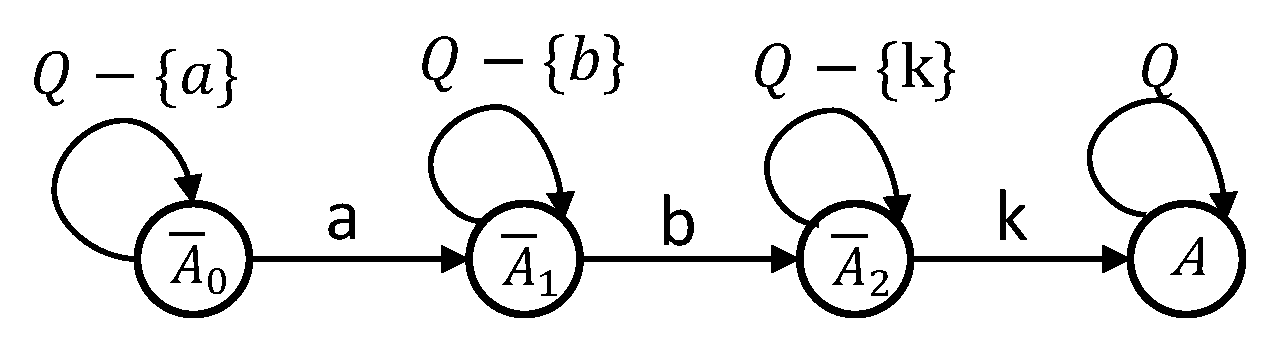Survey and Future Trends for Cybersecurity in Maritime and Port Sectors: A Discrete Event Systems Perspective
Abstract
1. Introduction
- Identifying vulnerabilities: assessing all components, including hardware, software, and network configurations, to identify potential weaknesses that could be targeted by cyber attacks.
- Assessing risk impact: evaluating the potential impact of identified vulnerabilities on the CIA of critical maritime and port systems.
- Prioritizing vulnerabilities: ranking vulnerabilities based on their severity and the likelihood of exploitation, allowing for targeted mitigation efforts.
- Mitigation and protection: implementing security measures, such as patch management, intrusion detection systems, and network segmentation, to reduce the risk of vulnerabilities being exploited.
- Continuous monitoring: regularly updating vulnerability analysis to adapt to new threats and changes in the technology landscape to ensure that the maritime and port sectors remain resilient against evolving cyber risks.
2. Architectures of On-Vessel and In-Port Communication Systems
3. Cyber Attacks in the Maritime and Port Domains
- Cyber incident: A cyber incident is an occurrence that actually or potentially results in adverse consequences to an onboard system, network, and computer or the information that they process, store, or transmit, and which may require a response action to mitigate the consequences (https://www.bimco.org/about-us-and-our-members/publications/the-guidelines-on-cybersecurity-onboard-ships, accessed on 7 July 2025).
- Cyber attack: any type of offensive maneuver that targets Information Technology (IT) and Operational Technology (OT) systems, computer networks, and/or personal computer devices attempting to compromise, destroy, or access company and ship systems and data.
- Confidentiality: Confidentiality of the data represents the use of sensitive and confidential information by authorized personnel only and provides the security mechanisms to maintain the privacy of the data and system.
- Integrity: Integrity refers to the protection of valuable information and data from external and internal actors during daily system use.
- Availability: Availability permits immediate access of authorized personnel to information and data for normal operation or in dangerous situations, providing independence for the company in terms of using its resources.
3.1. Main Types of Cyber Attacks
- AIS: Since 2002, AIS has been mandatory for all passenger and sea-going vessels with 300 gross tonnage or more. It is a tool for vessel safety, collision avoidance, and ship monitoring, providing vessel information and status. Course, speed, and position are some of the information displayed in the AIS for the safety and security of vessel operations. However, the exposure of the AIS, concerning connectivity and information providers, represents a high risk for vessel operations. If the AIS is attacked, the consequences in terms of communication interconnectivity with ship-to-ship, ship-to-shore, and shore-to-ship can be significant. Furthermore, it has been proven that the AIS does not have the necessary security measures integrated, exposing it to cyber attacks. For example, it is possible to deactivate and manipulate the AIS information to create a false collision or SAR alert.In a series of events in 2017, numerous vessels in the Black Sea reported their GPS positions being spoofed, causing them to display incorrect locations. Some ships showed their locations as being on land, while others appeared to be far from their actual positions. This raised concerns about the vulnerability of both GPS and AIS systems to cyber attacks and manipulation (https://maritime-executive.com/editorials/mass-gps-spoofing-attack-in-black-sea (accessed on 23 July 2025)). In particular, in 2017, the British Royal Navy’s destroyer HMS Defender was reportedly involved in an AIS spoofing incident while navigating near Crimea, in the Black Sea (https://www.euronews.com/next/2021/06/28/hms-defender-ais-spoofing-is-opening-up-a-new-front-in-the-war-on-reality (accessed on 23 July 2025)). In 2019 and 2020, there were reports of “phantom fleets” in the South China Sea and off the coast of South America. AIS data indicated the presence of fleets of ships that did not actually exist, likely created through spoofing. These ghost ships were used to mask illegal fishing operations or the movement of sanctioned oil cargoes, highlighting how AIS manipulation could facilitate illicit activities.
- Navigation systems: by emitting false or misleading signals that overlap with the ship’s true position or indicating fake emergencies. This risk is increased by the growing reliance on technologies that control navigation, cargoes, etc., and by systems such as dynamic positioning, ship-to-shore interfaces, propulsion controls, cargo valve actuators, and passenger-boarding systems.There exist several cases of navigation system attacks [52]. In 2013, the University of Texas demonstrated the possibility of attacking the navigation systems by taking control of a yacht by spoofing its GPS (https://newatlas.com/gps-spoofing-yacht-control/28644/, accessed 25 July 2025). In 2014 and 2017, ships were fooled in a GPS spoofing attack, suggesting a Russian cyberweapon (https://maritime-executive.com/editorials/mass-gps-spoofing-attack-in-black-sea, accessed on 25 July 2025, https://www.newscientist.com/article/2143499-ships-fooled-in-gps-spoofing-attack-suggest-russian-cyberweapon/, accessed on 25 July 2025). In 2016, cyber threats prompted the return of radio for ship navigation (https://www.reuters.com/article/us-shipping-gpscyber-idUSKBN1AN0HT/, accessed on 25 July 2025). In February 2017, hackers reportedly took control of the navigation systems of a German-owned 8250 TEU container vessel en route from Cyprus to Djibouti for hours (https://rntfnd.org/2017/11/25/hackers-took-full-control-of-container-ships-navigation-systems-for-10-hours-ihs-fairplay/, accessed on 25 July 2025).
3.2. Literature Review on Cybersecurity in Maritime and Port Sectors
3.3. Consequences of Cyber Attacks and Cybersecurity Mitigation Guidelines
- Safety impact: Cyber attacks pose significant threats to safety in the maritime and port industries. Modern ships and ports rely heavily on automated and digital systems, such as navigation, communication, and cargo management systems. If these systems are compromised by hackers, it could result in vessels losing control, navigating incorrectly, or even colliding with other ships, endangering the lives of crew and passengers.For example, in 2017, the global shipping giant Maersk was hit by the NotPetya cyber attack. This attack crippled their IT systems, causing severe disruptions in their ability to operate and schedule vessels, thereby affecting the global shipping network’s safety. While no direct collisions were reported, the incident exposed vulnerabilities that could lead to serious safety risks.
- Environmental impact: Cyber attacks can lead to catastrophic environmental disasters, especially when hazardous materials are involved. If attackers gain control of a ship’s navigation or control systems, they could cause the vessel to run aground or collide in environmentally sensitive areas, leading to oil spills, chemical leaks, and other environmental catastrophes.For example, in 2010, the Stuxnet worm, although primarily targeting nuclear facilities, demonstrated the potential for widespread damage if similar attacks were directed at maritime operations. In particular, a cyber attack on a vessel carrying hazardous chemicals could result in the ship grounding in a fragile marine ecosystem, causing significant environmental harm.
- Economic impact: The economic impact of cyber attacks on maritime and port operations can be devastating. Ports and shipping companies are critical nodes in global trade, and a cyber attack could lead to cargo delays, supply chain disruptions, and substantial financial losses. Additionally, the cost of restoring compromised systems and addressing security vulnerabilities can be significant.For example, in 2020, CMA CGM Group suffered a ransomware attack that disrupted its online systems, preventing customers from booking cargo shipments and severely interrupting the logistics chain. This incident not only resulted in direct financial losses for CMA CGM but also affected the stability of global supply chains, highlighting the far-reaching economic impact of cyber attacks.
