis
6.1. Provable Security
Based on the BPR2000 model [35], the following is the description of the random oracle model and the definition of AKE security:
- (1)
- Participants
As participants, users U and servers S have many different instances, which are called oracle. The i-th instance of U and the j-th instance of S are denoted as Ui and Sj, respectively, and any instance can be denoted as I uniformly.
- (2)
- Queries
: The query captures the passive eavesdropping of the scheme, and its output includes all the communication records of the scheme between and .
: This query indicates a login request that triggers the scheme startup and outputs .
: This query captures active attacks. More precisely, the adversary constructs a forged message m by interrupting and intercepting messages. Then, sends m to and gets a response from .
: If accepts the session and generates the session key SK, it will respond to with SK.
: The query simulates the capture of any two of the three security factors. If a = 1 and I = U, the user password and all parameters stored in the smart card are returned to . If a = 2 and I = U, the user biometrics and all parameters stored in the smart card are returned to . If a = 3 and I = U, the user password and biometrics are returned to . If a = 1 and I = S, the long-term private key of the server is returned to .
: The oracle tosses a coin b ∈ (0,1); if b = 1, it returns the session key; if b = 0, it returns a random number with the same length as the session key.
- (3)
- Partnership
and are called partnerships if: (i) and are accepted; (ii) and have the same session identifier (sid), that is, ; (iii) the partner identifier of is and vice versa.
- (4)
- Freshness
A user instance or server instance is called fresh if (i) I has calculated an acceptable session key; (ii) has not made any Reveal queries to I or its partners. (iii) From the beginning of the game, makes Corrupt query to I or its partners at most once.
Definition 1.
The adversary outputs the result of guess b’
through Test queries. If b’ = b, wins the game. The advantage probability of breaking the security of the protocolis defined as:
. If the probability is negligible for any probabilistic polynomial time adversary , the protocol is AKE secure.
Theorem 1.
Suppose the adversaryoperates Send queries, Execute queries and Hash queries to break the AKE security of the protocol. represents the advantage probability of solving CMCDH problem in the polynomial time t, then we have:
where C’ and s’ are the CDF-Zipf regression parameters of password space, l is the bit length of hash function output,
, and represents the running time of extended chaotic map operation.
Proof.
Game is created to prove that the proposed scheme is provably secure, and stands for correctly guessing b in game using Test queries.
Game : This game simulates the real attack in the random oracle model. We can get:
Game : This game manages Hash list while simulating random oracle. Then we get:
Game : In , if there is a collision of interactive information or a collision of Hash query results, the game ends; otherwise, simulates all queries in . According to the birthday paradox [36], the collision probability of the result of Hash query is and the collision probability of interaction information is ; therefore, we derive the following result:
Game : In game , if guesses the information M1 and M2 used for authentication correctly, the game ends; otherwise, is the same simulation as the previous game; therefore, we derive the following result:
Game : In this game, guesses the session key without asking the corresponding random oracle. Therefore, this game is indistinguishable from the previous game, except that makes queries for . Thus, we get that:
where .
Game : This game is similar to the previous game, but the only difference is the Test query. If performs the Test query on , the game will be terminated. Therefore, the maximum probability of obtaining session key by random oracle query is . Moreover, if query is executed, and can no longer be queried. According to reference [37], in the case of times of send query for online guess, the probability of getting the password is at most
.
According to the definition of freshness, can perform query after performing query. As a result, outdated copies are used in old games (perfect forward secrecy). Therefore, the maximum probability of getting is . Then, we get:
If does not request any random oracle query with valid input, then the game has no advantage to distinguish the real SK from the random string with the same length, so we get:
According to Formulas (2), (3), and (8), we come to the conclusion
6.2. BAN-Logic
Burrow, Abadi, and Needham proposed BAN-logic [38] in 1989. BAN-logic is a belief-based modal logic, which can be used to describe and verify authentication protocols. When using BAN-logic to analyze the security of authentication protocol, we first need to idealize the interaction information in the protocol, then make initialization assumptions according to the specific situation, and finally get the expected goal through reasoning rules. Table 4 introduces the notations for the BAN-logic, and some basic rules are described in Table 5.

Table 4.
BAN-logic notations.

Table 5.
Basic logical postulates of BAN-logic.
- (1)
- The idealized form of the proposed scheme
Message 1:
Message 2:
- (2)
- Verification goals
Goal 1: .
Goal 2: .
