Image Encryption Using Chaotic Maps: Development, Application, and Analysis
Abstract
1. Introduction
- Section 3 introduces the proposed image encryption scheme in detail, including the preprocessing steps, chaotic key generation, encryption and decryption procedures, and implementation specifics. A flowchart is provided to illustrate the full process.
- Section 4 builds on this foundation by introducing new insights into image encryption and comparing the results for each chaotic system using the same set of metrics. Additionally, the results of the chaos-based image encryption are compared to those obtained using AES (Advanced Encryption Standard), serving as a reference system for computational efficiency and data protection.
- Section 5 summarizes the main findings and explores potential directions for further research.
- We perform a structured comparative analysis of three classical chaotic systems (Henon, tent, and logistic maps) applied to image encryption.
- We generate encryption keys based on chaotic sequences filtered through a statistical independence test to enhance unpredictability.
- We benchmark the performance of these systems both visually and quantitatively using metrics such as MSE, PSNR, NPCR, EQ, and UACI.
- We provide a side-by-side comparison with the AES standard to contextualize the results within established cryptographic practices.
- We propose practical insights regarding the trade-offs between statistical encryption strength and perceptual (visual) encryption quality.
2. Theoretical Background
2.1. Chaotic Systems
2.2. Statistical Independence
- Step 1—Data Transformation: X and Y are transformed into U and V, ensuring they follow a standard normal distribution.
- Step 2—Chi-Square Test: the chi-square test is applied to U and V to assess their conformity with a specific uncorrelated, jointly normal probability law (4). This conformity is evaluated against the standard Gaussian bivariate probability law represented by the following equation:
- Step 3—Decision-Making: if U and V comply with the standard Gaussian bivariate probability law (Equation (4)), then X and Y are considered statistically independent. Conversely, a deviation from this distribution suggests dependence between X and Y.
2.3. Metrics Used to Evaluate the Encryption Results
- The execution time was the difference between the start and end time of the simulation, which included the key generation and encrypting/decrypting of the image. The computer used contained an Intel i5 processor (8th Gen) and 8 GB of RAM memory.
- MSE (mean-squared error) is the mean of the squared differences between the original image and the encrypted image. The squared difference is calculated for each pixel and color plane and the values are averaged over image size and color planes. The bigger the MSE, the harder it is to understand/decrypt the encrypted image.
- PSNR (peak signal-to-noise ratio) is calculated based on the MSE (5).If the MSE needs to be large to ensure a good encryption, this means that a small PSNR value is desired.
- EQ (encryption quality) is calculated based on (6). The encryption quality of an image, is calculated by comparing the pixels of the encrypted image with those of the original image. It is considered better when the difference between the pixel values of the two images is larger. The larger the EQ parameter value, the higher the encryption security.The encryption quality can be determined as follows: and represent the values of the pixel at row i and column j, in the encrypted image and the original image, respectively, each image having dimensions with L pixel levels. and are defined as the number of occurrences of each level L in the original image and the encrypted image, respectively. EQ represents the average number of changes for each level and considering all color planes of the image.
- NPCR (number of pixel (bit) change rate) calculates the percentage of bits that differ between two images with respect to the total number of bits in the images. It is desirable that the NPCR between the original and the encrypted image is as high as possible to 50%. Note that the acronym NPCR was preserved to maintain consistency with the well-known parameter from image processing, but in fact it could have been referred to as NBCR, being a bit by bit comparison.To calculate NPCR at the bit level, two images are considered—one corresponding to the original image and the other to the encrypted image, denoted as X and Y, respectively. Each pixel value is converted to its binary representation, and the bit strings of the original and encrypted images are compared. A bipolar matrix D, with the same dimensions as X and Y, is used to calculate the difference. The value of is determined by comparing and . If the bit strings of and differ, then ; otherwise, .The formula for calculating NPCR is as follows:where:The larger the NPCR value, the more significant the differences between the original and encrypted images at the bit level.
- UACI (unified average changing intensity) measures the average change in pixel intensity between the two images (8) and the higher it is, the better it is from an encryption point of view.
