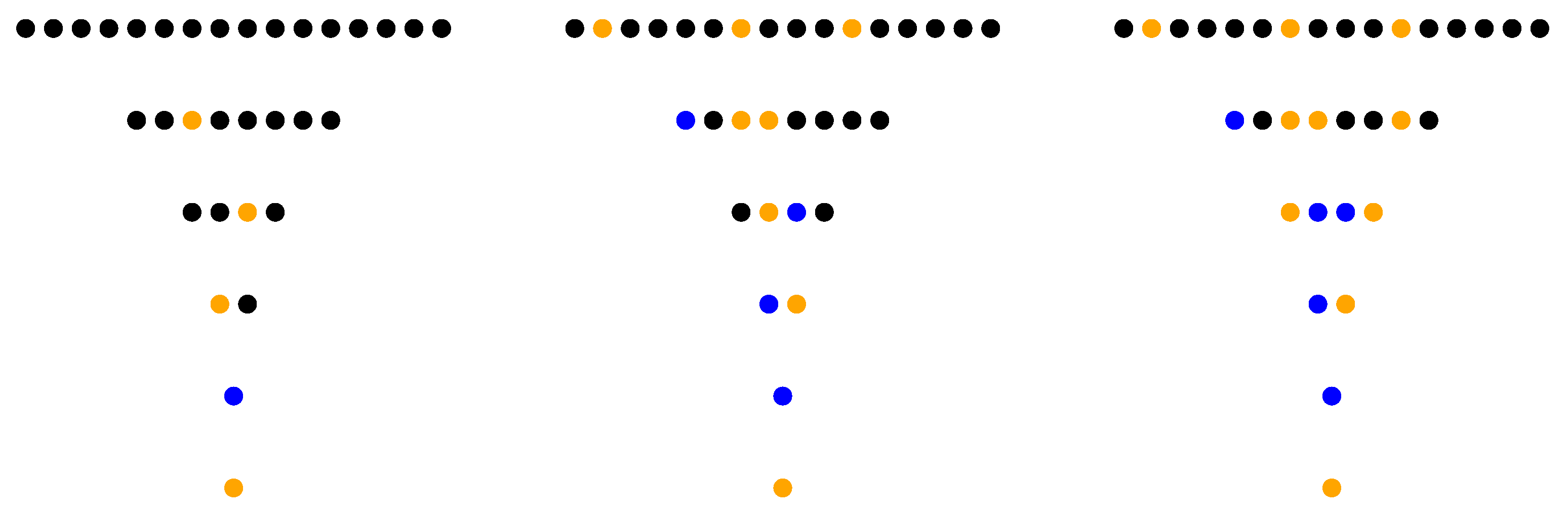1. Introduction
In 1937, Lothar Collatz established a conjecture known as the
problem, also known as Kakutani’s problem, the Syracuse algorithm, Hasse’s algorithm, Thwaites conjecture, and Ulam’s problem. The Collatz problem involves the iterative sequence defined as follows (see OEIS [
1] for the definition of the Collatz map):
Among others, Erdős and Conway [
2] conjectured that, given any initial term
, the sequence always terminates at 1. Conway proved that there is no nontrivial cycle with a length less than 400, with Lagarias [
3] later increasing this lower bound to 275,000. Conway [
2], and Kurtz and Simon [
4] also proved that the generalization of the Collatz problem is undecidable. The conjecture was first verified up to
by Leavens et al. [
5] and then to
by Vardi [
6]; then, Oliveira [
7] further extended the results to
, and as of 2020, it had been verified beyond
. The Collatz problem is often stated differently, for example by Terras [
8,
9], to essentially compress the division by 2 [
10,
11]:
Researchers have tried to model the problem in various ways. Wolfram [
12] represented it as an eight-register machine. Cloney et al. [
10] and Bruschi [
13] modeled it as a quasi-cellular automaton, with Zeleny [
14] specifically modeling it as a six-color one-dimensional quasi-cellular automaton. Among some notable recent developments, Machado [
15] provided an interesting clustering perspective on the Collatz conjecture and Tao [
16] demonstrated that almost all Collatz orbits attain almost bounded values.
The dynamical system generated by the
problem is known to create complex quivers (a quiver is simply a collection of arrows between points forming a set [
17], where the Collatz quiver used here is simply defined as the set of all arrows connecting any natural number to the next one under the Collatz map) over
, with one of the most picturesque being the so-called “Collatz Feather” or “Collatz Seaweed”, a name popularized by Clojure programmer Oliver Caldwell in 2017 [
18]. The inflation propensity of Collatz orbits remains so unpredictable that Bocart showed that it can form the core of a reliable proof-of-work algorithm for Blockchain solutions [
19], with groundbreaking applications to the field of number-theoretical cryptography as such algorithms are unrelated to primes yet, being based on the class of congruential graphs and still allowing for a wide diversity of practical variants. If Bocart thus demonstrated that graph-theoretical approaches to the
problem can be very fertile to applied mathematics, the authors have also endeavored to demonstrate its pure number-theoretical interest prior to this work [
20,
21,
22,
23,
24]. In this article, we refer to the Bocart proof-of-work in that expanding it and more precisely endowing it with a scannable certificate is an important side-result of our approach.
Our methodology consists of using the complete binary tree and the complete ternary tree (the complete binary tree over odd numbers is defined as
endowed with the following two linear applications
and all their possible combinations, with the complete ternary tree over the same set in turn defined as
endowed with operations
and all their possible combinations) over
as a general coordinate system for each node of the feather. We owe this strategy to earlier discussions with Feferman [
25] on his investigations on the continuum hypothesis, as it is known that the complete binary tree over natural numbers is one way of generating real numbers. The last author’s discussion with Feferman argued that morphisms, sections, and origamis of
n-ary trees over
could be a promising strategy to define objects of intermediate cardinalities between
and
, in a manner inspired from Conway’s construction of surreal numbers [
26], which itself began by investigating the branching factor of the game of Go. Central to our contribution to the Collatz conjecture in this paper is also the analysis of the branching factor of a zero-player cellular game developing in the complete binary tree over odd numbers.
3. Contributions to the State-of-the-Art
In acknowledgement of the intellectual influence of the study of quantum non-ergodicity to the study of discrete dynamical systems (for a more precise example, see [
41]) we meant to not reduce this article to its mathematical proofs but rather to accompany them with novel 3D visualizations of the Collatz phase space, along with specific empirical measurements of its behavior. As explained in the previous section, both the mathematical proofs and 3D visualizations are based on the ad hoc algebraic foundations, in particular, the coordinate system consisting of studying the intersections of both the binary and ternary trees over odd numbers that we established to gain further insight into the chaoticity of the Collatz feather. In
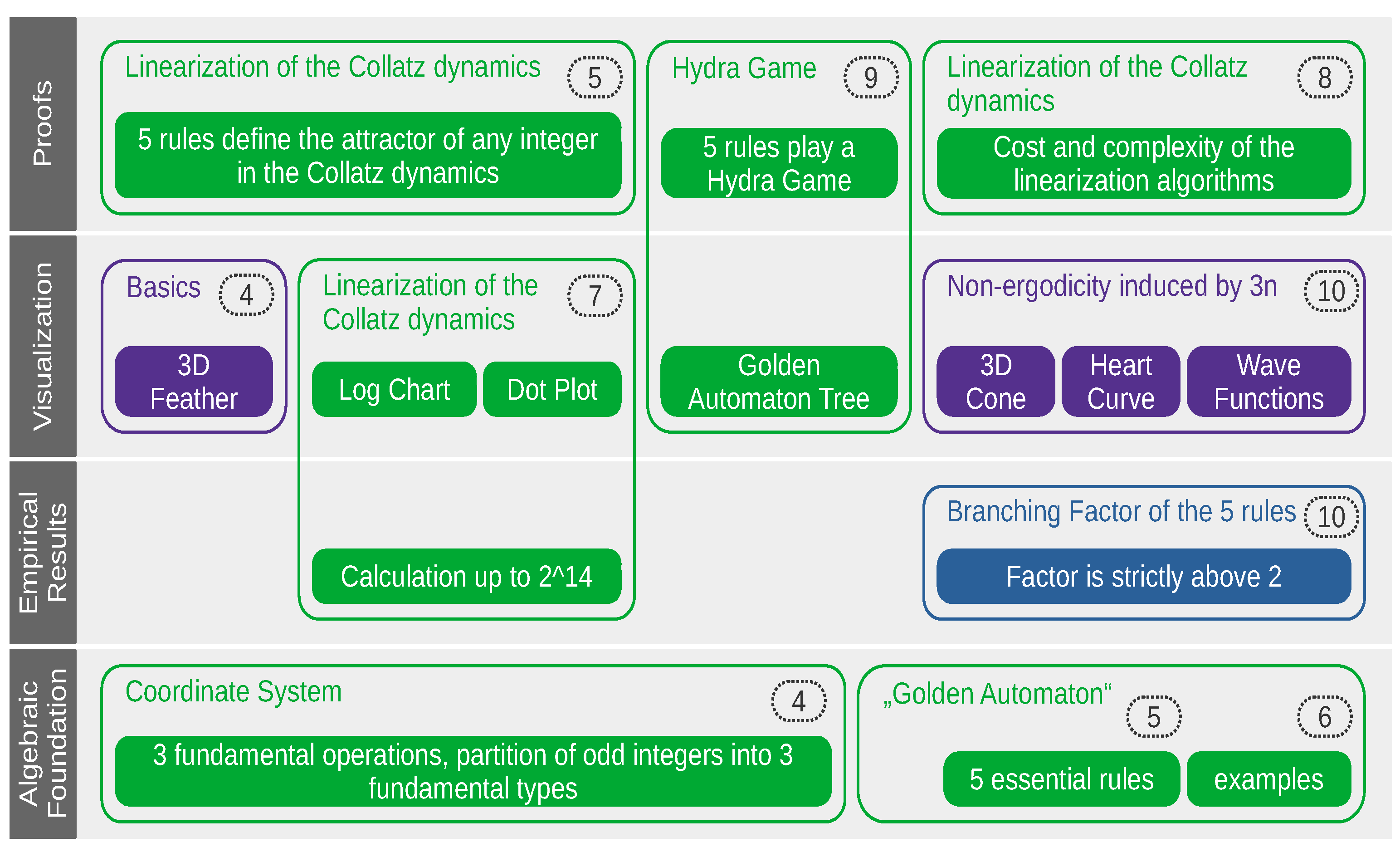
Figure 1, we outline the fundamental contributions we intend to make here. Green charts indicate the results obtained from a two-dimensional coordinate system; purple charts indicate those obtained from a 3D analysis of the feather; and the blue chart indicates a result obtained from both.
Fundamentally, our most essential theorems consist of the five rules that exactly define the basin of attraction of any odd number in the Collatz dynamical system. However, the emerging properties of those five rules are hard to predict and can be counterintuitive. They require equally novel developments in mathematical visualization and beyond a few novel concepts as well. This interplay between conceptual and visual progress is the reason we endeavored to develop many figures and frameworks, both in 2D and in 3D, and from graph theory to cellular automata, transfinite set theory, space-filling L-systems, and caustics. Though not intended ab initio, these many approaches practically complement each other in achieving what we believe to be one of the finest understandings of the fundamental chaoticity of Collatz orbits ever achieved.
4. Binary and Ternary Trees as a Novel Coordinate System for the Collatz Basins of Attraction
Note 1. For all intents and purposes, we define Syr(x) or the “Syracuse action” as “the next odd number in the forward Collatz orbit of x”. Whenever two numbers a and b have a common number in their orbit, we also note a≡b, a relation that is self-evidently transitive: The choice of symbol “≡” is a deliberate one to acknowledge a kinship between our method and modular arithmetic.
Definition 2. Actions G, V and S: For any natural number a,
- 1.
- 2.
.
- 3.
Definition 3. Rank: The rank of any odd natural number a is its number of consecutive end digits 1 in base 2. For computer scientists, the rank is thus strictly equivalent to the “number of trailing ones” or “number of trailing 1 bits” of its binary representation (the number of trailing zeros in any binary string is also known as count trailing zeros (ctz), and the number of trailing ones are known as count trailing ones (cto)).
Definition 4. Types A, B, andC:
- 1.
A number a is of type A if its base 3 representation ends with the digit 2.
- 2.
A number b is of type B if its base 3 representation ends with the digit 0.
- 3.
A number c is of type C if its base 3 representation ends with the digit 1.
In other words, a number of type A belongs to the residue class , a number of type B belongs to the residue class , and a number of type C belongs to the residue class in the ring . In modular arithmetic, using the standard definition of “≡”, we simply have , b , and c . However, we adopted this ABC nomenclature as a simpler way to assign types to numbers when coding our linearizing algorithms, especially when combining different properties (e.g., Bup or A in Section 2.1, which would have been too cumbersome in the current notations of modular arithmetic. To remember which is which, one need only remember the order of ABC: if a, b, and c are respectively of types A, B, and C, then a+1 is dividable by 3, as is c-1; thus, a is on the left of b and c is on the right of b.
We intend to use the quiver of
Figure 2 as a general coordinate system for each node of the Collatz feather. Paramount to our investigation is the comparative analysis of the branching factor of the feather compared with that of the binary tree.
