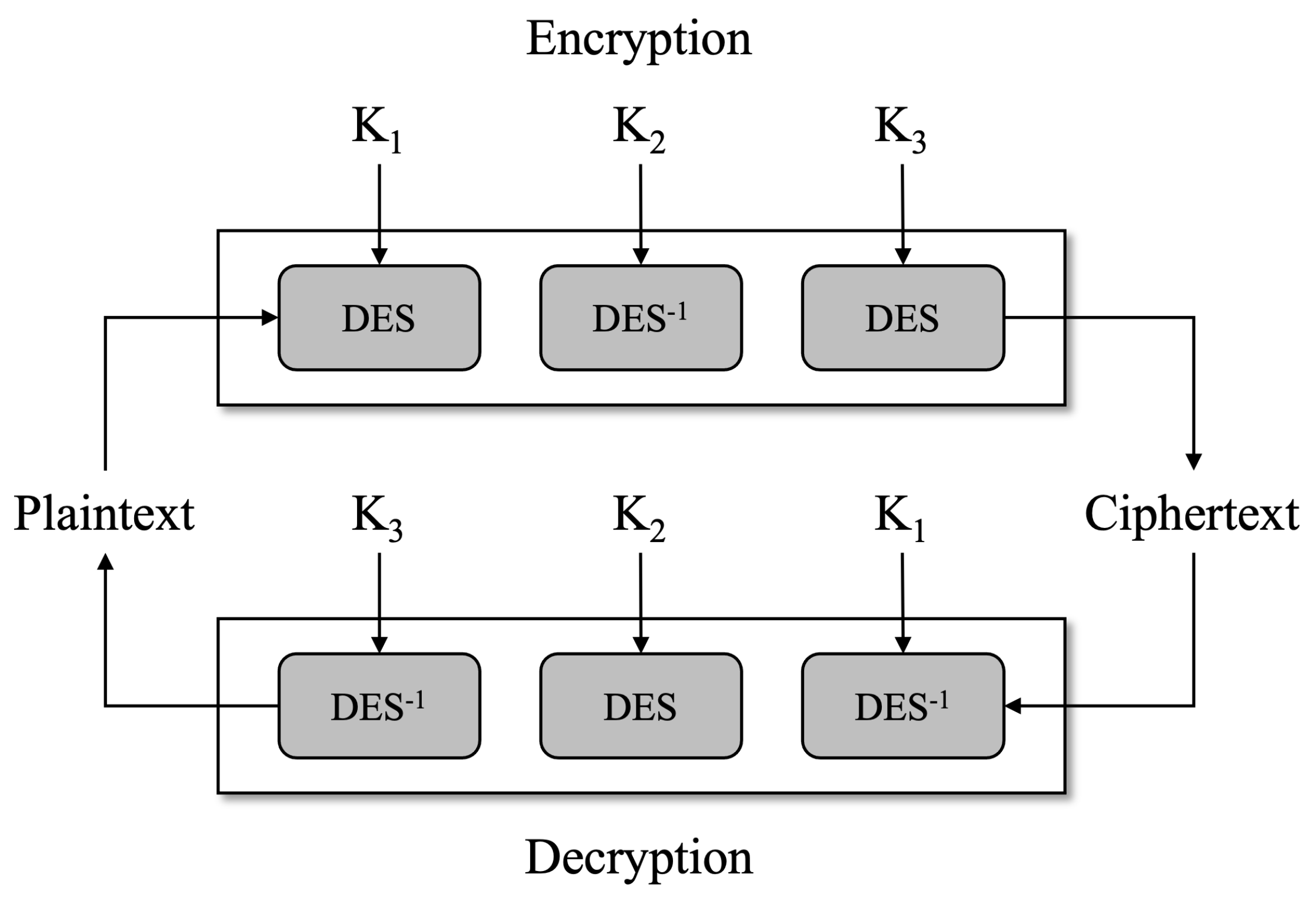
Quantum Circuit Implementation and Resource Analysis for Triple Data Encryption Standard (DES) (Triple-DES)
Abstract
1. Introduction
Contribution
- Optimized Quantum Circuit Components for DES and TDES: Our research proposes optimized quantum circuit designs for DES and TDES. We introduce two optimized designs for the expansion P-Box and four for the S-Box, incorporating both depth-optimized and qubit-optimized structures based on their characteristics.
- Quantum Resource Trade-off Analysis: We evaluated various TDES quantum circuits by analyzing different component combinations. Notably, optimizing individual components does not lead to linear improvements in overall circuit performance due to the complex interplay of parallel operations in quantum circuits.
- First Quantum Resource Evaluation of TDES in Grover’s Algorithm: This paper presents the most optimized TDES design, and we evaluated the quantum resources for Grover’s Algorithm.
