Practical Security of Continuous Variable Measurement- Device-Independent Quantum Key Distribution with Local Local Oscillator
Abstract
1. Introduction
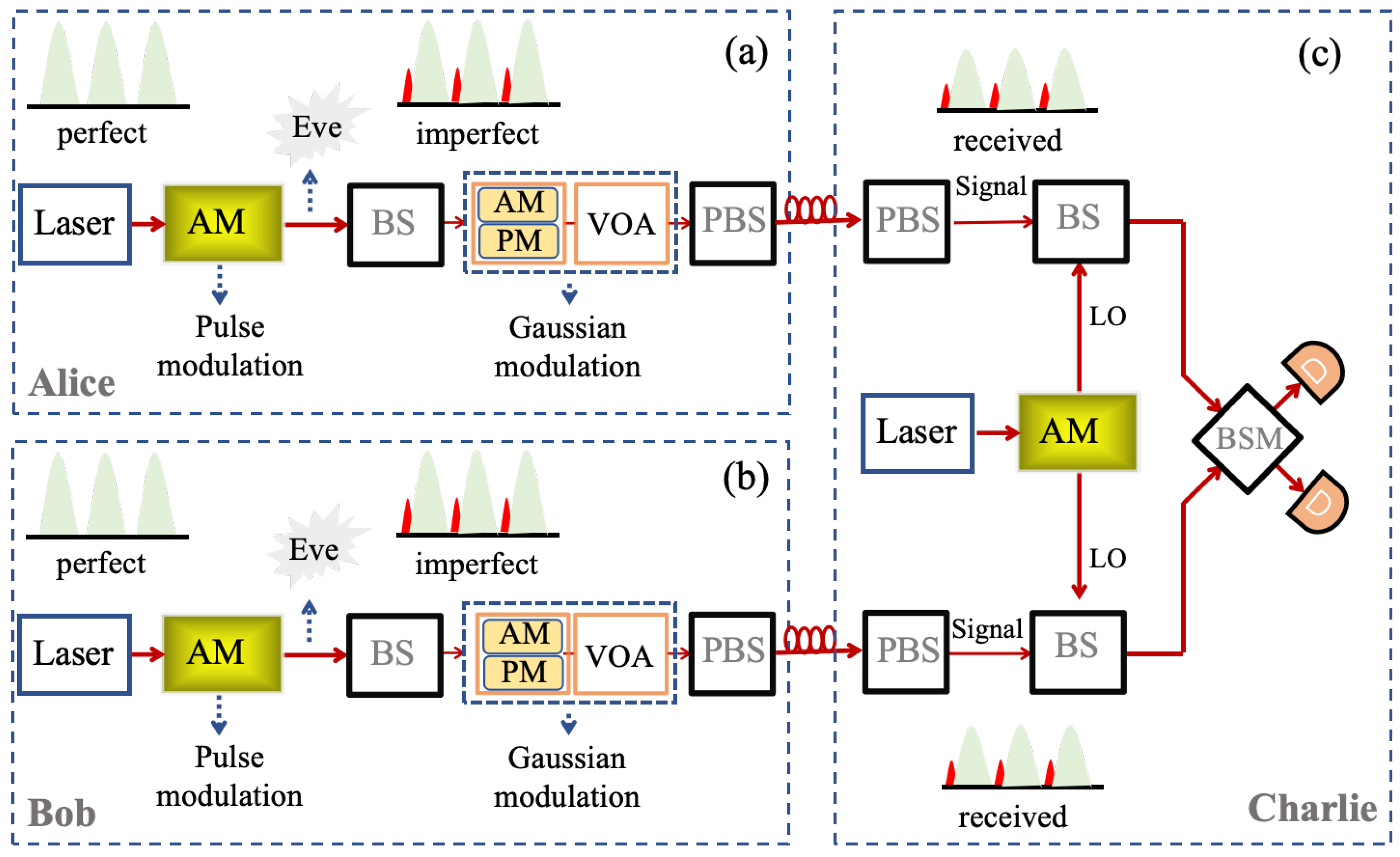
2. LLO-Based CV-MDI-QKD
2.1. CV-MDI-QKD Embedded with AM
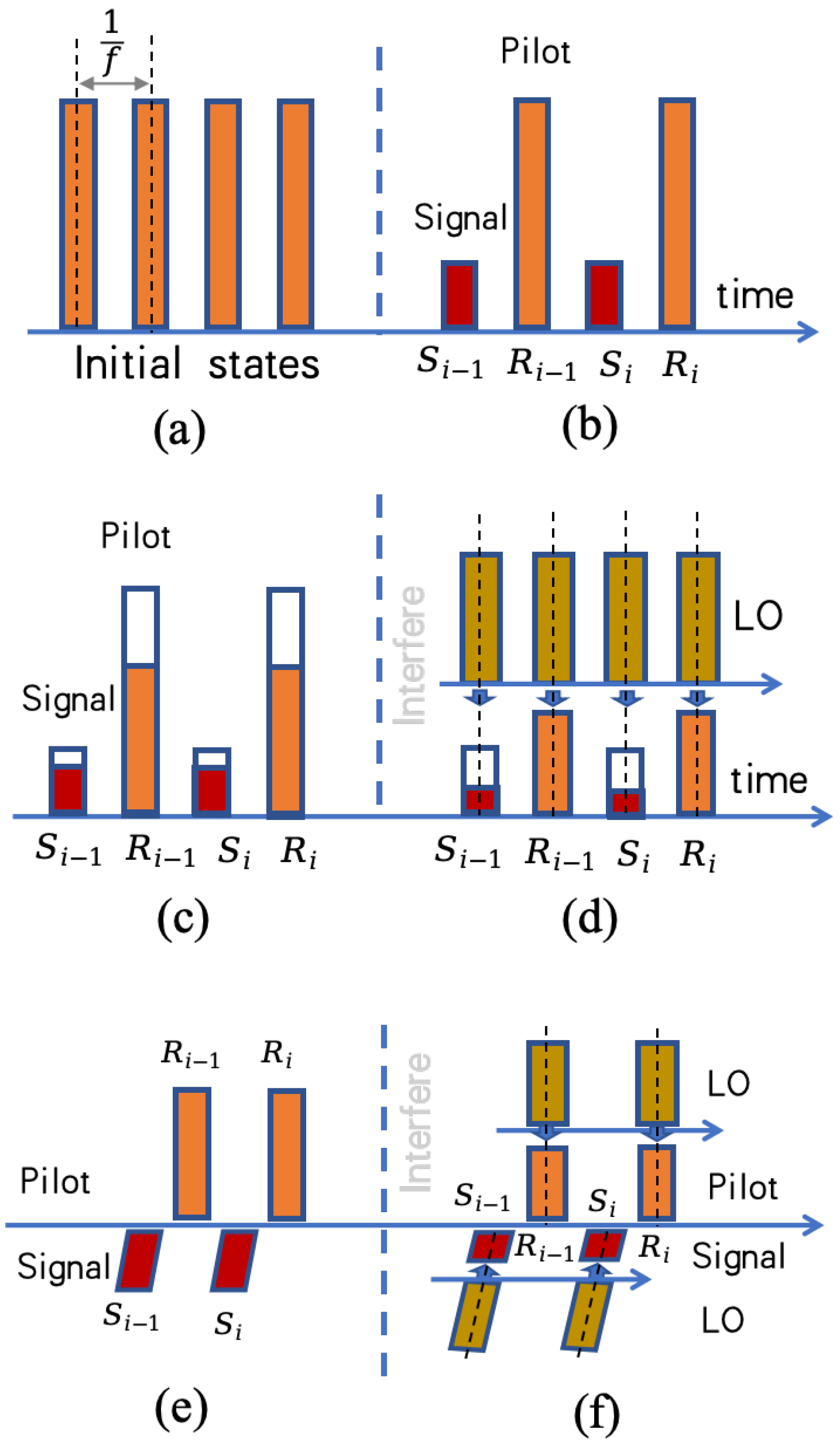
2.2. LLO Scheme with Orthogonal Block Transformation
3. Noise Analysis
3.1. Phase Noise
3.2. Photon Leakage Noise
4. Performance Analysis
4.1. AM Information Leakage
4.2. Security Analysis
4.2.1. Derivation of the Secret Key Rate
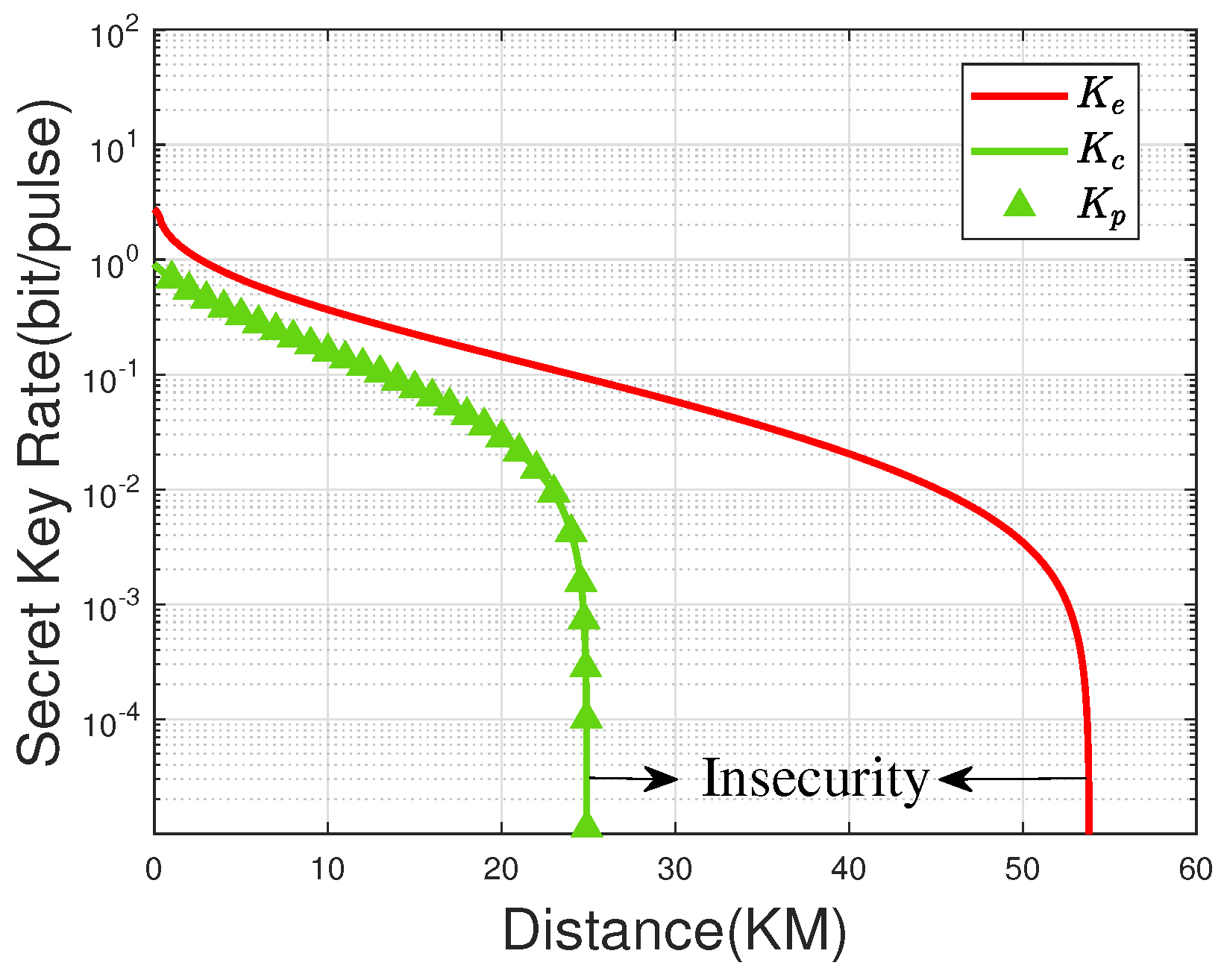
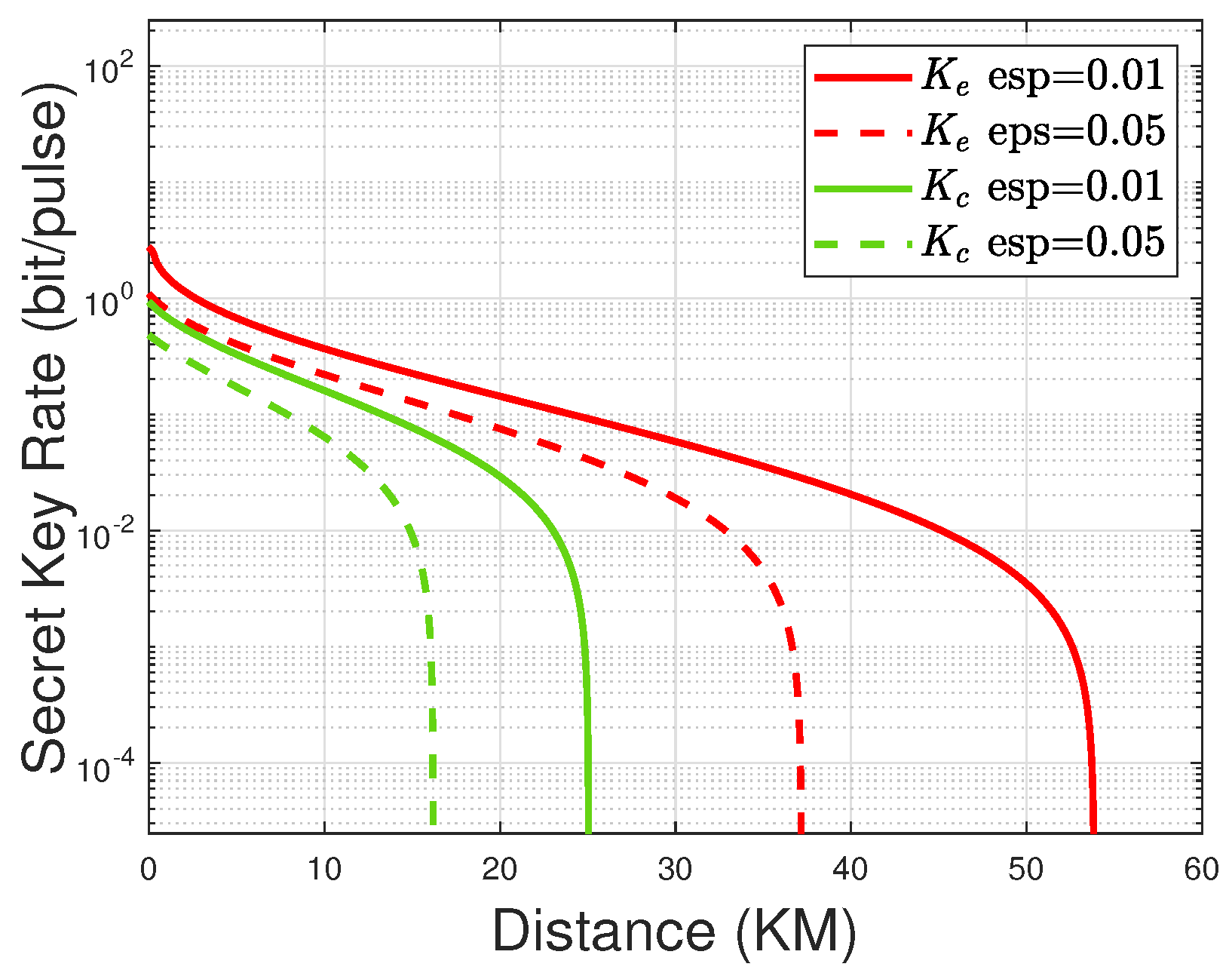
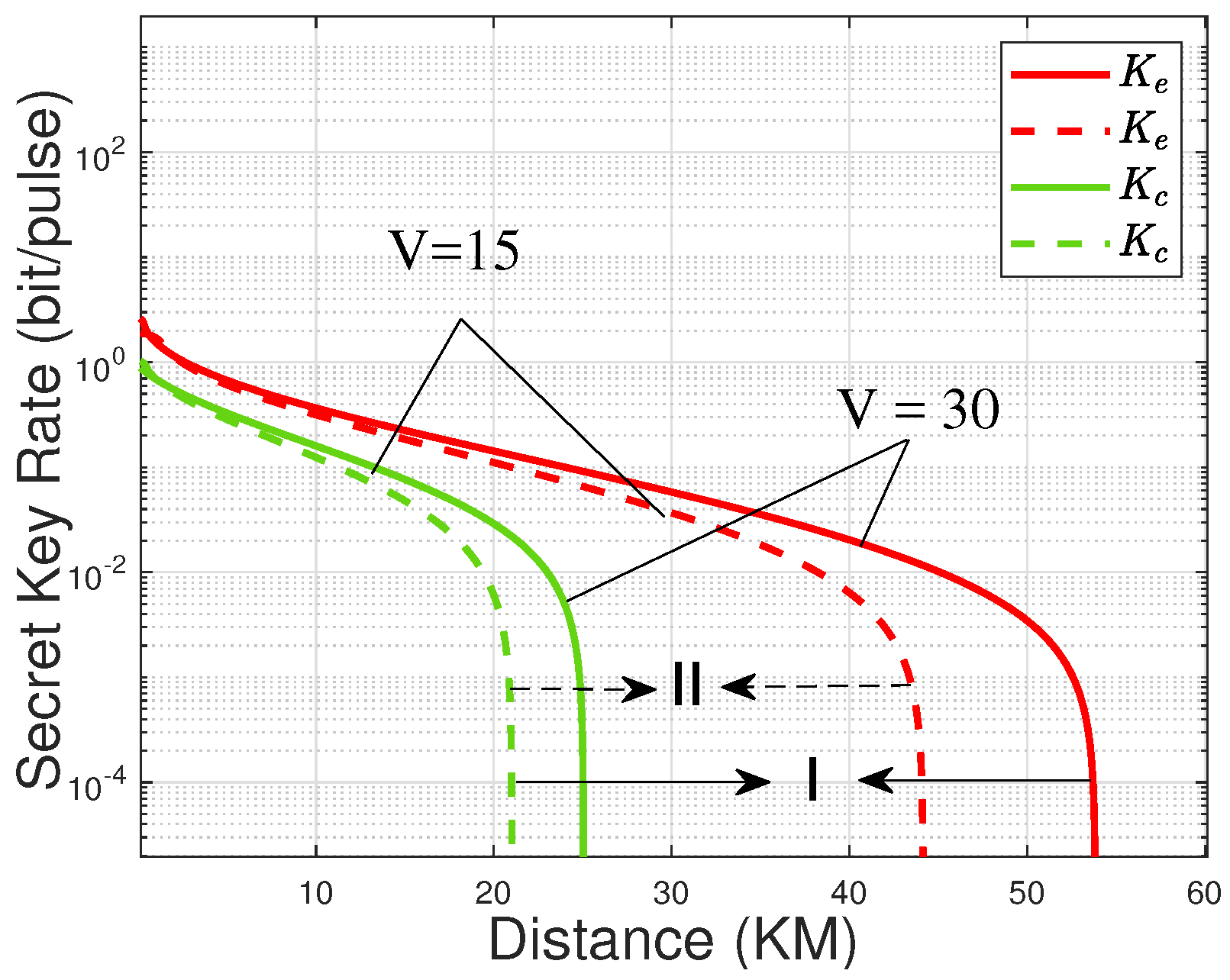
4.2.2. Numerical Simulations
5. Conclusions
Author Contributions
Funding
Data Availability Statement
Acknowledgments
Conflicts of Interest
Appendix A. Secret Key Rate
References
- Weedbrook, C.; Pirandola, S.; Garcia-Patron, R.; Cerf, N.J.; Ralph, T.C.; Shapiro, J.H.; Lloyd, S. Gaussian quantum information. Rev. Mod. Phys. 2012, 84, 621. [Google Scholar] [CrossRef]