Figure 3 visualizes the orbits of all numbers from 1 to 15,000 in 3D, with the colors set by the types of Definition 3: the type
A numbers are in teal, the type
B ones are in gold, and the type
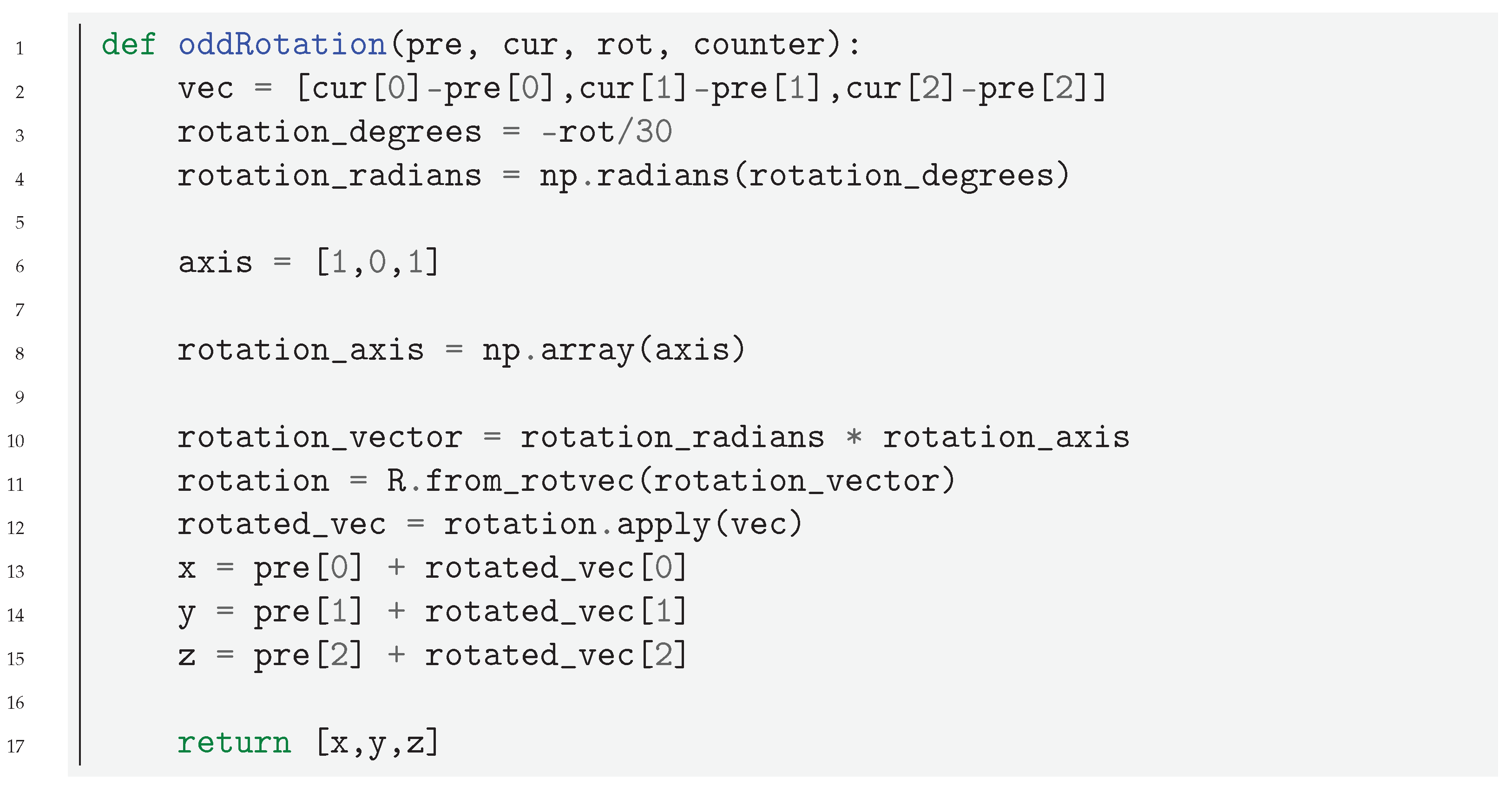
C ones are in purple. Each branch is generated from the complete sequence of each number: for an even number, the current branch is rotated in one direction and rotated in the opposite one for an odd number. Two points,
and
containing the previous and current points of the orbit in the form
, are handed over to the rotation function, which executes the rotation of the current point around a predefined axis. Rotating in opposite directions for even and odd numbers creates the feather-like construct shown in the figure.
Listing 1. Code for rotating the branches of the feather in
Figure 3, see [
42].
![Mathematics 09 01898 i001 Mathematics 09 01898 i001]()
Although the Collatz feather has often been represented in the literature and in popular mathematics circles, its fundamental geometry remains very poorly understood. In the next section, however, we identify the five fundamental rules that define the complete basin of attraction of any point of the feather.
5. The Five Fundamental Rules of the Collatz Dynamical System
Theorem 1. The following arithmetic rules apply anywhere over the system endowed with the Collatz dynamic. Their iteration ad infinitum from any odd number precisely defines the entirety of the basin of attraction leading to it. (The reader should note that, although we call them “rules” in anticipation of their use in programming our linearizing algorithm, they are in fact theorems, which we prove in the next subsections, where operator ⋀ is defined as , with ∧ representing the “AND” boolean operator).
Rule One:
odd,
Rule Two:
if x is odd, then, with k odd. If x is even with k even.
Rule Three:
, odd non B,
Rule Four:
, odd non B,
Rule Five:
, , odd non B where is of rank 1, ,
Let us now demonstrate that each of these rules is in fact a theorem.
Definition 5. In reference to Figure 2, we call "vertical odd" a number that can be written , where o is odd, and "vertical even" if it can be written , where e is even. For example, 5 is the first vertical odd in because and 9 is the first vertical even number in because .
5.1. Proving Rule One
If a is written , then ; therefore, .
5.2. Proving Rule Two
Lemma 2. Let a be a number of rank 1; thus, with an odd number p such that a = G(p), Syr(S(a)) = G(3· p). Let a be a number of rank n so that S(a) = G(p); then, Syr(a) = G(3 p)
Proof. If
,
p is odd; then, it follows that
Let us now generalize to the
n. If
can be written
, it is also of rank 1, whereas
is of rank 2; therefore, the Syracuse action (defined in Note 1) made it lose one rank. All we have to prove now is that
=
under those conditions:
If a is of rank , is of rank and . □
Note 2. Since the action over an odd number n always yields an even result, for any odd number, the Collatz map is equivalent to computing or, in plain English, adding one to the odd number, then halving the result, and then subtracting one. How many recursive times one can add a half of itself to an even number or, equivalently, what is the largest k such that is a natural number for any even n directly depends on the base 2 representation of n, in particular, the number of n of trailing zeroes in this base. If we consider the Collatz map of Mersenne numbers m for example, which are defined as with , for any of them, one can consecutively multiply by and still yield a natural number for a number of times equal their rank − 1. Indeed, 31, which is written as in base 2 is of rank 5 because ; therefore, if one repeats the action “add to the number+1 half itself”, this yields an even result exactly four consecutive times. Thus, any strictly ascending Collatz orbit concerns only numbers a of rank and is defined by While this may seem partly recreational, this property of Collatz orbits is in fact extremely useful to compress and characterize their non-decreasing segments, as the previous expression describes the one and only way an orbit can increase under the Syracuse action.
Lemma 4. Let a be an odd number of rank 1 that is vertical even; then, is of rank 2 or more, and is vertical even. Let a be an odd number of rank 1 that is vertical odd; then, is of rank 2 or more, and is vertical odd.
Proof. If a is vertical even, it can be written as and this number admits an that is , which is an odd number; therefore, is at least of rank 2.
Moreover, and this number admits a that is , an even number. Now, if a is vertical odd, it can be written as , and and . It follows that admits an and admits a of, respectively, and and that they are both odd. □
Theorem 5. (Rule Two) Let a be a number that is vertical even; then, and for any even k. Let a be a number that is vertical odd; then, and for any odd k.
Proof. If a is vertical even, then it can be written as , where p is necessarily vertical (odd or even). We proved that is then of rank 2 or more and that we have so it is necessarily vertical odd (since is of rank 2 or more) so and, therefore, . This behavior we can now generalize to n because, if a is vertical even with , then the lemmas we used also provide that and therefore is vertical even for any even n because is vertical (even or odd, depending on p only) for any even n.
Now, if a is vertical odd, it can be written as and p is necessarily of rank 2 or more because . Thus, is vertical (even or odd), and therefore, is vertical even. □
Note 3. Observe that, in the process of proving Rule Two, we also demonstrated that any number of rank 2 or more is finitely turned into a rank 1 number of type A by the Collatz dynamic and that any number x of rank 2 or more so that under Rule Two is finitely mapped to a type A number that is vertical even; therefore, proving the convergence of such numbers is enough to prove the Collatz Conjecture. In the upcoming sections, they are called the “” numbers (which one may admit is more practical than calling them “the intersection of residue classes , , and ”), and identified with set .
5.3. Proving Rules Three and Four
Theorem 7. (Rules Three and Four) Let a be a vertical even number with , where n and b are odd; then, . Let a be a vertical even number with , where m is even (zero included) and b is odd; then,
Proof. If , by definition, . Then, As this expression can be divided by 2 no more than twice, we have .
Note that, if , then , which is of course an odd number. Therefore, is vertical odd and ; thus, we proved that .
If , then , so ; therefore, and thus . From this, we can generalize the progression of numbers that can be written , where x is of rank 2 or more. □
Definition 6. Let x be any odd number:
All “Variety S”
numbers above x are written and
all“Variety V”
numbers above x are written or equivalently .
Any number
g that can be written
with
x odd and
may thus be finitely reduced under the Collatz dynamic to a number that can be written either
or
by the repeated following transformation:
Therefore, we indeed have that,
for variety S numbers, , which proves Rule Four and
for variety V numbers, which proves Rule Three because Rule One already provides that .
Just as in the process of proving Rule 2 we previously characterized and compressed the only way in which an orbit can ascend under the Syracuse action, proving Rules 3 and 4 incidentally allows one to compress and characterize the only way in which an orbit can descend under the Syracuse action as well, when is still understood as “the next odd number in the forward Collatz orbit”. If in plain English the ascending part could be described as “add one to a number and then half of the result, and then remove one”, the descending part may be equally described as “remove one from a number and then one quarter of the result, and then add one”. The monotonicity of this iterated transformation only depends on the base 2 representation of the initial number, hence the interest in using as a coordinate system for the Collatz orbits.
5.4. Proving Rule Five
Any type A number of rank 1 can be written , where b is of type B. In proving Rule Two, we showed that any number of rank is finitely mapped by the Collatz dynamics to , which combined with Rule Two itself gives Rule Five.
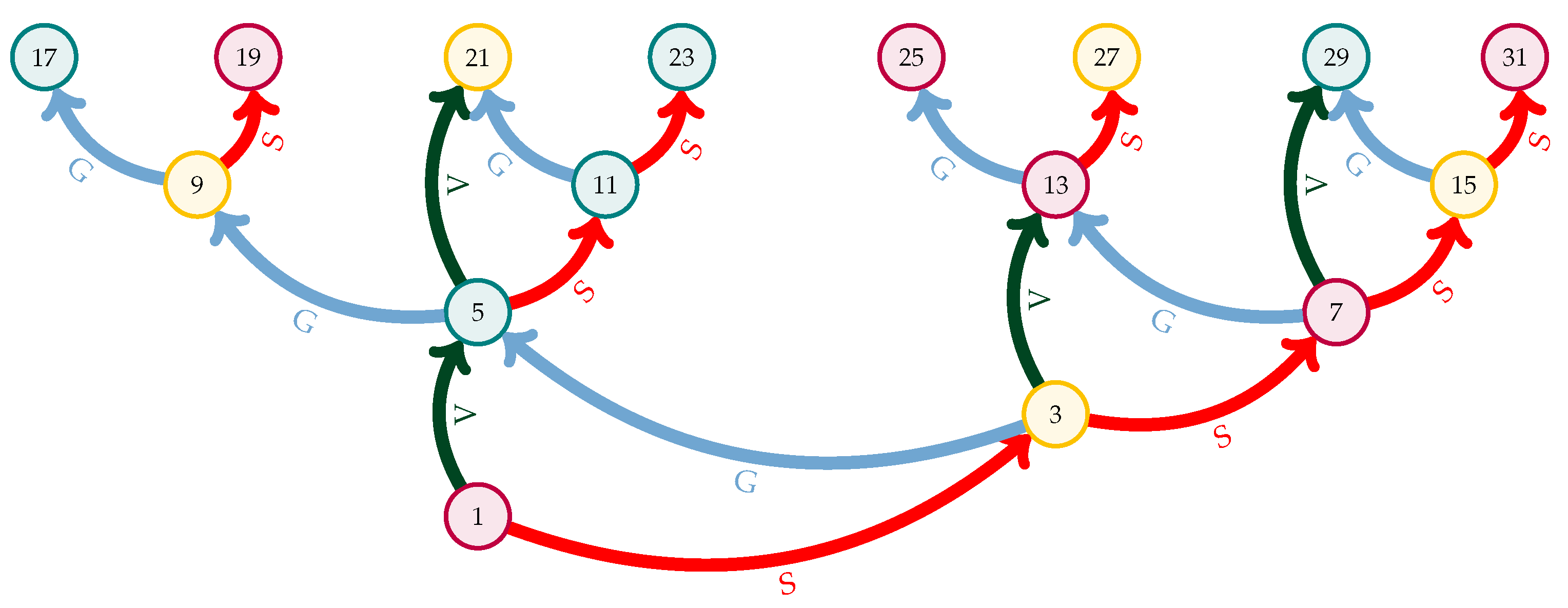
Figure 4 shows a few applications of
Rules Three, Four, and Five plotted in gold.
Rules One and Two are plotted in black. Whenever a number is connected to 1 by a finite path of black and/or gold edges, it is proven to converge to 1.
6. The Golden Automaton
Definition 7. On {; G, S}, the Turing machine recursively calculating the output of Rules One, Two, Three, Four, and Five from number 1 onward, in the natural order on is called the “Golden Automaton”.
6.1. “Golden Arithmetic”
Our purpose is to develop an ad hoc multi-unary algebra that could found a congruence arithmetic specifically made to prove the Collatz conjecture and which we intend as an epistemological extension of modular arithmetic, hence our use of the symbol ≡ in this article rather than the ∼ which is sometimes seen in Collatz-related literature. This “Golden arithmetic” involves words taken in the alphabet , which we call in their order of application, such as in turtle graphics. For example, VGS3 means
Rules 3, 4, and 5 may now be reformulated as such, without loss of generality as long as Rules One and Two are still assumed:
Rule Three: Let b be of type B; then, from b. We will all this action and it is defined in .
Rule Four: Let c be of type C; then, from c. We call this action and it is defined in .
Rule Five: Let a be of type A; then, from a. We call this action and it is defined on .
As
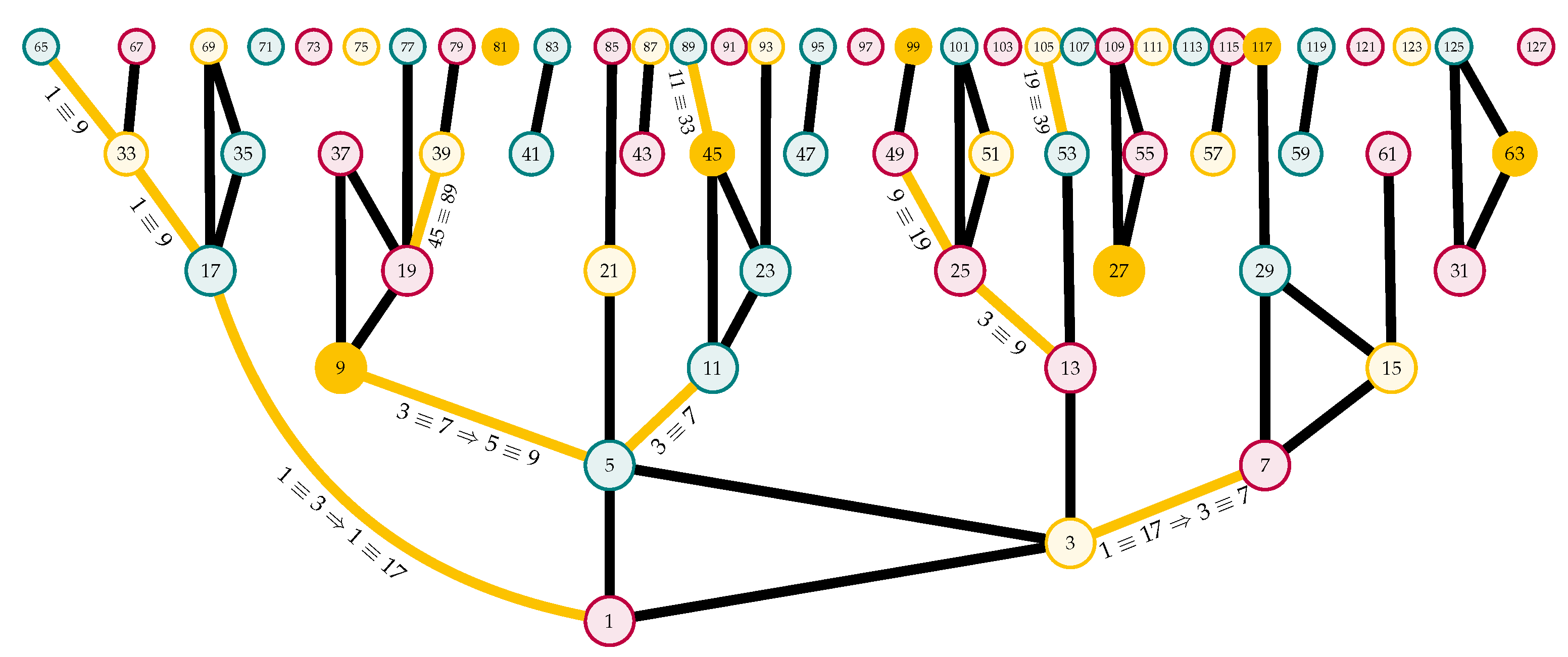
Rules One and Two ensure that the quiver generated by the Golden Automaton branches, with each type B number that is vertical even providing both a new A type and a new B type number to keep applying, respectively, Rules 5 and 3, we may follow only the pathway of type A numbers to define a single non-branching series of arrows, forming a single infinite branch of the quiver. The latter, if computed from number 15, leads straight to 31 and 27, solving a great deal of other numbers on the way:
Again, it is in no way a problem but rather a powerful property of the Golden Automaton that this particular quiver branch already covers 19 steps because each of them branches into other solutions.
