Abstract
This study introduces a novel control framework based on the Takagi–Sugeno–Kang wavelet fuzzy neural network, integrating brain imitated network and cerebellar network. The proposed controller demonstrates high robustness, making it an excellent candidate for handling intricate nonlinear dynamics, effectively mapping input–output relationships and efficiently learning from data. To enhance its performance, the controller’s parameters are fine-tuned using Lyapunov stability theory. Compared to existing approaches, the proposed model exhibits superior learning capabilities and achieves outstanding performance metrics. Furthermore, the study applies this synchronization technique to the secure transmission of medical images. By encrypting a medical image into a chaotic trajectory before transmission, the system ensures data security. On the receiving end, the original image is successfully reconstructed using chaotic trajectory synchronization. Experimental results confirm the effectiveness and reliability of the proposed neural network model, as well as the encryption and decryption process. Specifically, the average_RMSE of the Takagi–Sugeno–Kang fuzzy wavelet brain cerebral controller (TFWBCC) method is 2.004 times smaller than the cerebellar model articulation controller (CMAC) method, 1.923 times smaller than the RCMAC method, 1.8829 times smaller than the TSKCMAC method, and 1.8153 times smaller than the brain emotional learning controller (BELC) method.
Keywords:
Takagi–Sugeno–Kang (TSK) fuzzy system; CMAC; BELC; 4D hyper-jerk hyper chaotic system; medical image MSC:
93A10; 93B05; 93D05; 93C10; 93C42; 93C95
1. Introduction
With the rapid spread of the Internet, e-health is becoming more widespread and accessible. This approach, also known as e-healthcare, uses digital and telecommunications technologies—such as computers, mobile devices and online networks—to improve medical services. E-healthcare is often integrated with traditional healthcare to provide patients and healthcare consumers with direct access to medical information [1,2,3]. However, when confidential images are subjected to cryptanalysis, sensitive data may be exposed, which could jeopardize individual privacy. Therefore, ensuring the security of medical image data has become an important priority [4,5,6].
To safeguard sensitive medical data, patient images must undergo anonymization through encryption. Accessing the original image requires the use of a precise decryption key [7,8,9]. Medical images possess unique characteristics, including strong pixel correlation, large data size, and significant redundancy [10,11,12]. Encryption techniques such as tent maps and bit-plane manipulation can be employed to secure these images. Consequently, ensuring robust security measures for both the transmission and storage of digital medical images is essential.
In recent years, researchers have extensively explored the synchronization of chaotic trajectories, a topic that has garnered significant scientific attention. Chaotic synchronization refers to the phenomenon where initially uncoordinated chaotic systems evolve into a state of organized behavior over time, offering valuable insights into the dynamics of complex systems. Several studies have examined the application of the 3D Lorenz chaotic system for secure data transmission [13,14] and investigated methods to synchronize chaotic systems for enhancing secure communication [15,16].
The interest in chaotic synchronization stems from the intricate and partially unexplored characteristics of chaotic behavior. This field holds critical relevance across various domains, including secure communications, control engineering, robotics, neuroscience, information processing, and biomedical applications. Despite its promising potential, chaotic systems present significant challenges due to their inherent unpredictability and highly nonlinear properties, making their control and synchronization a complex endeavor.
In modern times, model-free approaches have become increasingly popular for describing systems with unpredictable and random properties in both structure and parameters. A growing challenge in control theory is the need for precise management of complex systems. While traditional control techniques are effective in well-defined, stable, and linear environments, they struggle to cope with the complexity and uncertainty inherent in nonlinear chaotic systems [17,18]. Although adaptive controllers offer partial solutions, they remain difficult to implement in high-dimensional datasets or unstructured environments [19,20].
To address these challenges, extensive research has focused on fuzzy mathematical models, which emulate human-like reasoning [21,22,23,24]. Fuzzy systems are broadly categorized into two types: the Takagi–Sugeno–Kang (TSK) fuzzy systems and the Mamdani–Larsen fuzzy systems. The Mamdani–Larsen approach is known for its linguistic clarity, robustness, and rule-based structure, making it suitable for interpretability and smooth decision-making. On the other hand, TSK fuzzy systems excel in function approximation, offering simpler rule bases, superior nonlinear modeling, fast learning, flexibility, and effective parameterization for optimization techniques. These properties make TSK fuzzy models particularly suitable for handling intricate nonlinear relationships between input and output variables and for efficient training using data. A deep TSK fuzzy classifier with a hierarchical architecture and interpretable linguistic rules has been developed and tested through computational experiments and real-world applications [25]. Additionally, TSK fuzzy systems have been widely used in domains such as finance, medicine, and intelligent control systems [26,27].
Despite their advantages, fuzzy control in chaotic systems remains challenging due to issues such as inherent imprecision, the complexity of designing rule bases, difficulty in tuning membership functions, high implementation costs, and limited theoretical guarantees. Furthermore, fuzzy controllers may struggle to adapt to external disturbances and parameter uncertainties, leading to synchronization errors and increased system complexity.
In recent years, neural networks (NNs) have gained significant attention across multiple scientific and engineering disciplines for their capacity to handle complex nonlinear functions [28,29]. Neural networks are particularly powerful in modeling complex systems, function approximation, and integrating diverse data sources. Several biologically inspired neural architectures have been investigated, including the brain emotional learning controller (BELC) [30], the cerebellar model articulation controller (CMAC) [31,32], RNN [33,34], radial basis function neural network (RBFNN) preprocessors combined with CMAC [35,36], and fuzzy neural networks (FNN) [37,38].
Neural networks possess several advantages, including the ability to process imprecise information, integrate human expertise, perform parallel computations, and exhibit high fault tolerance, making them well-suited for controlling complex systems. However, controlling chaotic systems remains highly challenging due to their sensitivity to initial conditions. The design and training of neural network controllers require careful selection of network architecture, data, and learning algorithms. Additionally, neural networks demand vast amounts of training data, involve computationally intensive architectures, and may face challenges in generalizability—controllers optimized for one system may not necessarily perform well for another.
The proposed method integrates the strengths of wavelet features with Takagi–Sugeno–Kang fuzzy system (TSKFS) to create a TSK fuzzy wavelet brain cerebellar controller (TFWBCC). The effectiveness of the method is demonstrated by simulating 4D hyperchaotic synchronization. The main contributions of this work are as follows:
- (1)
- A novel wavelet function is incorporated into the BELC and CMAC channels and improves their ability to account for uncertainty in the membership function. This approach utilizes TSKFS for dual-channel CMAC and BELC and enables more flexible parameter updates, improved mapping capabilities, and precise approximation performance.
- (2)
- A TFWBCC is proposed to achieve synchronization in hyperchaotic systems.
- (3)
- The stability of the proposed system is rigorously verified using Lyapunov stability theory.
This paper is structured as follows: The first section provides an overview of the problem being addressed. In the second section, the proposed TFWBCC approach for achieving chaotic system synchronization is detailed, along with an explanation of how the Lyapunov method is utilized to update the controller parameters, Section 3 shows the proposed TFWBCC for 4D hyper master and slave chaotic synchronization and its application for medical secure image transmission. Section 4 presents the numerical simulation results for the 4D hyperchaotic in MATLAB software. Section 5 presents the medical image encryption using 4D hyper chaotic synchronization. Finally, Section 6 presents the conclusion of the paper. To make it easier to understand the abbreviations, you can see the list of abbreviations used in this article in Table 1.

Table 1.
List of abbreviations used in the article.
The primary differences between the proposed control strategy and conventional methods are presented in Table 2.

Table 2.
Key distinctions of the proposed control approach compared to existing methods.
2. Problem Formulation
Generic four-dimensional master systems, which can be represented as follows:
where and are, respectively, the states of the master system and nonlinear functions.
The typical structure of the slave system is outlined below:
where , , , and are, respectively, system states, unknown external disturbances, control inputs, and uncertainties of the system. If a proper control input , is structured to ensure that the slave’s states align with those of the master. It indicates that both systems operate in perfect harmony, thus, . Take into account a particular instance of a four-dimensional hyperchaotic master system, as described in reference [38]:
in which the exact values can be determined, allowing the slave system to be represented as follows:
where is the control input vector, is the unknown external disturbance, is the uncertainty of the system, and is the slave state. The tracking error can be calculated as follows:
The measurement of the tracking discrepancy is determined as follows:
Rewriting Equation (6) to the vector form as follows:
where , , .
Given the known values , an optimal controller can be determined as follows:
where represents the feedback gain matrix. Substituting Equation (8) into Equation (7) yields
when is adjusted to satisfy the Hurwitz stability condition, then . However, in real-world applications, the ideal controller described in Equation (8) cannot be fully realized due to the unknown nature of the lumped uncertainty, . To address this challenge, this research introduces the TFWBCC model, aiming to ensure effective synchronization of four-dimensional hyperchaotic systems.
3. TFWBCC Model
This section introduces a novel control framework based on the TSKFS, combining wavelet BELC and wavelet CMAC. Figure 1 presents the flowchart for synchronizing 4D chaotic systems using the proposed TFWBCC, while Figure 2 outlines the TFWBCC framework, comprising two main components: the TSK wavelet BELC (TSKWBC) and the TSK wavelet cerebellar controller (TFWCC). Each of these branches operates based on specific TSK fuzzy inference rules, outlined as follows:
where is the fuzzy set for the i-th input, j-th layer, and k-th block; is the TSK-type output weight of TFWBC. is the dimension of the input, is the layer dimension, is the number of blocks for each layer; is the number of fuzzy rules.
where is the fuzzy set for the i-th input, j-th layer, and k-th block; is the TSK-type output weight of TFWCC.
3.1. Input Storage
is simultaneously an input vector for both TFWBC and TFWCC branches.
3.2. TFWBC Branch
- (a)
- Storage area for relational data: This storage contains some blocks K; each block is expressed by a wavelet function and it is determined as follows:where and are, respectively, the mean and variance, then:Let
- (b)
- Weight Storage (): The weight matrix of TFWBC is defined as follows:whereand is o-th output weight value of TFWBC; with represents the dimensionality of the output in the TFWBC system.Setwhere .SetThen
- (c)
- Sub-output Storage ()
3.3. TFWCC Branch
is Wavelet function
where and are, respectively, the mean and variance of TFWCC.
