Device Independent Quantum Private Queries Based on Quantum Key Distribution
Abstract
1. Introduction
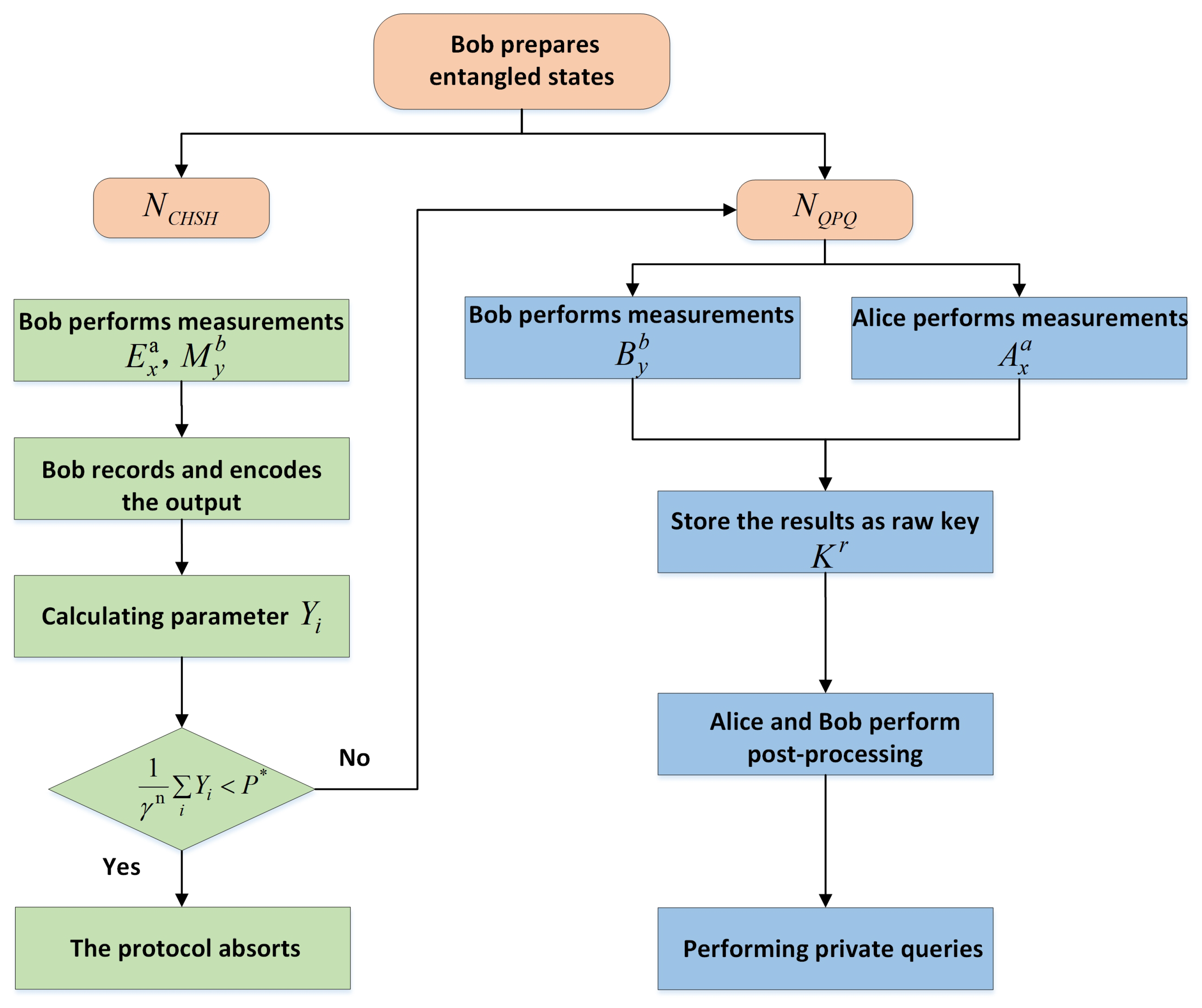
2. Analysis of DI-QPQ with Imperfect Source and Detectors
2.1. Review of DI-QPQ Protocol
- (1)
- Bob prepares a long sequence of entangled states , where and .
- (2)
- For each prepared entangled state, Bob divides it into two sets. One is and the other is . The set contains entangled states, whereas contains entangled states for .
- (3)
- For rounds
- Bob chooses and uniformly at random. If , he measures the first particle of the entangled state in the basis, and if , he measures it in the basis. Similarly, if , Bob measures the second particle of the entangled state in the basis, and if , he measures it in the basis. Here, we consider and .
- Bob records and encodes the output as for the first (second) particle. For the first particle in each pair, if the measurement result is or and if the result is or . For the second particle in each pair, if the measurement result is or and if the result is or .
- Define , if ; otherwise, .
- (4)
- If , Bob aborts the protocol.
- (5)
- Conditional on the event that the local test at Bob’s end has been successful, Bob proceeds to the subset and sends the other half of the remaining entangled pairs to Alice.
- (6)
- Alice performs the private query phase as in [26] or any other entanglement-based QPQ protocol.
2.2. Security of DI-QPQ Protocol with Imperfect Sources and Detectors
3. Practical Quantum Private Queries with Imperfect Sources and Detectors
- (1)
- The database holder Bob prepares a long sequence of entangled photon pairs in the statewhereThe parameter can be selected flexibly.