Goal 3: .
Goal 4: .
- (3)
- Assumptions about the initial state
A1: .
A2: .
A3: .
A4: .
A5: .
A6:
- (4)
- Proofs
Step 1: According to Message 1, we know that .
Step 2: According to Step1, A4, and the message-meaning rule, we obtain the following: .
Step 3: According to A2, freshness-conjuncatenation rule, , and , the following can be inferred: .
Step 4: From Step 2, Step 3, and the nonce verification rule, we get that: .
Step 5: From Step 4, A4, and , we prove Goal 4: .
Step 6: According Step 5, A6, and the jurisdiction rule, we prove Goal 3: .
Step 7: According to Message 2, we know that .
Step 8: According to Step 7, A3, and the message-meaning rule, we obtain the following: .
Step 9: According A1, freshness-conjuncatenation rule, , the following can be inferred: .
Step 10: From Step 8, Step 9, and the nonce verification rule, we get that: .
Step 11: From Step 10, A4, and , we prove Goal 2: .
Step 12: According Step 11, A5 and jurisdiction rule, we prove Goal 1: .
It can be seen from Goal 1, Goal 2, Goal 3, and Goal 4 that the mutual authentication between user and server is completed, and the session key SK trusted by both parties is reached.
6.3. Informal Security Analysis
The new scheme can effectively improve the shortcomings of Chatterjee et al.’s scheme. First of all, the new protocol ensures that the information related to user identity and security factors are used reasonably in the process of generating login request information, which can effectively resist the user impersonation attack. Secondly, in the verification phase of smart cards, the modular operation is introduced, which can avoid the offline password guessing attack so as to achieve three-factor security. Finally, the construction of user login request information needs the participation of random numbers to ensure the realization of user un-traceability.
On the other hand, according to the description of the login and authentication phase of the new protocol, only with the ID, password, biological information, and smart card of the legal user Ui, the user can generate the legal login request information while only the server Sj with the legal Kj can generate the legal response information. Therefore, on the basis of ensuring the mutual authentication between the user and the server, the server Sj can get the correct by calculating . Due to the semi-group property of the extended Chebyshev polynomials, , Ui and Sj reach the session key for future sessions. They complete the session key agreement, and the contributions to session key generation are equal. Next, we make a specific security analysis of our proposed protocol.
- (1)
- Anonymity and un-traceability
In the login and authentication phase, the adversary can intercept the login request information of the user and the response information of the server. Obviously, under the protection of Hash function, the adversary cannot obtain the user's identity. Therefore, the proposed scheme can achieve user anonymity. On the other hand, the construction of , and is related to the random number ni or nj. Therefore, the interactive information generated in each session is different. Even if the adversary intercepts the message, it is still unable to determine whether two sessions originate from the same user. Therefore, the new protocol can achieve user un-traceability.
- (2)
- Perfect forward secrecy
Suppose that the adversary accidentally obtains the private keys of RC: x and y, and intercepts the information propagated in the public channel. The adversary can compute , , , , . However, it is a CMCDH problem to get in polynomial time from the known information. Therefore, the adversary is still unable to calculate the session key between user Ui and Sj, and the perfect forward secrecy of the new scheme is realized.
- (3)
- Mutual authentication
According to the description of the new scheme, only with Ui's identity, password, smart card, and biometrics can the legitimate login request information be generated. The server can authenticate the Ui’s identity by verifying the legitimacy of the received information. On the other hand, only the server Sj with legal Kj can correctly respond to the user’s login request information. Therefore, the new scheme realizes the mutual authentication between the user and the server.
- (4)
- Session key agreement
Based on the description of the new scheme, the user and the server can reach the session key for future communication after completing the login and authentication phase .
- (5)
- Three-factor security
For the three-factor authentication protocol, the difficulty of breaking through the user password is obviously lower than the difficulty of breaking through the secret information of smart cards or user biometrics. Suppose the adversary accidentally obtains the smart card and biometrics of Ui, and the secret information in the smart card is extracted through the side-channel technology. However, the verification performed by the smart card in the login phase is a fuzzy verification. Even if the adversary’s guess passes the above verification, the adversary still cannot confirm whether is the real password of Ui. Specifically, through offline password guessing, the adversary can get possible pairs. The adversary still needs to log in online (not offline) and traverse these user identity and password pairs to obtain the accurate user password. The server can identify the victim according to the adversary’s login request. By setting the threshold of login times, when the adversary’s online login times exceed the threshold, the server can refuse the adversary’s login request. The adversary cannot log in to the system many times, so he cannot get the correct one of the possible passwords. Therefore, the new protocol can achieve three-factor security.
