Abstract
Numerous studies on the number pi () explore its properties, including normality and applicability. This research, grounded in two hypotheses, proposes and proves a theorem that employs a Bernoulli experiment to demonstrate the high probability of encountering any finite bit string within a sequence of consecutive bits in the decimal part of . This aligns with findings related to its normality. To support the hypotheses, we present experimental evidence about the equiprobable and independent properties of bits of , analyzing their distribution, and measuring correlations between bit strings. Additionally, from a cryptographic perspective, we evaluate the chaotic properties of two images generated using bits of . These properties are evaluated similarly to those of encrypted images, using measures of correlation and entropy, along with two hypothesis tests to confirm the uniform distribution of bits and the absence of periodic patterns. Unlike previous works that solely examine the presence of sequences, this study provides, as a corollary, a formula to calculate an upper bound N. This bound represents the length of the sequence from required to ensure the location of any n-bit string at least once, with an adjustable probability p that can be set arbitrarily close to one. To validate the formula, we identify sequences of up to 40 consecutive zeros and ones within the first N bits of . This work has potential applications in Cryptography that use the number for random sequence generation, offering insights into the number of bits of required to ensure good randomness properties.
MSC:
68Q87
1. Introduction
Throughout history, different discoveries have been made concerning the mathematical constant (pi) [1,2]. For instance, efforts have been made to find rational approximations of [3], propose methods for calculating the nth digit of [4], and compute the most accurate approximations of [5]. In addition, the significance of extends beyond mere mathematical formulas [6]. It finds applications across diverse fields, including Cryptography. Image encryption algorithms, for instance, leverage to simulate random numbers by utilizing successive decimals of [7]. This approach is valuable due to the high level of randomness inherent in the generated sequence, making it well-suited for cryptographic purposes [8]. Additionally, in cryptographic algorithms has been employed in combination with a secret key to generate permutations [9]. Furthermore, in the realm of chaos theory, a 2D chaotic map has been devised based on Euler’s number and , demonstrating hyperchaotic behavior in sequence generation [10].
In addition, investigations into the digits of have revealed patterns, such as the Feynman point, a sequence of six 9s starting from the 762nd decimal place [11]. In fact, in a normal number x in base b (where ), each of the different strings of length m occurs with equal frequency [12]. This concept is expressed mathematically as , where denotes the number of occurrences of the string s of length m in the first n digits of x. This idea has led to analyses of the normality of [13], suggesting that every possible string s eventually appears within the digits of [14].
The present study demonstrates that any bit string of length n appears with consecutive bits somewhere within , it is the first N bits to the right of the decimal point of with a probability approaching 1. In essence, it offers a formula to determine the length of a discrete interval of bit positions where a specified string occurs at least once, with an error as close to zero as desired.
The proposed upper bound contributes to the study of the normality of , a topic previously explored in other works [13,15]. By establishing such a bound, the assertion that any sequence of bits can be found within is further reinforced. This is because the bound provides an interval within which any given sequence can be located with a probability arbitrarily close to one.
Regarding the significance of this work in cryptographic applications, it can be particularly relevant for efforts that utilize the digits of to generate random sequences [9,10]. In such applications, the number of bits of used is often selected based on the algorithm’s requirements, without necessarily considering the randomness properties. The proposed upper bound can provide guidance on the number of bits needed to ensure that all possible sequences of a given length are highly likely to appear within the chosen range.
This approach minimizes the risk of omitting any specific sequence, thereby enhancing the randomness properties of the generated sequences. For instance, if is used as a source of randomness for a cryptographic application requiring the random selection of n-bit strings, the upper bound proposed in this study specifies the number N of bits that should be considered from . By using these N bits, it is highly probable that all possible n-bit sequences will be present, making a reliable source for random string generation.
Also, the present work includes a validation of the proposed formula by computing the upper bound N for various sizes of n, where a string is contained within with an error of . Beginning with a string length of , the increments progress in intervals of 5 up to . Additionally, it denotes the position within where the first bit of lies. While this investigation works on strings comprised solely of consecutive zeros or ones, it is worth noting that other combinations are also feasible.
Furthermore, this study relies on two key hypotheses in the number : the equiprobable distribution of bits and the independent events of selecting two different strings. The former asserts that when selecting a bit randomly from the bits of the decimal part of , each bit can be either zero or one, with an equal probability of 0.5. The latter hypothesis deals with the probabilistic experiment of selecting two distinct strings comprised of n and m consecutive bits, respectively, from the decimal part of . In this case, the probability of selecting the strings and is determined by the product of the probabilities of selecting each individual string: .
To validate these hypotheses, two numerical experiments will be presented as evidence in Section 3. Additionally, other studies corroborate these hypotheses. An analysis of the distribution for four trillion hexadecimal digits of was conducted [15], which later was complemented by several tests [16]. Furthermore, a hypothesis test was performed using the first 100 million decimal digits of , indicating that it is times more likely that is normal than the contrary [17].
Moreover, to substantiate the two hypotheses, we offer evidence about the chaotic distribution of information within the bits of the number . For this purpose, we employ methodologies commonly utilized in image encryption studies. Within this domain, key metrics such as entropy and the correlation coefficient serve to assess the chaotic nature of sequences. This research undertakes a comparative analysis between the outcomes derived from applying these metrics to encrypted images against those obtained from images generated by extracting blocks of random bits from the decimal part of .
