Abstract
The conventional supply chain management has undergone major advancements following IoT-enabled revolution. The IoT-enabled drones in particular have ignited much recent attention for package delivery in logistics. The service delivery paradigm in logistics has seen a surge in drone-assisted package deliveries and tracking. There have been a lot of recent research proposals on various aspects of last-mile delivery systems for drones in particular. Although drones have largely changed the logistics landscape, there are many concerns regarding security and privacy posed to drones due to their open and vulnerable nature. The security and privacy of involved stakeholders needs to be preserved across the whole chain of Supply Chain Management (SCM) till delivery. Many earlier studies addressed this concern, however with efficiency limitations. We propose a Physical Uncloneable Function (PUF)-based secure authentication protocol (PSL-IoD) using symmetric key operations for reliable last-mile drone delivery in SCM. PSL-IoD ensures mutual authenticity, forward secrecy, and privacy for the stakeholders. Moreover, it is protected from machine learning attacks and drone-related physical capture threats due to embedded PUF installations along with secure design of the protocol. The PSL-IoD is formally analyzed through rigorous security assessments based on the Real-or-Random (RoR) model. The PSL-IoD supports 26.71% of enhanced security traits compared to other comparative studies. The performance evaluation metrics exhibit convincing findings in terms of efficient computation and communication along with enhanced security features, making it viable for practical implementations.
Keywords:
authentication; Internet of Things (IoT); security; drones; logistics; supply chain management MSC:
68P25; 94A60
1. Introduction
The logistics industry is experiencing digital transformation incessantly. With the digital transformation, the logistics industry has leveraged many advanced technologies such as Artificial Intelligence, Big Data, blockchain, IoT-enabled drones, and sophisticated security algorithms, to improve efficiency, reliability and reduce overheads [1]. In addition, optimizing other factors in supply chain management, real-time monitoring of logistics, and instant response to emergency situations is one of the growing concerns. The trustworthy, flexible, and efficient last-mile delivery operations in smart logistics may not only enhance customer experience but also bring resilience to the whole supply chain management system. The accessibility for real-time data to all the supply chain segments is the key to innovative and intelligent logistics [2]. These real-time mechanisms of collaboration across the whole supply chain largely help to improve the operational efficiency of the logistics. Earlier, conventional logistics corporations in the late 20th century counted on manual record keeping as well as inventory management. The ICT developments such as barcode and radio frequency identification (RFID) were introduced further to improve the logistics in the 21st century [3]. Currently, IoT-enabled drones along with AI and blockchain technologies considerably improve the efficiency and reliability of real-time data collection in logistics. Drones carry IoT-based sensors for collecting and examining the physical phenomenon such as water level, wind flow, temperature, and humidity. Drone may be inducted in diverse nature of requirements for some organizations, e.g., rescue and surveillance, health management, traffic monitoring, disaster framework, traffic monitoring, precision farming, etc. The communicating unit of an unmanned aerial vehicle (UAV), also termed as drone, forwards messages to a ground controlling station for further computations and decisions [4].
The use of drones for last-mile package delivery in smart logistics can largely reduce the delivery time for rural terrain with underdeveloped infrastructure or catastrophic terrain where traffic cannot make its way effortlessly [5]. Nonetheless, the communication of drones depends on open wireless connectivity which renders it vulnerable to many inherent security attacks. There might be active as well as passive adversaries. The passive nature of adversaries is that they eavesdrop communication messages, while the active nature of adversaries is that they may intercept and delete messages or manipulate through forging it by generating false emergency fire alerts causing heavy losses. The distributed and autonomous drone systems embody a dynamic and critical category of IoT networks exhibiting mobility, irregular connectivity, and resource constraints which collectively result in increased attack surface. Similarly, delivery drones for last-mile delivery in supply chain management exhibiting similar constraints are prone to many security threats comprising the client’s privacy and physical drone assaults [6,7]. Such potential threats could be proactively countered with suitable security fixes comprising the design of effective cryptographic algorithms for various scenarios in logistics management. As these drones are multi-purpose devices and may cover a broad range of applications requiring Wireless Sensor Network (WSN)-based aerial operations, the delivery drones need to be securely programmed so that these can be restricted for last-mile delivery activities [8]. There is always a chance that the drones could be distracted from their specified roles of delivery activities if manipulated by malicious operators; thus, it would be desirable to restrict the drones’ oriented communication channels within the defined limits of logistics operations. Due to involvement of public channel, the delivery drones are largely vulnerable to replay, Man-in-the-Middle (MiTM), physical capture threats, and forgery threats. The drones carry critical secrets in their memory which may be examined or stolen in case of physical capture by malicious adversaries. These risks may be curtailed by embedding modern hardware circuits such as Physical Unclonable Function (PUF) in the drones [9]. These circuits behave in a certain manner that provides a unique output against any number, while each circuit produces a unique output due to its internal distinctive construction. It is unclonable, which is why it acts as a biometric fingerprint for any particular circuit as well as drone. There are many authentication protocols that employ PUF for ensuring physical security; however, its use does not guarantee the protocol is resilient [10,11,12]. A protocol needs to be designed that is not only privacy preserving but also immune to all known threats, including machine learning attacks and physical capture attacks. Therefore, considering this scenario, we propose an anonymous and efficient PUF-enabled authenticated key exchange mechanism for drone-oriented smart logistics.
1.1. Contribution
Although the drone-led administration of logistics seems to be promising, it carries many inherent security risks. The adversaries may disrupt the whole supply chain management by gaining physical access to the resources of drone. To overcome these concerns, a resiliently crafted authenticated key exchange method is crucial. It not only certifies mutual authenticity and generation of a commonly agreed session key among the members but is also resistant to most of the known threats. We can witness numerous key agreement mechanisms for drone authentication; however, most of these schemes do not cover PUF-based embedded drone communication scenarios with respect to supply chain management or logistics. A few schemes lately could be witnessed for the drone-oriented PUF-based access control technique, with many drawbacks, however. Thus, more drone-led PUF-embedded authentication schemes need to be tailored for logistics systems. The key contribution can be illustrated as follows:
- A privacy-preserving PUF-based drone key agreement scheme (PSL-IoD) is proposed for smart logistics to deliver packages with endorsement to the ultimate customer in the supply chain. The peculiar design of the scheme with a particular emphasis on prudent use of CRP-pairs makes the CRP pairs inaccessible to the adversary on a public channel that facilitates evading machine learning attacks.
- The PSL-IoD employs symmetric key-based lightweight crypto-primitives not only to align with low-end computational resources of the drone but to also boost efficiency of the delivery process in logistics.
- The security properties of PSL-IoD are formally analyzed using the Real-or-Random (RoR)-based random oracle model.
- The performance evaluation of PSL-IoD exhibits that the key agreement scheme is not only efficient in terms of computation and communication than other related schemes but also secure against forgery and physical capture attacks.
1.2. Scheme Organization
The organization of the scheme is mentioned as follows: Section 2 delineates the related work. Section 3 presents the preliminary details along with network architecture and threat model. The proposed model is demonstrated in Section 4. Section 5 describes informal and formal security analysis. Section 6 illustrates the comparative analysis and performance of various schemes. Section 7 concludes the scheme.
2. Literature Review
This section illustrates the literature on the security of IoT-enabled drones as well as logistics in the last few years. Without resolving security and privacy issues, the potential of smart logistics can never be realized in its full capacity. We can observe many promising key agreement protocols as of late [12,13,14,15,16,17,18,19,20,21,22,23,24,25,26,27,28,29,30,31,32,33,34]. In this regard, Koubaa et al. [12] designed an IoD-based authenticated key agreement (AKA) technique for reliable use of resources. Then, Gupta et al. [13] and Lin et al. [14] presented few security issues in IoD-based protocol development with a focus on the requirement of mutual key agreement among the participants. Then, Turkanovic et al. [15] demonstrated a key exchange method related to IoT system. Further, Farash et al. [16] identified few attacks such as session key guessing, impersonation threat, and stolen smart card attack in [15] and proposed an enhanced scheme. Thereafter, Amin et al. [17] pointed out few weaknesses including the offline password guessing attack, forgery, and the ephemeral secret leakage attack in [18]. Bera et al. [18] designed a drone-oriented Elliptic Curve Cryptography (ECC)-based key agreement scheme using blockchain as a central authority. Likewise, Li et al. [19] put forward an ECC-based key agreement protocol for the IoT network; nonetheless, the scheme was not cost-effective due to PKI-based encryption and computational-intensive crypto-primitives. Next, Ever et al. [20] presented an IoD-based key agreement protocol, although it was not only susceptible to physical drone capture attack but also expensive for costly bilinear pairing operations. Thereafter, Cho et al. [21] presented a certificate-oriented authentication scheme for the IoD network; however, the scheme was not protected from the temporary secret key exposure threat. Then, Husnain et al. [22] put forward another lightweight drone-based authentication scheme for smart cities; however, it was not immune to physical drone capture threats. Afterwards, Srinivas et al. [23] demonstrated an IoD-based key agreement scheme comprising temporal credentials. Ali et al. [24] reported that scheme [23] does not sustain privacy and mutual authenticity among participants. Then, Wazid et al. [25] presented an anonymous key agreement scheme for IoD, although it was prone to privileged insider threat in addition to its inability to support mutual authentication for its legal members. Also, Zhang et al. [26] designed an identity-based cryptography (IBC) key agreement scheme from an IoD ecosystem. However, the requirement of storage for the master key in the memory calls into question the practical viability of [26]. Nikooghadam et al. [27] designed an AKA scheme for an IoD-based smart city; however, it was susceptible to impersonation and physical capture threats.
