End-to-End Delay Bound for VR Services in 6G Terahertz Networks with Heterogeneous Traffic and Different Scheduling Policies
Abstract
:1. Introduction
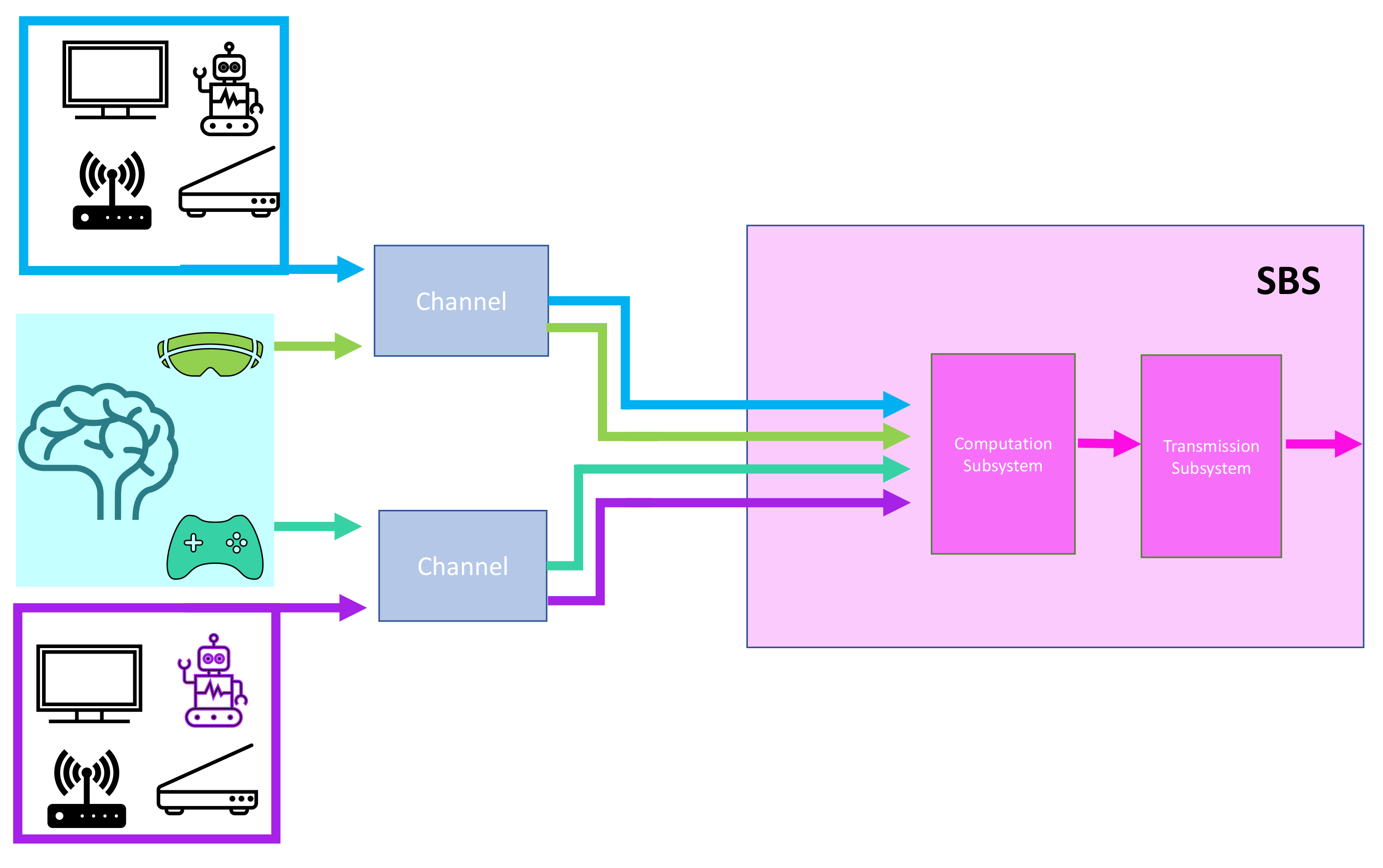
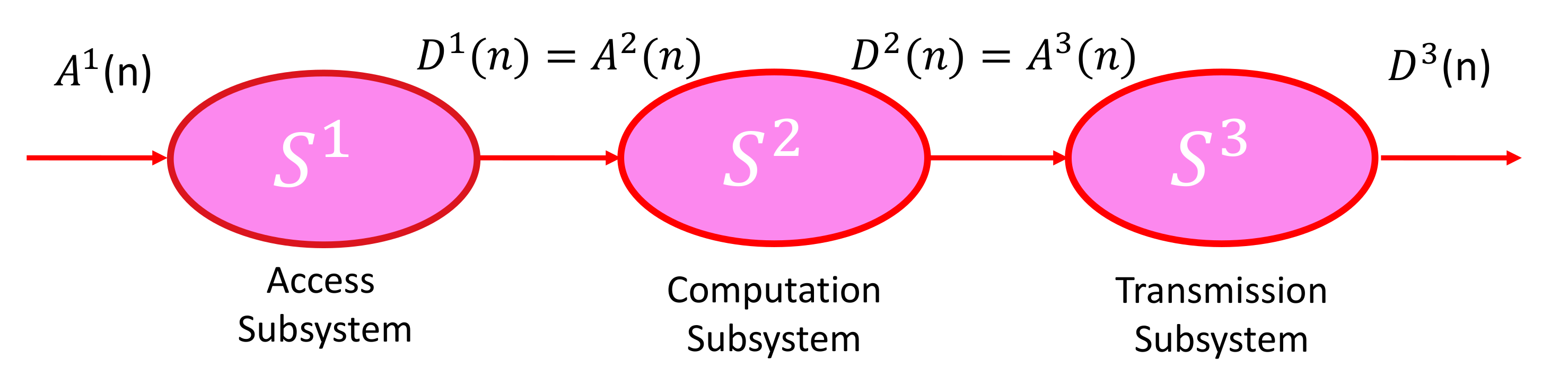
- The system performance analysis of a 6G PEC network’s behavior, operating at terahertz frequencies, in supporting the uVR services. The whole scenario has been modeled as a tandem system, in which the first subsystem represents the access towards the PEC node in order to send the packet needing computation, the second subsystem is the computation module, and the last subsystem models the transmission of the packet back to the user. The access subsystem is without contention, the computation module is shared among different traffic flows heterogeneous in QoS, which compete with each other to receive the service. Then, the tasks pass through the transmission subsystem to be sent back to the device;
- Formulation of the per-flow e2e delay bound of services in the presence of concurrent traffic flows, under the assumption of both the EDF and the FIFO scheduling policies. The proposed per-flow bounds have been modeled by resorting to the application of the SNC principles together with the martingale envelopes, which are a recognized theoretical tool capable of empowering the analytical prediction about the network’s behavior;
- The validation of the proposed analytical bounds that exhibit remarkable closeness between the theoretical results and the actual simulation outcomes, for both the considered scheduling policies. In fact, the per-flow e2e delay bounds achieve accurate performance predictions about the reliability of the PEC network in guaranteeing the QoS constraints imposed by the heterogeneous traffic flows. It is important to highlight that, due to the tightness of the proposed bound to the simulation results, the analytical prediction formulated is particularly suitable in the planning design phase of a next generation network that aims to guarantee fixed QoS requirements, providing the chance to perform proper resource allocation strategies.
2. Related Works
3. System Model
3.1. Channel Model
3.2. Channel Access Scheme
4. Stochastic Network Calculus Principles
Stochastic Network Calculus Fundamentals
5. End-to-End Delay Analysis
5.1. Martingale Bound for FIFO Policy
5.2. Martingale Bound for EDF Policy
- 1.
- , ;
- 2.
- .