| Ref. | Year | Title | Comments |
|---|---|---|---|
| [4] | 2025 | Port resilience: a systematic literature review | This paper systematically reviews research on port resilience, examining definitions, frameworks, and key influencing factors. It identifies gaps such as fragmented approaches and limited empirical studies and proposes directions for future research to enhance port resilience. |
| [34] | 2024 | Maritime autonomous surface ships: a review of cybersecurity challenges, countermeasures, and future perspectives | This paper reviews cybersecurity threats and defenses for maritime autonomous surface ships, highlighting AIS/GPS vulnerabilities and proposing multi-layer protections integrating IMO frameworks. It explores AI, blockchain, and behavior analytics to enhance maritime autonomous surface ship resilience. |
| [5] | 2024 | Blockchain implementation in the maritime industry: a literature review and synthesis analysis of benefits and challenges | This paper reviews blockchain applications in maritime logistics, highlighting its potential to improve transparency, traceability, and efficiency, while addressing challenges in standardization, scalability, and regulatory compliance, and exploring integration with IoT and AI. |
| [27] | 2024 | Maritime cybersecurity: A comprehensive review | A comprehensive survey of maritime cybersecurity, analyzing threats, incidents, countermeasures, and challenges across vessels, ports, and the global maritime supply chain to guide resilience and future research. |
| [54] | 2024 | Port cyber attacks from 2011 to 2023: a literature review and discussion of selected cases | This paper analyzes 15 cases showing that ransomware and disruption are the main motives. Weak procedures and low awareness increase risks, while timely detection, collaboration, and comprehensive disaster plans are crucial for resilience. |
| [55] | 2023 | Cyber-seaworthiness: a critical review of the literature | It reviews maritime cyber risks and policy frameworks, introducing the concept of “cyber-seaworthiness” to address rising threats from digitization and autonomous ships and to guide future industry, legal, and policy developments. |
| [56] | 2023 | Maritime cybersecurity threats: gaps and directions for future research | It examines maritime cybersecurity, identifying major research gaps, policy needs, and priorities, including the lack of real-time attack data, limited economic impact studies, inadequate professional training, and insufficient legal frameworks. |
| [57] | 2023 | Literature review on maritime cybersecurity: state-of-the-art | It reviews maritime cybersecurity research, noting current work is mostly conceptual and qualitative. It calls for quantitative methods and interdisciplinary collaboration to address complex cyber attacks and strengthen industry resilience. |
| [58] | 2023 | A survey on cybersecurity threats in the IoT-enabled maritime industry | This paper reviews the applications of IoT in the maritime industry and the major cybersecurity threats it faces, including attack types, vulnerabilities, and potential impacts. It also discusses the limitations of existing protection measures and suggests directions for future research and improvement. |
| [59] | 2022 | Cybersecurity challenges in the maritime sector | The paper maps key cybersecurity challenges in the maritime sector, but its analysis is mostly descriptive, lacking quantitative depth and concrete mitigation strategies. It usefully outlines vulnerabilities and gaps, yet more empirical and actionable research is needed. |
| [60] | 2022 | Developments and research directions in maritime cybersecurity: a systematic literature review and bibliometric analysis | The paper analyzes cybersecurity risks in the maritime industry’s digital transformation and highlights vulnerabilities in shipping and ports. It calls for stronger defenses through policies, technology, and training. |
| [61] | 2022 | Digital transformation of the maritime industry: a cybersecurity systemic approach | The paper proposes a systemic approach to maritime cybersecurity, stressing coordination across technology, organization, and policy. It argues that only a holistic governance framework can handle the evolving threat landscape. |
| [62] | 2022 | Review of ship information security risks and safety of maritime transportation issues | The paper reviews ship information security risks under digitalization, highlighting system vulnerabilities and cargo threats. It proposes risk assessment methods and stresses multilayered cyber resilience. |
| [39] | 2022 | Cyber security in the maritime industry: a systematic survey of recent advances and future trends | The paper outlines key cybersecurity challenges in maritime, stressing vulnerabilities in critical systems. It calls for regulation, technology, and training to strengthen defense. |
| [63] | 2021 | Maritime cybersecurity: a global challenge tackled through distinct regional approaches | This paper discusses maritime cybersecurity as a global challenge, analyzing IMO initiatives and regional responses in Europe and Asia. It highlights international cooperation and harmonized standards as key to strengthening overall industry cybersecurity. |
| Ref. | Year | Title | Comments |
|---|---|---|---|
| [3] | 2020 | Internet of ships: a survey on architectures, emerging applications, and challenges | This paper surveys the architectures, key technologies, and emerging applications of the Internet of Ships, highlighting its roles in smart shipping, port management, and maritime safety. It also identifies major challenges such as standardization, security, data processing, and cross-domain integration. |
| [2] | 2020 | Innovation and maritime transport: a systematic review | This paper reviews innovation research in maritime transport, summarizing types of innovation, driving factors, and their impact on the industry. It also points out that existing studies are fragmented and lack empirical evidence and proposes future research directions. |
| [64] | 2019 | Cybersecurity in the maritime industry: a literature review | This paper reviews maritime cybersecurity, highlighting incidents and key threats such as poor training, outdated IT, hacker targeting, and phishing. It proposes countermeasures including cybersecurity processes, training, system upgrades, and a stronger security culture. |
| [65] | 2019 | Evaluating cybersecurity risks in the maritime industry: a literature review | This paper surveys maritime cybersecurity, identifying key threats including lack of training and experts, outdated systems, and hacker targeting, and proposing mitigation strategies such as process development, training, regular system updates, and fostering a cybersecurity culture. |
| [66] | 2018 | Cyber attacks on ships: a wicked problem approach | This paper analyzes cyber attacks on ships as a “wicked problem,” emphasizing their complexity, unpredictability, and severe consequences for safety and operations. It highlights the urgent need for holistic, adaptive approaches to improve maritime cybersecurity resilience. |
| [67] | 2018 | Models and computational algorithms for maritime risk analysis: a review | This paper reviews models and computational algorithms for maritime risk analysis, covering probabilistic, simulation-based, and data-driven approaches. It identifies strengths and limitations of existing methods and suggests future research directions for improving maritime safety and decision-making. |
| [68] | 2018 | The global maritime industry remains unprepared for future cybersecurity challenges | This paper finds the maritime industry highly vulnerable to cyber attacks due to digital reliance, outdated systems, and weak preparedness. It stresses fast-growing threats, slow regulations, and the urgent need for stronger defenses, especially for autonomous vessels. |
| [69] | 2017 | Review on cybersecurity risk assessment and evaluation and their approaches to maritime transportation | This paper reviews cybersecurity risk assessment and evaluation approaches in maritime transportation, analyzing methods such as qualitative, quantitative, and hybrid models. It also highlights their limitations and emphasizes the need for more effective frameworks tailored to the maritime sector. |
| [70] | 2016 | Safety-critical maritime infrastructure systems resilience: a critical review | This paper analyzes safety-critical maritime infrastructure systems, focusing on their operations, risks, resilience, regulations, and lessons from past incidents to enhance safety and operational resilience. |
| [25] | 2016 | Threats and impacts in maritime cybersecurity | This paper analyzes cyber threats to maritime navigation, propulsion, and cargo systems, emphasizing vulnerabilities from outdated technologies. It illustrates attack scenarios and calls for stronger security design, crew training, and resilience. |
| [71] | 2016 | Maritime security: an introduction (book) | This book introduces maritime security across ports, vessels, and cargo supply chains, addressing threats like piracy, terrorism, smuggling, and cyber attacks. It also outlines legal frameworks and response strategies for industry and government. |
| [72] | 2015 | Challenges in maritime cyber-resilience | This paper discusses challenges in achieving maritime cyber-resilience, focusing on vulnerabilities in ships, ports, and supply chains. It emphasizes gaps in awareness, regulation, and preparedness, and calls for stronger collaboration, governance, and adaptive defense strategies. |
| [73] | 2008 | Port and maritime security: a research perspective | This paper reviews port and maritime security from a research perspective, analyzing existing measures, vulnerabilities, and challenges. It highlights the need for integrated frameworks, better risk assessment methods, and closer cooperation among stakeholders to address evolving threats. |
| [74] | 2008 | Security and risk-based models in shipping and ports: review and critical analysis | This paper reviews security and risk-based models in shipping and ports, examining their methodologies, applications, and limitations. |
- International Maritime Organization (IMO): Guidelines on Maritime Cyber Risk Management (https://www.imo.org/) provide a comprehensive framework for mananaging cyber risks in the maritime sector. These guidelines are integrated into the International Safety Management (ISM) Code, which requires shipping companies to include cyber risk management in their safety management systems.
- International Maritime Bureau (IMB): Best management practices to deter piracy and enhance maritime cybersecurity (https://www.icc-ccs.org/ offer practical advice for improving cybersecurity and managing risks, particularly in relation to piracy and other maritime threats.
- Baltic and International Maritime Council (BIMCO): Guidelines on cybersecurity onboard ships (https://www.bimco.org/) provide detailed recommendations for ship owners and operators on how to implement effective cybersecurity measures onboard ships.
- International Maritime Satellite Organization (IMSO): focuses on ensuring the security of global maritime communication systems. Their guidelines (https://imso.org/) emphasize protecting maritime communication networks and systems from cyber threats.
- European Maritime Safety Agency (EMSA): offers guidelines (https://www.emsa.europa.eu/) specifically for enhancing cybersecurity in ports, focusing on protecting port facilities and operations.
- United States Coast Guard (USCG): provides a cybersecurity (https://www.uscg.mil/) framework profile for maritime (https://www.uscg.mil/) based on the NIST cybersecurity framework, offering a detailed approach to managing cyber risks in maritime operations.
3.4. Vulnerability and Analysis Tools
- the exploitation of outdated IT and OT systems that are not supported and/or depend on obsolete operating platforms;
- reliance on OT systems, which cannot be patched or installed with antivirus software because of some type approval constraints;
- the participation of various stakeholders in ship operations and chartering can result in diffuse responsibility for the IT and OT infrastructure and the vessel’s systems;
- vessels that maintain online interfaces with onshore parties and various components of the global supply chain;
- ship equipment that is remotely monitored and accessed, for example, by manufacturers or service providers;
- sharing of business-critical and commercially sensitive data with shore-based entities, such as marine terminals, stevedores, and governmental authorities;
- reliance on computer-controlled critical systems that may be unpatched or inadequately secured, impacting both the vessel’s safety and environmental safeguards;
- cyber risk management culture with potential for enhancement, such as implementing structured training programs and exercises to better define roles and responsibilities;
- various subsystems assembled by shipyards with minimal attention to cyber risk considerations.
4. DES Models for the Security of Maritime and Port Domains
4.1. Vessel Traffic Management System
- is a finite set of states, so that ;
- E is an event set, so that , where is the set of observable events and is the set of unobservables ones;
- is an alphabet of observable labels;
- is a labeling function that assigns a label to each event, and is the symbol used to notify that an event is silent;
- is a transition relation, where (, ,, ) means that there is a transition from the state to the state triggered by the event that occurs with a rate ;
- is the vector of initial state probabilities, where its entry represents the probability that the system is initially in the state .
- is the set of states;
- is the set of observable events and is the set of unobservable ones;
- is the set of labels;
- is the labeling function, where , , , , ,, , , , ,;
- , , , , , , , , , , , is the transition relation;
- is the initial state probability distribution.
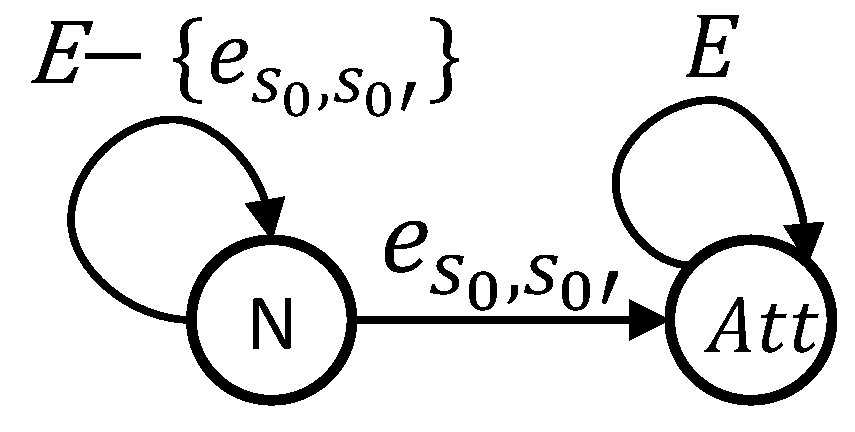
- is the set of states of the attack pattern;
- E is the set of events of the attack pattern, which is exactly the same as the set of events of the VTMS model;
- is the set of transitions of the attack pattern;
- N is the attack pattern initial state;
- is the attack pattern finale state.
