Abstract
This article investigates the issue of security output feedback control for a nonlinear networked cascade control system with deception attacks. First, to further reduce the amount of communication data, reasonably schedule network resources, and alleviate the impact of multi-channel deception attacks, an attack-dependent adaptive event-triggered mechanism is introduced into the primary network channel, and its adaptive triggered threshold can be adjusted according to the random attack probability. Secondly, the output dynamic quantization of the secondary network channel is considered. Then, a novel security cascade output feedback controller design framework based on the Takagi–Sugeno (T-S) fuzzy networked cascade control system under deception attacks is established. In addition, by introducing the Lyapunov–Krasovskii stability theory, the design conditions of the controller are given. Finally, the effectiveness and superiority of the proposed design strategies are verified by two simulation examples of power plant boiler–turbine system and power plant boiler power generation control system.
Keywords:
nonlinear networked cascade control system; attacks-dependent adaptive event-triggered mechanism; dynamic quantization; deception attacks MSC:
93B70; 93C42
1. Introduction
Since the cascade control strategy was proposed [1], it has become an effective means to optimize the control system performance. Especially in the presence of external disturbances, the performance improvement effect is remarkable. The cascade control systems are composed of two subsystems in series, which are divided into the primary loop and the secondary loop. Since the secondary loop has a faster response speed than the primary loop, the secondary loop can effectively suppress the system disturbance, and the primary loop is responsible for adjusting the steady-state performance of the system [2]. It is precisely because the cascade control system has the advantages of reducing the disturbance of the secondary loop and improving the control quality, that the cascade control strategy is widely used in many industrial production process controls such as heat exchange systems [3] and cyber-physical systems [4].
In recent years, networked control systems (NCSs) have been widely used in intelligent transportation, intelligent manufacturing, and daily life due to their advantages of low cost, space saving, and easy maintenance [5,6,7]. Compared with the cascade control systems that do not transmit signal through the network, the networked cascade control systems (NCCSs) of signals transmission through the network combine the advantages of cascade control systems and NCSs. Based on this, many studies related to NCCSs have been published; for example, in [8], a passivity-based controller design method for NCCSs was proposed and verified by a boiler–turbine system. The issue of control for NCCSs with uncertain time-delay was considered in [9]. However, the open network environment may lead to many important data being eavesdropped or maliciously attacked, which will lead to unreliable or unavailable communication data, and even serious security incidents [10]. Therefore, the problem of security controller design for NCCSs in practical engineering applications has attracted the attention of many scholars, and some results have been published. For example, in [11], a novel design method of networked cascade controller based on event-triggered control was proposed under stochastic nonlinear constraints and actuator faults. Considering the denial-of-service (DoS) attacks and the possible saturation problem of the actuator, the event-triggered controller of the NCCS was investigated in [12]. By proposing a switching method, the stabilization problem of event-triggered NCCSs under DoS attacks was proposed in [13].
However, in the cascade security control strategy studied above, only the threat of DoS attacks to the system was concerned. Unlike the purpose of DoS attacks to block data transmission by occupying network bandwidth, deception attacks mainly achieve the purpose of attack by destroying the integrity and availability of transmitted data. At the same time, it is more covert and sensitive than DoS attacks. After the transmitted data are tampered with by the attacker, it is difficult for the data receiver to detect [14]. Furthermore, deception attacks can also be subdivided into: (1) false data injection attacks [15,16,17]; that is, the attacker knows the system state information, and (2) replay attacks [18]; that is, the attacker is unknown to the system state information. In addition, it is worth noting that stealth attacks can also be regarded as a kind of covert false data injection attacks with better concealment [19].
In this article, we focus on the study of random deception attacks in which the attacker knows the system state information in advance, such as [20], considering the influence of primary loop random deception attacks and actuator saturation, and the control problem of NCCSs based on hybrid drive mechanism was studied. However, most of the existing literature only focuses on the threat of deception attacks on a single channel, and the research on deception attacks on any multi-channel is not sufficient [21,22], especially the security control problem of NCCSs under the threat of multi-channel deception attacks. Malicious adversaries that launch deception attacks on any multi-channel will seriously damage the integrity of the data transmitted by the main loop and the secondary loop of the NCCSs, thus affecting the adjustment of the entire NCCSs and affecting the performance and stability of the NCCSs. Therefore, the security cascade control strategy under the threat of arbitrary multi-channel deception attacks deserves further study.
In addition, we review the existing cascade control strategies based on event-triggered mechanism (ETM) under the influence of network attacks [8,13,14,20]. The design of event-triggered conditions or triggered thresholds only considers system-related information and ignores the impact of network attack sequences on event-triggered results. How to design the attacks-dependent adaptive ETM (ADAETM), obtain more stringent triggered conditions, and enhance the non-vulnerability of the triggered mechanism is a proposition worth exploring. On the other hand, the secondary network channel of the NCCSs also needs attention due to the transmission delay, packet disorder, and other threats caused by bandwidth constraints. Therefore, it is necessary to dynamically quantify the transmission signal of the secondary network channel. In recent years, many results on the controller and filter design of NCCSs under the joint framework of event-triggered and quantizer strategies have been published [23,24,25,26,27]. This inspires us to further explore the joint design method of ADAETM and dynamic quantization for NCCSs.