We may follow another interesting sequence to show that, in the same way that Mersenne number 15 finitely solves Mersenne number 31, Mersenne number 7 solves Mersenne number 127. This time, we follow a different branch of the Golden Automaton up to , which we proved is written because 127 is the Mersenne of rank 7.
By Rule 4, we have the first equivalence and .
Therefore, by Rule 2, we also have .
Rule 3 gives and again .
The cases of 15 proving the convergence of 31 and 27 and of 7 proving the one of 127 naturally leads us to the following conjecture:
Conjecture 1. Suppose that all odd numbers up to are proven to converge to 1 under the Collatz dynamic; then, the Golden Automaton finitely proves the convergence of those up to in Peano Arithmetic.
Indeed, we already have that the Golden Automaton starting with 1 proves 3 by Rule One; then, 3 proves all numbers from 5 to 15, which in turn prove all numbers from 33 to 127. In the next subsection, we render larger quivers generated by the Golden Automaton to provide a better understanding of their geometry and fundamental properties and to demonstrate why it is so and, more generally, how, granted Goodstein sequences converge (meaning this requires the axiom of choice), it can be proven that they can reach any number in .
7. The Golden Automaton Well-Behaves as a Collatz Convergence on the Binary Tree
Let us now represent each odd number in the binary tree over with a cell having only three possible states:
Black, meaning the odd number is not (yet) proven to converge under the iterated Collatz transformation or, equivalently, that it is only equivalent to another black number;
Gold, meaning the odd number is proven to converge and the consequences of its convergence have not yet been computed, i.e., it can have an offspring; and
Blue, meaning the number is proven to converge and the consequences of its convergence have been computed i.e., its offspring has already been turned gold.
In this ad hoc yet simpler “Game of Life”-like zero-player game, each gold cell yields an offspring and then turns blue, and whenever a cell is blue or gold, the odd number it represents is proven to converge. Starting with one cell colored in gold at the positions 1, the game applies the following algorithm to each gold cell in the natural order of odd numbers:
Rule 1: if a cell on x is gold, color the cell on in gold;
Rule 2: if a cell on x is gold, color the cell on in gold depending on the precise conditions of rule 2;
If a cell on x of type A is gold, then color the cell on in gold;
If a cell on x of type C is gold, then color the cell on in gold; and
After applying the previous rules for a gold cell, turn it blue.
Note that, when applying on a type B number equivalent to Rule 1, then for , the algorithm needs not implement a defined and we can in fact compress it to only four rules.
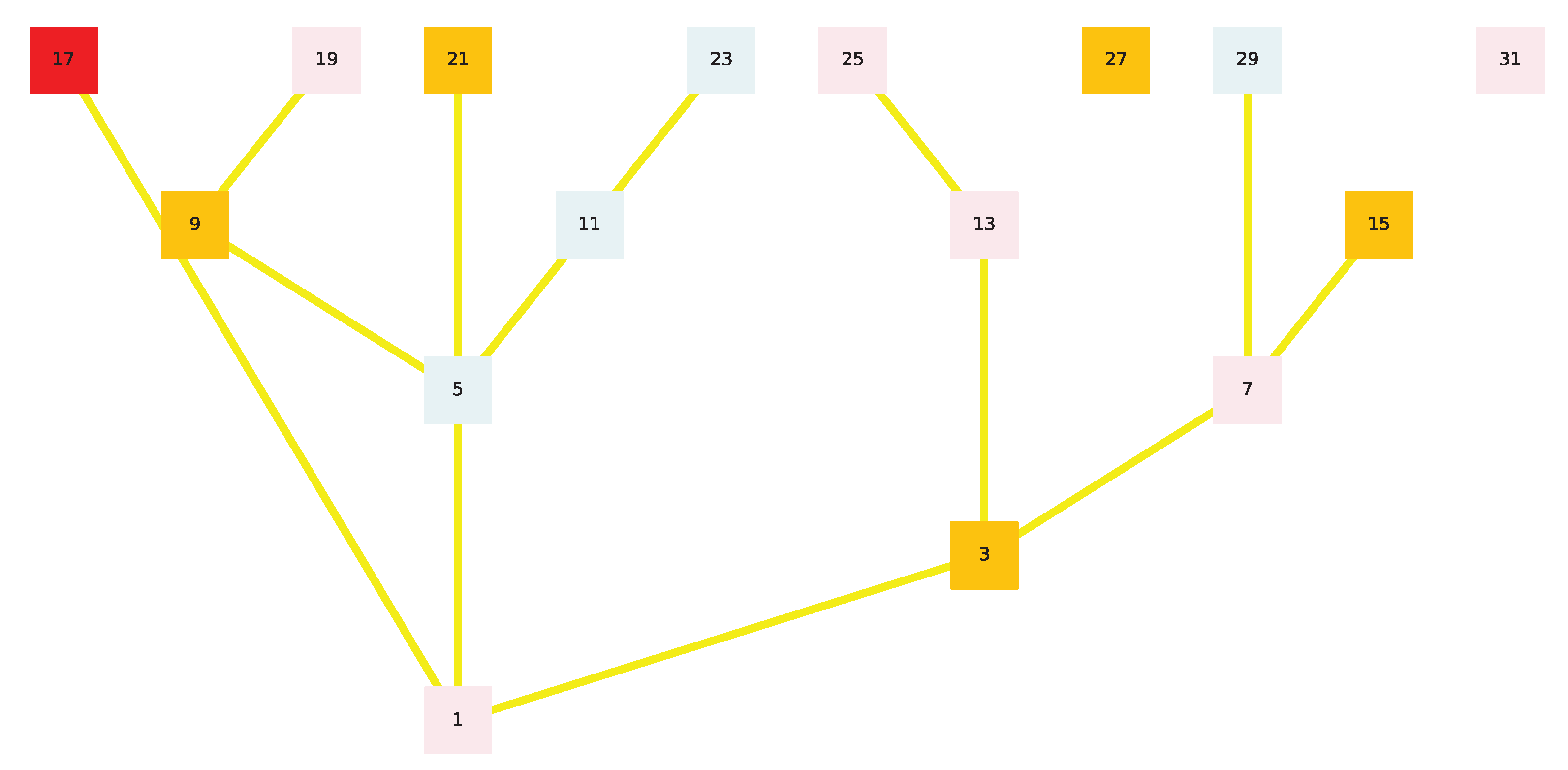
Whenever a complete series of odd numbers between and is colored in gold, the game takes it and returns what we call its "computational bonus" namely all numbers that are higher than are colored blue and gold, thus giving a clear measurement of the algorithmic time it takes the Golden Automaton to prove the convergence of each complete level of the binary tree over . From there, we later plot the evolution of this bonus on linear and logarithmic scales.
Figure 5 illustrates the game we defined for the case n = 6. On the middle image, row {5;7} was solved with a computational bonus of eight numbers also solved above it. On the right image, row {9; 11; 13; 15} has a computational bonus of 6. As number 1 is the neutral element of operation
, we leave it in gold during the simulations.
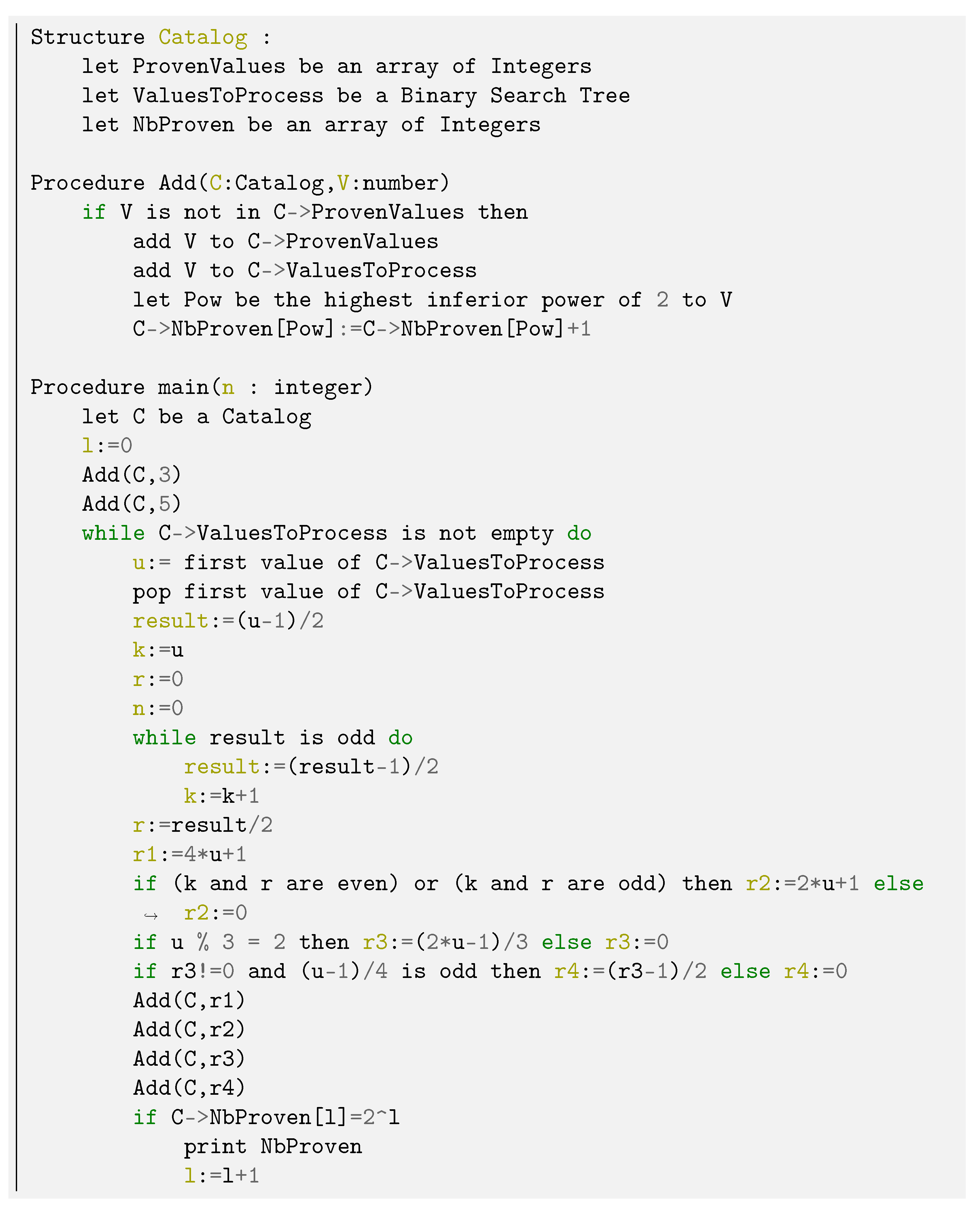
Note that this first implementation of the Golden Automaton was made in Python to streamline its graphical output but that a later barebone version for maximal scalability has also been implemented in C++, this time with no graphical output. The Python version is called “GAI” and the C++ one is called “GAII” (see
Section 8).