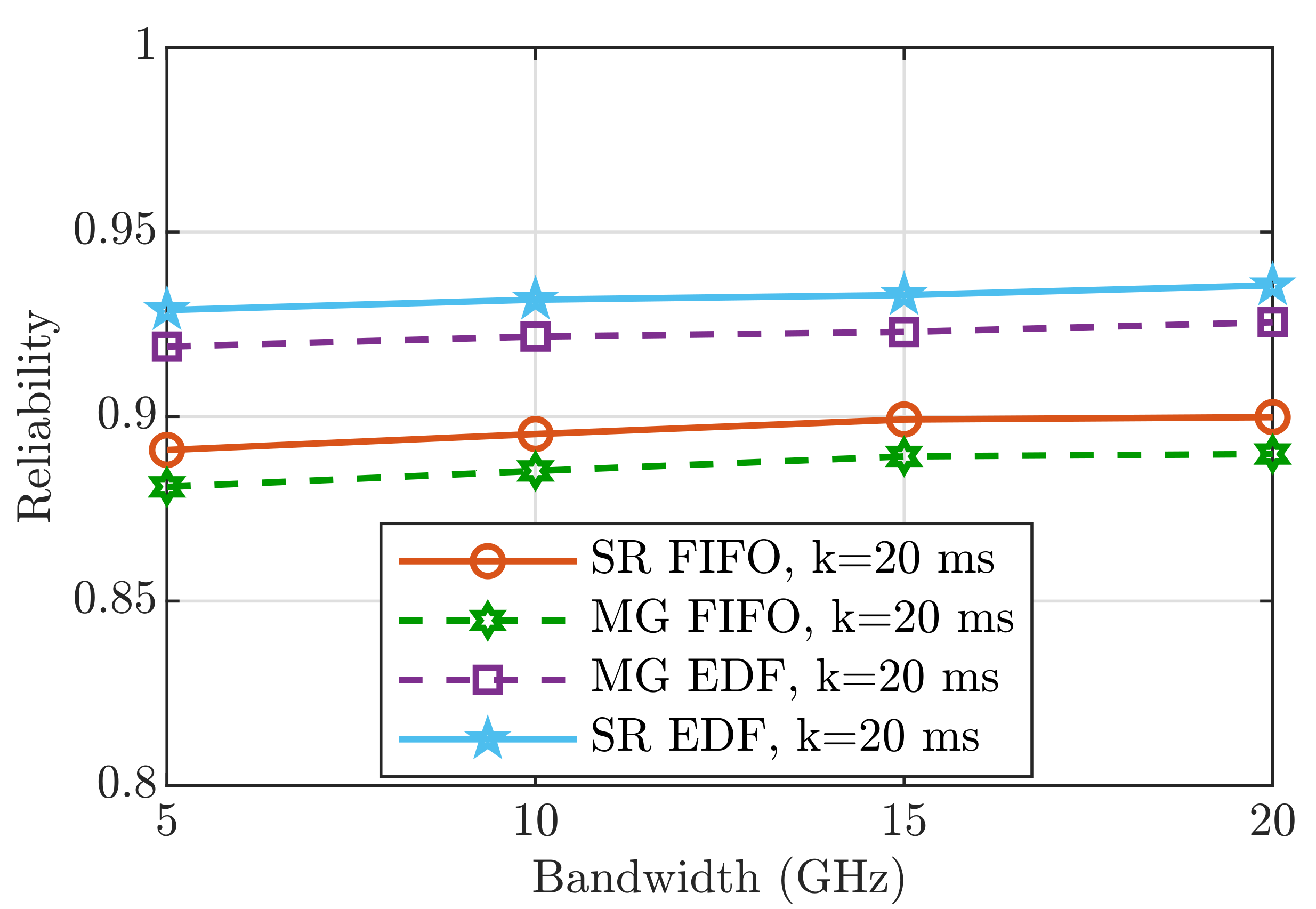
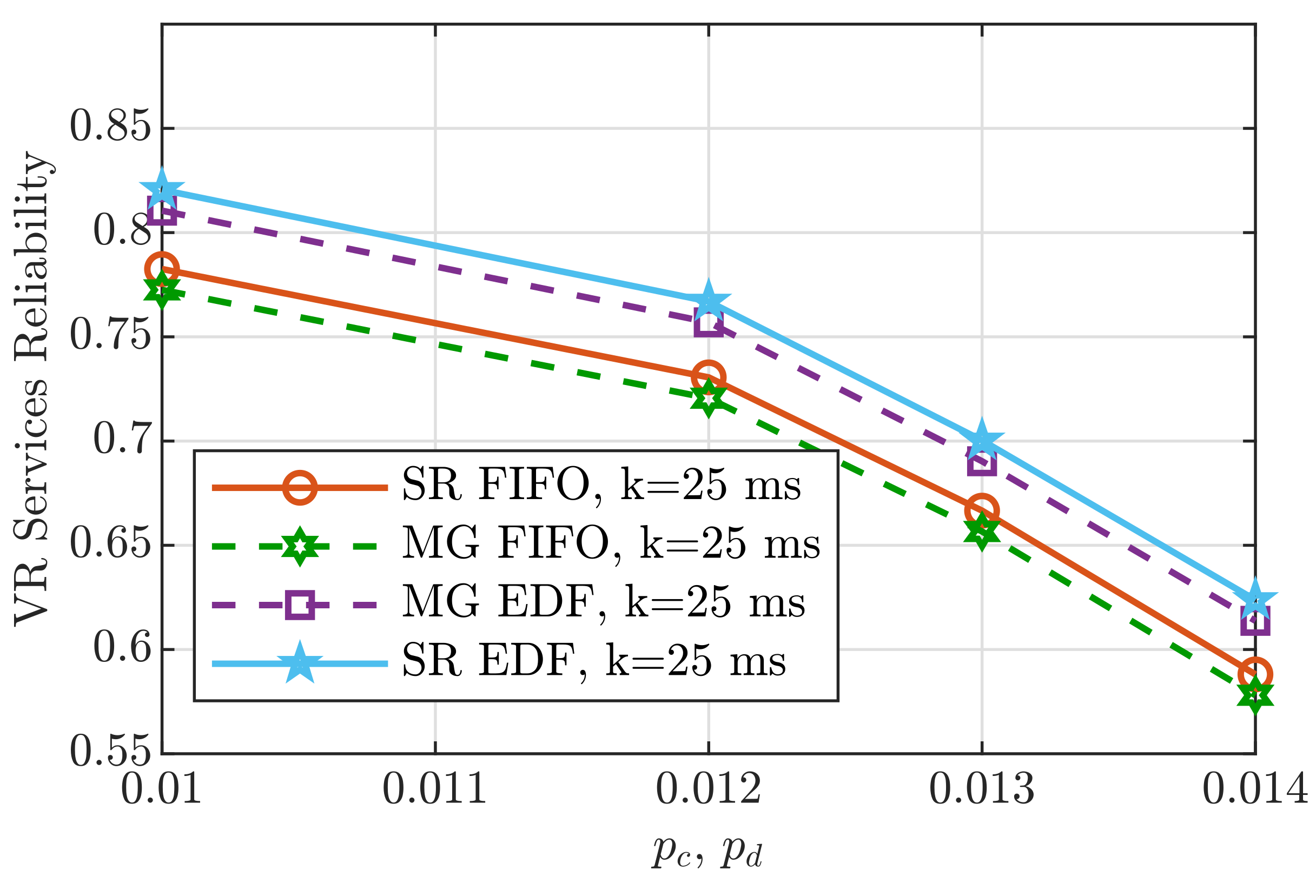
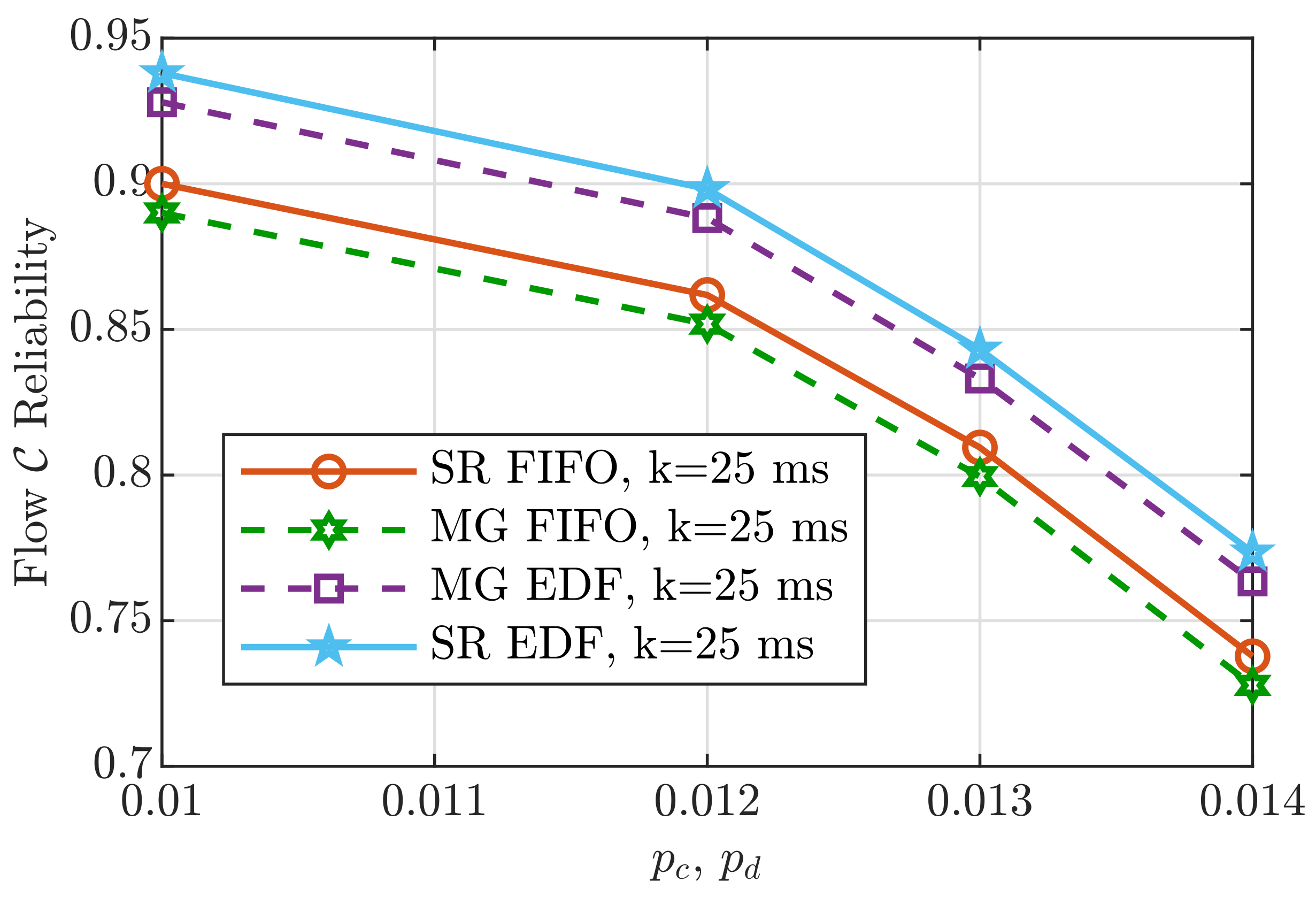
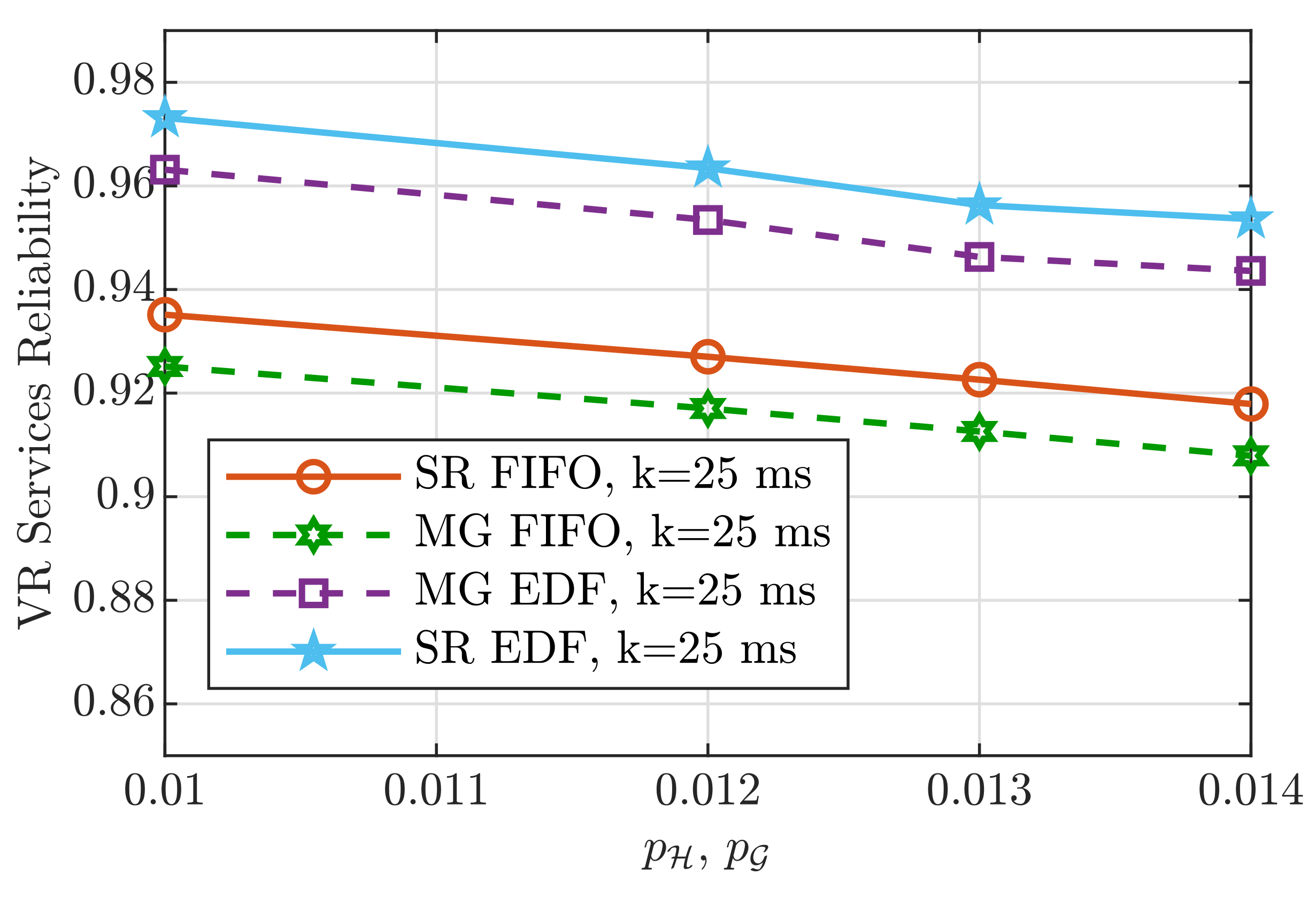
6. Performance Analysis
7. Conclusions
Funding
Institutional Review Board Statement
Informed Consent Statement
Conflicts of Interest
Appendix A
References
- Kasgari, A.T.Z.; Saad, W.; Debbah, M. Human-in-the-Loop Wireless Communications: Machine Learning and Brain-Aware Resource Management. CoRR 2018, 67, 7727–7743. [Google Scholar]
- Saad, W.; Bennis, M.; Chen, M. A Vision of 6G Wireless Systems: Applications, Trends, Technologies, and Open Research Problems. IEEE Netw. 2020, 34, 134–142. [Google Scholar] [CrossRef] [Green Version]
- Chen, M.; Saad, W.; Yin, C. Virtual Reality over Wireless Networks: Quality-of-Service Model and Learning-Based Resource Management. arXiv 2018, arXiv:1703.04209. [Google Scholar] [CrossRef] [Green Version]
- Al-Eryani, Y.F.; Hossain, E. Delta-OMA (D-OMA): A New Method for Massive Multiple Access in 6G. arXiv 2019, arXiv:1901.07100. [Google Scholar]
- Gomes de Sa, A.; Zachmann, G. Virtual reality as a tool for verification of assembly and maintenance processes. Comput. Graph. 1999, 23, 389–403. [Google Scholar] [CrossRef]
- Lin, P.; Song, Q.; Wang, D.; Yu, R.; Guo, L.; Leung, V. Resource Management for Pervasive Edge Computing-Assisted Wireless VR Streaming in Industrial Internet of Things. IEEE Trans. Ind. Inform. 2021. [Google Scholar] [CrossRef]