As an effective modeling method for nonlinear systems, the T-S fuzzy model is based on the principle of fuzzy logic. By setting appropriate membership functions (MFs), a series of local subsystems were smoothly connected to approximate the nonlinear systems [28]. Due to the advantages of the T-S fuzzy model, the related research results based on T-S fuzzy systems are remarkable, especially the control synthesis and filter design of nonlinear NCCSs in recent years [27,29,30,31,32,33]. For instance, the security fuzzy controller design problem of nonlinear NCCSs based on event-triggered and quantization strategy was studied in the network attacks environment [27]. The reachable set control problem for the T-S fuzzy singular Markov jump system was studied in [31]. Considering the DC microgrid system based on T-S fuzzy model, the security fuzzy control strategy under the influence of time-constrained DoS attacks was given in [32]. Moreover, considering the unmeasurable or unavailable state variables in NCCs, the output feedback control strategy is more reasonable than the state feedback control strategy and closer to the practical application background. The excellent results of NCSs output feedback have been reported in [34,35,36,37]. For example, in [34], the quantized output feedback security tracking controller design problem was studied, and a novel design framework was given. Considering the problem of time delay and packet loss, ref. [36] designed a output feedback controller under finite-time stability for NCCS. However, it is found that the output feedback control problem of nonlinear NCCS based on the T-S fuzzy model has not been solved in the existing literature, which inspires this work.
On the basis of the above existing research works, we will consider the design of fuzzy security cascade output feedback controller (SCOFC) based on ADAETM for the nonlinear NCCSs under the multi-channel deception attacks and secondary-loop signal dynamic quantization. The contributions of the proposed design strategy are as follows:
- 1.
- Different from the results of single-channel deception attacks in [20,27], this article focuses on the multi-channel deception attacks from the primary sensor to the primary controller communication link and from the secondary controller to the actuator communication link.
- 2.
- A novel ADAETM is proposed. Its adaptive law can flexibly adjust the adaptive triggered threshold by random deception attacks probability, which further alleviates the impact of deception attacks on the NCCS.
- 3.
- Compared with [8,9,11,12,13,20,26,27], the signal dynamic quantization of the secondary loop channel is considered for the first time. The data transmission amount of the secondary network channel is reduced, and the network channel burden is further reduced.
- 4.
- A novel SCOFC design strategy is proposed under the framework of ADAETM, dynamic quantization, and deception attacks. Based on this framework, the theoretical results of the developed security fuzzy controller are expressed by linear matrix inequalities (LMIs), and the mean square asymptotically stable with performance is ensured for the resulting system.
The structure of the follow-up research content of this article is as follows. The problem formulation of SCOFC is given in Section 2. In Section 3, the novel SCOFC design strategy and design results are given by LMIs. In Section 4, two simulation examples of power plant boiler–turbine system (PPBTS) and power plant boiler power generation control system (PPBPGCS) are shown the effectiveness of the proposed design strategy. The main conclusion of the article is concluded in Section 5.
Notations: Let and represent the n-dimensional Euclidean space and the real matrices sets, respectively. The matrices and denote the matrix transposition and inverse, respectively. stands for the block-diagonal matrix and , represent the n columns identity matrices and zero matrices with appropriate dimensions, respectively. Let denotes , and stands for the square-integrable function space. The symbol means that .
2. Problem Formulation
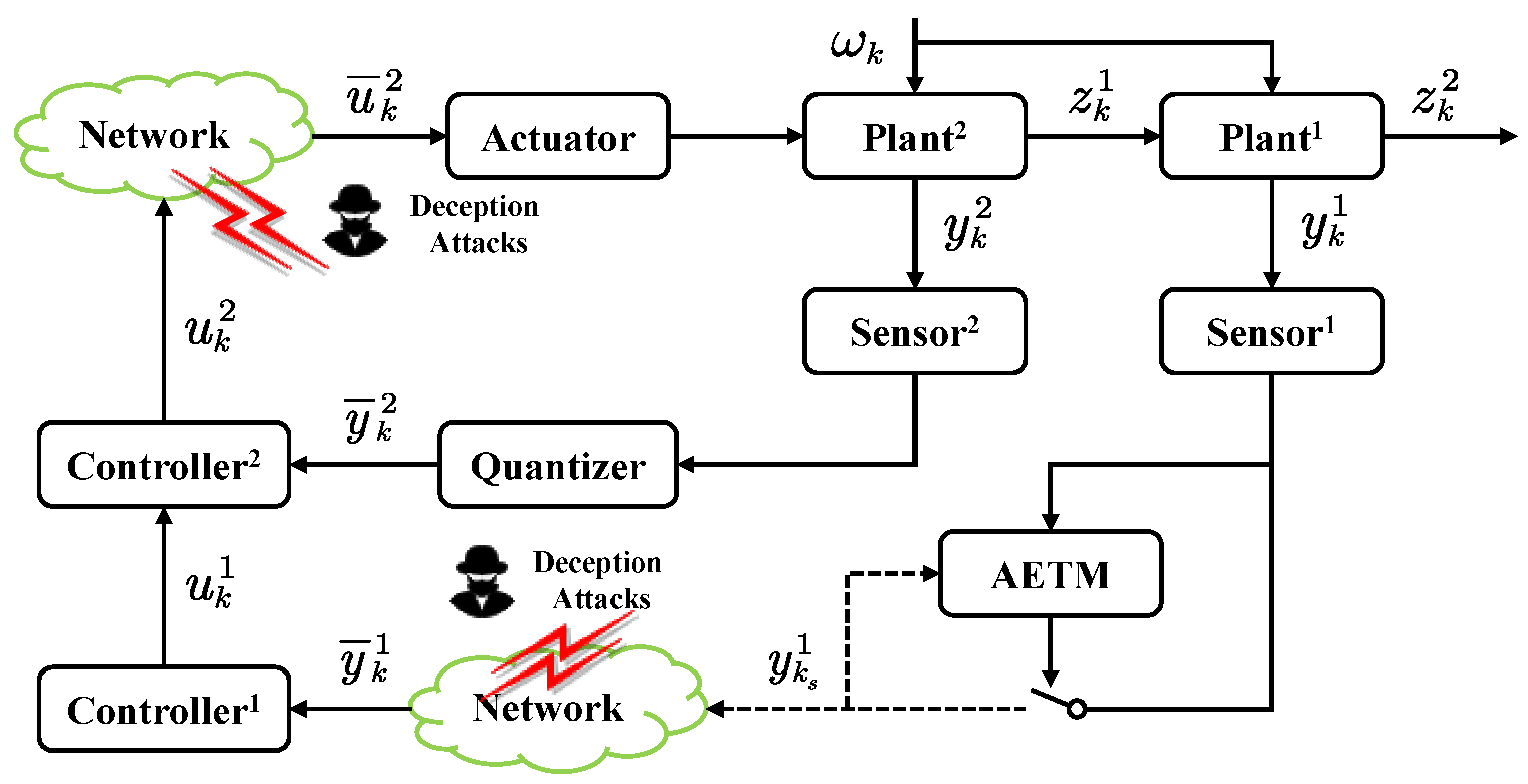
This article is concerned with security control for nonlinear NCCSs. As shown in Figure 1, the nonlinear NCCS is described by the T-S fuzzy model, which is mainly composed of primary and secondary systems in series. The primary loop consists of primary plant–, primary sensor–, primary controller–, and actuator. The secondary loop consists of secondary plant–, secondary sensor–, secondary controller–, and actuator.
