Abstract
COPA, introduced by Andreeva et al., is the first online authenticated encryption (AE) mode with nonce-misuse resistance, and it is covered in COLM, which is one of the final CAESAR portfolios. However, COPA has been proven to be insecure in the releasing unverified plaintext (RUP) setting. This paper mainly focuses on the integrity under RUP (INT-RUP) defect of COPA. Firstly, this paper revisits the INT-RUP security model for adaptive adversaries, investigates the possible factors of INT-RUP insecurity for “Encryption-Mix-Encryption”-type checksum-based AE schemes, and finds that these AE schemes with INT-RUP security vulnerabilities utilize a common poor checksum technique. Then, this paper introduces an improved checksum technique named polynomial intermediate checksum (PIC) for INT-RUP security and emphasizes that PIC is a sufficient condition for guaranteeing INT-RUP security for “Encryption-Mix-Encryption”-type checksum-based AE schemes. PIC is generated by a polynomial sum with full terms of intermediate internal states, which guarantees no information leakage. Moreover, PIC ensures the same level between the plaintext and the ciphertext, which guarantees that the adversary cannot obtain any useful information from the unverified decryption queries. Again, based on PIC, this paper proposes a modified scheme COPA-PIC to fix the INT-RUP defect of COPA. COPA-PIC is proven to be INT-RUP up to the birthday-bound security if the underlying primitive is secure. Finally, this paper discusses the properties of COPA-PIC and makes a comparison for AE modes with distinct checksum techniques. The proposed work is of good practical significance. In an interactive system where two parties communicate, the receiver can effectively determine whether the information received from the sender is valid or not, and thus perform the subsequent operation more effectively.
Keywords:
authenticated encryption; checksum technique; integrity under releasing unverified plaintext; provable security MSC:
94A60; 68P25
1. Introduction
1.1. Background
With the increasing demand for lightweight sensors in the development of space–aerial–ground–sea cooperative information networks, and the scalability, timeliness, and security of the network, lightweight cryptography has been deeply explored in academia and industry. To solve the practical application problems, authenticated encryption (AE) has been extended to lightweight AE, which provides both privacy and authenticity on resource-constrained devices. In conventional security models of AE, the decrypted plaintext must be released after integrity is successfully verified. However, in lightweight devices, there are not enough resources to store the whole decrypted plaintext. Moreover, there exist side channel attacks to obtain the properties of the plaintext indirectly. Thus, releasing the decrypted plaintext before verification (releasing unverified plaintext, RUP) is often desirable and can contribute effectively to the improvement of efficiency in lightweight devices [1,2,3,4].
Andreeva et al. introduced stronger security models in the RUP setting [1]. For privacy, they proposed a new notion called PA (Plaintext Awareness). PA, in fact, is a plaintext extractor which tries to deceive adversaries by simulating the decryption oracle. An AE scheme is PA if it is infeasible to distinguish the decryption oracle from the plaintext extractor. For authenticity, they proposed a new notion called INT-RUP (Integrity under Releasing Unverified Plaintext). INT-RUP is a stronger security metric than INT-CTXT (Integrity of Ciphertext). An AE scheme is INT-RUP if an adversary can not generate a fresh valid ciphertext–tag pair given the additional power of access to an unverified decryption oracle, after the encryption oracle. This paper is only interested in INT-RUP security of various AE schemes.
OCB [5,6,7] and COPA [8] are not INT-RUP. Andreeva et al. presented a forgery attack under the INT-RUP security model and left fixing OCB and COPA to be INT-RUP in an efficient way as an open problem [1]. Zhang et al. focused on the weakness of the checksum processing, described a new generalized checksum technique—PCC (Plaintext and Ciphertext Checksum)—and proved that all AE schemes with PCC are insecure under the INT-RUP security model [9]. To fix the weakness of PCC, they provided an intermediate checksum (IC) technique to generate the authentication tag. Based on the IC technique, they proposed a modified OCB scheme with IC, called OCB-IC, to settle the INT-RUP security of OCB [9,10]. Chakraborti et al. focused on the rate (which means the number of message blocks processed per block of cipher invocation) of block-cipher-based AE schemes to find the cause of INT-RUP insecurity [11]. They considered the weakness during the tag processing, showed a generic INT-RUP attack on a “rate-1” block-cipher-based affine AE mode, described an INT-RUP attack on CPFB (rate-3/4), and presented a variant mCPFB (rate-3/4) which supports INT-RUP security. Zhang and Wu focused on the security of online AE schemes in a RUP setting and looked for the reason of the INT-RUP insecurity of the schemes [12]. They found that if the encryption part of AE schemes has a CCJP (Control Ciphertext to Jump between two Plaintexts) property and the input of the authentication part is built by linear combinations of all plaintext blocks (i.e., the authentication tag is generated by the plaintext checksum), it is easy to make an INT-RUP forgery attack. Datta et al. investigated the integrity of the COLM structure in an RUP setting, rewrote a nonce-respecting INT-RUP forgery attack against COPA’s XOR mixing, and presented nonce-respecting and nonce-misusing INT-RUP forgery attacks for any mixing functions [13]. They demonstrated that its security highly depends on the choice of mixing function. Hirose et al. focused on the security of rate-1 AE schemes under RUP [14]. They showed that any rate-1 AE scheme cannot satisfy strong security requirements under RUP and then introduced new strictly weaker security notions of tag-PA and tag-INT by relaxing the security requirements; finally, they presented a new rate-1 AE scheme OCBt which is both tag-PA and tag-INT. They considered the efficiency by rate-1 and full parallelizability and security by robustness against decryption misuse. Chakraborti et al. considered the INT-RUP security of AE schemes under the lightweight application and proposed two lightweight AE modes: LOCUS and LOTUS with higher security and lighter primitives [15]. They utilized the intermediate checksum technique to generate the final authentication tag. In addition to the one-pass AE schemes with INT-RUP security, there exist two-pass AE modes with INT-RUP security. Andreeva et al. considered the INT-RUP security of SIV, HBS, and BTM and proved their INT-RUP security [1]. Chang et al. proposed a lightweight deterministic AE mode ANYDAE and proved that ANYDAE achieves INT-RUP security [16]. Recently, Andreeva et al. focused on the rate-1 online fork AE mode SAEF and showed that SAEF is INT-RUP secure up to the birthday bound by the H-coefficient technique [17]. Datta et al. considered SAEB and TinyJAMBU and presented their integrity security in the setting of a releasing unverified plaintext model [18].
This paper revisits the possible causes which result in INT-RUP insecurity, investigates almost all of the one-pass checksum-based AE schemes [5,6,7,8,11,13,19,20,21,22,23,24,25,26,27], and finds that these AE schemes with INT-RUP security defects utilize a common checksum technique. This paper focuses on the weakness of the checksum technique and tries to introduce an improved checksum technique to settle the INT-RUP security of COPA.
1.2. Problem Statement
For almost all of the one-pass AE schemes, their checksum is generated by the XOR-sum of all plaintext blocks, which results in INT-RUP insecurity. Andreeva et al. presented a forgery attack with a high probability by making one encryption query and two decryption queries under the INT-RUP security model, and they left fixing COPA to be INT-RUP in an efficient way as an open problem [1].
The IC technique [9,10] is a good technique for settling the INT-RUP security defect of OCB. However, the IC technique cannot be directly applied to COPA. COPA is an authenticated online cipher, which means that the i-block ciphertext just relies on the first i plaintext blocks. In other words, the intermediate checksum in this case only relates to the last ciphertext block. Even if you utilize the encrypted internal states to generate the intermediate checksum, the adversary just needs to keep the last ciphertext block the same to make a successful forgery. In addition, the intermediate parity checksum (IPC) technique [10] was utilized to try to settle the INT-RUP security defect of COPA, but it ultimately failed. The i-block plaintext can be recovered by the -block ciphertext and the i-block ciphertext, which can be used by adversaries to launch forgery attacks. Therefore, it is necessary to propose a new improved intermediate checksum technique for settling the INT-RUP security defect of COPA.