Thereafter, many schemes related to the IoD network presented AKA protocols countering physical counter threats. Gope and Sikdar [28] presented an anonymous PUF-based AKA scheme. Nonetheless, it was prone to the de-synchronization threat as it requires maintaining updated pseudonym identities to keep synchronization among entities. Likewise, Alladi et al. [29] designed a PUF-based AKA technique for a UAV-to-Ground station supporting UAV’s resistance to physical capture threats. Malik et al. [30] also designed a PUF-oriented 5G drone authentication method supporting resistance to physical capture attacks for the drone. Then, Yu et al. [31] designed another PUF-based biometric authentication scheme for smart city drones. Nevertheless, the protocol was faulty due to flaws in the drone registration procedure that hampers the construction of a common session key between legal members. Zhang et al. [33] provided a lightweight PUF-based authentication protocol for IoD. However, it was vulnerable to denial-of-service (DoS) and replay attacks. Park et al. [32] presented another PUF-based AKA technique for the IoD network; however, it was susceptible to Man-in-the-Middle (MiTM) attacks. Badshah et al. [34] designed an ultra-lightweight AKA technique for drones, although it was prone to insider threats in which the privileged insider can recover the user-oriented verifiers and pseudonyms from publicly intercepted contents. More recently, Sousa and Gondim [35] presented a multi-factor user authentication scheme for the IoD network, although this scheme was prone to DoS attacks. Thus, it can be deduced that most of the schemes for drones are prone to several vulnerabilities for the open nature of drone deployment. The above schemes demonstrate that many schemes utilize ECC- as well as ID-based costly operations for authentication of IoT-enabled drones from the ground controlling station, while the rest of the schemes employed symmetric key operations from drone authentication. A few schemes used PUF to evade physical device or drone capture threats. However, despite the use of costly operations, lightweight symmetric, and PUF-based circuits, most of these schemes are vulnerable to several known threats as discussed above, which requires construction of novel drone-based AKA solutions to adapt with current needs of the time.
It can be seen that the design of most of the previous IoT-based authentication schemes is based on costly asymmetric cryptography. However, as of late, we can observe several lightweight PUF-oriented drone authentication protocols using low-cost primitives, although they are vulnerable to many known threats including impersonation, pivileged insider threat, physical device capture threat, Man-in-the-Middle threats, machine learning attacks, etc. Thus, existing drone access control techniques are not meeting the up-to-date requirements of the real-world drone deployments and require even more resilient lightweight PUF-enabled schemes. The brief summary is depicted in Table 1.

Table 1.
Summary of related work.
3. Preliminaries
This section discusses preliminaries with respect to Physical Unclonable Function, network architecture, and the adversary model as demonstrated below.
3.1. Physical Unclonable Function
The Physical Unclonable Function (PUF) is a new hardware-oriented circuit exploiting the physical properties of the chip that lets the circuit behave in a unique way offering an identity-based authentication to the device equivalent to fingerprint [32,33]. These properties are immensely hard to replicate in a new chip, making it a viable option for sophisticated security systems based on Internet of Things, drones, smart gadgets, and overall network security. The microscopic deviations are noticeable in the chip, while even slight changes and irregularities make the chip largely unusable and resilient against physical attacks. The PUF function is , where D depicts a device carrying and n1 and n2 show the size of strings embedded for the device. The function bears the following properties:
- It is very complicated to clone or replicate the behavior of any existing PUF chip.
- It is convenient and easy to compute.
- Its result is constantly impulsive.
- It carries a physical micro structure which is mostly a constituent component in other devices.
- Any hardware or equipment carrying this chip receive enhanced security due to inherent device variations.
3.2. Network Architecture
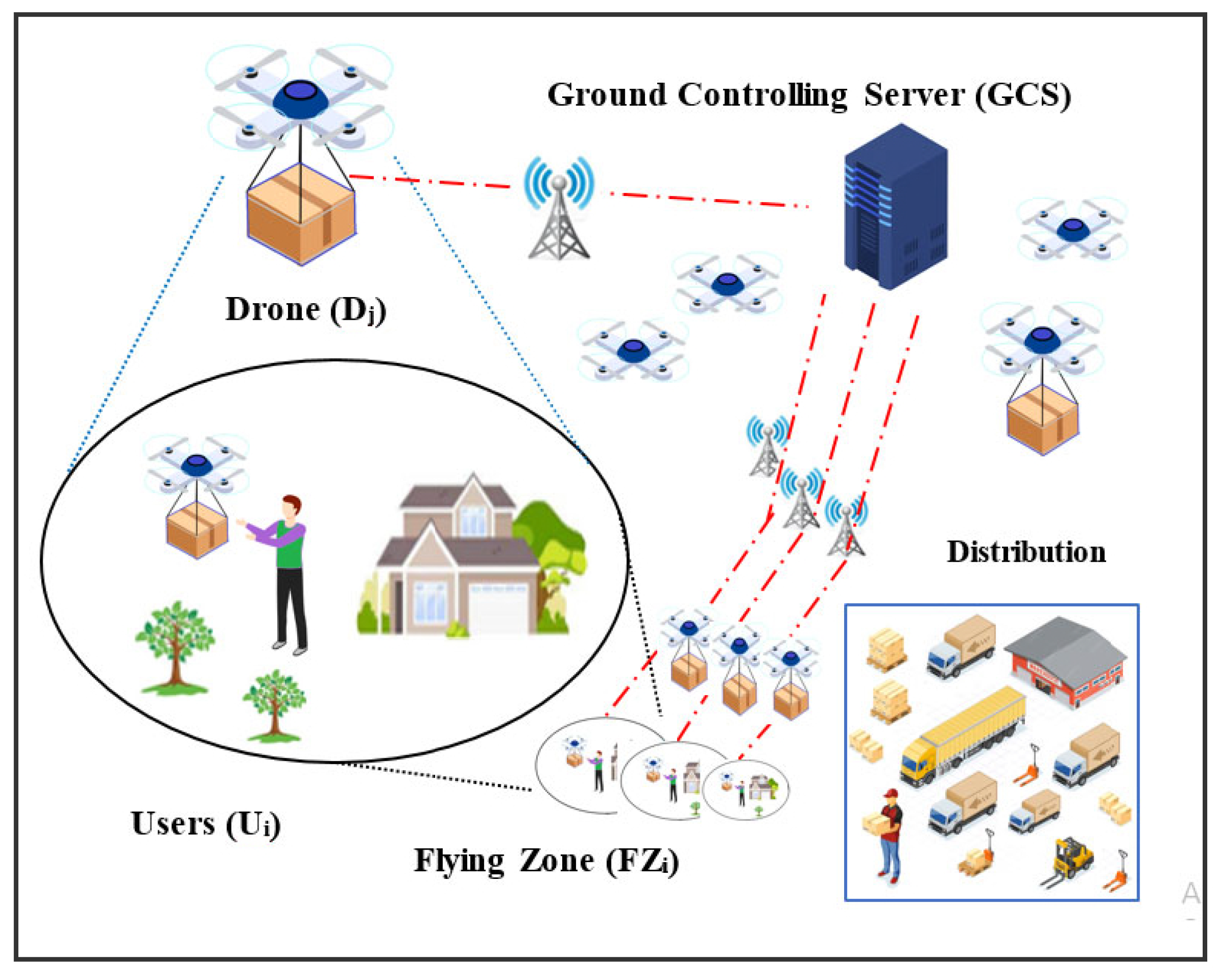
The network architecture for PSL-IoD consists of three distinct entities: (1) user (Ui), (2) ground controlling server (GCS), and (3) drone (Dj) as graphically exhibited in Figure 1. In this model, the GCS must register all users Ui and drones Dj assigned to corresponding flying zones. Although the users can normally track the status of their cargo or delivery packages in the whole supply chain process, this network model takes into consideration the last-mile delivery segment between drone and user with the help of GCS. Alternatively, the drones as a last-mile delivery option in supply chain management receive an authenticated session established with the ultimate customer/user (Ui) by creating an agreed session key SK with the assistance of GCS and deliver the packages after adopting due course of authentication procedures. The details of these entities are illustrated below.
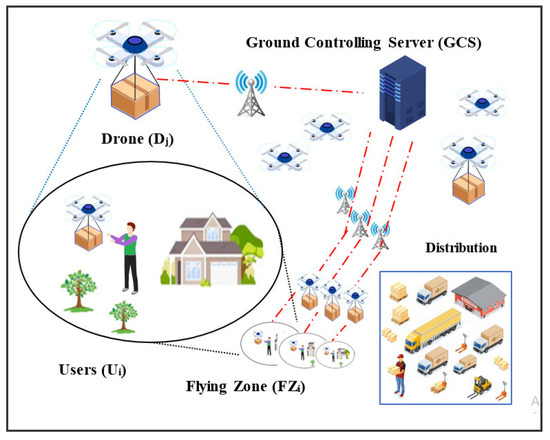
Figure 1.
Network architecture.
User (Ui). The Ui registers itself with GCS and receives secret credentials in return. Then, it obtains its cargo delivered from the drone entity after establishing a mutual authentication procedure with the help of GCS. The commonly agreed SK is used to communicate with the delivery drone for ultimate service.
Ground Controlling server (GCS). The GCS acts as a trusted authority responsible for registering drones and users. It also ensures that both entities mutually authenticate one another and establish an agreed session key for trusted execution of last-mile delivery.
