1. Introduction
The P2P network is an open, dynamic, distributed system where nodes can communicate directly with each other, eliminating the need for a centralized server. In these networks, services are provided by peers; the nodes in the network are anonymous and autonomous. However, due to the openness and anonymity of the distributed network environment, malicious service providers can easily infiltrate the network to obtain improper benefits, thereby affecting the quality of services available to users. To effectively avoid the false and malicious services provided by these internal threats, it is crucial to identify malicious nodes among service providers and ensure the provision of trusted web services to maintain service quality. Consequently, establishing a trust management system is essential to encourage the sharing of resources within the network [
1].
In P2P networks, due to the structural characteristics of the distributed network, traditional network security mechanisms such as encryption and authentication, which are heavily reliant on central nodes, struggle to identify malicious nodes within the distributed network. The credit-based trust model is applied to a distributed system to manage the trust relationships between nodes and calculate the credit value of nodes, achieving good results in identifying malicious nodes within the self-organized distributed network [
2]. Therefore, the study of the trust mechanism in distributed systems is essential [
3] for finding trusted web services, establishing trusted connections [
4], and ensuring service quality [
5]. Currently, most studies regarding trust models in P2P networks rely on user feedback for trust calculations, which are typically divided into local trust models [
6] with smaller global trust and less computational complexity, e.g., EigenTrust [
7], PeerTrust [
8], and that presented in the work of Ref. [
9], among others. Many emerging studies have focused on trust management systems in P2P networks [
10,
11,
12]. In the realm of web service discovery, a multitude of research outcomes employ diverse methods to achieve effectiveness and accuracy. The goal is to enhance the user experience during the service discovery process. For example, the authors of Reference [
13] proposed a Quality of Service (QoS)-aware service discovery method that leverages the whale optimization algorithm and the genetic algorithm. A service discovery method based on the elephant swarm optimization algorithm was proposed in Reference [
14]. While numerous studies have explored bio-inspired approaches [
15] or machine learning [
16], they have not addressed the security of services. Furthermore, to the best of our knowledge, all proposed bio-inspired trust management algorithms are based on metaheuristics, also known as problem-independent heuristics, such as ant colony optimization (ACO) [
17,
18] and the artificial bee colony algorithm.
In P2P networks, path selection based on ant colony optimization (ACO) offers significant advantages over other biological heuristic methods, particularly in dynamic and decentralized environments. The ant colony algorithm has demonstrated excellent performance in numerous NP-hard combinatorial optimization problems, including routing, scheduling, data mining, machine learning, and bioinformatics [
19]. Meanwhile, ants make path selection based on local pheromone concentration, without the need for a global network state, which is suitable for the distributed nature of P2P networks [
20]. Flooding is a typical routing algorithm used in traditional unstructured P2P networks for resource lookup. However, its method of blind message forwarding leads to substantial communication overhead. In large-scale P2P networks, even employing TTL-restricted broadcast methods can result in significant waste of network resources. The ant colony algorithm [
21], due to its excellent adaptability and dynamic self-organizing capabilities, can effectively address routing issues in large-scale P2P networks.
This paper presents a novel algorithm for discovering trusted web services, which integrates a credibility-based trust model with the ant colony search algorithm. The proposed system facilitates the identification of reliable service providers by simulating the behavior of real ants in an ant colony. In summary, the primary contributions of this paper are as follows:
1. This study proposes a trust mechanism that leverages the characteristics of distributed P2P networks, grounded in social credibility, to facilitate trust evaluation among unreliable service nodes, as previously suggested [
22]. In our earlier proposed trust evaluation model, we have confirmed the mechanism’s ability to identify various attacks, such as Sybil and collusion attacks. This approach enables the distributed storage and computation of trust information. The analysis reveals that the mechanism incorporates its own incentive structure designed to encourage nodes to deliver authentic services.
2. In the search for trusted web services, a group intelligent algorithms is utilized, and an ant colony algorithm is proposed as a method for discovering trusted web services. The ant information collection strategy, trust information merging strategy, routing strategy, and random fluctuation strategy, respectively, are established to guide the ant search.
3. Through experimental simulation of various attack types across different network environments, the results demonstrate that this method achieves high recall and precision in discovering trusted web services and effectively identifies trusted nodes. This ensures that trusted services are recognized promptly and efficiently.
The paper is organized as follows:
Section 2 reviews the main trust and reputation models related to this paper.
Section 3 describes the research question, while
Section 4 introduces the algorithm’s design.
Section 5 presents and discusses the theoretical analysis of the algorithm.
Section 6 presents and discusses the experimental results. Lastly,
Section 7 summarizes the conclusions and suggests possible future directions for this research.