Regarding the distribution of this research, this section contains the introduction and a comprehensive overview of the current state of the field. Subsequently, the theoretical framework utilized in this study is expounded upon in Section 2. Section 3 elucidates the experimental results, validating the two hypotheses posited in this investigation. In Section 4, the theorem regarding finite sequences of consecutive bits of is proven, along with establishing the upper bound for locating the strings within . Section 5 offers the analysis and discussion of the obtained results. Lastly, Section 6 encapsulates the conclusions drawn from this research.
2. Materials and Methods
This section begins by describing the Bernoulli model utilized for analyzing the bits of the number . Subsequently, encryption tools commonly employed to measure chaotic properties of information are applied to evaluate two images constructed from the bits of . These tools include correlation analysis, entropy measurement, and two hypothesis tests: the Discrete Fourier Transform and the Goodness-of-Fit test.
2.1. Bernoulli Model
In a Bernoulli test, there are only two possible outcomes: 1 and 0, where one is defined as success and the other as failure [18]. In this context, the probability of obtaining the value 1 is denoted by p, and q represents the probability of obtaining the value 0, satisfying . When there are reproduced n different trials, which are also independent of each other, the Binomial distribution is constructed [19]. In this context, the mathematical model that describes this process is in Equation (1), where x represents the number of successes after n trials for .
On the other hand, an unbiased estimator for the parameter p is expressed as .
2.2. Information Entropy
Information entropy H is a measure frequently utilized in Cryptography [20,21,22], this parameter offers insights into the level of chaos within a block of bits. It is defined in Equation (2). In this research, it serves as a key metric to apply it to consecutive bits of . However, it is essential to note that while information entropy provides essential insights, it alone does not suffice to conclusively determine the chaotic nature of the data. Hence, the assessment of chaotic properties involves the consideration of various parameters to reinforce the results.
The parameter will be utilized to assess the chaotic level of pixels within an image generated using a block of bits from the number . These images, depicted in color in Figure 1 and Figure 2, undergo segmentation into blocks of 8 bits per color for entropy computation. It is noted that information is deemed to be chaotically distributed when the entropy value approaches 8 [23].
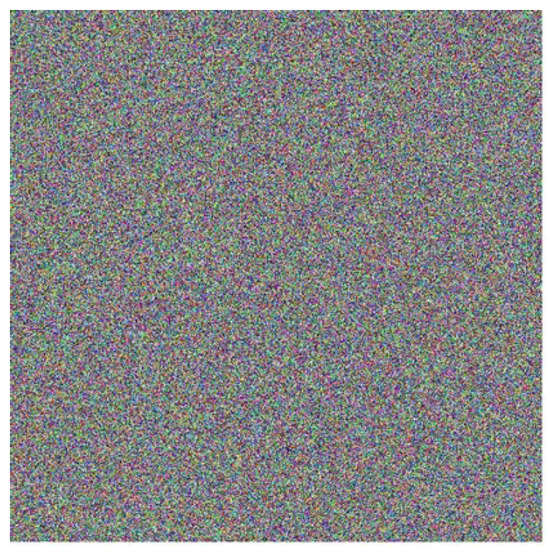
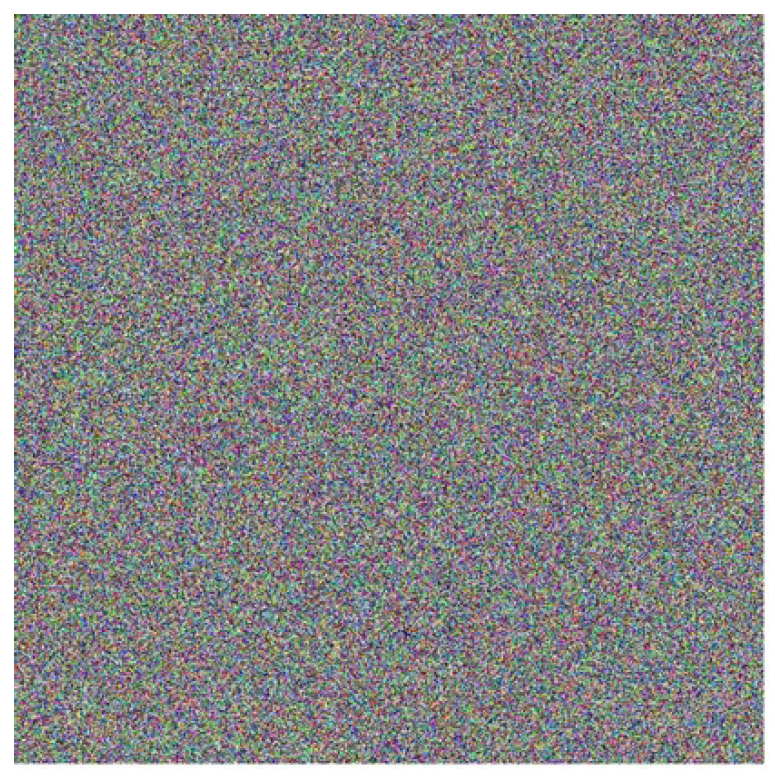
Figure 1.