- (2)
- For each prepared entangled state, Bob divides it into two sets and . The set contains entangled states, which is used to conduct the CHSH local test, whereas contains entangled states for , which is used to perform private queries.For round in , Bob chooses and uniformly at random. denotes Bob measures the first particle of the entangled state in the basis. If , he measures it in the basis. If , Bob measures the second particle of the entangled state in the basis, and if , he measures it in the basis. Here, we considerWe use positive-operator valued measures (POVMs) to describe Bob’s measurements: Bob randomly performs one of two possible POVMs denoted by , where and represent the basis choice for the first and the second particles of the entangled state, respectively. Taking signal loss and detection inefficiency into account, each measurement has three possible outcomes , where ∅ represents the empty detection event.
- (3)
- Bob records and encodes the output as for the first (second) particle. For the first particle in each pair, if the measurement result is and if the result is . For the second particle in each pair, if the measurement result is or and if the result is or .
- (4)
- Define for the test roundIf , Bob aborts the protocol.
- (5)
- Conditional on the event that the local test at Bob’s end has been successful, Bob proceeds to the subset and sends the photon A of the remaining entangled states in each pair to Alice. and represent the bits 0 and 1.
- (6)
- Alice declares which qubits are received successfully. The bits carried by the lost photons are discarded. For each successfully received qubit, Bob measures his corresponding qubits in the basis. Then, Alice chooses to measures her qubits either in the basis or in the basis randomly. If Alice’s measurement result is , she can obtain that the raw key bit at Bob’s end must be 1. If it is , the raw key bit must be 0. We also use POVMs and to describe Alice’s and Bob’s measurements, where and represent the basis choice, respectively. Taking signal loss and detection inefficiency into account, each measurement has three possible outcomes .
