1. Introduction
Due to their powerful adaptability, self-organization, and self-learning abilities, neural networks (NNs) have become a research hotspot for many scholars [
1,
2,
3,
4]. However, in the implementation of NNs, uncertainties are often encountered because of inaccurate modeling or environmental noise, which can degrade system performance and further lead to system instability [
5,
6,
7]. In addition, on account of unreliable communication channels and limited bandwidth, the control signal may not reach the receiving terminal successfully. Hence, data packet dropout is an inevitable problem for the control of NNs. When packet dropout occurs from the controller to the actuator channel, it is referred ti as missing control input [
8]. This phenomenon is inevitable due to actuator failure, intermittent controller unavailability, and other reasons. Generally, there are two methods to cope with this problem. One is the hold-input method [
9,
10]; that is, when the controller signal is lost, the latest control signal is taken as the input of the actuator. The other is the zero-input method [
11,
12,
13,
14]; that is, when the control signal is lost, the input of the actuator is set to zero, then the controlled system can be converted to a switched system. Promising results on systems with packet dropout have been achieved. For example, based on the zero-input method, robust synchronization for uncertainty delayed NNs with control packet dropout was implemented under sampling control in [
12]. For fuzzy system with packet dropouts, refs. [
13,
14] studied robust
control and exponential stabilization using the zero-input method under sampling control, respectively. It should be noted that although related research on neural networks incorporating these two network-induced phenomena has achieved certain results, there remains significant room for improvement.
On the other hand, networked control methods have attracted considerable attention in recent decades. As is well known, traditional time-triggered control methods will generate redundant data and therefore lead to over-occupation of limited communication bandwidth and blockage of information channels. It has been proved in [
15] that the integration of an event-triggered scheme into the controller can effectively reduce the number of control task executions. Thereafter, ET control has attracted increasing attention from scholars [
16,
17,
18,
19,
20]. The sampling of ET control is carried out only when a preset event is triggered; that is, the system will transmit information only as needed. In this way, the waste of network resources can be reduced while guaranteeing the expected performance. Among the existing ET schemes, the periodic event-triggered (PET) scheme is a classic one, in which the preset triggering condition is monitored periodically [
21,
22]. It can ensure that the interval between two adjacent triggers is greater than zero, so it can automatically avoid the emergence of Zeno phenomena. Based on the PET scheme, a novel ET scheme called the memory-based event-triggered (MET) scheme was devised in [
23]. The MET scheme comprehensively utilizes the difference between historically transmitted data and the currently sampled data to design the triggering condition [
24,
25,
26,
27]. What needs to be pointed out is that most existing METs use the discrete mean value of a certain number of historically sampled or triggered data. However, if packet dropouts occur, some sampled data are partial, or all missing, then the effect of the MET scheme using a discrete mean value will be reduced. However, if the continuous mean value—that is, the integral over a past continuous interval—is employed to design the triggering condition, even if some sampled data are lost, the integral can still address the issue related to packet dropout due to the good property of the integral. In this way, both higher control performance and fewer triggering times can be achieved.
Enlightened by the above thoughts, this paper will investigate the stabilization of NNs with uncertainty and control input missing by designing an ET scheme. The contributions of this paper can be summarized as follows:
(1) To deal with the impact of packet dropout, a novel MET scheme, named IMET, is devised, which introduces an integral of the system state over a specified memory interval. The proposed IMET scheme can not only make use of the historical state information but also alleviate the effects of packet dropout and exclude the occurrence of Zeno phenomena.
(2) Under the proposed IMET scheme, the uncertain NN with control input missing is modeled by a switched system on the basis of the zero-input method. Then, a piecewise time-dependent Lyapunov functional consisting of a looped functional is designed. The exponential stability of the switched closed-loop system is analyzed and low conservative stability conditions and control gain design algorithms are developed.
The remainder of this paper is organized as follows. The IMET scheme is proposed and the closed-loop system is established in
Section 1. The sufficient conditions for exponential stability and the co-design method of the control law are given in
Section 2. The obtained results are verified using an example in
Section 3.
Section 4 concludes this paper.
Some special symbols are explained in
Table 1.