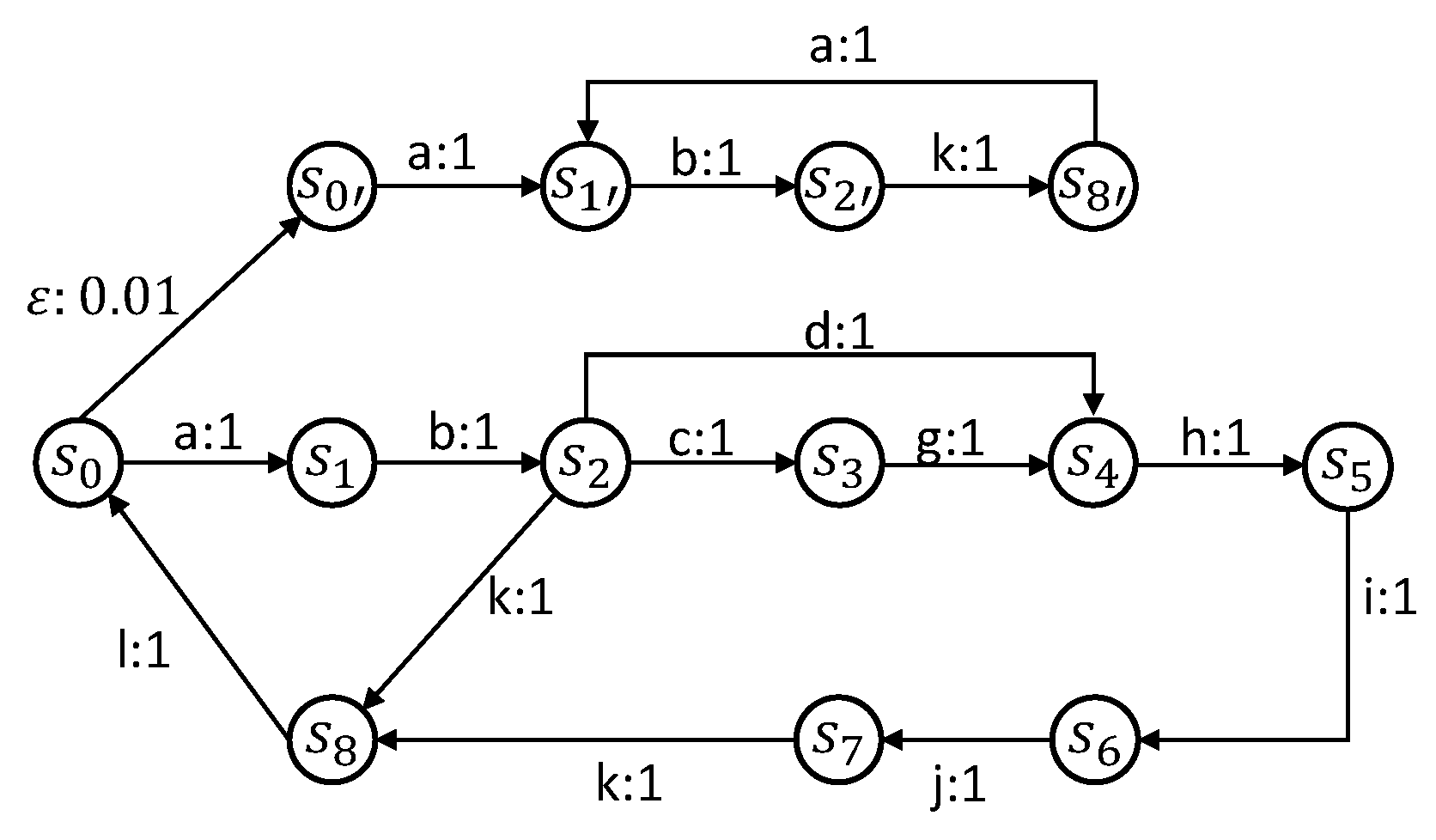
| States | Labels |
|---|---|
| No vessel in VTMS range; | A vessel entered in port neighborhood; |
| Vessel approaching port; | Request to dock; |
| Vessel authentication and waiting for authorization to dock; | Request accepted but no dock is currently available; |
| Vessel waiting the dock to be available; | Request accepted and a dock is assigned; |
| Vessel approaching port; | Authentication failed and docking refused; |
| Docking in progress; | Dock assigned; |
| Cargos loading or unloading; | Docking start; |
| Vessel departure; | Docking finished and begin of cargos loading or unloading; |
| Vessel is leaving VTMS range; | Cargos operations completed; |
| Idle state (Attack); | Vessel starts leaving VTMS range; |
| Fake vessel approaching port; | Vessel quits VTMS range; |
| Fake vessel authentication and waiting authorization to dock; | Begin of an attack. |
| Fake vessel is leaving VTMS range. |
4.2. Radar System
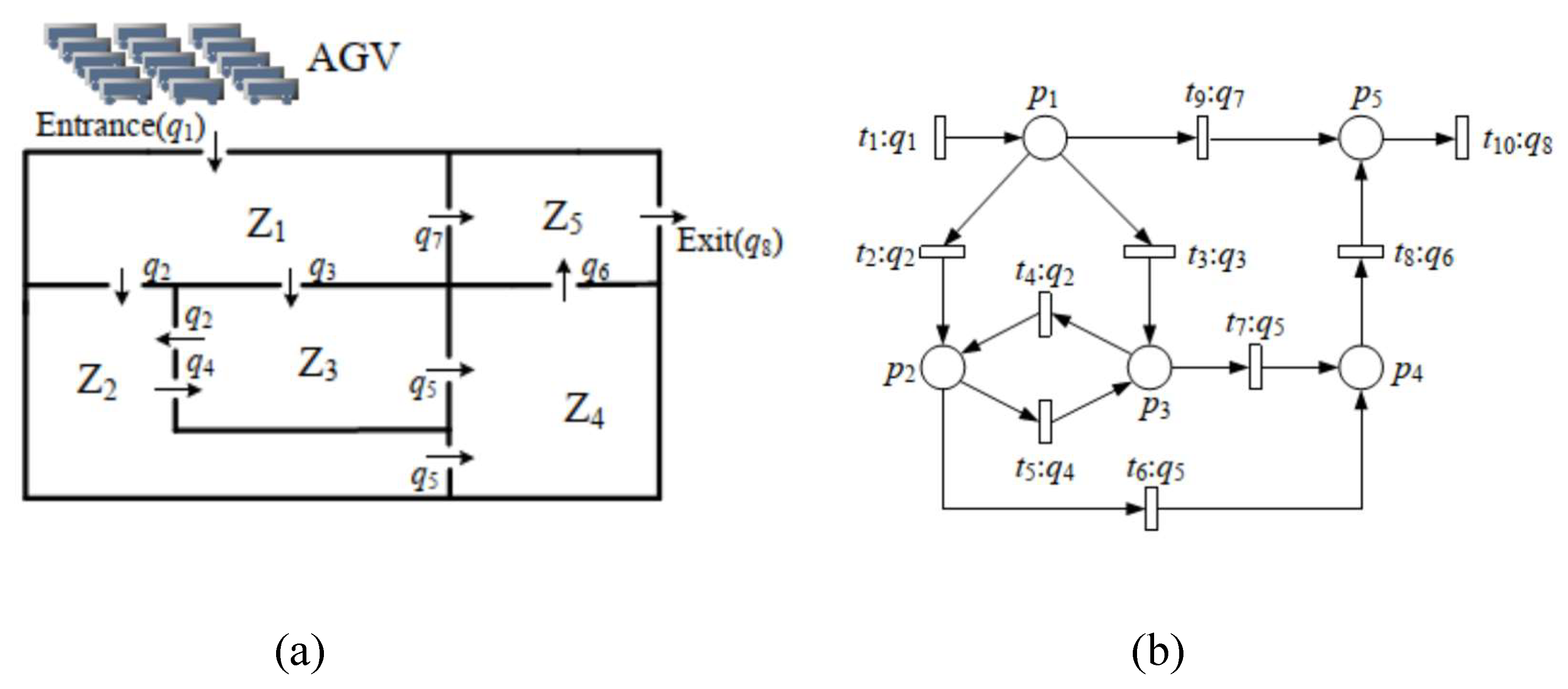
4.3. Port Automated Guided Vehicles System
5. Cybersecurity Analysis and Enforcement with DES
5.1. Security Metrics
- Shortest path: This metric is used to assess the security of a system by identifying the shortest path from the initial security state to the targeted one. Roughly speaking, it represents the least effort required by an attacker to compromise the target.
- Number of paths: This metric quantifies the number of routes an attacker can take to compromise the system. The higher the number of routes, the lower the security level, because the attacker has more opportunities to succeed.
- Mean path length metric: This metric assesses the average number of exploits an attacker needs to exploit to reach the target.
- Mean time to security failure: This metric measures the expected time an attacker needs to successfully compromise a system. Generally, it is expressed as the mean time to the first security failure.
- Steady-state security: This metric evaluates the level of security in a system in the long run i.e., as time approaches infinity.
- The type of security failure: This metric classifies the security issues. As in practice, different attack paths exist that the attacker may follow to compromise the system, i.e., an intruder can breach the security of the system with different privilege levels, and this metric is the probability of each attack path being selected.
5.2. Cybersecurity in Discrete Event Systems
5.3. Performance Evaluation with Markov Models and Probabilistic Automata
- is the set of states;
- is a set of events, which corresponds to the system set of labels;
- is the set of transitions;
- is the initial state;
- is the final state.