2. Background
2.1. Data Encryption Standard (DES)
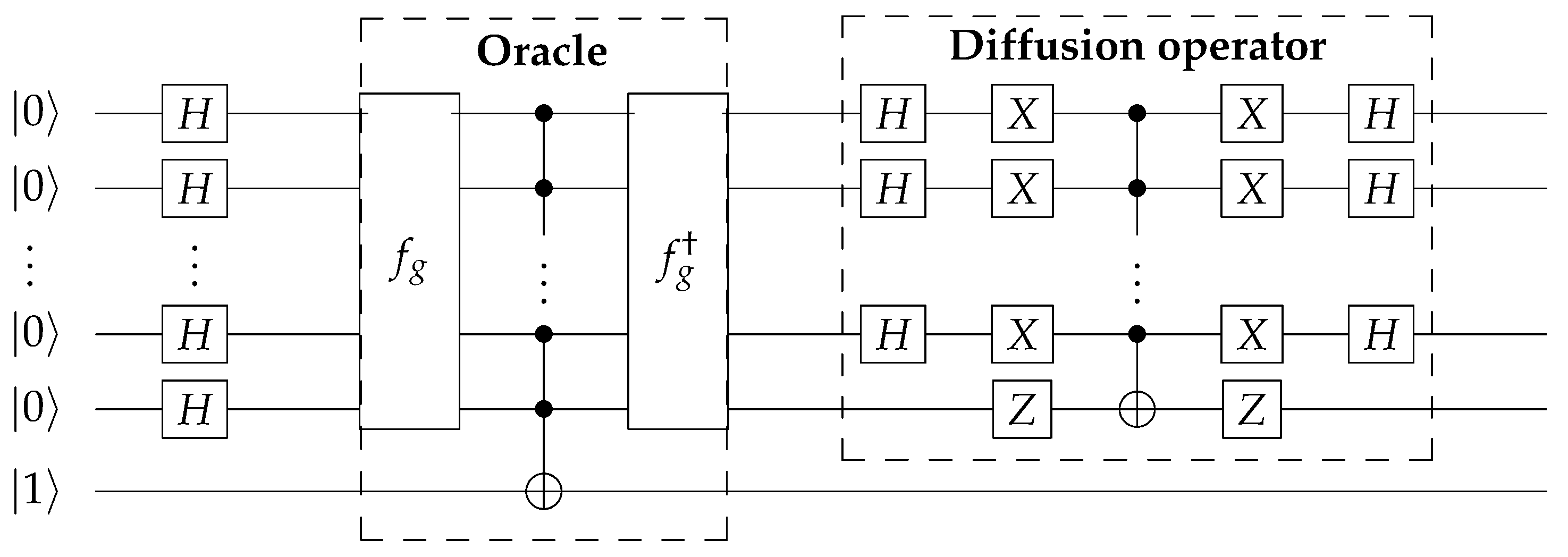
2.2. Grover Algorithm
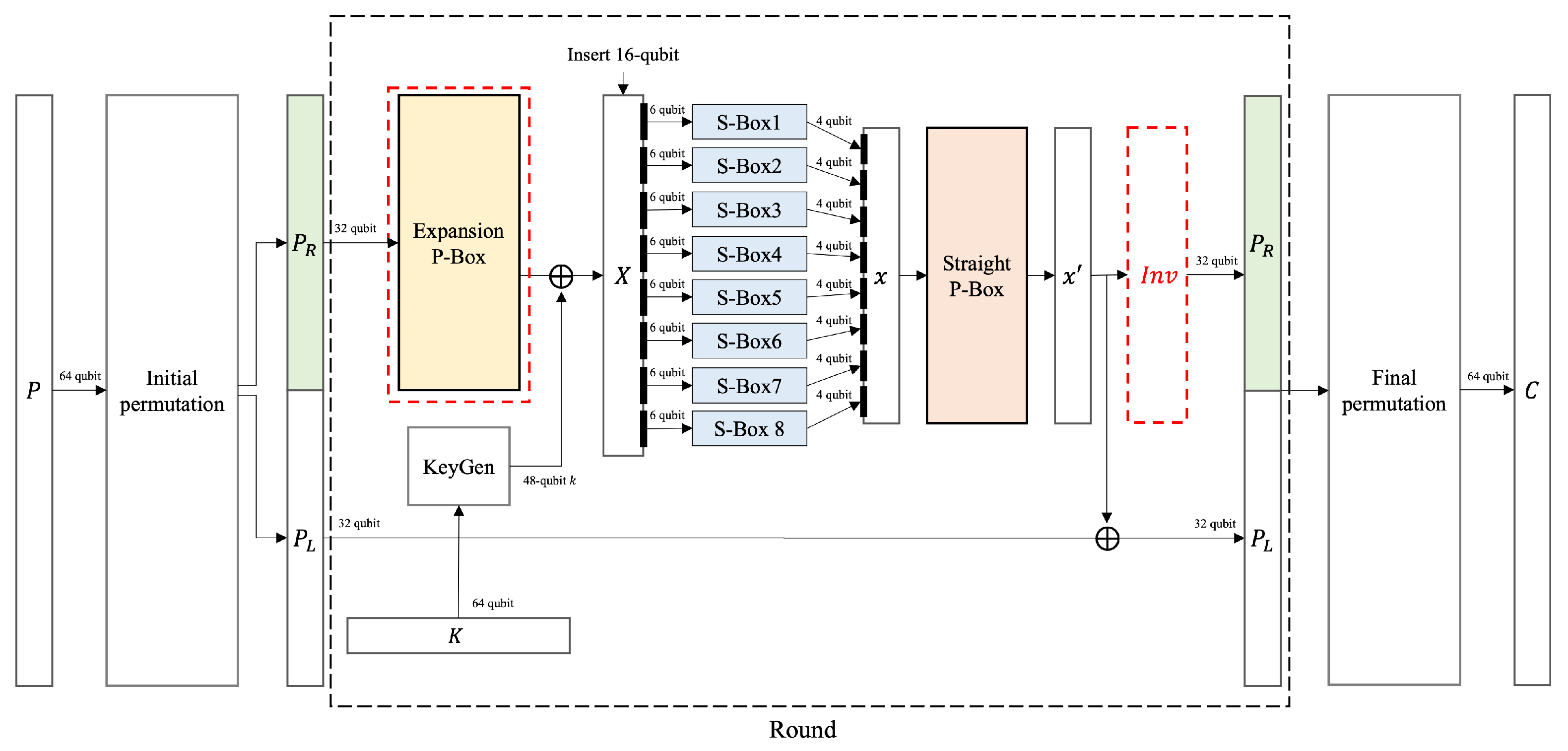
3. Flow of Quantum Circuit for DES and TDES
4. Components of the Quantum Circuit for DES
4.1. Key Generator
4.2. Initial Permutation
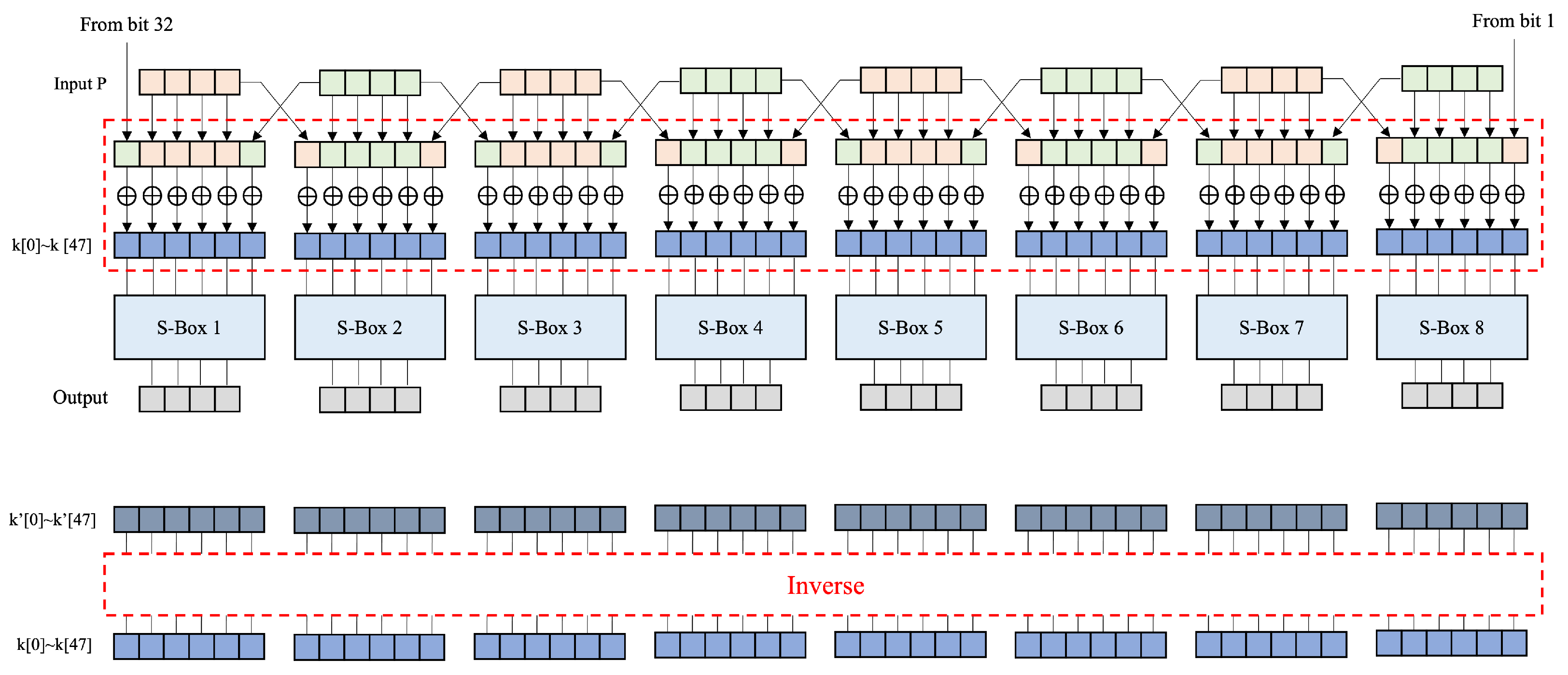
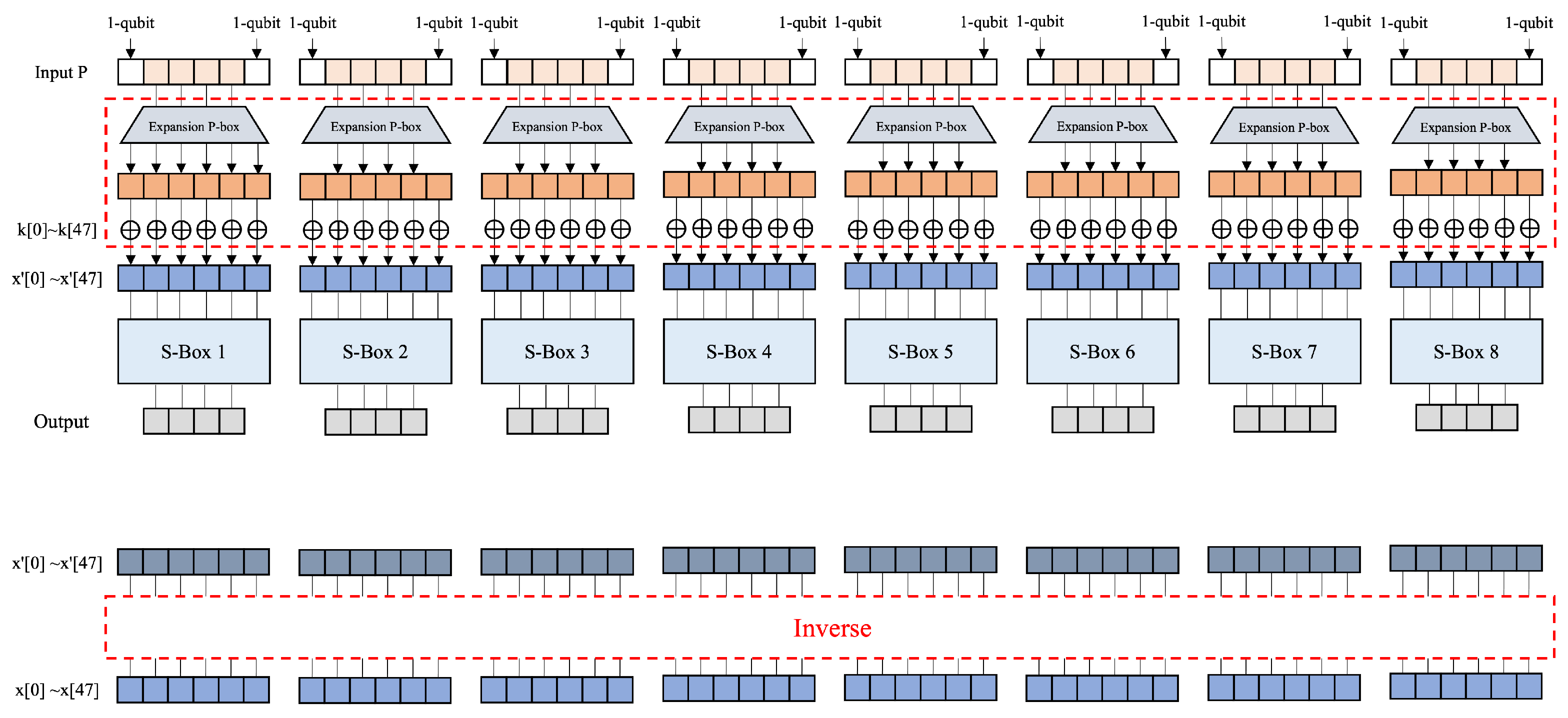
4.3. Expansion P-Box
Optimized Expansion P-Box
- : The message expansion process is skipped. An XOR operation is performed on the message P and key k at the expansion location: k ← CNOT; (e.g., ← CNOT). The k is used as input to the S-Box. Once it is used in the S-Box, the k is inverted back to its original value. This method requires an operation to invert k, and the S-Boxes operate in parallel.
- : The message expansion process is skipped. An XOR operation is performed on P and k at the expansion location: P ← CNOT; (e.g., ← CNOT). In this method, the eight S-Boxes cannot operate in parallel because the expanded indices overlap. To address this limitation, only S-Boxes with non-overlapping