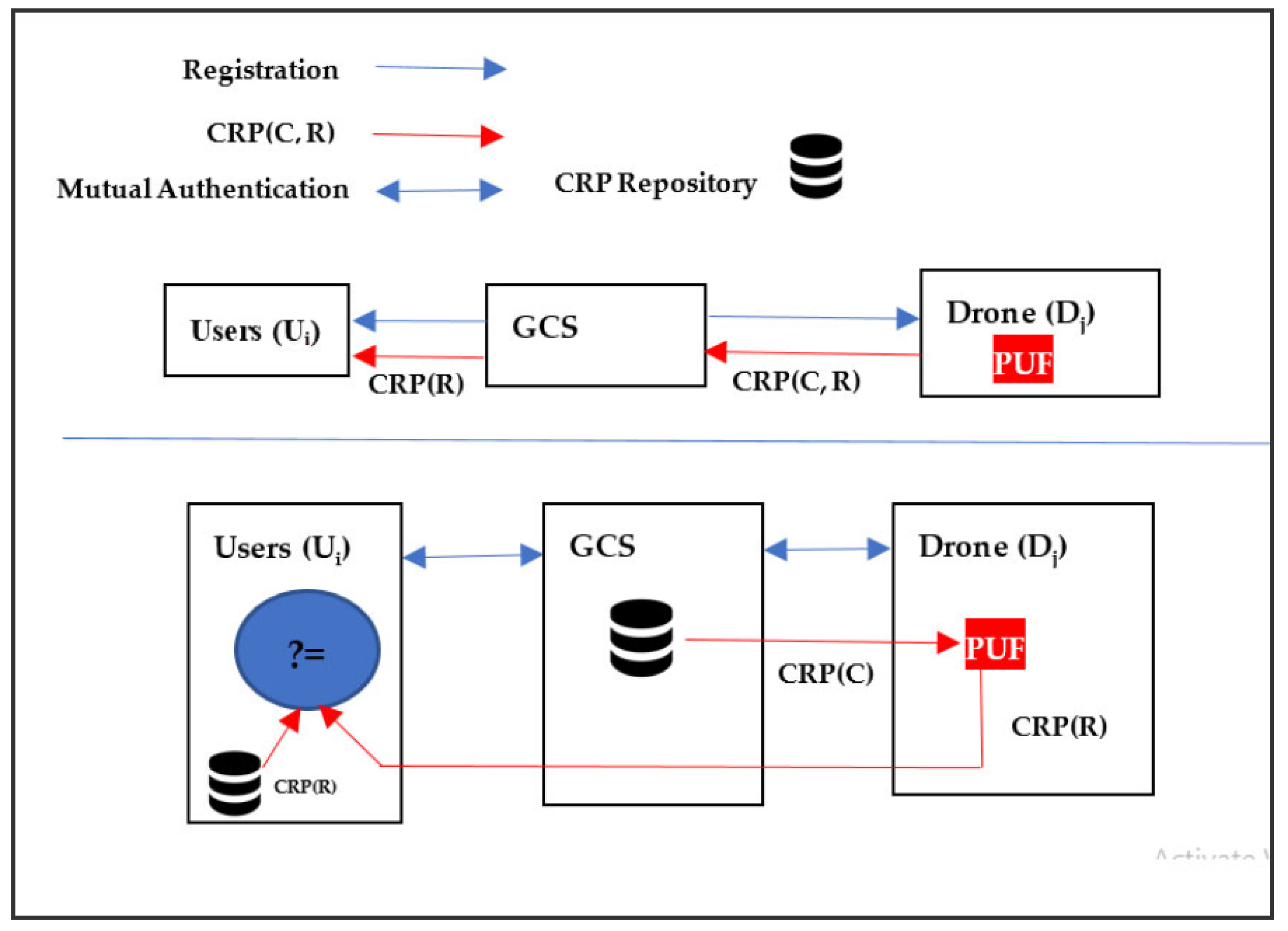
Drone (Dj): The Dj also becomes registered with GCS and receives secret credentials in return. In addition, it is embedded with the PUF circuit to ensure physical protection from tampering procedures on the part of the adversary. The drone comes into contact with the user after the mutual authentication process facilitated by GCS being online. The commonly agreed SK between user and delivery drone is used to communicate and negotiate for ultimate service. The communication framework is exhibited in Figure 2.
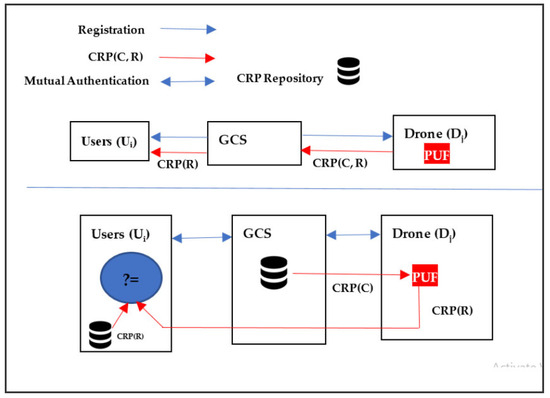
Figure 2.
Communication framework.
3.3. Adversary Model
An adversary model delineates the assumed capability of the adversary to launch attacks on the contributed protocol. It defines what an adversary can do and what resources it can have. Considering the capability of the state-of-the-art adversary, the protocol needs to be designed. We assume two adversary models, i.e., (1) the Dolev–Yao (DY) model propounded by Dolev and Yao [36] and (2) the Canetti–Krawczyk (CK) model introduced by Canetti and Krawczyk [37]. Both of the models collectively assume the capabilities of adversary . The DY model acts as a basic theoretical model used extensively by the researchers in security and cryptography. According to the DY model, possess the capability to intercept, block, delete, and forward messages, although it lacks the ability of decrypting enciphered messages. may initiate replay or retransmission attacks by intercepting the messages. may also initiate impersonation threats after eavesdropping personal data of the user. The CK model extends the capability of the adversary beyond the DY-based threat model by incorporating more complicated operations and severe breaches such as exposure to ephemeral secret keys and random nonces.
4. Proposed Technique (PSL-IoD)
We suggest a novel lightweight and privacy preserving PUF-based authenticated key agreement technique (PSL-IoD) for supply chain management encompassing three communication round trips. The session key is mutually developed in the end of the protocol between user Ui and delivery drone Dj with the aid of GCS. Table 2 exhibits the notations used in PSL-IoD. The PSL-IoD consists of three phases: (1) drone enrollment process, (2) user enrollment process, and (3) mutual authenticating process. The detailed narrative of each phase is mentioned below.

Table 2.
Symbols with definitions.
4.1. Drone Enrolment Process
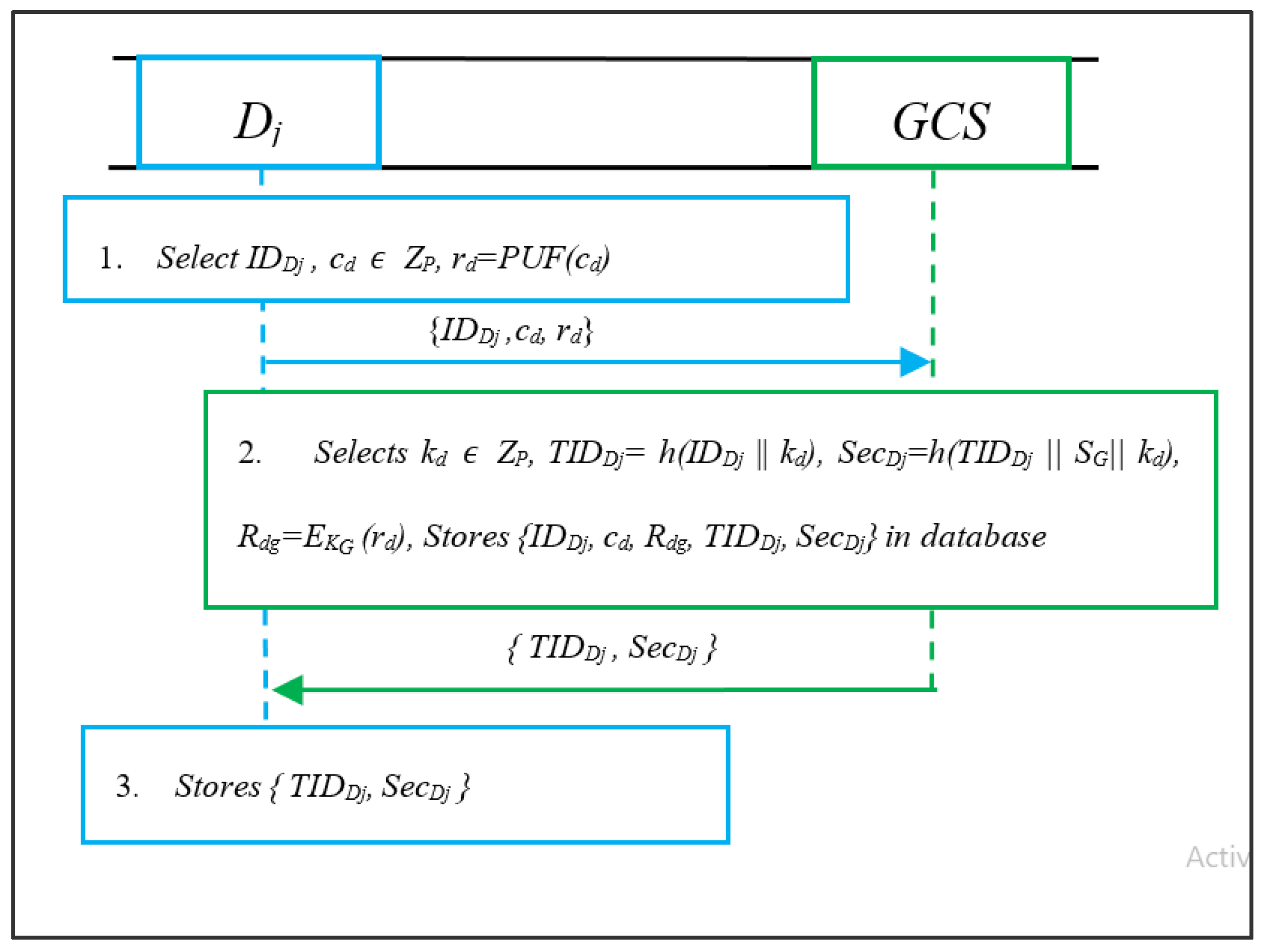
The drone Dj is registered by GCS on a secure channel. For this purpose, the Dj initiates the following procedure:
- The Dj selects its identity IDDj, generates a random challenge cd ZP, and computes rd = PUF(cd). Then, it submits registration request {IDDj, cd, rd} to GCS.
- The GCS, upon receiving the request, selects kd ZP and computes TIDDj = h(IDDj||kd), SecDj = h(TIDDj||SG||kd) and Rdg = EKG (rd). It stores {IDDj, cd, Rdg, TIDDj, SecDj} in its database and submits {TIDDj, SecDj} to Dj as shown in Figure 3.