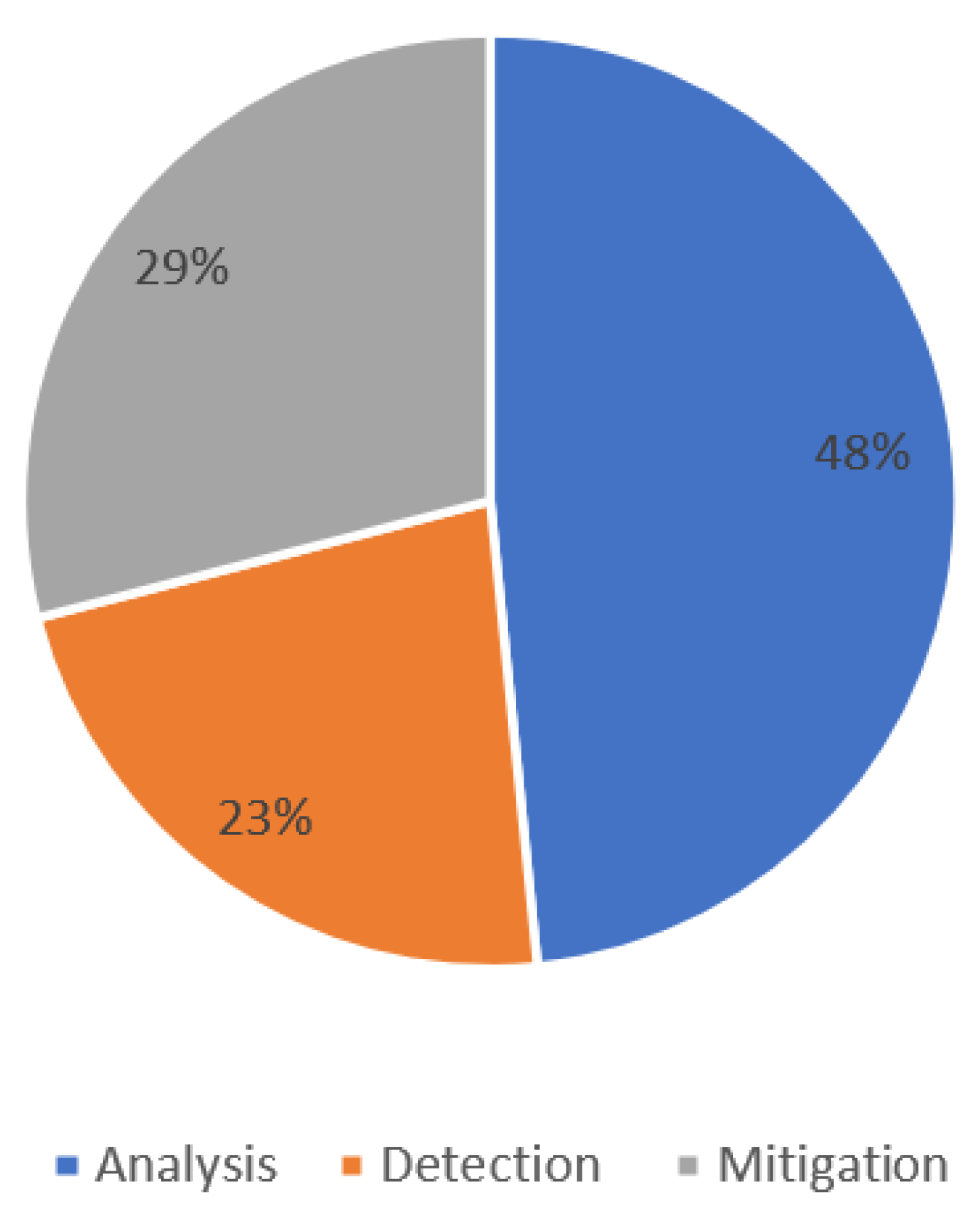
| Ref. | Year | Analysis | Detection | Mitigation | Method | Maritime |
|---|---|---|---|---|---|---|
| [119] | 2017 | ✓ | PN | ✓ | ||
| [120] | 2017 | ✓ | PN | ✓ | ||
| [5] | 2024 | Blockchain | ✓ | |||
| [102] | 2014 | ✓ | Markov | |||
| [26] | 2023 | ✓ | ✓ | ✓ | DES | |
| [121] | 2021 | ✓ | DES | |||
| [122] | 2021 | ✓ | DES | |||
| [123] | 2022 | ✓ | ✓ | ✓ | CPS | |
| [124] | 2015 | ✓ | PN | ✓ | ||
| [125] | 2023 | ✓ | PN | ✓ | ||
| [126] | 2025 | ✓ | PN | |||
| [101] | 2013 | ✓ | Markov | |||
| [127] | 2019 | ✓ | PN | ✓ | ||
| [128] | 2021 | ✓ | Automata | |||
| [129] | 2018 | ✓ | Automata | |||
| [130] | 2017 | ✓ | DES | |||
| [99] | 2022 | ✓ | DES | |||
| [131] | 2009 | ✓ | PN | |||
| [132] | 2019 | ✓ | DES | |||
| [133] | 2025 | ✓ | PN | |||
| [134] | 2025 | ✓ | PN | |||
| [135] | 2017 | ✓ | ✓ | DES | ||
| [107] | 2023 | ✓ | ✓ | Automata | ||
| [108] | 2005 | ✓ | Bayesian | |||
| [109] | 2008 | ✓ | Bayesian | |||
| [83] | 2016 | ✓ | Attack graph | |||
| [89] | 2023 | ✓ | Markov |
5.4. Security Enforcement with Petri Nets
- Step 1: (Initialization) observation: , set of forbidden transitions at :
- Step 2: (Online) Wait until a label q is observed
- Step 2.1:
- Step 2.2:
- Compute , where with refers to the number of occurrences of in
- Step 2.3:
- Disable all transitions in
6. Open Problems and Future Directions
7. Conclusions
Author Contributions
Funding
Data Availability Statement
Conflicts of Interest
References
- Trade, U.N. Review of Maritime Transport 2024: Navigating Maritime Chokepoints; United Nations: New York, NY, USA, 2024. [Google Scholar]
- Koukaki, T.; Tei, A. Innovation and maritime transport: A systematic review. Case Stud. Transp. Policy 2020, 8, 700–710. [Google Scholar] [CrossRef]
- Aslam, S.; Michaelides, M.P.; Herodotou, H. Internet of ships: A survey on architectures, emerging applications, and challenges. IEEE Internet Things J. 2020, 7, 9714–9727. [Google Scholar] [CrossRef]
- Tsoulfas, G.T. Port resilience: A systematic literature review. In Maritime Economics & Logistics; Springer: Berlin/Heidelberg, Germany, 2025; pp. 1–21. [Google Scholar]
- Li, K.; Lee, J.Y.; Gharehgozli, A. Blockchain implementation in the maritime industry: A literature review and synthesis analysis of benefits and challenges. In Maritime Economics & Logistics; Springer: Berlin/Heidelberg, Germany, 2024; pp. 1–28. [Google Scholar]
- Haugli-Sandvik, M.; Lund, M.S.; Bjørneseth, F.B. Maritime decision-makers and cybersecurity: Deck officers’ perception of cyber risks towards IT and OT systems. Int. J. Inf. Secur. 2024, 23, 1721–1739. [Google Scholar] [CrossRef]
- Yousaf, A.; Zhou, J.Y. From sinking to saving: MITRE ATT&CK and D3FEND frameworks for maritime cybersecurity. Int. J. Inf. Secur. 2024, 23, 1603–1618. [Google Scholar]
- Poza, J.L.; Simarro, R.; de la Fuente, M.A.; Simó, J.; Crespo, A. Real-time control and monitoring in a container terminal. Ifac Proc. 2002, 35, 219–224. [Google Scholar] [CrossRef]
- Aboul-Dahab, K.M.A. Demonstrating the cyber vulnerabilities of significant maritime technologies to the port facilities and on board of vessels. Inf. Technol. 2020, 29, 31. [Google Scholar] [CrossRef]
- Kanwal, K.; Shi, W.; Kontovas, C.; Yang, Z.; Chang, C.H. Maritime cybersecurity: Are onboard systems ready? Marit. Policy Manag. 2024, 51, 484–502. [Google Scholar] [CrossRef]
- Alcaide, J.I.; Llave, R.G. Critical infrastructures cybersecurity and the maritime sector. Transp. Res. Procedia 2020, 45, 547–554. [Google Scholar] [CrossRef]
- Androjna, A.; Twrdy, E. Cyber threats to maritime critical infrastructure. In Cyber Terrorism and Extremism as Threat to Critical Infrastructure Protection; Ministry of Defense, Republic of Slovenia: Ljubljana, Slovenia, 2020; pp. 163–170. [Google Scholar]
- Mraković, I.; Vojinović, R. Maritime cybersecurity analysis—How to reduce threats? Trans. Marit. Sci. 2019, 8, 132–139. [Google Scholar] [CrossRef]
- Cook, P. Comment: The emerging spectrum of maritime security. Int. J. Marit. Crime Secur. 2020, 1, 30–55. [Google Scholar] [CrossRef]
- Yan, X.; Nie, X. Optimal placement of multiple types of detectors under a small vessel attack threat to port security. TRansportation Res. Part E Logist. Transp. Rev. 2016, 93, 71–94. [Google Scholar] [CrossRef]
- Ahokas, J.; Kiiski, T.; Malmsten, J.; Ojala, L.M. Cybersecurity in ports: A conceptual approach. In Proceedings of the Hamburg International Conference of Logistics; epubli GmbH: Berlin, Germany, 2017; Volume 23, pp. 343–359. [Google Scholar]
- Meyer-Larsen, N.; Müller, R. Enhancing the cybersecurity of port community systems. In Dynamics in Logistics: Proceedings of the 6th International Conference LDIC, Bremen, Germany, 20–22 February 2018; Springer International Publishing: Cham, Switzerland, 2018; pp. 318–323. [Google Scholar]
- König, S. Understanding complex attacks on a maritime port. ERCIM News 2020, 123, 22–23. [Google Scholar]
- Gunes, B.; Kayisoglu, G.; Bolat, P. Cyber security risk assessment for sea ports: A case study of a container port. Comput. Secur. 2021, 103, 102196. [Google Scholar] [CrossRef]
- Nganga, A.; Nganya, G.; Lützhöft, M.; Mallam, S.; Scanlan, J. Bridging the gap: Enhancing maritime vessel cyber resilience through security operation centers. Sensors 2023, 24, 146. [Google Scholar] [CrossRef]
- Oruc, A.; Chowdhury, N.; Gkioulos, V. A modular cybersecurity training programme for the maritime domain. Int. J. Inf. Secur. 2024, 23, 1477–1512. [Google Scholar] [CrossRef]
- Rajaram, P.; Goh, M.; Zhou, J. Guidelines for cyber risk management in shipboard operational technology systems. J. Phys. Conf. Ser. 2022, 2311, 012002. [Google Scholar] [CrossRef]
- Göge, D.; Enge, H.C. Look-Out 2016 Maritime Domain Cyber: Risks, Threats & Future Perspectives; Lampe & Schwartze KG: Bremen, Germany, 2015. [Google Scholar]
- Lagouvardou, S. Maritime Cyber Security: Concepts, Problems and Models; Kongens Lyngby: Copenhagen, Denmark, 2018. [Google Scholar]
- Jones, K.D.; Tam, K.; Papadaki, M. Threats and Impacts in Maritime Cybersecurity; Engineering & Technology Reference: Stevenage, UK, 2016. [Google Scholar]
- Oliveira, S.; Leal, A.B.; Teixeira, M.; Lopes, Y.K. A classification of cybersecurity strategies in the context of Discrete Event Systems. Annu. Rev. Control 2023, 56, 100907. [Google Scholar] [CrossRef]
- Li, M.; Zhou, J.; Chattopadhyay, S.; Goh, M. Maritime cybersecurity: A comprehensive review. arXiv 2024, arXiv:2409.11417. [Google Scholar]
- Swiler, L.P.; Phillips, C.; Gaylor, T. A Graph-Based Network-Vulnerability Analysis System; Sandia National Lab. (SNL-NM): Albuquerque, NM, USA, 1998. [Google Scholar]
- Liu, R.T.; Hu, Y.H.; Mangini, A.M.; Fanti, M.P. K-corruption intermittent attacks for violating the codiagnosability. IEEE/CAA J. Autom. Sin. 2025, 12, 159–172. [Google Scholar] [CrossRef]
- Lhomme, S. Vulnerability and resilience of ports and maritime networks to cascading failures and targeted attacks. In Maritime Networks; Routledge: Oxford, UK, 2015; pp. 229–241. [Google Scholar]
- Ding, S.C.; Liu, G.Y.; Yin, L.; Wang, J.Z.; Li, Z.W. Detection of cyber-attacks in a discrete event system based on deep learning. Mathematics 2024, 12, 2635. [Google Scholar] [CrossRef]
- Silgado, D.M. Cyber-attacks: A Digital Threat Reality Affecting the Maritime Industry. Master’s Thesis, World Maritime University, Malmö, Sweden, 2018. [Google Scholar]