2. Problem Formulation
Consider a NN with uncertainties modeled as follows:
where
denote the state vector and the control input, respectively;
and
are known real matrices, and
and
represent the parameter uncertainties. The system nonlinearity
is a piecewise-continuous function with
and satisfies
where
is a constant and
H is a constant matrix.
Assumption 1. Suppose the parameter uncertainties and are of the following structure:where are known real matrices and the uncertain matrix is bounded by We denote
as the sampling instants with sampling period
, and
with
as the triggering instants; that is, at
, the sampled data packets are transmitted. We define
with the integral period
. Then, the triggering condition of the IMET scheme is presented as follows:
where
is the current sampling instant, and
is the next triggering instant to be determined;
with the memory period
and
;
is the triggering matrix to be designed, and
is a given constant.
Remark 1. The existing MET (EMET) scheme is that proposed in [23].where m denotes the number of historically transmitted packets, , , and . The distinction between EMET and IMET can be summarized in two points. First, the EMET scheme employs a discrete average of some historic data at , such as and . However, the IMET scheme adopts the continuous mean of the system state over the interval , resulting in and . Second, IMET further incorporates the Jensen’s inequality to derive a more stringent triggering condition. Using Jensen’s inequality to yieldsFinally, the proposed IMET scheme can be obtained. Furthermore, the IMET scheme can exclude Zeno behavior directly, because it is devised on the basis of the PET scheme and therefore can guarantee . Remark 2. It follows that the triggering condition of IMET is more stringent, which is beneficial for reducing redundant data transmission. Meanwhile, as is well known, the value of an integral over some time interval can not be affected by a finite number of discontinuous points. Therefore, for system (1), even if the sampled or triggered data at finite instants in are missing, the introduction of the integral term can take full use of the historical information of the system state over this interval. In this way, it can better reflect the “memory" characteristic to reduce false triggers caused by fluctuations in signal measurements. In this paper, the state feedback controller is taken as
where
K is the control gain. By combining it with (
3), the closed-loop system can be described as follows:
From a practical point of view, it is assumed that packet losses happen in the controller–actuator channel; that is to say, if some triggering instants
may be lost, then
. In this case, the closed-loop system with control packet loss has the following description:
If we introduce a switching signal
with
and
to distinguish whether the triggering instant is lost, then a switched system can be organized as follows:
Obviously, system (
9) switches between the stable subsystem (
7) and the unstable subsystem (
8).
The switched system based on the zero-input method is shown in
Figure 1. From
Figure 1, it can be observed that the occurrence of packet loss generates a switching signal
, which subsequently determines the value of the feedback controller and activates the corresponding subsystem.
Assumption 2. In this paper, it is assumed that missing packets only occur in the controller–actuator channel, and δ is employed to represent the loss rate of control packets.
According to the triggering condition in (
5), there are
sampling instants within the triggering interval
. Next, using the partition method, the triggering interval
can be written as follows:
We define the time-varying delay
, then
. Thus, one can have the following:
Therefore, the closed-loop system (
9) can finally be expressed as follows:
Definition 1 ([
28])
. If there exist satisfyingthen the closed-loop system (1) is said to be exponentially stable. Definition 2. For a switching signal , if there exists a constant , such thatholds for , where stands for the number of switching events on , then is called the average dwell time (ADT) of . Lemma 1 ([
29])
. For any continuously differentiable function , the following inequality holds for a given matrix :where . 3. Main Results
The stability criterion and the controller design for the resulting system (
12) will be proposed in this section.
Theorem 1. For given scalars , , and feedback gain matrix K, the closed-loop system in (12) is exponentially stable if there exist matrices , and matrices , such that the following LMIs hold:where and are symmetric matrices, and , , , , , , , , , , , , , , , , , , , , , , , , , , , , , , , . The ADT and the pocket loss rate δ satisfy the following constraints: Proof. Consider a Lyapunov functional
as follows, where
is for the stable subsystem (
7) and
is for the unstable subsystem (
8):
with
in which
,
, and
,
are given constants.