- (7)
- Then, they store the measurement results of remaining signal states as the raw key. They share the raw key , in which Bob knows all the bits while Alice only knows part of .
- (8)
- Alice and Bob perform classical post-processing. Assume an N-bit database is concerned, the created string should be of length (k is a security parameter). Bob first randomly announces a permutation mapping, then Alice announces a shift from randomly. After that, they shift the raw key by , then apply the permutation mapping on it and cut it into kN-bit substrings. These substrings are added bitwise to obtain the final key in order that Alice knows only roughly one bit in . If Alice does not know any bit of , the protocol is aborted.
- (9)
- Suppose Alice knows the j-th bit and wants the i-th item in the database, then she declares a shift . Bob encrypts his database with shifted by s, i.e., , and sends the encrypted database to Alice. Then, Alice recovers the wanted item by her known bit, i.e., .
4. Security Analysis
- (1)
- Devices are causally independent. This assumption implies that the devices are memoryless.
- (2)
- The adversary’s attacks are independent and identically distributed.
- (3)
- All the detectors at Bob’s end have a trusted loss.
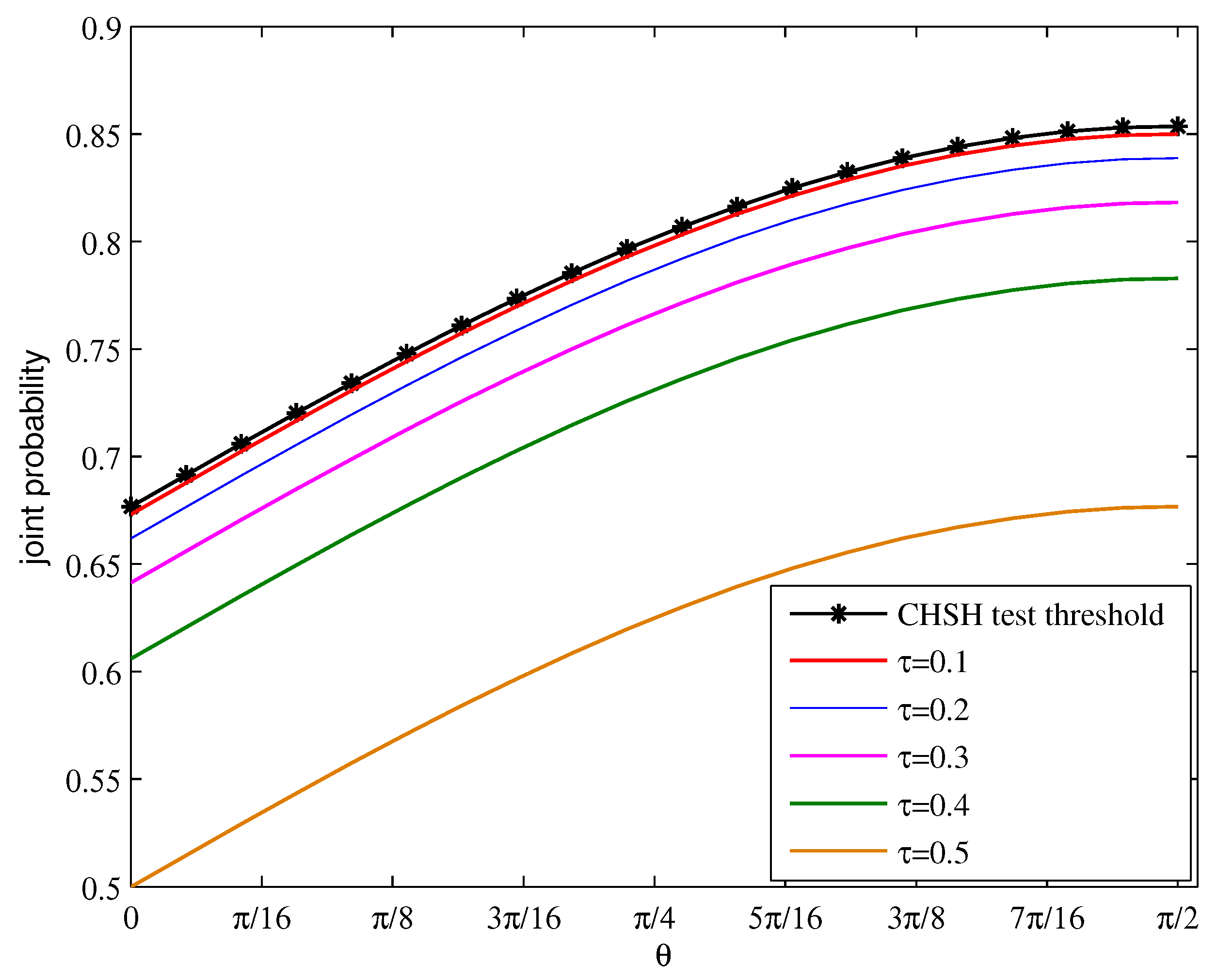
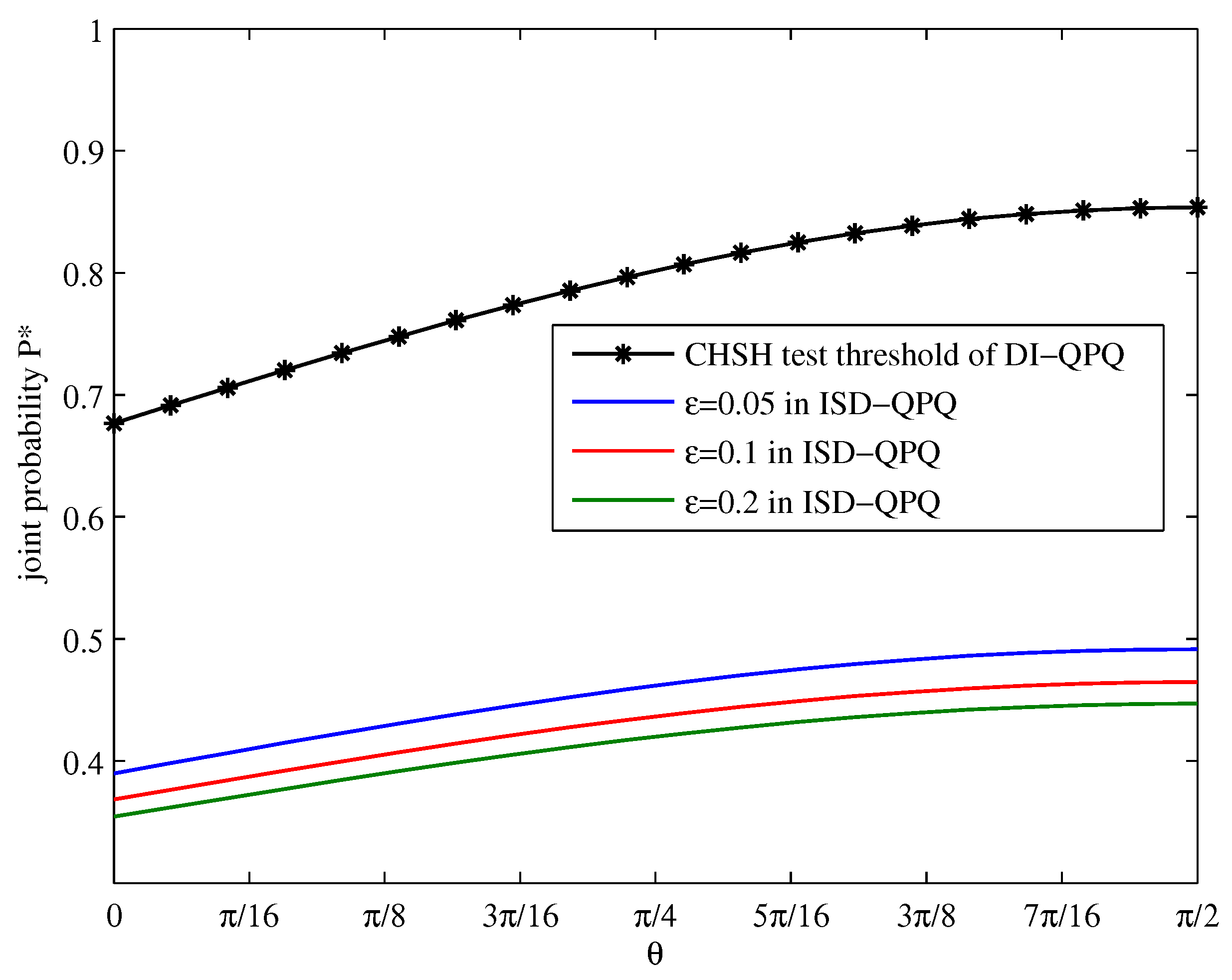
4.1. SDP Optimization Problem for Bounding the Joint Probability
4.2. Correctness
4.3. Database Security
4.4. User Privacy
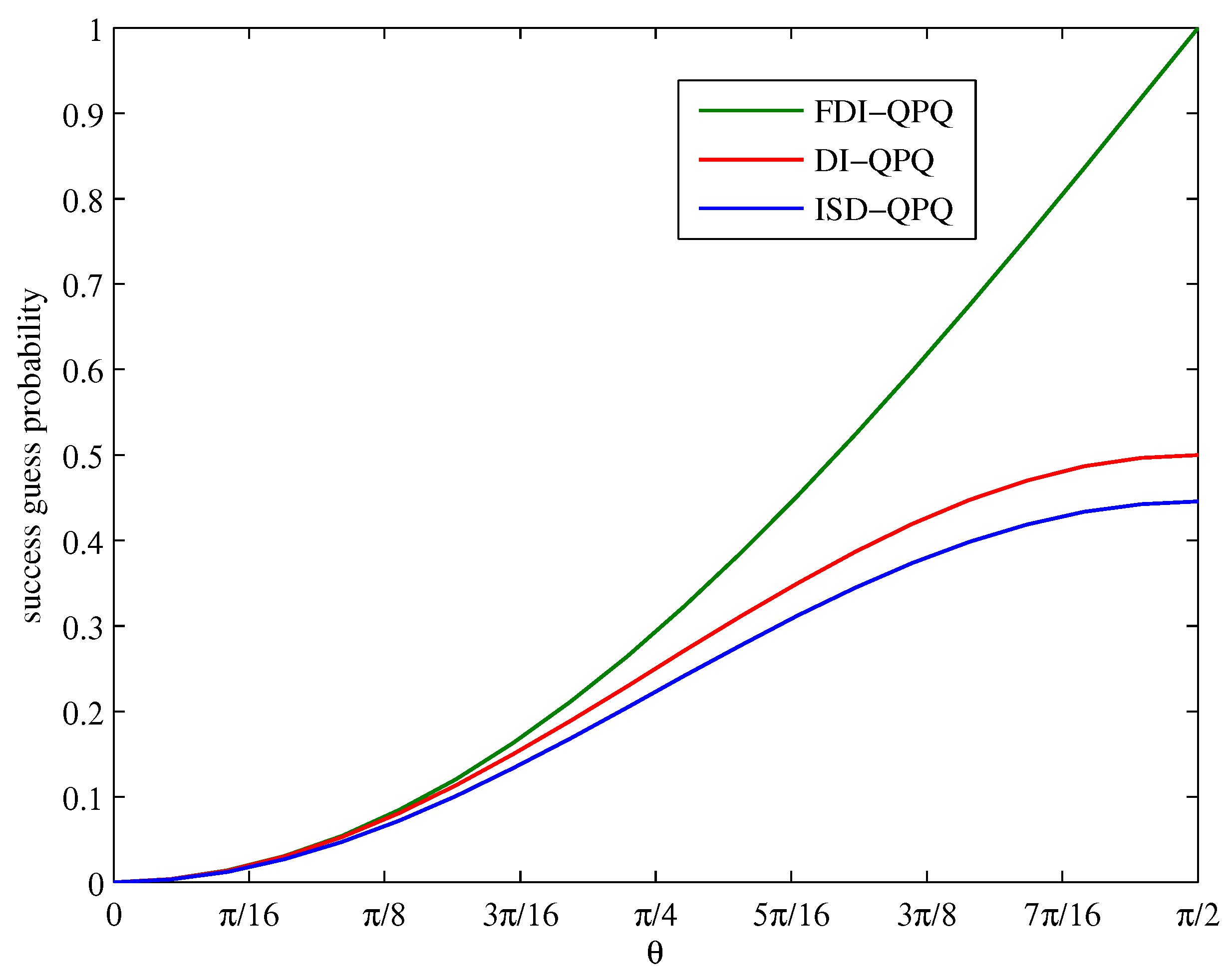
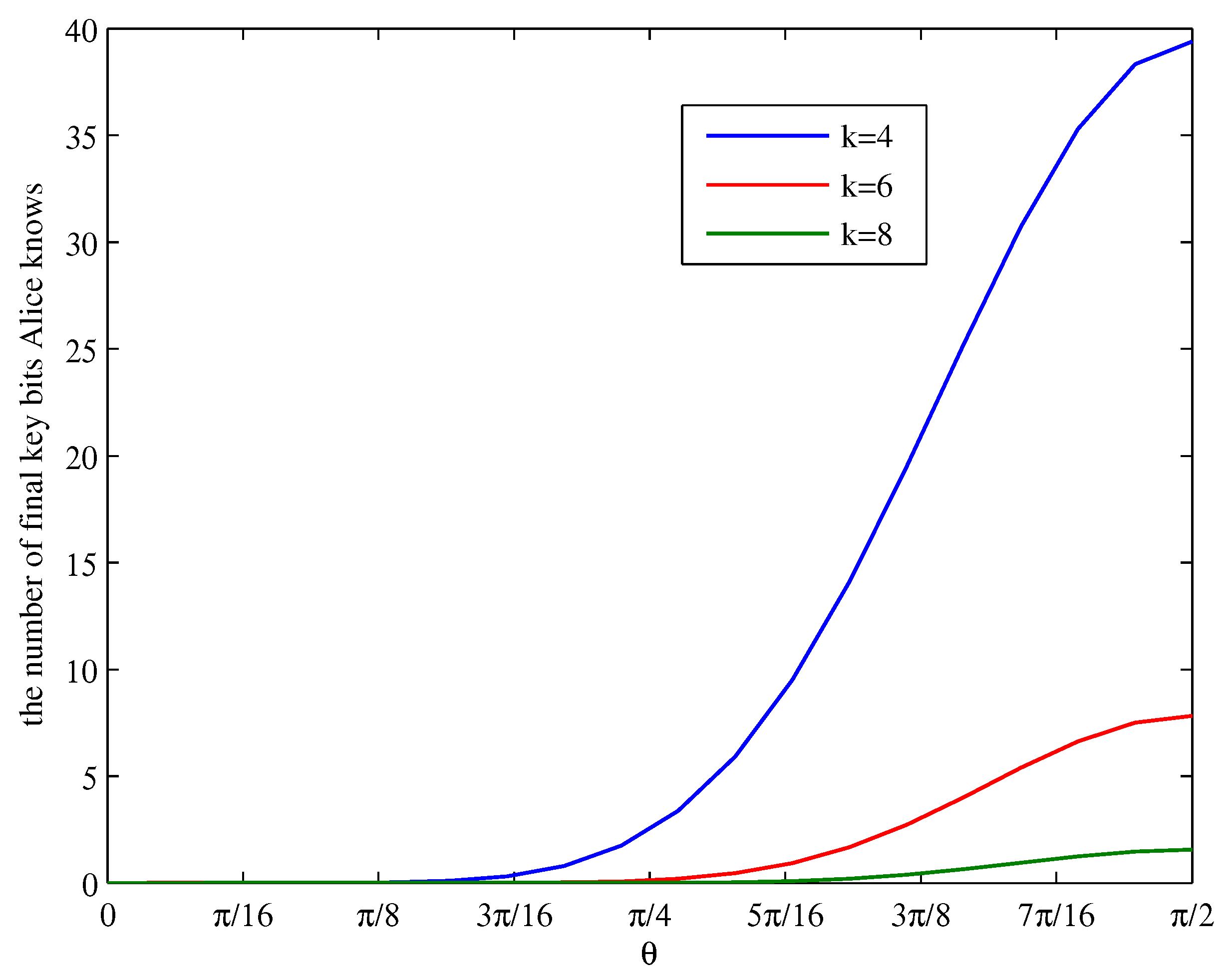
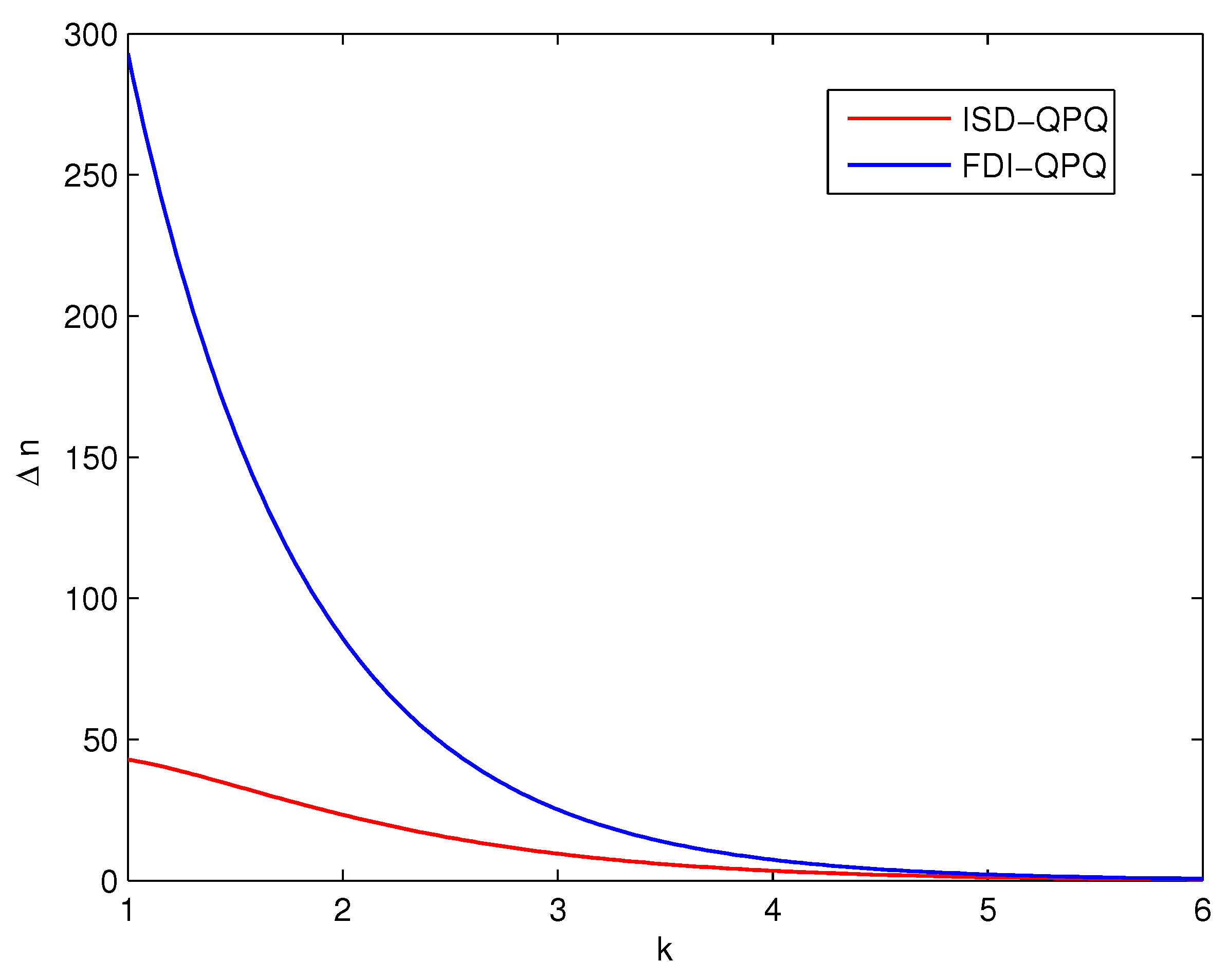
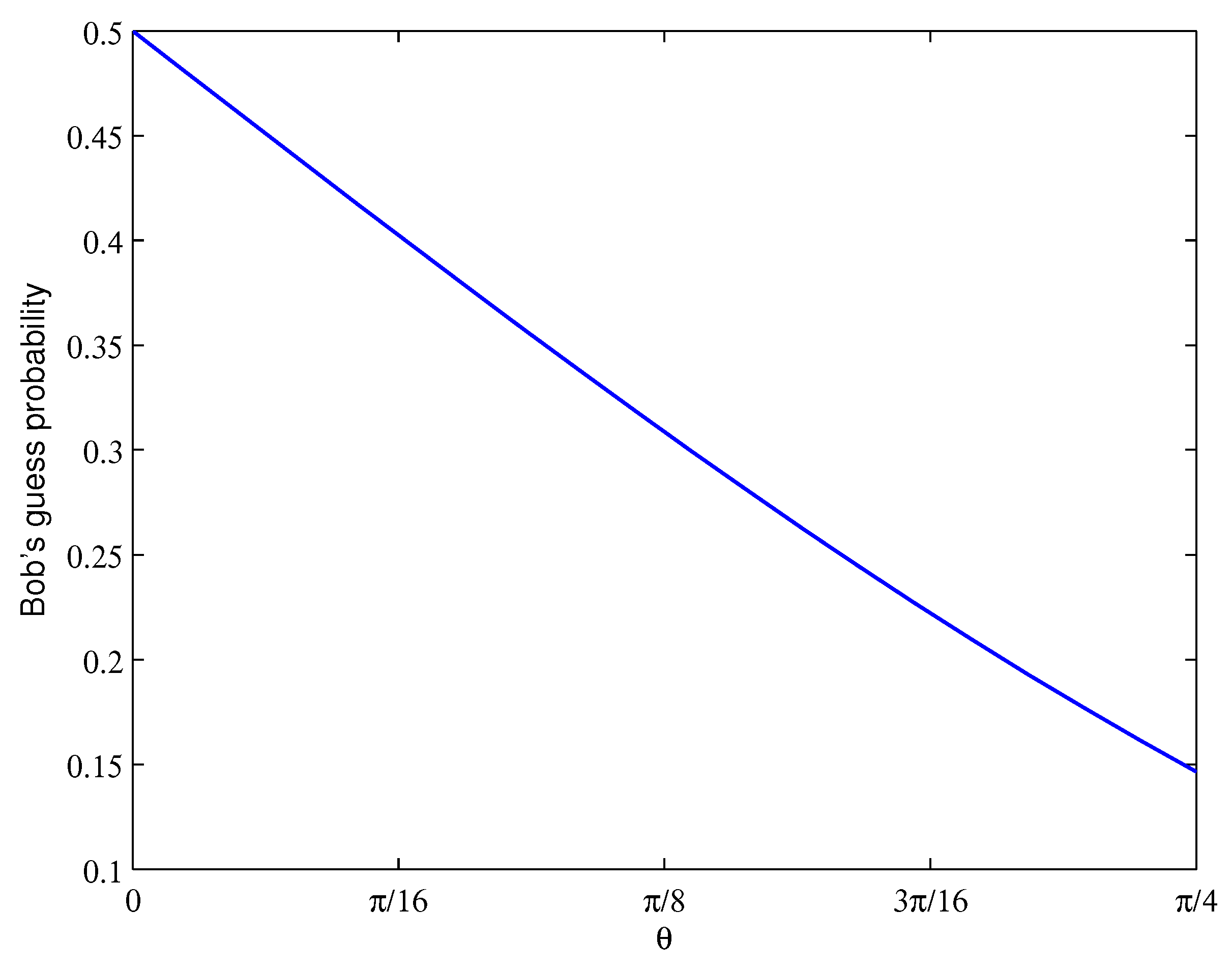
5. Simulation Results
6. Conclusions
Author Contributions
Funding
Data Availability Statement
Conflicts of Interest
Abbreviations
| PIR | Private information retrieval |
| SPIR | Symmetric private information retrieval |