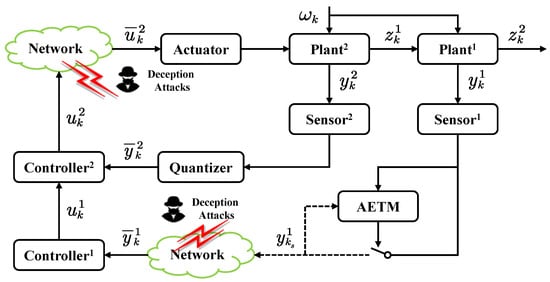
Figure 1.
Framework of an NCCS under deception attacks.
Combining the advantages of NCCSs and traditional cascade control systems, the definition of NCCSs is mainly reflected in the sensor–controller, and the data between the controller and actuator are transmitted through the wireless network. Considering the characteristics of the NCCS, a dynamic quantizer is introduced in the secondary loop, and an ADAETM is introduced in the primary loop. At the same time, the risk of deception attacks from primary sensor– to primary controller– and from secondary sensor– to actuator is considered.
2.1. System Description
In the nonlinear NCCS, the discrete-time T-S fuzzy primary system– is described as follows:
: is , and is ,
where denotes the fuzzy sets, is premise variable and ; , , and denote the state vector, measured output, regulated output of , and the measurement output of , respectively; belongs to and represents the exogenous disturbances. , , , , and are the known system matrices of the appropriate dimensions.
By using a standard fuzzy inference approach, the fuzzy primary system (1) is inferred as follows:
where are the normalized MFs satisfying that , with which denotes the MFs of the primary system with premise variable .
In addition, the introduction of event-triggered strategy in the network channel will lead to the problem of asynchronous signal transmission. And the asynchrony and mismatch of premise variables of the fuzzy primary controller– are considered.
: is , and is ,
where are the gains, is the final input of the after event-triggered and deception attacks, and denote control input of . denotes the fuzzy sets, is premise variable, and .
By using single-point fuzzification, product reasoning, and the central weighted average defuzzification method, the output form of the fuzzy is as follows:
where are the normalized MFs satisfying that , with which denotes the MFs of the with premise variable .
Based on the reconstruction strategy in [22], the asynchronous problem of MFs caused by event-triggered strategy was effectively solved. Suppose the minimum values of and , the relationship between and is interpreted as
where , are some positive constants, is a parameter related with , and .
Based on the conditions mentioned above, one obtains
where and denote the known lower bound and upper bound of , which yields that
Setting and for i, , one has
In the nonlinear NCCS, the discrete-time T-S fuzzy secondary system– is described as follows:
: is , and is ,
where denotes the fuzzy sets, are fuzzy premise variables and ; and denote the state vector and the final control input of , respectively; The remaining parameters are defined with reference to . , , , , , and are the known system matrices of the appropriate dimensions.
Then, based on fuzzy inference approach, the secondary system– (7) is inferred as follows:
where are the normalized MFs satisfying that , with denotes the MFs of the system with premise variable .
The model of secondary controller– considering quantization in network channel is given as follows:
where is the gain and is the quantized system measurement output.
2.2. Dynamic Quantizer
In this article, consider the following form of dynamic quantizer:
where is the dynamic parameter and suppose that the dynamic quantizer (10) satisfies the following constraints:
where and represent the quantization range and quantization error bound of dynamic quantizer, respectively.
Then, the quantized measurement output signal of is in the following form:
where is a dynamic quantizer defined by (10), and . The measurement output signal quantization process and parameter update of dynamic quantizer are shown in Algorithm 1.
Remark 1.
Due to the introduction of network in cascade control systems, it is necessary to consider the network phenomenon of each loop. Different from the existing literature [8,9,11,12,13,20,26,27], this article considers the signal quantization problem of the secondary loop for the first time. In addition, in order to balance the number of packets and quantization error in the network signal, based on the method proposed in [34], the quantization error term can be well processed.
| Algorithm 1 Calculation of and in dynamic quantizer |
| Input:
, M, and ℏ Output: , and
|
2.3. Multi-Channel Deception Attacks
The deception attacks in the NCCSs mainly inject the wrong data into the communication channel intermittently, and replace the real data at the same time, which affect the stability and performance of the systems. Therefore, the security problem of NCCSs interfered by multi-channel deception attacks cannot be ignored.
Considering the characteristics of the deception attacks signals and , which assumes that the following constraints are satisfied:
where and are constant matrices denoting the upper bound of the error data function with nonlinear characteristics. Bernoulli variables and are used to describe the probabilistic characteristics of deception attacks, satisfying
Then, the signals and transmitted to the communication network after being deception attacks are expressed as follows:
Remark 2.