Image of dimensions pixels, generated using 786,432 blocks of 8 bits randomly selected from the decimal part of . Each pixel comprises 24 bits (three blocks), representing the red, green, and blue color channels.

Figure 2.
Image of dimensions pixels, generated using 3,145,728 blocks of 8 bits randomly selected from the decimal part of . Each pixel comprises 24 bits (three blocks), representing the red, green, and blue color channels.
2.3. Correlation Coefficient
Another tool utilized to assess the absence of a linear relationship between the bits within an image is the correlation coefficient [24]. For the computation of this parameter, w pixels are haphazardly chosen from an image. Each pixel has three possible neighborhoods [25], having adjacent pixels in horizontal, vertical, and diagonal directions d. In addition, a pixel is represented with the colors c: red, green, and blue, and a byte with 256 different intensity levels.
Subsequently, the correlation for each direction d and color c is evaluated. Let the value of the ith randomly chosen pixel be denoted as , where the subscripts d and c represent the basic color direction and type, respectively. Similarly, denotes the value of the adjacent pixel in direction d and for color c. The formula to calculate it is provided in Equation (3).
where the means of each variable are as follows and .
2.4. Discrete Fourier Transform
The Discrete Fourier Transform (DFT) is used as a statistical hypothesis test that serves to assess the degree of disorder in which the bits of a string appear [26], particularly in our case, a sequence of consecutive bits from forming an image. Specifically, this parameter evaluates the presence of periodic features within a given sequence of m bits {}. In addition, the null hypothesis posits that the information in a randomly selected block of bits, sourced from the decimal part of , follows a random distribution. Within the framework of hypothesis testing the test statistic is d, presented in Equation (4) using the length m of the sequence and two constants .
For computing the constant , it is defined below in Equation (5).
Regarding , it requires the bound l, it is defined in Equation (6) and a sequence . The computation of Y is using the bits in the following manner: , for .
Additionally, it is necessary to compute complex functions , for according to Equation (7), where is the complex unit. In this way, m is the number of pixels expressed in bits and even. Subsequently, the module is computed for each function. If , 1 is added to ; otherwise, the value of does not change. It is important to note that the initial value of is zero. After comparing all the moduli, the final value of is obtained, and therefore, d can be computed.
In this context, the decision parameter of the hypothesis test is the p-value and is expressed in Equation (8). The rejection of the null hypothesis of randomness occurs when p-value ; otherwise, it is accepted.
Finally, the erfc function uses the cumulative function of the standard normal distribution as Equation (9) presents it.
2.5. Goodness-of-Fit Test
This hypothesis test has a null hypothesis positing that the information distribution is uniform [27], contrasting with the alternative hypothesis suggesting otherwise. The aim of this tool is to assess the extent to which the information in the histograms conforms to a uniform distribution. This assessment is conducted for each color channel red, green, and blue, given that every pixel in the images we employ is depicted by these colors. Each of them is defined by a byte, allowing for 256 possible decimal values. Within this framework, the test statistic is expressed in Equation (10).
Equation (10) must be applied to each color channel individually. For a specific color channel, represents the number of occurrences of intensity level i across the entire image, while exp denotes the expected frequency of each intensity level to create a uniform distribution. The expected frequency can be calculated as the total number of pixels divided by 256, which corresponds to the total number of possible intensity values in an 8-bit representation.
According to the Central Limit Theorem, the distribution of the statistic tends towards a normal distribution [28] of mean and standard deviation . Moreover, a significance level rejects the null hypothesis if ; otherwise, it is accepted.
In this work, the test is used to analyze the distribution of 8-bit blocks within the pixels. Specifically, it assesses whether the bits of the number , grouped into 8-bit blocks, exhibit a uniform distribution. This means verifying whether all 256 possible values that can be represented with 8 bits occur with approximately equal frequency.
3. Two Hypothesis Derived from Pi
In this section, the analysis is focused on the bits of the decimal expansion of . First, the distribution of bits equal to zero and one is examined. Next, the correlation between two strings of bits is analyzed, followed by an evaluation of the chaotic properties of two images constructed from the bits of . This comprehensive analysis provides further evidence supporting two hypotheses.
3.1. Equiprobable Property of Bits
This subsection will provide evidence that the bits of the number present an equiprobable distribution. In other words, if a bit is randomly selected from these bits, the probability of it being either 0 or 1 is . To verify this, eight strings of distinct length were extracted, all starting from the first bit of the decimal part of and consisting of n consecutive bits. Furthermore, the probability was assessed using the estimator mean . Table 1 presents the percentages of zeros and ones for each string. Pertinent comments will be provided in Section 5.

Table 1.
Percentage distribution of zeros and ones in strings of varying lengths extracted from the bits of . The results support the hypothesis that each bit of is equiprobable, with a 50% chance of being either zero or one.