1.3. Our Contributions
This paper mainly considers the INT-RUP insecurity of COPA and focuses on the weakness of the checksum processing. This paper first revisits the INT-RUP security model which allows for an adaptive adversary to make queries in any order and then introduces a new improved checksum technique: polynomial intermediate checksum (PIC), which is a generalization of IC. In the PIC technique, the intermediate internal states generated by either an encryption or a decryption algorithm are hidden from the adversaries, and PIC is generated by a polynomial sum with full terms of intermediate internal states, which guarantees no information leakage. Moreover, PIC maintains the same level between the plaintext and the ciphertext, which guarantees that the adversary cannot obtain any useful information from the unverified decryption queries. This technique is very effective in solving the INT-RUP security of checksum-based AE schemes. Finally, based on the PIC technique, a modified scheme called COPA-PIC is proposed to fix the INT-RUP security defect of COPA. COPA-PIC retains the main structure and the advantages of COPA.
From the perspective of the design idea, at the beginning, COPA-PIC is designed in terms of tweakable blockciphers (TBCs), as TBC-based AE modes have more advantages than AE modes based on other primitives; particularly, their structure is clear and their proof is simple [19,22,28,29,30,31]. In addition, TBCs can also be constructed by distinct primitives. Therefore, a TBC-based COPA-PIC is first illustrated, and then a blockcipher-based TBC and a permutation-based TBC are utilized to further instantiate COPA-PIC.
From the perspective of the security guarantee, COPA-PIC is proven INT-RUP up to the birthday bound of -bit security if the underlying primitive (including TBC, block cipher, and permutation) is secure, where n is the block size of the underlying primitive.
From the perspective of the efficiency, the number of underlying primitive invocations of COPA-PIC is less than that of COPA. To be specific, let a be the number of blocks of the associated data and l be the number of blocks of the plaintext. Then, the encryption, decryption, and verification algorithms of COPA-PIC invoke , , and underlying primitives, respectively, while the encryption, decryption, and verification algorithms of COPA invoke underlying primitives. In other words, the encryption and decryption costs of COPA-PIC are the same as those of COPA, but the verification cost of COPA-PIC is close to half of COPA. In practical scenarios, such as an interactive system where two parties communicate, the receiver can first effectively determine whether the information received from the sender is valid or not, and then perform the decryption operation more effectively to obtain the correct plaintext. Therefore, the efficiency of COPA-PIC is significantly improved in practical applications. The comparison between COPA and COPA-PIC is shown in Table 1.

Table 1.
Comparison between COPA and COPA-PIC for a-block associated data and l-block plaintext, where # Encryption, # Decryption, and # Verification, respectively, stand for the number of invoking underlying primitives in the encryption, decryption, and verification algorithms, and n is the block size.
The proposed work is of high significance to both theoretical investigations and practical applications. This work supports Zhang and Wu’s view that it is easy to make an INT-RUP forgery attack if the encryption part of the AE schemes has a CCJP property and the input of the authentication part is mainly subject to linear combinations of all plaintext blocks [12]. The PIC technique is essentially an improvement of Chakraborti et al.’s technique and covers the IC technique. The PIC technique aims to settle the problem of INT-RUP security for “Encryption-Mix-Encryption”-type checksum-based AE schemes. Moreover, the proposed work also meets the requirements of strong security and high efficiency in lightweight devices in the next-generation network. In particular, it is of good practical significance to establish the rapid feedback mechanism of third-party error authentication.
1.4. Organization of This Paper
Some preliminaries are presented in Section 2. A new polynomial intermediate checksum (PIC) technique is described in Section 3. Section 4 provides a modified scheme COPA-PIC to fix the INT-RUP security defect of COPA and derives its security proof. Finally, this paper concludes with some discussions and a mention of future works in Section 5.
2. Preliminaries
The basic notations and concepts closely follow [9,10]. Some of the important symbols are described in Abbreviations.
- Block ciphers. Block cipher is an important part of symmetric-key ciphers, and its standardized algorithms, such as AES or SM4, have been widely used in practice.
Let be a block cipher, where is a key space and n is the block size. For any , is an n-bit permutation. Let be an adversary with access to the encryption oracle or encryption and decryption oracles; then, the pseudorandom permutation (PRP) and strong pseudorandom permutation (SPRP) advantages of against E are, respectively, defined as
- Tweakable blockciphers (TBCs). As the generalization of block ciphers, TBCs have been widely used in the fields of disk encryption, length-preserving encryption, storage encryption, etc. Related works about TBCs include [30,32,33,34,35,36,37,38,39].
Let be a TBC, where is a key space and is a tweak space. For any , , is an n-bit permutation. Let be an adversary with access to the tweakable encryption oracle or tweakable encryption and tweakable decryption oracles, then the tweakable PRP (TPRP) and strong TPRP (STPRP) advantages of against are, respectively, defined as
The above adversary is just allowed to query the encryption oracle in the tweak space for TPRP, while it is allowed to query both encryption and decryption oracles in the tweak space for STPRP. However, in real life, the encryption part of some cryptographic schemes is allowed to query both encryption and decryption oracles in a subset of tweaks and the authentication part of an associated data is just allowed to query the encryption oracle in another subset of tweaks, such as COPA. Granger et al. introduced a mixed security notion to settle this problem [22]. Consider a partition of the tweak space into encryption-only tweaks and encryption-and-decryption tweaks ; then, the mixed TPRP (MTPRP) advantage of against is defined as
Note that, here, is not allowed to query or for tweaks from . In fact, MTPRP covers TPRP if and STPRP if .
- Construction of TBCs. TBCs can be constructed from primitives that are widely used today, such as block ciphers and permutations. In these constructions, since the tweak is an important component of TBCs, it must be instantiated in advance when implementing with block ciphers and permutations. Moreover, considering the application of TBC in the actual modes of operations, the update of the tweak is as simple as possible. In practice, due to the wide application of nonce-based encryption, authentication, and authenticated encryption modes of operations, using a nonce to instantiate a tweak has become a common technical means. Here, we consider a nonce-based instantiation of a tweak space , where is a nonce space, is a large-integer set, and is a small-integer set, and we give two general methods for constructing TBCs as follows.
Method 1: Let be a block cipher. By the XEX* construction [6], a blockcipher-based TBC is built as follows:
where , and .
Method 2: Let be a public n-bit permutation. By the MEM construction [22], a permutation-based TBC is built as follows:
where , and .
The security of these two general methods for constructing TBCs is shown in the following lemmas.
Lemma 1
(XEX* [6]). Assume that the adversary makes q construction queries to and and for all . Let ; then,
Lemma 2
(MEM [22]). Assume that the adversary makes q construction queries to and and p primitive queries to π and and for all . Let ; then,
- Syntax of AE. In the RUP setting, Andreeva et al. introduced a new syntax for AE modes [1]. They divided the conventional decryption algorithm into a decryption algorithm and a verification algorithm so that the decryption algorithm always releases plaintext and the verification algorithm only performs integrity verification. The new syntax of nonce-based AE schemes consists of an encryption algorithm , a decryption algorithm : , and a verification algorithm , which is described as follows:where , and the symbols ⊤ and ⊥ indicate the success and failure of integrity verification, respectively.
- INT-RUP security model of AE. Let be a nonce-based AE scheme. Let and be an adversary which makes at most q queries to and , and at most queries to . Assume that is an adaptive adversary which can perform encryption and decryption oracle queries in any order. In other words, can perform the interleaved queries to and . forges if at least one forgery attempt in all forgery attempts succeeds. Then, the INT-RUP-advantage of against is defined as
Let be the INT-RUP-advantage of the adversary against the nonce-based AE scheme under the limited running time t, queries q, block length l, query complexity , and other resources.
3. Polynomial Intermediate Checksum (PIC) Technique
This paper investigates almost all of the “Encryption-Mix-Encryption”-type checksum-based AE schemes with INT-RUP insecurity, focuses on the weakness of their checksum technique, and tries to introduce an improved checksum technique to settle the INT-RUP insecurity of COPA. This section first introduces a polynomial intermediate checksum (PIC) technique for supporting INT-RUP security and then presents the INT-RUP security of “Encryption-Mix-Encryption”-type AE modes with PIC.