- Liu, Y.; Liu, J.; Argyriou, A.; Ci, S. MEC-Assisted Panoramic VR Video Streaming Over Millimeter Wave Mobile Networks. IEEE Trans. Multimed. 2019, 21, 1302–1316. [Google Scholar] [CrossRef]
- Bastug, E.; Bennis, M.; Medard, M.; Debbah, M. Toward Interconnected Virtual Reality: Opportunities, Challenges, and Enablers. IEEE Commun. Mag. 2017, 55, 110–117. [Google Scholar] [CrossRef]
- Fidler, M.; Rizk, A. A Guide to the Stochastic Network Calculus. IEEE Commun. Surv. Tutor. 2015, 17, 92–105. [Google Scholar] [CrossRef]
- Jiang, Y. A Basic Stochastic Network Calculus. SIGCOMM Comput. Commun. Rev. 2006, 36, 123–134. [Google Scholar] [CrossRef]
- Li, C.; Burchard, A.; Liebeherr, J. A Network Calculus With Effective Bandwidth. IEEE/ACM Trans. Netw. 2007, 15, 1442–1453. [Google Scholar] [CrossRef] [Green Version]
- Fidler, M. Survey of deterministic and stochastic service curve models in the network calculus. IEEE Commun. Surv. Tutor. 2010, 12, 59–86. [Google Scholar] [CrossRef]
- Poloczek, F.; Ciucu, F. Service-martingales: Theory and applications to the delay analysis of random access protocols. In Proceedings of the 2015 IEEE Conference on Computer Communications (INFOCOM), Hong Kong, China, 26 April–1 May 2015; pp. 945–953. [Google Scholar] [CrossRef] [Green Version]