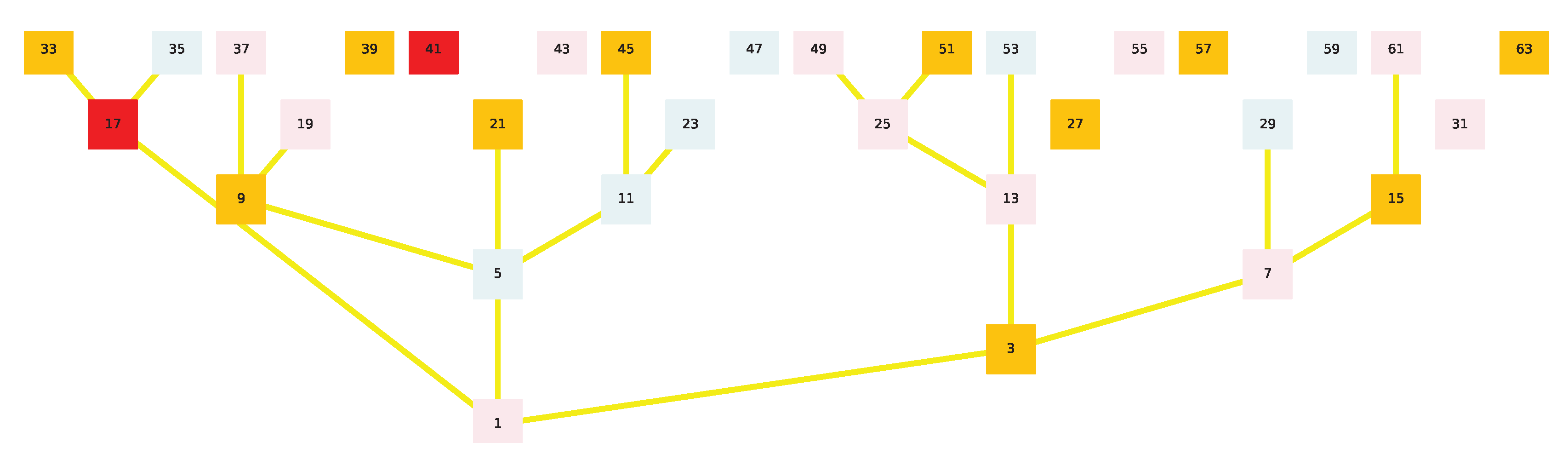
Now that the functioning of the Golden Automaton appears in a clearer way, in spite of the seeming complexity of its rules, we can scale it up to n = 12, which is detailed in the next six figures (
Figure 6,
Figure 7,
Figure 8,
Figure 9,
Figure 10 and
Figure 11) (produced by GAI):
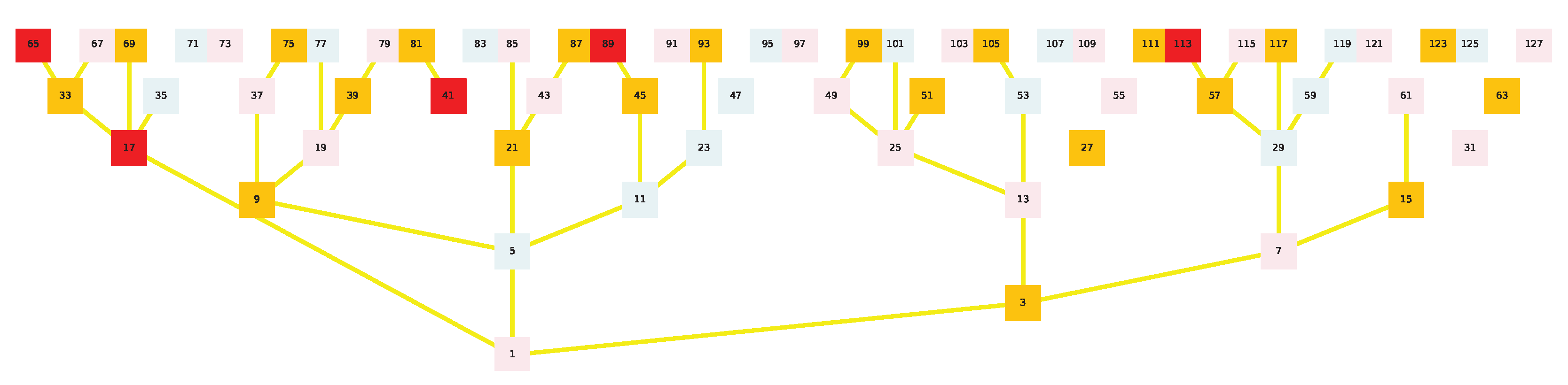
To facilitate the observation of each row of the binary tree being covered by the Golden Automaton, we now zoom into each of them individually(
Figure 8,
Figure 9,
Figure 10 and
Figure 11):
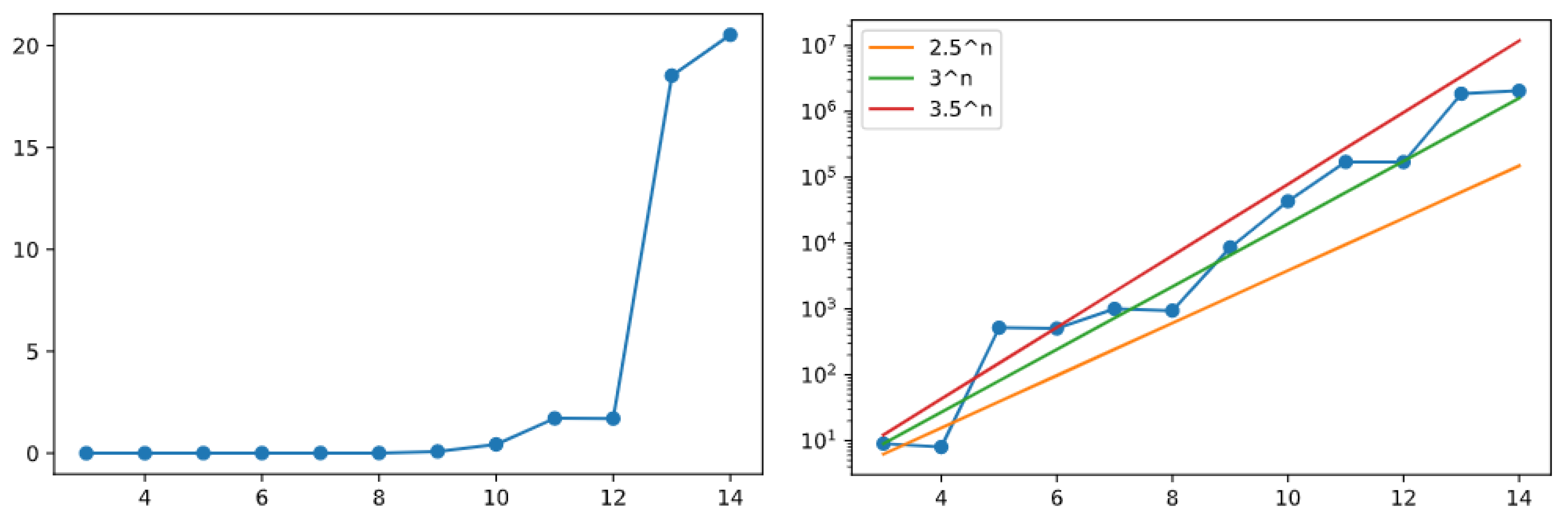
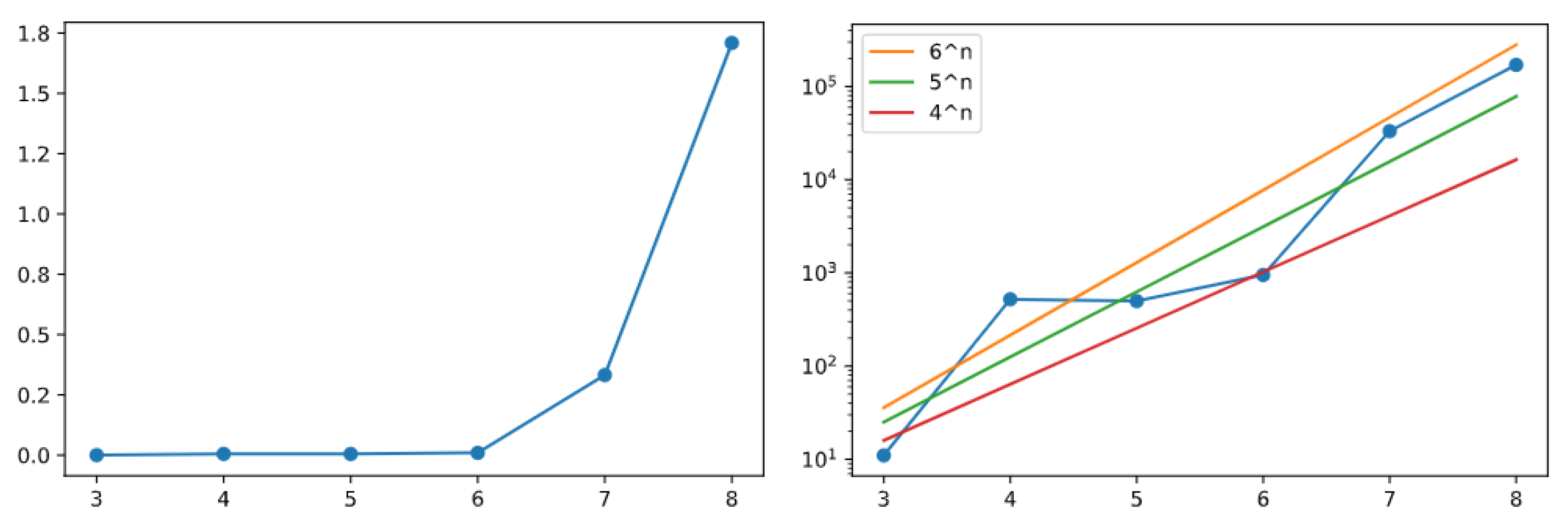
The charts shown in
Figure 12 (created out of the results obtained by GAI) now plot the
bonus above any row
n of the binary tree when the Golden Automaton just finished proving its entire convergence. The chart on the right plots the result against a logarithmic scale, with progressions
(orange line),
(green), and
(red) in comparison, giving an early indication of the linear behavior of the Golden Automaton at the logarithmic scale, solving the rows of the binary tree in their natural order and having also solved about
additional odd numbers above any full row
that it just solved.
We also investigated the behavior of the Golden Automaton when mapped on the ternary tree over odd numbers, that is, the set of odd numbers endowed with operations
. The automaton still demonstrated the entire rows
one after another, this time with about
extra numbers solved above each row. These graphs are shown in
Figure 13 (created out of results obtained by GAI).
From there, we can thus provide two strategies to finalize a proof of the Collatz conjecture. The first would be to demonstrate that the Golden Automaton defines a game that is strictly simpler than a Hydra game over the graph of all unsolved numbers up to any arbitrary odd integer. The second would be to demonstrate that the comparative branching factor of the Golden Automaton, as it is diagonal to the binary tree, is strictly above 2 and that, thus, the population of solved dots can only finitely take over the population of unsolved ones, or put in another way, that the basin of attraction of any supposedly diverging odd number grows too fast not to collide with the basin of number 1.
8. Cost and Complexity of the Algorithms for Linearizing the Collatz Convergence
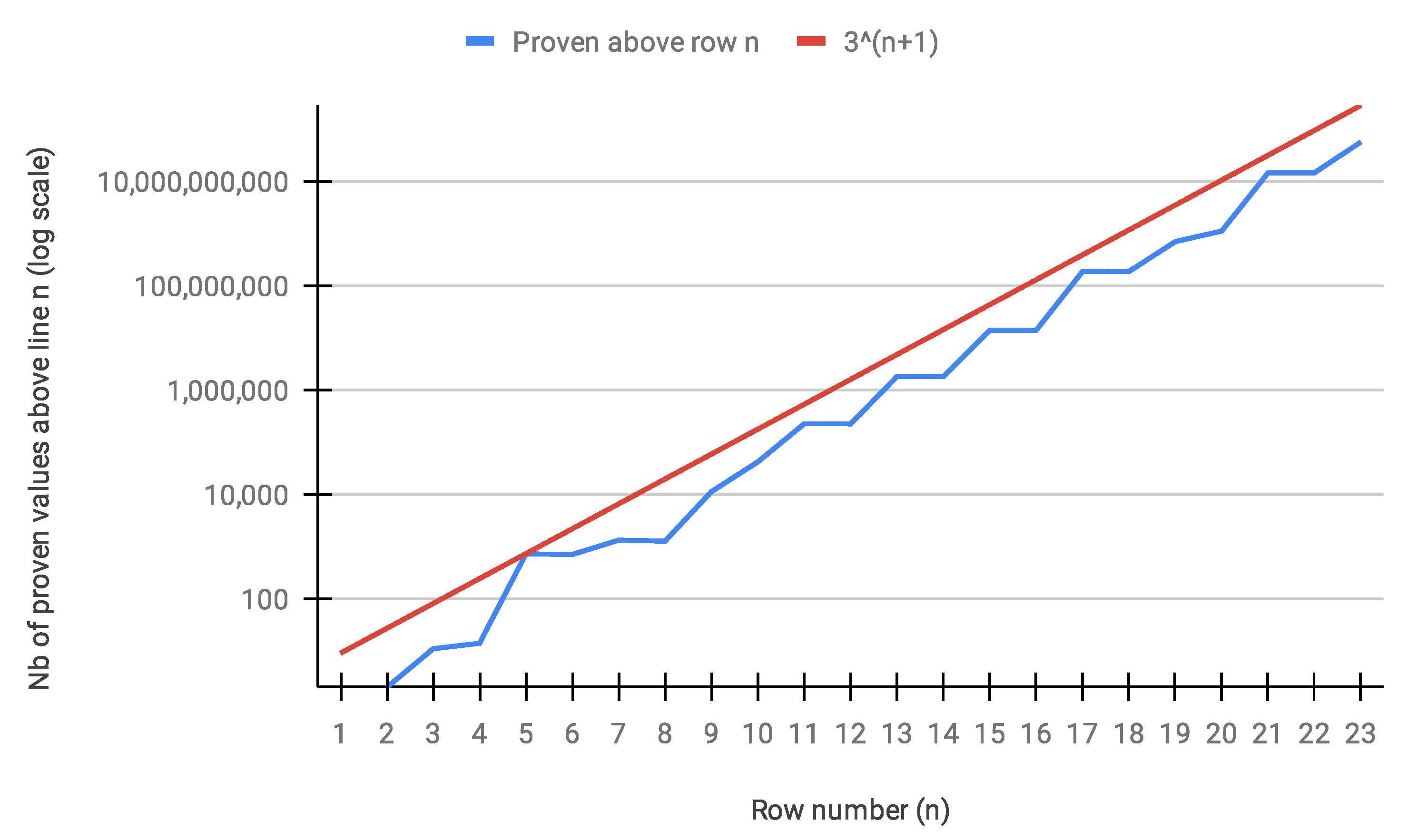
Following insightful comments from the reviewers, a second, leaner version of the Golden Automaton was written in C++ by Baptiste Rostalski, an intern at Strasbourg University’s department of computer science, which made it possible to push the results to line 23 (that is, in the binary tree) to further study its algorithmic complexity, in particular, to which extent the proportion of unproven nodes above any proven line n decreases in time. Here, we thus further describe the first version of our algorithm (“Golden Automaton One” or “GAI”, implemented in Python) and the second, “lean” one (“Golden Automaton Two or “GAII”, implemented in C++) for maximal scalability and the reproducible metrics it outputs.
8.1. Golden Automaton I (Implemented in Python)
The purpose of this first implementation, although it was conceived with scalability in mind, remained modularity and the ability to easily output representations within the binary tree (in 2D and 3D with Blender for the 3D outputs). To minimize complexity, all numbers that have just been proven are stored in an array and sorted by size. To make sure no new number is included in this array, it is compared with a second array storing all previously used numbers, the relevant rule introduced in
Section 6.1. (The previously used numbers are now in blue in the 2D representation of
Section 7. A binary search function then executes all searches, and a binary insert function executes all inserts. When a number is not included in the second array storing the already used numbers, it is inserted at the correct position of the first array of the proven numbers. After applying all five rules to all numbers in their normal ascending order, GAI deletes it from the first array (proven numbers) and inserts it into the second one (used proven numbers). Thus, the algorithm always takes the first of the proven number and applies it, depending on its type—see Definition 4). In this way, the algorithm ensures that the rows is completed as soon as possible. The algorithm counts the proven numbers per row to output the
bonus as soon as it is completed. Remember that the
bonus is the amount of proven numbers in all rows above the completed row. This procedure allows us to follow the exact sequence of the proven numbers as well as the exact time of completion of the individual rows.
8.2. Golden Automaton II (Implemented in C++) and Its Output
While the initial Python versions of the Golden Automaton were very modular and flexible enough to produce various graphical outputs on the fly, during the review process of this article, we also developed a barebone version to be executed in C++, which reached line 23. The exact algorithm of this version is described in the
Appendix A. The first confirmation it provided was that the Golden Automaton solved every row while never proving more than
extra numbers above any of them which is shown in
Figure 14.