3.1. PIC Technique
The checksum technique used in the previous “Encryption-Mix-Encryption”-type AE modes includes the plaintext checksum (PC), the plaintext and ciphertext checksum (PCC), intermediate checksum (IC), and intermediate parity checksum (IPC). However, these checksum techniques do not always guarantee INT-RUP security for “Encryption-Mix-Encryption”-type AE modes. To always guarantee INT-RUP security for “Encryption-Mix-Encryption”-type AE modes, here, we introduce a new polynomial intermediate checksum (PIC) technique, which is a generalization of IC. As the name suggests, PIC is a full-term polynomial XOR-sum of intermediate internal states. The intermediate internal states are generated by encrypting all of the plaintext blocks or decrypting all of the ciphertext blocks, which make them hidden from the adversaries. In other words, PIC guarantees no information leakage.
To always guarantee the INT-RUP security, PIC must satisfy the following two conditions simultaneously:
Condition 1. It is generated by all of the plaintext blocks.
Condition 2. It is generated by all of the ciphertext blocks.
The above two conditions are indispensable. Conditions 1 and 2 show that PIC is constructed by polynomials with full terms and provides the same level for the plaintext and the ciphertext to resist the releasing unverified plaintext attack. What calls for special attention is that PIC must be a polynomial function with full terms of the plaintext blocks, and it must also be a polynomial function with full terms of the ciphertext blocks. Otherwise, leaving the missing term unchanged makes it easy to make a successful forgery. Having the same level between the plaintext and the ciphertext ensures that the adversary cannot obtain any useful information from the unverified decryption queries. In other words, PIC can resist the unverified decryption queries. For “Encryption-Mix-Encryption”-type checksum-based AE schemes, PIC is a sufficient condition for guaranteeing the INT-RUP security.
3.2. INT-RUP Security of “Encryption-Mix-Encryption”-Type AE Modes with PIC
The following mathematical model is utilized to formally describe “Encryption-Mix-Encryption”-type AE modes with PIC.
Let be a TBC, where is a key space, is a tweak space, is a nonce space, is a large-integer set, and is a small-integer set. Let N be a nonce, M be a plaintext, C be a ciphertext, and T be an authentication tag. The overview of “Encryption-Mix-Encryption”-type nonce-based AE modes with PIC is described in Figure 1.
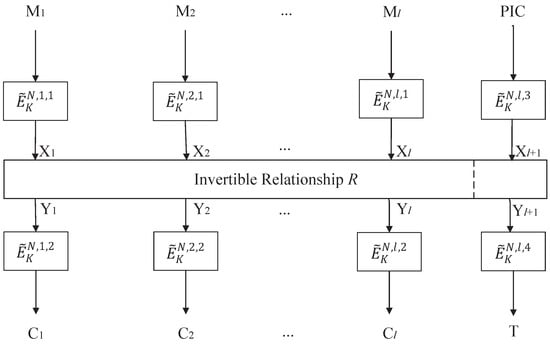
Figure 1.
“Encryption-Mix-Encryption”-type nonce-based authenticated encryption modes with polynomial intermediate checksum (PIC).
Let be the encrypted internal states of the plaintext , and be the decrypted internal states of the ciphertext , . There exists some invertible mathematical relationship R between and , i.e., and for each , the following equation holds:
where for and for are arbitrary constants.
Let be a polynomial intermediate checksum, where for and are arbitrary constants. Then,
where and () satisfy the following relationship:
In particular, if for any , then , where . It follows that the relationship (I) degenerates to
OCB-IC [9] is a typical example when and . In this case, for and PIC degrades to IC (i.e., ).
If for any , then is an online function (i.e., just depends on the first i inputs , where ). It follows that, the relationship (I) degenerates to
In this case, authenticated encryption schemes are also called authenticated online ciphers. The typical authenticated online ciphers include ELmE [25], ELmD [24], and COLM [13]. Similar checksum techniques are actually used in their design. To take it one step further, if , then for , where c is an arbitrary constant. In this case, PIC must satisfy the following equation:
where and () satisfy the following relationship:
Theorem 1.
For “Encryption-Mix-Encryption”-type AE modes with PIC, if PIC is generated by all terms of the plaintext blocks and it can also be generated by all terms of the ciphertext blocks, then the INT-RUP security can be guaranteed.
Proof.
Let be “Encryption-Mix-Encryption”-type AE modes with PIC. Assume that the adversary makes encryption queries to the encryption oracle and receives , where , and makes decryption queries to the decryption oracle and obtains the unverified plaintext , where . Note that and . Then, forges challenge queries , , to the verification oracle , where .
All TBCs of are replaced with tweakable random permutations to obtain , where and is a tweak space. Then the INT-RUP-advantage of is
where is an MTPRP adversary against .
Let be an event that at least one forgery attempt in all forgery attempts succeeds. Then, the INT-RUP-advantage of is
Define a collision as the same output from distinct inputs. Let be the event that a collision of the authentication tag occurs for the encryption queries.
With the total probability formula and the probability inequality, one has
Step 1: Bound the probability of event occurring: .
Step 2: Evaluate the upper bound of the probability that event occurs under the condition : . For simplicity, a single forgery attempt , is first considered, where is divided into blocks and is divided into blocks for . Let be a set of the authentication tags generated by the encryption oracle (Under the condition , are distinct from each other).
Case 1: is new, i.e., . In this case, the adversary already knows the value of , where , and with this knowledge, the adversary tries to guess the preimage of another new tag. Therefore, the probability that the adversary correctly guesses this value is at most , which is also the probability that the adversary’s forgery attempt succeeds.
Case 2: is old, i.e., . Let us say , where . According to the last two tweaks and of the authentication tag generation, a further analysis is discussed as follows.
Case 2-1: If , the last two tweaks and are new. The adversary tries to forge an identical tag () using a new nonce . The image of a single point under a tweakable random permutation is uniform, so the generated tag is an independent and uniform random value. Thus, the probability that the adversary correctly forges an identical tag () is .
Case 2-2: If and , the last two tweaks and are new. The adversary tries to forge an identical tag () using a new block-length . The image of a single point under a tweakable random permutation is uniform, so the generated tag is an independent and uniform random value. Thus, the probability that the adversary correctly forges an identical tag () is .
Case 2-3: If and , the last two tweaks and in this case are the same as those of previous query–response pairs . According to , where for all , a further discussion is shown as follows.
- is new and is new, i.e., . The probability that this case occurs is about . The adversary tries to forge an identical tag using a new checksum . Thus, the probability that the adversary’s forgery attempt succeeds is .
- is new and is old, i.e., . According to the fact that for any , where c is a constant from , the probability that is old is at most . Therefore, the probability that the adversary can guess the correct value in this case is the probability that is old, which is at most .
- is old. This contradicts .
Summarizing all cases above, the successful probability of the single forgery attempt is upper-bounded by
Therefore, for forgery attempts, it is easy to bound the probability that event occurs under the condition :
The INT-RUP advantage of , after q encryption and decryption queries, and forgery queries, is
where is an MTPRP adversary against . If is a secure MTPRP, then with PIC guarantees the INT-RUP security. □
Here, PIC just focuses on the authentication of the plaintext. The authentication of the associated data should be included in the verification algorithm. This paper directly utilizes PMAC1 algorithm [6] to generate the authentication of the associated data A, i.e., . In addition, the associated data can also be treated in a similar way to messages, just saving the final output as its authentication tag.
4. COPA-PIC: COPA with Polynomial Intermediate Checksum for INT-RUP Security
To solve the INT-RUP security defect of COPA, the PIC technique is applied to COPA, and an improved variant, COPA-PIC, is proposed. In this section, the top-level design of COPA-PIC is first described from the angle of TBCs, and then blockcipher-based and permutation-based COPA-PIC instances are presented.