Different from [20,27], this article also considers the impact of deception attacks between the primary loop to network channel and to actuator network channel. Compared with [20,27], the controller design method proposed in this article under multi-channel deception attacks is closer to the actual situation and more meaningful.
Remark 3.
It is worth noting that the success of network attacks is random, which is determined by the built-in hardware and software protection in the device, the data transmitted based on the network protocol, and the network conditions with random fluctuation characteristics; that is, network congestion, network load, and so on [17,20]. Therefore, this article discusses random multi-channel deception attacks, and assumes that the deception attacks occur in the primary loop to network channel and to actuator network channel. At the same time, the way deception attacks destroy data integrity is to completely replace real data with false data attack signals [15] (refer to (14)).
Remark 4.
It should be further pointed out that the attack signal of the network attacks is generated by the attacker’s strategy formulation of the attack object, so the network attacks may be difficult to detect or undetectable, and the attack signal may be associated with the systems state data, output data, control data, and other information [14]. Referring to the description of the attack signal in [20], the two deception attack signals considered in this article are modeled as nonlinear functions related to the output data of and the control signal of , respectively, and satisfy the constraints in (13).
2.4. Attacks-Dependent Adaptive Event-Triggered Mechanism
In order to alleviate the impact of deception attacks on the triggered effect and system performance, the following form of ADAETM is given:
where , is the current sampled measurement output and is the latest measurement output signal that satisfies the triggered condition, is the event-triggered weighting matrix to be designed, and is an adaptive parameter and satisfies the following adaptive law:
where is the inverse-tangent function. , , , and are the event-triggered threshold adjustment positive parameters. , , and are known constant thresholds. Then, the ADAETM operating mechanism is shown in Algorithm 2.
Remark 5.
Considering the influence of deception attacks, attack probability is introduced to design the random adaptive law . It is obvious that the expression is always greater than 0. When the attack intensity increases, that is, the attack probability becomes larger, then the term makes the adaptive law smaller, the triggered condition is easier to meet, so that more sampling data are transmitted to compensate for the impact of the deception attacks. On the other hand, when the communication channel data are transmitted normally, the will degrade into ; thus, will relatively increase. Such changes can make the triggered condition more stringent, help to further reduce the triggered data, and improve resource utilization. The detailed operation process can be understood by Algorithm 2.
Consider the network induced delay satisfying , where is a positive integer. Based on the analysis process in [29], define the following:
Then, the introduced time-varying delay variable and output data error are expressed as
where , , , .
Then, the range of is as follows:
where is a constant, which is the upper bound of event-triggered data transmission delay. Then, the signal transmitted to the can be obtained as
| Algorithm 2 Calculation of and (k, ) in ADAETM |
| Input:
, , , , , , , , and . Initial set , , , . Output: and (k, ).
|
2.5. System Formulation
By combining (2), (4), (8), (9), (12), (14), (20), and defining , , , it can yield a new model for NCCSs as follows:
The nonlinear NCCS is considered in this article, and under the influence of multi-channel deception attacks, the ADAETM and dynamic quantizer are introduced, so that the designed SCOFC satisfies the following objectives:
- 1.
- The system (21) is mean square asymptotically stable in the absence of external disturbances, i.e., ;
- 2.
- Under zero initial conditions, for all , there exists a positive scalar , such that the following condition holds: .
3. Main Results
In this section, the design conditions that guarantee the mean square asymptotically stable and performance of the system (21) are given. Then, the design results of the security fuzzy controller gains under event-triggered and dynamic quantization strategy are given.
Theorem 1.
For given scalars , , , , , , , , , and , the system (21) is mean square asymptotically stable and satisfies the predetermined performance index γ if there exist positive definite symmetric matrices , , , , , , , Ω, and slack matrix with appropriate dimensions, such that the following inequalities hold for :
where
Proof.
Consider the discrete-time piecewise Lyapunov–Krasovskii functional in the following form:
where
Then, defining , the piecewise Lyapunov–Krasovskii functional difference equation under the mathematical expectation can be obtained as
Considering , one has
where .
Without loss of generality, the dynamic parameters for the dynamic quantizer considered in this article are defined as with . Then, as in [35], according to the definition of the dynamic quantizer given in (11) and the homogeneity property of Euclidean norm, it can be obtained that
Considering the constraint of nonlinear deception attack signals and , we obtain
Based on the event-triggered condition (15), one has
Then, it is obtained from conditions (23) and (24) that
Due to , we have
Then, the following result can be obtained:
The sum of the two sides of the inequality (33) from to can have
Considering the fact that and , the following conclusions can be obtained:
which implies the system is mean square asymptotically stable without disturbance and satisfies the performance index . The proof is completed. □
Remark 6.
Through the proof of Theorem 1, the sufficient conditions that the system satisfies performance and mean square asymptotic stability are obtained. Specifically, this article considers the impact of event-triggered, dynamic quantization, and deception attacks on the system. To reduce the conservatism of the design results, the artificial time delay caused by event-triggered control is introduced, and the performance and stability of the system are analyzed by constructing the Lyapunov–Krasovskii functional. In the mean square sense, the inequality (22) and integral inequality (28) are used to reduce the inevitable time-delay summation term, and the inequality constraints (29)–(31) is introduced in a targeted manner. The preliminary inequality result is obtained in (32). Furthermore, the related design conditions of MFs are considered. Due to the introduction of ETM, the asynchronous phenomenon of MFs are inevitable. Through the method in [12] and Schur complement lemma, the final sufficient design conditions (23) and (24) are obtained.
Remark 7.
It should be noted that, if the assumptions of cascade controller gain, dynamic quantizer parameters, and event-triggered weight matrix are removed, there will be some nonlinear terms and coupling terms in inequality conditions (23) and (24). This makes the inequality difficult to solve. In Theorem 2, this difficulty can be solved by some variable substitutions, basic inequalities, and matrix decoupling techniques.
Theorem 2.
