Abstract
This paper presents a systematic investigation into the solvability and the general solution of a tensor equation system within the split quaternion algebra framework. As an extension of classical quaternions with distinctive pseudo-Euclidean properties, split quaternions offer unique advantages in multidimensional signal processing applications. We establish rigorous necessary and sufficient conditions for the existence of solutions to the proposed tensor equation system, accompanied by explicit formulations for general solutions when solvability criteria are satisfied. The theoretical framework is further strengthened by the development of computational algorithms and numerical validations through concrete examples. Notably, we demonstrate the practical implementation of our theoretical findings through encryption/decryption algorithms for color video data.
Keywords:
split quaternion algebra; tensor equations; Einstein product; general solution; video encryption MSC:
15A09; 15A24; 15B33
1. Introduction
In 1843, William Rowan Hamilton introduced the concept of real quaternions [1] defined by
where and , respectively, denote the set of real quaternions and the set of real numbers. Quaternions have been utilized in numerous areas, including the analysis of quaternion random signals [2], color image processing [3] and face recognition [4]. As the theory of quaternions evolved, James Cockle introduced the concept of split quaternions [5] in 1849:
where the imaginary identities satisfied
Split quaternions have diverse applications across various fields. In physics, they are used to model spacetime symmetries and rotations in relativity [6]. In computer graphics, split quaternions assist in efficiently handling 3D rotations and transformations [7]. Split quaternions also have applications in control theory, signal processing, and robotics, where they help in representing and solving complex spatial relationships and transformations [8].
Tensors, as mathematical constructs that generalize scalars, vectors, and matrices to higher dimensions, are extensively applied across a wide range of scientific and engineering domains due to their capability to manage complex data structures. In computer vision and image processing, tensors are used to represent multidimensional image data, with convolution operations in neural networks being performed as tensor operations [9]. In physics, tensors are fundamental in general relativity for describing spacetime geometry [10] and in electromagnetism for unifying electric and magnetic fields [11]. In machine learning, tensors are core data structures in frameworks like TensorFlow and PyTorch, playing a crucial role in optimization and model training [12,13]. They are also essential in data analysis for dimensionality reduction and feature extraction, particularly within recommendation systems [14]. The multidimensional nature of tensors makes them powerful tools for handling complex data, and their significance continues to grow with advancements in computational power and algorithms.
presents an N-dimensional tensor, which is a natural extension of the matrix. For , is a vector. For , is a matrix. In recent decades, numerous researchers have made significant contributions to the study of tensors and quaternions. For example, Qi et al. [15,16,17,18,19] researched the spectral theory of tensor and tensor eigenvalues. Zhang et al. [20,21] investigated some terative solutions of generalized Sylvester quaternion tensor equations. Gao et al. [22] established the necessary and sufficient conditions for the existence of (anti-)-Hermitian solutions to a system of matrix equations over split quaternion algebra. Xie et al. [23] proposed the BiCG algorithm for solving the minimal Frobenius norm solution of generalized Sylvester tensor equation over the quaternions. Yang et al. [24] researched a system of tensor equations over the dual split quaternion algebra with an application.
To the best of our knowledge, research on systems of tensor equations over split quaternions remains relatively scarce in the current literature. Building upon the aforementioned studies and leveraging the existing applications of tensor equation systems within split quaternion algebra, this paper aims to systematically investigate the solvability conditions and derive the general solution for the following system of split quaternion tensor equations
where and are given quaternion tensors and are unknown split quaternion tensors.
Significantly, this study marks the first successful resolution of complex multilinear tensor equation systems over split quaternion algebra, representing a substantial advancement in the field. Moreover, our research can provide an application of split quaternion tensor equations in practical cryptographic implementations.