indices operate in parallel: Parallel 1 includes S-Boxes 1, 3, 5, and 7; Parallel 2 includes S-Boxes 2, 4, 6, and 8. This approach enables efficient parallel processing without any index conflicts. First, after completing the first parallel S-Box operation, the P is restored through an inverse function. The returned P is XORed with the appropriate k and used as the input for the second parallel operation. After completing the operations of the second parallel set of S-Boxes, the inverse function is applied to invert the value of P to its original state.
| S-Box1: P[31], P[0], P[1], P[2], P[3], P[4] | S-Box2: P[3], P[4], P[5], P[6], P[7], P[8] |
| S-Box3: P[7], P[8], P[9], P[10], P[11], P[12] | S-Box4: P[11], P[12], P[13], P[14], P[15], P[16] |
| S-Box5: P[15], P[16], P[17], P[18], P[19], P[20] | S-Box6: P[19], P[20], P[21], P[22], P[23], P[24] |
| S-Box7: P[23], P[24], P[25], P[26], P[27], P[28] | S-Box8: P[27], P[28], P[29], P[30], P[31], P[0] |
| Algorithm 1 Key XOR in expansion P-Box Type A |
| Input: 1: ← 2: ← 3: ← 4: ← 5: ← 6: ← return: |
| Algorithm 2 Key XOR in expansion P-Box Type B |
| Input: 1: ← 2: ← 3: ← 4: ← 5: ← 6: ← return: |
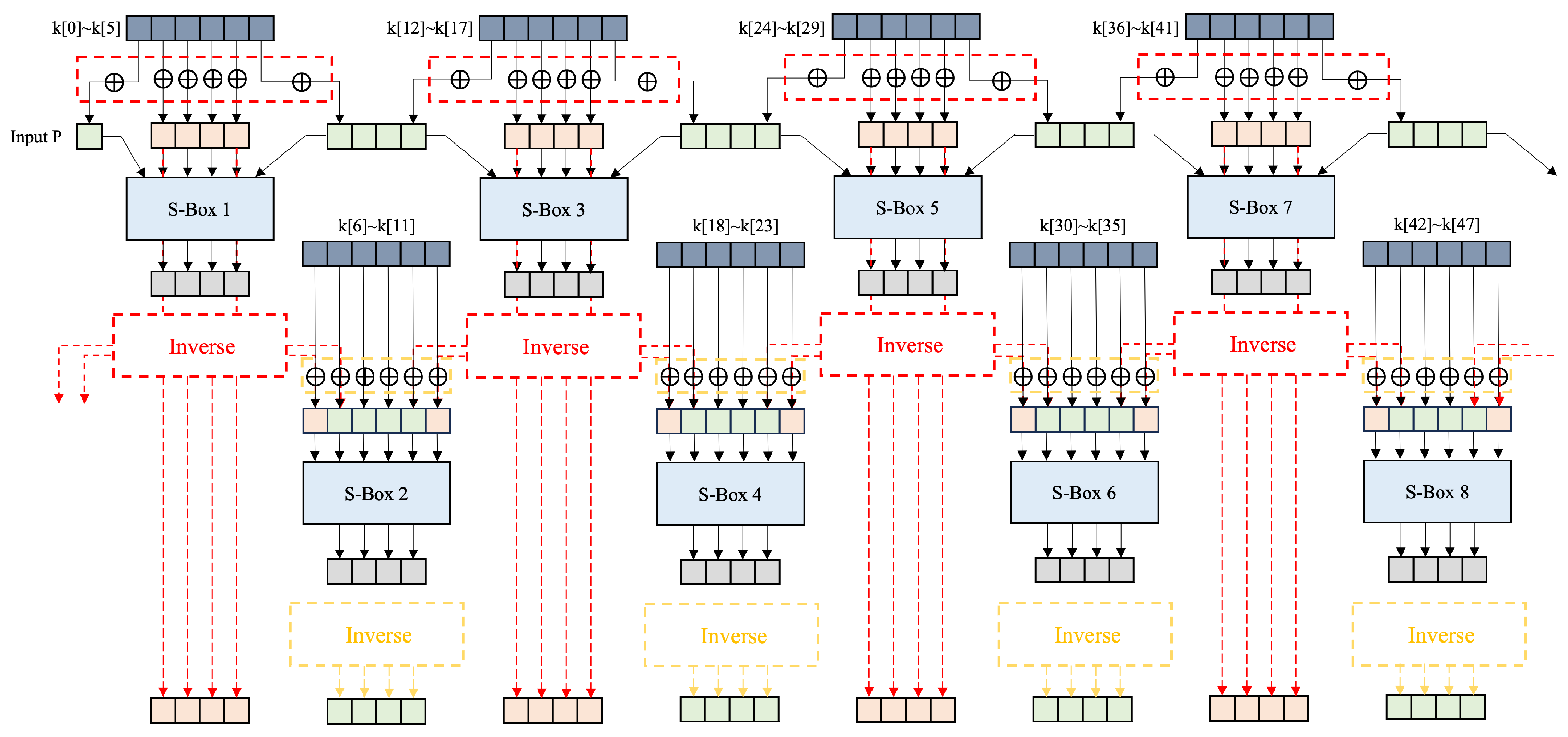
4.4. S-Box
Optimized S-Box for DES
- Type A S-Box: A single ancilla n-qubit is continuously reused across S-Box 1 to S-Box 8. The inverse point of the ancillary qubit remains the same throughout all S-Boxes. However, instead of storing results in ancillary qubits, four dedicated qubits are assigned for each S-Box to store the result. Therefore, a total of 512 qubits are additionally required, calculated as follows: S-Box count(8) × Result qubits per S-Box(4) × r(16). In this approach, after an ancilla qubit is used in an S-Box, all of them are reset using the inverse operation. As a result, the reset ancillary qubits become available for reuse in subsequent S-Box operations. By utilizing inverse operations, ancilla qubits can be reused, reducing the overall qubit count compared to the basic implementation. However, because each S-Box must be fully processed before moving to the next, parallel operation is impossible, leading to increased circuit depth. The ancilla qubit required for the next S-Box is maintained, and an inverse operation is added per S-Box for initialization. In the last round, the ancilla inverse operation is omitted.
- Type B S-Box: This approach assigns four qubits to store the results of each S-Box operation. Consequently, a total of 512 additional qubits are required, calculated as follows: S-Box count(8) × Result qubits per S-Box(4) × r(16). Ancilla arrays are allocated separately for each S-Box, enabling parallel operation. After completing their use in the S-Box, all ancilla qubit arrays are reset through inverse operations, making them available for reuse in the next round. This allows for efficient ancilla qubit recycling, potentially reducing the total number of qubits required for the implementation. All ancilla qubits used in previous rounds are preserved and can be reused in subsequent rounds. An inverse operation is added per round for ancilla qubit initialization, but in the last round, the inverse operation is omitted.