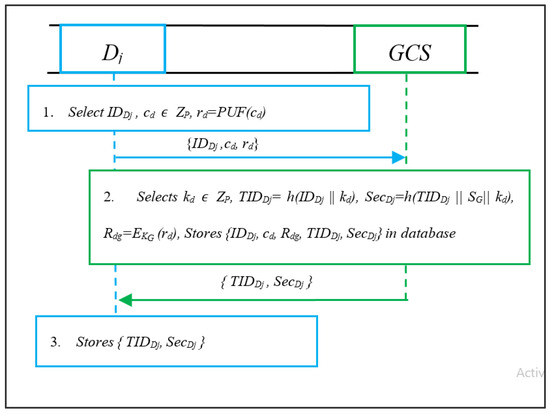 Figure 3. Registration of drone (Dj).
Figure 3. Registration of drone (Dj). - Dj, upon receiving the parameters, stores them in its memory safely.
4.2. User Enrollment Process
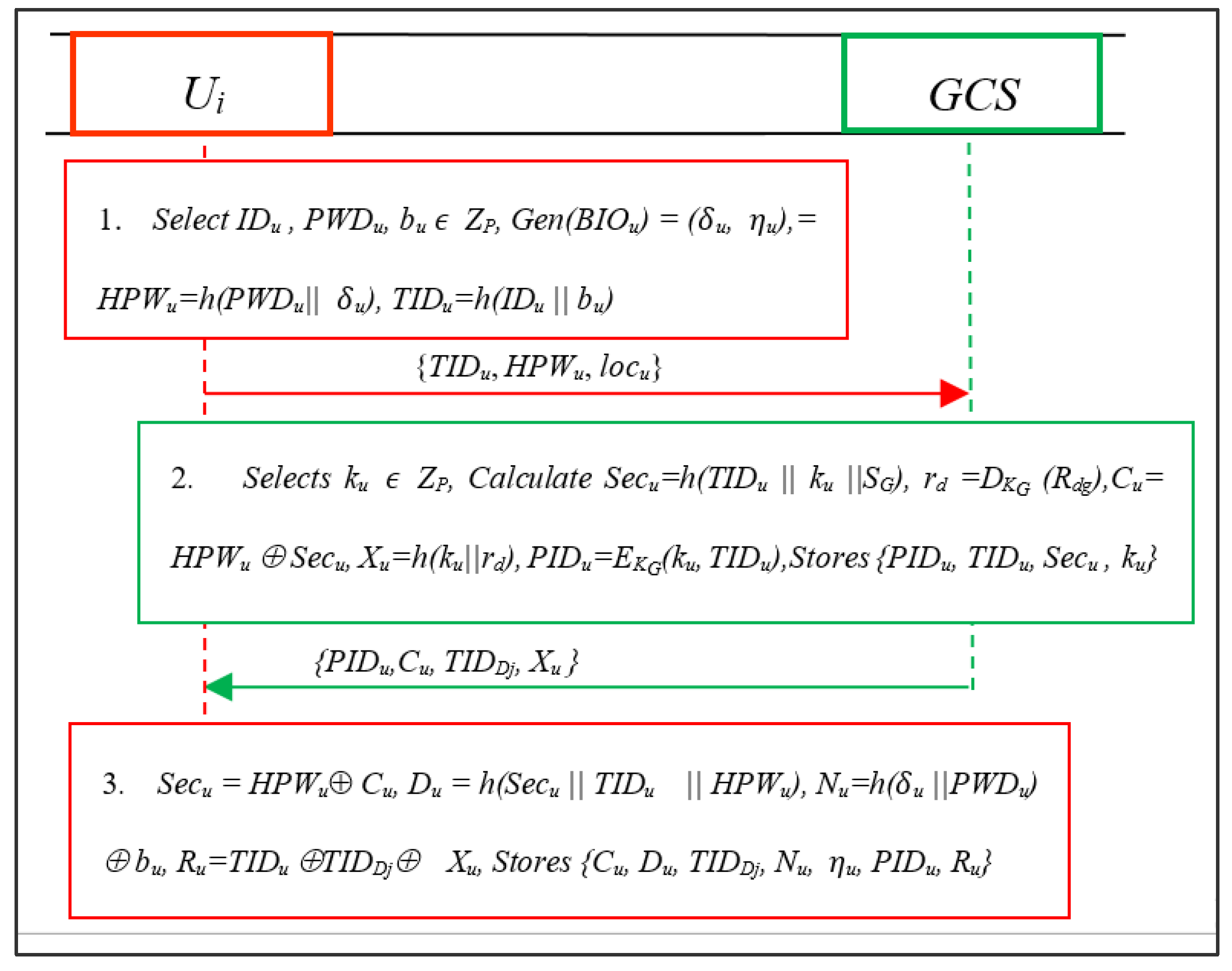
The user Ui employs the following steps to register itself with GCS:
- The user selects its identity IDu, password PWDu, and a random integer bu ZP. Then, it computes Gen (BIOu) = (u, u), HPWu = h(PWDu||u), TIDu = h(IDu||bu). Then, Ui sends {TIDu, HPWu, locu} to the GCS using secure channel.
- The GCS selects a random integer ku ZP and calculates Secu = h(TIDu ||ku ||SG), rd = DKG (Rdg), Cu= HPWu ⊕ Secu, Xu = h(ku||rd), and PIDu = EKG(ku, TIDu). Then, it stores {PIDu, TIDu, Secu, ku} in a repository while sending {PIDu, Cu, TIDDj, Xu} to Ui to finalize the registration.
- Next, the Ui computes Secu = HPWu ⊕ Cu, Du = h(Secu||TIDu||HPWu), Nu = h(u ||PWDu) ⊕ bu, Ru = TIDu ⊕ TIDDj ⊕ Xu, and stores {Cu, Du, TIDDj, Nu, u, PIDu, Ru} parameters in the smart card safely as shown in Figure 4.
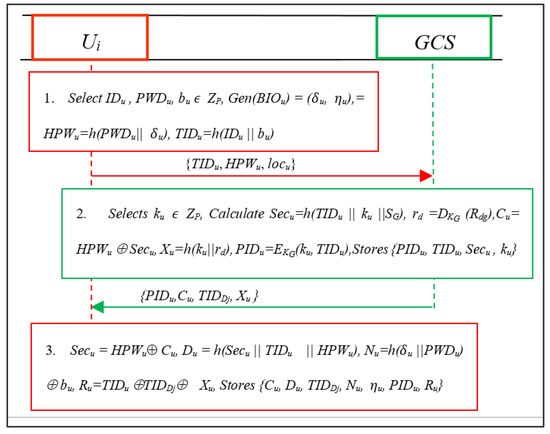 Figure 4. Registration of user (Ui).
Figure 4. Registration of user (Ui).
4.3. Mutual Authentication Process
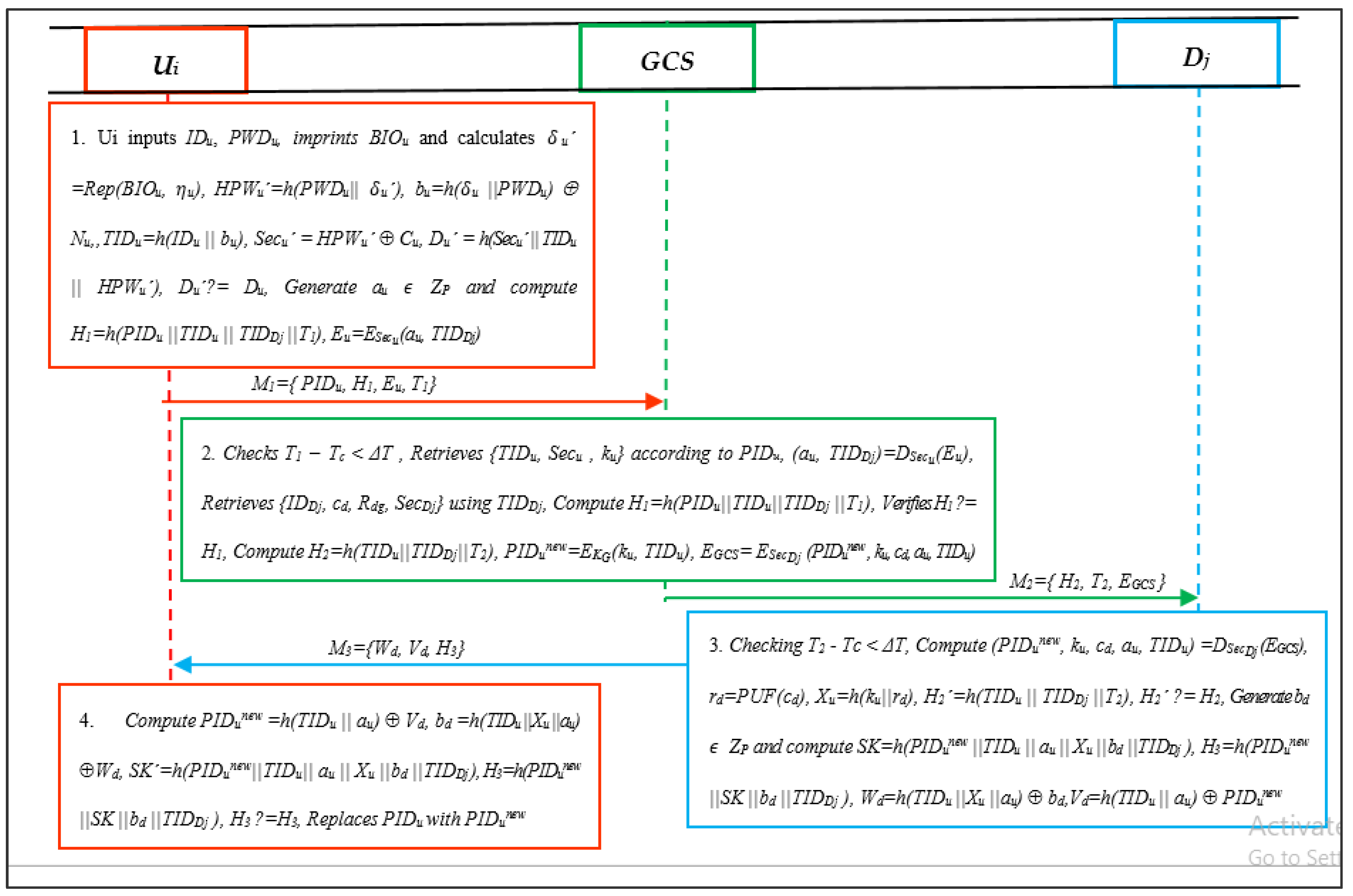
In this phase, the user verifies the drone on a public channel with the help of GCS. The Ui and Dj establish an agreed session key after utilizing all steps in this phase. This phase takes three round trips to complete the protocol, i.e., (1) Ui-to-GCS, (2) GCS-to-Dj, and (3) Dj-to-Ui. The steps incorporated in this process are explained below.