This paper is organized as follows: In Section 2, some basic theories and relevant properties of quaternion tensors are reviewed. In Section 3, we derive some practical necessary and sufficient conditions for the existence of the general solution to system (1) over . Furthermore, the formula of the general solution to system (1) is also given when it is solvable. Especially, the unique solution is given when the uniqueness condition is satisfied. In Section 4, two algorithms and one numerical example are given in order to illustrate our results. In Section 5, we provide four algorithms and two examples for color video encryption and decryption. In Section 6, we present a conclusion to summarize this paper.
In subsequent sections, the symbols , , , and are used to represent the set of all real matrices, all complex matrices, all n dimensional split quaternion column vectors, and all split quaternion matrices. The symbol denotes the rank of the matrix A. I denotes the identity matrix and O the zero matrix with an appropriate size. denote the conjugate, the transpose, the conjugate transpose, and the Moore–Penrose inverse of the matrix A, respectively. Let and represent the set of all corresponding dimensional real tensors, complex tensors, and split quaternion tensors, respectively.
2. Preliminaries
This section primarily introduces split quaternion tensors, the Einstein product of split quaternion tensors, the complex representation and related properties of split quaternion matrices, and so on. These concepts lay the groundwork for deriving the main conclusions presented in the subsequent sections.
Definition 1
([25]). For two split quaternion tensors and , the Einstein product of and is defined by the operation via
where .
The Einstein product of tensors is closely related to matrix multiplication. We introduce a mapping that establishes an isomorphic relationship between tensors with respect to the Einstein product and matrices with respect to the general matrix product.
Definition 2
([26]). There exists an isomorphic mapping f from to denoted as
where and .
It is apparent that f is a one-to-one mapping. Therefore, the inverse mapping exists. Subsequently, we prove that f is an isomorphic mapping.
Proof.
For and , we need to prove that , where and · denote the Einstein product and matrix product, respectively.
Through the definition of the Einstein product, then
By direct computation, we obtain
Therefore, f is isomorphic. □
As f is an isomorphic mapping, utilizing f can convert split quaternion tensors into matrices during operations. In what follows, we present the complex representation of split quaternions and split quaternion matrices.
For any split quaternion , it can be uniquely expressed as where and are complex numbers, which is known as the complex representation of split quaternions. Noting that and , we know the algebra of split quaternions is a noncommutative algebra.
Definition 3.
The complex representation of a split quaternion is where . We use the symbol g to denote it as
Similarly, for any given split quaternion matrix A, the complex representation of matrix where is denoted by G as
It is evident that and A correspond one to one. Moreover, considering its properties, we can summarise this as the following proposition.
Proposition 1.
If and G is defined in Definition 3, then
- (a)
- if and only if ;
- (b)
- ;
- (c)
- ;
- (d)
- .
Proof.
It is evident that (a), (b), and (c) hold, so we just need to prove (d). By computation, on the one hand,
On the other hand,
□
In what follows, we explore the structure of the operator .
Definition 4
([27]). For any , A can be uniquely expressed as where . It can also be uniquely expressed as where . According to this, we define
where the symbol ≅ denotes an equivalence relation. We define that
It is evident that the following is true:
Then, we focus on the main properties related to as follows.
Proposition 2.
Let and . Φ is defined in Definition 4. Then,
- (a)
- if and only if ;
- (b)
- ;
- (c)
- .
Proof.
It is evident that (a) and (b) hold, so we only need to prove (c). By calculating, we have
Then,
□
Based on this proposition, we then investigate the structure of the operator .
Theorem 1
([27]). Suppose that and , where and . Then,
The result on in Theorem 1 about the complex representation of split quaternion matrix product is an essential tool for transforming the split quaternion matrix equation into the complex matrix equation.
Lemma 1.
For Let
and then
Proof.
According to the given conditions, it follows that
□
By Theorem 1 and Lemma 1, we can obtain the following corollary.
Corollary 1.