4.1. TBC-Based COPA-PIC: COPA-PIC[]
At the beginning of the design, the idea was to retain as much of the COPA structure as possible. Therefore, the mainly structure of COPA-PIC is the same as that of COPA except that the plaintext checksum used in the encryption and verification algorithms is replaced with PIC. For PIC, a polynomial sum with full terms of internal intermediate states is utilized to ensure INT-RUP security. Therefore, the verification algorithm and the decryption algorithm of COPA-PIC share parts of computing resources such that the cost of the authentication tag is minimal.
Let be a TBC, where is a key space, is a tweak space, is a nonce space, is a large-integer set, and is a small-integer set. We assume that COPA-PIC takes a key K, a nonce N, associated data A, and a plaintext as input and returns the corresponding ciphertext and an authentication tag T. Then, the checksum of COPA-PIC is , where and for all , and g is a full-term polynomial function. It is essential to call two extra TBCs in the tag-generating process (let and ; then, ; for two distinct associated data , if the final authentication tag is generated by calling once extra primitive, we can get the difference in the authentication tag of associated data and the difference in the final authentication tag, which can be easily used to obtain a forgery attack).
The overview of COPA-PIC[] is shown in Figure 2, and its authentication component of the associated data is depicted in Figure 3. The authentication of associated data utilizes the TBC-based PMAC1 algorithm, which is shown in Algorithm 1. COPA-PIC[] consists of an encryption algorithm , a decryption algorithm , and a verification algorithm , which are shown in Algorithms 2–4.
| Algorithm 1 PMAC1 algorithm |
|
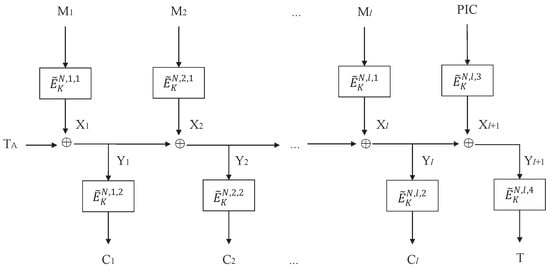
Figure 2.
TBC-based COPA-PIC: COPA-PIC[], where is a TBC and is the authentication of associated data A, i.e., . If there are no associated data, then set .
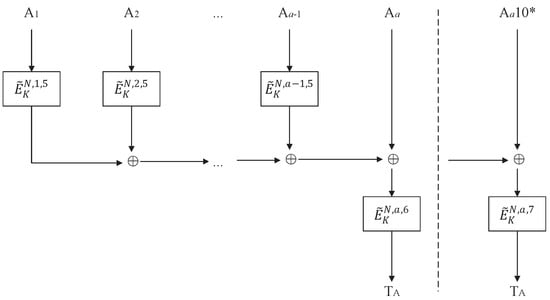
Figure 3.
TBC-based PMAC1: PMAC1[].
| Algorithm 2 Encryption algorithm |
|
| Algorithm 3 Decryption algorithm |
|
| Algorithm 4 Verification algorithm |
|
For COPA-PIC, we check the correctness as follows:
Thus, PIC is both a polynomial function with full terms of the plaintext blocks and a polynomial function with full terms of the ciphertext blocks, which meets Conditions 1 and 2. Therefore, according to Theorem 1, COPA-PIC[] ensures INT-RUP security.
Next, the strict INT-RUP security of COPA-PIC[] is given in the following theorems.
Theorem 2
(INT-RUP security of COPA-PIC based on ideal TBCs). For COPA-PIC[], real TBCs are replaced with tweakable random permutations to obtain COPA-PIC[]. Let be a nonce-misusing adversary with q encryption and decryption queries and forgery attempts. Then, one has
Proof.
Similar to the proof of Theorem 1, assume that makes encryption queries to and receives , where , and makes decryption queries to and obtains the unverified plaintext , where . Note that and . Then, forges challenge queries , , to , where .
Let be an event that at least one forgery attempt in all forgery attempts succeeds. Then, the INT-RUP-advantage of is
Denote variables of internal state values as , which is also equal to , where and is the authentication of the associated data A. Define a collision as the same value from different prefixes and . More precisely, and , which means . Let be the event that a collision of occurs for some . Similarity, let be the event that a collision of the tag occurs for the encryption queries. Let be the event that a collision of occurs for two different associated data. Let be the union of events , , and ; then, .
With the total probability formula and the probability inequality, one has
Step 1: Bound the probability of event occurring: . As COPA-PIC and COPA have the same encryption and decryption structures, the events , , and are exactly the same as those of COPA. Moreover, COPA-PIC and COPA use different methods for generating tags, but their authentication tags are all generated through the randomization of the checksum and the last ciphertext block. The only difference is whether the checksum has been randomized before. This does not make much difference in authentication processing, but it needs to be carefully considered in verification processing. Therefore, the event is exactly the same as that of COPA.
According to two claims and in COPA and the total probability formula, one has
Step 2: Evaluate the upper bound of the probability that event occurs under the condition : . For simplicity, a single forgery attempt is considered, where is divided into blocks and is divided into blocks for . Let be a set of the authentication tags generated by the encryption oracle.
Case 1: is new, i.e., . In this case, the adversary already knows the value of , where , and with this knowledge, the adversary tries to guess the preimage of another new tag. Therefore, the probability that the adversary correctly guesses this value is at most , which is also the probability that the adversary’s forgery attempt succeeds.
Case 2: is old, i.e., . Let us say , where . According to the last two tweaks and of generating the authentication tag, a further analysis should be discussed as follows.
Case 2-1: If , the last two tweaks and are new. The adversary tries to forge an identical tag () using a new nonce . The image of a single point under a tweakable random permutation is uniform, so the generated tag is an independent and uniform random value. Thus, the probability that the adversary correctly forges an identical tag () is .
Case 2-2: If and , the last two tweaks and are new. The adversary tries to forge an identical tag () using a new block length . The image of a single point under a tweakable random permutation is uniform, so the generated tag is an independent and uniform random value. Thus, the probability that the adversary correctly forges an identical tag () is .
Case 2-3: If and , the last two tweaks and in this case are the same as those of the previous query–response pair . According to , where and for all , a further discussion should be considered as follows.
- . Let , where . Under the condition that (), are distinct from each other. According to , we consider the following two cases.
- (a)
- is new, i.e., . The probability that this case occurs is .
- is new. Then, is new. The adversary tries to forge an identical tag () using a new ciphertext block . Therefore, the probability that the adversary correctly forges an identical tag () is .
- is old and is new. Then, is old and there exists at least one more fresh value in . According to whether is new or not, the following subcases are discussed.
- is new, i.e., . The probability that this case occurs is about . The adversary tries to forge an identical tag using a new checksum . Thus, the probability that the adversary’s forgery attempt succeeds is .
- is old, i.e., . According to the fact that for any , where c is a constant from , the probability that is old is at most . As , , and are old, the probability of obtaining an identical tag is 1. Therefore, the probability that the adversary can guess the correct value in this case is the probability that is old, which is at most .
- is old. Then, is old, where . According to ; then, is a fresh random value. The adversary tries to forge an identical tag () using new associated data (or a new checksum ). Therefore, the probability that the adversary can guess the correct value is .
Summarizing the cases of (a), the probability that the adversary can guess the correct value is at most . - (b)
- is old, i.e., . The probability that this case occurs is .
- is new. Then, is new. The adversary tries to forge an identical tag () using a new ciphertext block . Therefore, the probability that the adversary correctly forges an identical tag () is .
- is old and is new. Then, is old and there exists at least one more fresh value in . If there only exists one fresh value in , according to , then is new. Therefore, the probability that the adversary’s forgery attempt succeeds is . If there exist at least two more fresh values in , according to whether is new or not, the following subcases are discussed.
- is new, i.e., . The probability that this case occurs is about . The adversary tries to forge an identical tag using a new checksum . Thus, the probability that the adversary’s forgery attempt succeeds is .