- Park, J.; Bennis, M. URLLC-eMBB Slicing to Support VR Multimodal Perceptions over Wireless Cellular Systems. In Proceedings of the 2018 IEEE Global Communications Conference (GLOBECOM), Abu Dhabi, United Arab Emirates, 9–13 December 2018; pp. 1–7. [Google Scholar] [CrossRef] [Green Version]
- Sun, Y.; Chen, Z.; Tao, M.; Liu, H. Communication, Computing and Caching for Mobile VR Delivery: Modeling and Trade-Off. In Proceedings of the 2018 IEEE International Conference on Communications (ICC), Kansas City, MO, USA, 20–24 May 2018; pp. 1–6. [Google Scholar]
- Popovski, P.; Stefanović, Č.; Nielsen, J.J.; de Carvalho, E.; Angjelichinoski, M.; Trillingsgaard, K.F.; Bana, A.S. Wireless Access in Ultra-Reliable Low-Latency Communication (URLLC). IEEE Trans. Commun. 2019, 67, 5783–5801. [Google Scholar] [CrossRef] [Green Version]
- Angjelichinoski, M.; Trillingsgaard, K.F.; Popovski, P. A Statistical Learning Approach to Ultra-Reliable Low Latency Communication. IEEE Trans. Commun. 2019, 67, 5153–5166. [Google Scholar] [CrossRef] [Green Version]
- Li, Y.; Luo, X.; Lobo, E.; Pilco, A.; Chen, Y. Wireless Ad Hoc Network Simulation Based on Virtual Reality Technology. In Proceedings of the 2017 International Conference on Virtual Reality and Visualization (ICVRV), Zhengzhou, China, 21–22 October 2017; pp. 458–460. [Google Scholar]