| QKD | Quantum key distribution |
| PQ | Private query |
| QPQ | Quantum private query |
| DI | Device-independent |
| NPA | Navascués–Pironio–Acín |
| SDP | Semi-definite programming |
| LSA | Low-shift and addition |
| FDI-QPQ | Full DI certification quantum private query |
| ISD-QPQ | Quantum private query with imperfect sources and detectors |
| POVM | Positive operator value measurement |
| USD | Unambiguous state discrimination |
References
- Chor, B.; Kushilevitz, E.; Goldreich, O.; Sudan, M. Private Information Retrieval. J. ACM 1998, 45, 968–981. [Google Scholar] [CrossRef]
- Chor, B.; Goldreich, O.; Kushilevitz, E.; Sudan, M. Private information retrieval. In Proceedings of the 36th Annual Symposium on Foundations of Computer Science, Milwaukee, WI, USA, 23–25 October 1995; IEEE: New York, NY, USA, 1995; p. 41. [Google Scholar]
- Gertner, Y.; Ishai, Y.; Kushilevitz, E.; Malkin, T. Protecting Data Privacy in Private Information Retrieval Schemes. J. Comput. Syst. Sci. 2000, 60, 592–629. [Google Scholar] [CrossRef]
- Wang, S. Symmetric private information retrieval supported by quantum-secure e key-exchange network. Light. Sci. Appl. 2022, 11, 301. [Google Scholar] [CrossRef] [PubMed]
- Hayashi, M.; Song, S. Unified Approach to Secret Sharing and Symmetric Private Information Retrieval With Colluding Servers in Quantum Systems. IEEE Trans. Inf. Theory 2023, 69, 6537–6563. [Google Scholar] [CrossRef]
- Lo, H. Insecurity of quantum secure computations. Phys. Rev. A 1997, 56, 1154–1162. [Google Scholar] [CrossRef]
- Lipmaa, H. An Oblivious Transfer Protocol with Log-Squared Communication. In Proceedings of the International Conference on Information Security, Singapore, 20–23 September 2005; pp. 357–371. [Google Scholar]
- Chou, T.; Orlandi, C. The Simplest Protocol for Oblivious Transfer. In Proceedings of the International Conference on Cryptology and Information Security in Latin America, Guadalajara, Mexico, 23–26 August 2015; pp. 40–58. [Google Scholar]