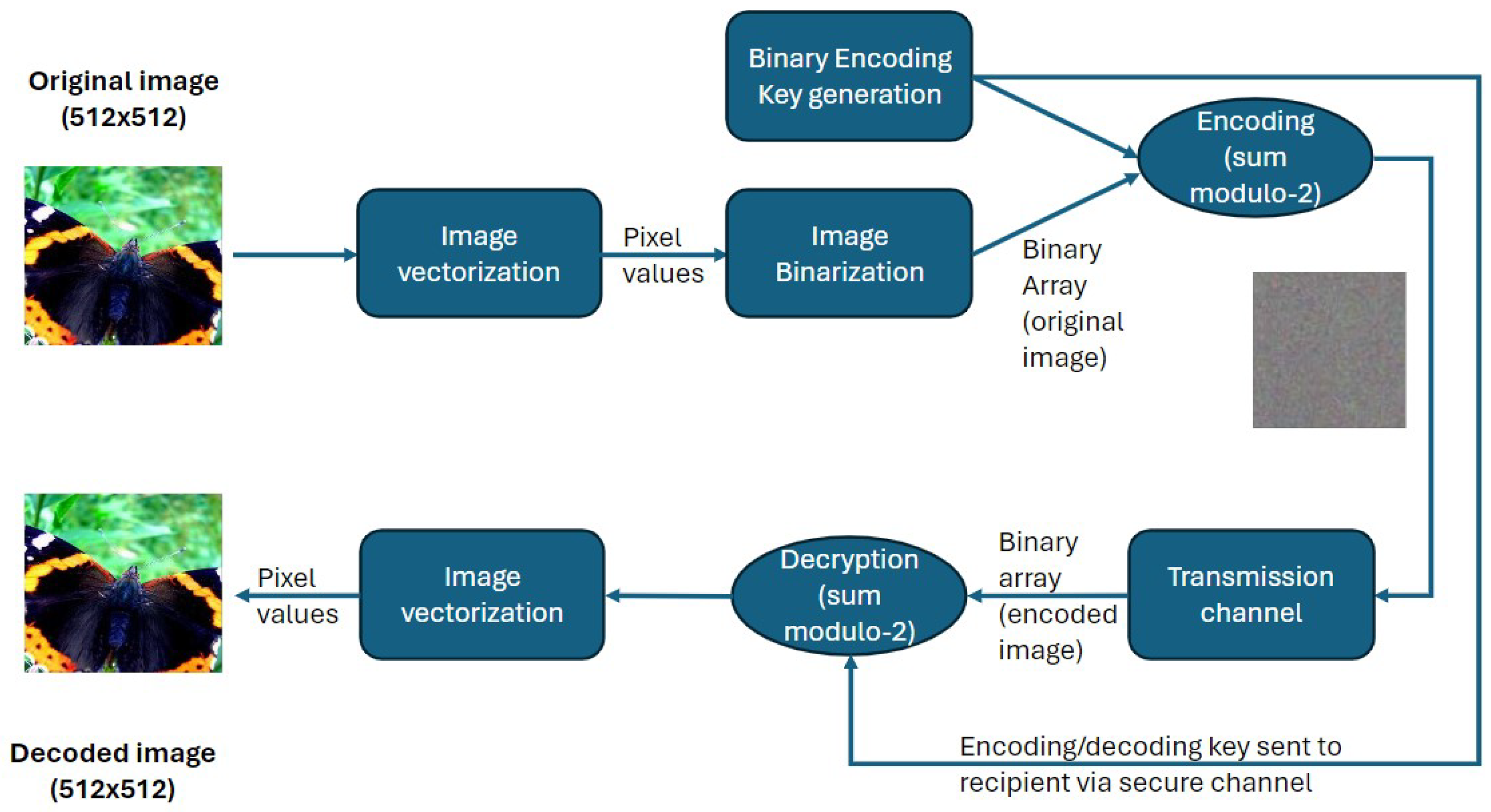
3. Proposed Image Encryption Scheme
- Step 1: Image preprocessing—vectorization and binarization
- Step 2: Binary encoding key generation
- Step 3: XOR-based encryption
- Step 4: Image reconstruction/decryption
- Hardware and Software Configuration
- Dataset Description
- Implementation notes and key synchronization
4. Experimental Results and Encryption Performance Analysis
- Encryption scheme: describes the process of encrypting an image using different chaotic systems and AES. This includes converting pixel values into binary arrays and applying encryption keys.