2. Related Works
Currently, trust models and reputation models can be categorized into traditional systems and bio-inspired systems. Trust models in P2P networks are based on feedback information and can be roughly divided into global trust models and local trust models. Traditional systems encompass any trust management system that is not based on biological systems. For instance, the EigenTrust [
11] trust model is a global trust model that calculates local trust based on the transaction history of the nodes. It then computes a unique global trust value for each node in the network through an iterative process of mutual trust among neighbors. Similarly, the trust model proposed by Dou [
23] also calculates a global trust value for each node based on their historical behavior with uploaded files. On the other hand, PeerTrust [
8] introduces a local trust model which considers various credit evaluation factors from different perspectives to assess the credibility of the P2P network structure. However, it has been noted that this method does not effectively penalize the malicious behavior of nodes nor provide reasonable convergence rates for large-scale P2P systems. PowerTrust [
24], a reputation system that leverages a trust overlay network (TON), employs regular random walks to capture initial reputation values and forward random walks to update reputation values from power nodes. TrueTrust [
25], on the other hand, calculates service responder credibility as a function of all feedback collected, without implementing any feedback filtering mechanism. It is important to note that this calculation heavily relies on service requester feedback towards service responders, conceptually reflecting the principle of retribution justice. Additionally, Ref. [
26] presents an algorithm that aggregates local trusts using weighted averaging and scaling techniques before calculating global trusts through best linear unbiased estimation methods. In Ref. [
27], a system is proposed that utilizes best linear unbiased estimation to account for the uncertainty of input variables in defining the trust estimation method. Trust values are calculated based on request and actual transfer rates, as well as other relevant parameters. In Ref. [
28], another system is proposed that gathers statistics on the activities of participating partners within the network. This system defines two factors (local contribution and credibility) based on the collected statistics. Each counterpart is then assigned a rank depending on these credibility factors, with this rank being propagated to all participating counterparts within the network.
Compared to the multitude of trust management systems that adhere to traditional methods, only a few have looked to nature for inspiration to tackle the trust issue. In Ref. [
29], a trust management system for P2P networks, which is based on a genetic algorithm, was introduced. This algorithm identifies abnormal behavior by comparing it against peer profiles and determines the trustworthiness of peers through anomaly detection, using the behaviors of reliable peers as historical data. Each peer maintains a distinct profile of others’ behaviors, derived from direct interactions within the network. TrustIs [
30] is a trust model inspired by the human immune system (IS), integrating concepts from the body’s defense mechanisms against viral infections. This model combines peer reputation and object reputation to prevent the spread of corrupted files and communication with malicious peers. AntRep [
12] employs ants to gather evidence about a peer’s reputation and relays this information to the requester. TACS [
10] utilizes ants that follow pheromone trails, in conjunction with heuristic values, to locate trustworthy service providers. AntPS [
31], on the other hand, selects trustworthy providers based on resource and trust similarity pheromone values. In another study [
17], a trust management system inspired by ant colonies is proposed, utilizing problem-specific heuristics to locate trustworthy peers in a reasonable amount of time. It locates trustworthy file providers based on current trust, recommendation, feedback, and collective trust factors. In Ref. [
18], a trustworthy service discovery method based on a modified ant colony algorithm (TSDMACS) is proposed. The authors significantly enhance the algorithm’s global search capability and the accuracy of credibility evaluation by introducing dynamic volatility coefficients, implementing reward and punishment strategies, and optimizing the probability model for path selection. This optimization includes the integration of trustworthy factors such as quality of service (QoS) and node reputation. Furthermore, the authors of Ref. [
32] proposed an efficient neighboring selection process and multi-pheromone distribution method named enhanced flying ant colony optimization for optimization algorithms searching for the best combinations of web services to achieve workflow task functionality.
3. Question Description
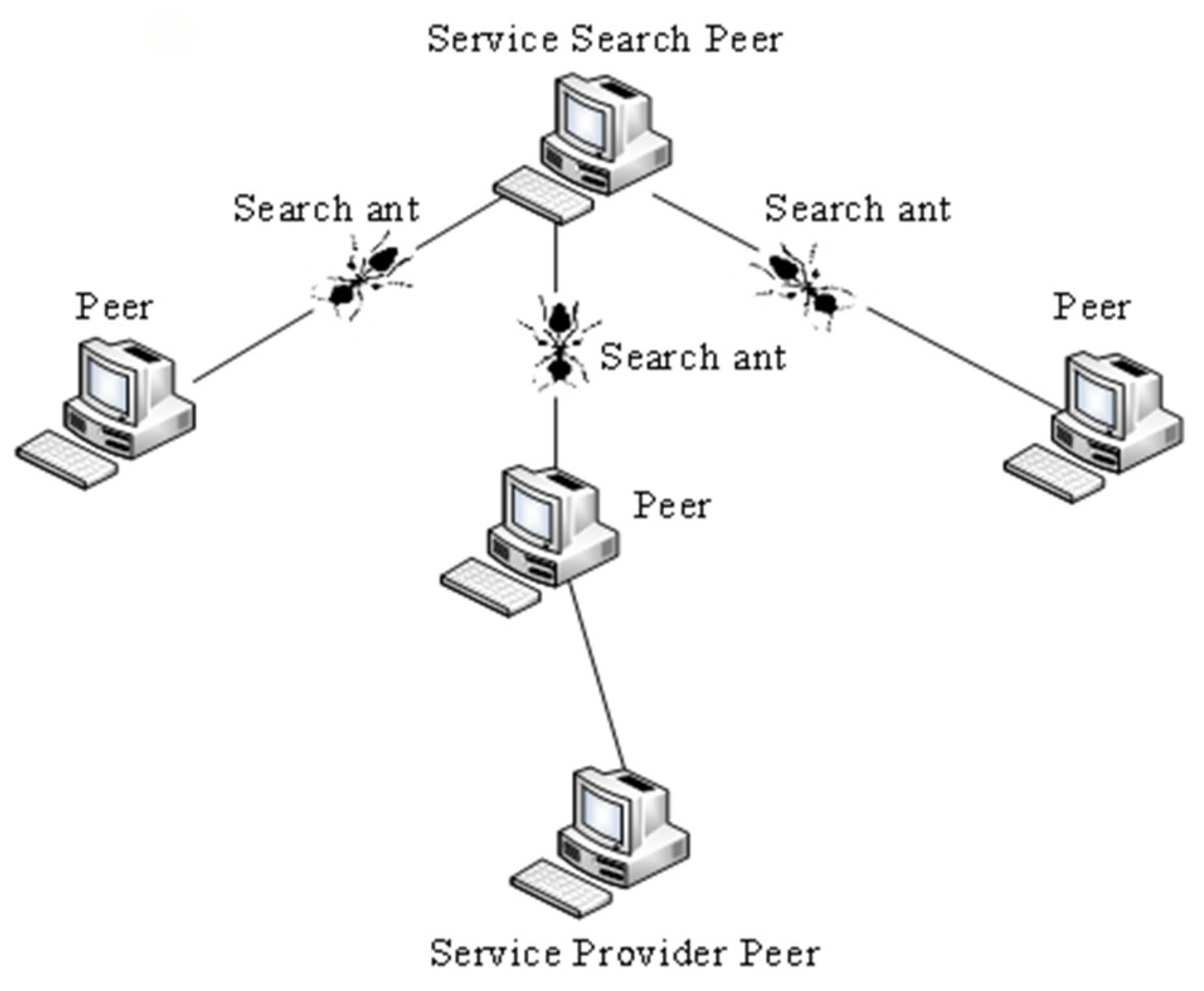
Employing the ant colony algorithm for trusted web service discovery in P2P necessitates the creation of an appropriate search model for the algorithm. In a P2P network, the entire system can be envisioned as a colony network composed of numerous nests, food sources, and pathways that connect them (
Figure 1). Within this network, the service query node is analogous to an ant nest, and the service provider node is akin to a food source. Each node has the potential to serve as both a service requester and a provider.