- (a)
- Receptive-field Storage (): Each block value is the product of the equivalent block of the recurrent associative memory storage, R, which is determined by the following:Let
- (b)
- Weight Memory Storage :Letwhere .is the o-th output weight value of TFWCC, and is the output dimension of TFWCC.Setwhere .SetThen
3.4. Output Storage (u)
The output of the proposed TFWBCC is defined as follows:
Then
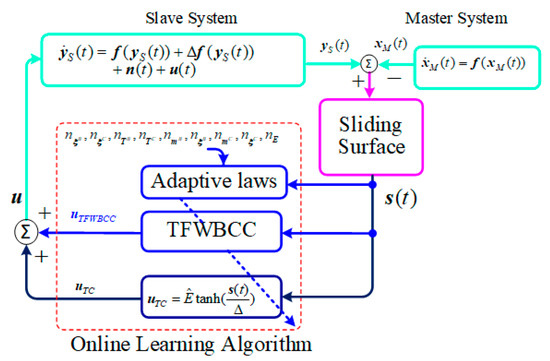
Figure 1.
The diagram for chaotic synchronization using the proposed TFWBCC.
Figure 1.
The diagram for chaotic synchronization using the proposed TFWBCC.
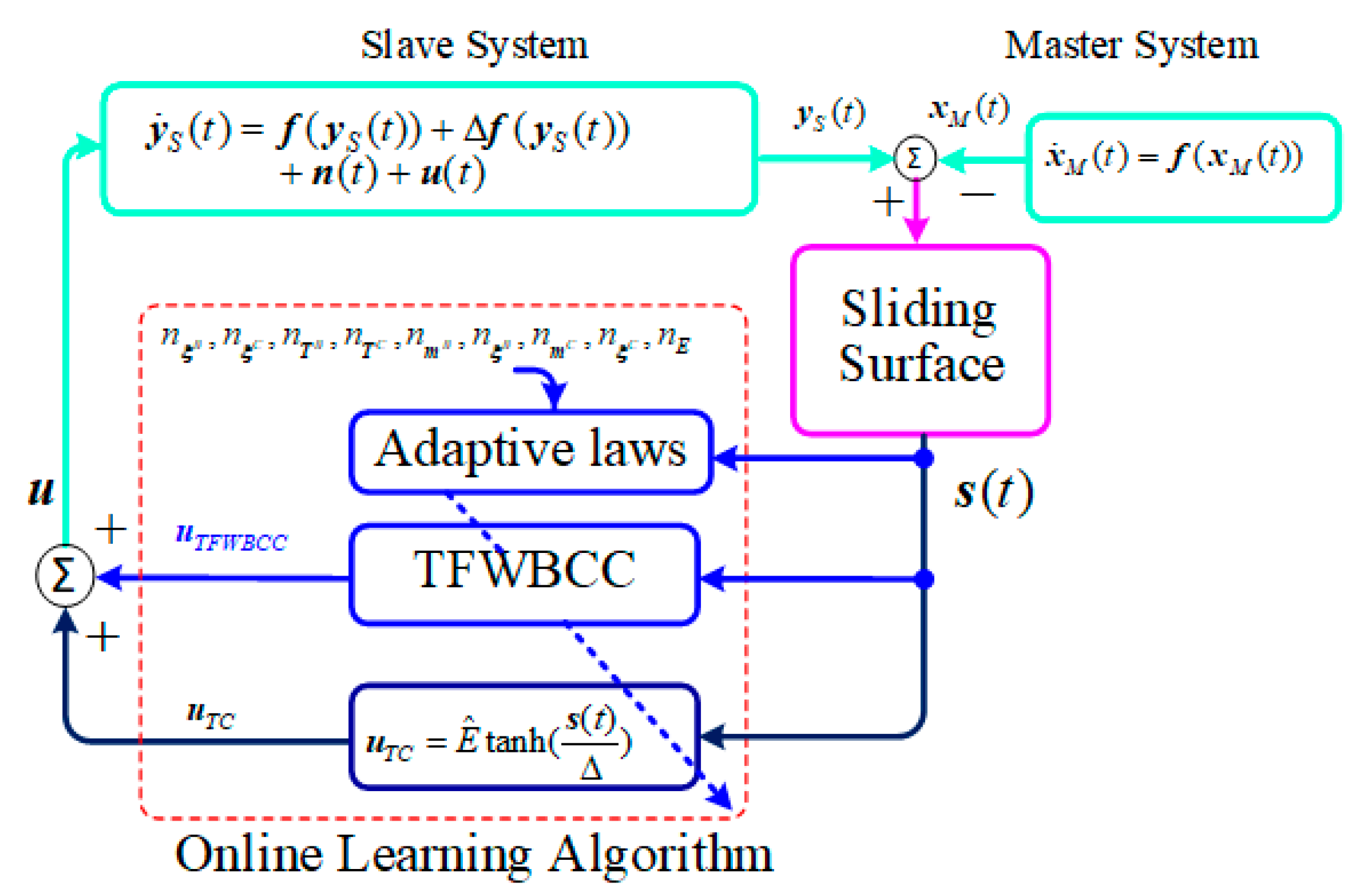
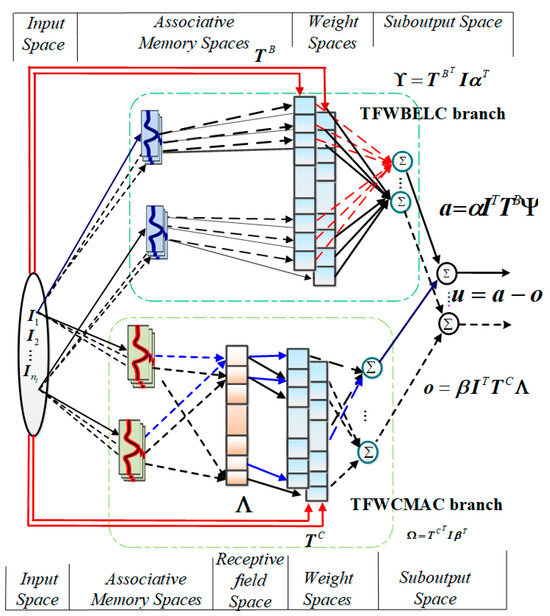
Figure 2.
The architecture of the proposed TFWBCC.
Figure 2.
The architecture of the proposed TFWBCC.
There always exists an approximate error between the proposed TFWBCC and the ideal controller. Thus,
where is a minimum error vector; are the optimal parameter matrices and vectors of . However, the ideal controller may be unattainable. Therefore, a compensation is used to calculate with the ideal controller.
where is the estimated TFWBCC, is the robust compensator using to estimate the approximate error . are the estimate values of the optimal parameter matrices and vectors , respectively. From Equations (29) and (30), the approximate error can be calculated as follows:
where , , , , .
The extension of in the Taylor series can be achieved as follows [39]:
where , , , ; are, respectively, higher-order term vectors of . , , , , are defined by:
From Equation (33), we can attain:
Substituting Equation (34) to Equation (31), yields:
where
It is supposed that is bounded by , and , where represents a constant with a positive value.
Theorem 1.
Consider a four-dimensional hyperchaotic system described by Equations (1) and (2). The introduced TFWBCC framework is formulated in Equation (28), incorporating updated parameters from Equations (36)–(43). Additionally, the robust compensator is specified in Equation (44) and governed by the adaptive update law in Equation (45). Under these conditions, the stability of the robust system is assured.
Proof.
Set sliding mode control function as follows:
where . The differential equation of is taken as follows:
Equation (46) is calculated via Equation (35) as follows:
Choosing the Lyapunov function as follows:
Then,
□
Remark 1.
are constants, therefore, , , , , , , , , and
Remark 2.
Remark 3.
For 4D hyper chaotic, .
Via the hyperbolic tangent compensator in Equation (43) and the update parameters in Equations (36)–(42) and Equation (44), becomes:
for > 0, attains
where is a positive coefficient that satisfies . Using inequality (50), (49) can be rewritten as follows:
where and are positive constants given by the following:
Meanwhile and the solution of Equation (52) satisfies:
where is the initial value of , then E is bound [39,40]. From Equation (54),
So
which implies , such that for all , the tracking error system satisfies:
Here, represents a positive constant. A small value is selected for , ensuring that the finite time remains extended, which results in accurate error tracking. Consequently, the stability of the suggested system is assured [39,40].
4. Synchronization of a 4D Hyper Chaotic System [38]
This part of the study evaluates the performance of the proposed control approach by conducting extensive computational experiments in MATLAB/Simulink R2022b. The specific parameter values for the four-dimensional hyperchaotic model can be found in Table 3.

Table 3.
The parameter values of 4D master–slave hyper chaotic system.
The function rand(.) generates a random value within the interval [0, 1]. For the TFWBCC control framework, the chosen parameter settings are specifically tailored to its operation. A detailed overview of these parameters is provided in Table 4.

Table 4.
The parameter values of the proposed TFWBCC.