Suppose , and , where , and . Then,
Lemma 2
([28]). With and , the matrix equation has a solution if and only if
In that case, it has the general solution given by
where is an arbitrary vector. In particular, it has a unique solution if
3. Solution of System (1)
From the previous discussion, we now turn our attention to solving the system of split quaternion matrix Equation (1). For convenience, we define some useful notations that will be used in the following section. For , we denote , and then , and , where . We set
For , we suppose
and
Evidently, the following equation
holds. Now, according to Lemma 2 and Equation (10), we can give the expression of general solution to system (1).
Theorem 2.
For , we suppose , , and . For , we denote , and then , and , where . Meanwhile, are defined in Equations (8) and (9). Then, system (1) has a set of solutions if and only if
In this case, the set of general solutions can be expressed as
where y is an arbitrary vector with appropriate size. Furthermore, the system of split quaternion matrix equation (1) has a unique solution if and only if
After calculation, we have
Proof.
According to Corollary 1 and Theorem 2, it follows that
By Lemma 2, we can obtain that system (1) has a solution if and only if Equation (11) holds. That is to say,
which is expressed as set (12). Moreover, if Equation (11) holds, then system (1) has a unique solution if and only if
Equivalently, Equation (13) holds and set (14) is the unique solution. □
In the next part, we consider the Moore–Penrose generalized inverse of the column block matrix. Let
where n is same as system (1) and are the same as in Theorem 2. From the results in [29], we have
Corollary 2
([30]). The system of split quaternion matrix in Equation (1) has a solution if and only if
In this case, the set of general solution of system (1) can be expressed as
where and y is an arbitrary vector with appropriate size. Furthermore, if Equation (18) holds, then system (1) has a unique solution if and only if Equation (13) holds. In this case,
Corollary 3.
Let the condition be satisfied in Corollary 2. Then, the optimization problem
has a unique minimizer that satisfies
4. Numerical Exemplification
In this section, we give two numerical algorithms (Algorithms 1 and 2) and one numerical example to solve system (1).
| Algorithm 1 General Solution of System (1) |
(1) Input the factors: n. (2) Input the tensors: and . (3) Calculate the matrices and , where . (5) If both Equation (11) and Equation (13) hold, then calculate the unique solution by Equation (14). (7) Output: . |
| Algorithm 2 General Solution of System (1) |
(1) Input the factors: n. (2) Input the tensors: and . (3) Calculate the matrices and , where . (5) If both Equation (18) and Equation (13) hold, then calculate the unique solution by Equation (21). (7) Output: . |
Example 1.
Given the split quaternion tensors:
By MATLAB calculation, the output is that there exists a unique solution and the unique numerical solution is
The true solution is
It is worth noting that the error between the numerical solution and the true solution is , which undoubtedly demonstrates the accuracy of our results.
5. One Application Based on (1)
Sylvester-type quaternion tensor equations hold great significance across numerous fields, such as systems science, cybernetics, and signal processing. This section centers around utilizing the outcomes of system (1) to present an application example. Split quaternion tensors are capable of representing color videos, especially when the video is divided into multiple image slices. Here, we introduce a method for the encryption and decryption of videos by employing Theorem 2. In what follows, we provide encryption and decryption algorithms (Algorithms 3 and 4), block encryption and decryption algorithms (Algorithms 5 and 6), and two examples to demonstrate our results.
| Algorithm 3 Encryption Process of Videos |
(1) Input: n original videos and system coefficients and . (2) Parse the videos: represents the i-th video where and represents the j-th frame of the i-th video. (3) Calculate the tensors and by system (1). (4) Encrypt the i-th video by where . and is the key of the i-th video. (5) Output: Encrypted video. |
| Algorithm 4 Decryption Process of Videos |
(1) Input: Encrypted videos , keys and system coefficients where . (2) Calculate the numerical tensors by Algorithm 1. (3) Recover the videos: represents the i-th recovered video where and represents the j-th recovered frame of the i-th video. (4) Calculate the error norm for and . (5) Output: Decrypted video. |
In order to more intuitively understand Algorithms 5 and 6 that we present next, we give the corresponding flowcharts (Figure 1).