- Kon, W.Y.; Lim, C.C.W. Provably Secure Symmetric Private Information Retrieval with Quantum Cryptography. Entropy 2021, 23, 54. [Google Scholar] [CrossRef]
- Gong, L.H.; Li, M.L.; Cao, H.; Wang, B. Novel semi-quantum private comparison protocol with Bell states. Laser Phys. Lett. 2024, 21, 055209. [Google Scholar] [CrossRef]
- Ostrovsky, R.; Iii, W.E.S. A Survey of Single-Database Private Information Retrieval: Techniques and Applications. Int. Workshop Public Key Cryptogr. 2007, 4450, 393–411. [Google Scholar]
- Giovannetti, V.; Lloyd, S.; Maccone, L. Quantum private queries. Phys. Rev. Lett. 2008, 100, 230502. [Google Scholar] [CrossRef]
- Olejnik, L. Secure quantum private information retrieval using phase-encoded queries. Phys. Rev. A 2011, 84, 3242–3244. [Google Scholar] [CrossRef]
- Giovannetti, V.; Lloyd, S.; Maccone, L. Quantum Private Queries: Security Analysis. IEEE Trans. Inf. Theory 2010, 56, 3465–3477. [Google Scholar] [CrossRef]
- Jakobi, M.; Simon, C.; Gisin, N.; Bancal, J.D.; Branciard, C.; Walenta, N.; Zbinden, H. Practical private database queries based on a quantum-key-distribution protocol. Phys. Rev. A 2011, 83, 022301. [Google Scholar] [CrossRef]
- Yin, H.L.; Chen, T.Y.; Yu, Z.W.; Liu, H.; You, L.X.; Zhou, Y.H.; Chen, S.J.; Mao, Y.; Huang, M.Q. Measurement-Device-Independent Quantum Key Distribution Over a 404km Optical Fiber. Phys. Rev. Lett. 2016, 117, 190501. [Google Scholar] [CrossRef]
- Lucamarini, M.; Yuan, Z.L.; Dynes, J.F.; Shields, A.J. Overcoming the rate–distance limit of quantum key distribution without quantum repeaters. Nature 2018, 557, 7705. [Google Scholar] [CrossRef]
- Wang, W.; Wang, R.; Hu, C.; Zapatero, V.; Qian, L.; Qi, B.; Curty, M.; Lo, H.K. Fully Passive Quantum Key Distribution. Phys. Rev. Lett. 2023, 130, 220801. [Google Scholar] [CrossRef]
