1. Introduction
Based on the principles of quantum mechanics, particularly the Heisenberg uncertainty principle and the No-Cloning theorem, quantum cryptography transcends the computational limitations of classical encryption by utilizing physical laws to guarantee security. For example, the famous BB84 protocol [
1] enables two parties to generate a shared secret key with unconditional security. This security arises from the impossibility of measuring or copying an unknown quantum state chosen from four mutually unbiased base states rather than unproven mathematical hardness assumptions. Thus, quantum cryptography’s security is information-theoretically verifiable, rendering it immune to advances in quantum computing. In the past three decades, researchers have attempted to use quantum cryptography to address other security issues, such as quantum secret sharing [
2,
3,
4,
5], quantum secure direct communication [
6,
7,
8,
9], quantum private comparison [
10,
11,
12,
13,
14], and so on.
The extension of quantum cryptographic principles to multi-party computation introduces quantum private set intersection (QPSI), which is a critical tool for secure collaborative data analysis. In QPSI, multiple parties aim to compute the intersection of their private data sets without revealing any information beyond the intersection itself. Traditional classical private set intersection protocols face vulnerabilities to quantum attacks, as their security often hinges on computational assumptions that quantum computers could invalidate. In contrast, QPSI uses quantum-resistant techniques, such as single-photon manipulation [
15,
16,
17,
18], rotation operations [
19,
20,
21], and entanglement-based correlations [
22,
23,
24], to achieve quantum-proof security. By embedding security into the fabric of quantum physics, QPSI protocols offer a future-proof solution for privacy-preserving applications, such as contact tracking, federated learning, and medical data sharing, where the integrity of sensitive information must be preserved against both classical and quantum threats.
As demonstrated in Ref. [
25], some theoretically secure quantum cryptography protocols remain susceptible to man-in-the-middle attacks, due to the lack of identity verification. This is especially true for QPSI. In a two-party QPSI protocol, if an adversary successfully impersonates a legitimate participant, he can easily steal the private data set of the other participant. Here, he does not need to perform any attack operation, but only needs to enter his secret data set as the full set when executing the protocol and then obtain the other private data set based on the final intersection result. Therefore, identity authentication should be considered when designing a practical QPSI protocol. In Ref. [
25], Wu et al. delved into the issue and proposed a quantum protocol theoretically to achieve the computation of private sets with identity authentication. The protocol hinges on the quantum entanglement properties of Greenberger–Horne–Zeilinger (GHZ) states, ensuring that only two authenticated users can compute the private set intersection/union cardinality. Stimulated by this work, an authenticated multi-party quantum private set intersection protocol with single particles is presented in this paper. In the designed protocol, a third party is incorporated to enable the secure execution of private set intersection involving multiple participating entities. First, the TP shares a master key with each individual party that forms the cornerstone for authenticating the identity of every participant, ensuring a secure and verified environment throughout the protocol’s execution. Secondly, single-particle quantum states prepared by the TP, which serve as carriers of sensitive data, are sequentially transmitted among the participating parties. Upon receiving the circulating particle, each party applies two phase operations to it. One operation is employed to encode the party’s private data, while the other aims to keep the information confidential. Similarly to the BB84 protocol, mutually unbiased bases are utilized here to ensure the secure transmission of the particles. Finally, based on the public message declared by the TP, all participants can simultaneously determine the intersection of their private data sets. In this way, the goal of the protocol is achieved in a secure and efficient manner. Note that the TP in the proposed protocol here is assumed to be semi-honest [
26]. If he were misbehaving, TP could collude with other participants to attack the protocol. In such a case, the protocol could be viewed as secure computation between two parties: one being the honest participants, and the other being the misbehaving TP combined with the remaining dishonest participants. According to the no-go theorem [
27,
28], such a quantum secure computation protocol would theoretically be unsafe. Therefore, like most quantum secure multi-party computation protocols, the TP in this protocol is also assumed to be semi-honest. That is, he behaves honestly during the protocol execution and refrains from colluding with other participants, but may attempt to infer more information afterward.