Case 1: When the closed-loop system (
12) is in the stable subsystem, the derivative of
along the trajectory of the stable subsystem (
7) is as follows:
By applying Jensen’s inequality to the first integral term in (
22), one obtains the following:
with
.
In terms of Lemma 1, the second integral term in (
22) can be estimated as follows:
where
.
Utilizing the free-weighing matrix method, the following equation holds for constants
,
and appropriate dimension matrices
:
in which
and
.
Meanwhile, based on (
4), one obtains
; then, for constant
, it follows that
where
,
.
Substituting (
2), (
5), (
23)–(
26) into (
22), and considering the fact that
we can have
where
are defined in Theorem 1. Next, according to LMIs (
14) and (15), one can finally obtain the following:
Case 2: When the closed-loop system (
12) is in the unstable subsystem, taking the derivation of
yields the following:
With the same operation, we give the estimation of the integral term in (
28) as follows:
in which
.
Simultaneously, we have the following identical equation and inequality:
where
and
.
Combining with (
2), (
28)–(
30), one has the following:
Based on (16), one can conclude the following:
Furthermore, synthesizing (
27) and (
32), one can now obtain that
in which
Moreover, we denote as the switching series between the stable subsystem and the unstable subsystem during . Then, the triggering instant may be transmitted or lost. In what follows, these two cases will be discussed in detail.
If
is the lost triggering instant, then one has the following:
In terms of the condition in (17), one further has
If is the transmitted triggering instant, then based on (18), the same result can still be obtained.
During the interval
, we denote
and
as the total length of all stable intervals and the total length of all unstable intervals, respectively. Obviously, the loss rate of control packet
can be represented as follows:
Let
be the switching instant nearest to
t. Due to the condition (
27), (
32), and (
34)–(
35), the following holds:
with
,
.
In line with (
20) and (21), one can obtain
and
in which
,
,
and
.
Considering (
36), the following inequality can be deduced:
where
. Thus, based on Definition 1, the system (
12) is exponentially stable. □
Remark 3. Looped functionals and can result in and , in which and are sampling instants. Given that the switching instant comes from the set of sampling instants, it follows that and . As a result, and will not appear during the analysis of . This enables LMIs for system stability to be simplified, consequently enlarging the feasible region of the LMIs. Additionally, looped functionals and can fully utilize the system information over and , which contributes to obtaining results with reduced conservatism.
Next, the controller design for the system (
1) based on the aforementioned analysis will be given by employing the matrix decoupling method.
Theorem 2. For given positive scalars β, ν, ρ, ϖ, , κ, , , and negative scalar , the closed-loop system (1) is exponentially stable under the design of control gain matrix if there exist matrices , , arbitrary matrices , such that the following LMIs hold:where and are symmetric matrices, and , , , , , , , , , , the other blocks of , have the same definition as those of in Theorem 1, and the ADT and the pocket loss rate satisfy and . Proof. We define
. Then, LMIs (
14)–(18) can be represented as (
37)–(41). Based on (
37)–(41), one can calculate the gain matrix
, which achieve the proof. □
4. Numerical Simulation
In this section, a numerical example will be employed to demonstrate the effectiveness of the proposed IMET scheme.