- Makarov, V.; Abrikosov, A.; Chaiwongkhot, P.; Fedorov, A.K.; Huang, A.; Kiktenko, E.; Petrov, M.; Ponosova, A.; Ruzhitskaya, D.; Tayduganov, A. Preparing a commercial quantum key distribution system for certification against implementation loopholes. Phys. Rev. Appl. 2023, 22, 044076. [Google Scholar] [CrossRef]
- Zhou, L.; Lin, J.; Jing, Y.; Yuan, Z. Twin-field quantum key distribution without optical frequency dissemination. Nat. Commun. 2023, 14, 928. [Google Scholar] [CrossRef]
- Zhou, Y.; Yin, Z.Q.; Shan, Y.G.; Wang, Z.H.; Wang, S.; Chen, W.; Guo, G.C.; Han, Z.F. Phase-error-rate analysis for quantum key distribution with phase postselection. Phys. Rev. A 2024, 109, 022416. [Google Scholar] [CrossRef]
- Zeng, P.; Zhou, H.; Wu, W.; Ma, X. Mode-pairing quantum key distribution. Nat. Commun. 2022, 13, 3903. [Google Scholar] [CrossRef]
- Chen, Y.A.; Zhang, Q.; Chen, T.Y.; Cai, W.Q.; Liao, S.K.; Zhang, J.; Chen, K.; Yin, J.; Ren, J.G.; Chen, Z. An integrated space-to-ground quantum communication network over 4,600 kilometres. Nature 2021, 589, 214–219. [Google Scholar] [CrossRef]
- Zhou, S.; Xie, Q.M.; Zhou, N.R. Measurement-free mediated semi-quantum key distribution protocol based on single-particle states. Laser Phys. Lett. 2024, 21, 065207. [Google Scholar] [CrossRef]
- Gao, F.; Liu, B.; Huang, W.; Wen, Q.Y. Postprocessing of the oblivious key in quantum private query. IEEE J. Sel. Top. Quantum Electron. 2015, 21, 6600111. [Google Scholar] [CrossRef]
- Yang, Y.G.; Sun, S.J.; Xu, P.; Tiang, J. Flexible protocol for quantum private query based on B92 protocol. Quantum Inf. Process. 2014, 13, 805–813. [Google Scholar] [CrossRef]
- Wei, C.Y.; Wang, T.Y.; Gao, F. Practical quantum private query with better performance in resisting joint-measurement attack. Phys. Rev. A 2016, 93, 042318. [Google Scholar] [CrossRef]
- Wei, C.Y.; Cai, X.Q.; Wang, T.Y.; Qin, S.J.; Gao, F.; Wen, Q.Y. Error Tolerance Bound in QKD-Based Quantum Private Query. IEEE J. Sel. Areas Commun. 2020, 38, 517–527. [Google Scholar] [CrossRef]