The remainder of this paper is organized as follows. The relevant preliminary knowledge related to this paper is introduced in
Section 2. Subsequently, the proposed multi-party quantum private set intersection protocol and a toy example are elaborated in
Section 3 and
Section 4, respectively. The security of the proposed protocol is analyzed in
Section 5. In
Section 6, the experimental simulation is provided to demonstrate its feasibility. Finally,
Section 7 offers a short conclusion.
3. Proposed Protocol
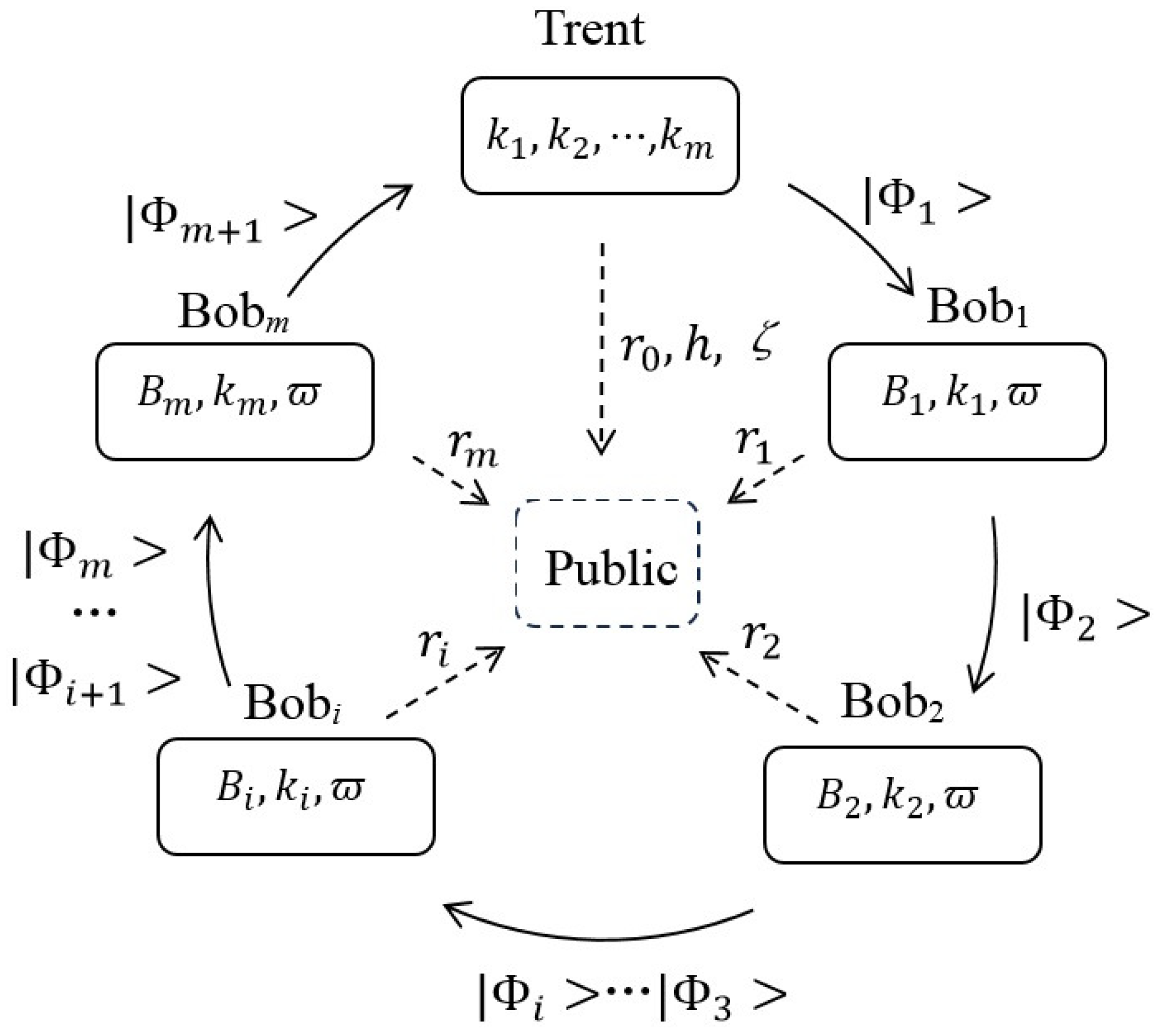
In this section, we propose a multi-party QPSI protocol with identity authentication. For generality, we consider a system model consisting of
m participants, Bob
i (
) and a third party, Trent. Each participant Bob
i holds a private data set
, and has a secure key
with Trent. With the help of Trent, the
m participants aim to securely compute the intersection of their private sets, denoted as
. Meanwhile, the identity of each Bob
i is authenticated by Trent. The entire communication process is shown in
Figure 1. The proposed protocol consists of four phases, which are detailed as follows.