- Visual analysis: provides visual comparisons of the original, encrypted, and decrypted images for each encryption method, highlighting their effectiveness and any observable weaknesses.
- Histograms: analyzes the histograms of the original and encrypted images to assess how well each encryption method disperses pixel value distributions.
- Quantitative metrics: evaluates the encryption methods using metrics such as execution time, mean-squared error (MSE), peak signal-to-noise ratio (PSNR), encryption quality (EQ), number of pixel change rate (NPCR), and unified average changing intensity (UACI) to determine the overall effectiveness of each encryption technique.
5. Conclusions
- The tent and logistic maps achieved strong encryption quality and pixel randomness, often outperforming Henon in visual encryption clarity and NPCR/UACI scores.
- The AES algorithm remained the most efficient in terms of execution time and histogram uniformity, validating its role as a performance benchmark.
- Classical chaotic maps can produce satisfactory results when used with statistically independent sampling and binary key derivation.
- The integration of hyperchaotic systems and hybrid encryption structures;
- Robustness testing under noise, compression, and partial image loss;
- Energy-efficient implementations for embedded or real-time systems;
- Applying machine learning models to optimize chaotic parameter tuning dynamically.
Author Contributions
Funding
Data Availability Statement
Conflicts of Interest
References
- Zhang, B.; Liu, L. Chaos-Based Image Encryption: Review, Application, and Challenges. Mathematics 2023, 11, 2585. [Google Scholar] [CrossRef]
- Tusset, A.M.; Fuziki, M.E.K.; Balthazar, J.M.; Andrade, D.I.; Lenzi, G.G. Dynamic Analysis and Control of a Financial System with Chaotic Behavior Including Fractional Order. Fractal Fract. 2023, 7, 535. [Google Scholar] [CrossRef]
- Xu, X.; Li, J.; Zhu, Z.; Zhao, L.; Wang, H.; Song, C.; Chen, Y.; Zhao, Q.; Yang, J.; Pei, Y. A Comprehensive Review on Synergy of Multi-Modal Data and AI Technologies in Medical Diagnosis. Bioengineering 2024, 11, 219. [Google Scholar] [CrossRef] [PubMed]
- Lin, C.-F.; Lin, Y.-X.; Chang, S.-H. Medical Image Encryption Using Chaotic Mechanisms: A Study. Bioengineering 2025, 12, 734. [Google Scholar] [CrossRef]
- Hou, Y.-Y. Synchronization of Chaotic Systems and Its Application in Security Terminal Sensing Node of Internet of Things. Micromachines 2022, 13, 1993. [Google Scholar] [CrossRef] [PubMed]
- Alghamdi, Y.; Munir, A. Image Encryption Algorithms: A Survey of Design and Evaluation Metrics. J. Cybersecur. Priv. 2024, 4, 126–152. [Google Scholar] [CrossRef]
- Lawnik, M.; Moysis, L.; Volos, C. Chaos-Based Cryptography: Text Encryption Using Image Algorithms. Electronics 2022, 11, 3156. [Google Scholar] [CrossRef]
- El-Latif, A.A.A.; Ramadoss, J.; Abd-El-Atty, B.; Khalifa, H.S.; Nazarimehr, F. A Novel Chaos-Based Cryptography Algorithm and Its Performance Analysis. Mathematics 2022, 10, 2434. [Google Scholar] [CrossRef]
- Hamida Alrekaby, S.N.; Khodher, M.A.A.; Adday, L.K.; Aljuaidi, R. Secure Image Transmission Using Multilevel Chaotic Encryption and Video Steganography. Algorithms 2025, 18, 406. [Google Scholar] [CrossRef]
- Zolfaghari, B.; Koshiba, T. Chaotic Image Encryption: State-of-the-Art, Ecosystem, and Future Roadmap. Appl. Syst. Innov. 2022, 5, 57. [Google Scholar] [CrossRef]
- Feng, W.; Zhang, K.; Zhang, J.; Zhao, X.; Chen, Y.; Cai, B.; Zhu, Z.; Wen, H.; Ye, C. Integrating Fractional-Order Hopfield Neural Network with Differentiated Encryption: Achieving High-Performance Privacy Protection for Medical Images. Fractal Fract. 2025, 9, 426. [Google Scholar] [CrossRef]