During the search process, ants symbolize messages traversing the network; they seek out specific services that meet the demand. The food source symbolizes nodes providing matching web services. The discovery process of trusted web services involves ants starting from a service query request node, collecting reputation information and web services through neighboring nodes, and returning with information from destination nodes. Ants can record their search paths to prevent circling.
Ants possess the remarkable ability to identify the most efficient routes between their nests and food sources, taking into account not only the distance but also the reliability of the nodes along these paths. This is accomplished through the release of pheromones along their search paths. As they progress, ants deposit pheromones on their trail, influencing the likelihood of other ants selecting that path based on the current concentration of the pheromone. As additional ants traverse a specific route, more pheromones are deposited, creating a positive feedback loop.
Based on the characteristics of unstructured P2P networks, and by employing ant colony algorithms and trust models, the relevant data structures within the networks are established as follows:
1. Local Service Directory (LocSdir)
The node stores and maintains information about the web services it can provide and offers a keyword vector to represent the service, facilitating the ant search. Each entry in the directory is a two-tuple {service keyword vector (kws), service description information (des)}. The keyword vector is utilized by the ant to match the service, while the service description information primarily includes the service implementation platform, functionality, call mode, and parameters. If LocSdir equals the empty set (), it signifies that the node does not offer any services; conversely, if LocSdir is not equal to the empty set (), it indicates that the node is a Service Provider (SP).
2. Neighbor Service Directory (NbrSdir)
The neighbor service directory caches the web service description information published by neighboring nodes. Each entry in this directory is a triplet {, des, kws}, where represents the neighbor of the node, des describes the services that can provide, and kws represents the keyword vector for those services. The neighbor service directory is generated by collecting cached service information from neighboring nodes.
3. Pheromone table
Each node in the network must maintain a pheromone table (), where each entry consists of a pair {}. Here, represents the neighbor node of , while indicates the intensity of the pheromone concentration on the path from node to its neighboring node . All pheromones in this initial stage table are set to a minimum value ().
4. Neighbor table ()
Each node in the P2P network maintains a neighbor table, where each entry is a triplet {}. Here, signifies the reputation of node as recorded by node , and m denotes the count of evaluations node . Initially, the reputation of all neighbors for each node is set to 0.1, and the evaluation count is set to 1.
5. Direct reputation table ()
This table records the credibility of nodes with direct trust relationships with itself. It is accessible only by the node itself; other nodes cannot access it. Each entry in this table consists of a pair {}, where represents node observed for another node, and denotes cumulative evaluation of node .
6. Recommended reputation table ()
This table primarily serves to record the credibility of target nodes, as determined by transaction evaluations from other nodes. Each item in this table is a triplet , where the latter two components share similar meanings with those in the neighbor table. It is important to note, however, that node is not necessarily a neighbor of . The recommended reputation table does not require initialization.
7. Node ()
Nodes must be uniquely identified within the P2P network to facilitate user search and interaction. Furthermore, each node should contain six data structures, i.e., the node table is a septuple .
8. Ant (
Ants are message packets generated by a service request node and can be transferred between nodes to discover web services and collect the reputation information of the service node. To prevent the message from lingering in the network for too long, each ant sets a record path length (TTL). When the ant takes a step forward in its search, TTL will increase by 1. If the ant’s search exceeds the set limit, it will return along its original path. Each ant also utilizes a taboo search table (tb) with a stack structure to sequentially record its search path. The bottom node of tb is the service query node. Additionally, each ant has a target node set (tp), which is initialized by the service query node before each round of search. This set records the service provider nodes and remains unchanged throughout the searching process. As ants “crawl” during their search, they gather reputation information about their target nodes which is stored in an ant node reputation table (tpr). Both tpr and the recommended reputation table (RR) utilize data structures to record the searched nodes, their reputations, and evaluation quantities. The rlt is used to document matching service information discovered during an ant’s crawl; each entry in rlt consists of {sp, des}, where sp represents the service provider node, and des denotes service description information. In this paper, ants are defined as a septuple {id, kws, tb, tp, tpr, rlt, TTL}.