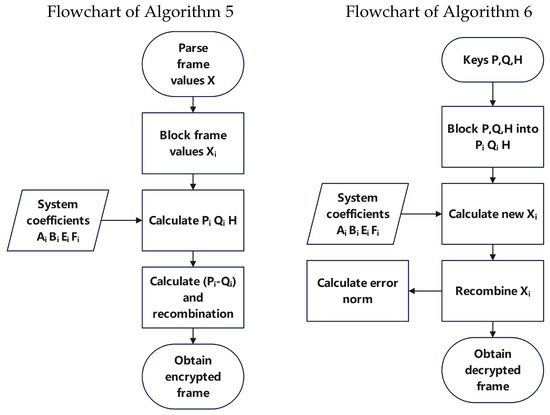
Figure 1.
Flowcharts of Algorithms 5 and 6.
First, we take a frame from the video and parse its pixel data. We divide the frame into 3600 subblocks. Then, we set the coefficients by generating random matrices. We calculate for each subblock. We take as the cryptographic subblock corresponding to each subblock. Then, is restored to the corresponding position and the encrypted frame is generated. The decryption process is that the input coefficients calculate the new subblock and then it is restored according to the corresponding position to generate the decrypted frame. Then, we calculate that the decrypted frame has a good restoration effect with the original frame.
| Algorithm 5 Block Encryption Process of Frame |
(1) Input: one original frame and system coefficients and . (2) Parse the frames: represents the frame and represents the i-th sub-frame of the frame where . (3) Calculate the matrices and by system (1). (4) Assemble the i-th sub-frame where back into the frame . Encrypt the frame X by . (5) Output: Encrypted frame. |
| Algorithm 6 Block Decryption Process of Frame |
(1) Input: Encrypted frame , keys and system coefficients where . (2) Calculate the matrices by Algorithm 1. (3) Recover the frame: represents the i-th recovered sub-frame where ; assemble the back into the frame . (4) Calculate the error norm between X and . (5) Output: Decrypted frame. |
Remark 1.
As the dimensions of the decrypted video increase, the time and space complexity of Algorithms 3 and 4 increase exponentially. Therefore, we propose a block encryption and decryption algorithm in Algorithms 5 and 6. By reusing Algorithms 5 and 6, the memory usage can be reduced and the operational speed can be significantly enhanced. It is worth mentioning that Algorithms 5 and 6 are also suitable for local encryption and decryption tasks.
All numerical experiments in this paper were performed in the following hardware and software configurations: Intel(R) Core(TM) i5-10210U CPU @ 1.60 GHz 2.11 GHz, 16 GB RAM, Windows 11 operating system, and MATLAB R2018a. In addition, all test videos were taken using the author’s camera.
Example 2.
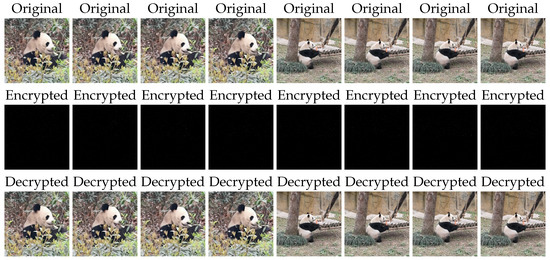
Let us input two videos and execute the above algorithms. The following is the result using MATLAB (Figure 2):

Figure 2.
Frames before and after Encryption and Decryption.
In the result, the average error between the numerical solution and the true solution is . The error of each frame is shown in Table 1 as follows.

Table 1.
Error between numerical solution and true solution.
To further evaluate the quality of the decrypted videos, we use the Peak Signal-to-Noise Ratio (PSNR), Structural Similarity Index (SSIM), and Feature Similarity Index (FSIM) [31]. The results are summarized in Table 2. All PSNR values exceed 50, while both SSIM and FSIM values are 1, demonstrating the outstanding quality of our decrypted videos.

Table 2.
PSNR, SSIM, and FSIM of video 1 and video 2.
Example 3.