- Li, H.; Yu, S.; Feng, W.; Chen, Y.; Zhang, J.; Qin, Z.; Zhu, Z.; Wozniak, M. Exploiting Dynamic Vector-Level Operations and a 2D-Enhanced Logistic Modular Map for Efficient Chaotic Image Encryption. Entropy 2023, 25, 1147. [Google Scholar] [CrossRef]
- Feng, W.; Zhang, J.; Chen, Y.; Qin, Z.; Zhang, Y.; Ahmad, M.; Wozniak, M. Exploiting Robust Quadratic Polynomial Hyperchaotic Map and Pixel Fusion Strategy for Efficient Image Encryption. Expert Syst. Appl. 2024, 246, 123190. [Google Scholar] [CrossRef]
- Shi, L.; Li, X.; Jin, B.; Li, Y. A Chaos-Based Encryption Algorithm to Protect the Security of Digital Artwork Images. Mathematics 2024, 12, 3162. [Google Scholar] [CrossRef]
- Chang, H.; Wang, E.; Liu, J. Research on Image Encryption Based on Fractional Seed Chaos Generator and Fractal Theory. Fractal Fract. 2023, 7, 221. [Google Scholar] [CrossRef]
- Huang, L.; Huang, Q.; Chen, H.; Cai, S.; Xiong, X.; Yang, J. A Novel One-Dimensional Chaotic System for Image Encryption in Network Transmission Through Base64 Encoding. Entropy 2025, 27, 513. [Google Scholar] [CrossRef]
- Zhang, H.; Feng, X.; Sun, J.; Yan, P. Chaotic Image Security Techniques and Developments: A Review. Mathematics 2025, 13, 1976. [Google Scholar] [CrossRef]
- Premkumar, R.; Mahdal, M.; Elangovan, M. An Efficient Chaos-Based Image Encryption Technique Using Bitplane Decay and Genetic Operators. Sensors 2022, 22, 8044. [Google Scholar] [CrossRef] [PubMed]
- Zhao, Y.; Shi, Q.; Ding, Q. Cryptanalysis of an Image Encryption Algorithm Using DNA Coding and Chaos. Entropy 2025, 27, 40. [Google Scholar] [CrossRef]
- Zhu, C.; Wang, G.; Sun, K. Improved Cryptanalysis and Enhancements of an Image Encryption Scheme Using Combined 1D Chaotic Maps. Entropy 2018, 20, 843. [Google Scholar] [CrossRef]
- Zhu, C.; Wang, G.; Sun, K. Cryptanalysis and Improvement on an Image Encryption Algorithm Design Using a Novel Chaos Based S-Box. Symmetry 2018, 10, 399. [Google Scholar] [CrossRef]
- Badea, B.; Vlad, A. Revealing Statistical Independence of Two Experimental Data Sets. In An Improvement on Spearman’s Algorithm, Lecture Notes in Computer Science, Vol. 3980 (ICCSA 2006); Springer: Berlin/Heidelberg, Germany, 2006; pp. 1166–1176. ISSN 0302-9743. [Google Scholar]
- Vaduva, A.; Vlad, A.; Badea, B. Evaluating the Performance of a Test-Method for Statistical Independence Decision in the Context of Chaotic Signals. In Proceedings of the 2016 International Conference on Communications (COMM), Bucharest, Romania, 9–11 June 2016; pp. 417–422. [Google Scholar] [CrossRef]
- Dinu, A.; Frunzete, M. The Lorenz Chaotic System, Statistical Independence and Sampling Frequency. In Proceedings of the 2021 International Symposium on Signals, Circuits and Systems (ISSCS), Iasi, Romania, 15–16 July 2021; pp. 1–4. [Google Scholar] [CrossRef]
- Dinu, A.; Frunzete, M. Singularity, Observability and Statistical Independence in the Context of Chaotic Systems. Mathematics 2023, 11, 305. [Google Scholar] [CrossRef]
- Luca, A.; Vlad, A.; Badea, B.; Frunzete, M. A Study on Statistical Independence in the Tent Map. In Proceedings of the IEEE International Symposium on Signals, Circuits and Systems (ISSCS 2009), Iasi, Romania, 9–10 July 2009; IEEE: New York, NY, USA; pp. 1–4. [Google Scholar] [CrossRef]
- Vlad, A.; Ilyas, A.; Luca, A. Unifying Running-Key Approach and Logistic Map to Generate Enciphering Sequences. Ann. Telecommun. 2013, 68, 179–186. [Google Scholar] [CrossRef]
- Dinu, A.; Vlad, A. The Compound Tent Map and the Connection Between Gray Codes and the Initial Condition Recovery. UPB Sci. Bull. Ser. A Appl. Math. Phys. 2014, 76, 17–28. Available online: https://www.scientificbulletin.upb.ro/rev_docs_arhiva/full72a_882955.pdf (accessed on 20 July 2024).
