2.1. GAF-Based Time-Series Imaging
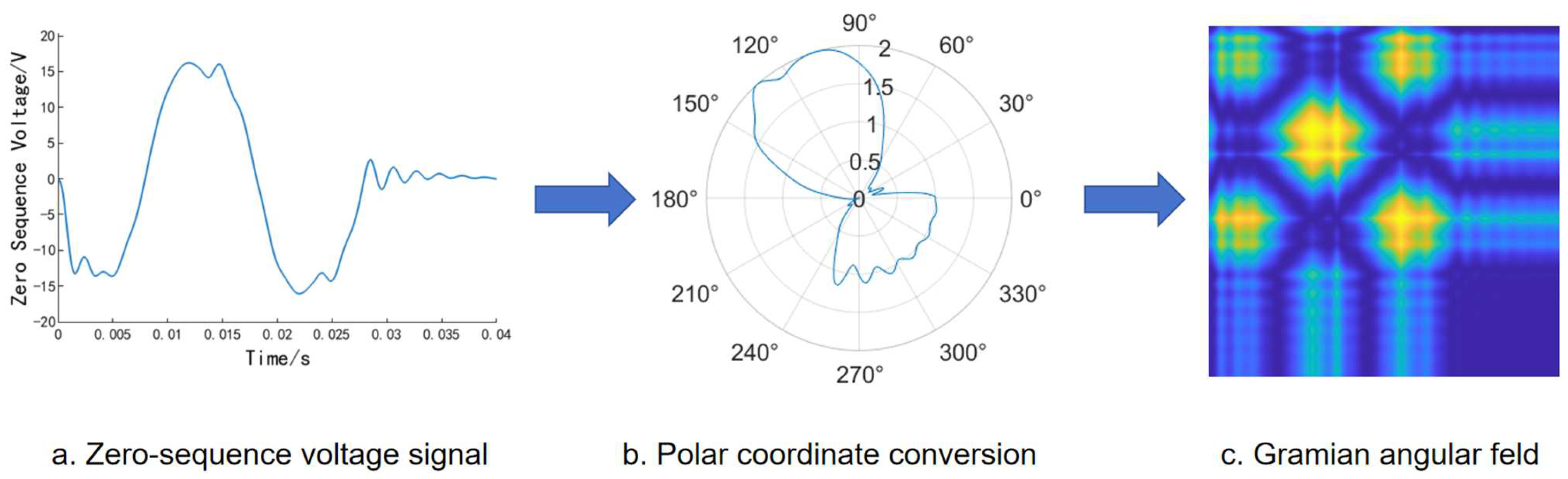
The Gramian Angular Field (GAF) is an encoding technique for time-series data. It transforms temporal data into image representations by integrating coordinate transformation and Gramian matrices. The Gramian matrix, constructed from inner products between vectors, effectively preserves temporal dependencies within the time-series. One key limitation of Gramian matrices lies in their inability to distinguish between meaningful signal patterns and Gaussian noise components. To overcome this challenge, we transform the time-series data from Cartesian to polar coordinates before constructing the Gramian matrix representation [
31].
Given a time-series where t represents the temporal index and , the Gramian Angular Field transformation proceeds as follows:
The symbols and notations used in this paper are listed in the Nomenclature. Following Wang et al. [
31], We first normalize the time-series data to the interval [−1, 1] through min–max scaling, which preserves the underlying data distribution. This transformation is expressed as Formula (1):
where
represents the
i-th data point in the original time-series, and
represents the complete time-series dataset.
- 2.
Polar Coordinate Transformation
The data
obtained from Formula (1) undergoes a polar coordinate transformation to derive the corresponding angle and radius for each data point, with the angle expressed in Formula (2) and the radius in Formula (3):
where
represents the position of the data point in the sequence, and
is the normalization factor.
- 3.
Generation of Gramian Angular Field Image
Using the summation angle relationships presented in Formula (4), we obtain the corresponding Gramian Angular Summation Field (GASF) images:
where
and
represent the angular values at time points
i and
j, respectively,
denotes the normalized time-series matrix,
is the transpose of
, and
represents the identity matrix.