- is old, i.e., . According to the fact that for any , where c is a constant from , the probability that is old is at most . As , and are old, the probability of obtaining an identical tag is 1. Therefore, the probability that the adversary can guess the correct value in this case is the probability that is old, which is at most .
- is old. Then, is old, where . As , , and are old, the probability that the adversary can guess the correct value is 1.
Summarizing the cases of (b), the probability that the adversary can guess the correct value is at most .
- ; then, . As ; therefore, must be new.
- (a)
- is new. Then, is new. The adversary tries to forge an identical tag () using a new ciphertext block . Therefore, the probability that the adversary correctly forges an identical tag () is .
- (b)
- is old and is new. Then, is old and there exists at least one more fresh value in .
- If there only exists one fresh value in , according to , then is new. The adversary tries to forge an identical tag using a new checksum . Therefore, the probability that the adversary’s forgery attempt succeeds is .
- If there exist at least two more fresh values in , according to whether is new or not, the following subcases are discussed.
- is new, i.e., . The probability that this case occurs is about . The adversary tries to forge an identical tag using a new checksum . Thus, the probability that the adversary’s forgery attempt succeeds is .
- is old, i.e., . According to the fact that for any , where c is a constant from , the probability that is old is at most . As , , and are old, the probability of obtaining is 1. Therefore, the probability that the adversary can guess the correct value in this case is the probability that is old, which is at most .
Summarizing all cases above, the successful probability of the single forgery attempt is upper-bounded by
Therefore, for forgery attempts, the probability that event occurs under the condition is
Combining Equations (1)–(4), the INT-RUP advantage of , after q encryption and decryption queries, and forgery queries, is
The proof of Theorem 2 is finished. □
Theorem 3
(INT-RUP security of COPA-PIC based on TBCs). Let be a TBC, where is a tweak space, is a nonce space, is a large-integer set, and is a small-integer set. Let be a nonce-misusing adversary with q encryption and decryption queries and forgery attempts. For COPA-PIC[], one has
where for some absolute constant c, and l is the maximum block length.
Proof.
For COPA-PIC[], all TBCs are replaced with tweakable random permutations to obtain COPA-PIC[], where and is a tweak space.
Let be the total query complexity of message blocks for queries. According to the MTPRP advantage, COPA-PIC[] can be replaced with COPA-PIC[], which together cost at most (here, comes from the queries of TBCs in the upper and lower layers; in other words, is the query complexity of TBCs), i.e.,
Therefore, combining Equation (5) and Theorem 2, it is easy to obtain the bound of Theorem 3. □
4.2. Blockcipher-Based COPA-PIC Instance: COPA-PIC[E]
Let be a block cipher and be a TBC, where is a key space and is a tweak space. This section presents a blockcipher-based instance of COPA-PIC[] by the XEX* construction [6] and renames it as COPA-PIC[E].
The overviews of COPA-PIC[E] and blockcipher-based PMAC1 are depicted in Figure 4 and Figure 5, respectively. The blockcipher-based PMAC1 algorithm, and an encryption algorithm , a decryption algorithm , and a verification algorithm of COPA-PIC[E] are shown in Algorithms 5, 6, 7, and 8, respectively.
| Algorithm 5 Blockcipher-based PMAC1 algorithm |
|
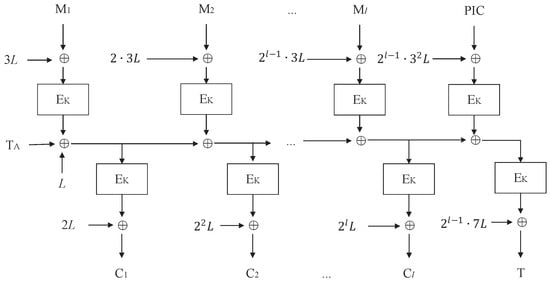
Figure 4.
Blockcipher-based COPA-PIC: COPA-PIC[E], where and .
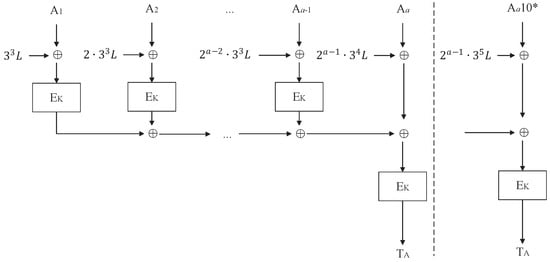
Figure 5.
Blockcipher-based PMAC1: , where .
| Algorithm 6 Encryption algorithm |
|
| Algorithm 7 Decryption algorithm |
|
Theorem 4
(INT-RUP security of COPA-PIC based on block ciphers). Let be a block cipher and be a TBC, where is a key space, is a tweak space, is a nonce space, is a large-integer set, and is a small-integer set. Let and assume that for all . Then, for a nonce-misusing adversary , one has
where a new adversary has an additional running time equal to the time needed to process the queries from .
Proof.
The security proof includes two steps. First, COPA-PIC[E] is converted to COPA-PIC[]. The dummy masks and , are introduced to the upper and lower layers of COPA-PIC[E], respectively, in terms of the XEX* construction, where . Therefore, distinct TBCs , and are utilized to replace the block ciphers with distinct masks, where . For the blockcipher-based PMAC1, distinct TBCs , and are utilized to replace the block ciphers with distinct masks, where . According to Lemma 1 and the blockcipher-based PMAC1 [6], COPA-PIC[E] can be replaced with COPA-PIC[], which together cost
Then, combining Equation (6) and Theorem 3, the bound of Theorem 4 is obtained. □
| Algorithm 8 Verification algorithm |
|
4.3. Permutation-Based COPA-PIC Instance: COPA-PIC[]
Let be a public n-bit permutation, be a set of k-bit keys, be a tweak space, be a set of large integers, and be a set of small integers, we reload COPA-PIC[] by [22] to obtain an instance called COPA-PIC[].
Let , and T be the key, the nonce, the associated data, the plaintext, the ciphertext, and the authentication tag, respectively. The overviews of COPA-PIC[] and PMAC1 are depicted in Figure 6 and Figure 7, respectively. The PMAC1 algorithm and an encryption algorithm , a decryption algorithm , and a verification algorithm of COPA-PIC[] are shown in Algorithms 9, 10, 11, and 12, respectively.
| Algorithm 9 Permutation-based PMAC1 algorithm |
|
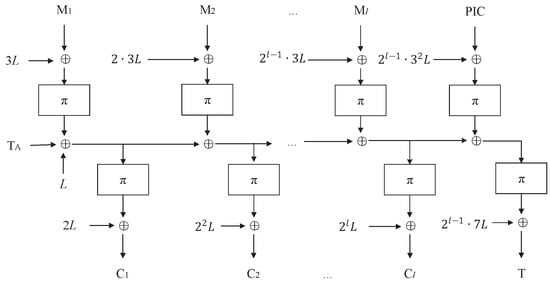
Figure 6.
Permutation-based COPA-PIC: COPA-PIC[], where and .
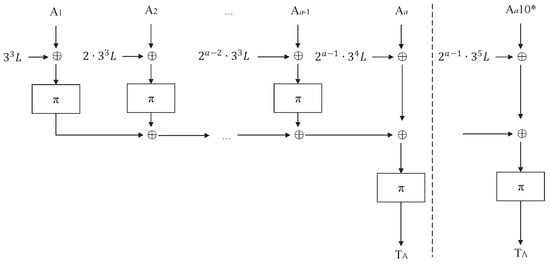
Figure 7.
Permutation-based PMAC1: , where .
| Algorithm 10 Encryption algorithm |
|
| Algorithm 11 Decryption algorithm |
|
| Algorithm 12 Verification algorithm |
|
For an INT-RUP security model with a permutation, the adversary is allowed to make queries in addition to the previous oracle queries; then, the INT-RUP-advantage of against is defined as
Theorem 5
(INT-RUP security of COPA-PIC based on permutations). Let be a public n-bit permutation and be a TBC, where is a key space, is a tweak space, is a nonce space, is a large-integer set, and is a small-integer set. Assume that for all . Let . For a nonce-misusing adversary , one has
Proof.