- Gao, F.; Qin, S.J.; Huang, W.; Wen, Q.Y. Quantum private query: A new kind of practical quantum cryptographic protocol. Sci. China Phys. Mech. Astron. 2019, 62, 70301. [Google Scholar] [CrossRef]
- Yang, Y.G.; Yang, P.Z.; Xu, G.B.; Jiang, D.H.; Zhou, Y.H.; Shi, W.M.; Li, D. Error-Tolerant Measurement-Device-Independent Quantum Private Queries of Blocks. Int. J. Theor. Phys. 2024, 63, 1–13. [Google Scholar] [CrossRef]
- Basak, J. Multi-user semi-device independent quantum private query. Quantum Inf. Process. 2023, 22, 276. [Google Scholar] [CrossRef]
- Wei, C.Y.; Cai, X.Q.; Liu, B.; Wang, T.; Gao, F. A generic construction of quantum-oblivious-key-transfer-based private query with ideal database security and zero failure. IEEE Trans. Comput. 2018, 67, 2–8. [Google Scholar] [CrossRef]
- Liu, L.; Guo, F.Z.; Wen, Q.Y. Practical decoy-state quantum private queries against joint-measurement attack under weak coherent pulse sources. Quantum Inf. Process. 2021, 20, 392. [Google Scholar] [CrossRef]
- Liu, B.; Xia, S.; Xiao, D.; Huang, W.; Xu, B.; Li, Y. Decoy-state method for quantum-key-distribution-based quantum private query. Sci. China Phys. Mech. Astron. 2022, 65, 240312. [Google Scholar] [CrossRef]
- Maitra, A.; Paul, G.; Roy, S. Device-independent quantum private query. Phys. Rev. A 2017, 95, 042344. [Google Scholar] [CrossRef]
- Basak, J.; Chakraborty, K.; Maitra, A.; Maitra, S. Improved and Formal Proposal for Device Independent Quantum Private Query. J. Phys. A Math. Theor. 2024, 57, 085302. [Google Scholar] [CrossRef]
- Basak, J.; Chakraborty, K. Fully device independent quantum private query. Adv. Math. Commun. 2024, 19, 494–545. [Google Scholar] [CrossRef]
- Lim, C.C.W.; Portmann, C.; Tomamichel, M.; Renner, R.; Gisin, N. Device-Independent Quantum Key Distribution with Local Bell Test. Phys. Rev. X 2013, 3, 031006. [Google Scholar] [CrossRef]
- Navascués, M.; Pironio, S.; Acín, A. Bounding the set of Quantum Correlations. Phys. Rev. Lett. 2007, 98, 010401. [Google Scholar] [CrossRef]