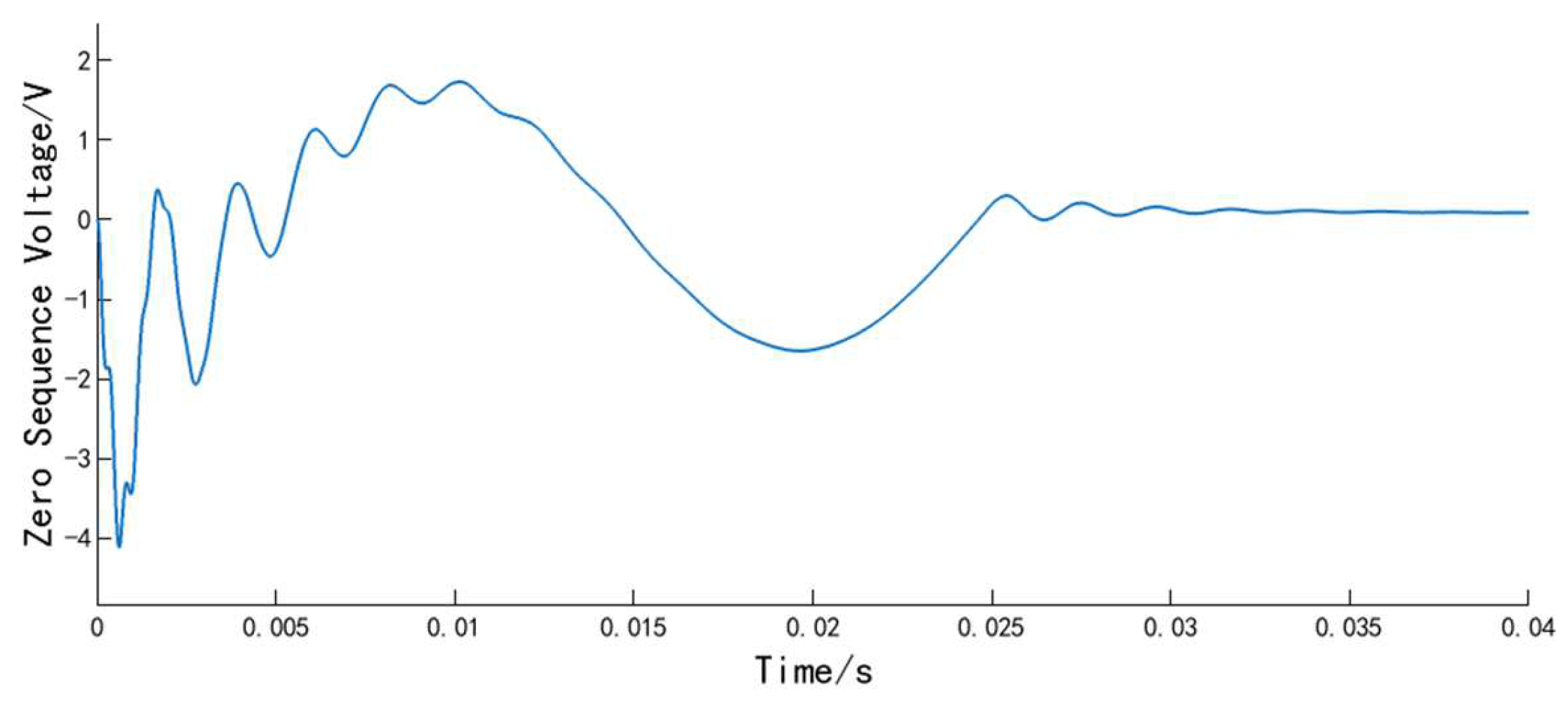
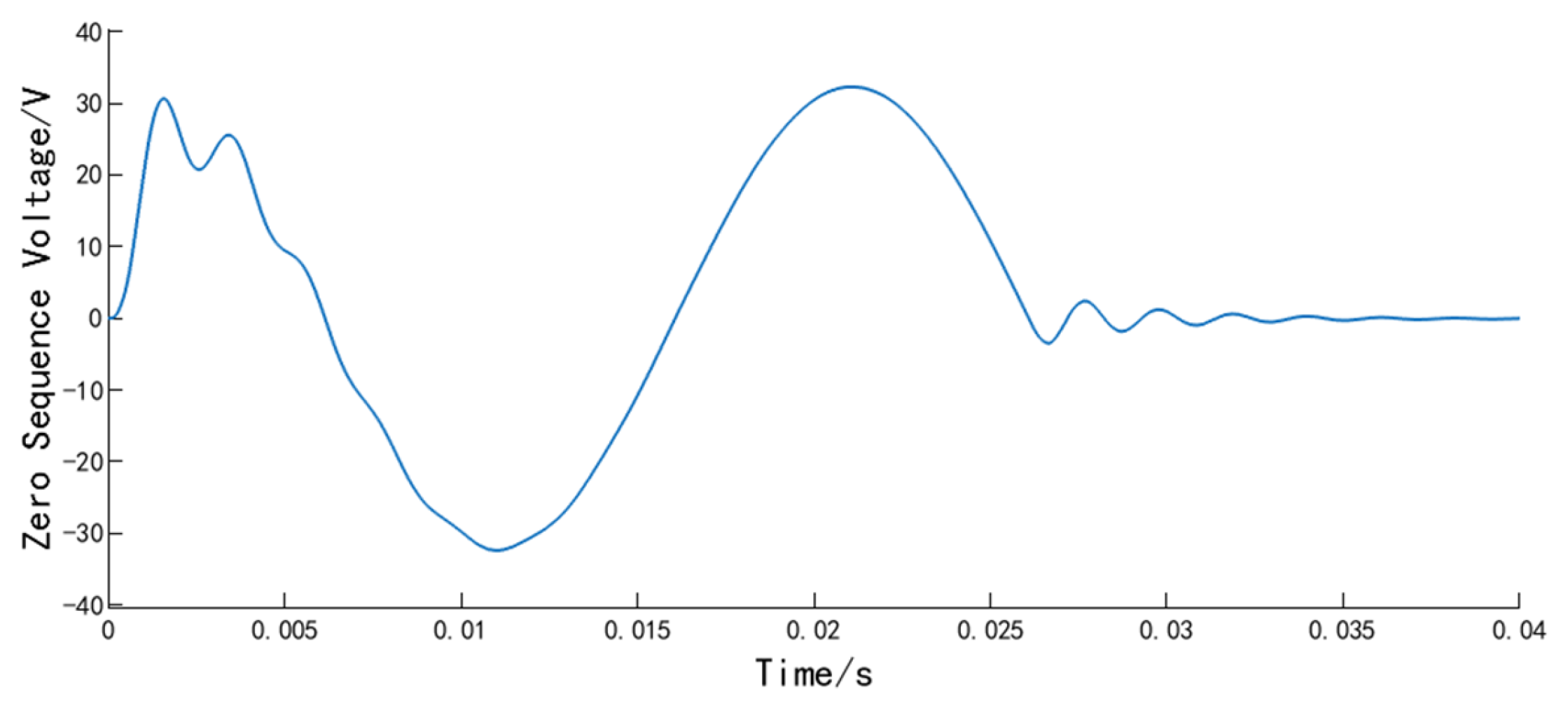
Figure 2 illustrates the procedure in which Gramian Angular Field transformation converts time-series to images.
2.2. The Crested Porcupine Optimizer (CPO) Algorithm
Inspired by crested porcupine defensive behavior, M. Abdel-Basset et al. [
32] developed the CPO. The algorithm features a Cyclic Population Reduction (CPR) technique, reflecting how only threatened individuals activate their defense mechanisms. Following M. Abdel-Basset et al. [
32], the mathematical model is expressed in Formula (5):
where
denotes the current population size,
represents the initial population size, and
is the minimum population size required to prevent excessive population reduction. The parameters
and
indicate the current and maximum number of iterations, respectively. % represents the remainder or modulo operator.
T is a variable to determine the number of cycles.
When predators are distant, CPs employ two defensive strategies: visual and acoustic responses. These strategies facilitate broad spatial exploration, focusing on global search capabilities.