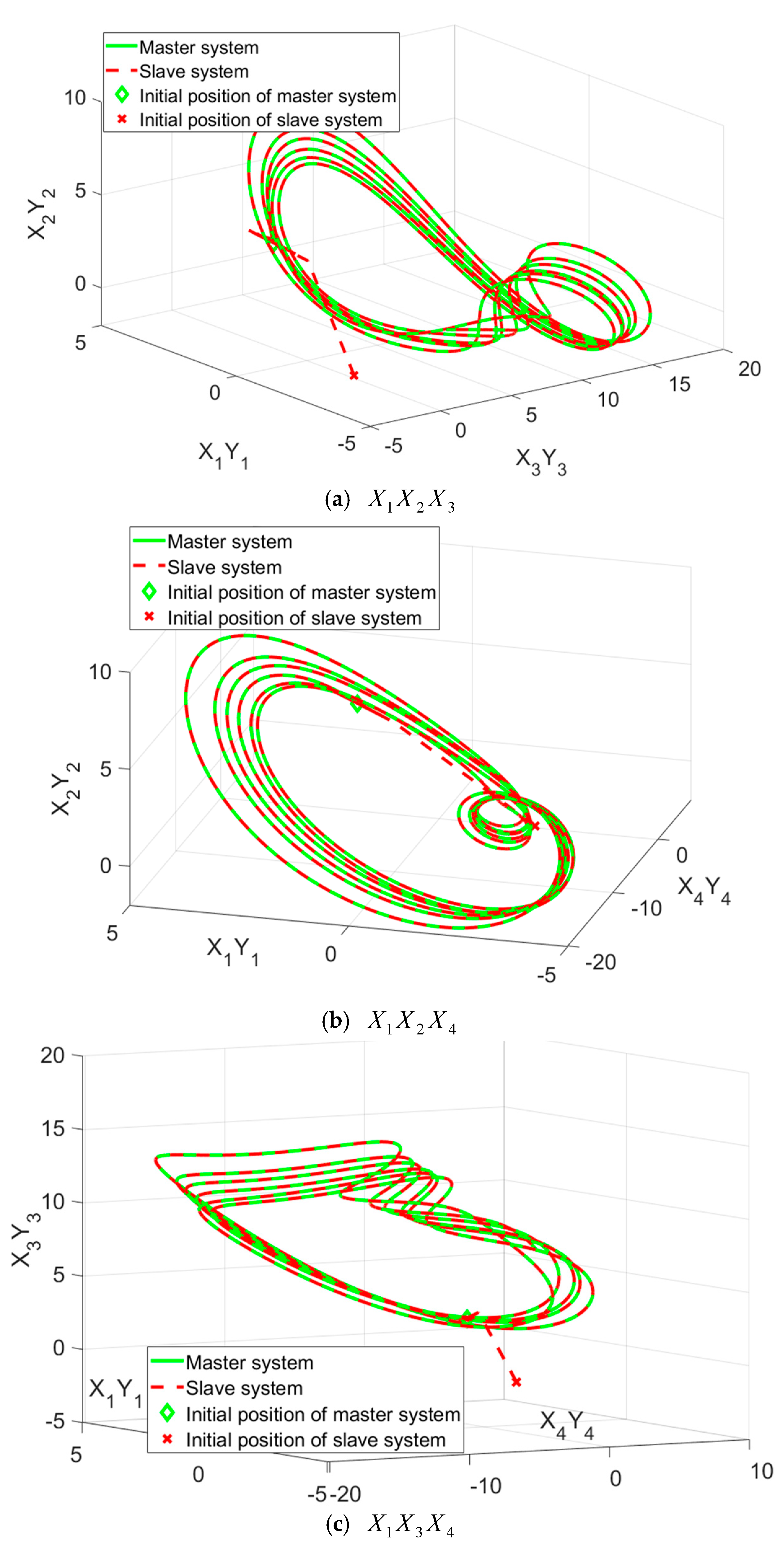
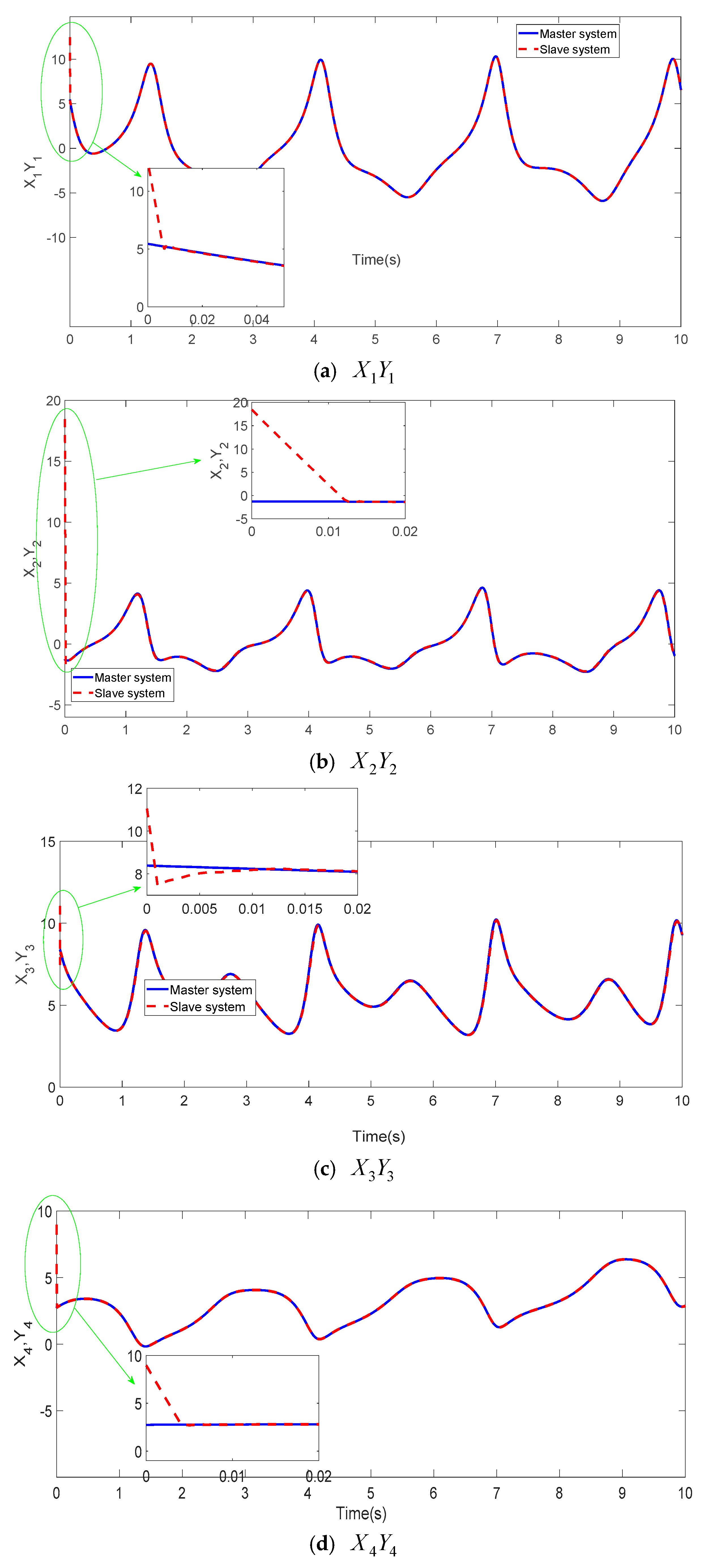
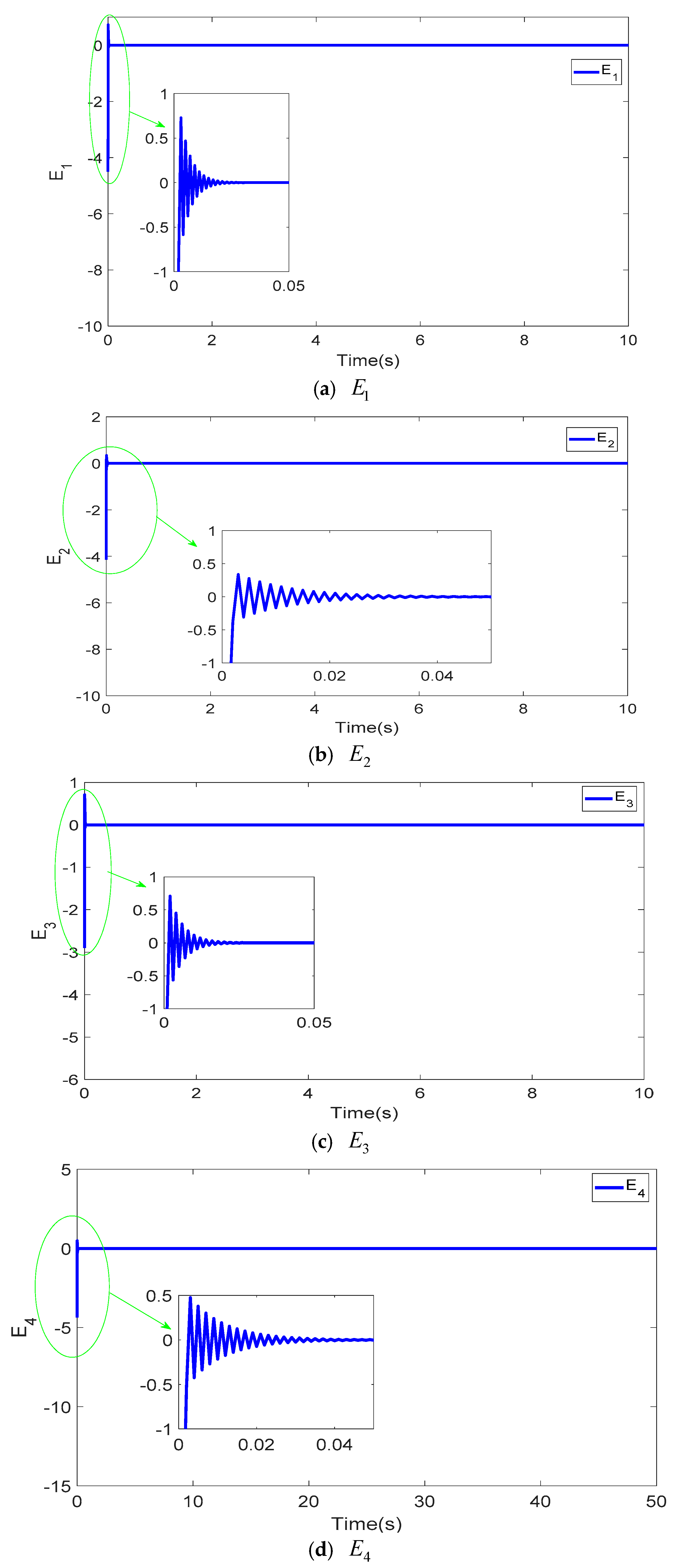
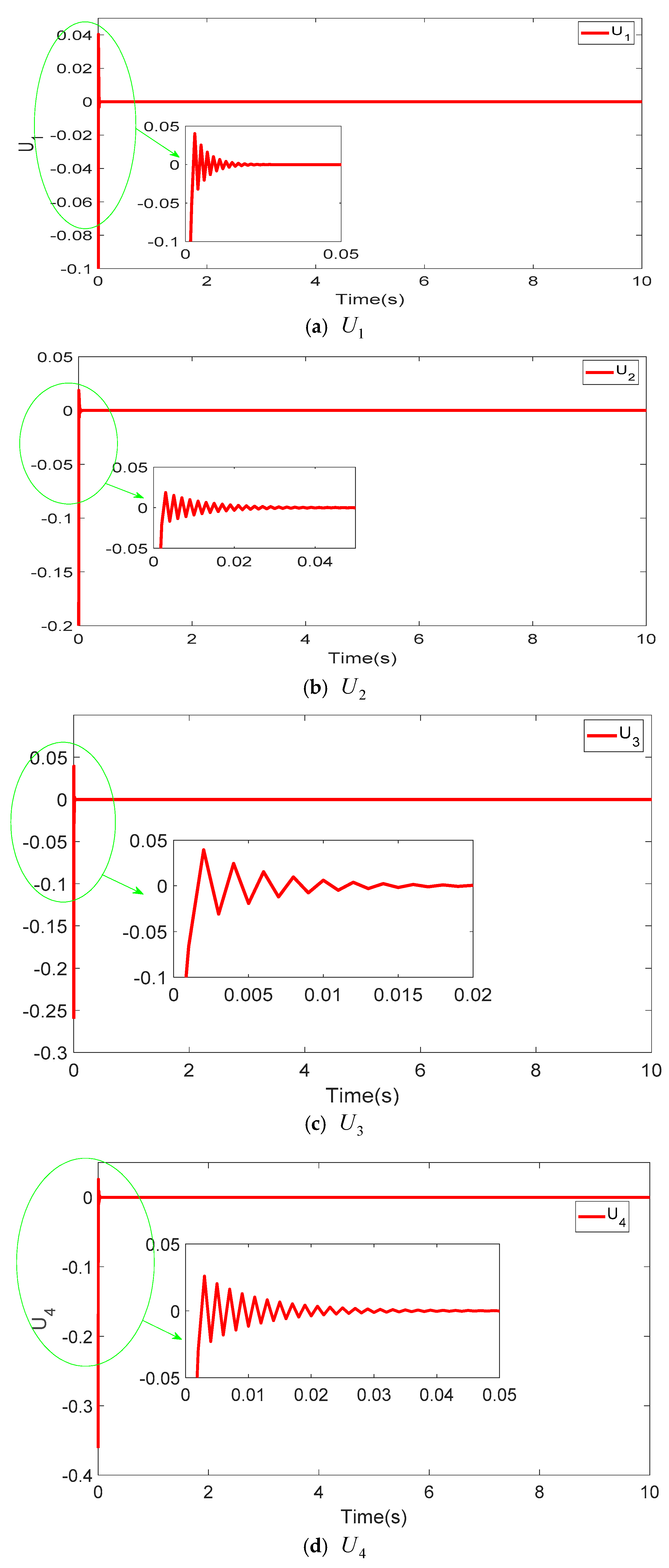
Figure 3 showcases the projection views of the synchronized states in the four-dimensional hyper-chaotic system using the TFWBCC approach. In Figure 4, the comparative analysis of state trajectories between the master and slave systems under the proposed TFWBCC methodology is illustrated. Figure 5 highlights the tracking error evolution, while Figure 6 visualizes the applied control inputs. The