- Initially, the Ui inputs identity IDu and password PWDu and imprints a biometric BIOu. Next, it calculates u′ = Rep (BIOu, u), HPWu′ = h(PWDu||u′), bu = h(u||PWDu) ⊕ Nu, TIDu = h(IDu||bu), Secu′ = HPWu′ ⊕ Cu and Du′ = h(Secu′||TIDu||HPWu′). Then, it verifies Du′? = Du. If it is not true, Ui aborts. Otherwise, Ui generates au ZP, computes H1 = h(PIDu||TIDu||TIDDj||T1), Eu = ESecu (au, TIDDj), and submits M1 = { PIDu, H1, Eu, T1} to GCS.
- The GCS, after receiving the authentication request, checks the freshness of T1 using T1 − Tc < ΔT. Then, it retrieves {TIDu, Secu, ku} in line with PIDu, and computes (au, TIDDj) = DSecu (Eu). Then, it retrieves {IDDj, cd, rd, SecDj} using TIDDj, and computes H1 = h(PIDu||TIDu||TIDDj||T1) to verify H1 ? = H1. If it is not true, the GCS aborts. Otherwise, it computes H2 = h(TIDu || TIDDj ||T2), PIDunew = EKG(ku, TIDu), EGCS = ESecDj (PIDunew, ku, cd, au, TIDu) and submits M2 = {H2, T2, EGCS} to Dj for further verification as displayed in Figure 5.
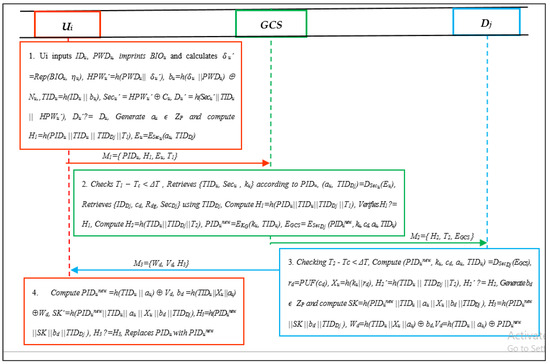 Figure 5. Proposed scheme (PSL-IoD).
Figure 5. Proposed scheme (PSL-IoD). - The Dj checks expiry of timestamp using T2 − Tc < ΔT. If it is fresh, it further calculates (PIDunew, ku, cd, au, TIDu) = DSecDj (EGCS), rd = PUF(cd), Xu = h(ku||rd), H2′ = h(TIDu||TIDDj||T2), and verifies H2′ ? = H2. In the case it is not true, it abandons the session. Otherwise, it generates bd ZP and computes SK = h(PIDunew||TIDu||au||Xu||bd||TIDDj), H3 = h(PIDunew||SK||bd||TIDDj), Wd = h(TIDu||Xu||au) ⊕ bd, and Vd = h(TIDu||au) ⊕ PIDunew. Then, it submits the message M3 = {Wd, Vd, H3} to Ui for final verification.
- The Ui, upon the receipt of M3, computes PIDunew = h(TIDu||au) ⊕ Vd, bd = h(TIDu||Xu||au) ⊕ Wd, SK′ = h(PIDunew||TIDu||au||Xu||bd||TIDDj) and H3 = h(PIDunew||SK||bd||TIDDj). Then, it verifies H3 ? = H3. If it is true, it validates Dj and replaces PIDu with PIDunew in its smart card.
5. Security Analysis
In this section, both informal and formal security analysis pertaining to PSL-IoD are comprehensively discussed.
5.1. Informal Security Analysis
- (a)
- Mutual Authenticity
In PSL-IoD, the Ui authenticates GCS as well as Dj on account of verification for the H3 parameter after computing H3 = h(PIDunew||SK||bd||TIDDj). Ui knows the fact that the session key SK′ = h(PIDunew||TIDu||au||Xu||bd||TIDDj) cannot be constructed by the adversary without compromising GCS and Dj entities and obtaining the secrets held with them. The au can only be extracted from Eu by the GCS entity having access to the shared secret Secu, while Xu = h(ku||rd) can only be computed by legal Dj having the specified PUF circuit. Likewise, GCS authenticates Ui on account of verification of H1 = h(PIDu||TIDu||TIDDj||T1); as it can discern, only a valid Ui has access to effective TIDu parameter. Similarly, Dj verifies the validity of Ui after checking the validity of the H2′ = h(TIDu||TIDDj||T2) parameter along with its freshness. Thus, the PSL-IoD ensures mutual authentication for all legitimate participants.
- (b)
- Anonymity and non-traceability
The PSL-IoD supports anonymity as the scheme does not propagate the original identity of the user on communication; rather, it submits the pseudonym identity TIDu to GCS for making itself authenticated. In addition, there is no single piece of content in communicated messages that remains the same across various communicative sessions among the same participants.
- (c)
- Replay attack
In PSL-IoD, an adversary could initiate replaying the messages to masquerade any legal entity and come into session key agreement in any possible way. However, the PSL-IoD employs timestamps to check the freshness of messages which makes it infeasible for the adversary to replay the contents without becoming noticed by the legal participants.
- (d)
- Impersonation attack
If attempts to impersonate either as Ui, GCS, or Dj, it will not be able to achieve this since these entities hold private and master secrets along with embedded PUF circuits to thwart any possibility of impersonation or Man-in-the-Middle-based threat.
- (e)
- Drone physical capture threat
An adversary may attempt recovering critical secrets from the memory of the captured drone and compute previous session keys. In PSL-IoD, if an adversary attempts to compute rd = PUF(cd) as well as Xu = h(ku||rd) for any user or clone it after physically approaching the drone, it may not be able to achieve this primarily due to the change in PUF-generated identifier signaling to the system regarding the tampering attempt. Thus, the PSL-IoD is protected from physical drone capture attacks.
- (f)
- Session-specific temporary secret leakage threat
In PSL-IoD, even if the short-term secrets of the user such as au for various sessions are revealed to the adversary, the latter may not compute previous session keys related to the user. The construction of session key SK = h(PIDunew||TIDu||au||Xu||bd||TIDDj) requires many other parameters besides short session-specific short-term secrets to compute it. That is, it requires access to TIDu, Xu, bd, and TIDDj parameters.
- (g)
- Perfect forward secrecy
The PSL-IoD supports perfect forward secrecy even if the long-term master secret key KG of GCS is revealed to the adversary. In the proposed scheme, the adversary needs to approach both long-term master secret KG and all verifiers stored in the database either for drones or users to calculate past session keys established between the user and the specified drone.
- (h)
- Resistance to machine learning attacks
The PSL-IoD may resist machine learning (ML) attacks. An adversary requires access to adequate CRP pairs to initiate brute force attacks for guessing other pairs against the same PUF-circuit. In PSL-IoD, the adversary may not access either challenge or response out of CRP pairs that render the proposed scheme immune to ML attacks.
5.2. Formal Security Analysis
The Real-or-Random (RoR) model-oriented formal security analysis is employed to prove the security of a mutually settled session key in PSL-IoD. This analysis framework was suggested by Canetti et al. [37,38]. It is based on scientific formulations for proving the features of authentication techniques and compromising the session key through probabilistic calculations using various rounds of games. The illustration of proof is given below.
Participants: It is assumed that the participants , and are th, th, and th oracle instances of Ui, Di, and GCS, respectively.
Accept state: The oracle is said to be in the accept state when it receives the last message of the PSL-IoD communication protocol. After concatenation of all communication messages, it assigns the session-based identifier to the established session sid.
Effectiveness: The oracles are said to be valid instances in the case the malicious attacker remains unsuccessful in establishing SK between user and drone.
Cooperation: The suggested protocol employs the protocol identifier sid to establish a collaborative association between user- and drone-based oracle instances , which is followed with the accept state.
The malicious adversary may use the oracles as per the CK-compliant threat model which is shown in Table 3.

Table 3.
Queries with semantics.
Theorem 1.
We assume any polynomial time t attackerbreaking into PSL-IoD. In the RoR model, we can approximate the benefit of A between Ui and Dj for obtaining SK in PSL-IoD as mentioned below:
In Equation (1), the |Dict|, |PUF|, |H|, lp, and lh characterize the length of password dictionary (uniformly distributed), PUF outcome space, hash function-based space, length for PUF-based factors, and length of hash function, respectively [39]. In addition, wh, wp, and ws symbolize the number of queries for corresponding hash function, PUF, and Send oracle, respectively.
Proof.
This proof involves five rounds of games in aggregate, i.e., from GmR0 to GmR4. (t) describes the attacker’s advantage for guessing the parameter c with high probability in GmRi. Hence, the benefit of guessing may be shown as (t) [40].