- (i)
Visual Strategy
As their primary long-range defense, porcupines erect their quills to appear larger and deter predators. This exploration-oriented strategy is mathematically expressed in Formula (6):
where
denotes the
i-th individual position,
represents the global best solution,
and
are step-size control parameters, and
indicates the candidate solution.
- (ii)
Acoustic Strategy
If visual deterrence fails, porcupines escalate their defense by producing threatening sounds. This behavior is mathematically represented as an expansion of the search space through perturbation, as expressed in Formula (7):
where
and
are random numbers used to balance the relationship between current and new positions and control the perturbation amplitude, and
represents the target position of the predator after disturbance, while
and
denote randomly selected individual positions.
- 2.
Exploitation phase
In this phase, the CP implements defensive behaviors based on predator proximity, utilizing two strategies: odor attack and physical attack.
- (i)
Odor attack strategy
When a predator approaches, the porcupine releases odors to disrupt its movement. In mathematical terms, this strategy involves narrowing the search space to focus on local optima, as shown in Formula (8):
where
denotes the position of a randomly selected individual,
is the parameter controlling the search direction,
represents the defense factor, and
defines the scent diffusion coefficient.
- (ii)
Physical attack strategy
When all else fails, porcupines resort to physical attacks as their last defense. This behavior is mathematically represented by Formula (9):
where
is the convergence rate control factor, while
and
are random numbers that control the step size and balance between current and new positions, respectively.
represents the force acting on the current individual, simulating the predator’s behavioral response after receiving a physical attack.
Compared to traditional optimization algorithms like Particle Swarm Optimization (PSO) and Genetic Algorithms (GAs), the CPO offers several advantages in hyperparameter optimization. While PSO may suffer from premature convergence and GAs can be computationally intensive, the CPO’s Cyclic Population Reduction (CPR) technique provides a better balance between exploration and exploitation. The defense strategies in the CPO—visual, acoustic, odor, and physical attack—enable more effective searching of the parameter space compared to single-strategy algorithms.
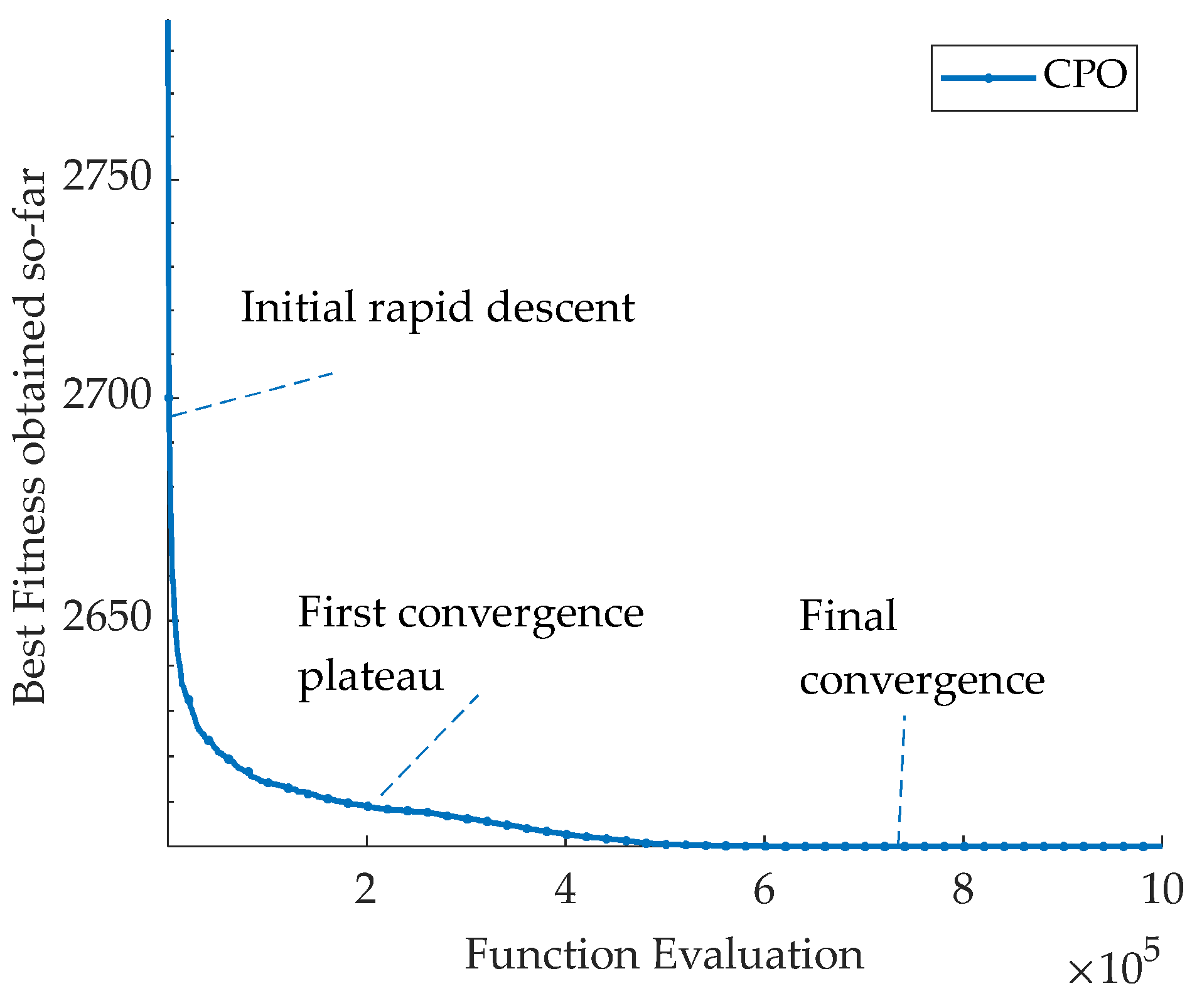
Figure 3 shows the evolution of the objective function value during the CPO algorithm optimization process. The following key observations can be drawn:
The algorithm exhibits rapid initial convergence, with the objective function value decreasing sharply. This fast convergence is attributed to the effective global exploration capabilities of visual and sound strategies, allowing the quick identification of promising solution regions. As iterations progress, the convergence curve gradually levels