simulation results confirm that the proposed strategy successfully achieves synchronization with minimal tracking deviations.
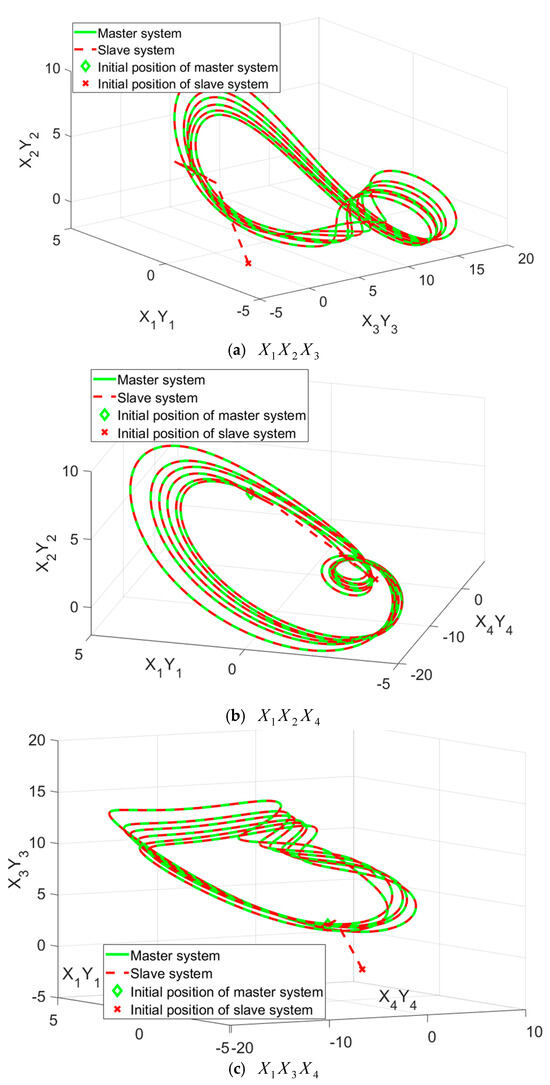
Figure 3.
Visualization of a four-dimensional chaotic system in three-dimensional space.
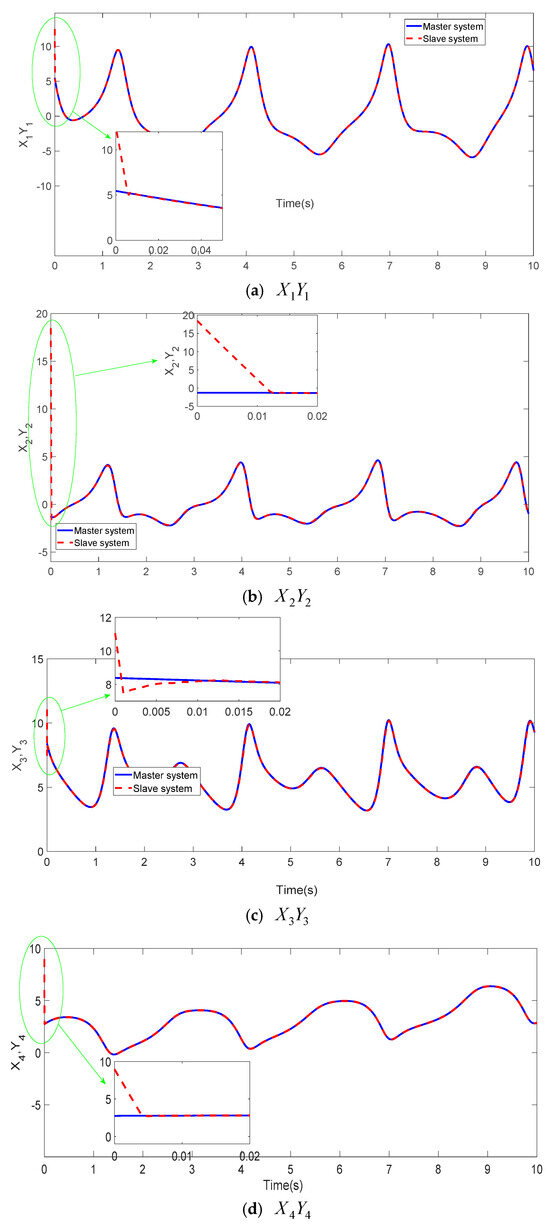
Figure 4.
Utilizing TFWBCC for monitoring the path of each dimension in a four-dimensional chaotic framework.
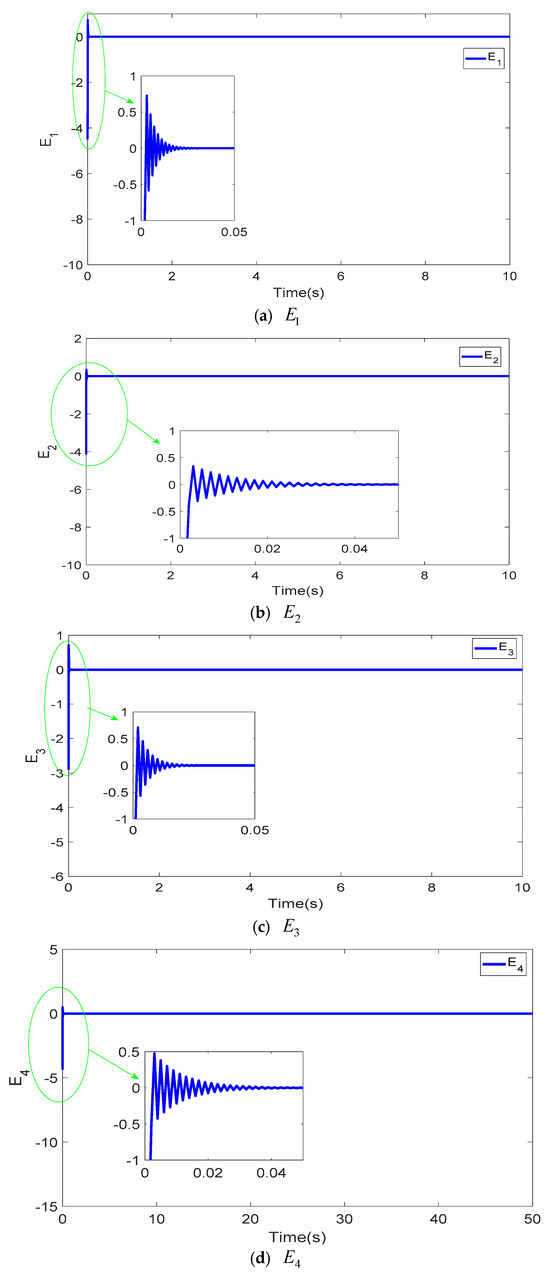
Figure 5.
Application of TFWBCC to analyze the deviance signals across all dimensions in a four-dimensional chaotic model.