- (6)
- Good Repairability
In our proposed scheme, the user Ui's private information stored in the smart card includes , , , . Therefore, Ui's password and biometrics will directly affect the secret information. When the smart card SCi is lost, Ui only needs to modify his password and biometrics to ensure the security of the system. Thus, our scheme has good repairability.
- (7)
- Resistance of other known attacks
Insider attack: Insiders can get the registration information of user Ui. However, the information is protected by Hash function, and the attacker cannot extract the user’s password or biometrics. Therefore, the insider attack is invalid for the proposed new scheme.
Stolen verifier table attack: There is no password-related and biometric-related information table stored in the servers and RC. Therefore, the stolen verifier table attack is infeasible in our proposed scheme.
Temporary information leakage attack: In our proposed scheme, the user and the server reach a session key . Even if an adversary captured the temporary information ni and nj, he could not launch a temporary information leakage attack without . As a result, our proposed scheme can resist a temporary information leakage attack.
Replay attack: According to the description of the proposed protocol, the user and the server generate the new random number ni and nj in the authentication phase. Both sides can easily find replay attacks by checking the validity of the received message. Therefore, the new protocol can effectively resist replay attacks.
DoS attack: After receiving the login request from Ui, the server Sj verifies whether holds. Only Ui calculates the legitimate login request information according to his identity, password, biometrics, and smart card and can pass the verification. Therefore, Sj can confirm that the login request is from Ui, which can effectively reject a large number of invalid login requests from attackers.
According to the previous analysis and proof, we also know that the new scheme can resist user impersonation attacks, server spoofing attacks, man-in-the-middle attacks, offline password guessing attacks, and smart card stolen attacks.
7. Performance Analysis
In this section, we will compare the performance of the proposed new protocol with other authentication protocols based on the extended chaotic map in multi-server environments, including the comparison of computation cost and communication cost. Since the registration phase of users and servers only occurs once, and users do not frequently update their passwords and biometrics, this section only discusses the performance comparison between the login and authentication phases.
7.1. Comparison of Computing Costs
The new scheme and other similar protocols [30,39,40,41] all use fuzzy extractor algorithm or bio-hash function to extract users’ biometrics for protocol design. According to literature [42,43], the time cost of the fuzzy extractor algorithm and bio hash function is considered equal. Therefore, the user biometric extraction operation is ignored in the comparison of computation cost.
The comparison between the new proposed protocol and the protocols proposed by Chatterjee et al. [30], Lee et al. [39], Irshad et al. [40], and Braeken et al. [41] is shown in Table 6. The symbols used in the table have the following meanings:

Table 6.
Comparison of computing costs (millisecond).
: Time to execute a general hash operation.
: Time to execute a symmetric encryption/decryption algorithm.
: Time to execute a chaotic map operation.
(The computation overhead of XOR operation is ignored).
The running time of the user to perform the above operation is obtained from the experiment of Intel Pentium 4 2600 MHZ processor and 1024 MB memory platform in reference [30]. The server performance is assumed to be 10 times of 2.4 GHz processor and 2GB memory platform. The running time of different operations on two platforms is shown in Table 7.

Table 7.
Running time of operations (millisecond).
From the results in Table 7, the proposed protocol has a lower computation cost than the other four protocols for both the user and server sides.
7.2. Comparison of Communication Costs
For the convenience of comparison, it is assumed that the length of identification, random number, timestamp, and other parameters involved in the new protocol and other related protocols is 128 bits, the length of large prime p is 128 bits, the output length of Hash function is 160 bits (such as SHA-1), and the ciphertext length of the symmetric encryption algorithm is an integral multiple of 128 bits (such as AES).
In the login and authentication phase of the proposed protocol, the interaction information between the user and the server includes , and . The total length of interactive information is .
In the login and authentication phase of Chatterjee et al.’s protocol, the interaction information between the user and the server includes and . The total length of interactive information is .