off, indicating the algorithm’s transition to fine-tuning. In this phase, scent and physical attack strategies perform local exploitation, thoroughly exploring promising areas. The convergence curve ultimately stabilizes at a low value, indicating successful identification of near-optimal solutions and algorithm stability. The entire optimization process demonstrates the CPO’s excellent performance through its balanced exploration and exploitation mechanisms.
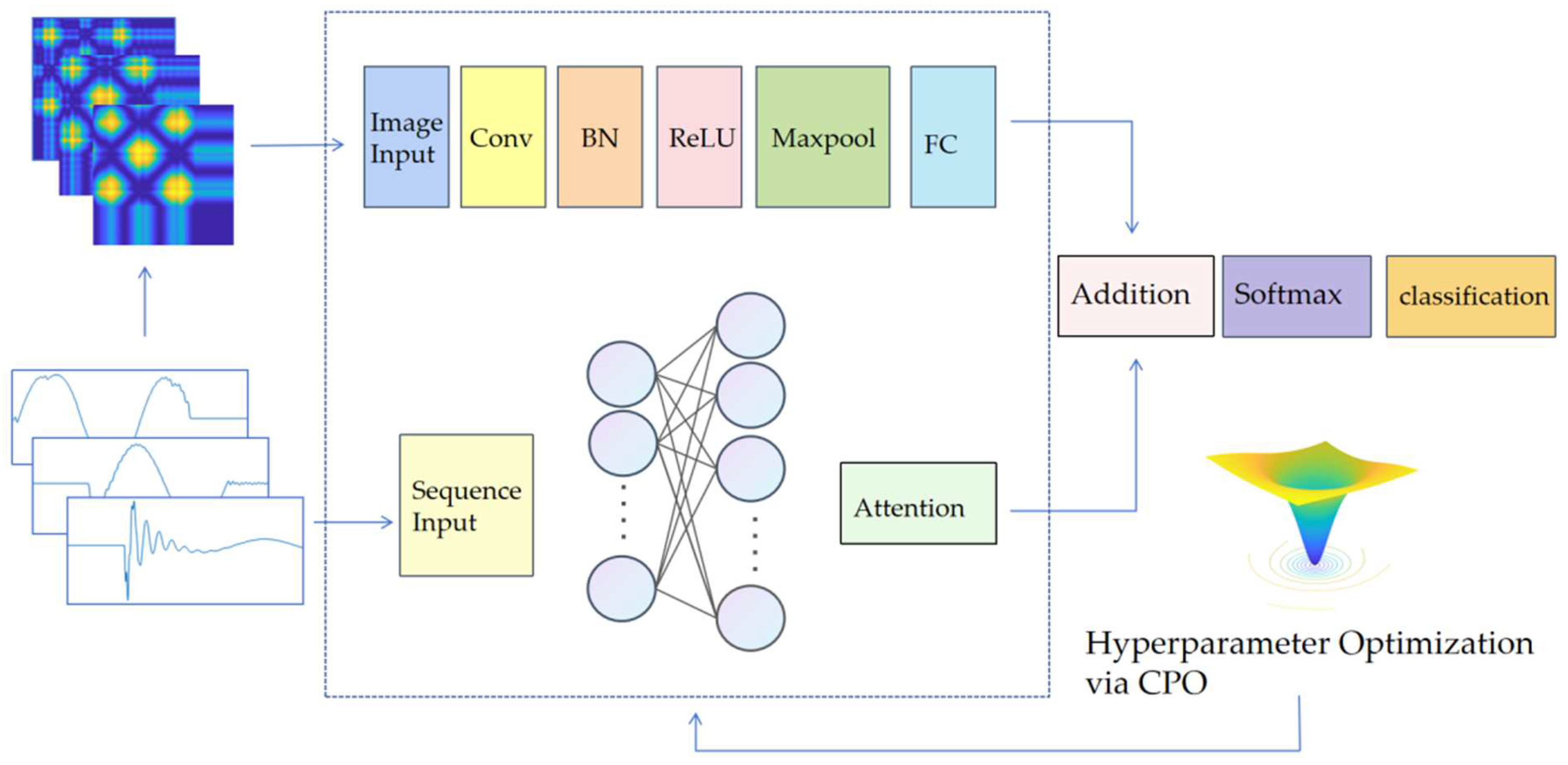
2.3. Dual-Path Neural Networks Optimized by CPO
The proposed framework integrates two core components: a deep learning architecture and an optimization algorithm. Drawing from the dual-channel parallel CNN proposed by Li et al. [
33], we designed a dual-path neural network that processes both image and temporal data simultaneously, achieving high-impedance fault identification through feature fusion.
The image processing branch employs a CNN-based structure. It takes 300 × 300 × 3 RGB images as an input with Z-score normalization. A 3 × 3 convolution (stride = 2, padding = 3) is applied, followed by ReLU activation and 3 × 3 max-pooling (stride = 2, padding = 1). The features are then flattened through a 128-neuron fully connected layer. The temporal branch utilizes GRU layers with a self-attention mechanism. Features from both branches are converted to one-dimensional vectors and merged via an addition layer. A three-node fully connected layer processes the fused features before Softmax transformation.