Similar to the proof of Theorem 4, the security proof includes two steps. First, COPA-PIC[] is converted to COPA-PIC[]. The dummy masks and are introduced to the upper and lower layers of COPA-PIC[], respectively, in terms of the MEM construction, where . Therefore, distinct TBCs , and are utilized to replace permutations with distinct masks, where . For the permutation-based PMAC1, distinct TBCs , and are utilized to replace permutations with distinct masks, where . According to Lemma 2 and the permutation-based PMAC1 [6], COPA-PIC[] can be replaced with COPA-PIC[], which together cost
Then, combining Equation (7) and Theorem 3, the bound of Theorem 5 is obtained. □
5. Discussions and Future Works
COPA-PIC is a secure “rate-1/2” parallelizable delayed authenticated online cipher with nonce-misuse resistance. The structure of COPA-PIC is the same as that of COPA except that the authentication checksum is replaced with PIC. Therefore, COPA-PIC inherits all the advantages of COPA and calculates the authentication tag ahead of time in the verification oracle. It can be viewed as an instance of the generic B1 scheme introduced by Namprempre et al. [40]. At the beginning of the design, TBCs are used to improve COPA from the perspective of a top-level design, and the updating of the tweaks is as simple as possible. Then, by using the XEX* construction [6] and the MEM construction [22], provably secure block-cipher-based and permutation-based instances are presented. For the update of tweaks, a simple and efficient technique—point doubling is used to update tweaks. This technique follows the framework of the XEX* and MEM constructions, which makes proposed instances and proofs very simple. This paper considers the message whose length is a positive multiple of the block size n. In fact, for any length message, it also works.
There have been many studies on COPA in recent years [1,13,41,42]. Among them, the INT-RUP security is one of the most important research contents. COPA-PIC enjoys INT-RUP security up to the birthday bound in the nonce-misuse setting if the underlying primitive (including TBC, block cipher, and permutation) is secure. Of course, COPA-PIC just settles the problem of INT-RUP in the nonce-misuse setting, while the problem of privacy in the RUP setting still exists. It is left as an open problem to settle the privacy of COPA-PIC in the RUP setting.
COPA-PIC utilizes a new checksum technique—polynomial intermediate checksum (PIC)—to fix the INT-RUP security. PIC is a very vital technique which guarantees no information leakage and the same level between the plaintext and the ciphertext. In the AE schemes with PIC, the adversary cannot obtain any useful information to make a successful forgery even if given the additional power of access to an unverified decryption oracle. mCPFB with INT-RUP security combines a distance 4 error correcting code and delayed dislocation technique which is essentially a similar PIC technique. LOCUS and LOTUS are based on OCB and OTR, and their final checksum utilizes IC, which is a degenerated version of PIC. Table 2 shows the comparison of AE modes with distinct checksum techniques. Our work finds a new technique, PIC, and we believe that PIC can settle the INT-RUP security defects of any “rate < 1” and “Encryption-Mix-Encryption”-type checksum-based AE schemes. In addition, the mixing function of COLM (ELmE/ELmD) essentially provides an implementation of PIC for the authentication part, but COLM (ELmE/ELmD) also utilizes PCC in the authentication part. In fact, COLM (ELmE/ELmD) could have been designed entirely using PIC.

Table 2.
Comparison of AE modes with distinct checksum techniques.
The proposed work is of high practical significance to establish a rapid feedback mechanism for third-party error authentication. The computational costs of COPA-PIC’s encryption and decryption algorithms are about the same as those of COPA, but the verification cost is close to one half of COPA (see Table 1). Thus, in practical applications, the receiver first verifies whether the received message is valid or not, and then determines whether to perform the next action (decrypt and obtain the correct plaintext or reject and return an error symbol). The proposed work supports Chakraborti et al.’s works and Zhang and Wu’s views, introduces a new intermediate checksum technique, PIC, and gives a possible direction for settling the security of all one-pass checksum-based AE schemes in the RUP setting. Recently, Andreeva et al. focused on SAEF which is a rate-1 online AE mode using a forkcipher as a building block, and they showed that SAEF is INT-RUP-secure up to the birthday bound by the H-coefficient technique [17]. Therefore, forkcipher is a hot future research direction. Additionally, there have been some achievements in RUP security for two-pass AE schemes in recent years, such as GCM-RUP [43] and its variant [44]. This is also a direction to watch in the future.
Funding
This work was supported by National Natural Science Foundation of China (Grant Nos. 61902195, 62272238 and U23B2002) and NUPTSF (Grant Nos. NY219131 and NY2019004).
Data Availability Statement
The data used to support the findings of the study are available within the article.
Acknowledgments
I am grateful to Peng Wang and Honggang Hu et al. for providing some good suggestions on PIC and COPA-PIC. I would also like to express my sincere thanks to the editors and the anonymous reviewers for the valuable comments and suggestions.
Conflicts of Interest
The author declares no conflicts of interest.
Abbreviations
The following abbreviations are used in this manuscript:
| the nonempty set of keys (the key space) | |
| the nonempty set of tweaks (the tweak space) | |
| the nonempty set of nonces (the nonce space) | |
| the nonempty set of associated data (the associated data space) | |
| the nonempty set of plaintexts (the plaintext space) | |
| the nonempty set of ciphertexts (the ciphertext space) | |
| the nonempty set of authentication tags (the authentication tag space) | |
| the encryption of block ciphers with a key K | |
| the decryption of block ciphers with a key K | |
| the encryption and decryption oracles of block ciphers with a key K | |
| the encryption of tweakable blockciphers with a key K | |
| the decryption of tweakable blockciphers with a key K | |
| the encryption and decryption oracles of tweakable blockciphers with a key K | |
| the set of all n-bit permutations | |
| the permutation and its inverse | |
| the set of all n-bit tweakable permutations with the tweak space | |
| the tweakable permutation and its inverse | |
| the set containing all finite bit strings (including the empty string) | |
| the nonempty set containing all n-bit strings | |
| the adversary outputs 1 after interacting with the oracle O | |
| the value x randomly chosen from the set X | |
| the probability of the event | |
| the encryption algorithm | |
| the decryption algorithm | |
| the verification algorithm | |
| the bit length of the finite string x | |