- Ahn, J.; Kim, Y.Y.; Kim, R.Y. Delay oriented VR mode WLAN for efficient Wireless multi-user Virtual Reality device. In Proceedings of the 2017 IEEE International Conference on Consumer Electronics (ICCE), Las Vegas, NV, USA, 8–10 January 2017; pp. 122–123. [Google Scholar]
- Hu, Y.; Li, H.; Chang, Z.; Han, Z. End-to-End Backlog and Delay Bound Analysis for Multi-Hop Vehicular Ad Hoc Networks. IEEE Trans. Wirel. Commun. 2017, 16, 6808–6821. [Google Scholar] [CrossRef]
- Hu, Y.; Li, H.; Han, Z. Delay Bound Analysis Using Martingale for Multimedia DTN under Heterogeneous Network for High-Speed Trains. In Proceedings of the 2015 IEEE Global Communications Conference (GLOBECOM), San Diego, CA, USA, 6–10 December 2015; pp. 1–6. [Google Scholar] [CrossRef]
- Qi, R.; Chi, X.; Zhao, L.; Yang, W. Martingales-Based ALOHA-Type Grant-Free Access Algorithms for Multi-Channel Networks With mMTC/URLLC Terminals Co-Existence. IEEE Access 2020, 8, 37608–37620. [Google Scholar] [CrossRef]
- Shortle, J.; Thompson, J.; Gross, D.; Harris, C. Fundamentals of Queueing Theory; Wiley Series in Probability and Statistics; John Wiley & Sons, Incorporated: Hoboken, NJ, USA, 2018. [Google Scholar]
- Mutairi, A.; Roy, S.; Hwang, G. Delay Analysis of OFDMA-Aloha. IEEE Trans. Wirel. Commun. 2013, 12, 89–99. [Google Scholar] [CrossRef] [Green Version]