As a result of the observations presented in Table 1, the evidence suggests a hypothesis regarding the random selection of a bit from , proposing that it can be either zero or one with an equal probability of 50%. This is stated in Hypothesis 1. However, the evidence in Table 1 is based on our analysis of up to bits of . In this way, this result aligns with other studies examining the properties of . For instance, Bailey et al. analyzed the first trillion hexadecimal digits of , reporting that each hexadecimal digit from 0 to f appears approximately the expected number of 62,500,000,000 times in a sample of 1,000,000,000,000 digits [15]. Although their study focuses on the normality of across its first four trillion hexadecimal digits, it also incorporates complementary tests on the randomness of ’s digits [16], yielding results consistent with our results.
Hypothesis 1.
The probability of being 0 or 1 is . In other words, when selecting a bit randomly from the bits to the right of π, it can have a value of either zero or one, each with a probability of 0.5.
3.2. Independence Property of Bit Strings
To provide evidence for this property, we first define the strings that will be used in a subsequent experiment. Let represent a string of n bits, where denotes the first bit, located immediately to the right of the decimal point in the number . More generally, a string of length n starting at the i-th bit to the right of the decimal point in is represented as . For instance, following this notation, we have , and the sequence continues to generate , , up to .
Using these strings, an experiment is conducted to measure the correlation coefficient between pairs of strings. Specifically, the correlations are computed between and , and , and , and so on. This test is performed for four different string lengths (n), and the results are summarized in Table 2.

Table 2.
Correlation coefficients between pairs of string and shifted strings , for four lengths n, derived from ’s digits. Values near 0 suggest independence, with correlations decreasing as string length n increases.
A correlation value close to 0, as the values reported in Table 2, between two strings ( and ) derived from the digits of , indicates the absence of a relationship between them and, therefore, suggests independence. Additionally, as the string length n increases, the linear correlation approaches zero, further reinforcing their independence.
To provide additional support for the hypothesis of independence between different strings from , in addition to the correlation coefficient analysis, other independence tests commonly applied to encrypted images were reproduced. For this purpose, two color images were created by selecting blocks of 8 consecutive bits randomly from the decimal expansion of . The first image, shown in Figure 1, has dimensions of pixels, while the second, shown in Figure 2, has dimensions of pixels.
Regarding the construction of these images, as they are color images, each pixel consists of 24 bits (8 bits per color channel: red, green, and blue). Thus, the creation of a single pixel requires three blocks of 8 bits. For this work, the 8-bit blocks were selected randomly from the digits of . To generate the pixels in Figure 1, a total of 786,432 bytes were extracted from (calculated as ). Similarly, for Figure 2, which contains pixels, 3,145,728 bytes were utilized.
After creating the images, we evaluated them using four parameters similar to those employed in analyzing encrypted images [29,30]. These methods assess the degree of chaos in the information and the relationships between pixels. In this case, they were applied to Figure 1 and Figure 2 to evaluate the chaotic nature of the corresponding bits (represented by pixels and derived from the digits of ) in both figures.
In this case, the tests were applied to Figure 1 and Figure 2 to evaluate the chaotic nature of the corresponding bits (represented by pixels and derived from the digits of ) in both images. Additionally, conducting this analysis in such a manner implicitly involves analyzing the bits of in 8-bit blocks rather than solely in binary form, as it was shown in Table 1 and Table 2. This is feasible because the evaluation of the images is performed per color channel for each pixel, which, as previously explained, comprises 8 bits.
The parameters analyzed include entropy and the correlation coefficient between adjacent pixels in three directions (horizontal, vertical, and diagonal) for each primary color. The results of these evaluations are summarized in Table 3.

Table 3.
Entropy and correlation coefficients for adjacent pixels in three directions (horizontal, vertical, and diagonal) for each primary color, derived from ’s bits in Figure 1 and Figure 2. Entropy values near indicate uniform distribution, while near-zero correlations suggest independence between adjacent pixels.
From the data in Table 3, it is shown that the entropy values are close to the ideal value of , indicating that the 256 possible values representing a pixel’s color channel occur with nearly uniform frequency. This observation supports the equiprobable distribution of the bits of . Additionally, the correlation coefficients are near the ideal value of , suggesting an absence of relationships between adjacent pixels. In this context, these results imply a lack of correlation between the bits of from which the pixels are generated, across all three analyzed directions.
Additionally, two hypothesis tests were performed on Figure 1 and Figure 2: the Discrete Fourier Transform (DFT) test and the goodness-of-fit test [31]. The results, presented in Table 4, use the symbol ✔ to denote acceptance of the null hypothesis. For the DFT test, the acceptance of the null hypothesis indicates the absence of periodic features within the sequence, which in this context pertains to the pixels but can also be interpreted as the bits of from which the pixels are derived.

The acceptance of the null hypothesis in the goodness-of-fit test confirms that the pixel intensity distribution closely resembles a uniform distribution. This result is significant, as it suggests that the digits of , when expressed as 8-bit numbers (within a 256-numerical system), each of them occurs approximately with the same frequency. The conclusions derived from entropy and correlation are further validated by these two hypothesis tests, as the acceptance of the null hypothesis, in summary, signifies a random distribution of the information. In this case, the information pertains to the pixels but is fundamentally tied to the bits of .
With these observations in mind, and based on the correlation between the pairs of strings analyzed in this section, the second hypothesis is stated in Hypothesis 2. To ensure clarity, the relevant elements referenced within the hypothesis are defined below.
- Let represent a bit to the right of the decimal point of the number .