For given , , , , , , , , , and , the system (21) is mean square asymptotically stable and satisfies the performance index γ if there exist positive definite symmetric matrices , , , , , , , Ω, and slack matrix with appropriate dimensions, such that (22) and the following inequalities hold for :
where
in which is obtained from by substituting , , , , , , and with , , , , , , and , and
In addition, the gains of and are given as follows:
Proof.
Perform congruence transformation to (23) by with , the inequality (23)–(25) can be rewritten as
where .
Defining . Then, the condition (39), (40) can be reexpressed as
the definitions of , , , , , , and are shown in Theorem 2, and
Remark 8.
Through the proof of Theorem 2, the sufficient conditions for solving the cascade controller gain, quantizer parameter, and ADAETM weighting matrix are obtained. In the proof process, the nonlinear terms and coupling terms that affect the inequality solution are eliminated by congruence transformation, basic inequality transformation, and matrix decoupling technology, such as , , , and so on. Then, the solution of LMIs is a convex optimization problem. Many existing optimization methods and numerical tools, such as the YALMIP toolbox in MATLAB, can be used to solve convex optimization problems. Based on Theorem 2 and the existing solving tools, the design results can be more easily obtained by off-line execution. The detailed solution process is given by Algorithm 3.
Remark 9.
The computational complexity of the LMIs in Theorem 2 is determined by the number of decision variables and the dimension of the LMIs. Based on Theorem 2, we have and .
| Algorithm 3 Solve the control gains, quantizer parameter, and ADAETM weighting matrix |
| Input:
parameter matrices , , , , , , , , , , , and parameter scalars , , , , , , M, , , , , and . Output: , , ℏ, and .
|
4. Simulation Results
4.1. Design Example with PPBTS
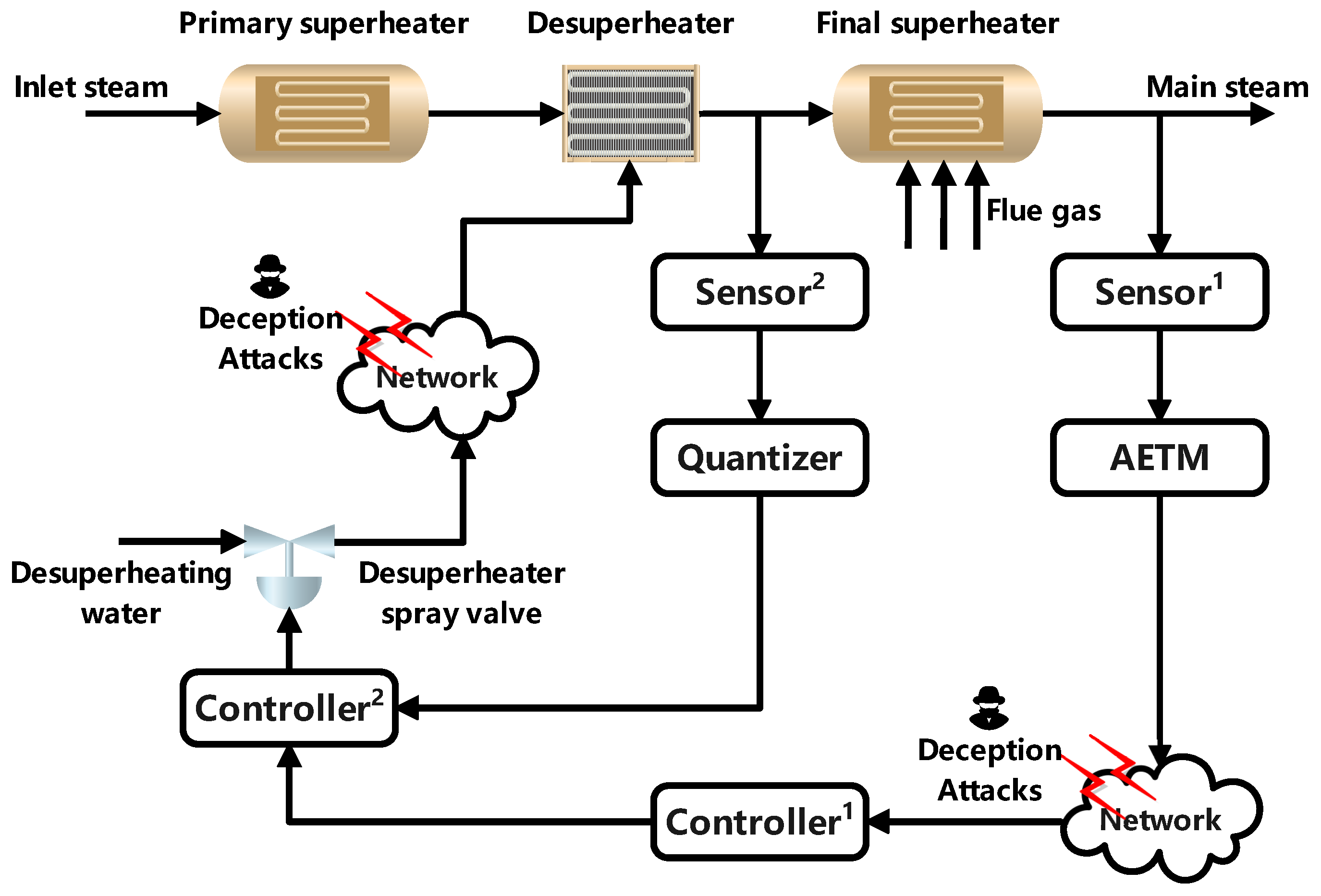
By constructing the NCCS shown in Figure 2, the problem of excessive temperature deviation during the operation of the power PPBTS will be solved. measures the steam temperature value of the secondary superheater. After the ADAETM and the influence of the deception attacks, the measurement data are fed back to . compares the measured data with the expected data, and then the output signal of is transmitted to as the expected data. compares the expected data with the quantized steam temperature measurement data at the Desuperheater end, and transmits the control output signal to the Desuperheater spray valve. The Desuperheater spray valve will be attacked during the adjustment of the Desuperheater. Through the proposed controller design strategy, we can ensure the stability and controllability of the steam temperature in the PPBTS under the network environment where the whole system is threatened by deception attacks.