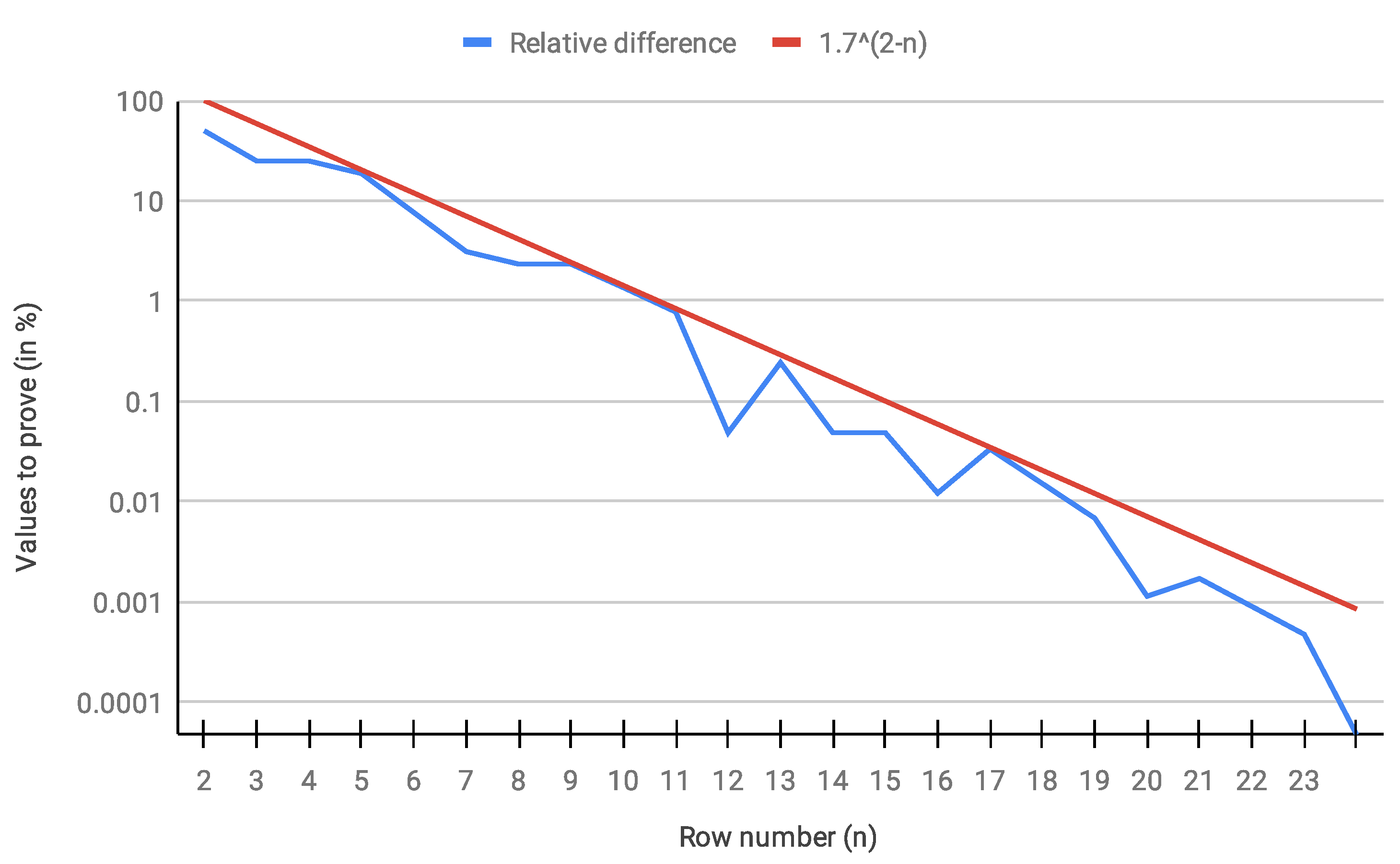
An even more interesting figure was the evolution of the relative difference between any row
n and its successor
, meaning, when row
n is finished, how many numbers still remain to be solved in row
, in which we confirmed an exponentially decreasing trend (see
Figure 15). This result somehow improved in [
16] in that it evidences a trend of the frequency of presumed unsolved numbers decreasing exponentially with
n, yet while Tao obtained that the complement of its set of presumed unproven numbers attained only almost bounded values, here, the complementary set is that of proven numbers, of which the orbit is therefore not almost bounded but bounded.
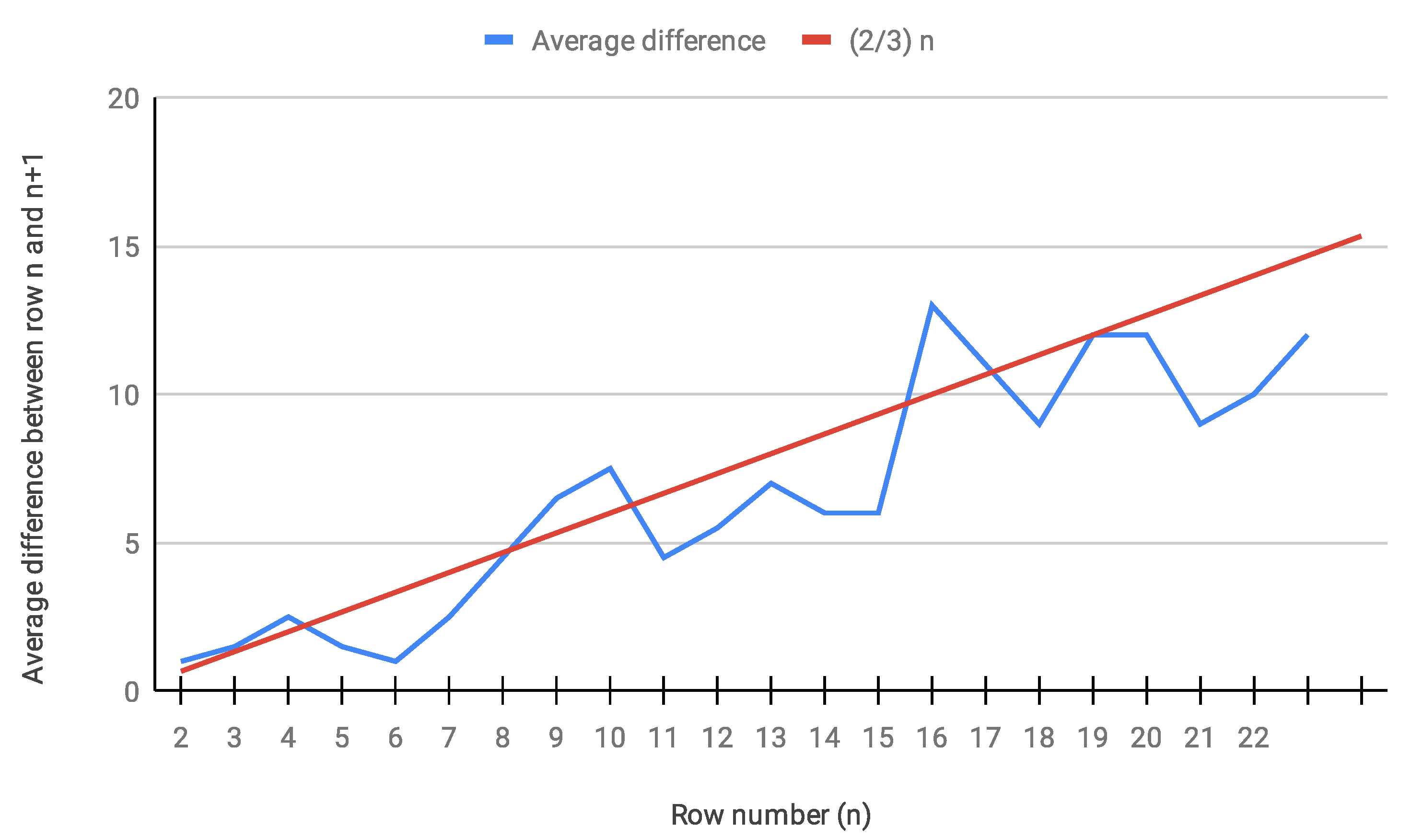
Averaged across pairs of successive rows, the amount of presumed unproven numbers in every row
when row
n had been proven to exhibit a linear tendency (see
Figure 16).
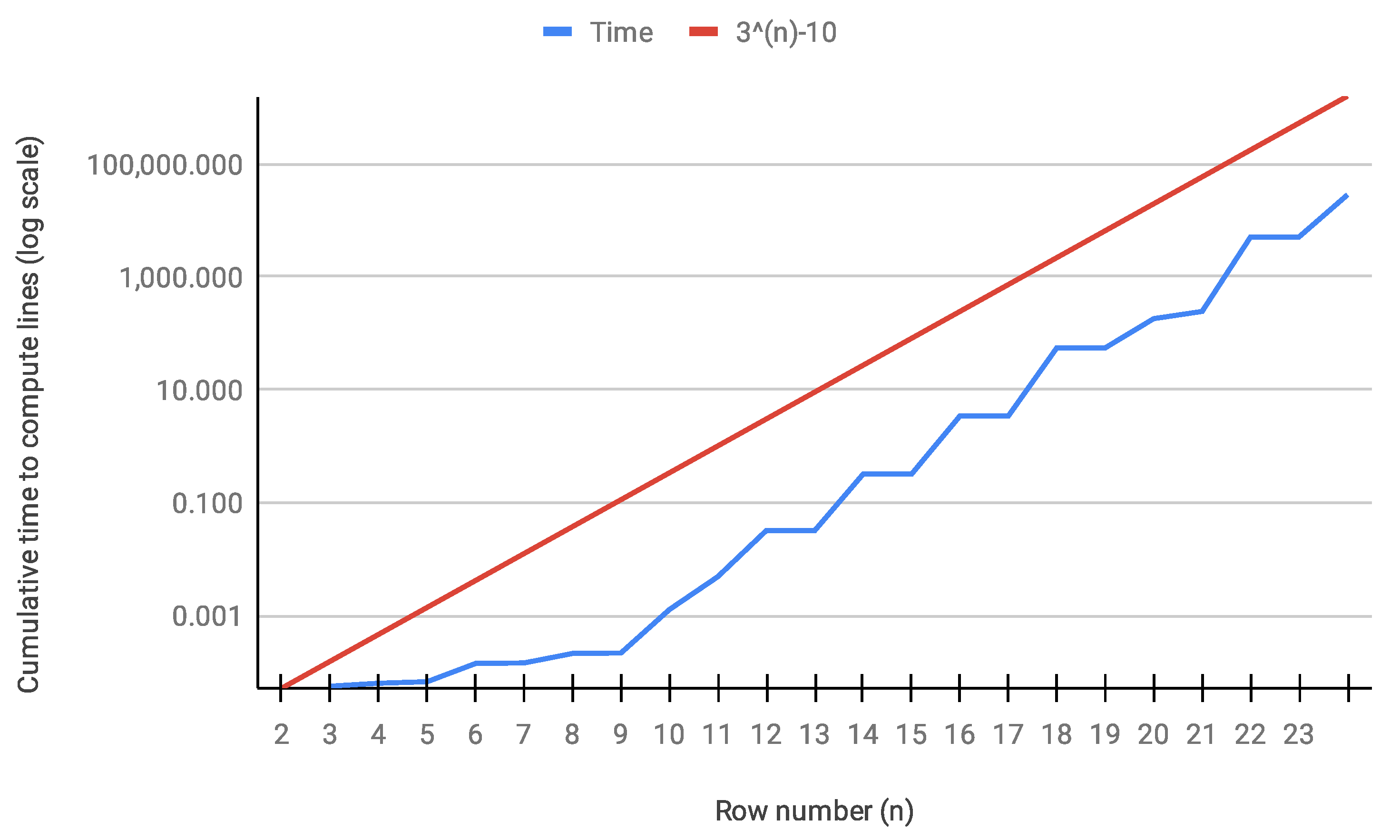
Although the Golden Automaton II is RAM-intensive (needing a little less than 1.5 TByte of Random Access Memory to go all the way to row 23), we confirmed experimentally that its computing time, which is shown in
Figure 17, in
n never exceeded
, which, given its barebone structure, is in accordance with the observation that the Golden Automaton proved less than
extra numbers above each row
n when it finished.
As Golden Automaton II is based on the same, unchanging five rules we demonstrated at the beginning of this article, we can now posit that its time complexity is below , although we only intend to demonstrate that it is finite with n in the next sections.
9. The Golden Automaton as a Hydra Game
As we mentioned in
Section 2.1 the idea of attacking the Collatz conjecture from the angle of transfinite arithmetic, in particular, the model of the Hydra game is not new, as Arzarello and others considered it in 2015 [
28]. Both Goodstein sequences and Collatz sequences iterate base changes, but the Collatz sequences do so in a much less divergent manner, involving only bases 2, 3, and 4, with each critical step of their trajectory obeying the following rules:
If a number is written in base 2, then it is finitely mapped to the result of operation G on the number written in base 3 with . Note that this is the one and only way an orbit can grow in the Collatz dynamics.
If a number is written in base 4, then it is immediately mapped to a number written in base 2.
If a number is written in base 2, then it is equivalent to the result of operation S on in base 3 with r as the base 3 representation of s.
If a number is written in base 2, then it is equivalent to in base 3 with w as the base 3 representation of v.
The purpose of this subsection is to identify provable fundamental properties of the Golden Automaton by computationally scaling it up on the full binary tree over
,
but this time studying not the vertices but the edges of the graph. To streamline its algorithmic scaling, we use the simplified rules we defined in the previous subsection, again, without loss of generality. Our precise purpose is to pave the way for a formal demonstration that proving the convergence of odd numbers up to
n is always isomorphic to a Hydra game, which justifies that we now study edges and not vertices. In
Figure 18,
Figure 19,
Figure 20 and
Figure 21, we color all of the elements of
, for example
, in red; as we demonstrate in the next section, they are precisely from the “heads” of the Hydra Game.
Theorem 9. If Goodstein sequences converge, the Collatz conjecture is true.
Definition 8. A
Hydra
is a rooted tree with arbitrarily many and arbitrarily long finite branches. Leaf nodes are called
heads. A head is
short
if the immediate parent of the head is the root and
long
if it is neither short nor the root. The object of the
Hydra game
is to cut down the Hydra to its root. At each step, one can cut off one of the heads, after which the Hydra grows new heads according to the following rules:
If the head was long, grow n copies of the subtree of its parent node minus the cut head, rooted in the grandparent node.
If the head was short, grow nothing.
Lemma 10. The Golden Automaton reaching any natural number is
at worst
a Hydra game over a finite subtree of the complete binary tree over .
Proof. The essential questions to answer in demonstrating either a homomorphism between a Hydra game and the Golden Automaton reaching any odd number, or that the Golden Automaton is playing at worst a Hydra game are as follows:
These questions are answered in detail below. □
Definition 9. A type A number that is
vertical even
is called an . The set of numbers is . Type B numbers that verify and type C numbers that verify under
Rule Two
are called
Bups
and
Cups, respectively.
9.1. What Are the Hydra’s Heads?
numbers are the heads of the Hydra. They are 12 points apart on (24 in nominal value, e.g., 17 to 41), and any Bup or Cup of they represent under Rule Five is smaller than them since action strictly decreases. Thus, up to the nth , there are (Bups + Cups) of rank 2 or more and half of them are equivalent to those (e.g., between 17 and 41, Bup 27 is equivalent to 41, which is equivalent to Cup 31 by Rule Four).
9.2. How Do They Grow?
Between any two consecutive in , there are
Moreover, we always have the following:
Let b be of type B; there are numbers of type that are smaller than ;
Let c be of type C; there are numbers of type that are smaller than ;
Let 3c be of type B, where c is of type C; there are numbers of type up to included; and
Let 3a be of type B, where a is of type A; there are numbers of type smaller than ,
which define the growth of the heads. Any supposedly diverging forms a Hydra, as contains an image of all undecided Collatz numbers and any non-decreasing trajectory identifies a subtree within this set.