- Jain, I.; Kumar, R.; Panwar, S. The Impact of Mobile Blockers on Millimeter Wave Cellular Systems. IEEE J. Sel. Areas Commun. 2019, 37, 854–868. [Google Scholar] [CrossRef] [Green Version]
- Petrov, V.; Moltchanov, D.; Koucheryavy, Y. Interference and SINR in Dense Terahertz Networks. In Proceedings of the 2015 IEEE 82nd Vehicular Technology Conference (VTC2015-Fall), Boston, MA, USA, 6–9 September 2015; pp. 1–5. [Google Scholar]
- Wang, C.C.; Yao, X.W.; Han, C.; Wang, W.L. Interference and Coverage Analysis for Terahertz Band Communication in Nanonetworks. In Proceedings of the GLOBECOM 2017—2017 IEEE Global Communications Conference, Singapore, 4–8 December 2017; pp. 1–6. [Google Scholar] [CrossRef]
- Liu, T.; Li, J.; Shut, F.; Han, Z. Quality-of-Service Driven Resource Allocation Based on Martingale Theory. In Proceedings of the 2018 IEEE Global Communications Conference (GLOBECOM), Abu Dhabi, United Arab Emirates, 9–13 December 2018; pp. 1–6. [Google Scholar] [CrossRef]
- Fidler, M. An End-to-End Probabilistic Network Calculus with Moment Generating Functions. In Proceedings of the 2006 14th IEEE International Workshop on Quality of Service, New Haven, CT, USA, 19–21 June 2006; pp. 261–270. [Google Scholar]
- Williams, D. Probability with Martingales; Cambridge University Press: Cambridge, UK, 1991. [Google Scholar] [CrossRef]
- Ethier, S.; Kurtz, T. Markov Processes: Characterization and Convergence; Wiley Series in Probability and Statistics; Wiley: Hoboken, NJ, USA, 2009. [Google Scholar]