I. Initializing phase
I.1.
m participants Bob
i request a PSI from Trent. They each generate a random bit string
and send it to Trent. Meanwhile, according to the following rule,
each participant Bob
i converts his secret private set
into an
n-bit string
.
I.2. Based on the actual environment and security requirements, Trent sets a security parameter , which is the number of particles detected. Then, he chooses a hash function from a class of universal one-way hash function, , where and . He generates a random bit string , and calculates m private strings, , where . At last, Trent announces , h, and to all participants.
I.3. After receiving the messages announced by Trent, each participant Bobi obtains his authenticated message by calculating . After that, these m participants agree on a permutation function , which transforms each element of the set into a unique element within the same set, with no repetitions or omissions. Finally, each participant Bobi generates a private -bit string, , which is used as the check samples. Bobi utilizes the function to permute the bit string and obtain a new bit string .
II. Quantum phase
II.1. Trent prepares particles, each initially in the state . For the j-th particle (), Trent generates two random numbers . According to these two values, he performs the operation on the particle, and obtains the state, . Finally, Trent sends these particles in the state to the first participant Bob1.
II.2. Upon receiving the quantum state (), Bob1 performs his encoding operation on the signal particle, and executes the encrypting operation, . In this way, Bob1 obtains the state , where and sends it to the next participant, Bob2.
II.3. Bobi () conducts a process analogous to that in II.2. Specifically, when Bobi receives the j-th signal particle, he performs his operation on it. Then, he sends the quantum state to the subsequent participant. Notably, the last participant, Bobm, returns these signal particles to Trent.
II.4. When receiving the quantum state , Trent performs the corresponding decrypting operation, , on the state . Then, he measures these signal particles in the bases , and obtains the result, . According to and , Trent calculates , and obtains .
III. Eavesdropping check phase
The m participants tell Trent the positions of the test samples, i.e., , and tell Trent their s, respectively. In terms of these public messages, Trent uses these samples to execute the eavesdropping detection process. Concretely, for the j-th sample (), Trent judges whether is equal to or not. If they are not equal, the number of errors is increased by 1. Finally, if the error rate exceeds a predefined threshold, Trent believes that the protocol is eavesdropping, abandons and restarts the protocol. Otherwise, he proceeds to the next step.
IV. Result announcement phase
After abandoning these test samples, Trent obtains the remaining n results to get . When , he announces the value of j. In accordance with this message, all participants infer that the -th element is present in the intersection of their private data sets. In this way, the m participants simultaneously acquire the intersection of their private data sets, .
4. Toy Example
In this section, we will take a toy example (depicted in
Table 1) to better understand the presented protocol and show that it is correct. Suppose Bob
1, Bob
2, Bob
3, and Bob
4 are four parties (
,
), and
(
) are their private sets, respectively, where
and
. In accordance with Equation (
7), the four participants each calculate their private six-bit strings,
= ‘010010’,
= ‘001110’,
= ‘100110’, and
= ‘000011’. Additionally, they each share four master keys,
= ‘0010111111’,
= ‘1100011010’,
= ‘0100000110’, and
= ‘0011001111’, with Trent.
In Step I.1, these participants respectively generate four random bit strings,
= ‘0011010001’,
= ‘1101000010’,
= ‘0111111101’, and
= ‘1111001011’, and send them to Trent. Then, Trent sets
(
),
= ‘0100000110’, and the hash function
h. Here, for simplicity, the hash function is set as
, where ⊕ denotes a bitwise exclusive-OR (XOR) operation. Based on this function and
, Bob
i (i = 1, 2, 3, 4) and Trent obtain
, depicted in
Table 1, and keep it secret. In Step I.3, four participants respectively generate four 4-bit strings,
= ‘1101’,
= ‘1000’,
= ‘0101’, and
= ‘0100’, and agree on a permutation function
that is only known to them. Based on this function, the corresponding permutation table (
Table 2) is derived. Then, Bob
i can calculate
as specified in
Table 1.