9.3. Does the Golden Automaton Play a Hydra Game?
It could be demonstrated that the Golden Automaton plays an even simpler game as it branches and thus cuts heads several at a time—unlike Hercules in the regular Hydra game—in particular cutting some long heads without them doubling. (The reason the Golden Automaton dominates so fast is that it plays a significantly simpler game one could call “Hecatonchire vs. Hydra”, namely a Hydra game where Hercules’ number of arms also multiplies at each step.) However, as this is needless for the final proof, we can now simply demonstrate that, even under the worst possible assumptions, it follows at least the rules of a regular Hydra game.
The computation of that we detailed in Subsection 3.1 is one case of playing the Hydra game by the Golden Automaton; we underlined each use of Rule 5 specifically so that the reader can now report it more easily because, each time this rule is used, a head (that is, an ) has just been cut.
The demonstration that 27 and 31 converge corresponds to the cutting of heads 41 and 161, respectively. This single branch of the automaton having first cut head 17 reaches head 1025 via B-typed numbers 15 and 81. It therefore plays a Hydra game with heads, of which one (17) is already cut at this point and of which at least 8 are rooted (so cutting them does not multiply any number of heads). This process being independent of the targeted number, we now have that the reach of any number by the Golden Automaton is at least equivalent to playing a Hydra game with n heads of which are rooted. Even without demonstrating more precise limit theorems for factors n and m (which could still be a fascinating endeavor), the road is now open for a final resolution of the Collatz conjecture.
From there, indeed, we know from Goodstein [
29] and from Kirby and Paris [
27] that assuming
is well-ordered (that is, assuming the axiom of choice), no Hydra game can be lost. Since we have that reaching any number
n is a Hydra game for the Golden Automaton, we have that the Golden Automaton cannot fail to finitely reach any natural number.
10. The Golden Automaton as a Winning Cellular Game Represented as a 3D L-System, with Some Important Applications in Industrial Cryptography
Beyond graph theory, we want to outline here a different strategy towards a resolution of the Collatz conjecture (this time in Peano arithmetics and thus independently of the axiom of choice) by studying the Golden Automaton as a cellular game invading the phase space defined by the complete binary tree over odd numbers. For this section, we need a 3D representation of the dynamic we studied in
Section 7, designed to specifically display potential collisions between the basins of attraction of number 1 and any supposedly diverging other number. We employ the same game, that is, a zero-player game that is significantly simpler than John Conway’s Game of Life and played on the complete binary tree
, except that we now allow it to start from any point rather than 1 and study its development within the basin of 1. The purpose of this approach is both to identify possibly provable patterns in the way any subbasin would be embedded in the 1-basin and to simply observe whether the five rules, for any point, finitely spawn a population of points between any starting number
x and
that is bigger than
, which would imply that finite collisions between any two basins are inevitable. Moreover, in terms of industrial cryptographic applications, this approach provides the first 3D visualization of the Bocart [
19] proof-of-work using the pseudorandomness of the inflation propensity of Collatz orbits as the asymmetric number-theoretical problem to be used to authenticate blockchain transactions yet that is independent of prime numbers. This 3D visualization, although it does provide novel theoretical insight on the Collatz conjecture, is practically important because it now makes the Bocart proof-of-work scannable, similar to a QR code.
Figure 22,
Figure 23,
Figure 24 and
Figure 25 provide a 3D-Visualisation of the Golden Automaton.
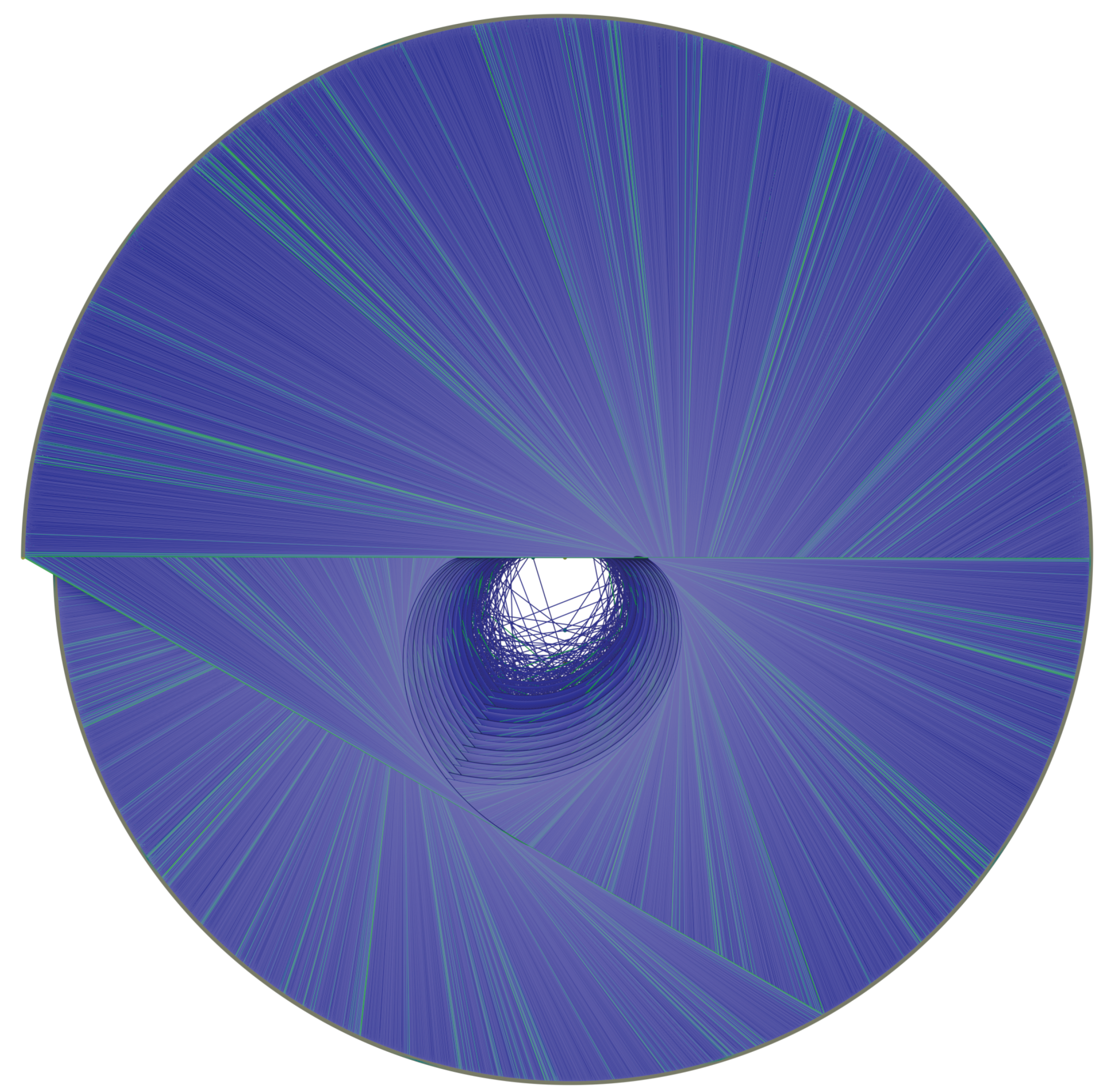
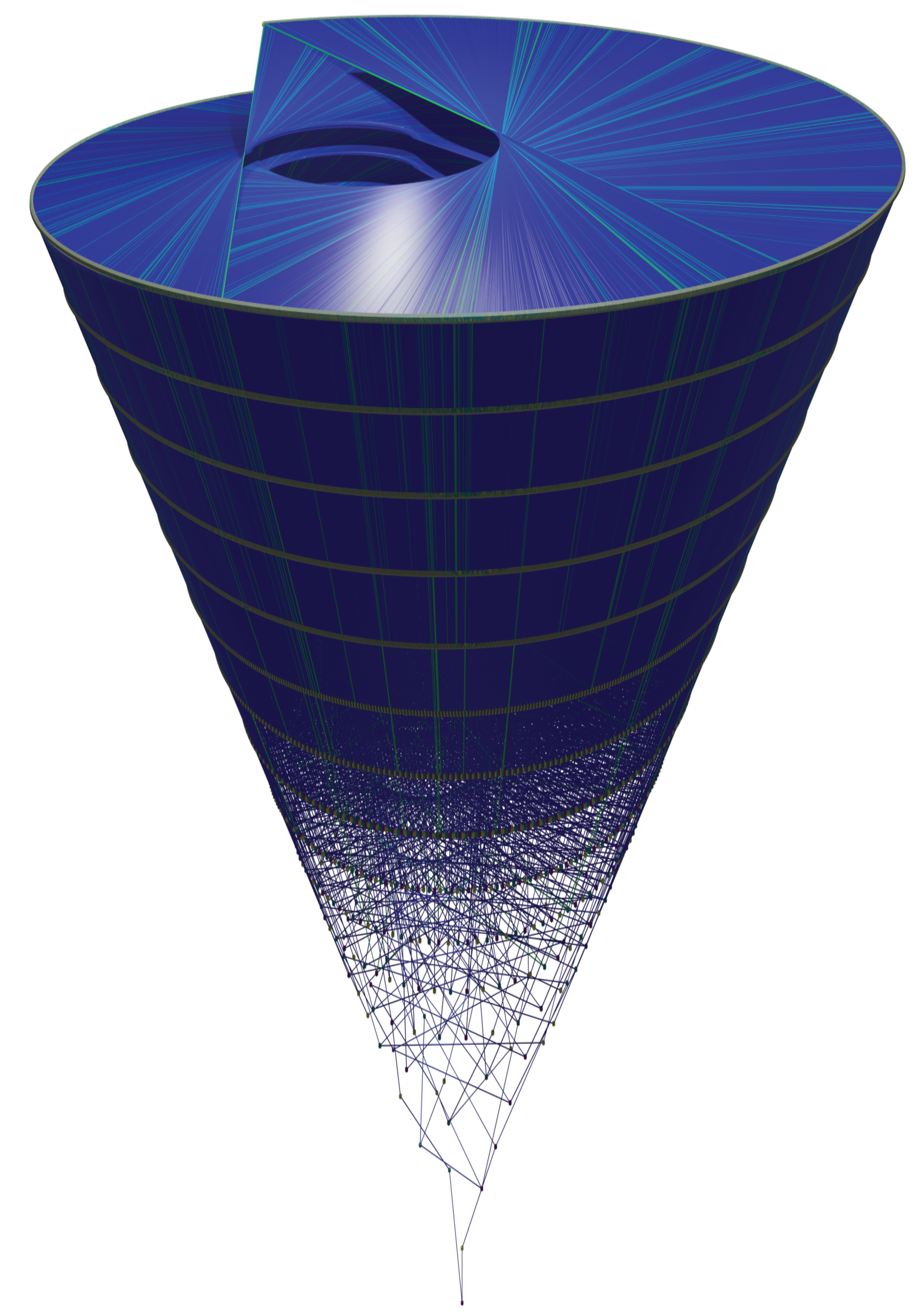
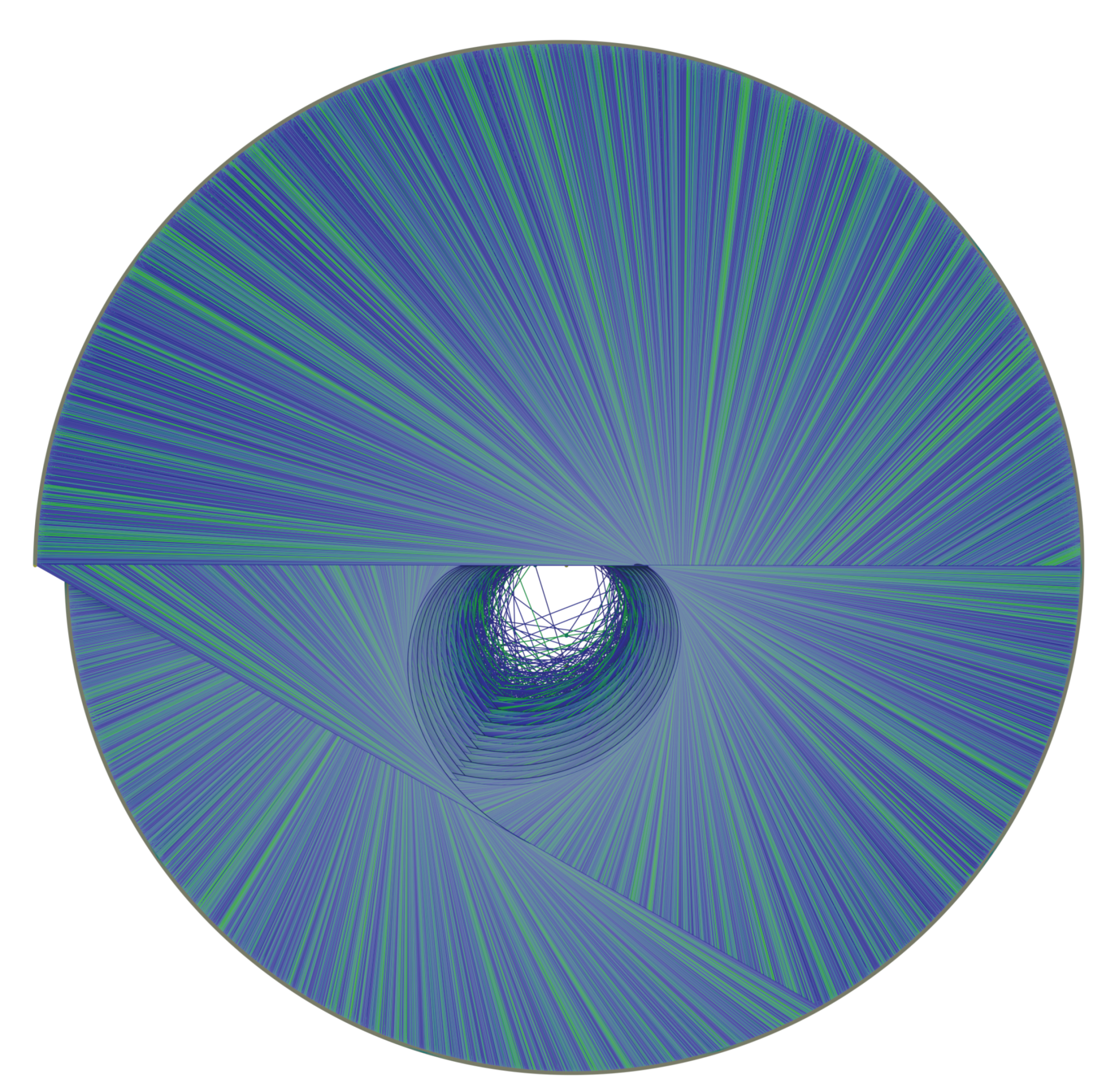
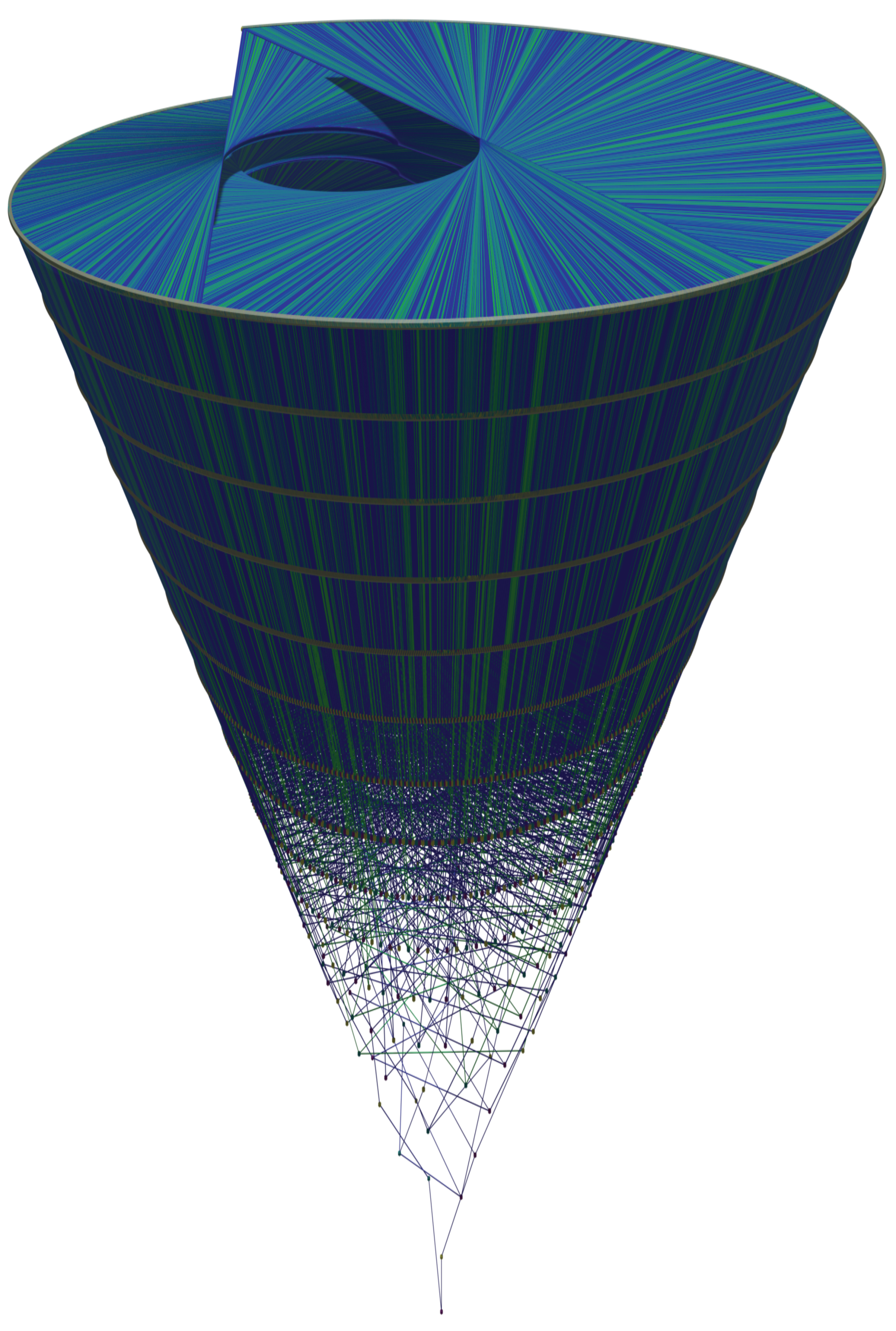
Figure 22 shows an orthogonal view of the Golden Automaton starting from 1 (in blue) merged with another starting from 1457 (in green), which is the first
in the trajectory of 127. We input the
rather than 127 itself to specifically study the impact of divergence on the form of the basin.