- Ciucu, F. Exponential supermartingales for evaluating end-to-end backlog bounds. SIGMETRICS Perform. Eval. Rev. 2007, 35, 21–23. [Google Scholar] [CrossRef]
- Fantacci, R.; Picano, B. End-to-End Delay Bound for Wireless uVR Services over 6G Terahertz Communications. IEEE Internet Things J. 2021. [Google Scholar] [CrossRef]



Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2021 by the author. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Picano, B. End-to-End Delay Bound for VR Services in 6G Terahertz Networks with Heterogeneous Traffic and Different Scheduling Policies. Mathematics 2021, 9, 1638. https://doi.org/10.3390/math9141638
Picano B. End-to-End Delay Bound for VR Services in 6G Terahertz Networks with Heterogeneous Traffic and Different Scheduling Policies. Mathematics. 2021; 9(14):1638. https://doi.org/10.3390/math9141638
Chicago/Turabian StylePicano, Benedetta. 2021. "End-to-End Delay Bound for VR Services in 6G Terahertz Networks with Heterogeneous Traffic and Different Scheduling Policies" Mathematics 9, no. 14: 1638. https://doi.org/10.3390/math9141638
APA StylePicano, B. (2021). End-to-End Delay Bound for VR Services in 6G Terahertz Networks with Heterogeneous Traffic and Different Scheduling Policies. Mathematics, 9(14), 1638. https://doi.org/10.3390/math9141638