- Let denote a string of n bits.
- Let a different bit string with m bits. It is assumed that there is at least a bit at position j in that does not exist at the same position in , and vice-versa.
Hypothesis 2.
In the probabilistic experiment of selecting two strings, each comprising n and m consecutive bits, respectively, from the decimal part of the number π, the probability of selecting the strings and is calculated as the product of the probability of selecting the string and the probability of selecting the string . In other words, .
4. The Upper Bound
This section outlines the methodology to establish an upper bound on the number of bits of ’s decimal expansion required to locate any given string at least once with a probability p.
4.1. The Probability of Selecting a String
From the presented information in Hypothesis 1 and 2, the following Lemma is presented.
Lemma 1.
In the probabilistic experiment of selecting a string of n consecutive bits from the decimal part of the number π, the probability of selecting the string is equal to , expressed as .
Proof of Lemma 1.
The proof of this lemma shall proceed through the method of mathematical induction.
- Base case: The base case is considered when , representing the probability of selecting the 1-bit string , which consists solely of the bit . In other words, . According to the first hypothesis, it follows thatThis result aligns with the statement of the Lemma, confirming consistency.
- Inductive hypothesis: Assume that the Lemma holds true for . Under this assumption, the inductive hypothesis states that the probability of selecting the k-bit string is given by .
- Inductive step: Prove that the formula also holds for . We then analyze the scenario wherein a string of bits is selected, it is . Consequently, the probability of selecting the string can be expressed as the probability of selecting the k-bit string and the 1-bit string .Leveraging the Hypothesis 2, we deduceSubsequently, utilizing the inductive hypothesis and the Hypothesis 1 indicating , it follows thatConsequently,
□
4.2. The Probability of Finding
Before presenting the theorem, another string will be presented. Consider as a string of bits, representing the first N consecutive bits to the right of the decimal point within the number . Here, the initial bit of corresponds to the first bit within the decimal part of .
Theorem 1.
As the length N of the string approaches infinity, the probability of the n-bit string appearing at least once as a contiguous bit string within tends to 1.
Proof of Theorem 1.
Next, we demonstrate the probability that appears at least once as a sequence of consecutive bits within the string of length N. This involves analyzing the probability that appears times within .
To achieve this, we present the following probabilistic experiment: each group of n consecutive bits from is compared to the string . If they match, it is considered a success. This setup constitutes a Bernoulli experiment, as each trial has exactly two possible outcomes: success or failure. The details of the experiment are outlined below.
- First trial: The initial n consecutive bits of the string are selected and compared to determine if they match the string . A successful outcome occurs when the selected sequence matches the string, while failure arises if there is no match. Referring to Lemma 1, the probability of success is . In addition, it is possible to form strings of n consecutive bits in one of length N, which implies that the number of trials is .
- Second trial: Another string of n bits is obtained from starting from bit position 1 and extending to bit n. Following the same reasoning, the probability of this string being equal to is . Additionally, since the string of n bits from trial 1 is different from that of trial 2, it is independent as per the second hypothesis.
- i-th trial: In general, for the i-th trial, the string to be compared with starts from bit number of , encompassing the consecutive n bits.
Under this experiment, the probability of the string appearing y times as consecutive bits within the string is expressed in Equation (11).
Then, the probability of appearing at least once as a consecutive bit string in can be expressed through its complement, where it does not appear at all:
By substituting into Equation (11), we obtain Equation (12), which represents the probability that the string appears at least once within .
Subsequently, by applying the limit as to both sides of Equation (12), we have
which can be simplified to
It is important to note that for any arbitrary but fixed . Therefore, and . Consequently, as , . In other words, . In conclusion, given that the first term is a constant () and the limit obtained earlier corresponds to the second term, it follows that
□
From this, we conclude that, on the long path to infinity, it is highly probable that the string appears at least once, within .
4.3. An Upper Bound N for Finding
Continuing this discussion, another problem to address is determining the length N of a bit string, starting from the zero bit position of the decimal part of , such that a given string of length n is contained at least once within with consecutive bits and a probability of p. As a result of this consideration, the following corollary is formulated:
Corollary 1.
The length N at which appears at least once within as a string of consecutive bits can be determined using Equation (13) in terms of the probability p of its occurrence and the length n.
Proof of Corollary 1.
In this proof, we utilize the results of Theorem 1. Accordingly, the probability of appearing at least once as a consecutive bit string in , , is given by Equation (12). Let , then Equation (12) is written as,
By rearranging terms, we obtain
Upon applying the natural logarithm on both sides and its properties
□
On the other hand, the probability p can be made as close to one as desired, minimizing the error to find any desired length. In this study, a probability of is employed, resulting in an error of . Furthermore, it is important to clarify that in this investigation, N is rounded using the ceiling function, denoted by , to return the smallest integer greater than or equal to the expression in Equation (13), i.e., the integer part plus one. Subsequently, the results of finding strings for different values of N will be presented in the next section.