| or | the concatenation of two finite strings x and y |
| ⊕ | the XOR/addition operation over the finite field |
| · | the multiplication operation over the finite field |
| a set of large integers, such as | |
| a set of small integers, such as |
References
- Andreeva, E.; Bogdanov, A.; Luykx, A.; Mennink, B.; Mouha, N.; Yasuda, K. How to Securely Release Unverified Plaintext in Authenticated Encryption. In Proceedings of the Advances in Cryptology-ASIACRYPT 2014-20th International Conference on the Theory and Application of Cryptology and Information Security, Kaoshiung, Taiwan, 7–11 December 2014; Sarkar, P., Iwata, T., Eds.; Springer: Berlin/Heidelberg, Germany, 2014; Volume 8873, pp. 105–125. [Google Scholar] [CrossRef]
- Vaudenay, S. Security Flaws Induced by CBC Padding-Applications to SSL, IPSEC, WTLS. In Proceedings of the Advances in Cryptology-EUROCRYPT 2002, International Conference on the Theory and Applications of Cryptographic Techniques, Amsterdam, The Netherlands, 28 April–2 May 2002; Knudsen, L.R., Ed.; Springer: Berlin/Heidelberg, Germany, 2002; Volume 2332, pp. 534–546. [Google Scholar] [CrossRef]
- Canvel, B.; Hiltgen, A.P.; Vaudenay, S.; Vuagnoux, M. Password Interception in a SSL/TLS Channel. In Proceedings of the Advances in Cryptology-CRYPTO 2003, 23rd Annual International Cryptology Conference, Santa Barbara, CA, USA, 17–21 August 2003; Boneh, D., Ed.; Springer: Berlin/Heidelberg, Germany, 2003; Volume 2729, pp. 583–599. [Google Scholar] [CrossRef]
- AlFardan, N.J.; Paterson, K.G. Lucky Thirteen: Breaking the TLS and DTLS Record Protocols. In Proceedings of the 2013 IEEE Symposium on Security and Privacy, SP 2013, Berkeley, CA, USA, 19–22 May 2013; pp. 526–540. [Google Scholar] [CrossRef]
- Rogaway, P.; Bellare, M.; Black, J. OCB: A block-cipher mode of operation for efficient authenticated encryption. ACM Trans. Inf. Syst. Secur. 2003, 6, 365–403. [Google Scholar] [CrossRef]
- Rogaway, P. Efficient Instantiations of Tweakable Blockciphers and Refinements to Modes OCB and PMAC. In Proceedings of the Advances in Cryptology-ASIACRYPT 2004, 10th International Conference on the Theory and Application of Cryptology and Information Security, Jeju Island, Republic of Korea, 5–9 December 2004; Lee, P.J., Ed.; Springer: Berlin/Heidelberg, Germany, 2004; Volume 3329, pp. 16–31. [Google Scholar] [CrossRef]
- Krovetz, T.; Rogaway, P. The Software Performance of Authenticated-Encryption Modes. In Proceedings of the Fast Software Encryption-18th International Workshop, FSE 2011, Lyngby, Denmark, 13–16 February 2011; Joux, A., Ed.; Springer: Berlin/Heidelberg, Germany, 2011; Volume 6733, pp. 306–327. [Google Scholar] [CrossRef]
- Andreeva, E.; Bogdanov, A.; Luykx, A.; Mennink, B.; Tischhauser, E.; Yasuda, K. Parallelizable and Authenticated Online Ciphers. In Proceedings of the Advances in Cryptology-ASIACRYPT 2013-19th International Conference on the Theory and Application of Cryptology and Information Security, Bengaluru, India, 1–5 December 2013; Sako, K., Sarkar, P., Eds.; Springer: Berlin/Heidelberg, Germany, 2013; Volume 8269, pp. 424–443. [Google Scholar] [CrossRef]
- Zhang, P.; Wang, P.; Hu, H.; Cheng, C.; Kuai, W. INT-RUP Security of Checksum-Based Authenticated Encryption. In Proceedings of the Provable Security-11th International Conference, ProvSec 2017, Xi’an, China, 23–25 October 2017; Okamoto, T., Yu, Y., Au, M.H., Li, Y., Eds.; Springer: Berlin/Heidelberg, Germany, 2017; Volume 10592, pp. 147–166. [Google Scholar] [CrossRef]
- Zhang, P.; Wang, P.; Hu, H. The INT-RUP Security of OCB with Intermediate (Parity) Checksum. IACR Cryptol. ePrint Arch. 2016, 1059. Available online: https://eprint.iacr.org/2016/1059 (accessed on 25 March 2024).
- Chakraborti, A.; Datta, N.; Nandi, M. INT-RUP Analysis of Block-cipher Based Authenticated Encryption Schemes. In Proceedings of the Topics in Cryptology-CT-RSA 2016-The Cryptographers’ Track at the RSA Conference 2016, San Francisco, CA, USA, 29 February–4 March 2016; Sako, K., Ed.; Springer: Berlin/Heidelberg, Germany, 2016; Volume 9610, pp. 39–54. [Google Scholar] [CrossRef]
- Zhang, J.; Wu, W. Security of Online AE Schemes in RUP Setting. In Proceedings of the Cryptology and Network Security-15th International Conference, CANS 2016, Milan, Italy, 14–16 November 2016; Foresti, S., Persiano, G., Eds.; 2016; Volume 10052, pp. 319–334. [Google Scholar] [CrossRef]
- Datta, N.; Luykx, A.; Mennink, B.; Nandi, M. Understanding RUP Integrity of COLM. IACR Trans. Symmetric Cryptol. 2017, 2017, 143–161. [Google Scholar] [CrossRef]
- Hirose, S.; Sasaki, Y.; Yasuda, K. Rate-One AE with Security Under RUP. In Proceedings of the Information Security-20th International Conference, ISC 2017, Ho Chi Minh City, Vietnam, 22–24 November 2017; Nguyen, P.Q., Zhou, J., Eds.; Springer: Berlin/Heidelberg, Germany, 2017; Volume 10599, pp. 3–20. [Google Scholar] [CrossRef]
- Chakraborti, A.; Datta, N.; Jha, A.; Mancillas-López, C.; Nandi, M.; Sasaki, Y. INT-RUP Secure Lightweight Parallel AE Modes. IACR Trans. Symmetric Cryptol. 2019, 2019, 81–118. [Google Scholar] [CrossRef]
- Chang, D.; Datta, N.; Dutta, A.; Mennink, B.; Nandi, M.; Sanadhya, S.; Sibleyras, F. Release of Unverified Plaintext: Tight Unified Model and Application to ANYDAE. IACR Trans. Symmetric Cryptol. 2019, 2019, 119–146. [Google Scholar] [CrossRef]
- Andreeva, E.; Bhati, A.S.; Vizár, D. RUP Security of the SAEF Authenticated Encryption mode. IACR Cryptol. ePrint Arch. 2021, 2021, 103. [Google Scholar]
- Datta, N.; Dutta, A.; Ghosh, S. INT-RUP Security of SAEB and TinyJAMBU. In Proceedings of the Progress in Cryptology-INDOCRYPT 2022-23rd International Conference on Cryptology in India, Kolkata, India, 11–14 December 2022; Isobe, T., Sarkar, S., Eds.; Springer: Berlin/Heidelberg, Germany, 2022; Volume 13774, pp. 146–170. [Google Scholar] [CrossRef]
- Bao, Z.; Guo, J.; Iwata, T.; Minematsu, K. ZOCB and ZOTR: Tweakable Blockcipher Modes for Authenticated Encryption with Full Absorption. IACR Trans. Symmetric Cryptol. 2019, 2019, 1–54. [Google Scholar] [CrossRef]
- Inoue, A.; Iwata, T.; Minematsu, K.; Poettering, B. Cryptanalysis of OCB2: Attacks on Authenticity and Confidentiality. In Proceedings of the Advances in Cryptology-CRYPTO 2019-39th Annual International Cryptology Conference, Santa Barbara, CA, USA, 18–22 August 2019; Boldyreva, A., Micciancio, D., Eds.; Springer: Berlin/Heidelberg, Germany, 2019; Volume 11692, pp. 3–31. [Google Scholar] [CrossRef]
- Chakraborty, D.; Nandi, M. Attacks on the Authenticated Encryption Mode of Operation PAE. IEEE Trans. Inf. Theory 2015, 61, 5636–5642. [Google Scholar] [CrossRef]
- Granger, R.; Jovanovic, P.; Mennink, B.; Neves, S. Improved Masking for Tweakable Blockciphers with Applications to Authenticated Encryption. In Proceedings of the Advances in Cryptology-EUROCRYPT 2016 - 35th Annual International Conference on the Theory and Applications of Cryptographic Techniques, Vienna, Austria, 8–12 May 2016; Fischlin, M., Coron, J., Eds.; Springer: Berlin/Heidelberg, Germany, 2016; Volume 9665, pp. 263–293. [Google Scholar] [CrossRef]