- Notarnicola, M.N.; Olivares, S. Long-distance continuous-variable quantum key distribution with feasible physical noiseless linear amplifiers. Phys. Rev. A 2023, 108, 022404. [Google Scholar] [CrossRef]
- Zhang, J.; Wang, X.; Xia, F.; Yu, S.; Chen, Z. Multiple-quadrature-amplitude-modulation continuous-variable quantum key distribution realization with a downstream-access network. Phys. Rev. A 2024, 109, 052429. [Google Scholar] [CrossRef]
- Weedbrook, C. Continuous-variable quantum key distribution with entanglement in the middle. Phys. Rev. A 2013, 87, 022308. [Google Scholar] [CrossRef]
- Pirandola, S.; Laurenza, R.; Ottaviani, C.; Banchi, L. Fundamental limits of repeaterless quantum communications. Nat. Commun. 2017, 8, 15043. [Google Scholar] [CrossRef]
- Peng, Q.; Gao, B.; Wang, D.; Liao, Q.; Zuo, Z.; Zhong, H.; Huang, A.; Guo, Y. Defending against a laser-seeding attack on continuous-variable quantum key distribution using an improved optical power limiter. Phys. Rev. A 2023, 108, 052616. [Google Scholar] [CrossRef]
- Wang, N.; Du, S.; Liu, W.; Wang, X.; Li, Y.; Peng, K. Long-distance continuous-variable quantum key distribution with entangled states. Phys. Rev. Appl. 2018, 10, 064028. [Google Scholar] [CrossRef]