- Liu, L.; Wang, Y.; Lavie, E.; Ricou, A.; Wang, C.; Guo, F.Z.; Lim, C.C.W. Practical quantum key distribution with non-phase-randomized coherent states Authors. Phys. Rev. Appl. 2019, 12, 024048. [Google Scholar] [CrossRef]
- Wang, Y.; Primaatmaja, I.W.; Lavie, E.; Varvitsiotis, A.; Lim, C.C.W. Characterising the correlations of prepare-and-measure quantum networks. NPJ Quantum Inf. 2019, 5, 17. [Google Scholar] [CrossRef]
- Gaidash, A.; Kozubov, A.; Miroshnichenko, G. Countermeasures for advanced unambiguous state discrimination attack on quantum key distribution protocol based on weak coherent states. Phys. Scr. 2019, 94, 12. [Google Scholar] [CrossRef]
- Löfberg, J. YALMIP: A Toolbox for Modeling and Optimization in MATLAB. In Proceedings of the IEEE International Conference on Robotics and Automation (IEEE Cat. No. 04CH37508), Taipei, Taiwan, 2–4 September 2004; pp. 284–289. [Google Scholar]
- Sturm, J.F. Using SeDuMi 1.02, A Matlab toolbox for optimization over symmetric cones. Optim. Methods Softw. 1999, 11, 625–653. [Google Scholar] [CrossRef]
- Inamori, H.; Lütkenhaus, N.; Mayers, D. Unconditional Security of Practical Quantum Key Distribution. Eur. Phys. J. D 2007, 41, 599. [Google Scholar] [CrossRef]
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Liu, L.; Du, Q.; Gao, X. Device Independent Quantum Private Queries Based on Quantum Key Distribution. Mathematics 2025, 13, 951. https://doi.org/10.3390/math13060951
Liu L, Du Q, Gao X. Device Independent Quantum Private Queries Based on Quantum Key Distribution. Mathematics. 2025; 13(6):951. https://doi.org/10.3390/math13060951
Chicago/Turabian StyleLiu, Li, Qingshan Du, and Xu Gao. 2025. "Device Independent Quantum Private Queries Based on Quantum Key Distribution" Mathematics 13, no. 6: 951. https://doi.org/10.3390/math13060951
APA StyleLiu, L., Du, Q., & Gao, X. (2025). Device Independent Quantum Private Queries Based on Quantum Key Distribution. Mathematics, 13(6), 951. https://doi.org/10.3390/math13060951