- Chang, C.H.; Kontovas, C.; Yu, Q.; Yang, Z.L. Risk assessment of the operations of maritime autonomous surface ships. Reliab. Eng. Syst. Saf. 2021, 207, 107324. [Google Scholar] [CrossRef]
- Tabish, N.; Chaur-Luh, T. Maritime autonomous surface ships: A review of cybersecurity challenges, countermeasures, and future perspectives. IEEE Access 2024, 12, 17114–17136. [Google Scholar] [CrossRef]
- Bošnjak, R.; Kezic, D.; Belamaric, G.; Krile, S. Modelling of VTS supervisor by algorithm based on Petri net: Case study of Dover incident. Transport 2021, 36, 305–316. [Google Scholar] [CrossRef]
- Bou-Harb, E.; Kaisar, E.I.; Austin, M. On the impact of empirical attack models targeting marine transportation. In 2017 5th IEEE International Conference on Models and Technologies for Intelligent Transportation Systems; IEEE: New York, NY, USA, 2017; pp. 200–205. [Google Scholar]
- Qin, T.; Yin, L.; Liu, G.Y.; Wu, N.Q.; Li, Z.W. Strong current-state opacity verification of discrete-event systems modeled with time labeled Petri nets. IEEE/CAA J. Autom. Sin. 2025, 12, 54–58. [Google Scholar] [CrossRef]
- Caprolu, M.; Di Pietro, R.; Raponi, S.; Sciancalepore, S.; Tedeschi, P. Vessels cybersecurity: Issues, challenges, and the road ahead. IEEE Commun. Mag. 2020, 58, 90–96. [Google Scholar] [CrossRef]
- Ben Farah, M.A.; Ukwandu, E.; Hindy, H.; Brosset, D.; Bures, M.; Andonovic, I.; Bellekens, X. Cyber security in the maritime industry: A systematic survey of recent advances and future trends. Information 2022, 13, 22. [Google Scholar] [CrossRef]
- Hagaseth, M.; Rødseth, Ø.J.; Krogstad, T.; Bakke, M. A new architectural framework for digitalization of maritime Intelligent transport systems. Transnav. Int. J. Mar. Navig. Saf. Sea Transp. 2023, 17, 769–779. [Google Scholar] [CrossRef]
- Balduzzi, M.; Pasta, A.; Wilhoit, K. A security evaluation of AIS automated identification system. In Proceedings of the 30th Annual Computer Security Applications Conference, New Orleans, LA, USA, 8–12 December 2014; pp. 436–445. [Google Scholar]
- DiRenzo, J.; Goward, D.A.; Roberts, F.S. The little-known challenge of maritime cybersecurity. In 6th International Conference on Information, Intelligence, Systems and Applications (IISA); IEEE: New York, NY, USA, 2015. [Google Scholar]
- Tu, E.; Zhang, G.; Rachmawati, L.; Rajabally, E.; Huang, G.B. Exploiting AIS data for intelligent maritime navigation: A comprehensive survey from data to methodology. IEEE Trans. Intell. Transp. Syst. 2017, 19, 1559–1582. [Google Scholar] [CrossRef]
- Kessler, G.C.; Craiger, J.P. A taxonomy framework for maritime cybersecurity: A demonstration using the automatic identification system. Transnav Int. J. Mar. Navig. Saf. Sea Transp. 2018, 12, 429–437. [Google Scholar] [CrossRef]
- Goudossis1, A.; Katsikas, S.K. Towards a secure automatic identification system (AIS). J. Mar. Sci. Technol. 2019, 24, 410–423. [Google Scholar] [CrossRef]
- Aziz, A.; Tedeschi, P.; Sciancalepore, S.; Di Pietro, R. Secure AIS-securing pairwise vessels communications. In 2020 IEEE Conference on Communications and Network Security; IEEE: New York, NY, USA, 2020; pp. 1–9. [Google Scholar]
- Coleman, J.; Kandah, F.; Huber, B. Behavioral model anomaly detection in automatic identification systems. In 2020 10th Annual Computing and Communication Workshop and Conference (CCWC); IEEE: New York, NY, USA, 2020; pp. 0481–0487. [Google Scholar]
- Struck, M.C.; Stoppe, J. A backwards compatible approach to authenticate automatic identification system messages. In 2021 IEEE International Conference on Cyber Security and Resilience (CSR); IEEE: New York, NY, USA, 2021; pp. 524–529. [Google Scholar]
- Leite Junior, W.C.; de Moraes, C.C.; de Albuquerque, C.E.; Machado, R.C.S.; de Sá, A.O. A triggering mechanism for cyber attacks in naval sensors and systems. Sensors 2021, 21, 3195. [Google Scholar] [CrossRef]
- Ahmed, A.; Gkioulos, V. From click to sink: Utilizing AIS for command and control in maritime cyber attacks. Lect. Notes Comput. Sci. 2022, 13556, 535–553. [Google Scholar]
- Soner, O.; Kayisoglu, G.; Bolat, P.; Tam, K. Risk sensitivity analysis of AIS cybersecurity through maritime cyber regulatory frameworks. Appl. Ocean. Res. 2024, 142, 103855. [Google Scholar] [CrossRef]
- Boudehenn, C.; Cexus, J.C.; Abdelkader, R.; Lannuzel, M.; Jacq, O.; Brosset, D.; Boudraa, A. Holistic approach of integrated navigation equipment for cybersecurity at sea. In Proceedings of the International Conference on Cybersecurity, Situational Awareness and Social Media: Cyber Science 2022; Springer Nature: Singapore, 2023; pp. 75–86. [Google Scholar]
- Tam, K.; Jones, K.D. Maritime cybersecurity policy: The scope and impact of evolving technology on international shipping. J. Cyber Policy 2018, 3, 147–164. [Google Scholar] [CrossRef]
- Senarak, C. Port cyberattacks from 2011 to 2023: A literature review and discussion of selected cases. Marit. Econ. Logist. 2024, 26, 105–130. [Google Scholar] [CrossRef]
- Schinas, O.; Metzger, D. Cyber-seaworthiness: A critical review of the literature. Mar. Policy 2023, 151, 105592. [Google Scholar] [CrossRef]
- Afenyo, M.; Caesar, L.D. Maritime cybersecurity threats: Gaps and directions for future research. Ocean. Coast. Manag. 2023, 236, 106493. [Google Scholar] [CrossRef]
- Yu, H.C.; Meng, Q.; Fang, Z.X.; Liu, J.X. Literature review on maritime cybersecurity: State-of-the-art. J. Navig. 2023, 76, 453–466. [Google Scholar] [CrossRef]
- Ashraf, I.; Park, Y.; Hur, S.; Kim, S.W.; Alroobaea, R.; Zikria, Y.B.; Nosheen, S. A survey on cybersecurity threats in IoT-enabled maritime industry. IEEE Trans. Intell. Transp. Syst. 2022, 24, 2677–2690. [Google Scholar] [CrossRef]
- Akpan, F.; Bendiab, G.; Shiaeles, S.; Karamperidis, S.; Michaloliakos, M. Cybersecurity challenges in the maritime sector. Network 2022, 2, 123–138. [Google Scholar] [CrossRef]
- Bolbot, V.; Kulkarni, K.; Brunou, P.; Banda, O.V.; Musharraf, M. Developments and research directions in maritime cybersecurity: A systematic literature review and bibliometric analysis. Int. J. Crit. Infrastruct. Prot. 2022, 39, 100571. [Google Scholar] [CrossRef]
- Kechagias, E.P.; Chatzistelios, G.; Papadopoulos, G.A.; Apostolou, P. Digital transformation of the maritime industry: A cybersecurity systemic approach. Int. J. Crit. Infrastruct. Prot. 2022, 37, 100526. [Google Scholar] [CrossRef]
- Melnyk, O.; Onyshchenko, S.; Onishchenko, O.; Shumylo, O.; Voloshyn, A.; Koskina, Y.; Volianska, Y. Review of ship information security risks and safety of maritime transportation issues. Transnav. Int. J. Mar. Navig. Saf. Sea Transp. 2022, 16, 717–722. [Google Scholar] [CrossRef]
- Karamperidis, S.; Kapalidis, C.; Watson, T. Maritime cyber security: A global challenge tackled through distinct regional approaches. J. Mar. Sci. Eng. 2021, 9, 1323. [Google Scholar] [CrossRef]
- Park, C.; Shi, W.M.; Zhang, W.; Kontovas, C.; Chang, C.H. Cybersecurity in the maritime industry: A literature review. In Proceedings of the 20th Commemorative Annual General Assembly, AGA 2019—Proceedings of the International Association of Maritime Universities Conference, Tokyo, Japan, 30 October–1 November 2019; pp. 79–86. [Google Scholar]