Game GmR0: The starting game GmR0 simulates an actual security experiment between and challenger against the contributed protocol . The bit c is chosen by the attacker in the beginning of GmR0. The probability of winning the game is dependent on the chance that PSL-IoD may not provide resilience from the attack initiated from . According to the definition of semantic security in PSL-IoD [41], we have
Game GmR1: GmR1 is modeled as an eavesdropping attack. Under this game, all of the communicated messages M1 = {PIDu, H1, Eu, T1}, M2 = {H2, T2, EGCS}, M3 = {Wd, Vd, H3} exchanged among Ui, GCS and Dj during the mutual authentication procedure are intercepted with the simulation of the Execute (.) query. The attacker performs the Test query for verifying whether the output is a real session key SK or any random value. The session key constructed between Ui and Dj is SK = h(PIDunew||TIDu||au||Xu||bd||TIDDj) where Xu = h(ku||rd). For deriving the session key, the attacker needs to calculate PIDunew, TIDu, au, Xu, bd, and TIDDj. However, for computing these parameters, needs to know about high-entropy long-term credentials KG, PUF-generated response, access to GCS repository, and ephemeral secrets such as au and bd. The interception of communication messages on the public channel does not help the attacker in compromising long- or short-term credentials, and the probability of winning game GmR1 also does not increase at all for the attacker [42]. Thus,
Game GmR2: GmR2 serves as an active attack with added simulations for Send (.) and Hash (.) queries. The adversary in this game attempts to impersonate and convince legal participants to receive the tampered messages. The attacker could frequently initiate Hash (.) queries for checking collisions in message digests for {M1, M2, M3}; however, each of these messages is embedded with fresh timestamps, random nonces, and pseudonym identities other than long-term secrets. Thus, there is a negligibly small probability of collisions while employing the Send (.) query initiated by . Using the birthday paradox [43], we have
Game GmR3: GmR3 is an extension of GmR2 with added simulation of the PUF query. Again, employing the birthday paradox, we obtain
Game GmR4: GmR4 simulates GmR2 with an added Corrupt (.) oracle query. Employing this game, the attacker gains access to all stored factors including {Cu, Du, TIDDj, Nu, u, PIDu, Ru}. To guess the IDu and PWDu, the attacker needs access to the user’s biometric factor BIOu which cannot be recovered in a polynomial amount of time [43]. To guess the identity or the password, the number of attempts from the corrupt query may reach the maximum limit. Likewise, the attacker may attempt to extract all stored secrets from the memory of drone Dj upon physically capturing it. However, the probability to guess PUF-oriented critical secret of length lp can be estimated as [41]. The probability of each attempt from the adversary’s end remains less than the specified threshold. Thus, the chance that the attacker wins this game is
Subsequently, after modeling oracle queries, need to guess the value of factor c with the help of the Test query for winning this game [44,45]. Therefore, exhibits the advantage of the adversary for predicting c as given in the following equation:
Using Equations (2), (3) and (7), we have
We can apply the principle of triangular inequality [43,46] with the help of Equations (4)–(6) and infer the following results:
Using Equations (8) and (9), we obtain the following findings:
□
6. Performance Evaluation
We conducted a comparative analysis of the proposed PSL-IoD with other contemporary schemes focusing on security functionality as well as computational and communicational overheads. For evaluating the computational costs and latency of drone-based schemes [17,19,20,27,32,33,35], an experiment was performed using a mobile phone with a 2.45 Ghz processor having 4 GB memory, Android (4.4.2), for drones and the user. Another experiment was performed for a server using 2.9 Ghz CPU with 6 GB memory and a Windows 10 operating system. The system was configured using a Python 3.13-assisted cryptographic library called “Pycrypto”. To compute the primitive-based computational cost and time, we calculated the average execution latency over a hundred iterations. The experimental cost of these primitives in line with the above-mentioned experiment is shown in Table 4.

Table 4.
Computational delay for each primitive.
Table 5 exhibits comparison attributes for security features of various IoT- or drone-based authentication protocols [17,19,20,27,32,33,35], [PSL-IoD]. It can be witnessed that scheme [17] could not support anonymity and also lacks resistance to physical drone capture threats. Scheme [20] has privacy concerns and is also not immune to stolen device attacks initiated by the adversary. Likewise, scheme [27] does not counter impersonation attacks, and it is susceptible to physical device as well as drone capture attacks. Scheme [19] does not show resistance to stolen device attacks that may be initiated by the attacker on PSL-IoD. Similarly, [32] is not resilient against Man-in-the-Middle attacks, while scheme [33] is not resilient against replay attacks and denial-of-service (DoS) attacks. Scheme [35] does not support mutual authentication for its legal members, and it is also susceptible to DoS threats.

Table 5.
Attack Resistance Attributes and Comparison.
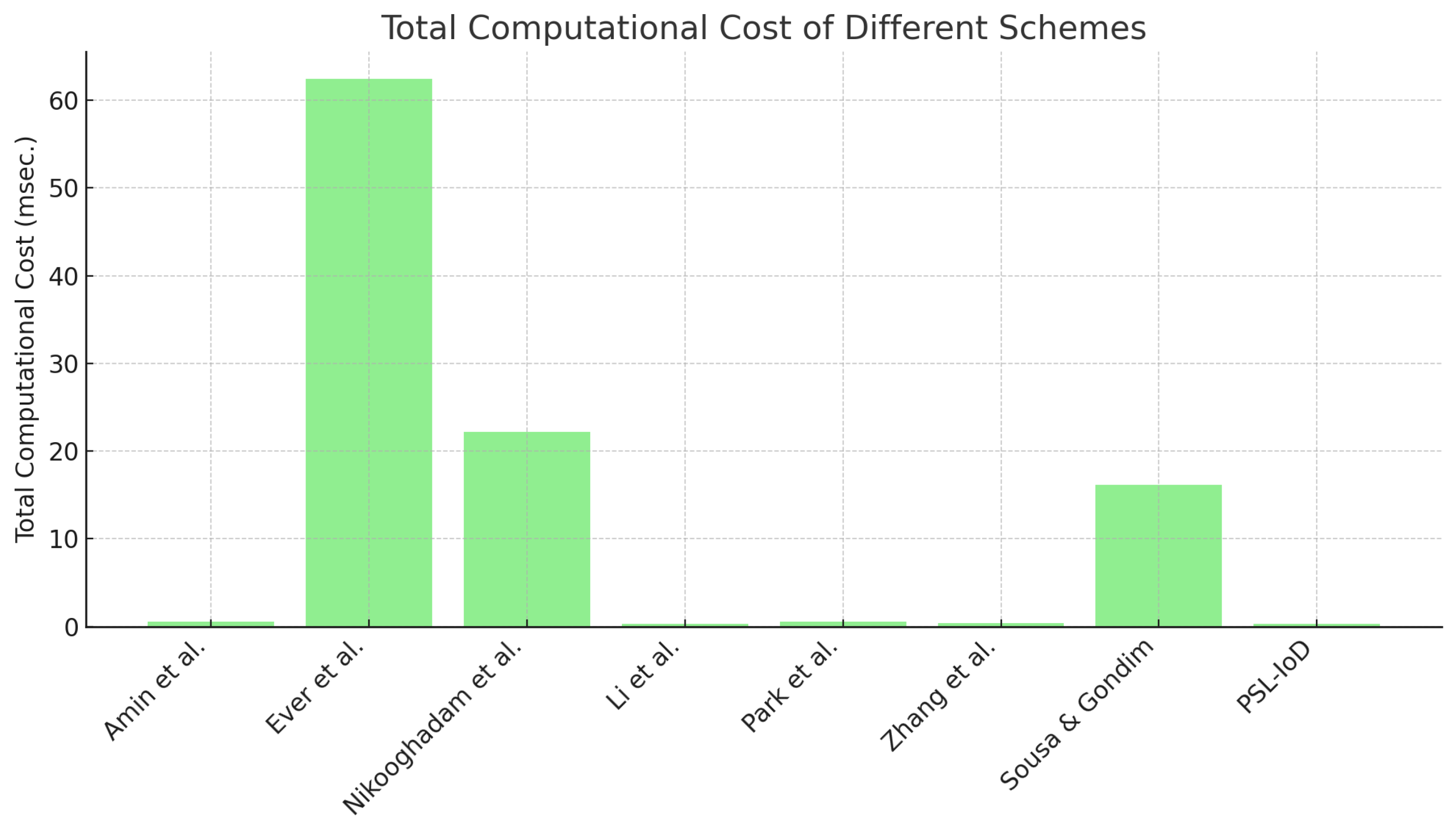
The computational cost of schemes [17,19,20,27,32,33,35], [PSL-IoD] is demonstrated in Table 6. In this table, notations Th, Ta, TPUF, TPM, TS, and Tfe represent the timing latency of hash operation, point addition, PUF-based operation, ECC-oriented scalar point multiplication, symmetric key and fuzzy extractor operation, respectively. Figure 6 depicts a high-level pseudo-code for computing the timing of each operation in the experiment. We can see that schemes [17,19,20,27,32,33,35] take Tfe + 29Th, 12Th + 10TPM + 3Ta, 19Th + 4TPM, 27Th, 2Tfe + 32Th, 2TPUF + 20Th, Tfe + 3TPM + 4Ta + 12Th, and TPUF + 17Th + 5Ts, respectively. The computational latency for schemes may be computed as 0.6 ms, 62.43 ms, 22.23 ms, 0.31 ms, 0.529 ms, 0.372 ms, 16.12 ms, and 0.302 ms, respectively. It can be witnessed in Figure 7 that the computational cost and latency of PSL-IoD is less than that of the compared schemes.

Table 6.
Computational and communicational overheads.

Figure 6.
High-level pseudo-code of experiment (PSL-IoD).
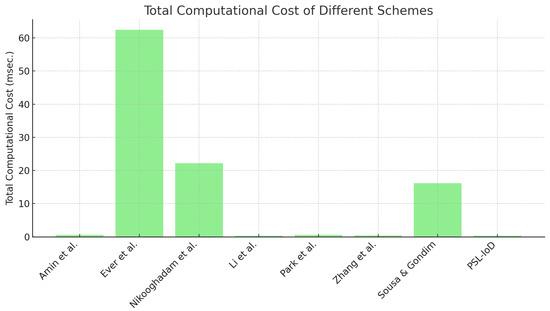
Figure 7.
Computational cost (ms) [17,19,20,27,32,33,35].