9. Ant colony (AC)
Colony refers to a group of ants residing in a nest node. In this article, it is defined as a quad group {Ants, C, c, Srlt}. The term Ants represents the collection of ants in the current iteration, while C denotes the total number of iterations of the colony. The variable c represents the current number of iterations. Additionally, Srlt stands for the result set of the service that matches the keyword. Each item in the Srlt is represented as a quad {sp, des, T, UT}. Herein, sp signifies the service provider node, and des represents service description information. Furthermore, T reflects the credibility of sp, and UT indicates its non-credibility. Both T and UT are calculated through a voting process based on credibility information about sp searched by ants in each round. In summary, T and UT serve to reflect both credibility and untrustworthiness regarding service delivery from different perspectives.
4. The Design of the Algorithm
Based on the credibility model of unstructured P2P networks, a trusted service discovery algorithm based on an ant colony system (TSDA-ACS) is proposed. TSDA-ACS incorporates various strategies, including ant routing, pheromone updating, and credit information merging. The specific content is as follows:
1. Initialization Strategy for New Nodes
In the credit mechanism, credit information is stored and distributed. For newly added nodes, or Newcomers, in the network, there is no reputation information about their neighbors, and the same applies to the neighbors regarding the Newcomers. When a Newcomer initializes its neighbor table, all credit information within is set to 0.1, accompanied by an evaluation number of 1. Likewise, the neighbor node assigns a basic credit value of 0.1 to the Newcomer in its neighbor table, also with an evaluation number of 1. The Newcomer operates as a Service Provider (SP) node, whereas its neighboring nodes act as evaluation nodes. The network model includes several scenarios.
Initially, when the network is established, nodes populate their neighbor tables according to a new node initialization policy designed to establish fundamental trust information.
During the operation of the network, when a new node joins, neighboring nodes are required to store the trust information of this Newcomer using an appropriate trust initialization strategy for Newcomers.
Upon receiving service transaction evaluation data (including the evaluation node, target node, and evaluation result), if a node lacks reputation information about the evaluation node, it will treat that evaluation node as a Newcomer to calculate the reputation for the target node.
In instances where ants are conducting searches for service information and encounter an SP node that matches their search criteria but lacks an associated trust value, this SP should be treated as a Newcomer.
2. Node Service Publishing Policy
When a service provider node has a new service for other nodes to discover and invoke, it is necessary to publish the description information and keyword vectors of the new service it offers to its neighboring nodes. As depicted in
Figure 2, when a node
creates a new service
WS, it generates the service release message (
,
WS.des,
kws) and transmits it to all its neighbors. The neighbor node of
will then be included in the neighbor service directory (
NbrSdir). This method enables ants to reduce message costs during their search for web services and facilitates the discovery of more matching services.
3. Ant Information Collection Strategy
During the process of service discovery, when ant reaches node , is added to the taboo table . The ant will then search for the required information in node , based on the carried query service keyword vector and the target node collection . Ants primarily search for two types of information in : node reputation information in and service description information matching with .
First, searches the recommended reputation table and the neighbor table of the node . For each node in , if a reputation record {} related to node is present in either or , it is added to the ant’s node reputation table .
Next, searches for the local service directory of the node . If there is a service WS in where and satisfies then the service information {} is added to . This indicates that Node provides a service meeting the ant’s requirements, without any previous iteration.
Finally, ant searches the neighbor’s services directory of Node . If Node provides a Service existing at where matches and satisfies , then this Service Information {} is added to . This shows that Neighbor of the node provides the Service meeting demands, without any previous iterations.
Whether ant searches for matching Service Information at or , in this situation, called a hit, we call ant the Hit ant. If an ant does not search for Matching Service Information during its life time, it is called a Missed Ant.
4. Ant Routing Selection Strategy
In the TSDA-ACS algorithm, two types of ants are utilized: ordinary ants and abnormal ants. The only difference between these two types of ants lies in the different rules of routing selection. Based on the principles of the ant colony algorithm, ant routing selection is influenced by two types of information: pheromone
and heuristic information
. In the network model, nodes not only store pheromones to neighboring edges but also maintain records of their neighbors’ reputation values. Therefore, in the TSDA-ACS algorithm, ant routing is associated with both pheromones and reputation. The probability that ant
selects neighbor
at node
can be expressed using Equation (1), as follows:
where
represents the reputation value of the neighbor node
in
, while jc represents the set of neighbor nodes not previously visited and whose reputation is greater than 0. Additionally,
represents the reputation of the neighbor node
in
, and
s is the node that ant
k will choose next. In ACS, ants use the pseudo-stochastic proportion rule to select the moving node in the next step. The variable s uses the node selected by the probability proportion of Equation (2), as follows:
where
s is the node to be selected by the ant
k for its next move,
is a random number evenly distributed over [0, 1], and
determines the probability of selecting a node most promising to visit, with
The value of
is dynamically determined as the number of ant colony iterations increases, as shown in Equation (3):
Here,
C represents the total number of ant colony iterations,
c represents the number of current round iterations, and
represents a constant used to adjust the range of
(where
= 0.999 [
18]).
The function curve of
is illustrated in
Figure 3. At the beginning of the colony iteration, when there are fewer pheromones in the network, selection depends on the reputation of neighbor nodes. As the iteration progresses and the ant colony gradually converges, it becomes important to increase randomness in ant routing and search for more service and reputation information to prevent premature convergence into a local optimal solution.