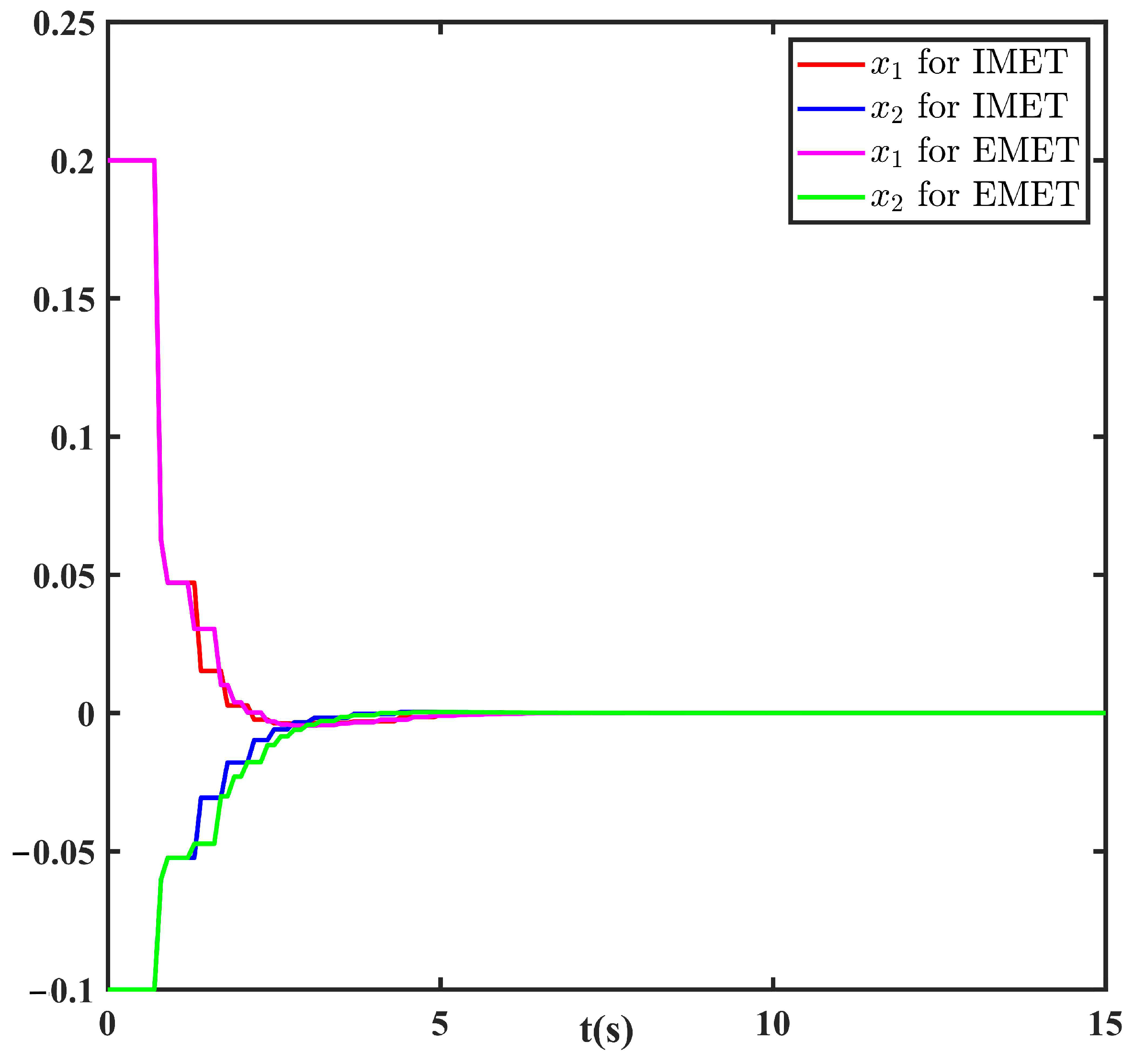
Example 1. Consider the following NN with the following uncertainties:The initial condition is chosen as . We select , then the loss rate is calculated as based on Condition (19) in Theorem 1. Then, we set and , and the ADT is calculated as . We take and constant matrix ; then, the control gain matrix and the triggering parameter Ω are calculated based on Theorem 2 as follows: The state responses under the EMET and the IMET are shown in
Figure 2. It is clear that the system trajectories obtained via the IMET scheme are gentler and can converge to zero much faster than the ones obtained by the EMET. This means that the IMET can ensure better system performance.