Table 8 shows the comparison of communication cost between the proposed new protocol and Chatterjee et al. [30], Lee et al. [39], Irshad et al. [40], and Braeken et al. [41]. From the comparison results, it can be seen that the communication cost of the new proposed scheme is at a better level compared with similar protocols, and it has good communication efficiency. It should be noted that our scheme is the only one that needs three times of data transmission. This is to further strengthen the identity authentication of the server to the user, to further ensure the security of the system. If we give up the information M4 that the user transmits to the server, the server can complete the authentication of the user in the second step of the authentication phase and also generate the session key . We finally choose stronger security, and the communication overhead caused by this is acceptable.

Table 8.
Comparison of communication costs.
8. Conclusions
In recent years, multi-server network architecture is widely used in practical applications. Moreover, due to the insecurity of the network, abundant researches on authentication and key agreement protocol for multi-server architecture have been put forward. In 2018, Chatterjee et al. published an authentication protocol based on an extended Chebyshev chaotic map for multi-server environments. However, through the analysis of their protocol, we find that the protocol cannot achieve user un-traceability and three-factor security and cannot resist the counterfeiting attacks launched by malicious users. In order to ensure the communication security of participants in multi-server network environments, this study proposed a secure three-factor authentication protocol based on the extended chaotic map. The new protocol can effectively avoid the security defects of Chatterjee’s protocol and achieve all known security goals. Moreover, the proposed scheme is analyzed and verified by the provable security and BAN logic. The results show that our scheme realizes the mutual authentication of communication participants and can effectively resist all kinds of attacks. Compared with other related protocols, the new protocol has good practicability and can be applied to multi-server environments.
Author Contributions
Conceptualization, Y.Y.; Methodology, Y.Y. and O.T.; Supervision, O.T.; Visualization, R.L; Writing—original draft, Y.Y and R.L.; Writing—review & editing, Y.Y. and B.S. All authors have read and agreed to the published version of the manuscript.
Funding
This research was funded by Keele University’s Central Fund.
Institutional Review Board Statement
Not applicable.
Informed Consent Statement
Not applicable.
Data Availability Statement
Not applicable.
Conflicts of Interest
The authors declare no conflict of interest.
References
- Segura Beltran, F. Development of Gauging Services in Spain. The Network of Stations of Jucar Hydrographic Confederation. Boletin De La Asociacion De Geografos Espanoles 2013, 63, 566–568. [Google Scholar]
- Jia, M.; Komeily, A.; Wang, Y.; Srinivasan, R.S. Adopting Internet of Things for the development of smart buildings: A review of enabling technologies and applications. Autom. Constr. 2019, 101, 111–126. [Google Scholar] [CrossRef]
- Satyanarayanan, M. Fundamental challenges in mobile computing. In Proceedings of the Fifteenth Annual ACM Symposium on Principles of Distributed Computing, Philadelphia, PA, USA, 23–26 May 1996. [Google Scholar]
- Fu, Z.; Sun, X.; Liu, Q.; Zhou, L.; Shu, J. Achieving Efficient Cloud Search Services: Multi-Keyword Ranked Search over Encrypted Cloud Data Supporting Parallel Computing. IEICE Trans. Commun. 2015, 190–200. [Google Scholar] [CrossRef]
- Tsai, C.-H.; Su, P.-C. The application of multi-server authentication scheme in internet banking transaction environments. Inf. Syst. e-Bus. Manag. 2021, 19, 77–105. [Google Scholar] [CrossRef]
- Li, L.-H.; Lin, L.-C.; Hwang, M.-S. A remote password authentication scheme for multiserver architecture using neural networks. IEEE Trans. Neural Netw. 2001, 12, 1498–1504. [Google Scholar] [CrossRef]