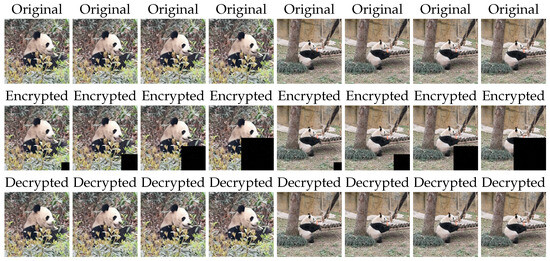
Let us input two videos and finish local encryption and decryption using Algorithms 5 and 6 with MATLAB (Figure 3):

Figure 3.
Frames before and after Block Encryption and Decryption.
In the result, the average error between the numerical solution and the true solution is . The error of each frame is listed in Table 3 as follows.

Table 3.
Error between numerical solution and true solution.
The results of PSNR, SSIM, and FSIM are shown in Table 4. PSNR values all exceed 50, while both SSIM and FSIM values reach 1, indicating that the quality of local decryption is excellent.

Table 4.
PSNR, SSIM, and FSIM of video 1 and video 2.
6. Conclusions
The system of quaternion tensor equation (1) is universal, encompassing many other systems. This kind of system of quaternion tensor equations has practical applications in many areas. In this paper, we first transformed the quaternion tensor equations into quaternion matrix equations through the function f. By using the complex representation of split quaternion matrices and Moore–Penrose inverse, we presented a necessary and sufficient condition for the existence of a general solution to system (1). When the solvability conditions hold, we also derived the expression of the general solution to system (1). In particular, the unique solution was also given when the uniqueness condition held. Then, we converted the obtained quaternion matrix solution back into a quaternion tensor solution using the function . Additionally, we established two algorithms to solve system (1), and one example was given to prove the correctness of our results. In the last part, we provided the algorithms and two examples for color video encryption and decryption using the obtained results of system (1). To the best of our knowledge, a substantial body of excellent work has been dedicated to the encryption and decryption of color images. For instance, Feng et al. [32,33,34,35] have put forward numerous effective algorithms for color image encryption and decryption. Kong et al. [36] realized image encryption on a Field-Programmable Gate Array (FPGA). Similarly, Yu et al. [37] developed a system that was implemented on an FPGA digital hardware platform. Moving forward, we will concentrate on some systems of tensor equations over the split quaternion algebra and delve deeper into the study of encryption and decryption.
Author Contributions
Methodology, Z.-R.J. and Q.-W.W.; Software, Z.-R.J.; Investigation, Q.-W.W.; Writing—original draft, Z.-R.J.; Writing—review and editing, Q.-W.W.; Supervision, Q.-W.W.; Funding acquisition, Q.-W.W. All authors have read and agreed to the published version of the manuscript.
Funding
This research is supported by the National Natural Science Foundation of China (No. 12371023).
Data Availability Statement
Data are contained within the article.
Conflicts of Interest
The authors declare that the research was conducted in the absence of any commercial or financial relationships that could be constructed as a conflict of interest.