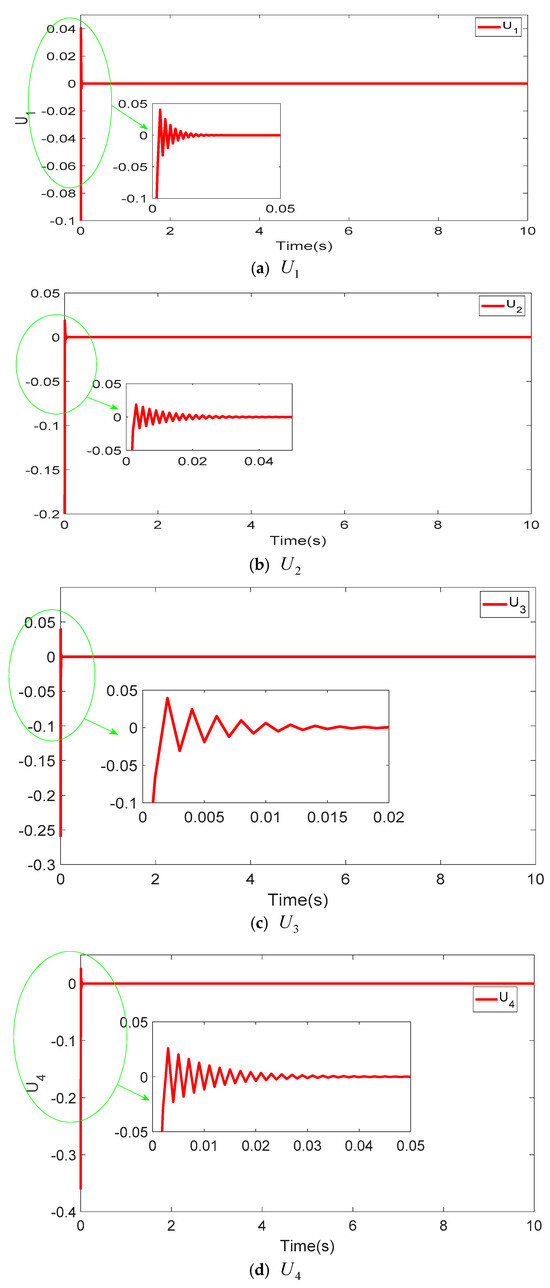
Figure 6.
Employing TFWBCC to regulate the command signals for every dimension in a four-dimensional chaotic system.
Notably, the TFWBCC method significantly reduces the average RMSE, attaining the lowest error value among all compared techniques (see Table 5). However, due to its complex structure, the computational cost is higher. This trade-off is reasonable, as improved synchronization accuracy generally comes at the expense of increased processing demands. Specifically, the average RMSE of TFWBCC is reduced by a factor of 2.004 compared to the CMAC [32] method, 1.923 times compared to RCMAC [35], 1.8829 times compared to TSKCMAC [13], and 1.8153 times compared to BELC [13]. Additionally, the computation time of the TFWBCC approach is 5.6923 times lower than that of CMAC [32], 5.2857 times lower than RCMAC [35], and 4.3529 times lower than BELC [13].

Table 5.
Evaluating the RMSE performance of TFWBCC against alternative approaches.
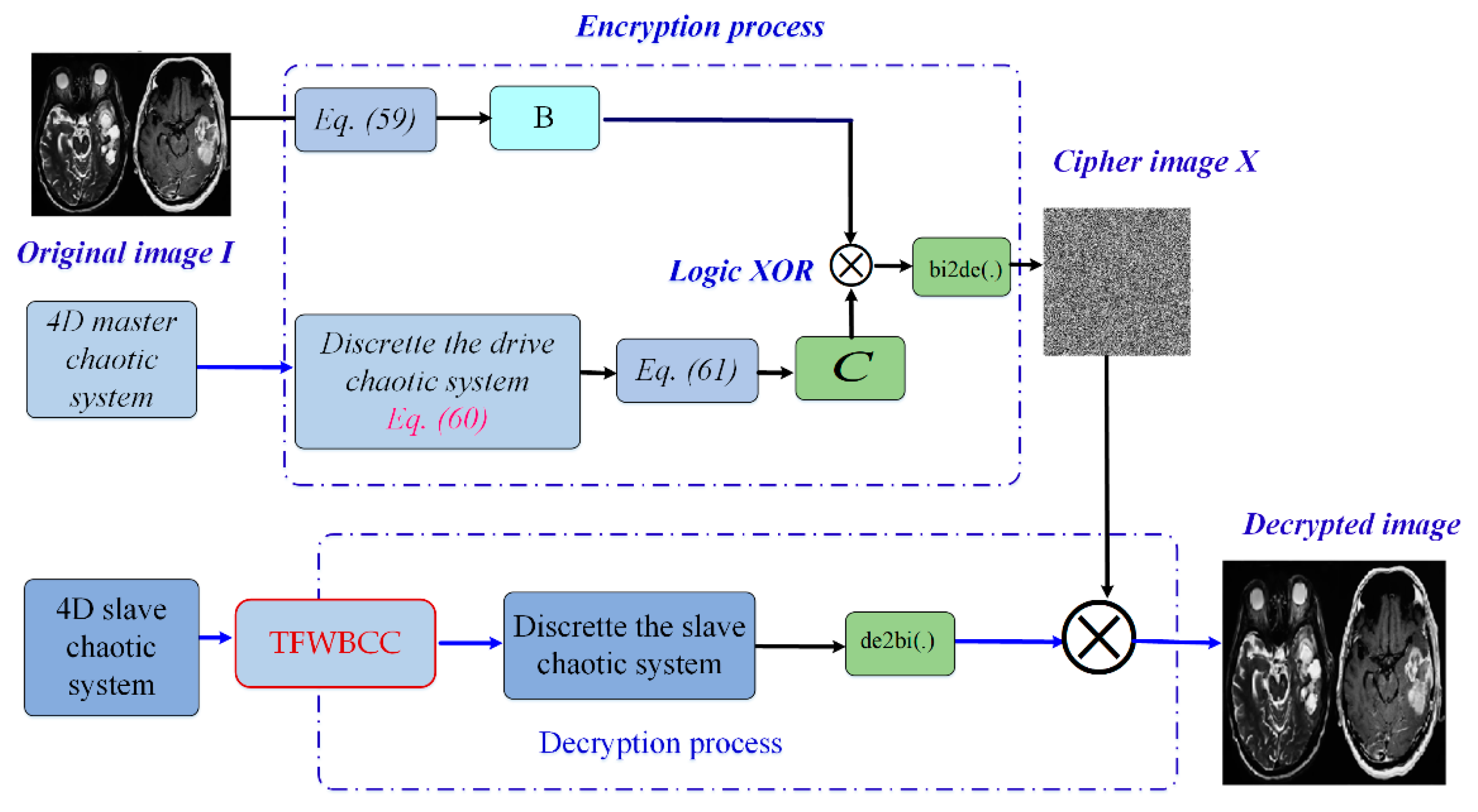
5. The Application of 4D Master–Slave Chaotic Synchronization for Medical Image Encryption
The following outlines the image security algorithm:
Step 1: The original medical image undergoes a sorting process based on a dual-number scheme [13,41]
where m and n are the length size and width size of the original image, respectively.
Step 2: Synchronize the master and the slave system.
Step 3: After the synchronization, discrete the master system of the chaotic 4D system
where j = 1, 2, … p × q represents the index of the j-th iteration within the chaotic system’s progression.
Step 4: The initial step involves thoroughly preprocessing the decimal value as follows:
where round(x) approximates x to the nearest whole number, mod(x, y) computes the remainder when x is divided by y, abs(x) determines the absolute magnitude of x, and floor(x) rounds x down to the nearest integer that is less than or equal to x.
Step 5: The process of image encryption is integrated with the primary chaotic system through the application of the XOR logical operation, as described below
here, de2bi(.) transforms a decimal number into its binary equivalent, while ⊕ represents the logical XOR operation.
Step 6: Convert the binary representation of G into decimal form, then reorganize to generate the encrypted image.
Step 7: Decryption Procedure.
The decryption method reverses the encryption steps, with the key difference being that the master chaotic time series is substituted by the corresponding slave chaotic time series. The structure of the medical image encryption using master–slave chaotic synchronization is presented in Figure 7.
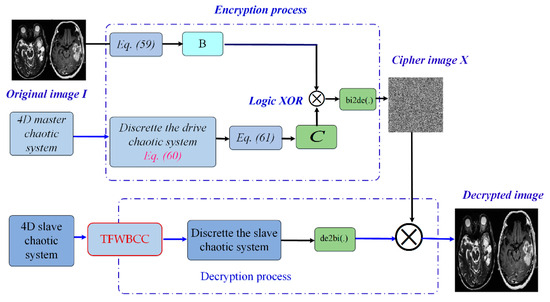
Figure 7.
The structure of the medical image encryption using 4D master–slave chaotic synchronization.
Some statistical analyses are performed to validate the proposed algorithm, such as histogram analysis and entropy analysis and NIST-SP800-22 test.