- Lin, I.-C.; Hwang, M.-S.; Li, L.-H. A new remote user authentication scheme for multi-server architecture. Future Gener. Comput. Syst. 2003, 19, 13–22. [Google Scholar] [CrossRef]
- Cao, X.; Zhong, S. Breaking a remote user authentication scheme for multi-server architecture. IEEE Commun. Lett. 2006, 10, 580–581. [Google Scholar] [CrossRef]
- Lee, C.-C.; Lin, T.-H.; Chang, R.-X. A secure dynamic ID based remote user authentication scheme for multi-server environment using smart cards. Expert Syst. Appl. 2011, 38, 13863–13870. [Google Scholar] [CrossRef]
- Kim, H.-W.; Lim, S.-Y.; Lee, H.-J. Symmetric Encryption in RFID Authentication Protocol for Strong Location Privacy and Forward-Security. In Proceedings of the 2006 International Conference on Hybrid Information Technology, Cheju Island, Korea, 9–11 November 2006. [Google Scholar]
- Fotouhi, M.; Bayat, M.; Das, A.K.; Far, H.A.N.; Pournaghi, S.M.; Doostari, M. A lightweight and secure two-factor authentication scheme for wireless body area networks in health-care IoT. Comput. Netw. 2020, 177, 107333. [Google Scholar] [CrossRef]
- Sadri, M.J.; Asaar, M.R. A lightweight anonymous two-factor authentication protocol for wireless sensor networks in Internet of Vehicles. Int. J. Commun. Syst. 2020, 33, e4511. [Google Scholar] [CrossRef]
- Kwon, D.; Yu, S.; Lee, J.; Son, S.; Park, Y. WSN-SLAP: Secure and Lightweight Mutual Authentication Protocol for Wireless Sensor Networks. Sensors 2021, 21, 936. [Google Scholar] [CrossRef] [PubMed]
- Hathal, W.; Cruickshank, H.; Sun, Z.; Maple, C. Certificateless and Lightweight Authentication Scheme for Vehicular Communication Networks. IEEE Trans. Veh. Technol. 2020, 69, 16110–16125. [Google Scholar] [CrossRef]
- Tu, Y.-J.; Gaurav, K.; Selwyn, P. Security of lightweight mutual authentication protocols. J. Supercomput. 2020, 77, 4565–4581. [Google Scholar] [CrossRef]
- Yoon, E.-J.; Yoo, K.-Y. Robust biometrics-based multi-server authentication with key agreement scheme for smart cards on elliptic curve cryptosystem. J. Supercomput. 2013, 63, 235–255. [Google Scholar] [CrossRef]
- Kim, H.; Kim, H.; Jeon, W.; Jeon, W.; Lee, K.; Lee, K.; Lee, Y.; Lee, Y.; Won, D.; Won, D. Cryptanalysis and Improvement of a Biometrics-Based Multi-server Authentication with Key Agreement Scheme. In Proceedings of the International Conference on Computational Science and Its Applications, Salvador, Brazil, 18–21 June 2012. [Google Scholar]
- He, D.; Wang, D. Robust Biometrics-Based Authentication Scheme for Multiserver Environment. IEEE Syst. J. 2014, 9, 816–823. [Google Scholar] [CrossRef]
- Odelu, V.; Das, A.K.; Goswami, A. A Secure Biometrics-Based Multi-Server Authentication Protocol Using Smart Cards. IEEE Trans. Inf. Forensics Secur. 2015, 10, 1953–1966. [Google Scholar] [CrossRef]
- Tsai, J.-L.; Lo, N.-W. A Privacy-Aware Authentication Scheme for Distributed Mobile Cloud Computing Services. IEEE Syst. J. 2015, 9, 805–815. [Google Scholar] [CrossRef]
- He, D.; Kumar, N.; Khan, M.K.; Wang, L.; Shen, J. Efficient Privacy-Aware Authentication Scheme for Mobile Cloud Computing Services. IEEE Syst. J. 2016, 12, 1621–1631. [Google Scholar] [CrossRef]
- Kumari, S.; Li, X.; Wu, F.; Das, A.K.; Choo, K.-K.R.; Shen, J. Design of a provably secure biometrics-based multi-cloud-server authentication scheme. Future Gener. Comput. Syst. 2017, 68, 320–330. [Google Scholar] [CrossRef]
- Wu, F.; Xu, L.; Li, X. A New Chaotic Map-Based Authentication and Key Agreement Scheme with User Anonymity for Multi-server Environment. In Proceedings of the International Conference on Frontier Computing, Kuala Lumpur, Malaysia, 3–6 July 2018. [Google Scholar]
- Feng, Q.; He, D.; Zeadally, S.; Wang, H. Anonymous biometrics-based authentication scheme with key distribution for mobile multi-server environment. Future Gener. Comput. Syst. 2018, 84, 239–251. [Google Scholar] [CrossRef]