- Jouguet, P.; Kunz-Jacques, S.; Leverrier, A. Long-distance continuous-variable quantum key distribution with a Gaussian modulation. Phys. Rev. A 2011, 84, 062317. [Google Scholar] [CrossRef]
- Wang, T.; Huang, P.; Zhou, Y.; Liu, W.; Zeng, G. Pilot-multiplexed continuous-variable quantum key distribution with a real local oscillator. Phys. Rev. A 2018, 97, 012310. [Google Scholar] [CrossRef]
- Qi, B.; Lougovski, P.; Pooser, R.; Grice, W.; Bobrek, M. Generating the Local Oscillator Locally in Continuous-Variable Quantum Key Distribution Based on Coherent Detection. Phys. Rev. X 2015, 5, 041009. [Google Scholar] [CrossRef]
- Huang, D.; Huang, P.; Wang, T.; Li, H.S.; Zhou, Y.M.; Zeng, G.H. Continuous-variable quantum key distribution based on a plug-and-play dual-phase-modulated coherent-states protocol. Phys. Rev. A 2016, 94, 032305. [Google Scholar] [CrossRef]
- Pirandola, S.; Ottaviani, C.; Spedalieri, G.; Weedbrook, C.; Braunstein, S.L.; Lloyd, S.; Gehring, T.; Jacobsen, C.S.; Andersen, U.L. High-rate measurement-device-independent quantum cryptography. Nat. Photon 2015, 9, 397–402. [Google Scholar] [CrossRef]