5.1. Histogram Examination
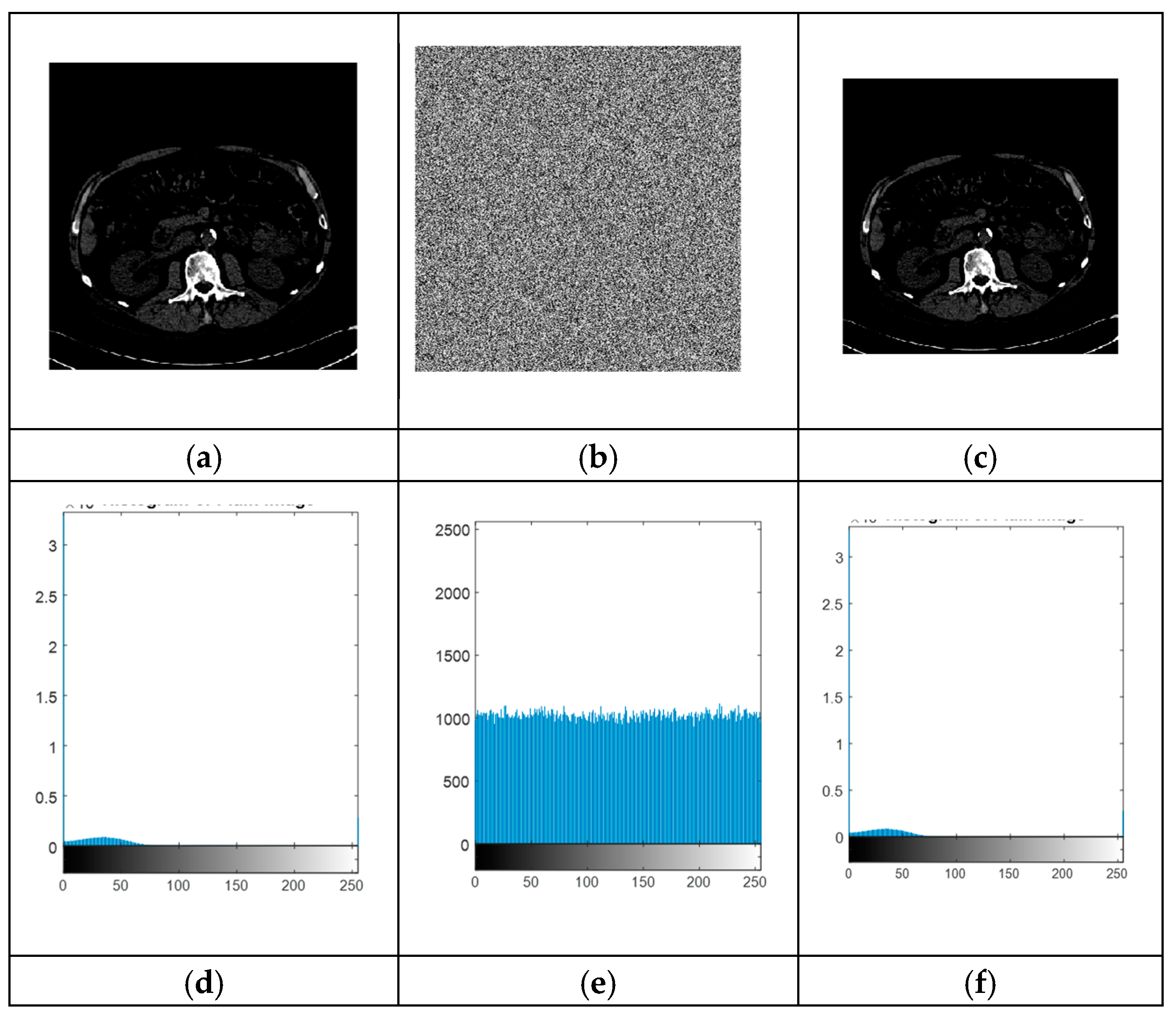
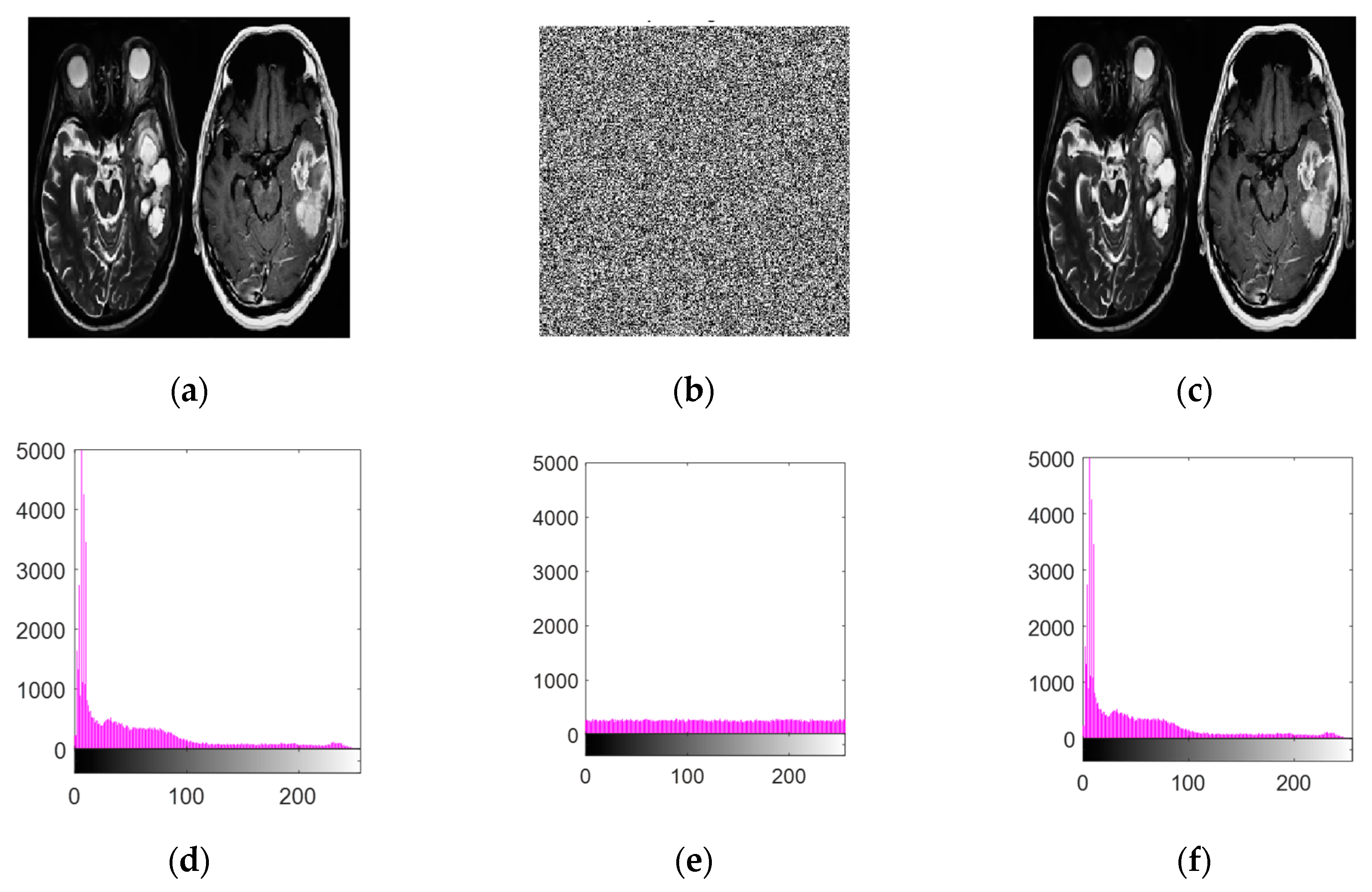
A histogram represents the pixel distribution within an image. To ensure security, the encrypted image must exhibit a distinct statistical distribution compared to the original plain image (refer to Figure 8 and Figure 9).
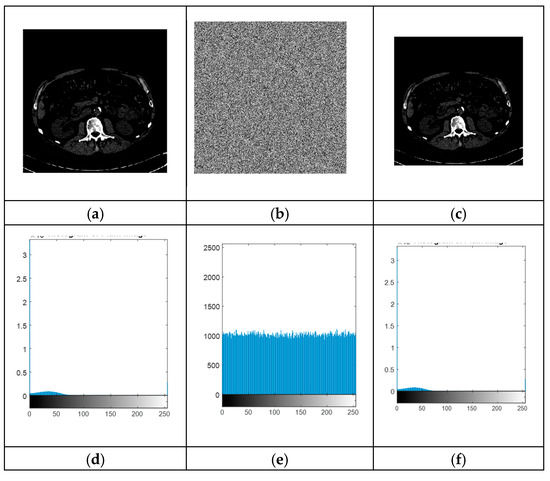
Figure 8.
(a) The initial brain image, (b) its encrypted counterpart, (c) the decrypted version after restoration, (d) the pixel intensity distribution of the original image, (e) the histogram analysis of the encrypted image, and (f) the histogram corresponding to the decrypted image.
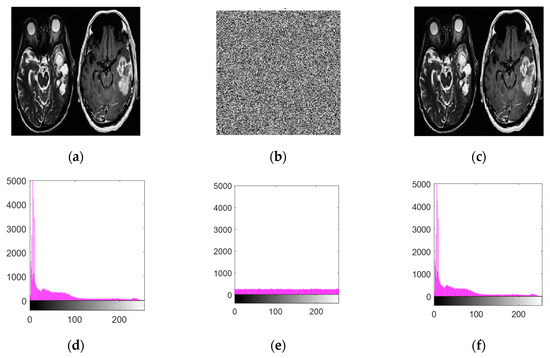
Figure 9.
(a) Unaltered brain scan, (b) its encrypted transformation, (c) the restored image post-decryption, (d) intensity distribution analysis of the original image, (e) histogram visualization of the encrypted version, and (f) histogram representation of the decrypted image.
5.2. Entropy
Entropy quantifies the dispersion of grayscale values within an image. A uniform distribution results in a higher entropy value, reaching a theoretical maximum of 8. The entropy calculation is defined as follows:
where 2N represents the total number of states in the information source, while denotes the probability of occurrence for the symbol . An ideally random image, R, exhibits a uniform pixel intensity distribution within the range [0, 255], implying that the probability is equal to 1/2561/2561/256 for every j within [0, 255].
The entropy of the original image and the scrambled image is described in Table 6. The different values between the original and the brain show that our method works well. Table 6 shows the entropy of the scrambled images of our method compared to other methods. It can be seen that our method achieves a value close to 8, namely 7.9988 for the scrambled image lung and 7.9967 for the scrambled image ruptured brain. Our method gives the highest value among all methods. This shows that the content of the image is secure when there is an attack on the image information.

Table 6.
Entropy of the cipher image.
5.3. NIST SP800-22 Test
Referring to [42], the randomness of output sequences is evaluated using the National Institute of Standards and Technology (NIST) SP800-22 test suite. This standard includes 15 distinct subtests, each producing a p-value. To be considered random, the resulting p-value for each subtest must lie between 0.01 and 1. Table 7 presents the assessment results for a 100-bit sample derived from 262,144 (512 × 512) bits of the encrypted “Brain Image”. The findings indicate that all p-values from the 15 subtests fall within the permissible range of 0–1, demonstrating that the encrypted image’s binary sequences successfully meet the randomness criteria. Consequently, the encryption effectively ensures pixel-level randomness.

Table 7.
Analysis results of the NIST evaluation for the scrambled brain image.