In Step II, Trent generates two random bit strings
= ‘1000010101’, and
= ‘1011011000’, and prepares 10 particles that are in the state
. After that, these ten signal particles are transmitted among the four participants. Each participant Bob
i performs his encoding operation and encrypting operation on these particles, and obtains the state
as outlined in
Table 1. In Step II.4, Trent applies the corresponding decrypting operation to these particles, and measures them in the basis
. For example, the first qudit is in the state
, after Trent applies the operation
on state
. Subsequently, four participants, respectively, execute operations
,
,
, and
, when they receive this qudit. In this case, the state is transformed to
and returned to Trent. After that, Trent executes the decrypting operation
, and obtains the measurement result ‘5’. From this result and the first bit of
, he deduces that the first bit of
Z is ‘4’.
In the eavesdropping check phase, the four participants tell Trent the positions of four samples, i.e., 2, 5, 6, and 9, and their s. Based on these messages and Z, Trent determines whether the particles have been transmitted securely. After discarding the four samples, Trent obtains , and announces it in Step IV. From this public message and the permutation function , the four participants can concurrently ascertain the intersection of their private data sets, i.e., .
From the above example, it can be seen that the proposed protocol requires that the dimension of the signal particles be a prime number greater than the number of participants, . When the number of participants is large, this prime number becomes very large, which greatly limits the practicality of the proposed protocol. To solve this problem, we can group the users. Concretely, all participants are randomly divided into g disjoint groups, and then each group of participants performs the proposed protocol with Trent. In this way, Trent can obtain the intersection of private data sets of participants in each of the g groups, and further intersecting these intersections can yield the intersection of all private data sets. This solution effectively addresses the issue of the number of participants in the proposed protocol, but may lead to the leakage of some information to Trent, thereby reducing the security level of the protocol.
To further address this issue, the Chinese Remainder Theorem can be applied, which is similar to that in Ref. [
30]. Given the number of participants
m, a series of small primes
can be obtained such that
. By executing the proposed protocol for
r rounds, a series of values
can be obtained and satisfy the following equation:
Then, according to the Chinese Remainder Theorem,
can be calculated,
where
,
, and
. Next, let us consider the same scenario as in the above example. Here, the four master keys, four private data sets, and two functions (
h,
) are identical to those in the previous example and are denoted using the same notation. Additionally, Trent and four participants agree on two primes
and
, and execute the proposed protocol in two rounds.
In the first round, Trent and four participants respectively generate five new random bit strings,
= ‘1101000010’,
= ‘0111111101’,
= ‘1111001011’,
= ‘0100000110’, and
= ‘1111101100’. Based on two new random bit strings
= ‘0000000110’ and
= ‘0001001111’, Trent prepares ten qubits in the state
and transmits them to Bob
1. After four participants respectively perform their operation on these qubits and send them back to Trent, he measures these qubits and obtains
= ‘011101’. Similarly, in the second round, ten qutrits are used as signal particles and transmitted among Trent and four participants. After that, Trent obtains
= ‘011101’. The corresponding quantum and classical sequences of these two rounds are presented in
Table 3 and
Table 4, respectively. In terms of
and
, Trent calculates
t = ‘411121’ using Equation (
8), and then declares
to four participants.
6. Simulation Experiment
In this section, the feasibility of the multi-party QPSI protocol is verified through an example simulation. The experimental circuit was constructed based on the proposed protocol described in
Section 3 and simulated on IBM quantum experience.