- Xu, F.; Ma, X.; Zhang, Q.; Lo, H.-K.; Pan, J.-W. Secure quantum key distribution with realistic devices. Rev. Mod. Phys. 2020, 92, 025002. [Google Scholar] [CrossRef]
- Li, Z.Y.; Zhang, Y.C.; Xu, F.H.; Peng, X.; Guo, H. Continuous-variable measurement-device-independent quantum key distribution. Phys. Rev. A 2014, 89, 052301. [Google Scholar] [CrossRef]
- Lo, H.-K.; Curty, M.; Qi, B. Measurement-device-independent quantum key distribution. Phys. Rev. Lett. 2012, 108, 130503. [Google Scholar] [CrossRef]
- Braunstein, S.L.; Pirandola, S. Side-channel-free quantum key distribution. Phys. Rev. Lett. 2012, 108, 130502. [Google Scholar] [CrossRef]
- Patron, R.G.; Cerf, N.J. Unconditional optimality of Gaussian attacks against continuous-variable quantum key distribution. Phys. Rev. Lett. 2006, 97, 190503. [Google Scholar] [CrossRef]
- Qin, H.; Kumar, R.; Makarov, V. Homodyne-detector-blinding attack in continuous-variable quantum key distribution. Phys. Rev. 2018, 98, 012312. [Google Scholar] [CrossRef]