5.4. Cropping Attack Analysis
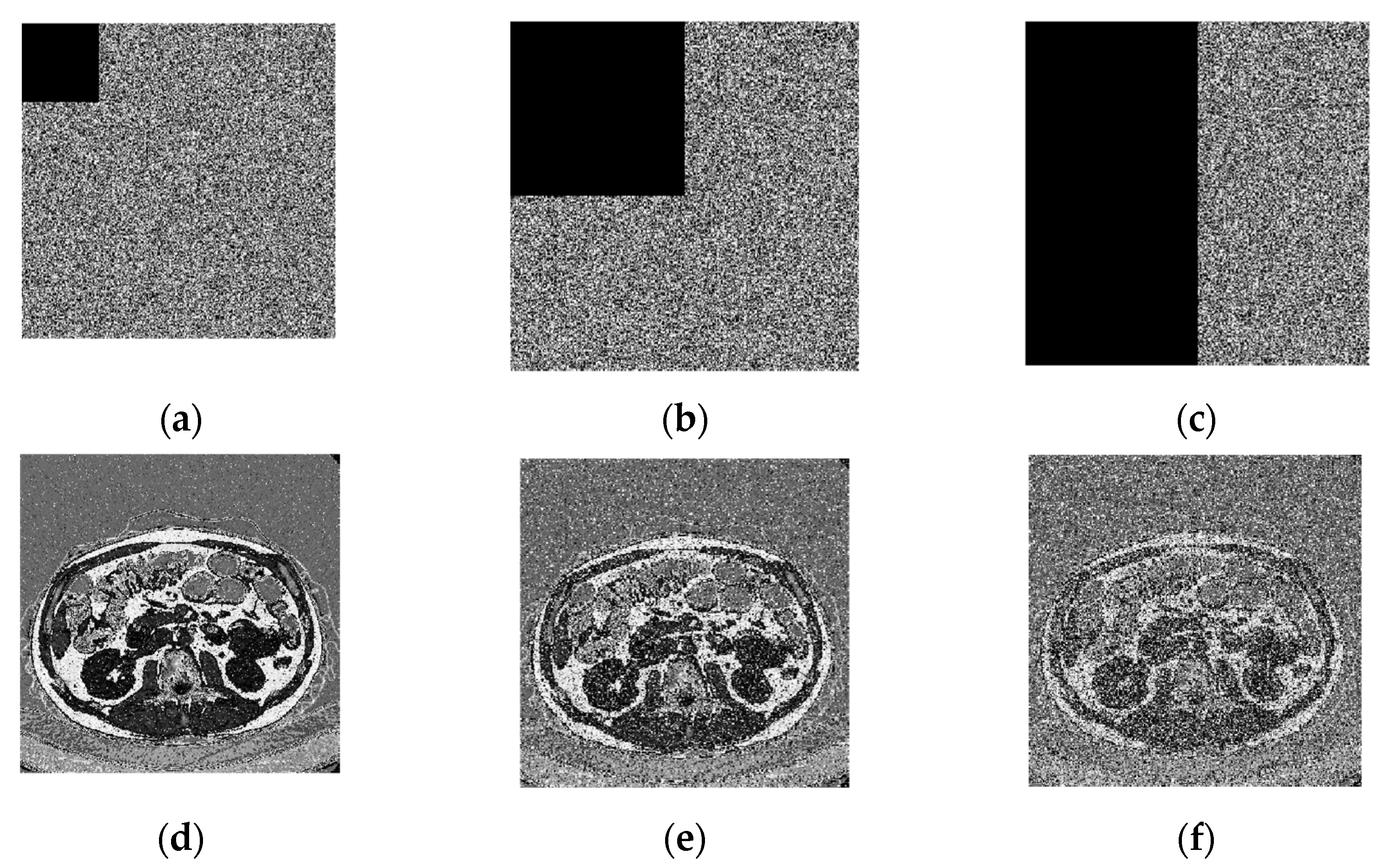
Our approach effectively handles data loss caused by cropping attacks. Figure 10 a,c,e displays scrambled images with varying levels of data removal—specifically, 1/16, 1/4, and 1/2 of the original content. Correspondingly, Figure 10b,d,f showcase the reconstructed images after decryption. The results indicate that our technique successfully recovers missing data. A comparative analysis in Table 8 demonstrates that our method achieves a higher PSNR value, validating its superior ability to reconstruct images even in the presence of data loss.
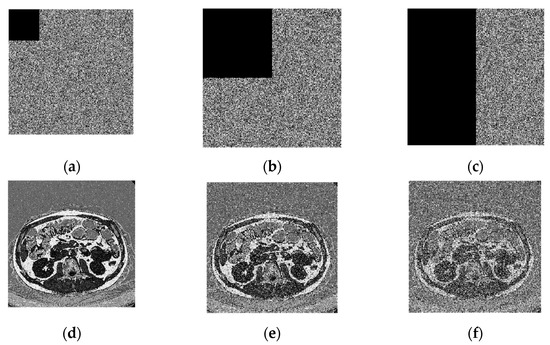
Figure 10.
The result of brain image cropping attack, (a) 1/16 data loss, (b) 1/4 data loss, (c) 1/2 data loss, (d) decrypted image of (a), (e) decrypted image of (b), (f) decrypted image of (c).

Table 8.
Quantitative results of cropping attacks using our method.
5.5. Image with Noise Analysis
To evaluate the effectiveness of the suggested approach, an image with adjustable noise parameters—both mean and variance—is utilized. This allows for an assessment of how varying levels of degradation impact on the method’s ability to encode the image while minimizing data loss. In this analysis, a lung image serves as the benchmark for testing the proposed technique. Figure 11 presents the encoded image subjected to Salt and Pepper Noise (SPN) with noise variances of 0.005, 0.05, and 0.1. The corresponding PSNR values, which are detailed in Table 9, indicate that (1) our encoding algorithm demonstrates significant robustness against SPN, maintaining PSNR values above 5.8 dB, and (2) the reconstructed images retain superior visual quality. These results confirm the method’s strong resistance to noise-induced distortions.

Figure 11.
Decrypted images under different noises with different variances.

Table 9.
Image with difference noise addition.
6. Conclusions
This research introduces a novel synchronization strategy for a four-dimensional hyper-jerk hyper-chaotic system. To accomplish this, adaptive parameter laws are formulated using a hybrid neural framework that combines TFWBC and TFWCC. The Lyapunov stability theorem is employed to establish online learning rules, ensuring both stability and system convergence. The proposed control mechanism effectively synchronizes the 4D master–slave hyper-jerk hyper-chaotic system with high precision. Additionally, the innovative TFWBCC approach is utilized to achieve synchronization of the chaotic states within the 4D Lorenz system. Furthermore, it is highlighted that this method can be applied to enhance the secure transmission of medical images. Simulation outcomes confirm the robustness and efficiency of the proposed control and encryption/decryption techniques. Statistical analyses further validate that the encryption/decryption approach ensures a high level of security.
Future advancements will first focus on adapting the proposed approach for hardware implementation, along with the development of a novel optimization algorithm, specifically an improved sparrow swarm optimization, will be implemented to improve the performance of the TFWBCC. In this study, we proposed a novel method for medical image encryption, demonstrating its effectiveness in ensuring data security and privacy. While the primary focus has been on medical imaging, the proposed approach holds significant potential for broader applications. Future studies could also explore its adaptation to other domains, such as secure communication systems, IoT device data encryption, and financial data protection. Investigating these avenues would further validate the versatility and scalability of the method, addressing critical security challenges across diverse fields. We believe these explorations will open new research directions and enhance the practical impact of the proposed framework.
Author Contributions
D.H.P. and M.T.V. jointly contributed to the conceptualization and methodology of the study. D.H.P. and M.T.V. were responsible for software development, validation, formal analysis, resource management, data curation, original draft preparation, review and editing, visualization (alongside M.T.V.), and supervision. M.T.V. handled project administration and secured funding. All authors have read and agreed to the published version of the manuscript.
Funding
This study did not receive any external funding.
Data Availability Statement
The original contributions presented in this study are included in the article. Further inquiries can be directed to the corresponding author.
Conflicts of Interest
The authors declare no conflicts of interest.