Let us now compare the inflation propensity of 31, for which Collatz orbit is much more complex than 127, and observe that, as predicted by the five rules, the figure it outputs now shows a much more voluminous basin of attraction. The reason this result was expected is that, under the five rles, the assumed divergence of a number implies that it leaves a trail of type A numbers (on each of which Rule 5 can be applied) that is strictly proportional to the inflation propensity of its orbit since for any number
x of rank 2 or more, action
outputs a type A number. The following
Figure 24 provides an orthogonal view of the Golden Automaton starting from 1 (blue) merged with one starting from 161 (green), which is the first
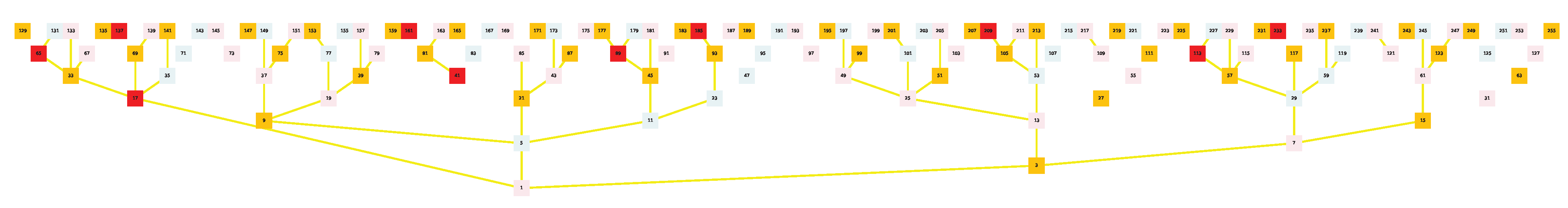
of number 31. As 31 is both lower than 127 in the binary tree and displays a higher orbit inflation propensity, its overlap ends up much larger than that of 127, as
its basin of attraction inflates along with its orbit.The convexoid that is the structure of the center of the basin of attraction of any number appears to be the truncated caustic generated by multiplication by 3 on the binary tree projected on the unit circle. In
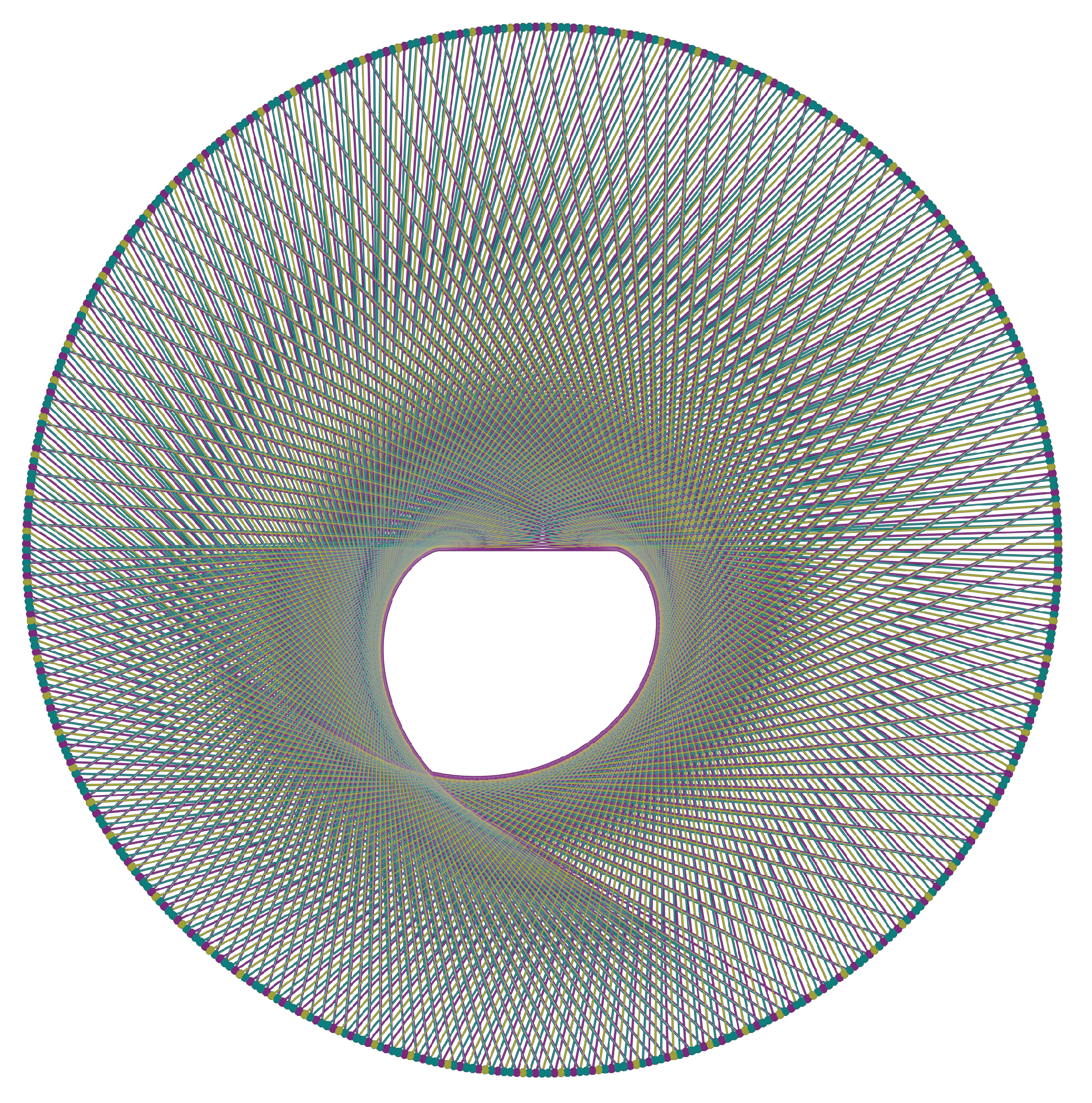
Figure 26, we thus implement the fundamental operations of the ternary tree,
, thus visualizing the way it develops itself on top of the binary tree. Operation
is shown in yellow,
is in purple, and
is in teal. Number 1 is at exactly
, number 3 is at
, number 7 is at
, and number 5 is at
.
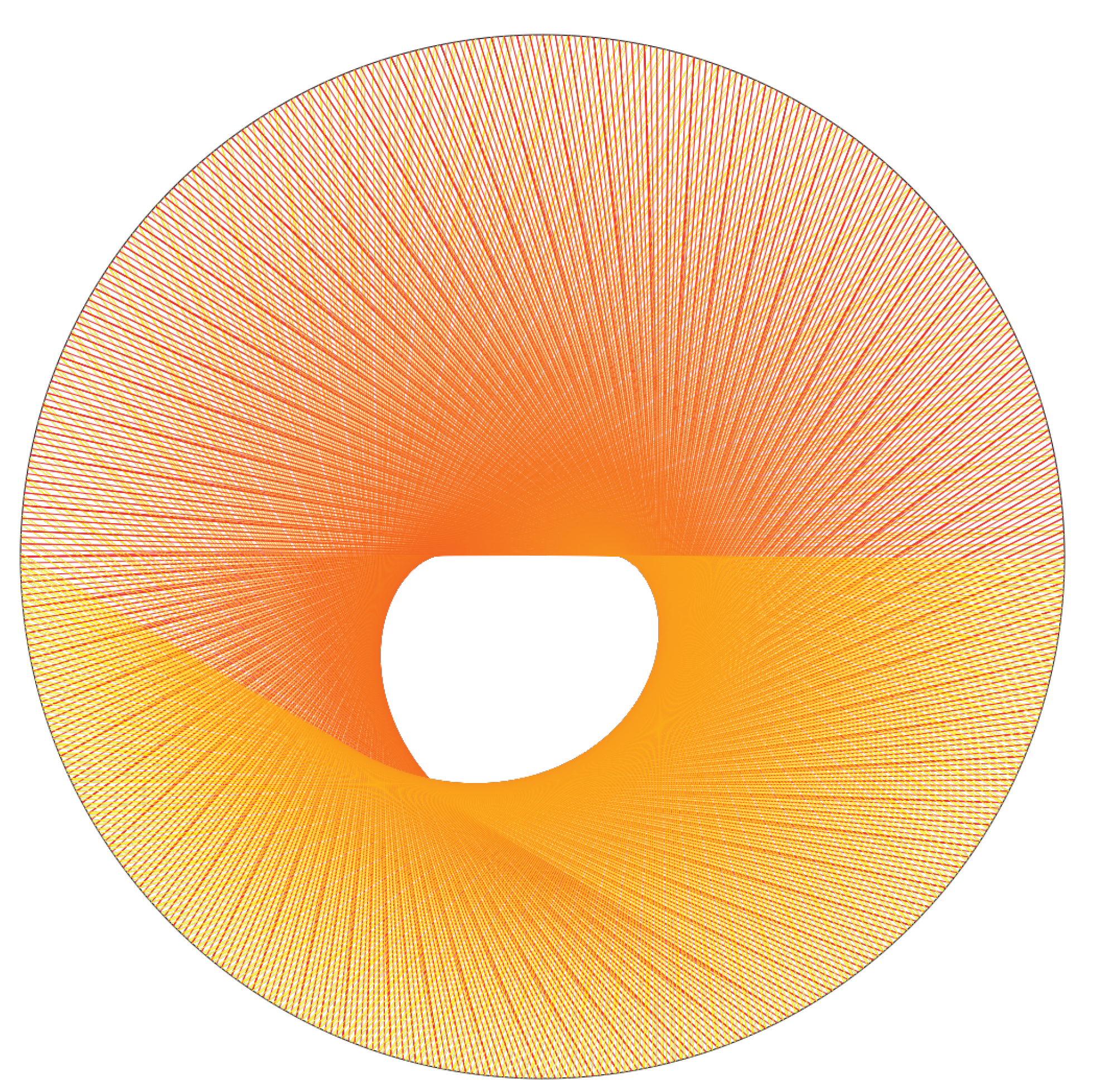
Moreover a truncated caustic generated by the
map on the binary tree is visualized in
Figure 27.
The shape of the truncated caustic that is the envelope of the family of curves generated by the
map over the binary tree embedded on the unit circle gives particular insight into how the chaoticity of conversions between bases 2 and 3 and the chaoticity of the Collatz map are tightly interrelated. Although it was not our initial objective, we may comment that a further understanding of the non-ergodicity generated by the
action on the binary tree, in particular its concentrating Collatz orbits to certain subtrees, may threaten the long-term solidity of the first Bocart proof-of-work, although all the while opening the way to other protocols inspired from it. The following graphs provide some measurements of the non-ergodicity generated by the truncated caustic (
Figure 28).