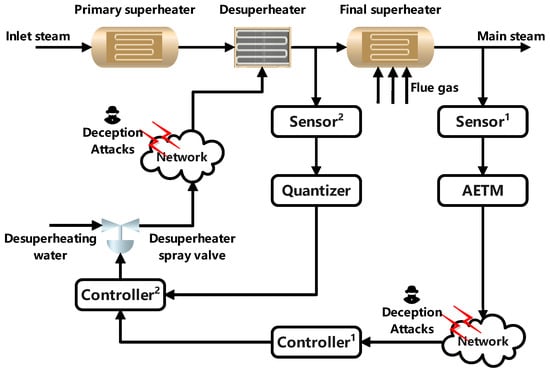
Figure 2.
Structure diagram of an NCCS for a nonlinear PPBTS.
The discrete nonlinear networked PPBTS [9] parameters considered in the article are given as follows:
Moreover, the MFs are chosen by , , , and . The initial states of the and are given as and the external disturbance is given as follows: , ; otherwise, .
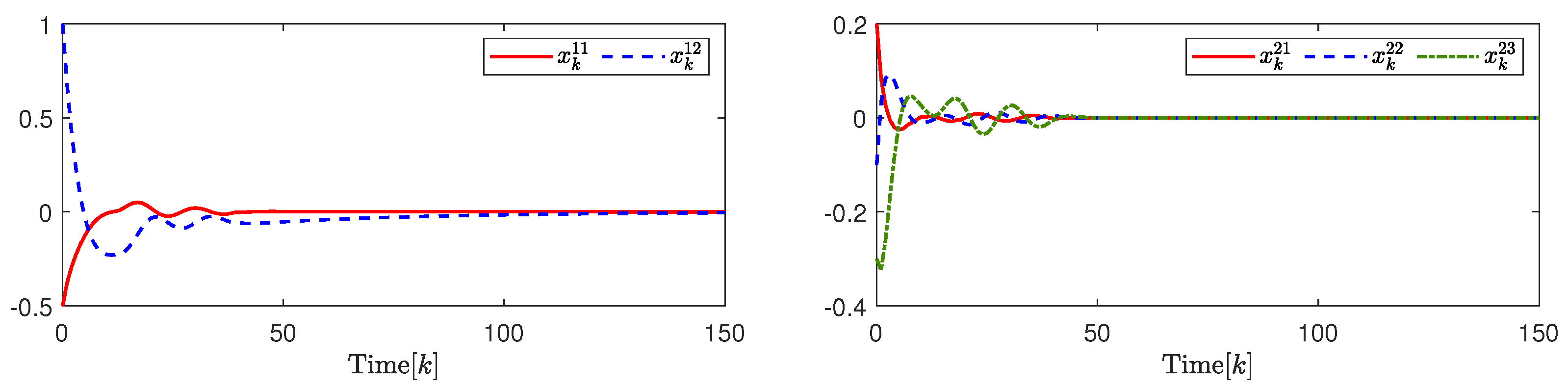
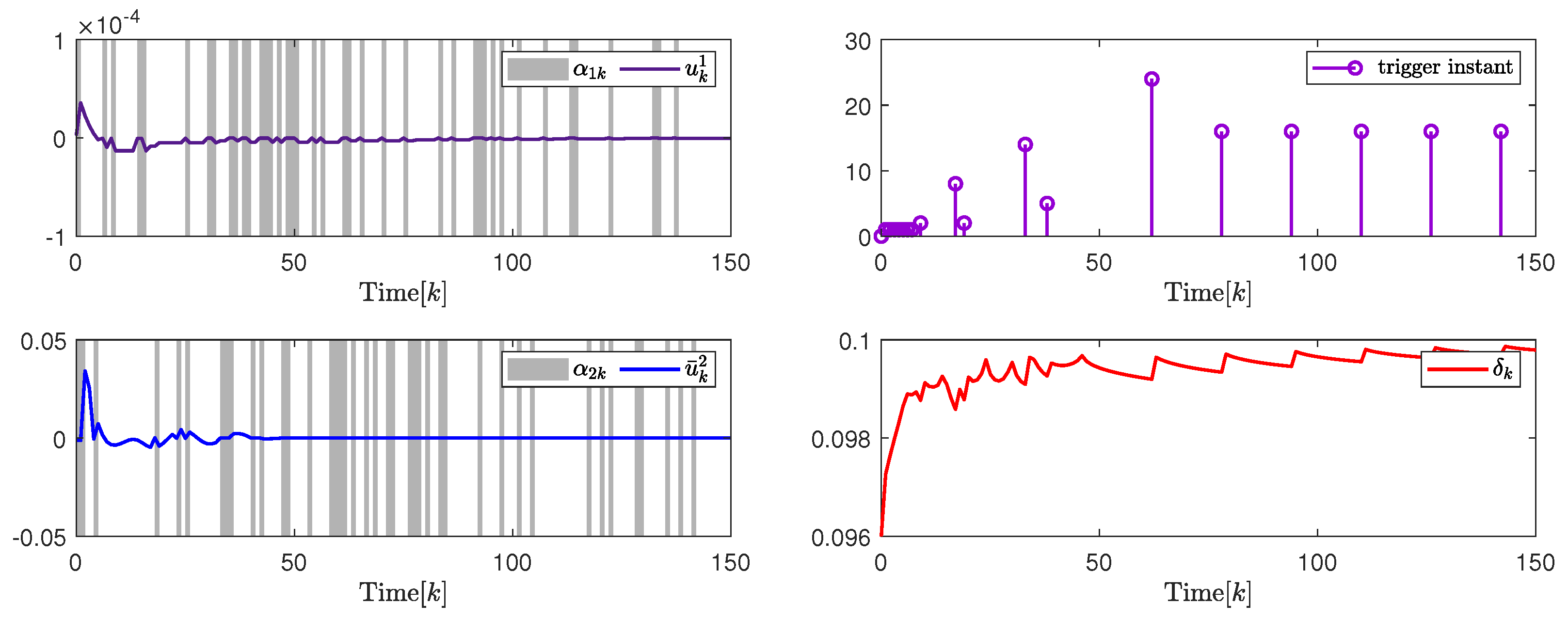
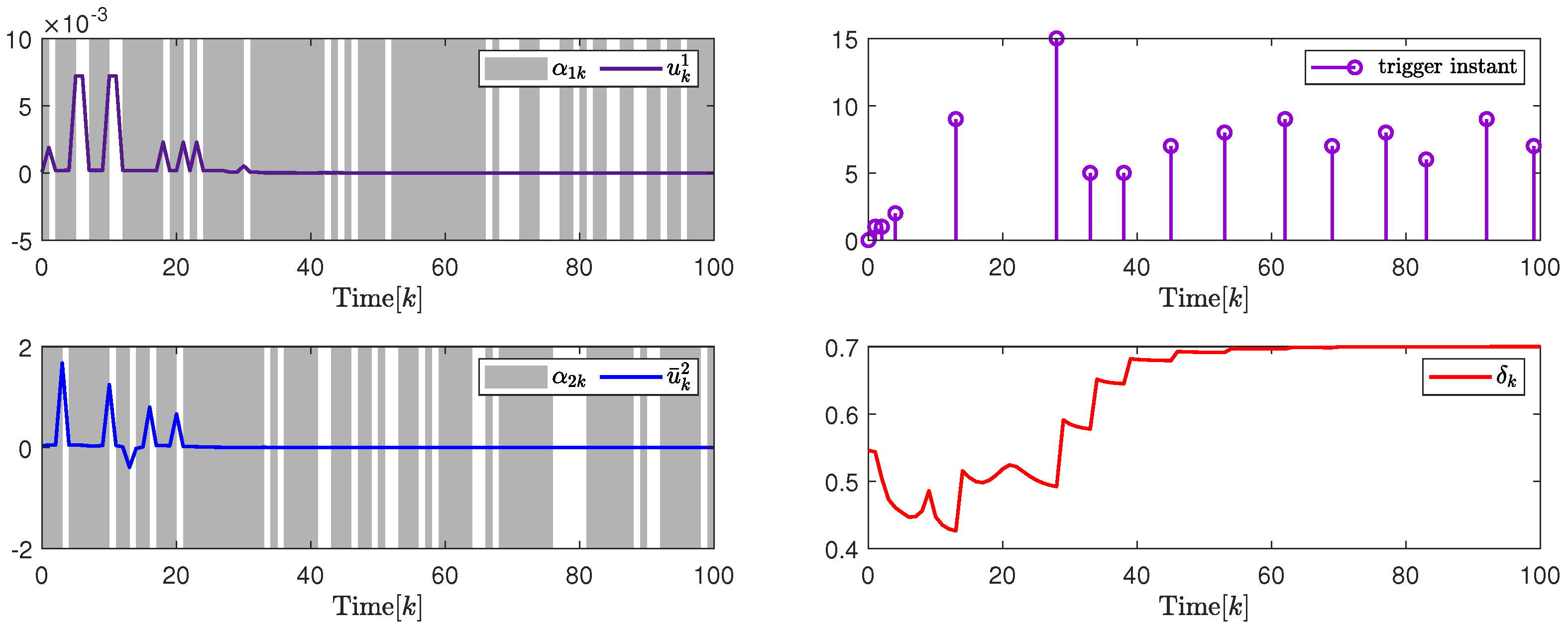
Selecting , , , , , , , , , , , , , and . By the design results in Theorem 2, the quantization parameter, security fuzzy controller gains, and the ADAETM weighting matrix are obtained as , , , , and . The state responses of and are shown in Figure 3. The change trajectory of control signals and are demonstrated on the left in Figure 4. The release instants, the release intervals, and the adaptive law are shown on the right in Figure 4.
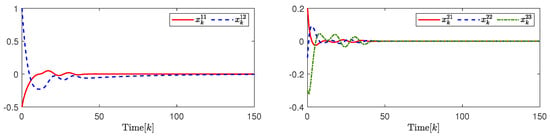
Figure 3.
(Left). The response of system state ; (Right). The response of system state .
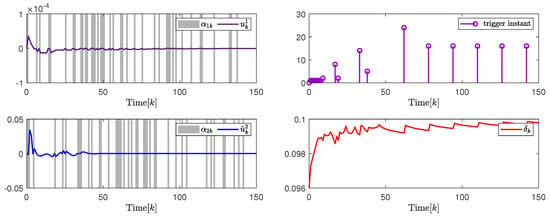
Figure 4.
(Left). The control input and with ; (Right). The release instants and the release intervals and the adaptive law with .