For convenience, the experimental data are taken from
Table 3 and
Table 4. Two rounds of the protocol, based on the primes
and
, were executed to obtain the private set intersection of four participants. Since external attacks and eavesdropping are considered independent processes in quantum protocol design, the quantum circuit in this simulation excludes identity authentication and eavesdropping detection. Therefore, the quantum simulation here focuses solely on implementing Phase II of the protocol. In the first round, the system is initialized as a quantum system with
qubit. Based on this quantum system, the operations in the protocol can be simplified. Specifically, the Fourier transform corresponds to the Hadamard gate (
H), the operations
and
correspond to the identity gate
I, whereas
,
and
correspond to the Pauli-Z gate
Z. According to
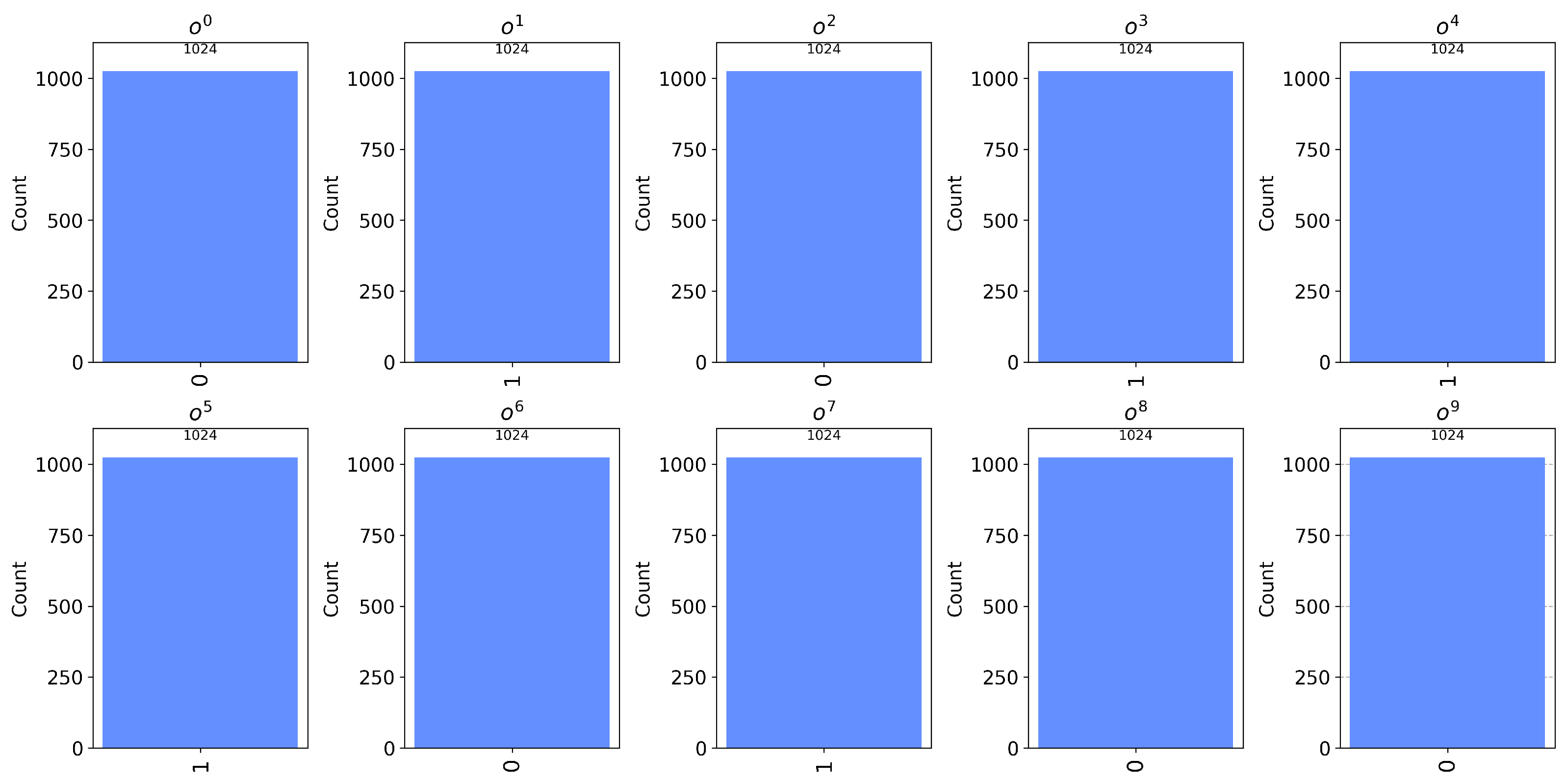
Table 3, Trent prepares ten particles in the protocol, and each participant applies different operations to each particle. To maintain clarity, the circuit diagram depicting the evolution of the first particle is provided in
Figure 2. The measurement results, including those of the first particle and the others, are given as ‘0101110100’, as illustrated in
Figure 3. Then, we can obtain
Z = ‘0101110010’ using
.