- Chang, C.H.; Wenming, S.; Wei, Z.; Changki, P.; Kontovas, C.A. Evaluating cybersecurity risks in the maritime industry: A literature review. In Proceedings of the International Association of Maritime Universities Conference, Tokyo, Japan, 30 October–1 November 2019. [Google Scholar]
- Mileski, J.; Clott, C.; Galvao, C.B. Cyber-attacks on ships: A wicked problem approach. Marit. Bus. Rev. 2018, 3, 414–430. [Google Scholar] [CrossRef]
- Lim, G.J.; Cho, J.; Bora, S.; Biobaku, T.; Parsaei, H. Models and computational algorithms for maritime risk analysis: A review. Ann. Oper. Res. 2018, 271, 765–786. [Google Scholar] [CrossRef]
- Forbes, V.L. The global maritime industry remains unprepared for future cybersecurity challenges. Shipbuild. Ind. 2018, 12, 42–44. [Google Scholar]
- You, B.; Zhang, Y.; Cheng, L.C. Review on cybersecurity risk assessment and evaluation and their approaches on maritime transportation. In Proceedings of the 30th Annual Conference of International Chinese Transportation Professionals Association, Houston, TX, USA, 19–21 May 2017; pp. 19–21. [Google Scholar]
- John, A.; Nwaoha, T.C. Safety critical maritime infrastructure systems resilience: A critical review. Int. J. Marit. Eng. 2016, 158. [Google Scholar] [CrossRef]
- McNicholas, M. Maritime Security: An Introduction; Butterworth-Heinemann: Oxford, UK, 2016. [Google Scholar]
- Jensen, L. Challenges in maritime cyber-resilience. Technol. Innov. Manag. Rev. 2015, 5, 35. [Google Scholar] [CrossRef]
- Helmick, J.S. Port and maritime security: A research perspective. J. Transp. Secur. 2008, 1, 15–28. [Google Scholar] [CrossRef]
- Bichou, K. Security and Risk-Based Models in Shipping and Ports: Review and Critical Analysis; OECD: Paris, France, 2008. [Google Scholar]
- Barik, M.S.; Sengupta, A.; Mazumdar, C. Attack graph generation and analysis techniques. Def. Sci. J. 2016, 66, 559. [Google Scholar] [CrossRef]
- Chukwuka, V.; Chen, Y.C.; Grijalva, S.; Mooney, V. Bad data injection attack propagation in cyber-physical power delivery systems. In 2018 Clemson University Power Systems Conference (PSC); IEEE: New York, NY, USA, 2018; pp. 1–8. [Google Scholar]
- Al-Mohannadi, H.; Mirza, Q.; Namanya, A.; Awan, I.; Cullen, A.; Disso, J. Cyber-attack modeling analysis techniques: An overview. In 2016 IEEE 4th International Conference on Future Internet of Things and Cloud Workshops (FiCloudW); IEEE: New York, NY, USA, 2016; pp. 69–76. [Google Scholar]
- Hoffmann, R.; Napiórkowski, J.; Protasowicki, T.; Stanik, J. Risk based approach in scope of cybersecurity threats and requirements. Procedia Manuf. 2020, 44, 655–662. [Google Scholar] [CrossRef]
- Yadav, T.; Rao, A.M. Technical aspects of cyber kill chain. In International Symposium on Security in Computing and Communication; Springer International Publishing: Cham, Switzerland, 2015; pp. 438–452. [Google Scholar]
- Polatidis, N.; Pavlidis, M.; Mouratidis, H. Cyber-attack path discovery in a dynamic supply chain maritime risk management system. Comput. Stand. Interfaces 2018, 56, 74–82. [Google Scholar] [CrossRef]
- Shandilya, V.; Simmons, C.B.; Shiva, S. Use of attack graphs in security systems. J. Comput. Netw. Commun. 2014, 2014, 818957. [Google Scholar] [CrossRef]
- Amri, O.; Lefebvre, D. Mode Recognition in Attack Graphs Based on Conditional State Probability. In 2023 9th International Conference on Control, Decision and Information Technologies (CoDIT); IEEE: New York, NY, USA, 2023; pp. 999–1004. [Google Scholar]
- Liu, S.C.; Liu, Y. Network security risk assessment method based on HMM and attack graph model. In 2016 17th IEEE/ACIS International Conference on Software Engineering, Artificial Intelligence, Networking and Parallel/Distributed Computing (SNPD); IEEE: New York, NY, USA, 2016; pp. 517–522. [Google Scholar]
- Schneier, B. Attack trees. J. Softw. Tools Prof. Program. 1999, 24, 21–31. [Google Scholar]
- Jhawar, R.; Lounis, K.; Mauw, S. A stochastic framework for quantitative analysis of attack-defense trees. In International Workshop on Security and Trust Management; Springer International Publishing: Cham, Switzerland, 2016; pp. 138–153. [Google Scholar]
- Lounis, K.; Ouchani, S. Modeling attack-defense trees’ countermeasures using continuous time markov chains. In International Conference on Software Engineering and Formal Methods; Springer International Publishing: Cham, Switzerland, 2020; pp. 30–42. [Google Scholar]
- Lefebvre, D.; Seatzu, C.; Hadjicostis, C.; Giua, A. Probabilistic state estimation for labeled continuous time Markov models with applications to attack detection. J. Discret. Event Syst. 2022, 32, 65–88. [Google Scholar] [CrossRef]
- Lefebvre, D.; Seatzu, C.; Hadjicostis, C.; Giua, A. Detectability notions for a class of finite labeled Markovian systems. Nonlinear Anal. Hybrid Syst. 2025, 57, 101586. [Google Scholar] [CrossRef]
- Amri, O.; Lefebvre, D. Performance evaluation of SCADA systems by means of discrete event systems. In Proceedings of the 2023 International Conference on Networking, Sensing and Control (ICNSC), Marseille, France, 25–27 October 2023; pp. 1–6. [Google Scholar]
- Amri, O.; Seatzu, C.; Giua, A.; Lefebvre, D. State estimation of timed probabilistic discrete event systems via artificial neural networks. Discret. Event. Dyn. Syst. 2025, 35, 107–135. [Google Scholar] [CrossRef]
- Wang, J.C.; Wang, J.; Zeng, Q.T.; Liu, G.Y. Formal analysis of emergency department staffing based on stochastic timed Petri net models. IFAC PapersOnLine 2020, 53, 405–410. [Google Scholar] [CrossRef]
- Meriah, R.; Barkaoui, K.; Liu, G.Y.; Driss, O.B. On modelling and evaluation of corrective and preventive maintenance policies of unreliable manufacturing systems. In Proceedings of the 2019 6th International Conference on Control, Decision and Information Technologies (CoDIT), Paris, France, 23–26 April 2019; pp. 1752–1757. [Google Scholar]
- Lefebvre, D.; Leclercq, E.; Khalij, L.; Souza de Cursi, E.; El Akchioui, N. Approximation of MTS stochastic Petri nets steady state by means of continuous Petri nets: A numerical approach. Ifac Proc. Vol. 2009, 42, 62–67. [Google Scholar] [CrossRef]
- Lefebvre, D.; Leclercq, E.; El Akchioui, N.; Souza de Cursis, E.; Khalij, L. A geometric approach for the homothetic approximation of stochastic Petri nets. Ifac Proc. Vol. 2010, 43, 235–240. [Google Scholar] [CrossRef]
- Lefebvre, D. About the stochastic and continuous Petri nets equivalence in the long run. Nonlinear Anal. Hybrid Syst. 2011, 5, 394–406. [Google Scholar] [CrossRef]
- Ould El Mehdi, S.; Bekrar, R.; Messai, N.; Leclercq, E.; Lefebvre, D.; Riera, B. Design and identification of stochastic and deterministic stochastic Petri nets. IEEE Trans. Syst. Man. Cybern. Part A Syst. Humans 2012, 42, 931–946. [Google Scholar] [CrossRef]
- Miler, R.; Bujak, A. Electronic cargo tracking systems as a part of the intelligent freight technologies. Their impact on the global integrated supply chain security and effectiveness based on the Avante system. Arch. Transp. Syst. Telemat. 2014, 7, 31–36. [Google Scholar]
- Liang, Y.; Lefebvre, D.; Li, Z.W. Polynomial-time verification of pattern diagnosability for timed discrete event systems. Inf. Sci. 2025, 706, 121997. [Google Scholar] [CrossRef]
- Li, Y.T.; Hadjicostis, C.N.; Wu, N.Q. Tamper-tolerant diagnosability under bounded or unbounded attacks. IFAC PapersOnLine 2022, 55, 52–57. [Google Scholar] [CrossRef]
- Wang, A.J.A. Information security models and metrics. In Proceedings of the 43rd annual ACM Southeast Conference, Kennesaw, GA, USA, 18–20 March 2005; Volume 2, pp. 178–184. [Google Scholar]