- Wang, P.; Zhang, Z.; Wang, D. Revisiting Anonymous Two-Factor Authentication Schemes for Multi-server Environment. In Proceedings of the International Conference on Information and Communications Security, Lille, France, 8 June 2018. [Google Scholar]
- Haq, I.U.; Wang, J.; Zhu, Y.; Maqbool, S. An efficient hash-based authenticated key agreement scheme for multi-server architecture resilient to key compromise impersonation. Digit. Commun. Netw. 2021, 7, 140–150. [Google Scholar] [CrossRef]
- Ying, B.; Nayak, A. Lightweight remote user authentication protocol for multi-server 5G networks using self-certified public key cryptography. J. Netw. Comput. Appl. 2019, 131, 66–74. [Google Scholar] [CrossRef]
- Kumar, A.; Om, H. An improved and secure multiserver authentication scheme based on biometrics and smartcard. Digit. Commun. Netw. 2018, 4, 27–38. [Google Scholar] [CrossRef]
- Irshad, A.; Sher, M.; Ahmad, H.F.; Alzahrani, B.A.; Chaudhry, S.A.; Kumar, R. An improved Multi-server Authentication Scheme for Distributed Mobile Cloud Computing Services. KSII Trans. Internet Inf. Syst. 2016, 10, 6092–6115. [Google Scholar] [CrossRef]
- Chatterjee, S.; Roy, S.; Das, A.K.; Chattopadhyay, S.; Kumar, N.; Vasilakos, A.V. Secure Biometric-Based Authentication Scheme Using Chebyshev Chaotic Map for Multi-Server Environment. IEEE Trans. Dependable Secur. Comput. 2018, 15, 824–839. [Google Scholar] [CrossRef]
- Zhang, L. Cryptanalysis of the public key encryption based on multiple chaotic systems. Chaos Solitons Fractals 2008, 37, 669–674. [Google Scholar] [CrossRef]
- Veyrat-Charvillon, N.; Veyrat-Charvillon, N.; Standaert, F.-X.; Standaert, F.-X. Generic Side-Channel Distinguishers: Improvements and Limitations. In Proceedings of the Annual Cryptology Conference, Santa Barbara, CA, USA, 14–18 August 2011. [Google Scholar]
- Das, M.L. Two-factor user authentication in wireless sensor networks. IEEE Trans. Wirel. Commun. 2009, 8, 1086–1090. [Google Scholar] [CrossRef]
- Wang, D.; Li, W.; Wang, P. Measuring Two-Factor Authentication Schemes for Real-Time Data Access in Industrial Wireless Sensor Networks. IEEE Trans. Ind. Informatics 2018, 14, 4081–4092. [Google Scholar] [CrossRef]
- Bresson, E.; Chevassut, O.; Pointcheval, D. Security proofs for an efficient password-based key exchange. In Proceedings of the 10th ACM Conference on Computer and Communications Security, Washington, DC, USA, 27–31 October 2003. [Google Scholar]
- Borja, M.C.; Haigh, J. The birthday problem. Significance 2007, 4, 124–127. [Google Scholar] [CrossRef]
- Zhang, L.; Tang, S.; Cai, Z. Cryptanalysis and improvement of password-authenticated key agreement for session initiation protocol using smart cards. Secur. Commun. Netw. 2014, 7, 2405–2411. [Google Scholar] [CrossRef]
- Burrows, M.; Abadi, M.; Needham, R.M. A logic of authentication. Proc. R. Soc. Lond. A Math. Phys. Sci. 1989, 426, 233–271. [Google Scholar]
- Lee, T.-F.; Diao, Y.-Y.; Hsieh, Y.-P. A ticket-based multi-server biometric authentication scheme using extended chaotic maps for telecare medical information systems. Multimedia Tools Appl. 2019, 78, 31649–31672. [Google Scholar] [CrossRef]
- Irshad, A.; Sher, M.; Chaudhary, S.A.; Naqvi, H.; Farash, M.S. An efficient and anonymous multi-server authenticated key agreement based on chaotic map without engaging Registration Centre. J. Supercomput. 2016, 72, 1623–1644. [Google Scholar] [CrossRef]
- Braeken, A.; Kumar, P.; Liyanage, M.; Hue, T.T.K. An efficient anonymous authentication protocol in multiple server communication networks (EAAM). J. Supercomput. 2017, 74, 1695–1714. [Google Scholar] [CrossRef]
- Shin, S.; Kwon, T. A Lightweight Three-Factor Authentication and Key Agreement Scheme in Wireless Sensor Networks for Smart Homes. Sensors 2019, 19, 2012. [Google Scholar] [CrossRef]
- He, D.; Kumar, N.; Lee, J.-H.; Sherratt, R.S. Enhanced three-factor security protocol for consumer USB mass storage devices. IEEE Trans. Consum. Electron. 2014, 60, 30–37. [Google Scholar] [CrossRef]
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2021 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).