The above describes the routing rules for ordinary ants. In addition to these rules, an abnormal ant is specially set up to provide opportunities for exploration. These ants tend to choose neighbor nodes with low pheromone concentration and high credibility. Therefore, Equation (4) shows how
’
s probability of choosing neighbor
of node
is calculated:
The atypical ant mechanism can increase the likelihood of subsequent visits to new nodes in the ant colony iteration. Here are the specific steps of the ant routing selection algorithm (Algorithm 1).
| Algorithm 1: Ant Routing Selection Strategy. |
Input: ant , node and P2P network.
Output: The next neighbor node that the ant will visit.
Method:
(1) Ant utilizes locally stored reputation information to access the reputation of its neighboring nodes;
(2) Ant uses the collected reputation information to evaluate the reputation of the current node’s neighboring nodes in . If there are unvisited high-reputation nodes, it returns; otherwise, it proceeds to Step 3.
(3) The reputation of the neighboring nodes of the current node is evaluated, and any malicious service nodes with low reputation are detected and subsequently excluded.
(4) The pseudo-stochastic selection parameter is calculated according to Formula (3);
(5) Generate a random number rank between [0,1];
(6) if
{
selects the next neighbor node based on Formula (2) pseudorandom proportion and returns;
return nextNode;}
else
{
determines the next neighbor node following the Formula (4) probability rule and returns;
return nextNode;
} |
5. The Pheromone Update Strategy
To prevent the premature search convergence of ant colonies, the classic max–min ant colony algorithm (MMAS) [
33] is utilized in this paper to limit the range of pheromones on each path in the network to
; if the path pheromone
, then set
; if
, then set
. Upon creation of the network, the pheromone on each path is initially set to
During each iteration of the TSDA-ACS algorithm, ant
conducts a search within the maximum number of search steps in two cases: when it hits a service and when it misses a service. If
misses the service, it participates in pheromone update; if
hits the service, then during its return process, the pheromone on its path needs to be updated. When
returns from node
to node
, update
at node
, as follows:
where
represents the pheromone volatilization rate,
represents ant
releasing pheromone on
,
represents ants
traveling through path length, and
denotes the distance from node
along the access path of
to query node service. The greater
, the closer it is to the service provider and the higher the concentration of released pheromones on that path, functioning as an uneven pheromone update mechanism. According to Equations (5) and (6), shorter search paths lead to a greater release of pheromones, and paths that are closer to the service providers have higher concentrations of these pheromones. This strategy prevents ants from converging prematurely on neighboring nodes and ensures that they can locate nearby service providers during their search.
6. Ant Information Merging Strategy
Before the new iteration of the ant colony search begins, when all ants return to the service query node, each ant will summarize the reputation information and service information of the searched target node and update the service result set of the ant colony. This process can be specifically divided into five steps:
First, the ants will summarize their respective searched credit records. Each ant will calculate the reputation value of the target node based on the searched credit information about that node.
For a target node
in the target node set
of ant
, if there are
n credit records {
} about
in
, then for each record about
, ant
’
s credit calculation method is shown in Equation (7). The trust values from all n records are then added together, as shown in Equation (8).
where
and
.
m represent the credibility and number of evaluations of the
j-th records, respectively.
Second, the voting method is utilized to compute the credibility and reliability of the target nodes in this round.
Assume that in this iteration, there are w ants {} which have conducted searches regarding the reputation of . After these ants have calculated their findings, including x ants determining a reputation greater than 0.1 and y ants determining a reputation is less than 0.1, the reliability () and non-credibility () of the node are determined for the current iteration rounds (where c represents the current iteration).
Third, trust information obtained from this round’s search regarding target nodes is consolidated into the ant colony.
After calculating the reliability and unreliability of node
, denoted as
and
respectively, within
, the values are updated accordingly. If both
and
equal 0, indicating that
is a service provider newly discovered in the round
c − 1 search, then directly set
,
; otherwise, the direct trust value is calculated using Formula (9), and the indirect trust value is calculated using Formula (10):
where
[0, 1], this article takes
= 0.6, indicating that the algorithm focuses more on the service reputation information collected by ants in their history.
Fourth, in this round, all the successful ants will add the searched service information to the ant nest node service result set.
The search results of all successful ants in this round are merged to obtain the service information set found by this round of ants, where n indicates the number of ants that successfully hit the service in this round. Subsequently, each service information in Rlt is added to , and the and in the newly added service record are initialized to 0.
Fifth, recycle the ants and regenerate new ones for the next iteration to start a new round of search.
If , increase by 1 and generate m new ants. Then add all the service provider nodes in to the target node of each ant, add the ant nest node to the taboo search table of each ant, add search keywords to the ant’s field, and initiate a new round of search. If , then terminate the TSDA-ACS algorithm. Based on search results from , select the services provided by nodes with greater credibility than non-credibility and a larger reliability–non-credibility difference.
By integrating an ant routing strategy, an information acquisition strategy, and a pheromone update strategy, we present a trusted web service discovery algorithm based on an ant colony algorithm within an unstructured P2P network. The trusted service discovery algorithm is described as follows (Algorithm 2):
| Algorithm 2: The trusted service discovery algorithm. |
Input: Service query node QueryPeer, query keyword vector kws, ant colony AC, total iterations C, P2P network.