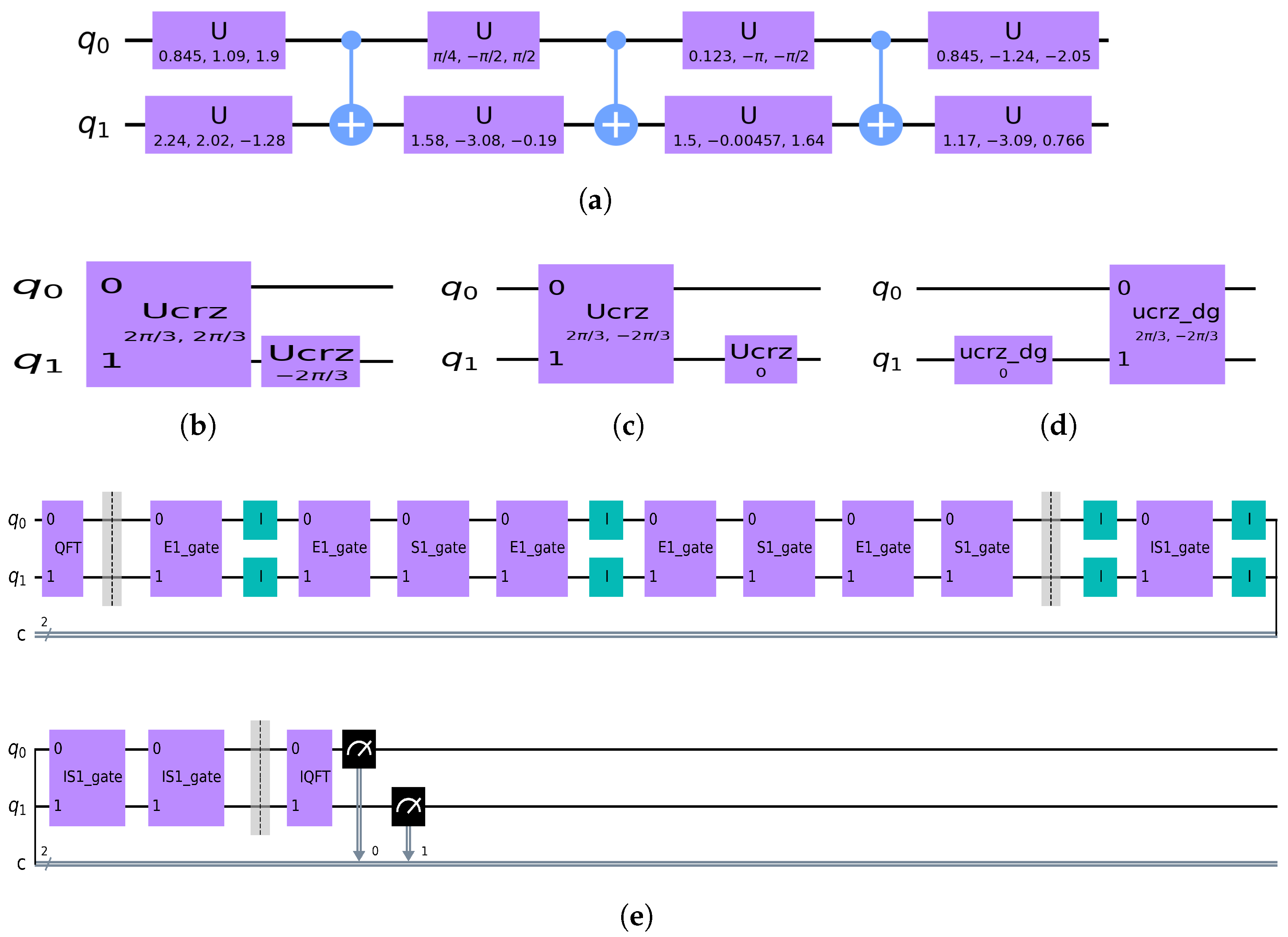
In the second round, the system is initialized as a quantum system consisting of
qubits. According to the protocol, a three-dimensional Fourier transform
is required to prepare the initial state, where
. Since Qiskit supports quantum gates only in dimensions that are powers of two, the transform matrix
is embedded into a four-dimensional space, denoted as matrix
. The corresponding circuit implementation is shown in
Figure 4a. Furthermore, the circuits for the operations
,
, and
are shown in
Figure 4b,
Figure 4c, and
Figure 4d, respectively.