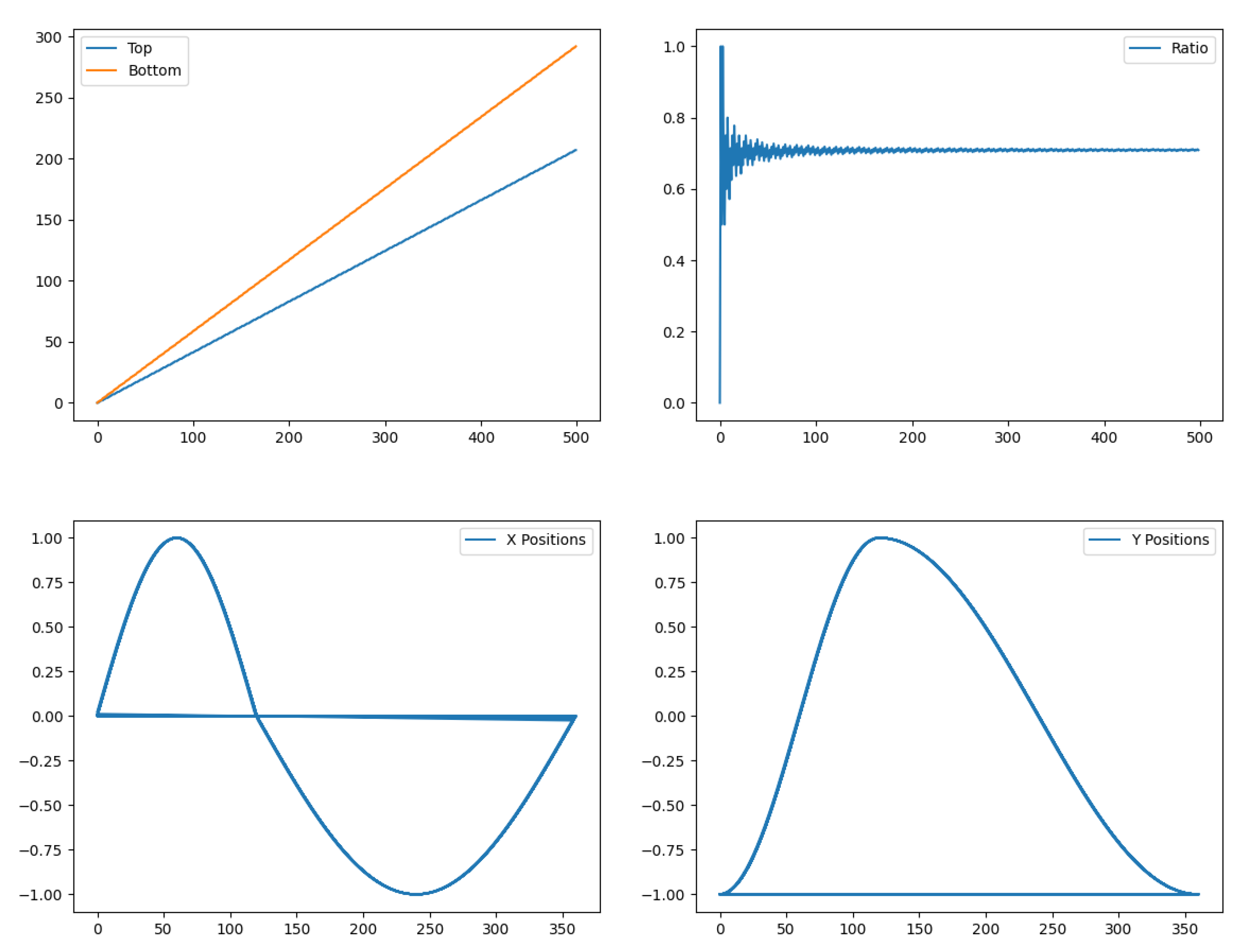
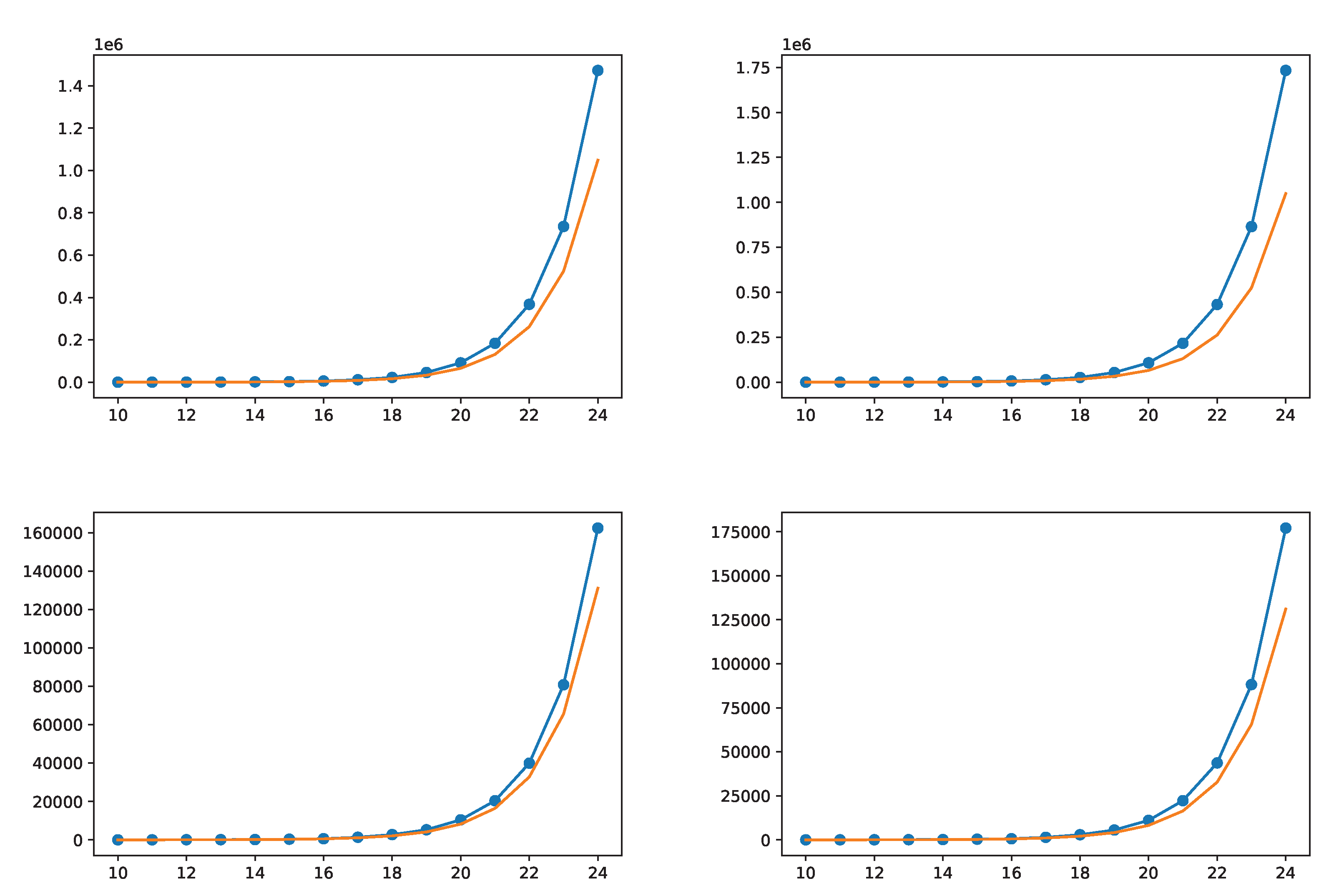
To provide more information about how many numbers the five rules solve,
Figure 29 finally analyzes the offspring they generate from any number, which we believe is the most promising strategy to finalize a Peano-arithmetical proof of the Collatz conjecture. Plotted are the number of points in the basin of attraction of two Mersenne numbers (31 and 511) with or without counting the points generated by their divergence to their first
against how high the basin is calculated. Function
is always plotted as a reference. The purpose is to show that the more the Five Rules are iterated, the more the amount of dots within the basin of attraction increases above
. The top-left figure indicates the number of dots in the basin of 31, and the top-right one indicates those in 161, that is, taking into account the divergence from 31 to 161. The bottom plots represent the basins of attraction of 511 and 13,121, which is the first
in the trajectory of 511, again, to take its divergence into account. The basin of 13,121 does not depart from
as fast as that of 511 but starts from a larger number of dots, generated by the 511–13,121 divergence.
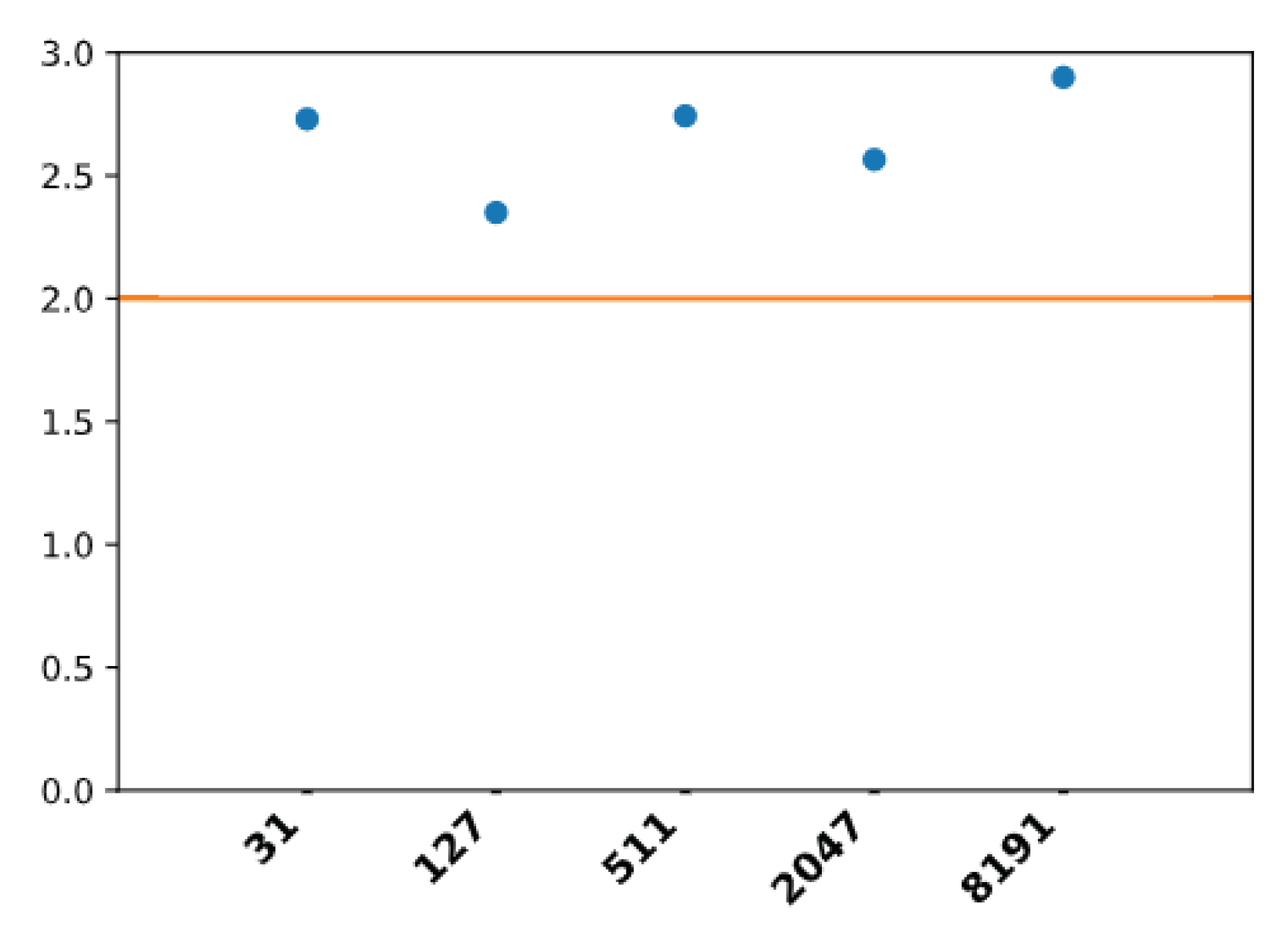
The apparent growth rate of all of the Mersenne numbers from 31 to 8191 is calculated as the solution for
x to
, where
N is the number of dots in the basin of the number that is found between itself and its first
(for example, 161 is the first
of 31) and
n is the number of multiplications by 2 from the initial number that are needed to reach the row of this first
in the binary tree (for example, n = 3 to go from 31 to 161). All of the growth rates are larger than 2 (orange line) (
Figure 30), explaining why the basins of attraction of each of these numbers cannot fail to collide with that of 1.
We already demonstrated in
Section 4 that any
can be written
, and it is precisely the catching of
numbers with a large factor
n by the Golden Automaton that increases the quantity of dots in its offspring per given finite series of rows of the binary tree. Specifically, those
numbers, which are by definition as the ones that can be iterated upon the most by the Golden Automaton are not evenly distributed on the unit circle, and we postulate that this is the most fundamental reason behind the apparent branching factor of the Golden Automaton being strictly greater than 2 in any point we calculated. In turn, if the branching factor of the Golden automaton tends to always be greater than two, it is impossible for two separate basins of attraction to cohabitate on the binary tree.
11. Conclusions
Whenever the Collatz conjecture is studied, one cannot fail to quote Paul Erdős’ famous claim that “mathematics may not be ready for such problems"; depending on one’s epistemological attitude, the quote may either seem discouraging or an incentive to achieve a novel theoretical breakthrough. This is what we attempted in this article, primarily by establishing an ad hoc equivalent of modular arithmetic for Collatz sequences to automatically demonstrate the convergence of infinite quivers of numbers based on five arithmetic rules we proved by application in the entire dynamical system and which we further simulated to gain insight into their graph geometry and computational properties. This endeavor has led us to focus on the origins of the non-ergodicity of the Collatz dynamical system, which we found in the geometric properties of multiplication by 3 on the complete binary tree over odd numbers. These symmetry-breaking properties, indeed, could be further studied in other contexts such as cryptography, harmonic analysis, or the study of L-functions. In particular, following Bocart, 2018 [
19], one can now gain a better insight into the geometric properties of the pseudorandomness generated by Collatz series and, even more, by the Collatz basins.
Furthermore, as Bocart had understood well, studying the Collatz map can lead to promising industrial applications in applied computer sciences, in particular cryptography and financial technologies (fintech). It is possible that the Golden Automaton we described in this article is used to successfully weaken the Bocart proof-of-work developed from the study of the inflation propensity of Collatz orbits; however, the endeavor of developing number theoretical Bocart proof-of-work independent of prime numbers must retain all its industrial interest. As Bocart also understood, it could be possible to extend his work to the 5x+1 map, but following this work, we believe that a stronger Bocart proof-of-work that could not be weakened by the Golden Automaton would be the one based on the inflation propensity of the Juggler sequence, which is well-known for its Collatz-like chaoticity and defined as follows:
As the inflation propensity of the Collatz orbits ultimately depends on the nature of conversions between base 2 and base 3, which Shmerkin [
44] has described as being the fundamental enquiry behind the Furstenberg
conjecture, we predict that advances in this matter would be the likeliest to weaken the Bocart proof-of-work in the future. (Would it be so, though we already mentioned the Juggler sequence as a promising second version of the Bocart proof-of-work, we believe that the study of non-ergodic number billiards could also be most fertile in novel cryptographic protocols) To this end, we believe that the truncated caustic we describe in
Figure 26 would be most relevant. In the larger field of using Physical Uncloneable Functions (or “PUF”) to ensure anonymity in electronic cash transactions, as was studied for example by Fragkos et al. [
45] with their promising paradigm of an “artificially intelligent money”, we believe not only our Golden Automaton but other Number Theoretic models such as primon gas [
46] could provide a useful direction to develop practical encryption protocols beyond the ubiquitous RSA.