References
- Hamilton, W.R. Lectures on Quaternions; Hodges and Smith: Dublin, Ireland, 1853. [Google Scholar]
- Took, C.C.; Mandic, D.P. Augmented second-order statistics of quaternion random signals. Signal Process. 2011, 91, 214–224. [Google Scholar] [CrossRef]
- Miao, J.; Kou, K.I. Color image recovery using low-rank quaternion matrix completion algorithm. IEEE Trans. Image Process. 2021, 31, 190–201. [Google Scholar] [CrossRef]
- Jia, Z.G.; Ling, S.T.; Zhao, M.X. Color two-dimensional principal component analysis for face recognition based on quaternion model. In Intelligent Computing Theories and Application: Proceedings of the 13th International Conference, Liverpool, UK, 7–10 August 2017; Springer: Cham, Switzerland, 2017; pp. 177–189. [Google Scholar] [CrossRef]
- Cockle, J. LII. On systems of algebra involving more than one imaginary; and on equations of the fifth degree. Lond. Edinb. Dublin Philos. Mag. J. Sci. 1849, 35, 434–437. [Google Scholar] [CrossRef]
- Adler, S.L. Quaternionic Quantum Mechanics and Quantum Fields; Oxford University Press: Cary, NC, USA, 1995. [Google Scholar]
- Shoemake, K. Animating rotation with quaternion curves. ACM SIGGRAPH Comput. Graph. 1985, 19, 245–254. [Google Scholar] [CrossRef]
- Antonelli, G.; Chiaverini, S. Fault tolerant kinematic control of platoons of autonomous vehicles. IEEE Int. Conf. Robot. Autom. 2004, 4, 3313–3318. [Google Scholar] [CrossRef]
- Krizhevsky, A.; Sutskever, I.; Hinton, G.E. Imagenet classification with deep convolutional neural networks. Commun. ACM 2017, 60, 84–90. [Google Scholar] [CrossRef]
- Carroll, S.M. Spacetime and Geometry: An Introduction to General Relativity, 2nd ed.; Cambridge University Press: Cambridge, UK, 2019. [Google Scholar]
- Griffiths, D.J.; Heald, M.A. Introduction to Electrodynamics, 4th ed.; Cambridge University Press: Cambridge, UK, 2013. [Google Scholar]
- Abadi, M.; Barham, P.; Chen, J.; Chen, Z.; Davis, A.; Dean, J.; Zheng, X. Tensorflow: A system for large-scale machine learning. In 12th USENIX Symposium on Operating Systems Design and Implementation, OSDI 16; USENIX Association: Savannah, GA, USA, 2016; pp. 265–283. [Google Scholar]
- Paszke, A.; Gross, S.; Massa, F.; Lerer, A.; Bradbury, J.; Chanan, G.; Chintala, S. Pytorch: An imperative style, high-performance deep learning library. Adv. Neural Inf. Process. Syst. 2019, 32, 8026–8037. [Google Scholar]
- Zhang, S.; Yao, L.; Sun, A.; Tay, Y. Deep learning based recommender system: A survey and new perspectives. ACM Comput. Surv. 2019, 52, 1–38. [Google Scholar] [CrossRef]
- Qi, L.Q.; Luo, Z.Y. Tensor Analysis: Spectral Theory and Special Tensors; Society for Industrial & Applied Mathematics: Philadelphia, PA, USA, 2017. [Google Scholar]
- Qi, L.Q. Tensor Eigenvalues and Their Applications; Springer Nature: Singapore, 2018. [Google Scholar]
- Ding, W.Y.; Luo, Z.Y.; Qi, L.Q. P-tensors, P0-tensors, and their applications. Linear Algebra Appl. 2018, 555, 336. [Google Scholar] [CrossRef]
- He, Z.H.; Wang, X.X.; Zhao, Y.F. Eigenvalues of quaternion tensors with applications to color video processing. J. Sci. Comput. 2023, 94, 1. [Google Scholar] [CrossRef]
- He, Z.H.; Liu, T.T.; Wang, X.X. Eigenvalues of quaternion tensors: Properties, algorithms and applications. Adv. Appl. Clifford Algebr. 2025, 35, 4. [Google Scholar] [CrossRef]
- Zhang, X.F.; Zhang, W.D.; Li, T. Tensor form of GPBiCG algorithm for solving the generalized Sylvester quaternion tensor equations. J. Franklin Inst. 2023, 360, 5929–5946. [Google Scholar] [CrossRef]