| S-Box | Ancilla Qubit | Inverse Point | Parallel | |
|---|---|---|---|---|
| Register | Result | |||
| Type A | n-qubit | S-Box | X | |
| Type B | qubits | Round | O | |
4.5. Straight P-Box
| X0 | X1 | X2 | X3 | X4 | X5 | X6 | X7 | → | X15 | X6 | X19 | X20 | X28 | X11 | X27 | X16 |
| X8 | X9 | X10 | X11 | X12 | X13 | X14 | X15 | X0 | X14 | X22 | X25 | X4 | X17 | X30 | X9 | |
| X16 | X17 | X18 | X19 | X20 | X21 | X22 | X23 | X1 | X7 | X23 | X13 | X31 | X26 | X2 | X8 | |
| X24 | X25 | X26 | X27 | X28 | X29 | X30 | X31 | X18 | X12 | X29 | X5 | X21 | X10 | X3 | X24 |
4.6. Final Permutation
| C0 | C1 | C2 | C3 | C4 | C5 | C6 | C7 | → | C39 | C7 | C47 | C15 | C55 | C23 | C63 | C31 |
| C8 | C9 | C10 | C11 | C12 | C13 | C14 | C15 | C38 | C6 | C46 | C14 | C54 | C22 | C62 | C30 | |
| C16 | C17 | C18 | C19 | C20 | C21 | C22 | C23 | C37 | C5 | C45 | C13 | C53 | C21 | C61 | C29 | |
| C24 | C25 | C26 | C27 | C28 | C29 | C30 | C31 | C36 | C4 | C44 | C12 | C52 | C20 | C60 | C28 | |
| C32 | C33 | C34 | C35 | C36 | C37 | C38 | C39 | C35 | C3 | C43 | C11 | C51 | C19 | C59 | C27 | |
| C40 | C41 | C42 | C43 | C44 | C45 | C46 | C47 | C34 | C2 | C42 | C10 | C50 | C18 | C58 | C26 | |
| C48 | C49 | C50 | C51 | C52 | C53 | C54 | C55 | C33 | C1 | C41 | C9 | C49 | C17 | C57 | C25 | |
| C56 | C57 | C58 | C59 | C60 | C61 | C62 | C63 | C32 | C0 | C40 | C8 | C48 | C16 | C56 | C24 |
5. Analysis of Quantum Resources
6. Conclusions
Author Contributions
Funding
Data Availability Statement
Conflicts of Interest
References
- Grover, L.K. A fast quantum mechanical algorithm for database search. In Proceedings of the 28th Annual ACM Symposium on Theory of Computing, Philadelphia, PA, USA, 22–26 May 1996; pp. 212–219. [Google Scholar]
- Shor, P.W. Polynomial-time algorithms for prime factorization and discrete logarithms on a quantum computer. SIAM Rev. 1999, 41, 303–332. [Google Scholar] [CrossRef]
- Grassl, M.; Langenberg, B.; Roetteler, M.; Steinwandt, R. Applying Grover’s algorithm to AES: Quantum resource estimates. In Proceedings of the Post-Quantum Cryptography, Fukuoka, Japan, 24–26 February 2016; Springer: Cham, Switzerland, 2016; pp. 29–43. [Google Scholar]
- Anand, R.; Maitra, A.; Mukhopadhyay, S. Grover on SIMON. Quantum Inf. Process. 2020, 19, 340. [Google Scholar] [CrossRef]
- Chauhan, A.K.; Sanadhya, S.K. Quantum resource estimates of grover’s key search on ARIA. In Proceedings of the Security, Privacy, and Applied Cryptography Engineering: 10th International Conference, SPACE 2020, Kolkata, India, 17–21 December 2020; Proceedings 10. Springer: Cham, Switzerland, 2020; pp. 238–258. [Google Scholar]
- Das, P.; Biswas, S.; Kanoo, S. Quantum implementation of SHA1 and MD5 and comparison with classical algorithms. Quantum Inf. Process. 2024, 23, 176. [Google Scholar] [CrossRef]
- Rahman, M.; Paul, G. Grover on KATAN: Quantum resource estimation. IEEE Trans. Quantum Eng. 2022, 3, 1–9. [Google Scholar]
- Huang, Z.; Sun, S. Synthesizing quantum circuits of AES with lower t-depth and less qubits. In Proceedings of the International Conference on the Theory and Application of Cryptology and Information Security, Taipei, Taiwan, 5–9 December 2022; Springer: Cham, Switzerland, 2022; pp. 614–644. [Google Scholar]
- Jang, K.; Baksi, A.; Kim, H.; Song, G.; Seo, H.; Chattopadhyay, A. Quantum analysis of AES. Cryptol. Eprint Arch. 2022. Available online: https://eprint.iacr.org/2022/683 (accessed on 30 March 2025).
- Zou, J.; Li, L.; Wei, Z.; Luo, Y.; Liu, Q.; Wu, W. New quantum circuit implementations of SM4 and SM3. Quantum Inf. Process. 2022, 21, 181. [Google Scholar] [CrossRef]
- Song, G.; Jang, K.; Seo, H. Improved Low-Depth SHA3 Quantum Circuit for Fault-Tolerant Quantum Computers. Appl. Sci. 2023, 13, 3558. [Google Scholar] [CrossRef]
- ProjectQ Framework. ProjectQ: An Open Source Software Framework for Quantum Computing. Available online: https://projectq.ch/ (accessed on 25 March 2025).
- ProjectQ Framework. ProjectQ GitHub Repository. Available online: https://github.com/ProjectQ-Framework/ProjectQ (accessed on 25 March 2025).
- FIPS PUB 46; Federal Information Processing Standards Publication 46. National Bureau of Standards: Gaithersburg, MA, USA, 1977.