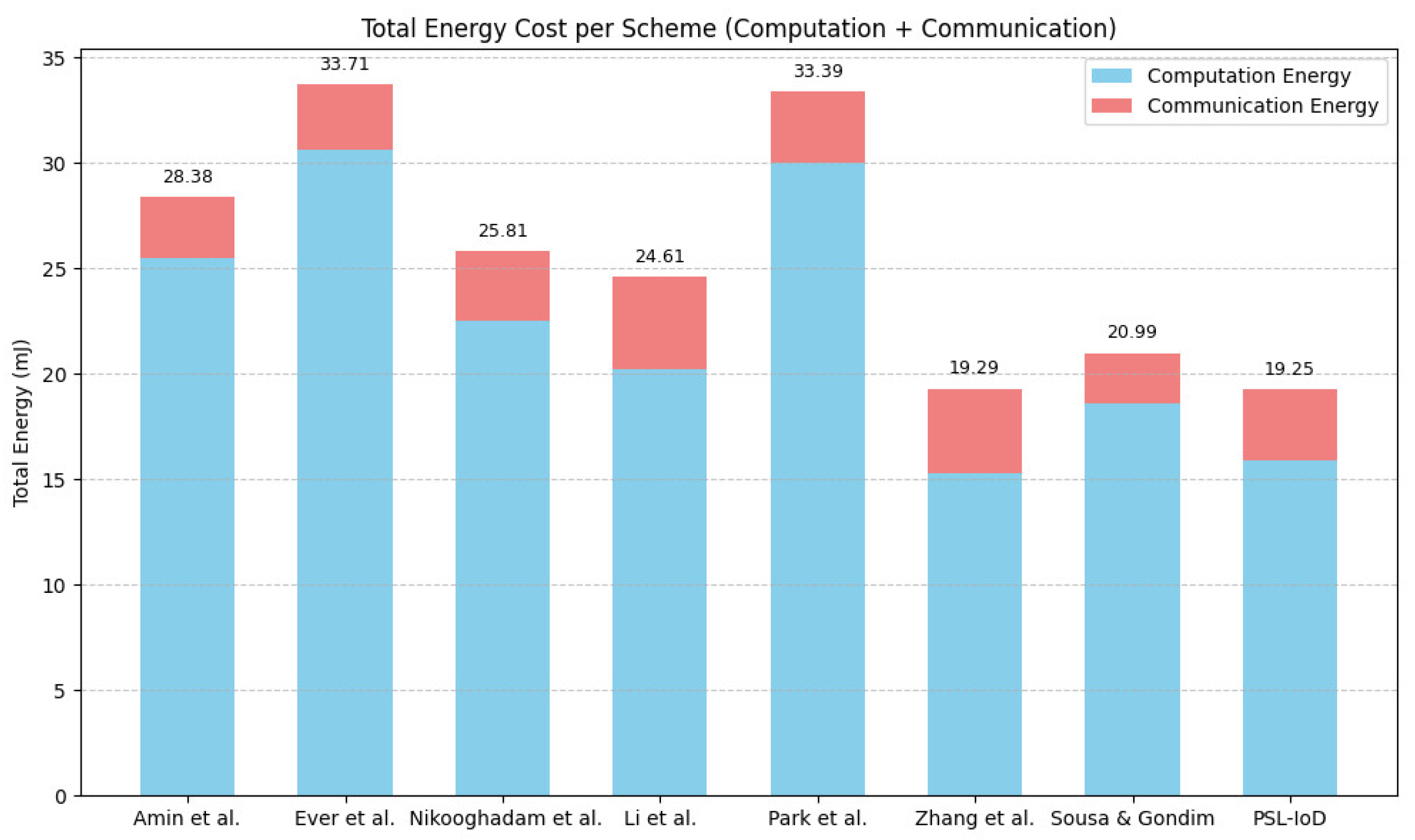
For calculating communication costs of comparative protocols, we assume that the bit lengths for the exchanged crypto-primitive factors in communication messages for hash digest function, original identity, pseudo-identity, random integer, ECC operation, and timestamp are 256 bits, 160 bits, 128 bits 160 bits, 320 bits, and 32 bits, respectively. The communication cost of schemes [17,19,20,27,32,33,35], [PSL-IoD] is computed as 2176 bits, 2336 bits, 2496 bits, 3292 bits, 2560 bits, 3008 bits, 1824 bits, and 2528 bits, respectively. Our scheme requires lesser communication cost in comparison with [19,32,33]. Although schemes [17,20,27,35] take less communication overhead than PSL-IoD, these schemes are prone to many security limitations as depicted in Table 6. Figure 8 depicts total energy cost, i.e., energy consumption for computation and communication, in millijoules (mJ) by considering the estimated energy cost per byte as computed in [39,45]. It can be witnessed from this table that besides maintaining a high degree of security, PSL-IoD requires the least energy consumption for computation and communication of bytes in comparison with other related studies.
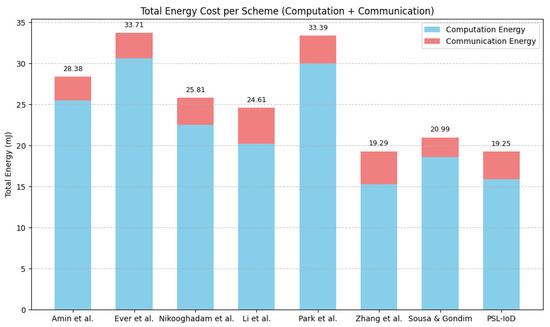
Figure 8.
Energy cost comparison (mJ) [17,19,20,27,32,33,35].
7. Conclusions
Drones can automate delivery and warehouse operations with least operational overhead. This work suggests the use of PSL-IoD, a lightweight and provably secure authentication protocol specifically designed for smart logistics environment. The customer can monitor package delivery status through a real-time tracking process by initiating PSL-IoD. The PSL-IoD generates a mutually agreed session between ultimate user and drone with embedded PUF to settle the authenticated last-mile delivery process in the supply chain management framework. A crucial aspect of the proposed scheme is that it not only ensures resilience from machine learning as well as physical drone capture threats but also supports perfect forward secrecy using low-end symmetric key-based operational primitives. The security features of PSL-IoD are proven under RoR-based random oracle model which ensures that the established session key between the participants is mutually agreed upon and protected from known threats. The performance evaluation exhibits that PSL-IoD is not only secure but also efficient in terms of computational and communicational overheads. The industrial implications of PSL-IoD for smart city managerial administrators are self-evident. In the future, we plan to work on more scalable adaptations of the proposed scheme by considering optimal batch authentication protocol designs for drone interactions with the ground station server.
Author Contributions
Conceptualization, M.D.A. and A.S.A.; methodology, M.D.A., A.S.A. and A.I.; software, M.D.A., A.S.A. and S.A.C.; validation, S.A.C. and M.D.A.; formal analysis, M.D.A. and A.S.A.; investigation, M.D.A., A.S.A., A.I. and S.A.C.; resources, S.A.C. and M.D.A., data curation, A.I.; writing original draft preparation, M.D.A. and A.S.A.; writing review and editing, M.D.A. and A.S.A.; visualization, M.D.A. and A.S.A.; supervision, S.A.C. and A.I. All authors have read and agreed to the published version of the manuscript.
Funding
The authors extend their appreciation to the Deputyship for Research & Innovation, Ministry of Education in Saudi Arabia for funding this research work through the project number MoE-IF-UJ-R2-22-753-2.
Data Availability Statement
The data presented in this study are available in the article.
Conflicts of Interest
The authors declare no conflicts of interest.