5. Results Analysis and Discussion
This section commences with the results derived from the experimental properties. Firstly, Table 1 illustrates that as the length n of the bit string increases, the proportion of zeros and ones tends toward 50%. Secondly, there is a fluctuation in the percentages of zeros and ones, with the percentage of zeros occasionally exceeding 50% and at other times falling below this percentage. This observation forms the basis for the first hypothesis proposed in this research. Additionally, this result is consistent with the concept of normal numbers [32]. To further support the second hypothesis, Table 2 is presented. In this analysis, four different bit lengths are considered to generate strings starting from various bit positions i within the decimal part of the number . It can be observed that as the length of the bit strings increases, the correlation between pairs of strings tends towards zero. This indicates a lack of a linear relationship between them, providing evidence in favor of the second hypothesis.
Additionally, two color images, presented in Figure 1 and Figure 2, are constructed using randomly selected blocks of bits from the decimal part of the number . The first image comprises 512 × 512 pixels, while the second one consists of 1024 × 1024 pixels. Subsequent evaluations are conducted to assess the level of chaos exhibited by the bits in both images from a cryptographic perspective. This evaluation is based on parameters such as entropy, correlation, goodness-of-fit test using the distribution, and the discrete Fourier transform. It is observed that there is no discernible relationship between the bits in both images, as evidenced by Table 1, Table 2, Table 3 and Table 4.
On the other hand, significant research in image encryption shows lower entropy levels of encrypted images than those observed in the images generated from the bits of , suggesting a comparatively lower degree of pixel randomness. For instance, the entropy values of Figure 1 and Figure 2 range from 7.99920 to 7.99982. In contrast, several encryption proposals report lower entropy values: the work in [33] achieves entropy values between 7.9931 and 7.9949, while another reports values ranging from 7.9968 to 7.9975 [34]. Similarly, a third study presents a range of 7.9972 to 7.9994 [35]. Other researches achieve entropy levels closer to those of the -based images, such as entropy values between 7.9969 and 7.9998 [36], and a range from 7.9992 to 7.9998 [37]. Consequently, it can be observed that the distribution of information within the blocks of the number exhibits chaotic properties, in some cases surpassing those observed in encrypted images.
Concerning the theorem presented, it is observed that as the string length N increases, the probability of locating the string within consecutive bits of approaches 1. However, this increase in N entails the need to search through more bits, which comes at a computational cost. Additionally, due to the probabilistic nature of the process, there remains a risk that certain strings may fall outside the range of consideration.
After establishing the theorem, a corollary was formulated to determine the length N of the sequence required to encompass, with consecutive bits, any string with a probability p. To validate the formula, 16 distinct strings were located in . These were composed entirely of zeros or ones, across eight different sizes. The formula’s predicted upper bound, computed with a probability , was used as a reference.
Table 5 summarizes the results of this validation. The first column specifies the length n of the target string, while the second column presents the calculated upper bound N. The third and fourth columns indicate the starting bit positions of the identified strings of zeros and ones, respectively, within the decimal part of . The results confirm that all identified strings are located within the proposed upper bound, except for the string of consecutive zeros, which was found at a position exceeding the predicted upper bound N. This discrepancy aligns with the 1% error margin inherent in the computation of Equation (13) with .

Table 5.
Validation results for locating strings of n consecutive zeros and ones within the decimal part of , compared against the predicted upper bound N with a 99% probability.
In this study, string searching was performed using a finite automaton search algorithm with n states, where n represents the length of the string being searched within a sequence of N bits of . A finite automaton of these characteristics has a computational complexity of [38] for locating an n-bit string within an N-bit sequence of . Regarding the storing, to search for sequences of 40 consecutive bits, the upper bound suggests examining 5,063,438,167,262 bits, which entails significant storage requirements. This highlights the importance of analyzing the type of storage used, whether a hard drive or a solid-state drive, particularly for cryptographic applications.
Finally, although the present study focuses on the number , the methodology developed here can be extended to analyze string searches in other numbers, such as transcendental numbers. Future research could expand this analysis to explore how the results vary with different numbers, identify the unique strengths of each number, and evaluate their potential applications. Such investigations could provide valuable options for utilizing these numbers in fields like Cryptography.
6. Conclusions
In this work, a theorem was presented and demonstrated, showing that any finite-length string has a probability arbitrarily close to 1 of appearing somewhere with consecutive bits after the decimal point of the number . From this theorem, a corollary has been derived, demonstrating how to calculate the length of the chain in such that, with a probability p, the chain appears at least once within . In this research, has been chosen, though it can approach 1 arbitrarily closely. The proof of this theorem relies on two hypotheses: firstly, when selecting a bit from the right side of the decimal point, . Secondly, it establishes that when two different bit strings of lengths n and m are chosen from the decimal part of , the probability of selecting and such that is independent; that is, . Experimentation has been conducted to provide evidence supporting these hypotheses, as shown in Table 1, Table 2, Table 3 and Table 4. Furthermore, the results derived from the images of in Figure 1 and Figure 2, when subjected to entropy and correlation parameters, resemble those of encrypted images known for their chaotic information. Finally, the upper bound N provides information about the number of bits of to use for generating random sequences effectively.