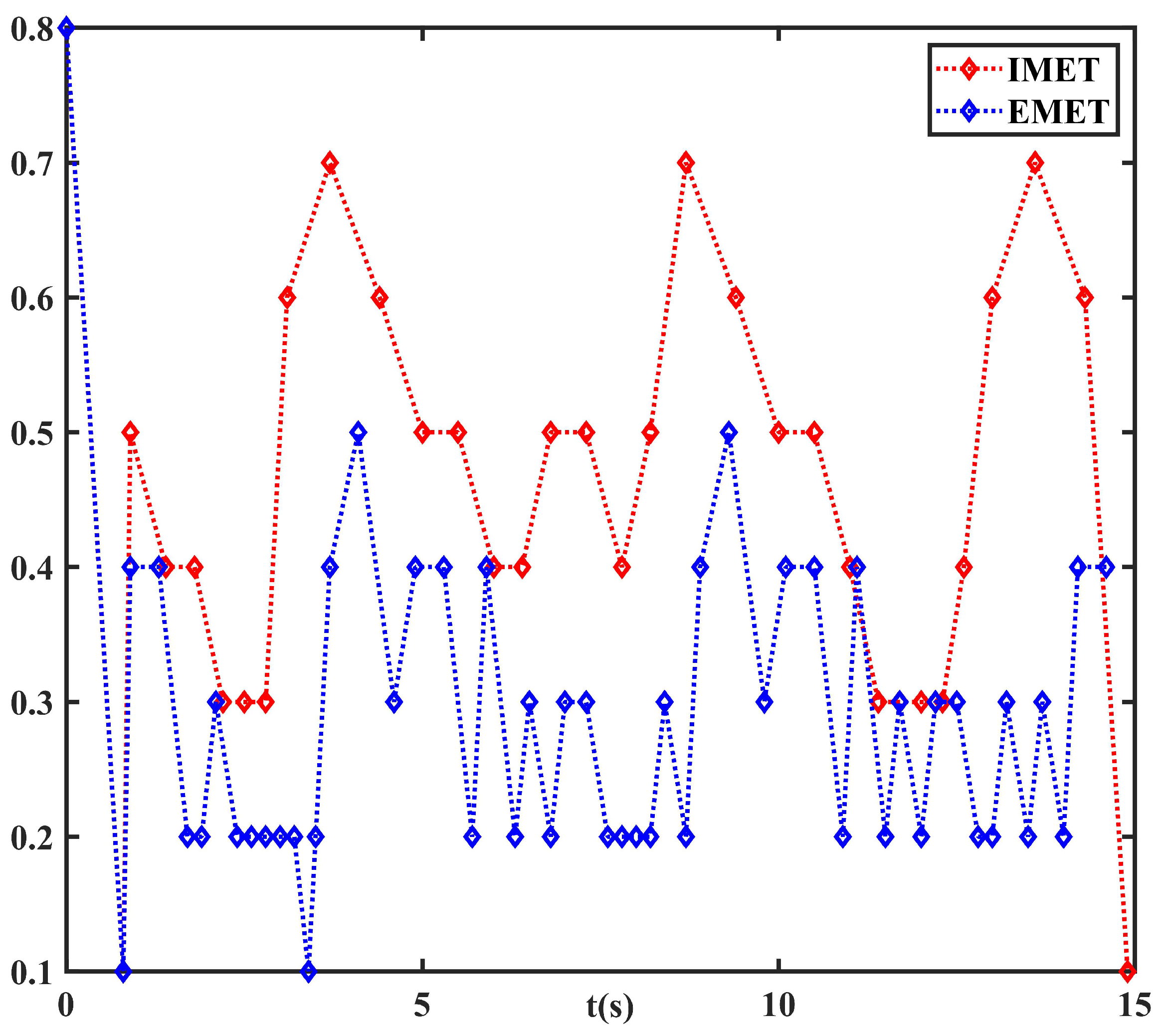
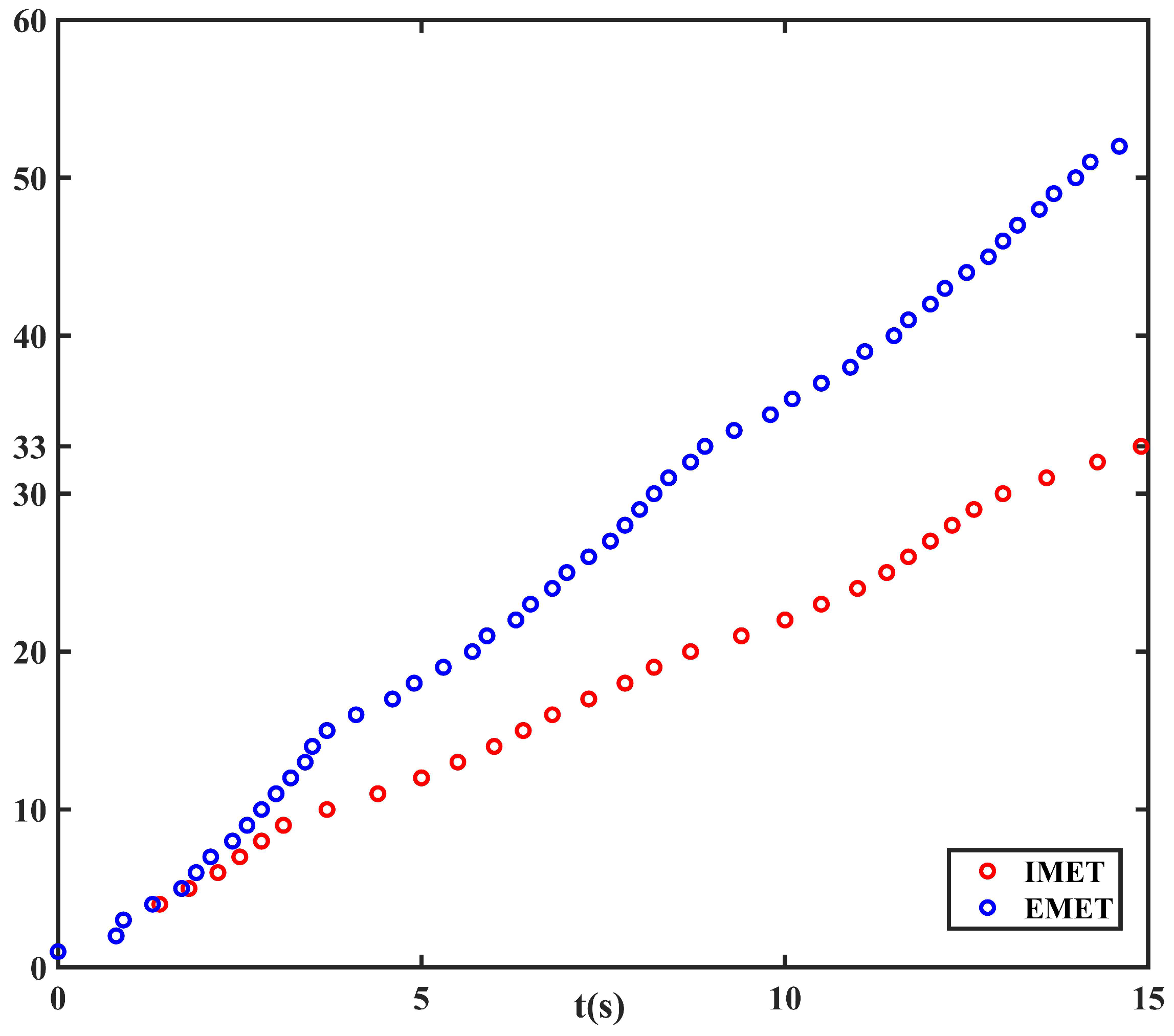
Figure 3 and
Figure 4 present the execution interval and the cumulative triggering times for the EMET scheme and the IMET scheme, respectively. One can determine that the triggering interval of the IMET is larger that of the EMET. Meanwhile, the total triggering number for the IMET scheme is 33, which is less than 52 obtained via the EMET scheme. Combining
Figure 2,
Figure 3 and
Figure 4, one can conclude that the proposed IMET scheme can reduce the network burden on the premise of ensuring good system performance.