- Huang, D.; Lin, D.K.; Huang, P.; Zeng, G.H. Continuous-variable quantum key distribution with 1 Mbps secure key rate. Opt. Lett. 2015, 40, 3695. [Google Scholar] [CrossRef]
- Leverrier, A.; Grangier, P. Unconditional security proof of long-distance continuous-variable quantum key distribution with discrete modulation. Phys. Rev. Lett. 2009, 102, 180504. [Google Scholar] [CrossRef]
- Yang, J.; Xu, B.J.; Guo, H. Source monitoring for continuous-variable quantum key distribution. Phys. Rev. A 2012, 86, 042314. [Google Scholar] [CrossRef]
- Huang, P.; Fang, J.; Zeng, G.H. State-discrimination attack on discretely modulated continuous-variable quantum key distribution. Phys. Rev. A 2014, 89, 042330. [Google Scholar] [CrossRef]
- Inoue, K.; Honjo, T. Modified general individual attack against differential-phase-shift quantum key distribution. Phys. Rev. A 2024, 110, 042626. [Google Scholar] [CrossRef]
- Zheng, Y.; Wang, Y.; Fang, C.; Shi, H.; Pan, W. Practical security of continuous-variable quantum key distribution with an optical amplifier. Phys. Rev. A 2024, 109, 022424. [Google Scholar] [CrossRef]