- Jutla, C.S. Encryption Modes with Almost Free Message Integrity. In Proceedings of the Advances in Cryptology-EUROCRYPT 2001, International Conference on the Theory and Application of Cryptographic Techniques, Innsbruck, Austria, 6–10 May 2001; Pfitzmann, B., Ed.; Springer: Berlin/Heidelberg, Germany, 2001; Volume 2045, pp. 529–544. [Google Scholar] [CrossRef]
- Bossuet, L.; Datta, N.; Mancillas-López, C.; Nandi, M. ELmD: A Pipelineable Authenticated Encryption and Its Hardware Implementation. IEEE Trans. Comput. 2016, 65, 3318–3331. [Google Scholar] [CrossRef]
- Datta, N.; Nandi, M. ELmE: A Misuse Resistant Parallel Authenticated Encryption. In Proceedings of the Information Security and Privacy-19th Australasian Conference, ACISP 2014, Wollongong, NSW, Australia, 7–9 July 2014; Susilo, W., Mu, Y., Eds.; Springer: Berlin/Heidelberg, Germany, 2014; Volume 8544, pp. 306–321. [Google Scholar] [CrossRef]
- Abed, F.; Fluhrer, S.R.; Forler, C.; List, E.; Lucks, S.; McGrew, D.A.; Wenzel, J. Pipelineable On-line Encryption. In Proceedings of the Fast Software Encryption-21st International Workshop, FSE 2014, London, UK, 3–5 March 2014; Cid, C., Rechberger, C., Eds.; Springer: Berlin/Heidelberg, Germany, 2014; Volume 8540, pp. 205–223. [Google Scholar] [CrossRef]
- Fleischmann, E.; Forler, C.; Lucks, S. McOE: A Family of Almost Foolproof On-Line Authenticated Encryption Schemes. In Proceedings of the Fast Software Encryption-19th International Workshop, FSE 2012, Washington, DC, USA, 19–21 March 2012; Canteaut, A., Ed.; Springer: Berlin/Heidelberg, Germany, 2012; Volume 7549, pp. 196–215. [Google Scholar] [CrossRef]
- Naito, Y.; Sasaki, Y.; Sugawara, T. Lightweight Authenticated Encryption Mode Suitable for Threshold Implementation. In Proceedings of the Advances in Cryptology-EUROCRYPT 2020 - 39th Annual International Conference on the Theory and Applications of Cryptographic Techniques, Zagreb, Croatia, 10–14 May 2020; Canteaut, A., Ishai, Y., Eds.; Springer: Berlin/Heidelberg, Germany, 2020; Volume 12106, pp. 705–735. [Google Scholar] [CrossRef]
- Naito, Y.; Sugawara, T. Lightweight Authenticated Encryption Mode of Operation for Tweakable Block Ciphers. IACR Trans. Cryptogr. Hardw. Embed. Syst. 2020, 2020, 66–94. [Google Scholar] [CrossRef]
- Naito, Y. Tweakable Blockciphers for Efficient Authenticated Encryptions with Beyond the Birthday-Bound Security. IACR Trans. Symmetric Cryptol. 2017, 2017, 1–26. [Google Scholar] [CrossRef]
- Peyrin, T.; Seurin, Y. Counter-in-Tweak: Authenticated Encryption Modes for Tweakable Block Ciphers. In Proceedings of the Advances in Cryptology-CRYPTO 2016-36th Annual International Cryptology Conference, Santa Barbara, CA, USA, 14–18 August 2016; Robshaw, M., Katz, J., Eds.; Springer: Berlin/Heidelberg, Germany, 2016; Volume 9814, pp. 33–63. [Google Scholar] [CrossRef]
- Mennink, B. XPX: Generalized Tweakable Even-Mansour with Improved Security Guarantees. In Proceedings of the Advances in Cryptology-CRYPTO 2016-36th Annual International Cryptology Conference, Santa Barbara, CA, USA, 14–18 August 2016; Robshaw, M., Katz, J., Eds.; Springer: Berlin/Heidelberg, Germany, 2016; Volume 9814, pp. 64–94. [Google Scholar] [CrossRef]
- Cogliati, B.; Lampe, R.; Seurin, Y. Tweaking Even-Mansour Ciphers. In Proceedings of the Advances in Cryptology-CRYPTO 2015-35th Annual Cryptology Conference, Santa Barbara, CA, USA, 16–20 August 2015; Gennaro, R., Robshaw, M., Eds.; Springer: Berlin/Heidelberg, Germany, 2015; Volume 9215, pp. 189–208. [Google Scholar] [CrossRef]
- Cogliati, B.; Seurin, Y. Beyond-Birthday-Bound Security for Tweakable Even-Mansour Ciphers with Linear Tweak and Key Mixing. In Proceedings of the Advances in Cryptology-ASIACRYPT 2015-21st International Conference on the Theory and Application of Cryptology and Information Security, Auckland, New Zealand, 29 November–3 December 2015; Iwata, T., Cheon, J.H., Eds.; Springer: Berlin/Heidelberg, Germany, 2015; Volume 9453, pp. 134–158. [Google Scholar] [CrossRef]
- Landecker, W.; Shrimpton, T.; Terashima, R.S. Tweakable Blockciphers with Beyond Birthday-Bound Security. In Proceedings of the Advances in Cryptology-CRYPTO 2012-32nd Annual Cryptology Conference, Santa Barbara, CA, USA, 19–23 August 2012; Safavi-Naini, R., Canetti, R., Eds.; Springer: Berlin/Heidelberg, Germany, 2012; Volume 7417, pp. 14–30. [Google Scholar] [CrossRef]
- Liskov, M.D.; Rivest, R.L.; Wagner, D.A. Tweakable Block Ciphers. J. Cryptol. 2011, 24, 588–613. [Google Scholar] [CrossRef]
- Minematsu, K. Beyond-Birthday-Bound Security Based on Tweakable Block Cipher. In Proceedings of the Fast Software Encryption, 16th International Workshop, FSE 2009, Leuven, Belgium, 22–25 February 2009; Dunkelman, O., Ed.; Springer: Berlin/Heidelberg, Germany, 2009; Volume 5665, pp. 308–326. [Google Scholar] [CrossRef]
- Chakraborty, D.; Sarkar, P. A General Construction of Tweakable Block Ciphers and Different Modes of Operations. IEEE Trans. Inf. Theory 2008, 54, 1991–2006. [Google Scholar] [CrossRef]
- Liskov, M.D.; Rivest, R.L.; Wagner, D.A. Tweakable Block Ciphers. In Proceedings of the Advances in Cryptology-CRYPTO 2002, 22nd Annual International Cryptology Conference, Santa Barbara, CA, USA, 18–22 August 2002; Yung, M., Ed.; Springer: Berlin/Heidelberg, Germany, 2002; Volume 2442, pp. 31–46. [Google Scholar] [CrossRef]
- Namprempre, C.; Rogaway, P.; Shrimpton, T. Reconsidering Generic Composition. In Proceedings of the Advances in Cryptology-EUROCRYPT 2014-33rd Annual International Conference on the Theory and Applications of Cryptographic Techniques, Copenhagen, Denmark, 11–15 May 2014; Nguyen, P.Q., Oswald, E., Eds.; Springer: Berlin/Heidelberg, Germany, 2014; Volume 8441, pp. 257–274. [Google Scholar] [CrossRef]
- Xu, Y.; Liu, W.; Yu, W. Quantum forgery attacks on COPA, AES-COPA and marble authenticated encryption algorithms. Quantum Inf. Process. 2021, 20, 131. [Google Scholar] [CrossRef]
- Bossuet, L.; Mancillas-López, C.; Ovilla-Martinez, B. Pipelined Hardware Implementation of COPA, ELmD, and COLM. IEEE Trans. Comput. 2020, 69, 1533–1543. [Google Scholar] [CrossRef]
- Ashur, T.; Dunkelman, O.; Luykx, A. Boosting Authenticated Encryption Robustness with Minimal Modifications. In Proceedings of the Advances in Cryptology-CRYPTO 2017-37th Annual International Cryptology Conference, Santa Barbara, CA, USA, 20–24 August 2017; Katz, J., Shacham, H., Eds.; Springer: Berlin/Heidelberg, Germany, 2017; Volume 10403, pp. 3–33. [Google Scholar] [CrossRef]
- Li, Y.; Leurent, G.; Wang, M.; Wang, W.; Zhang, G.; Liu, Y. Universal Forgery Attack Against GCM-RUP. In Proceedings of the Topics in Cryptology-CT-RSA 2020-The Cryptographers’ Track at the RSA Conference 2020, San Francisco, CA, USA, 24–28 February 2020; Jarecki, S., Ed.; Springer: Berlin/Heidelberg, Germany, 2020; Volume 12006, pp. 15–34. [Google Scholar] [CrossRef]
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2024 by the author. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).