- Almasizadeh, J.; Azgomi, M.A. A stochastic model of attack process for the evaluation of security metrics. Comput. Netw. 2013, 57, 2159–2180. [Google Scholar] [CrossRef]
- Abraham, S.; Nair, S. Cyber security analytics: A stochastic model for security quantification using absorbing markov chains. J. Commun. 2014, 9, 899–907. [Google Scholar] [CrossRef]
- Idika, N.; Bhargava, B. Extending attack graph-based security metrics and aggregating their application. IEEE Trans. On Dependable Secur. Comput. 2012, 9, 75–85. [Google Scholar] [CrossRef]
- Zenitani, K. Attack graph analysis: An explanatory guide. Comput. Secur. 2023, 126, 103081. [Google Scholar] [CrossRef]
- Hutchins, E.M.; Cloppert, M.J.; Amin, R.M. Intelligence-driven computer network defense informed by analysis of adversary campaigns and intrusion kill chains. Lead. Issues Inf. Warf. Secur. Res. 2011, 1, 80. [Google Scholar]
- Hareide, O.S.; Jøsok, Ø.; Lund, M.S.; Ostnes, R.; Helkala, K. Enhancing navigator competence by demonstrating maritime cybersecurity. J. Navig. 2018, 71, 1025–1039. [Google Scholar] [CrossRef]
- Ammour, R.; Amari, S.; Brenner, L.; Demongodin, I.; Lefebvre, D. Robust stealthy attacks based on uncertain costs and labeled finite automata with inputs. IEEE Robot. Autom. Lett. 2023, 8, 2732–2739. [Google Scholar] [CrossRef]
- Liu, Y.; Man, H. Network vulnerability assessment using Bayesian networks. In Data Mining, Intrusion Detection, Information Assurance, and Data Networks Security; Dasarathy, B.V., Ed.; Society of Photo-Optical Instrumentation Engineers Conference Series; SPIE: Bellingham, WA, USA, 2005; Volume 5812, pp. 61–71. [Google Scholar]
- Frigault, M.; Wang, L.; Singhal, A.; Jajodia, S. Measuring network security using dynamic Bayesian network. In Proceedings of the 4th ACM Workshop on Quality of Protection, Association for Computing Machinery, New York, NY, USA, 27 October 2008; pp. 23–30. [Google Scholar]
- Mohsendokht, M.; Li, H.; Kontovas, C.; Chang, C.H.; Qu, Z.; Yang, Z. Decoding dependencies among the risk factors influencing maritime cybersecurity: Lessons learned from historical incidents in the past two decades. Ocean. Eng. 2024, 312, 119078. [Google Scholar] [CrossRef]
- Aydin, M.; Sezer, S.I.; Akyuz, E.; Gardoni, P. Improved Z-number based Bayesian Network modelling to predict cyber-attack risk for maritime autonomous surface ship (MASS). Appl. Soft Comput. 2025, 180, 113416. [Google Scholar] [CrossRef]
- Chockalingam, S.; Pieters, W.; Teixeira, A.; van Gelder, P. Bayesian network model to distinguish between intentional attacks and accidental technical failures: A case study of floodgates. Cybersecurity 2021, 4, 29. [Google Scholar] [CrossRef]
- John, A.; Yang, Z.; Riahi, R.; Wang, J. A risk assessment approach to improve the resilience of a seaport system using Bayesian networks. Ocean. Eng. 2016, 111, 136–147. [Google Scholar] [CrossRef]
- Almasizadeh, J.; Azgomi, M.A. A new method for modeling and evaluation of the probability of attacker success. In 2008 International Conference on Security Technology; IEEE: New York, NY, USA, 2008; pp. 49–53. [Google Scholar]
- Almasizadeh, J.; Azgomi, M.A. Intrusion Process Modeling for Security Quantification. In Proceedings of the 2009 International Conference on Availability, Reliability and Security, Fukuoka, Japan, 16–19 March 2009; pp. 114–121. [Google Scholar]
- Kaminska, N.; Kravtsova, L.V.; Kravtsov, H.; Zaytseva, T. Modeling ship cybersecurity using Markov chains: An educational approach. In Proceedings of the 11th Workshop on Cloud Technologies in Education, Kryvyi Rih, Ukraine, 22 December 2023; pp. 22–35. [Google Scholar]
- Carlson, L.; Navalta, D.; Nicolescu, M.; Nicolescu, M.; Woodward, G. Early classification of intent for maritime domains using multinomial hidden Markov models. Front. Artif. Intell. 2021, 4, 702153. [Google Scholar] [CrossRef] [PubMed]
- Wolsing, K.; Roepert, L.; Bauer, J.; Wehrle, K. Anomaly detection in maritime AIS tracks: A review of recent approaches. J. Mar. Sci. Eng. 2022, 10, 112. [Google Scholar] [CrossRef]
- Bošnjak, R.; Kezić, D.; Vidan, P. Methodology of synthesis of the supervisors by using Petri net. Brodogr. Teor. Praksa Brodogr. Pomor. Teh. 2017, 68, 57–66. [Google Scholar] [CrossRef][Green Version]
- Bošnjak, R.; Kezić, D.; Vidan, P.; Kavran, Z. Collision prevention in Singapore Strait by using timed Petri net. Transport 2020, 35, 273–282. [Google Scholar] [CrossRef]
- Basilio, J.C.; Hadjicostis, C.N.; Su, R. Analysis and control for resilience of discrete event systems: Fault diagnosis, opacity, and cyber security. Found. Trends Syst. Control 2021, 8, 285–443. [Google Scholar] [CrossRef]
- Ding, D.R.; Han, Q.L.; Ge, X.H.; Wang, J. Secure state estimation and control of cyber-physical systems: A survey. IEEE Trans. Syst. Man, Cybern. Syst. 2021, 51, 176–190. [Google Scholar] [CrossRef]
- Duo, W.L.; Zhou, M.C.; Abusorrah, A. A survey of cyber attacks on cyber physical systems: Recent advances and challenges. IEEE/CAA J. Autom. Sin. 2022, 9, 783–800. [Google Scholar] [CrossRef]
- Sahnoun, A.; Maamri, R. Petri net modeling dynamic context of container for risk management. In Proceedings of the 2015 IEEE/ACS 12th International Conference of Computer Systems and Applications (AICCSA), Marrakech, Morocco, 17–20 November 2015; IEEE: New York, NY, USA, 2015; pp. 1–8. [Google Scholar]
- Jalal, M.R.; Kader, A.S.A.; Hamid, M.F.A.; Kang, H.S. A stochastic Petri net-based approach for operational performance estimation of quay cranes. Qual. Reliab. Eng. Int. 2023, 39, 1660–1680. [Google Scholar] [CrossRef]
- Liu, R.T.; Mangini, A.M.; Fanti, M.P. Synthesis of optimal stealthy attacks against diagnosability in labeled Petri nets. IEEE/CAA J. Autom. Sin. 2025, 12, 1661–1672. [Google Scholar] [CrossRef]
- Maione, G.; Mangini, A.M.; Ottomanelli, M. A generalized stochastic Petri net approach for modeling activities of human operators in intermodal container terminals. IEEE Trans. Autom. Sci. Eng. 2016, 13, 1504–1516. [Google Scholar] [CrossRef]
- Lin, L.; Su, R. Synthesis of covert actuator and sensor attackers. Automatica 2021, 130, 109714. [Google Scholar] [CrossRef]
- Carvalho, L.K.; Wu, Y.C.; Kwong, R.; Lafortune, S. Detection and mitigation of classes of attacks insupervisory control systems. Automatica 2018, 97, 121–133. [Google Scholar] [CrossRef]
- Lima, P.M.; Alves, M.V.; Carvalho, L.K.; Moreira, M.V. Security against network attacks in supervisory control systems. IFAC PapersOnLine 2017, 50, 12333–12338. [Google Scholar] [CrossRef]
- Basile, F.; Chiacchio, P.; Giua, A. Suboptimal supervisory control of Petri nets in presence of uncontrollable transitions via monitor places. Automatica 2006, 42, 995–1004. [Google Scholar] [CrossRef]
- Wonham, W.M.; Cai, K. Supervisory Control of Discrete-EVENT Systems; Springer: Cham, Switzerland, 2019. [Google Scholar]
- Zhang, Z.L.; Liu, G.Y.; Lefebvre, D.; Li, Z.W. Monitor-based supervisory control of labeled Petri nets under sensor attacks. IEEE Trans. Autom. Sci. Eng. 2025, 22, 9388–9403. [Google Scholar] [CrossRef]
- Jia, J.T.; Liu, G.Y.; Li, Z.W. Supervisory Control of Cyber-Physical Systems Using Labeled Petri Nets Under Sensor and Actuator Attacks; Lecture Notes in Computer Science; Springer Nature: Berlin/Heidelberg, Germany, 2025; Volume 15466, pp. 159–173. [Google Scholar]