Author Contributions
Conceptualization V.M.S.-G.; methodology M.A.C.-L.; formal analysis V.M.S.-G. and M.A.C.-L.; investigation M.A.C.-L., visualization M.A.C.-L., writing—review and editing M.A.C.-L. and R.F.-C.; data curation R.F.-C.; software R.F.-C.; validation R.F.-C.; writing—original draft preparation V.M.S.-G.; resources V.M.S.-G. and R.F.-C.; supervision V.M.S.-G.; project administration V.M.S.-G. and R.F.-C.; funding acquisition V.M.S.-G. and R.F.-C. All authors have read and agreed to the published version of the manuscript.
Funding
This work was funded in part by the economic support program of the Comisión de Operación y Fomento de Actividades Académicas (COFAA) and the Secretaría de Investigación y Posgrado (SIP) of the Instituto Politécnico Nacional under grants SIP-20241356 and SIP-20241716.
Data Availability Statement
The data of this study are available from the corresponding author upon request and the digits of were downloaded from: https://storage.googleapis.com/pi100t/index.html (accessed on 13 March 2024).
Acknowledgments
The authors would like to thank the Instituto Politécnico Nacional of México (Secretaría Académica, Comisión de Operación y Fomento de Actividades Académicas COFAA, SIP, and CIDETEC), and the CONAHCyT (SNI) for their support in the development of this work.
Conflicts of Interest
The authors declare no conflicts of interest.
Abbreviation
The following abbreviation is used in this manuscript:
| DFT | Discrete Fourier Transform |
References
- Agarwal, R.P.; Agarwal, H.; Sen, S.K. Birth, growth and computation of pi to ten trillion digits. Adv. Differ. Equ. 2013, 2013, 100. [Google Scholar] [CrossRef]
- Bailey, D.H.; Borwein, J.M. Pi: The Next Generation: A Sourcebook on the Recent History of Pi and Its Computation, 1st ed.; Springer International Publishing: Cham, Switzerland, 2016; Volume 5, pp. 1–501. [Google Scholar] [CrossRef]
- Balasubramanian, K.; Davidson, E.R. Rational approximations to pie: Transcendental π and Euler’s Constant e. J. Math. Chem. 2023, 61, 1471–1476. [Google Scholar] [CrossRef]
- Bailey, D.; Borwein, P.; Plouffe, S. On the rapid computation of various polylogarithmic constants. Math. Comput. 1997, 66, 903–913. [Google Scholar] [CrossRef]
- Frey, B.; Van Schie, A.; Zacheo, G. Pi-Experience—Making 62.8 Trillion Digits Come Alive. In Proceedings of the 15th International Symposium on Visual Information Communication and Interaction (VINCI), Chur, Switzerland, 16–18 August 2022; pp. 1–4. [Google Scholar] [CrossRef]
- Bokari, N. Piece of Pi: Wit-Sharpening, Brain-Bruising, Number-Crunching Activities With Pi, 1st ed.; Taylor & Francis: New York, NY, USA, 2023; pp. 1–3. [Google Scholar] [CrossRef]
- Wang, H.; Hsu, C.; Harn, L. A Lightweight and Robust Stream Cipher Based on PI for Intelligent Transportation Systems. Wirel. Pers. Commun. 2023, 130, 1661–1675. [Google Scholar] [CrossRef]
- Mengdi, Z.; Xiaojuan, Z.; Yayun, Z.; Siwei, M. Overview of randomness test on cryptographic algorithms. J. Phys. Conf. Ser. 2021, 1861, 012009. [Google Scholar] [CrossRef]
- Silva-García, V.M.; Ramírez-González, M.D.; Flores-Carapia, R.; Vega-Alvarado, E.; Escobar-Rodríguez, E. A novel method for image encryption based on chaos and transcendental numbers. IEEE Access 2019, 7, 163729–163739. [Google Scholar] [CrossRef]
- Erkan, U.; Toktas, A.; Toktas, F.; Alenezi, F. 2D eπ-map for image encryption. Inf. Sci. 2022, 589, 770–789. [Google Scholar] [CrossRef]
- Richards, N. Questions in Dataviz: A Design-Driven Process for Data Visualization, 1st ed.; AK Peters/CRC Press: Boca Raton, FL, USA, 2022; pp. 286–288. [Google Scholar] [CrossRef]
- Émile Borel, M. Les probabilités dénombrables et leurs applications arithmétiques. Rend. Circ. Matem. Palermo 1909, 27, 247–271. [Google Scholar] [CrossRef]
- Wagon, S. Is π normal? Math. Intell. 1985, 7, 65–67. [Google Scholar] [CrossRef]
- Lepore, A.; Palumbo, B.; Poggi, J.M. Interpretability for Industry 4.0: Statistical and Machine Learning Approaches, 1st ed.; Springer Nature: Cham, Switzerland, 2022; pp. 5–6. [Google Scholar] [CrossRef]
- Bailey, D.H.; Borwein, J.M.; Calude, C.S.; Dinneen, M.J.; Dumitrescu, M.; Yee, A. An empirical approach to the normality of π. Exp. Math. 2012, 21, 375–384. [Google Scholar] [CrossRef]