Output: Service Information Table SIT.
for c = 1 to C do
Step 1: Initialize Ant Colony Parameters
Initialize ant colony AC with:
Total iterations AC.C = C
Number of ants NAnt
Current iteration AC.c = 1
Maximum search path length TTLmax
Pheromone evaporation rate ρ
Pheromone bounds [, ]
Weight factors for pheromone () and reputation ()
Step 2: Generate and Initialize Ants
if AC.c > C then
goto Step 5 // End if iterations complete
else
Generate NAnt ants, including one abnormal ant
for each ant in AC do
ant.tp = AC.Srlt // Add service provider node
ant.tb = QueryPeer // Start from QueryPeer
ant.kws = kws // Set query keywords
ant.TTL = 0 // Initialize TTL
ant.tpr = 0 // Initialize pheromone
ant.rlt = ∅ // Initialize result set
end for
Step 3: Ant Search and Path Update
for each ant in AC do
while ant.TTL < TTLmax do
Pi = ant.current_node // Current node
ant.tb.add(Pi) // Add Pi to visited nodes
if Pi contains service matching kws then
ant.rlt.add(Pi) // Add Pi to result set
ant.return_to_QueryPeer() //Return to QueryPeer
update_pheromone(ant) //Update pheromone
break
else
ant.TTL += 1
if ant.TTL >= TTLmax then
ant.return_to_QueryPeer()
update_pheromone(ant) // Update pheromone
break
else
next_node = ant.select_next_node() // Routing strategy
ant.move_to(next_node) // Move to next node
end if
end if
end while
end for
Step 4: Merge Results and Prepare for Next Iteration
merge_ant_results(AC) // Merge results from all ants
destroy_ants(AC) // Destroy returned ants
AC.c += 1 // Increment iteration counter
end for
Step 5: Finalize and Return Results
SIT = generate_service_info_table(AC) // Generate service info table
sort(SIT) by:
Node credibility (descending)
If credibility is equal, sort by incredibility (ascending)
return SIT |
6. Results and Discussions
The experiment detailed in this paper utilizes Stanford University’s open-source P2P Simulator Query Cycle Simulator [
35] to implement the algorithm and record the experimental data. The TSDA-ACS algorithm involves ants searching not only for the target service but also for the reputation information of the service node within the P2P network. Consequently, it is essential to invoke the service to generate the associated reputation information. Prior to executing the TSDA-ACS algorithm on the newly created P2P network, multiple threads are initiated to run concurrently. Each thread randomly selects a service caller node from the network and invokes the service of a randomly chosen service provider node with each execution. Upon completion of a service call, the evaluation of the service pair is disseminated throughout the network, updating the node’s reputation. As multiple threads operate over a period, the accumulation of certain node reputations in the P2P network begins, marking the initiation of the TSDA-ACS algorithm.
As previously mentioned, only a few studies have concentrated on reputation and trust management systems within P2P networks, utilizing bio-inspired heuristics.
To validate the efficacy of the TSDA-ACS algorithm, this paper presents a comparison with the RW, MMAS, and TSDMACS algorithms. The RW algorithm selects a neighbor of the current node at random as the search node, without employing pheromone or node reputation information. The MMAS algorithm utilizes pheromone information and heuristic information, but disregards reputation information; it employs basic local pheromone update methods, as well as global pheromone update methods. Our algorithm, based on MMAS, has enhanced these strategies by incorporating new ones, such as a pheromone update strategy, an ant routing strategy, and an information merging strategy. The TSDMACS algorithm is a trusted service discovery method that combines the ant colony algorithm with a P2P network. A horizontal comparison with this algorithm highlights the performance enhancement achieved by the TSDA-ACS algorithm. The feasibility of the TSDA-ACS algorithm can be ascertained through comparison with the RW algorithm, and the effectiveness of the new strategy can be affirmed by comparing it with the MMAS algorithm.
In P2P networks, services are distributed and stored across each node. Hence, the service recall rate of an algorithm is a critical metric for evaluating its performance. Moreover, P2P networks encompass a variety of services, some of which may be malicious. To reduce exposure to malicious services, nodes and services that fail to meet certain requirements are filtered out. The accuracy rate of services is also a significant factor in measuring algorithm performance. The relevant evaluation indicators for the algorithm are defined as follows:
Definition 1. Trusted Service Recall Rate refers to the proportion of trusted web services discovered by the algorithm to the total number of trusted web services in the network so far (e.g., Equation (11), where TSResult represents the number of different trusted services discovered by the algorithm). This total number (allTSInP2P) is unpredictable within an unstructured P2P network but needs to be set during experimentation to test efficiency. Definition 2. Trusted Service Precision (TSPrecision) refers to the proportion of trusted services searched by the algorithm in the total number of services searched up to the current iteration. All services searched by the algorithm, including malicious and trusted types, are considered. In Equation (12), |AC.Srlt| represents the total number of services searched by the algorithm up to this point. If it indicates that no service node has yet been found. Definition 3. Trusted Service Single-Hop Recall (TSRSingleHop) refers to the ratio of trusted service recall obtained by the algorithm in the current iteration to the total number of queried messages. In Equation (13), af = 100 represents the amplification factor and totalMessages represents the total number of messages in the network, equivalent to the TSRecall message acquisition cost. Definition 4. Trusted Service Single-Hop Precision (TSTSingleHop) is defined as a ratio between trusted service precision and the total number of queried messages. In Equation (14), af = 100 is again used as an amplification factor, while totalMessages represents the overall message count within the network. In this paper, the recall rate and precision rate from the field of information retrieval are used as evaluation metrics to reflect the success rate of the TSDA-ACS algorithm in searching for trusted web services within unstructured P2P networks and its ability to filter out malicious service nodes. The single-hop recall rate and single-hop precision rate for trusted services are employed to evaluate the algorithm’s efficiency, considering the message cost during single-hop queries.