- Laso, P.M.; Brosset, D.; Puentes, J. Dataset of anomalies and malicious acts in a cyber-physical subsystem. Data Brief 2017, 14, 186–191. [Google Scholar] [CrossRef] [PubMed]
- Cremer, F.; Sheehan, B.; Fortmann, M.; Kia, A.N.; Mullins, M.; Murphy, F.; Materne, S. Cyber risk and cybersecurity: A systematic review of data availability. Geneva Pap. Risk Insur. Issues Pract. 2022, 47, 698. [Google Scholar] [CrossRef] [PubMed]
- Jacq, O. Détection, Analyse Contextuelle et Visualisation de Cyber-Attaques en Temps Réel: éLaboration de la Cyber Situational Awareness du Monde Maritime. Ph.D. Thesis, Ecole Nationale Supérieure Mines-Télécom Atlantique, Nantes, France, 2021. [Google Scholar]
- Pelissero, N.; Laso, P.M.; Puentes, J. Impact assessment of anomaly propagation in a naval water distribution cyber-physical system. In Proceedings of the 2021 IEEE International Conference on Cyber Security and Resilience (CSR), Rhodes, Greece, 26–28 July 2021; IEEE: Piscataway, NJ, USA, 2021; pp. 518–523. [Google Scholar]
- Bertelle, C.; Gouin, N.; Frémont, A. Maritime Ports, Supply Chains and Logistics Corridors; Taylor & Francis: Abingdon, UK, 2023. [Google Scholar]
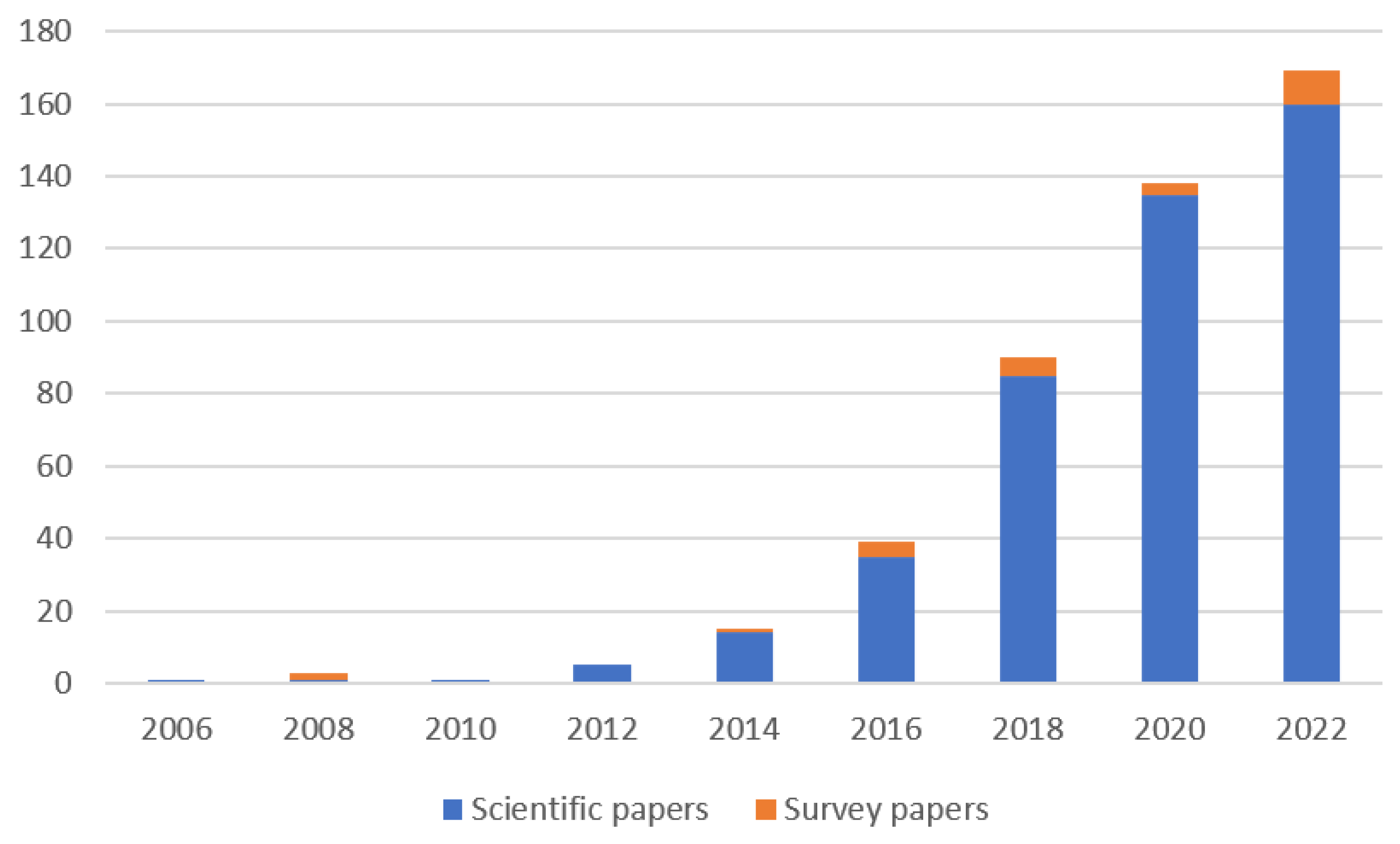
| Cyber Attack Types | Descriptions | Impacts | Past Real Cases |
|---|---|---|---|
| Malware Attacks | Involving malicious software like ransomware, viruses, or worms designed to disrupt operations, steal data, or cause damage. | These attacks can lead to system outages, data loss, and operational shutdowns. | In 2017, the global shipping giant Maersk was hit by the “NotPetya” ransomware attack, which crippled its IT systems and disrupted operations at 76 ports worldwide. 1 |
| Phishing | Using deceptive emails or messages to trick employees into revealing sensitive information or downloading malware. | These attacks lead to credential theft, unauthorized access to systems, or the spreading of malware. | In 2020, the Mediterranean Shipping Company (MSC) suffered a phishing attack where employees were tricked into clicking a malicious link from a seemingly legitimate email. 2 |
| Distributed Denial of Service (DDoS) Attacks | Overloading a port or maritime company’s servers with traffic, rendering systems and services unavailable. | These attacks cause significant delays, disrupt operations, and can lead to financial losses. | In 2024, the Port of Antwerp in Belgium was subjected to a DDoS attack that overloaded the port’s operational systems and communication networks, disrupting several operators’ activities. 3 |
| Man-in-the-Middle (MITM) Attacks | Intercepting and possibly altering communications between ships and ports or within a port’s network. | These attacks can lead to miscommunication, incorrect navigation, or unauthorized access to sensitive information. | In 2019, an Iranian port was targeted by an MITM attack, where attackers intercepted and altered communication between ships and the port. This led to ships receiving incorrect docking instructions, resulting in delays and mismanagement of cargo handling. 4 |
| Credential Theft | Stealing login credentials through phishing, brute force attacks, or social engineering. | These attacks allow attackers to access and manipulate sensitive systems, leading to data breaches or operational disruptions. | In 2020, a Danish shipping company faced a credential theft attack. Attackers obtained an employee’s login credentials and used them to access internal systems, altering shipping schedules and causing an incident that disrupted operations. 5 |
| Supply Chain Attacks | Targeting third-party suppliers of maritime systems or services to compromise the end-user systems. | These attacks can introduce vulnerabilities into navigation systems, cargo management, or other critical infrastructure. | In 2020, a navigation software supplier for several U.S. shipping companies was compromised in a supply chain attack. Hackers implanted malicious code into a software update, which then disrupted the navigation systems of multiple vessels, affecting their voyages. 6 |
| GPS Spoofing (GNSS Spoofing/AIS Spoofing) | Sending false GPS signals to mislead ships about their actual location. | These attacks cause navigation errors, potentially leading to collisions or grounding. | In 2017, vessels operating in the Black Sea reported GPS anomalies, with their navigation systems displaying incorrect locations. This was believed to be a targeted GPS spoofing attack, potentially intended to disrupt maritime traffic in the area. 7 |
| Advanced Persistent Threats (APT) | Long-term, targeted attacks often carried out by state-sponsored actors, focusing on stealth and persistence to gather intelligence or cause disruption. | These attacks can severely compromise national security, disrupt critical infrastructure, and cause significant financial damage. | In 2020, Iranian port systems were targeted by an APT attack, believed to be orchestrated by a state-sponsored group from Israel. This attack paralyzed operations at several Iranian ports, causing massive cargo backlogs and significantly impacting Iran’s maritime trade. 8 |
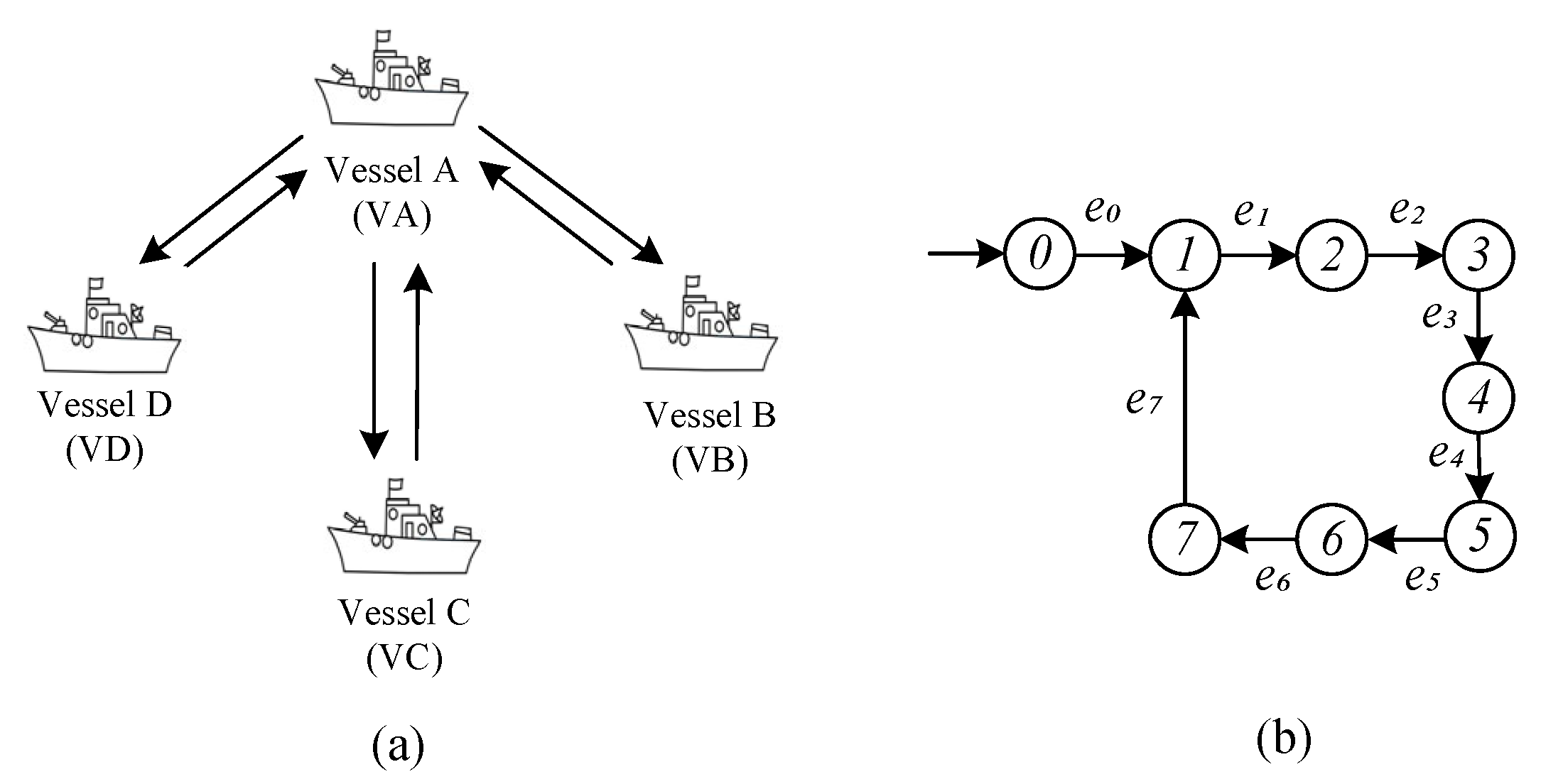
| State | Meaning of the State | Event | Meaning of the Event |
|---|---|---|---|
| 0 | All vessels are on standby, ready to commence the mission | VA initiates the reconn- aissance mission | |
| 1 | VA is on standby | VA transmits Radar signals to VB, VC, and VD | |
| 2 | VB, VC, and VD receive Radar signals from VA | VB, VC, and VD transmit Radar signals to VA | |
| 3 | VA receives Radar signals from VB, VC, and VD | VA analyzes the status of the surrounding vessels | |
| 4 | VA adjusts its own course, and completes the course correction | VA passes the token to VB | |
| 5 | VB adjusts its own course, and completes the course correction | VB passes the token to VC | |
| 6 | VC adjusts its own course, and completes the course correction | VC passes the token to VD | |
| 7 | VD adjusts its own course, and completes the course correction | VD passes the token to VA |
| Original/Attack | |||||
|---|---|---|---|---|---|
| delete | |||||
| insert |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Liu, G.; Amri, O.; Liang, Y.; Zhang, Z.; Merino Laso, P.; Bertelle, C.; Berred, A.; Lefebvre, D. Survey and Future Trends for Cybersecurity in Maritime and Port Sectors: A Discrete Event Systems Perspective. Mathematics 2025, 13, 3650. https://doi.org/10.3390/math13223650
Liu G, Amri O, Liang Y, Zhang Z, Merino Laso P, Bertelle C, Berred A, Lefebvre D. Survey and Future Trends for Cybersecurity in Maritime and Port Sectors: A Discrete Event Systems Perspective. Mathematics. 2025; 13(22):3650. https://doi.org/10.3390/math13223650
Chicago/Turabian StyleLiu, Gaiyun, Omar Amri, Ye Liang, Ziliang Zhang, Pedro Merino Laso, Cyrille Bertelle, Alexandre Berred, and Dimitri Lefebvre. 2025. "Survey and Future Trends for Cybersecurity in Maritime and Port Sectors: A Discrete Event Systems Perspective" Mathematics 13, no. 22: 3650. https://doi.org/10.3390/math13223650
APA StyleLiu, G., Amri, O., Liang, Y., Zhang, Z., Merino Laso, P., Bertelle, C., Berred, A., & Lefebvre, D. (2025). Survey and Future Trends for Cybersecurity in Maritime and Port Sectors: A Discrete Event Systems Perspective. Mathematics, 13(22), 3650. https://doi.org/10.3390/math13223650