References
- Song, Y.; Yu, F.R.; Zhou, L.; Yang, X.; He, Z. Applications of the Internet of Things (IoT) in smart logistics: A comprehensive survey. IEEE Internet Things J. 2020, 8, 4250–4274. [Google Scholar] [CrossRef]
- Chung, S.H. Applications of smart technologies in logistics and transport: A review. Transp. Res. Part E Logist. Transp. Rev. 2021, 153, 102455. [Google Scholar] [CrossRef]
- Das, D.N.; Sewani, R.; Wang, J.; Tiwari, M.K. Synchronized truck and drone routing in package delivery logistics. IEEE Trans. Intell. Transp. Syst. 2020, 22, 5772–5782. [Google Scholar] [CrossRef]
- Wu, C.K.; Tsang, K.F.; Liu, Y.; Zhu, H.; Wei, Y.; Wang, H.; Yu, T.T. Supply chain of things: A connected solution to enhance supply chain productivity. IEEE Commun. Mag. 2019, 57, 78–83. [Google Scholar] [CrossRef]
- Perera, S.; Dawande, M.; Janakiraman, G.; Mookerjee, V. Retail deliveries by drones: How will logistics networks change? Prod. Oper. Manag. 2020, 29, 2019–2034. [Google Scholar] [CrossRef]
- Hassija, V.; Chamola, V.; Gupta, V.; Jain, S.; Guizani, N. A survey on supply chain security: Application areas, security threats, and solution architectures. IEEE Internet Things J. 2020, 8, 6222–6246. [Google Scholar] [CrossRef]
- Lu, G.; Koufteros, X.; Lucianetti, L. Supply chain security: A classification of practices and an empirical study of differential effects and complementarity. IEEE Trans. Eng. Manag. 2017, 64, 234–248. [Google Scholar] [CrossRef]
- Irshad, A.; Farooq, M.; Mahmood, K.; Mallah, G.A.; Chaudhry, S.A. DAC-MD: A privacy preserving drone-access control scheme for last mile delivery. Trans. Emerg. Telecommun. Technol. 2024, 35, e4958. [Google Scholar] [CrossRef]
- Alshdadi, A.A.; Irshad, A. PDAC-SL: A PUF-enabled drone access control technique for smart logistics. Alex. Eng. J. 2024, 107, 747–756. [Google Scholar] [CrossRef]
- Mahmood, K.; Ghaffar, Z.; Farooq, M.; Yahya, K.; Das, A.K.; Chaudhry, S.A. A security enhanced chaotic-map based authentication protocol for internet of drones. IEEE Internet Things J. 2024, 11, 22301–22309. [Google Scholar] [CrossRef]
- Mekdad, Y.; Aris, A.; Babun, L.; El Fergougui, A.; Conti, M.; Lazzeretti, R.; Uluagac, A.S. A survey on security and privacy issues of UAVs. Comput. Netw. 2023, 224, 109626. [Google Scholar] [CrossRef]
- Koubaa, A.; Qureshi, B.; Sriti, M.F.; Javed, Y.; Tovar, E. A service-oriented Cloudbased management system for the Internet-of-Drones. In Proceedings of the 2017 IEEE International Conference on Autonomous Robot Systems and Competitions, ICARSC, Coimbra, Portugal, 26–28 April 2017; Institute of Electrical and Electronics Engineers Inc.: Piscataway Township, NJ, USA, 2017; pp. 329–335. [Google Scholar] [CrossRef]
- Gupta, L.; Jain, R.; Vaszkun, G. Survey of important issues in UAV communication networks. IEEE Commun. Surv. Tutor. 2016, 18, 1123–1152. [Google Scholar] [CrossRef]
- Lin, C.; He, D.; Kumar, N.; Choo, K.K.R.; Vinel, A.; Huang, X. Security and privacy for the Internet of Drones: Challenges and solutions. IEEE Commun. Mag. 2018, 56, 64–69. [Google Scholar] [CrossRef]
- Turkanovi’c, M.; Brumen, B.; Hölbl, M. A novel user authentication and key agreement scheme for heterogeneous ad hoc wireless sensor networks, based on the Internet of Things notion. Ad Hoc Netw. 2014, 20, 96–112. [Google Scholar] [CrossRef]
- Farash, M.S.; Turkanovi’c, M.; Kumari, S.; Hölbl, M. An efficient user authentication and key agreement scheme for heterogeneous wireless sensor network tailored for the Internet of Things environment. Ad Hoc Netw. 2016, 36, 152–176. [Google Scholar] [CrossRef]
- Amin, R.; Islam, S.H.; Biswas, G.; Khan, M.K.; Leng, L.; Kumar, N. Design of an anonymity-preserving three-factor authenticated key exchange protocol for wireless sensor networks. Comput. Netw. 2016, 101, 42–62. [Google Scholar] [CrossRef]
- Bera, B.; Chattaraj, D.; Das, A.K. Designing secure blockchain-based access control scheme in IoT-enabled Internet of Drones deployment. Comput. Commun. 2020, 153, 229–249. [Google Scholar] [CrossRef]
- Li, C.T.; Weng, C.Y.; Chen, C.L.; Lee, C.C.; Deng, Y.Y.; Imoize, A.L. An Efficient Authenticated Key Agreement Scheme Supporting Privacy-Preservation for Internet of Drones Communications. Sensors 2022, 22, 9534. [Google Scholar] [CrossRef] [PubMed]
- Ever, Y.K. A secure authentication scheme framework for mobile-sinks used in the internet of drones applications. Comput. Commun. 2020, 155, 143–149. [Google Scholar] [CrossRef]
- Cho, G.; Cho, J.; Hyun, S.; Kim, H. SENTINEL: A secure and efficient authentication framework for unmanned aerial vehicles. Appl. Sci. 2020, 10, 3149. [Google Scholar] [CrossRef]
- Hussain, S.; Mahmood, K.; Khan, M.K.; Chen, C.M.; Alzahrani, B.A.; Chaudhry, S.A. Designing secure and lightweight user access to drone for smart city surveillance. Comput. Stand. Interfaces 2022, 80, 103566. [Google Scholar] [CrossRef]
- Srinivas, J.; Das, A.K.; Kumar, N.; Rodrigues, J.J. TCALAS: Temporal credential-based anonymous lightweight authentication scheme for Internet of drones environment. IEEE Trans. Veh. Technol. 2019, 68, 6903–6916. [Google Scholar] [CrossRef]
- Ali, Z.; Chaudhry, S.A.; Ramzan, M.S.; Al-Turjman, F. Securing smart city surveillance: A lightweight authentication mechanism for unmanned vehicles. IEEE Access 2020, 8, 43711–43724. [Google Scholar] [CrossRef]
- Wazid, M.; Das, A.K.; Kumar, N.; Vasilakos, A.V.; Rodrigues, J.J. Design and analysis of secure lightweight remote user authentication and key agreement scheme in Internet of drones deployment. IEEE Internet Things J. 2018, 6, 3572–3584. [Google Scholar] [CrossRef]
- Zhang, Y.; He, D.; Li, L.; Chen, B. A lightweight authentication and key agreement scheme for Internet of Drones. Comput. Commun. 2020, 154, 455–464. [Google Scholar] [CrossRef]
- Nikooghadam, M.; Amintoosi, H.; Islam, S.H.; Moghadam, M.F. A provably secure and lightweight authentication scheme for Internet of Drones for smart city surveillance. J. Syst. Archit. 2021, 115, 101955. [Google Scholar] [CrossRef]
- Gope, P.; Sikdar, B. An efficient privacy-preserving authenticated key agreement scheme for edge-assisted Internet of Drones. IEEE Trans. Veh. Technol. 2020, 69, 13621–13630. [Google Scholar] [CrossRef]
- Alladi, T.; Naren; Bansal, G.; Chamola, V.; Guizani, M. SecAuthUAV: A novel authentication scheme for UAV-ground station and UAV-UAV communication. IEEE Trans. Veh. Technol. 2020, 69, 15068–15077. [Google Scholar] [CrossRef]
- Abdel-Malek, M.A.; Akkaya, K.; Bhuyan, A.; Ibrahim, A.S. A Proxy Signature-Based Drone Authentication in 5G D2D Networks. In Proceedings of the 2021 IEEE 93rd Vehicular Technology Conference (VTC2021-Spring), Helsinki, Finland, 25–28 April 2021; pp. 1–7. [Google Scholar] [CrossRef]
- Yu, S.; Das, A.K.; Park, Y.; Lorenz, P. SLAP-IoD: Secure and lightweight authentication protocol using physical unclonable functions for internet of drones in smart city environments. IEEE Trans. Veh. Technol. 2022, 71, 10374–10388. [Google Scholar] [CrossRef]
- Park, Y.; Ryu, D.; Kwon, D.; Park, Y. Provably secure mutual authentication and key agreement scheme using PUF in internet of drones deployments. Sensors 2023, 23, 2034. [Google Scholar] [CrossRef]
- Zhang, Z.; Hsu, C.; Au, M.H.; Harn, L.; Cui, J.; Xia, Z.; Zhao, Z. PRLAP-IoD: A PUF-based Robust and Lightweight Authentication Protocol for Internet of Drones. Comput. Netw. 2024, 238, 110118. [Google Scholar] [CrossRef]
- Badshah, A.; Abbas, G.; Waqas, M.; Tu, S.; Abbas, Z.H.; Muhammad, F.; Chen, S. USAF-IoD: Ultralightweight and secure authenticated key agreement framework for internet of Drones environment. IEEE Trans. Veh. Technol. 2024, 238, 110118. [Google Scholar] [CrossRef]
- de Jesus Sousa, M.; Gondim, P.R.L. A multi-factor user authentication protocol for the internet of drones environment. Peer Peer Netw. Appl. 2025, 18, 69. [Google Scholar] [CrossRef]
- Dolev, D.; Yao, A.C. On the security of public key protocols. IEEE Trans. Inf. Theory 1983, 29, 198–208. [Google Scholar] [CrossRef]
- Canetti, R.; Goldreich, O.; Halevi, S. The random oracle methodology, revisited. J. ACM 2004, 51, 557–594. [Google Scholar] [CrossRef]
- Chaudhry, S.A.; Nebhen, J.; Irshad, A.; Bashir, A.K.; Kharel, R.; Yu, K.; Zikria, Y.B. A physical capture resistant authentication scheme for the internet of drones. IEEE Commun. Stand. Mag. 2021, 5, 62–67. [Google Scholar] [CrossRef]
- Choi, J.; Son, S.; Kwon, D.; Park, Y. A PUF-Based Secure Authentication and Key Agreement Scheme for the Internet of Drones. Sensors 2025, 25, 982. [Google Scholar] [CrossRef]
- Irshad, A.; Naqvi, H.; Chaudhary, S.A.; Usman, M.; Shafiq, M.; Mir, O.; Kanwal, A. Cryptanalysis and improvement of a multi-server authenticated key agreement by chen and lee’s scheme. Inf. Technol. Control. 2018, 47, 431–446. [Google Scholar] [CrossRef]
- Sun, D.-Z.; Gao, Y.-N.; Tian, Y. On the Security of a PUF-Based Authentication and Key Exchange Protocol for IoT Devices. Sensors 2023, 23, 6559. [Google Scholar] [CrossRef]
- Al-Meer, A.; Al-Kuwari, S. Physical unclonable functions (PUF) for IoT devices. ACM Comput. Surv. 2023, 55, 1–31. [Google Scholar] [CrossRef]
- Alashjaee, A.M.; Irshad, A.; Daud, A.; Alhomoud, A.; Altowaijri, S.M.; Alshdadi, A.A. ReSOTS: RFID/IoT-enabled secure object tracking key exchange for trustworthy smart logistics. Wirel. Pers. Commun. 2024, 139, 777–799. [Google Scholar] [CrossRef]
- Khan, N.A.; Din, I.U.; Almogren, A.; Altameem, A.; Guizani, M. Secure and Efficient AI-SDN-based Routing for Healthcare-Consumer Internet of Things. IEEE Trans. Consum. Electron. 2024, 139, 801. [Google Scholar] [CrossRef]
- Ahmad, T.; Usman, M.; Murtaza, M.; Benitez, I.B.; Anwar, A.; Vassiliou, V.; Al-Ammar, E.A. A novel self-calibrated UWB based indoor localization systems for context-aware applications. IEEE Trans. Consum. Electron. 2024, 70, 1672–1684. [Google Scholar] [CrossRef]
- Subramani, J.; Maria, A.; Rajasekaran, A.S.; Lloret, J. Physically secure and privacy-preserving blockchain enabled authentication scheme for internet of drones. Secur. Priv. 2024, 7, e364. [Google Scholar] [CrossRef]
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).