6.1. Static Environment Experiment
The static experiment refers to a scenario where the network size and structure remain constant throughout the service discovery process. In this experiment, the scale (n) of the unstructured P2P network is set to 10,000, with the proportion of trusted service nodes and malicious service nodes both at 0.5%, resulting in 50 nodes each. The total number of iterations for the ant colony (
C) is set to 20, and the number of ants (
m) is 10, including one abnormal ant. In this article, we employ a mixed method that combines theoretical analysis with experimental verification to determine the parameters. Firstly, we establish the parameter range based on the convergence theory of ACO and previous research experiences. Secondly, we conduct parameter optimization using the control variable method and the orthogonal experimental method. The upper limit and lower limit of pheromone change are
= 0.999 and
= 0.001, respectively; the maximum number of steps sought by ants was
= 30, with an impact factor for pheromone (
α) set at 1.0 and an impact factor for reputation information (
β) at 1.0 [
18]. Through experimental comparison, when the volatilization rate of pheromones is
= 0.177, a balance is achieved between convergence speed and solution mass.
Given the inherent randomness within ant colony algorithms, results from a single experiment may not be representative. Consequently, this experiment is repeated ten times, and the average value of evaluation indicators across all experiments is utilized for plotting purposes.
The trusted service recall rate and trusted service accuracy rate from experimental data using four algorithms (RW, MMAS, TSDMACS, and TSDA-ACS) are presented in
Figure 4 and
Figure 5. As depicted in
Figure 4 and
Figure 5, throughout the iteration process, both the recall rate and precision rate for trusted services using the TSDA-ACS algorithm consistently outperform those achieved by other comparison algorithms. TSRecall reaches as high as 77% after just seven iterations, indicating early success for the TSDA-ACS algorithm. At the conclusion stage, TSRecall stands at impressive levels, reaching up to 82%, while TSPrecision achieves a remarkable level, reaching 91%. Thus, it can be seen that the recall rate of the TSDA-ACS algorithm is higher than that of the TSDMACS algorithm, and the recall rate of the MMAS algorithm is better than that of the RW algorithm. This indicates that the pheromone and heuristic information of the ant colony algorithm exert a good guiding effect, guiding ants to discover services as soon as possible. Dynamic trust assessment has been introduced into the TSDMACS and TSDA-ACS algorithms, resulting in a high success rate in the early stages of iteration. Through this set of experiments, it can be verified that TSDA-ACS exhibits a high ability to discover trusted services.
The TSRecall metric primarily assesses the service discovery capabilities of the algorithm and does not adequately reflect its ability to filter out malicious services. As illustrated in
Figure 5, the precision rates of the four algorithms indicate that TSDA-ACS exhibits a significantly higher accuracy during the iterative process compared to RW, MMAS, and TSDMACS. This disparity arises because neither MMAS nor RW incorporate node reputation information in their search processes, whereas TSDA-ACS and TSDMACS leverage this critical data for routing selection. Furthermore, TSDA-ACS demonstrates superior accuracy over TSDMACS. The TSDA-ACS algorithm employs a reputation evaluation mechanism; when an ant selects a route at its current node, it first assesses the reputations of neighboring nodes, based on historical service call data. If it identifies any malicious nodes with low reputations among these neighbors, it actively avoids them and subsequently selects a route using traditional ant colony optimization techniques. This approach significantly enhances the accuracy of trusted service lookups. In contrast, the TSDMACS algorithm implements a pheromone punishment mechanism aimed at malicious nodes, which provides some capability to differentiate between good and bad services. Its precision rate for trusted services is markedly higher than that of both the MMAS and RW algorithms. However, both MMAS and RW lack an effective reputation evaluation mechanism for trusted services, which makes it challenging to accurately differentiate between various types of reputational standings among target service provider nodes. As a result, their accuracy rates for reliable services have plateaued at around 50%, impeding potential enhancements in performance.
To assess the efficacy of malicious service detection, a comparative analysis was conducted on the number of malicious services identified by various algorithms.
Figure 6 illustrates how the quantity of malicious services detected by each algorithm evolves as iterations progress. The number of malicious services uncovered by both the MMAS and RW algorithms gradually increases with ongoing searches. In contrast, the TSDA-ACS and TSDMACS algorithms do not exhibit an increase in detected malicious service nodes with additional iterations. Notably, TSDA-ACS identifies fewer malicious service nodes than does the TSDMACS algorithm. This discrepancy can be attributed to the incorporation of a dynamic trust model [
18] within TSDA-ACS, along with an initialization strategy for new nodes. Through trust evaluation mechanisms, nodes exhibiting low reputation can be effectively isolated; consequently, as ants deposit more pheromones along trusted paths, they cease to discover new malicious service nodes in subsequent iterations. Experimental results demonstrate that this algorithm possesses a robust capability for identifying malicious nodes. Furthermore, different types of attacks, e.g., Sybil or collusion, have been validated in reference [
18].
To verify the execution efficiency and message cost of the algorithm, a comparative analysis was conducted on the single-hop recall and precision of the algorithm in searching for trusted services.
Figure 7 and
Figure 8, respectively, display variation curves for single-hop recall rates and precision rates for trusted services throughout iterative processes. The TSDA-ACS algorithm consistently demonstrates higher single-hop query efficiency than do the RW, MMAS, and TSDMACS algorithms, indicating that the routing of the TSDA-ACS algorithm follows a pseudo-random ratio rule. During the initial iteration, the algorithm prioritizes nodes with high reputation for access, resulting in a high recall rate of single-hop trusted services. However, as the ant colony matures over subsequent iterations, fewer new trusted services are discovered, leading to a decline in single-hop query efficiency. Through this implementation, it can be proven that TSDA-ACS exhibits high single-hop precision, and the ant routing selection strategy of this algorithm plays a key role in reducing system computation and network transmission overhead without the need for multiple iterations or complex steps.