- Khairullah, M.K.; Alkahtani, A.A.; Bin Baharuddin, M.Z.; Al-Jubari, A.M. Designing 1D Chaotic Maps for Fast Chaotic Image Encryption. Electronics 2021, 10, 2116. [Google Scholar] [CrossRef]
- Daoui, A.; Yamni, M.; Chelloug, S.A.; Wani, M.A.; El-Latif, A.A.A. Efficient Image Encryption Scheme Using Novel 1D Multiparametric Dynamical Tent Map and Parallel Computing. Mathematics 2023, 11, 1589. [Google Scholar] [CrossRef]
- Abikoye, O.C.; Haruna, A.D.; Abubakar, A.; Akande, N.O.; Asani, E.O. Modified Advanced Encryption Standard Algorithm for Information Security. Symmetry 2019, 11, 1484. [Google Scholar] [CrossRef]
- Kaggle. Available online: https://www.kaggle.com/ (accessed on 21 December 2024).











| SYSTEM | MSE | MSE LOW | MSE HIGH | PSNR | PSNR LOW | PSNR HIGH | NPCR | NPCR LOW | NPCR HIGH |
|---|---|---|---|---|---|---|---|---|---|
| AES | 105.51 | 105.37 | 105.66 | 27.90 | 27.89 | 27.90 | 49.98 | 49.95 | 50.01 |
| HENON | 133.39 | 133.30 | 133.48 | 26.88 | 26.87 | 26.89 | 45.18 | 45.17 | 45.19 |
| LOGISTIC | 119.02 | 118.99 | 119.05 | 27.37 | 27.36 | 27.38 | 54.12 | 54.11 | 54.13 |
| TENT | 119.29 | 119.25 | 119.32 | 27.36 | 27.35 | 27.37 | 54.53 | 54.52 | 54.54 |
| SYSTEM | UACI | UACI LOW | UACI HIGH | EQ | EQ LOW | EQ HIGH | TIME | TIME LOW | TIME HIGH |
|---|---|---|---|---|---|---|---|---|---|
| AES | 26.24 | 25.81 | 26.67 | 634.61 | 593.89 | 675.33 | 0.01 | 0.00 | 0.02 |
| HENON | 23.72 | 23.71 | 23.73 | 714.97 | 714.96 | 714.98 | 0.72 | 0.71 | 0.73 |
| LOGISTIC | 28.41 | 28.40 | 28.42 | 671.91 | 671.90 | 671.92 | 0.43 | 0.42 | 0.44 |
| TENT | 28.63 | 28.62 | 28.64 | 672.97 | 672.96 | 672.98 | 0.42 | 0.40 | 0.43 |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Dinu, A.; Frunzete, M. Image Encryption Using Chaotic Maps: Development, Application, and Analysis. Mathematics 2025, 13, 2588. https://doi.org/10.3390/math13162588
Dinu A, Frunzete M. Image Encryption Using Chaotic Maps: Development, Application, and Analysis. Mathematics. 2025; 13(16):2588. https://doi.org/10.3390/math13162588
Chicago/Turabian StyleDinu, Alexandru, and Madalin Frunzete. 2025. "Image Encryption Using Chaotic Maps: Development, Application, and Analysis" Mathematics 13, no. 16: 2588. https://doi.org/10.3390/math13162588
APA StyleDinu, A., & Frunzete, M. (2025). Image Encryption Using Chaotic Maps: Development, Application, and Analysis. Mathematics, 13(16), 2588. https://doi.org/10.3390/math13162588