In this study, we employed the CPO to optimize the hyperparameters of the dual-path neural network. The CPO algorithm was initialized with carefully selected parameters based on extensive empirical testing: a population size
N′ = 30 with a minimum population size
= 24, defense cycle parameter
T = 2, convergence rate
α = 0.03, and trade-off coefficient
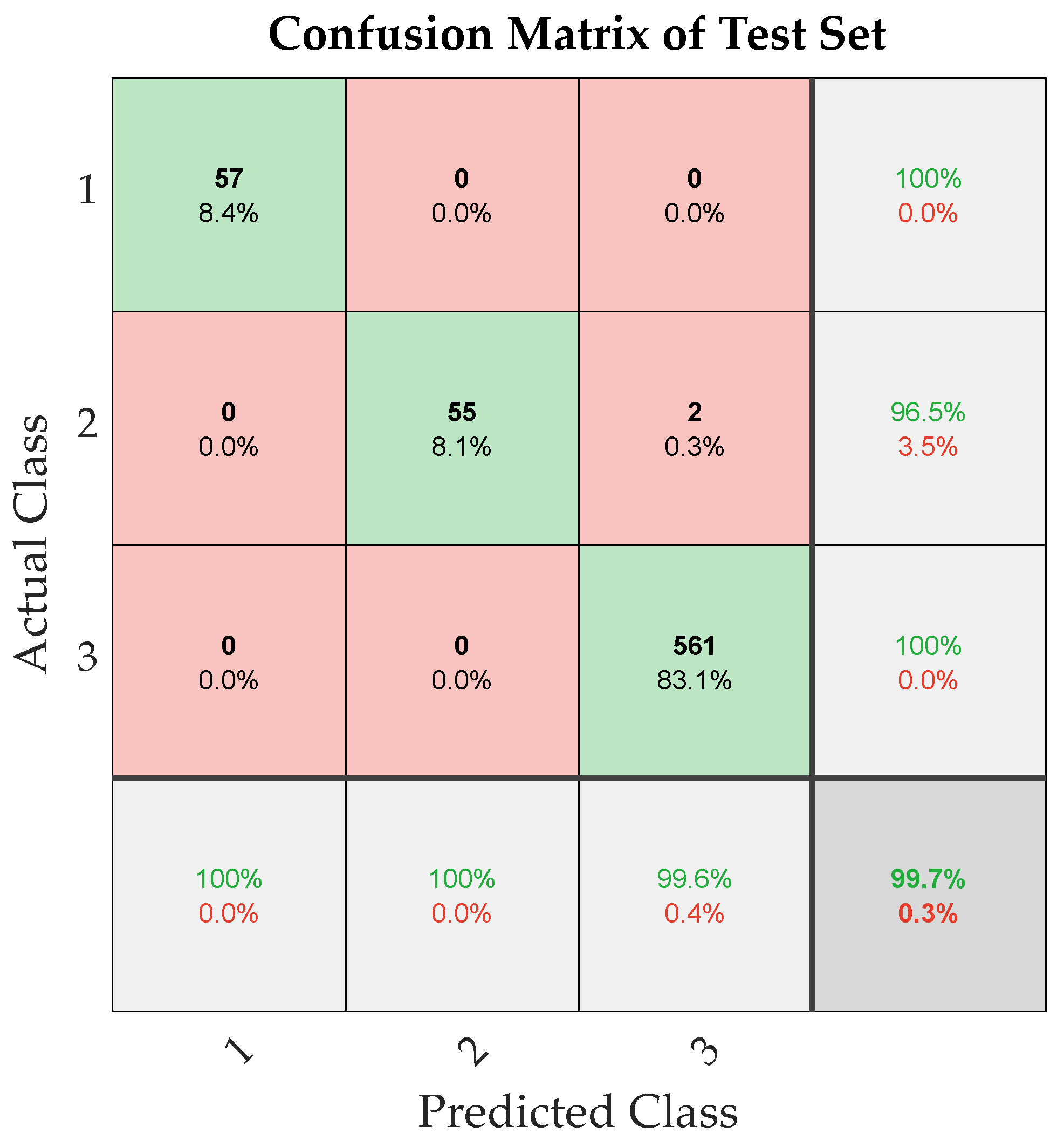
Tf = 0.8. These parameters were chosen to balance exploration and exploitation capabilities while maintaining population diversity. The optimization scope encompassed four critical hyperparameters: the learning rate (0.001, 0.01), number of convolution kernels (32, 128), number of GRU neurons(32, 128), and number of attention heads (1, 4). The CPO utilizes four sequential defense mechanisms (sight, sound, odor, and physical attack), while employing Cyclic Population Reduction for efficient convergence and diversity. The algorithm converged to an optimal configuration with 62 convolution kernels, 67 GRU neurons, single-head attention, and a learning rate of 0.0092204. This configuration demonstrated superior performance compared to traditional optimization methods, exhibiting enhanced convergence characteristics and stability. The final model implementation utilized the Adam optimizer with per-epoch data shuffling to mitigate overfitting risks. The CPO-optimized model achieved a remarkable accuracy of 99.7% on the test set, representing a significant improvement over the baseline model’s 98.9% accuracy.
Figure 4 illustrates the detailed workflow and structure of our proposed dual-path neural network for high-impedance fault detection.