- Huang, J.Z.; Weedbrook, C.; Yin, Z.Q.; Wang, S.; Li, H.W.; Chen, W.; Guo, G.C.; Han, Z.F. Quantum hacking of a continuous-variable quantum-key-distribution system using a wavelength attack. Phys. Rev. A 2013, 87, 062329. [Google Scholar] [CrossRef]
- Liao, Q.; Wang, Y.; Huang, D.; Guo, Y. Dual-phase-modulated plug-and-play measurement-device-independent continuous-variable quantum key distribution. Opt. Express 2018, 26, 19907–19920. [Google Scholar] [CrossRef]
- Ghalaii, M.; Pirandola, S. Continuous-variable measurement-device-independent quantum key distribution in free-space channels. Phys. Rev. A 2023, 108, 042621. [Google Scholar] [CrossRef]
- Ma, H.-X.; Huang, P.; Bai, D.-Y.; Wang, T.; Wang, S.-Y.; Bao, W.-S.; Zeng, G.-H. Long-distance continuous-variable measurement-deviceindependent quantum key distribution with discrete modulation. Phys. Rev. A 2019, 99, 022322. [Google Scholar] [CrossRef]
- Yang, H.; Liu, S.; Yang, S.; Lu, Z.; Li, Y.; Li, Y. High-efficiency rate-adaptive reconciliation in continuous-variable quantum key distribution. Phys. Rev. A 2024, 109, 012604. [Google Scholar] [CrossRef]

Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2024 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Guo, Y.; Zhang, H.; Guo, Y. Practical Security of Continuous Variable Measurement- Device-Independent Quantum Key Distribution with Local Local Oscillator. Mathematics 2024, 12, 3732. https://doi.org/10.3390/math12233732
Guo Y, Zhang H, Guo Y. Practical Security of Continuous Variable Measurement- Device-Independent Quantum Key Distribution with Local Local Oscillator. Mathematics. 2024; 12(23):3732. https://doi.org/10.3390/math12233732
Chicago/Turabian StyleGuo, Yewei, Hang Zhang, and Ying Guo. 2024. "Practical Security of Continuous Variable Measurement- Device-Independent Quantum Key Distribution with Local Local Oscillator" Mathematics 12, no. 23: 3732. https://doi.org/10.3390/math12233732
APA StyleGuo, Y., Zhang, H., & Guo, Y. (2024). Practical Security of Continuous Variable Measurement- Device-Independent Quantum Key Distribution with Local Local Oscillator. Mathematics, 12(23), 3732. https://doi.org/10.3390/math12233732