- Song, G.; Eum, S.; Kwon, H.; Sim, M.; Lee, M.; Seo, H. Optimized Quantum Circuit for Quantum Security Strength Analysis of Argon2. Electronics 2023, 12, 4485. [Google Scholar] [CrossRef]
- Kwan, M. Reducing the Gate Count of Bitslice DES. IACR Cryptol. ePrint Arch. 2000, 2000, 51. [Google Scholar]
- Jang, K.b.; Kim, H.J.; Song, G.J.; Sim, M.J.; Woo, E.S.; Seo, H.J. Quantum Cryptanalysis for DES Through Attack Cost Estimation of Grover’s Algorithm. J. Korea Inst. Inf. Secur. Cryptol. 2021, 31, 1149–1156. [Google Scholar]
| Opt. | P-Box | S-Box | |
|---|---|---|---|
| Version 1 | Version 2 | ||
| Qubit | Basic | Basic | Basic |
| Type A | Type A | ||
| Type B | Type B | ||
| Type A | Basic | Basic | |
| Type A | Type A | ||
| Type B | Type B | ||
| Type B | - | - | |
| Type A | Type A | ||
| Type B | Type B | ||
| Depth | Basic | Basic | Basic |
| Type A | Type A | ||
| Type B | Type B | ||
| Type A | Basic | Basic | |
| Type A | Type A | ||
| Type B | Type B | ||
| Type B | Basic | Basic | |
| Type A | Type A | ||
| Type B | Type B | ||
| Function | Quantum Resources | ||||
|---|---|---|---|---|---|
| Qubit | Toffoli | CNOT | 1qCliff | Depth | |
| Basic | 7536 | 3424 | 12,992 | 7184 | 1044 |
| Type A | 7280 | 3424 | 12,480 | 7184 | 1044 |
| Type B | 7280 | 3424 | 12,480 | 7184 | 1661 |
| Function | Quantum Resources | ||||
|---|---|---|---|---|---|
| Qubit | Toffoli | CNOT | 1qCliff | Depth | |
| Basic | 816 | 6848 | 20,160 | 11,232 | 2162 |
| Type A | 560 | 6848 | 19,648 | 11,232 | 2192 |
| Type B | − | − | − | − | − |
| Function | Quantum Resources | ||||
|---|---|---|---|---|---|
| Qubit | Toffoli | CNOT | 1qCliff | Depth | |
| S-Box1 | 63 | 32 | 85 | 75 | 60 |
| S-Box2 | 56 | 29 | 77 | 56 | 43 |
| S-Box3 | 57 | 27 | 86 | 66 | 52 |
| S-Box4 | 42 | 17 | 69 | 30 | 47 |
| S-Box5 | 62 | 29 | 91 | 61 | 65 |
| S-Box6 | 57 | 26 | 85 | 51 | 52 |
| S-Box7 | 57 | 29 | 80 | 57 | 67 |
| S-Box8 | 54 | 25 | 79 | 53 | 59 |
| Total | 448 | 214 | 652 | 449 | 67 |
| Function | Quantum Resources | ||||
|---|---|---|---|---|---|
| Qubit | Toffoli | CNOT | 1qCliff | Depth | |
| S-Box1 | 56 | 32 | 72 | 77 | 65 |
| S-Box2 | 50 | 28 | 66 | 57 | 63 |
| S-Box3 | 53 | 28 | 75 | 60 | 47 |
| S-Box4 | 39 | 18 | 63 | 43 | 53 |
| S-Box5 | 56 | 30 | 78 | 63 | 64 |
| S-Box6 | 53 | 31 | 66 | 62 | 74 |
| S-Box7 | 51 | 27 | 72 | 56 | 52 |
| S-Box8 | 50 | 27 | 69 | 57 | 68 |
| Total | 408 | 221 | 561 | 487 | 74 |
| S-Box (Version 1) | ||||||||
|---|---|---|---|---|---|---|---|---|
| Function | Quantum Resources | |||||||
| S-Box | P-Box | Qubit | Toffoli Depth | Toffoli | CNOT | 1qCliff | Depth | TD·M |
| (M) | (TD) | |||||||
| Basic | Basic | 7536 | 1024 | 3424 | 12,992 | 7184 | 1044 | 7,716,864 |
| A | 7280 | 1024 | 3424 | 12,480 | 7184 | 1044 | 7,454,720 | |
| B | 7280 | 1952 | 3424 | 12,480 | 7184 | 1661 | 14,210,560 | |
| A | Basic | 943 | 6848 | 6848 | 20,672 | 11,232 | 13,893 | 6,457,664 |
| A | 687 | 6848 | 6848 | 20,160 | 11,232 | 13,893 | 4,704,576 | |
| B | 687 | 6848 | 6848 | 20,160 | 11,232 | 13,892 | 4,704,576 | |
| B | Basic | 1328 | 1024 | 6848 | 20,672 | 11,232 | 2162 | 1,359,872 |
| A | 1072 | 1024 | 6848 | 20,160 | 11,232 | 2192 | 1,097,728 | |
| B | 1072 | 1952 | 6848 | 20,160 | 11,232 | 2982 | 2,092,544 | |
| S-Box (Version 2) | ||||||||
|---|---|---|---|---|---|---|---|---|
| Function | Quantum Resources | |||||||
| S-Box | P-Box | Qubit | Toffoli Depth | Toffoli | CNOT | 1qCliff | Depth | TD·M |
| (M) | (TD) | |||||||
| Basic | Basic | 6896 | 1024 | 3536 | 11,536 | 7,600 | 1012 | 7,061,504 |
| A | 6640 | 1024 | 3536 | 11,024 | 7600 | 1011 | 6,799,360 | |