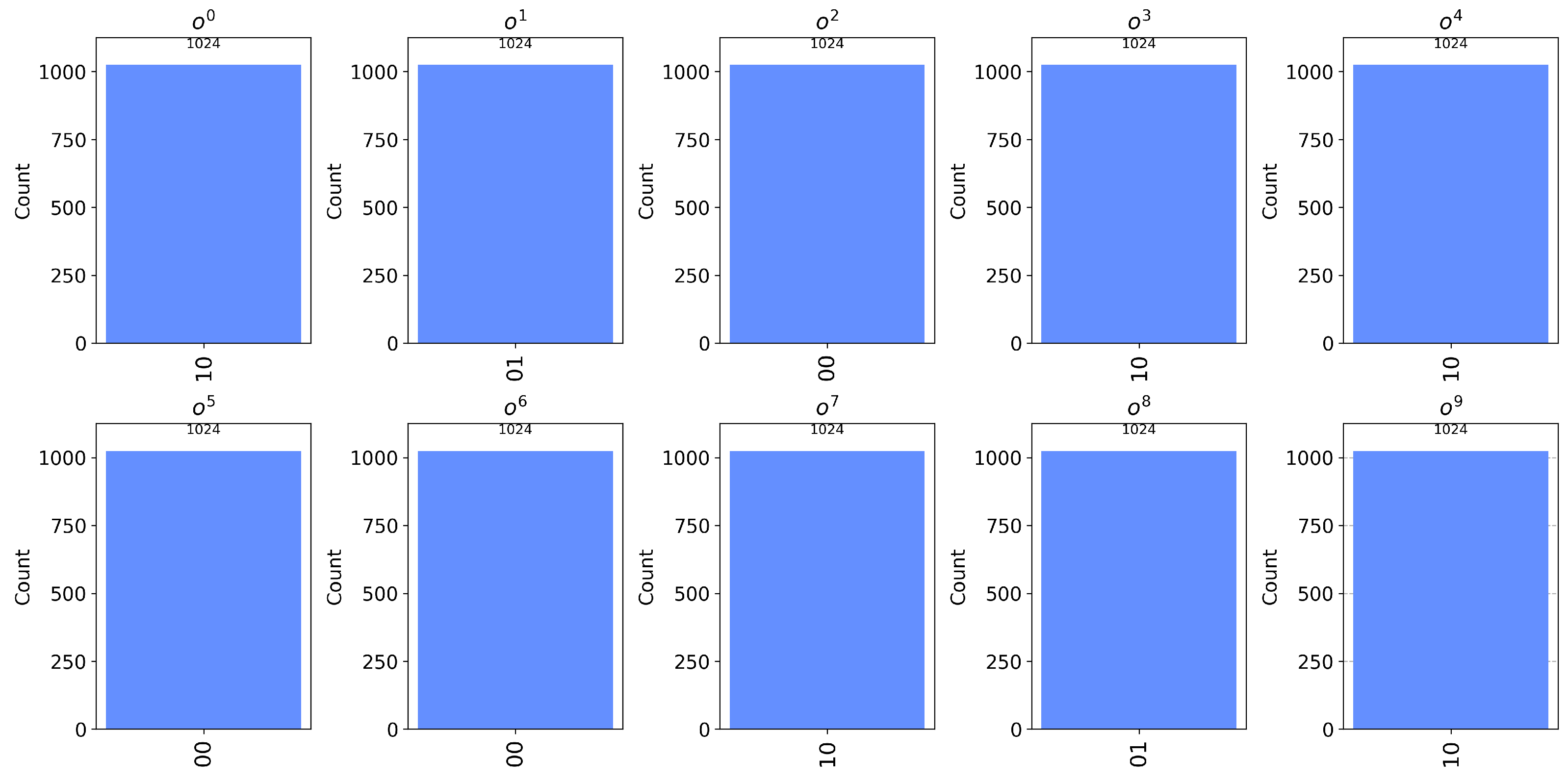
Figure 4e illustrates the circuit for the operations performed on the first particle. The measurement outcomes of this particle and the others are ‘2102200212’, as displayed in
Figure 5. Based on these measurement results, the value
Z = ‘1121102212’ can be obtained by calculating
.