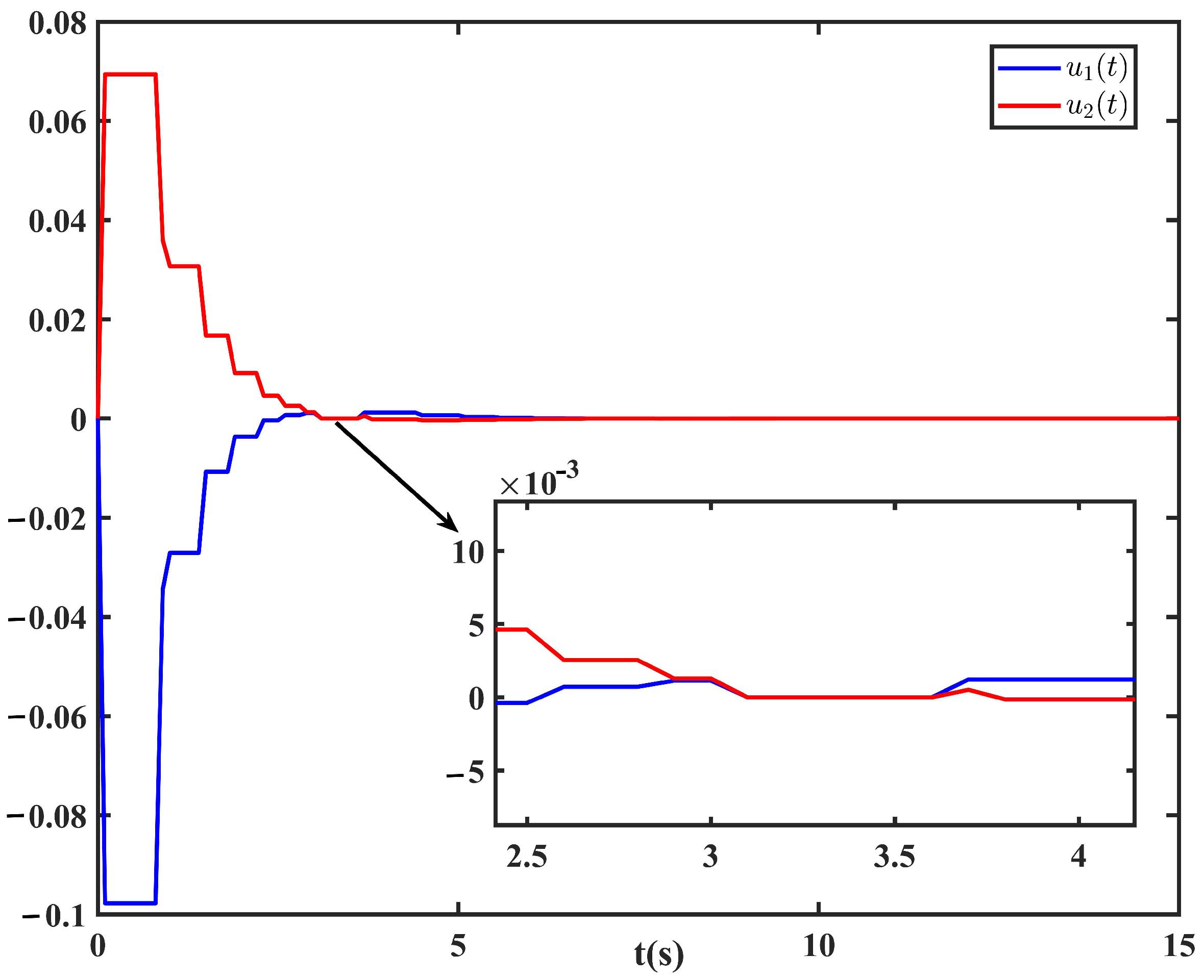
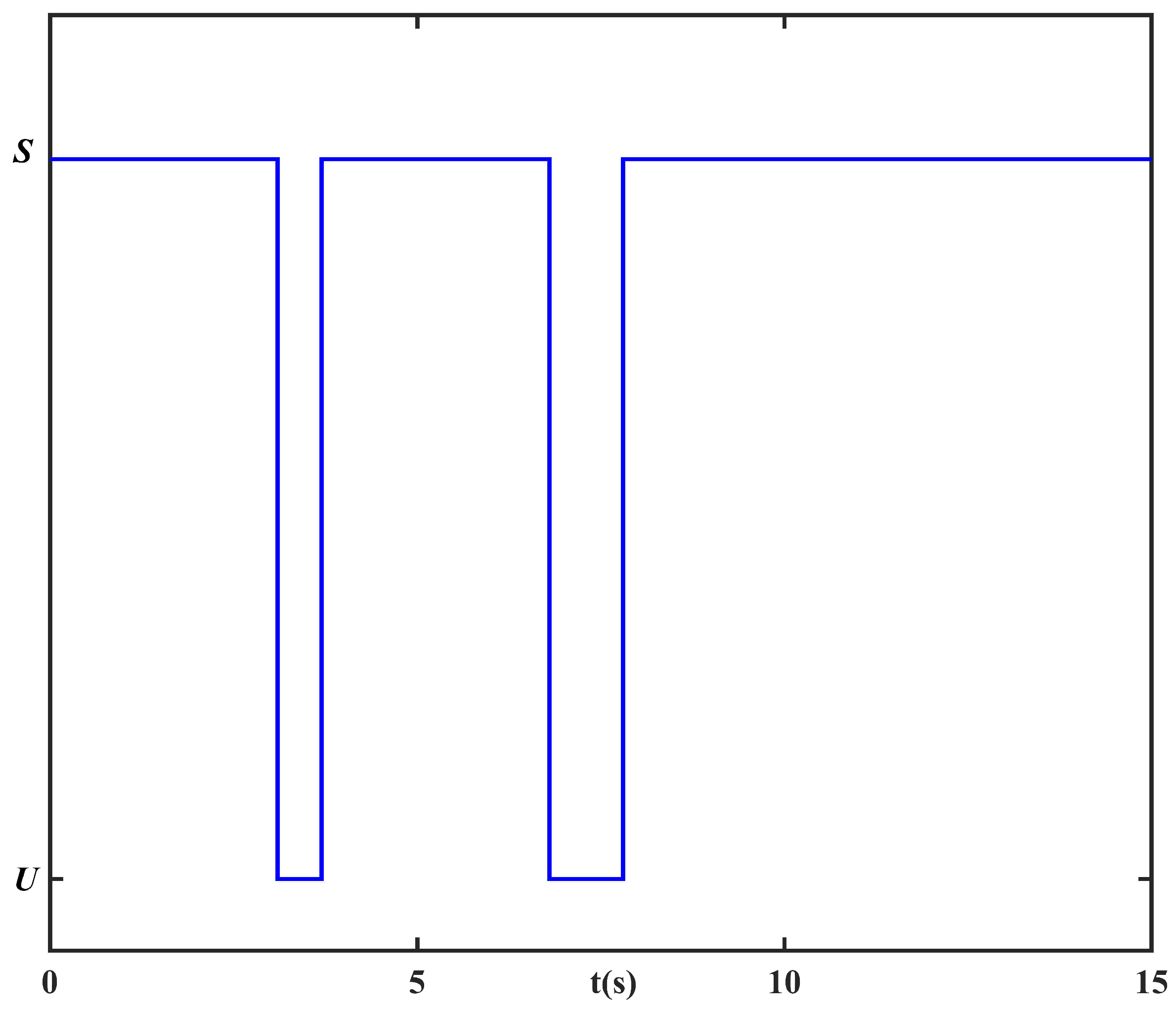
Figure 5 displays the trajectories of the control input under the IMET scheme with packet loss rate
. The intervals corresponding to
suggest that the system is under the unstable subsystem. The starting points of these intervals are the moments when the packets are lost, and the end points are the moments when the system is under the controller again. Meanwhile, the switching signal
is shown in
Figure 6.
5. Conclusions
In this paper, by employing the zero-input method, the stabilization problem of an uncertain NN with missing input is converted into the stability problem of a switched system and then is addressed by developing an IMET scheme. Compared with the EMET scheme, the proposed IMET scheme is based on the PET scheme and therefore can prevent Zeno behavior naturally. Moreover, it introduces an integral over a past time interval of the latest triggering instant to construct the triggering condition. Therefore, even if the packets close to the current trigger are missing, it can still employ the integral to cover the information of the system with packet loss. To study the switched closed-loop system, a new piecewise Lyapunov functional is designed, which not only contains a looped functional to fully use the state information but also contains a Lyapunov functional involving the memory period of the IMET scheme. Then, by using this functional and combining with some inequalities, we establish sufficient conditions that guarantee the exponential stability of the resulting closed-loop system. Finally, an example is provided to analyze the validity of the obtained results.