Figure 8 illustrates that the single-hop accuracy rate of the TSDA-ACS algorithm surpasses that of the RW, MMAS, and TSDMACS algorithms, particularly when the ant colony has not yet converged during iteration. In later stages, as convergence occurs within the ant colony and new trusted services become scarce, ants primarily focus on collecting reputation information rather than discovering new services, which causes a decline in the single-hop accuracy rate.
In conclusion, a comparison reveals that the TSDA-ACS algorithm surpasses the RW, MMAS, and TSDMACS algorithms in terms of recall rate and precision rate. Additionally, it demonstrates superior performance in single-hop query efficiency. This indicates that integrating a reputation model with an ant colony algorithm is not only viable but also beneficial. The query efficiency of this hybrid approach exceeds that of both RW and MMAS algorithms. From the analysis presented, it is evident that the trusted service algorithm in this article achieves a balance between coverage and accuracy in single-hop scenarios, validates the trust evaluation model within the algorithm, and decreases system computation and network overhead.
6.2. Static Environment Experiment with Different Scales
To verify the scalability of the algorithm, 10 independent experiments were conducted, each with a different network scale. In the experiments, the network scale increased from 10,000 to 28,000 in increments of 2000, while maintaining a constant number of malicious and trusted services. Each experiment was repeated 10 times, and the average value of the index at the completion of each iteration from these repetitions was used as the index value for that experiment.
Figure 9 and
Figure 10 illustrate the recall rate and precision rate for trusted services in networks of varying scales, respectively. The recall rates of various algorithms have exhibited a certain downward trend, which is attributed to the expansion of the network scale, while the absolute number of services remains constant, thereby diluting the density of services and increasing the difficulty for ant colonies to discover new services. However, despite this trend, the TSDA-ACS algorithm has demonstrated an average retrieval rate for trusted services of 70.52% across these 10 independent experiments, with an accuracy rate at 91.02%. This indicates that even amidst varying network scales, our algorithm consistently maintains relatively high service recall and accuracy rates, highlighting its robustness. The adaptability and scalability demonstrated by our reputation model and algorithm are crucial, given the ever-evolving nature of P2P networks. Furthermore, both tabulated data and graphical indicators clearly show that our proposed algorithm model possesses distinct advantages over the RW, MMAS, and TSDMACS algorithms. Compared to RW algorithms, the TSDA-ACS algorithm exhibits more directed, faster, and accurate search capabilities. Additionally, when compared to MMAS, it excels in filtering out malicious nodes due to its incorporation of service node reputation for routing purposes. In contrast to TSDMACS, the TSDA-ACS algorithm introduces an anomalous ant mechanism that enhances the likelihood of newly added nodes being accessed during later stages of ant colony iteration. In conclusion, the TSDA-ACS algorithm proves effective across various network scale environments.
6.3. Dynamic Environment Experiment
A dynamic network is characterized by nodes that can leave at any moment, while new nodes may join at any time. This node behavior results in dynamic changes to the network’s scale and topology. The aim of this experiment is to verify the stability of the TSDA-ACS algorithm within dynamic P2P networks. The reputation mechanism in TSDA-ACS depends on reputation information that is distributed and stored across the network. If all nodes that hold reputation information depart from the network and no new service evaluation records are created during the iterative process, it becomes evident that the query efficiency of the TSDA-ACS algorithm will be comparable to that of the MMAS algorithm. In this experiment, the network’s topology and nodes underwent dynamic changes throughout the algorithm’s operation. The network size was set to 10,000 nodes, with 20 iterations conducted by an ant colony while maintaining a constant number of services within the network. Prior to each iteration, 500 service consumption nodes were randomly selected for removal, while 500 new service consumption nodes were added. Initially, newly added nodes and isolated nodes that have just joined the network do not generate any new service call log information. Therefore, the reputation evaluation of these nodes is based on initial values for network activity, while all other parameters related to both networking and ant colony optimization remain consistent with those used in static network experiments.
The recall rate and precision rate of trusted services are illustrated in
Figure 11 and
Figure 12, respectively. It is evident from the figures that, compared to the results in a static network environment, the TSDA-ACS algorithm experiences a decrease in both the recall rate and precision rate of trusted services when there is frequent joining and leaving of nodes in the network. This indicates that service discovery becomes increasingly challenging in dynamic network environments characterized by constant changes and growing scale. The observed decline in accuracy can be attributed to the loss of reputation information resulting from the departure of numerous nodes from the network. Nevertheless, despite this challenge, the TSDA-ACS algorithm continues to achieve a high level of reliability in regards to service accuracy, reaching 79.5% at the end of its iterations, owing to its robust distributed storage mechanism for reputation information. In comparison with other algorithms, TSDA-ACS demonstrates enhanced performance under these conditions. This improvement is largely due to the effective application of relevant routing strategies tailored for dynamic network environments. The initialization strategy for new nodes facilitates local processing of information, while the node service publishing strategy restricts publications to neighboring nodes, thereby reducing message costs and aiding in the search for more compatible services. The ant routing strategy employs a pseudo-random proportional rule for selecting subsequent mobile nodes, ensuring both accuracy and reliability in next-hop node selection. Additionally, the pheromone update mechanism incorporates both local and global updates to optimize resource efficiency within the algorithm. These strategies collectively enhance the distributed execution efficiency of TSDA-ACS. Consequently, it remains capable of delivering high levels of accuracy and query efficiency for trusted services within dynamic network environments—demonstrating effective strategies specifically designed for such scenarios.