References
- Alber, D.A.; Yang, Z.; Alyakin, A.; Yang, E.; Rai, S.; Valliani, A.A.; Zhang, J.; Rosenbaum, G.R.; Amend-Thomas, A.K.; Kurland, D.B.; et al. Medical large language models are vulnerable to data-poisoning attacks. Nat. Med. 2025, 31, 618–626. [Google Scholar] [CrossRef]
- Wang, W.; Yan, D.; Wu, X.; He, W.; Chen, Z.; Yuan, X.; Li, L. Low-light image enhancement based on virtual exposure. Signal Process. Image Commun. 2023, 118, 117016. [Google Scholar] [CrossRef]
- An, X.; Du, L.; Jiang, F.; Zhang, Y.; Deng, Z.; Kurths, J. A few-shot identification method for stochastic dynamical systems based on residual multipeaks adaptive sampling. Chaos Interdiscip. J. Nonlinear Sci. 2024, 34, 073118. [Google Scholar] [CrossRef]
- Polson, L.A.; Fedrigo, R.; Li, C.; Sabouri, M.; Dzikunu, O.; Ahamed, S.; Karakatsanis, N.; Kurkowska, S.; Sheikhzadeh, P.; Esquinas, P.; et al. PyTomography: A python library for medical image reconstruction. SoftwareX 2025, 29, 102020. [Google Scholar] [CrossRef]
- Lu, S.Y.; Zhu, Z.; Tang, Y.; Zhang, X.; Liu, X. CTBViT: A novel ViT for tuberculosis classification with efficient block and randomized classifier. Biomed. Signal Process. Control 2025, 100, 106981. [Google Scholar] [CrossRef]
- Cai, L.; Fang, H.; Xu, N.; Ren, B. Counterfactual Causal-Effect Intervention for Interpretable Medical Visual Question Answering. IEEE Trans. Med. Imaging 2024, 43, 4430–4441. [Google Scholar] [CrossRef]
- Liu, X.; Yang, J. A novel multi-layer image encryption algorithm based on 2D drop-wave function. Nonlinear Dyn. 2025, 113, 1775–1797. [Google Scholar] [CrossRef]
- Han, X.; Li, Y.; Liu, W.; Chen, X.; Song, Z.; Wang, X.; Deng, Y.; Tang, X.; Jiang, Z. The Applications of Magnetic Particle Imaging: From Cell to Body. Diagnostics 2020, 10, 800. [Google Scholar] [CrossRef] [PubMed]
- Bing, P.; Liu, W.; Zhai, Z.; Li, J.; Guo, Z.; Xiang, Y.; He, B.; Zhu, L. A novel approach for denoising electrocardiogram signals to detect cardiovascular diseases using an efficient hybrid scheme. Front. Cardiovasc. Med. 2024, 11, 1277123. [Google Scholar] [CrossRef] [PubMed]
- Lai, Q.; Hua, H. Secure medical image encryption scheme for Healthcare IoT using novel hyperchaotic map and DNA cubes. Expert Syst. Appl. 2025, 264, 125854. [Google Scholar] [CrossRef]
- Wang, Y.; Xu, Y.; Song, J.; Liu, X.; Liu, S.; Yang, N.; Wang, L.; Liu, Y.; Zhao, Y.; Zhou, W.; et al. Tumor Cell-Targeting and Tumor Microenvironment–Responsive Nanoplatforms for the Multimodal Imaging-Guided Photodynamic/Photothermal/Chemodynamic Treatment of Cervical Cancer. Int. J. Nanomed. 2024, 19, 5837–5858. [Google Scholar] [CrossRef] [PubMed]
- Chu, L.; Su, Y.; Zan, X.; Lin, W.; Yao, X.; Xu, P.; Liu, W. A Deniable Encryption Method for Modulation-Based DNA Storage. Interdiscip. Sci. Comput. Life Sci. 2024, 16, 872–881. [Google Scholar] [CrossRef]
- Lin, C.-M.; Pham, D.-H.; Huynh, T.-T. Encryption and decryption of audio signal and image secure communications using chaotic system synchronization control by TSK fuzzy brain emotional learning controllers. IEEE Trans. Cybern. 2021, 52, 13684–13698. [Google Scholar] [CrossRef] [PubMed]
- Giap, V.N.; Pham, D.H.; Lin, C.-M.; Trinh, M.H.; Le, M.C.; Nguyen, Q.D. Fractional Order T–S Fuzzy Chaotic Models for Secure EEG Signal via a Wireless Communication Protocol Using a Disturbance Observer and Sliding Mode Control Technique. Int. J. Fuzzy Syst. 2024, 26, 1897–1915. [Google Scholar] [CrossRef]
- Aliabadi, F.; Majidi, M.-H.; Khorashadizadeh, S. Chaos synchronization using adaptive quantum neural networks and its application in secure communication and cryptography. Neural Comput. Appl. 2022, 34, 6521–6533. [Google Scholar] [CrossRef]
- Zhang, S.; Peng, X.; Wang, X.; Chen, C.; Zeng, Z. A Novel Memristive Multiscroll Multistable Neural Network with Application to Secure Medical Image Communication. IEEE Trans. Circuits Syst. Video Technol. 2024, 35, 1774–1786. [Google Scholar] [CrossRef]
- Katsikis, V.N.; Stanimirović, P.S.; Mourtas, S.D.; Xiao, L.; Karabašević, D.; Stanujkić, D. Zeroing neural network with fuzzy parameter for computing pseudoinverse of arbitrary matrix. IEEE Trans. Fuzzy Syst. 2021, 30, 3426–3435. [Google Scholar] [CrossRef]
- Zhu, G.; Ma, Y.; Hu, S. Event-Sampled Adaptive Fuzzy Control of MASS via Intermittent Position Data. IEEE Trans. Emerg. Top. Comput. Intell. 2025, 1–13. [Google Scholar] [CrossRef]
- Luo, Y.; Huang, Y.; Yu, F.; Liang, D.; Lin, H. Adaptive Asymptotic Shape Synchronization of a Chaotic System with Applications for Image Encryption. Mathematics 2025, 13, 128. [Google Scholar] [CrossRef]
- Liu, X.; Lv, H. Disturbance Observer-based Adaptive Synchronization of Heterogeneous Chaotic Systems with Uncertainties via DNA Strand Displacement. IEEE Trans. Comput. Biol. Bioinform. 2025, 22, 250–260. [Google Scholar] [CrossRef]
- Li, K.; Liu, X. Fuzzy Adaptive Cooperative Prescribed Time Control for Nonlinear Vehicular Platoon Systems. IEEE Trans. Fuzzy Syst. 2025, 1–10. [Google Scholar] [CrossRef]
- Yi, J.; Mao, J.; Zhang, H.; Chen, Y.; Liu, T.; Zeng, K.; Xie, H.; Wang, Y. Balancing Accuracy and Efficiency with a Multiscale Uncertainty-Aware Knowledge-Based Network for Transmission Line Inspection. IEEE Trans. Ind. Inform. 2025, 1–10. [Google Scholar] [CrossRef]
- Dang, G.; Wang, D. Online Self-Learning Fuzzy Recurrent Stochastic Configuration Networks for Modeling Nonstationary Dynamics. IEEE Trans. Fuzzy Syst. 2025, 1–14. [Google Scholar] [CrossRef]
- Fan, Q.; Ji, D. Identification and Convergence Analysis of Interval Type-2 Takagi-Sugeno-Kang Fuzzy Systems for High-Dimensional Classification Problems. IEEE Trans. Fuzzy Syst. 2025, 1–16. [Google Scholar] [CrossRef]
- Li, Y.; Zhou, E.; Vong, C.-M.; Wang, S. Stacked Ensemble of Extremely Interpretable Takagi–Sugeno–Kang Fuzzy Classifiers for High-Dimensional Data. IEEE Trans. Syst. Man Cybern. Syst. 2025, 1–12. [Google Scholar] [CrossRef]
- Shirgir, S.; Farahmand-Tabar, S. An enhanced optimum design of a Takagi-Sugeno-Kang fuzzy inference system for seismic response prediction of bridges. Expert Syst. Appl. 2025, 266, 126096. [Google Scholar] [CrossRef]
- Liu, C.-L.; Chang, Y.-H. Learning from imbalanced data with deep density hybrid sampling. IEEE Trans. Syst. Man Cybern. Syst. 2022, 52, 7065–7077. [Google Scholar] [CrossRef]
- Liu, A.; Zhao, H.; Song, T.; Liu, Z.; Wang, H.; Sun, D. Adaptive control of manipulator based on neural network. Neural Comput. Appl. 2021, 33, 4077–4085. [Google Scholar] [CrossRef]
- Liang, H.; Liu, G.; Zhang, H.; Huang, T. Neural-network-based event-triggered adaptive control of nonaffine nonlinear multiagent systems with dynamic uncertainties. IEEE Trans. Neural Netw. Learn. Syst. 2020, 32, 2239–2250. [Google Scholar] [CrossRef] [PubMed]
- Murugan, S.; Anh, L.H.; Le, T.-L. Non-linear Control System Using Function-Link Fuzzy Brain Emotional Controller. Int. J. Fuzzy Syst. 2024, 26, 434–448. [Google Scholar] [CrossRef]
- Chao, F.; Zhou, D.; Lin, C.M.; Yang, L.; Zhou, C.; Shang, C. Type-2 Fuzzy Hybrid Controller Network for Robotic Systems. IEEE Trans Cybern 2020, 50, 3778–3792. [Google Scholar] [CrossRef] [PubMed]
- Lin, F.-J.; Sun, I.-F.; Yang, K.-J.; Chang, J.-K. Recurrent fuzzy neural cerebellar model articulation network fault-tolerant control of six-phase permanent magnet synchronous motor position servo drive. IEEE Trans. Fuzzy Syst. 2015, 24, 153–167. [Google Scholar] [CrossRef]
- Yu, Y.; Si, X.; Hu, C.; Zhang, J. A review of recurrent neural networks: LSTM cells and network architectures. Neural Comput. 2019, 31, 1235–1270. [Google Scholar] [CrossRef] [PubMed]
- Sherstinsky, A. Fundamentals of recurrent neural network (RNN) and long short-term memory (LSTM) network. Phys. D Nonlinear Phenom. 2020, 404, 132306. [Google Scholar] [CrossRef]
- Fan, R.; Li, Y. An adaptive fuzzy trajectory tracking control via improved cerebellar model articulation controller for electro-hydraulic shovel. IEEE/ASME Trans. Mechatron. 2021, 26, 2870–2880. [Google Scholar] [CrossRef]
- Hou, S.; Fei, J.; Chen, C.; Chu, Y. Finite-time adaptive fuzzy-neural-network control of active power filter. IEEE Trans. Power Electron. 2019, 34, 10298–10313. [Google Scholar] [CrossRef]
- Zheng, K.; Zhang, Q.; Hu, Y.; Wu, B. Design of fuzzy system-fuzzy neural network-backstepping control for complex robot system. Inf. Sci. 2021, 546, 1230–1255. [Google Scholar] [CrossRef]
- Pham, V.-T.; Vaidyanathan, S.; Volos, C.; Wang, X.; Hoang, D.V. A hyperjerk memristive system with hidden attractors. In Advances in Memristors, Memristive Devices and Systems; Springer: Berlin/Heidelberg, Germany, 2017; pp. 59–80. [Google Scholar]
- Huynh, T.-T.; Lin, C.-M.; Pham, T.-T.T.; Cho, H.-Y.; Le, T.-L. A modified function-link fuzzy cerebellar model articulation controller using a PI-type learning algorithm for nonlinear system synchronization and control. Chaos Solitons Fractals 2019, 118, 65–82. [Google Scholar] [CrossRef]
- Utkin, V.I. Sliding Modes in Control and Optimization; Springer Science & Business Media: Berlin/Heidelberg, Germany, 2013. [Google Scholar]
- Wu, Y.; Zhang, L.; Berretti, S.; Wan, S. Medical image encryption by content-aware DNA computing for secure healthcare. IEEE Trans. Ind. Inform. 2022, 19, 2089–2098. [Google Scholar] [CrossRef]
- Bassham, L.E., III; Rukhin, A.L.; Soto, J.; Nechvatal, J.R.; Smid, M.E.; Barker, E.B.; Leigh, S.D.; Levenson, M.; Vangel, M.; Heckert, N.A.; et al. A Statistical Test Suite for Random and Pseudorandom Number Generators for Cryptographic Applications; SP 800-22 Rev. 1a; National Institute of Standards & Technology: Gaithersburg, MD, USA, 2010. [Google Scholar]
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).