| B | 6640 | 2016 | 3536 | 11,024 | 7600 | 1468 | 13,386,240 | |
| A | Basic | 936 | 7072 | 14,080 | 33,856 | 21,888 | 29,314 | 6,619,392 |
| A | 680 | 7072 | 14,080 | 33,344 | 21,888 | 29,312 | 4,808,960 | |
| B | 680 | 7072 | 7072 | 17,856 | 11,456 | 14,772 | 4,808,960 | |
| B | Basic | 1328 | 1024 | 13,246 | 36,636 | 20,316 | 4034 | 1,359,872 |
| A | 1072 | 1024 | 13,246 | 36,124 | 20,316 | 4064 | 1,097,728 | |
| B | 1072 | 2016 | 6848 | 20,160 | 11,232 | 2982 | 2,161,152 | |
| S-Box (Version 1) | ||||||||
|---|---|---|---|---|---|---|---|---|
| Function | Quantum Resources | |||||||
| S-Box | P-Box | Qubit | Toffoli Depth | Toffoli | CNOT | 1qCliff | Depth | TD·M |
| (M) | (TD) | |||||||
| Basic | Basic | 816 | 2048 | 6848 | 20,160 | 11,232 | 2162 | 1,671,168 |
| A | 560 | 2048 | 6848 | 19,648 | 11,232 | 2192 | 1,146,880 | |
| A | Basic | 936 | 13,696 | 14,080 | 33,856 | 21,888 | 29,314 | 12,819,456 |
| A | 680 | 13,696 | 14,080 | 33,344 | 21,888 | 29,312 | 9,313,280 | |
| B | 680 | 6848 | 7072 | 17,856 | 11,456 | 14,772 | 4,656,640 | |
| B | Basic | 1288 | 2048 | 13,444 | 32,262 | 18,598 | 4322 | 2,637,824 |
| A | 1032 | 2048 | 13,440 | 31,744 | 18,592 | 4352 | 2,113,536 | |
| B | 1032 | 1952 | 7072 | 17,856 | 11,456 | 2843 | 2,014,464 | |
| S-Box (Version 2) | ||||||||
|---|---|---|---|---|---|---|---|---|
| Function | Quantum Resources | |||||||
| S-Box | P-Box | Qubit | Toffoli Depth | Toffoli | CNOT | 1qCliff | Depth | TD·M |
| (M) | (TD) | |||||||
| Basic | Basic | 776 | 2048 | 7072 | 17,856 | 11,104 | 2354 | 1,589,248 |
| A | 520 | 2048 | 7072 | 17,344 | 11,104 | 2384 | 1,064,960 | |
| A | Basic | 1288 | 14,144 | 13,412 | 32,262 | 20,074 | 4386 | 18,217,472 |
| A | 680 | 14,144 | 14,080 | 33,344 | 21,472 | 29,888 | 9,617,920 | |
| B | 680 | 7072 | 7072 | 17,856 | 11,104 | 15,076 | 4,808,960 | |
| B | Basic | 1288 | 2048 | 13,412 | 32,262 | 20,074 | 4386 | 2,637,824 |
| A | 1032 | 2048 | 13,408 | 31,744 | 20,064 | 4416 | 2,113,536 | |
| B | 1032 | 2016 | 7072 | 17,856 | 11,104 | 2907 | 2,080,512 | |
| Algorithm | Quantum Resources | |||||
|---|---|---|---|---|---|---|
| Qubit |
Toffoli Depth (TD) | Toffoli | CNOT | 1qCliff | Depth | |
| DES (depth-optimized) | 6640 | 1024 | 3536 | 11,024 | 7600 | 1011 |
| DES (qubit-optimized) | 520 | 2048 | 7072 | 17,344 | 11,104 | 2384 |
| DES [17] | 6648 | N/A | 3536 | 8032 | 7552 | 3205 |
| Function | Quantum Resources | ||||||
|---|---|---|---|---|---|---|---|
| Opt. | S-Box | P-Box |
Toffoli Depth (TD) | Toffoli | CNOT | 1qCliff | Depth |
| Depth | ver.2 | Type A | |||||
| Basic | |||||||
| Qubit | ver.2 | Type A | |||||
| Basic | |||||||
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Song, G.; Yoon, S.; Seo, H. Quantum Circuit Implementation and Resource Analysis for Triple Data Encryption Standard (DES) (Triple-DES). Mathematics 2025, 13, 1171. https://doi.org/10.3390/math13071171
Song G, Yoon S, Seo H. Quantum Circuit Implementation and Resource Analysis for Triple Data Encryption Standard (DES) (Triple-DES). Mathematics. 2025; 13(7):1171. https://doi.org/10.3390/math13071171
Chicago/Turabian StyleSong, Gyeongju, Seyoung Yoon, and Hwajeong Seo. 2025. "Quantum Circuit Implementation and Resource Analysis for Triple Data Encryption Standard (DES) (Triple-DES)" Mathematics 13, no. 7: 1171. https://doi.org/10.3390/math13071171
APA StyleSong, G., Yoon, S., & Seo, H. (2025). Quantum Circuit Implementation and Resource Analysis for Triple Data Encryption Standard (DES) (Triple-DES). Mathematics, 13(7), 1171. https://doi.org/10.3390/math13071171