In summary of the above simulation results, the results are consistent with the theoretical descriptions in
Table 3 and
Table 4. This confirms the feasibility of the proposed protocol through a concrete example.
7. Discussion and Summary
Before drawing a conclusion, it is worthwhile to discuss the performance of the proposed protocol. To better demonstrate the performance of our proposed protocol, we compare it with two existing state-of-the-art QPSI protocols, the HZZ protocol [
21] and the WSW protocol [
24]. The comparison presented in
Table 5 is based on various factors, including communication complexity, quantum resources, quantum operations, etc.
Communication cost is an important indicator when analyzing the efficiency of QPSI protocols. As shown in
Figure 1, the protocol involves the transmission of
n qudits between Trent and
m participants. Additionally, from
Table 1, it is deduced that
classical bits are required. In total, the communication overhead includes
qubits and
classical bits. Given that
, the overall communication complexity of the proposed protocol is
. Additionally, in the proposed protocol, there are
particles used as the test samples. Here, the security parameter
is determined by various factors, such as the amount of information, channel noise, and security level. To better compare the eavesdropping detection efficiency of different protocols, we can assume that each detection uses
test samples. In addition to these
qudits, each participant needs to transmit
classical bits to Trent during the eavesdropping detection phase. Thus, the communication cost for the entire eavesdropping detection process is
. In the HZZ protocol, the TP is required to share
m rotation angle information with each participant, and it requires the transmission of
copies of particle sequences to ensure the correctness of the protocol. Therefore, its communication complexity is
. In addition, the HZZ protocol does not provide identity authentication, exposing it to impersonation risks. In the WSW protocol, which only considers the case of two parties,
n three-particle GHZ states are prepared by the TP who sends each participant
n particles. Thus, its quantum communication complexity is
. In order to calculate the result, two participants are required to send the
classical bits message to the TP, which means that its classical communication complexity is
. Therefore, the overall communication complexity of the WSW protocol is
. Furthermore, to ensure the security of the transmitted particles, both the HZZ protocol and the WSW protocol require the insertion of decoy states in the quantum communication, which mandates quantum storage capabilities for all participants. In the proposed protocol, its implementation does not require quantum memory, and only single particles are employed, which makes it more feasible with current technology.
In summary, we propose a multi-party QPSI protocol with identity authentication, by which multiple participants can concurrently obtain the intersection of their private data sets with the help of a semi-honest third party. In the protocol, the TP shares a master key with each participant beforehand, which is used to authenticate their identity. The single particles randomly located in one of the MUB states are prepared by the TP and transmitted among these participants, who respectively encode their private inputs into them. The security of the proposed protocol against some common attacks has been analyzed, which shows that it is secure in the zero-error case. In the protocol, eavesdropping detection and identity authentication are ingeniously integrated, thereby enhancing the protocol’s practical detection efficiency. Moreover, since no explicit identity authentication information is disclosed, the master key can be reused, which improves the applicability of the protocol. Additionally, there is no need for participants to store the traveling particles in the proposed protocol. Thus, the implementation of this protocol does not require quantum memory, which is still difficult to achieve directly at present. Furthermore, the use of only single particles in the proposed protocol makes it more feasible with current technology. Certainly, there are other practical issues during the application of the protocol. For instance, each particle transmission among the participants inevitably incurs optical loss and phase shift. Thus, how to design an effective error recovery strategy in real-world settings will be a focal point of our future work.