- Bailey, D.H.; Borwein, J.M.; Brent, R.P.; Reisi, M. Reproducibility in computational science: A case study: Randomness of the digits of Pi. Exp. Math. 2017, 26, 298–305. [Google Scholar] [CrossRef][Green Version]
- Gronau, Q.F.; Wagenmakers, E.J. Bayesian evidence accumulation in experimental mathematics: A case study of four irrational numbers. Exp. Math. 2018, 27, 277–286. [Google Scholar] [CrossRef]
- Miklas-Kalczynska, M.; Drezner, T.D.; Drezner, Z. Experimenting with the generalized binomial distribution. Commun. Stat. Case Stud. Anal. Appl. 2024, 10, 27–46. [Google Scholar] [CrossRef]
- Shapiro, S.S.; Zahedi, H. Bernoulli trials and discrete distributions. J. Qual. Technol. 1990, 22, 193–205. [Google Scholar] [CrossRef]
- Li, C.; Lin, D.; Feng, B.; Lü, J.; Hao, F. Cryptanalysis of a chaotic image encryption algorithm based on information entropy. IEEE Access 2018, 6, 75834–75842. [Google Scholar] [CrossRef]
- Zolfaghari, B.; Bibak, K.; Koshiba, T. The odyssey of entropy: Cryptography. Entropy 2022, 24, 266. [Google Scholar] [CrossRef] [PubMed]
- Kumar, V.; Pathak, V.; Badal, N.; Pandey, P.S.; Mishra, R.; Gupta, S.K. Complex entropy based encryption and decryption technique for securing medical images. Multimed. Tools Appl. 2022, 81, 37441–37459. [Google Scholar] [CrossRef] [PubMed]
- Wu, Y.; Zhou, Y.; Saveriades, G.; Agaian, S.; Noonan, J.P.; Natarajan, P. Local Shannon entropy measure with statistical tests for image randomness. Inf. Sci. 2013, 222, 323–342. [Google Scholar] [CrossRef]
- Alghamdi, Y.; Munir, A. Image Encryption Algorithms: A Survey of Design and Evaluation Metrics. J. Cybersecur. Priv. 2024, 4, 126–152. [Google Scholar] [CrossRef]
- Diaconu, A.V.; Dascalescu, A.C. Correlation distribution of adjacent pixels randomness test for image encryption. Proc. Rom. Acad. Ser. A 2017, 18, 351–360. [Google Scholar]
- Luengo, E.A.; Olivares, B.A.; Villalba, L.J.G.; Hernandez-Castro, J. Further analysis of the statistical independence of the NIST SP 800-22 randomness tests. Appl. Math. Comput. 2023, 459, 128222. [Google Scholar] [CrossRef]
- Cirrone, G.; Donadio, S.; Guatelli, S.; Mantero, A.; Mascialino, B.; Parlati, S.; Pia, M.; Pfeiffer, A.; Ribon, A.; Viarengo, P. A goodness-of-fit statistical toolkit. IEEE Trans. Nucl. Sci. 2004, 51, 2056–2063. [Google Scholar] [CrossRef]
- Brereton, R.G. The chi squared and multinormal distributions. J. Chemometr. 2014, 29, 9–12. [Google Scholar] [CrossRef]
- Zhang, X.; Liu, G.; Zou, C. An image encryption method based on improved Lorenz chaotic system and Galois field. Appl. Math. Model. 2024, 131, 535–568. [Google Scholar] [CrossRef]
- Wen, H.; Xie, Z.; Wu, Z.; Lin, Y.; Feng, W. Exploring the future application of UAVs: Face image privacy protection scheme based on chaos and DNA cryptography. J. King Saud Univ.-Comput. Inf. Sci. 2024, 36, 101871. [Google Scholar] [CrossRef]
- Singh, L.D.; Thingbaijam, R.; Patgiri, R.; Singh, K.M. Cryptanalysis of cross-coupled chaotic maps multi-image encryption scheme. J. Inf. Secur. Appl. 2024, 80, 103694. [Google Scholar] [CrossRef]
- Bailey, D.H.; Crandall, R.E. Random generators and normal numbers. Exp. Math. 2002, 11, 527–546. [Google Scholar] [CrossRef]
- Ponuma, R.; Amutha, R. Compressive sensing based image compression-encryption using novel 1D-chaotic map. Multimed. Tools Appl. 2018, 77, 19209–19234. [Google Scholar] [CrossRef]
- Iqbal, N.; Hussain, I.; Khan, M.A.; Abbas, S.; Yousaf, S. An efficient image cipher based on the 1D scrambled image and 2D logistic chaotic map. Multimed. Tools Appl. 2023, 82, 40345–40373. [Google Scholar] [CrossRef]
- Du, L.; Teng, L.; Liu, H.; Lu, H. Multiple face images encryption based on a new non-adjacent dynamic coupled mapping lattice. Expert Syst. Appl. 2024, 238, 121728. [Google Scholar] [CrossRef]
- Xian, Y.; Wang, X. Fractal sorting matrix and its application on chaotic image encryption. Inf. Sci. 2021, 547, 1154–1169. [Google Scholar] [CrossRef]
- Wang, C.; Chong, Z.; Zhang, H.; Ma, P.; Dong, W. Color image encryption based on discrete memristor logistic map and DNA encoding. Integration 2024, 96, 102138. [Google Scholar] [CrossRef]
- Holzer, M.; Kutrib, M. Descriptional and computational complexity of finite automata—A survey. Inf. Comput. 2011, 209, 456–470. [Google Scholar] [CrossRef]
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).