- Zhang, X.F.; Li, T.; Ou, Y.G. Iterative solutions of generalized sylvester quaternion tensor equations. Linear Multilinear Algebra 2023, 72, 1259–1278. [Google Scholar] [CrossRef]
- Gao, Z.H.; Wang, Q.W.; Xie, L.M. The (anti-)η-hermitian solution to a novel system of matrix equations over the split quaternion algebra. Math. Methods Appl. Sci. 2024, 47, 13896–13913. [Google Scholar] [CrossRef]
- Xie, M.Y.; Wang, Q.W.; Zhang, Y. The BiCG algorithm for solving the minimal frobenius norm solution of generalized sylvester tensor equation over the quaternions. Symmetry 2024, 16, 1167. [Google Scholar] [CrossRef]
- Yang, L.Q.; Wang, Q.W.; Kou, Z. A system of tensor equations over the dual split quaternion algebra with an application. Mathematics 2024, 12, 3571. [Google Scholar] [CrossRef]
- Sun, L.Z.; Zheng, B.D.; Bu, C.J.; Wei, Y.M. Moore–Penrose inverse of tensors via Einstein product. Linear Multilinear Algebra 2016, 64, 686–698. [Google Scholar] [CrossRef]
- Liu, T.T.; Yu, S.W. Some properties of reduced biquaternion tensors. Symmetry 2024, 16, 1260. [Google Scholar] [CrossRef]
- Yuan, S.F.; Wang, Q.W.; Yu, Y.B.; Tian, Y. On hermitian solutions of the split quaternion matrix equation AXB + CXD = E. Adv. Appl. Clifford Algebras 2017, 27, 3235–3252. [Google Scholar] [CrossRef]
- Ben-Israel, A.; Greville, T.N.E. Generalized Inverses: Theory and Applications; Springer Science & Business Media: New York, NY, USA, 2006. [Google Scholar]
- Magnus, J.R. L-structured matrices and linear matrix equations. Linear Multilinear Algebra 1983, 14, 67–88. [Google Scholar] [CrossRef]
- Xie, L.M.; Wang, Q.W. A system of matrix equations over the commutative quaternion ring. Filomat 2023, 37, 97–106. [Google Scholar] [CrossRef]
- Sara, U.; Akter, M.; Uddin, M.S. Image quality assessment through FSIM, SSIM, MSE and PSNR-a comparative study. J. Comput. Commun. 2019, 7, 8–18. [Google Scholar] [CrossRef]
- Feng, W.; Zhang, J.; Qin, Z.T. A secure and efficient image transmission scheme based on two chaotic maps. Complexity 2021, 2021, 1898998. [Google Scholar] [CrossRef]
- Feng, W.; Zhao, X.Y.; Zhang, J.; Qin, Z.T.; Zhang, J.K.; He, Y.G. Image encryption algorithm based on plane-level image filtering and discrete logarithmic transform. Mathematics 2022, 10, 2751. [Google Scholar] [CrossRef]
- Feng, W.; Yang, J.X.; Zhao, X.Y.; Qin, Z.T.; Zhang, J.; Zhu, Z.G.; Wen, H.P.; Qian, K. A novel multi-channel image encryption algorithm leveraging pixel reorganization and hyperchaotic maps. Mathematics 2024, 12, 3917. [Google Scholar] [CrossRef]
- Feng, W.; Zhang, J.; Chen, Y.; Qin, Z.T.; Zhang, Y.S.; Ahmad, M.; Woźniak, M. Exploiting robust quadratic polynomial hyperchaotic map and pixel fusion strategy for efficient image encryption. Expert Syst. Appl. 2024, 246, 123190. [Google Scholar] [CrossRef]
- Kong, X.X.; Yu, F.; Yao, W.; Cai, S.; Zhang, J.; Lin, H.R. Memristor-induced hyperchaos, multiscroll and extreme multistability in fractional-order HNN: Image encryption and FPGA implementation. IEEE Trans. Neural Netw. 2024, 171, 85–103. [Google Scholar] [CrossRef]
- Yu, F.; Lin, Y.; Yao, W.; Cai, S.; Lin, H.R.; Li, Y. Multiscroll hopfield neural network with extreme multistability and its application in video encryption for IIoT. IEEE Trans. Neural Netw. 2025, 182, 106904. [Google Scholar] [CrossRef] [PubMed]
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).