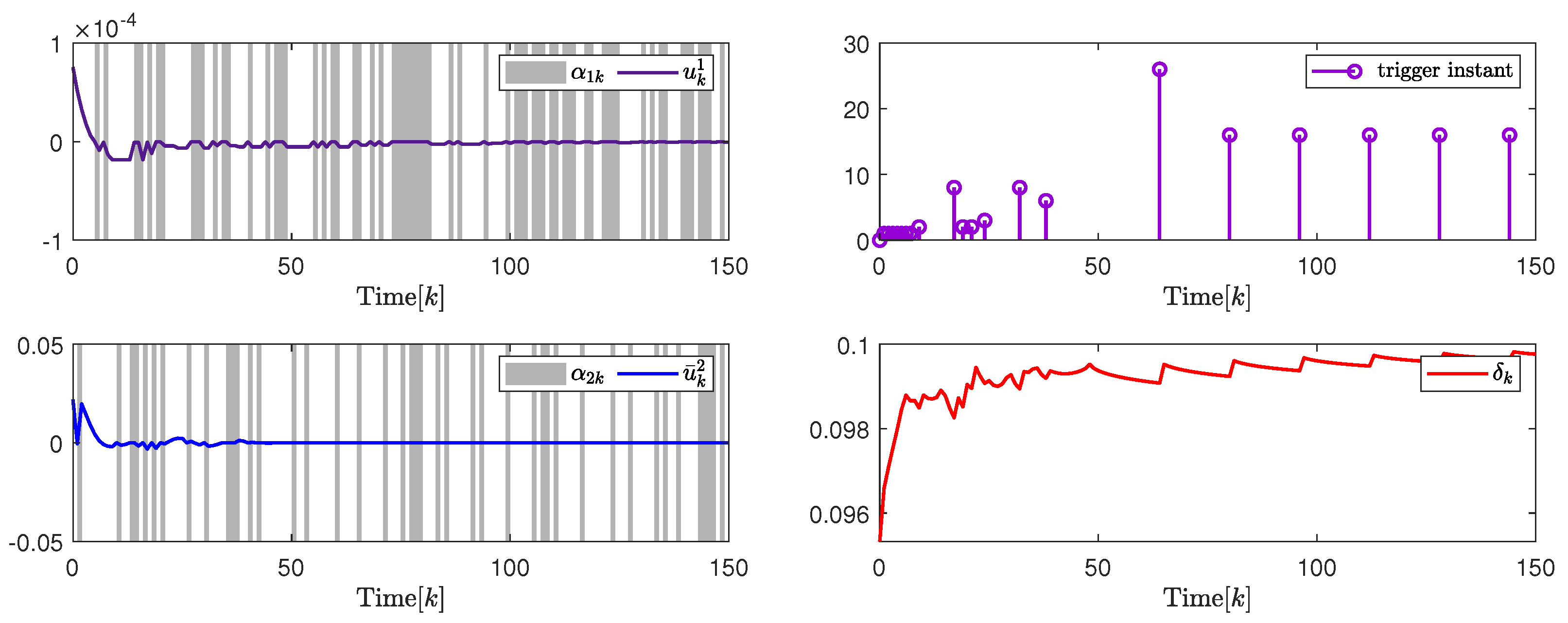
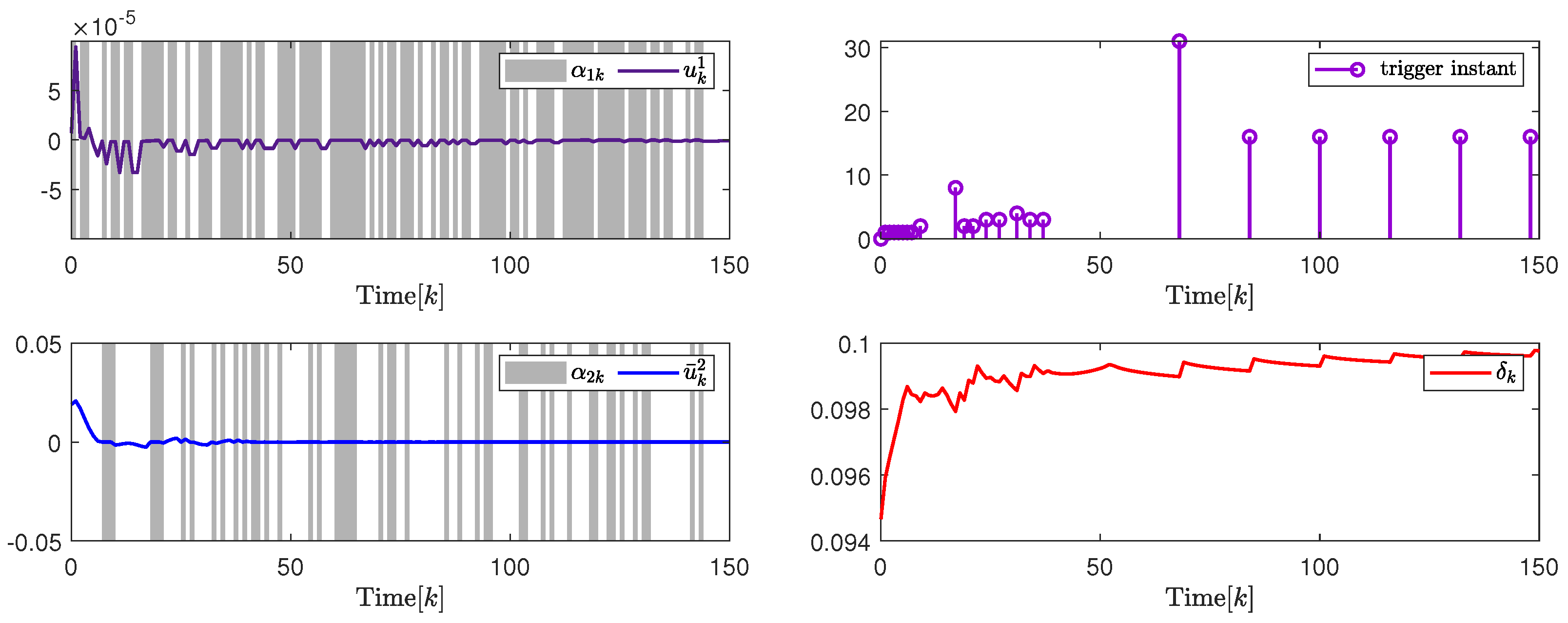
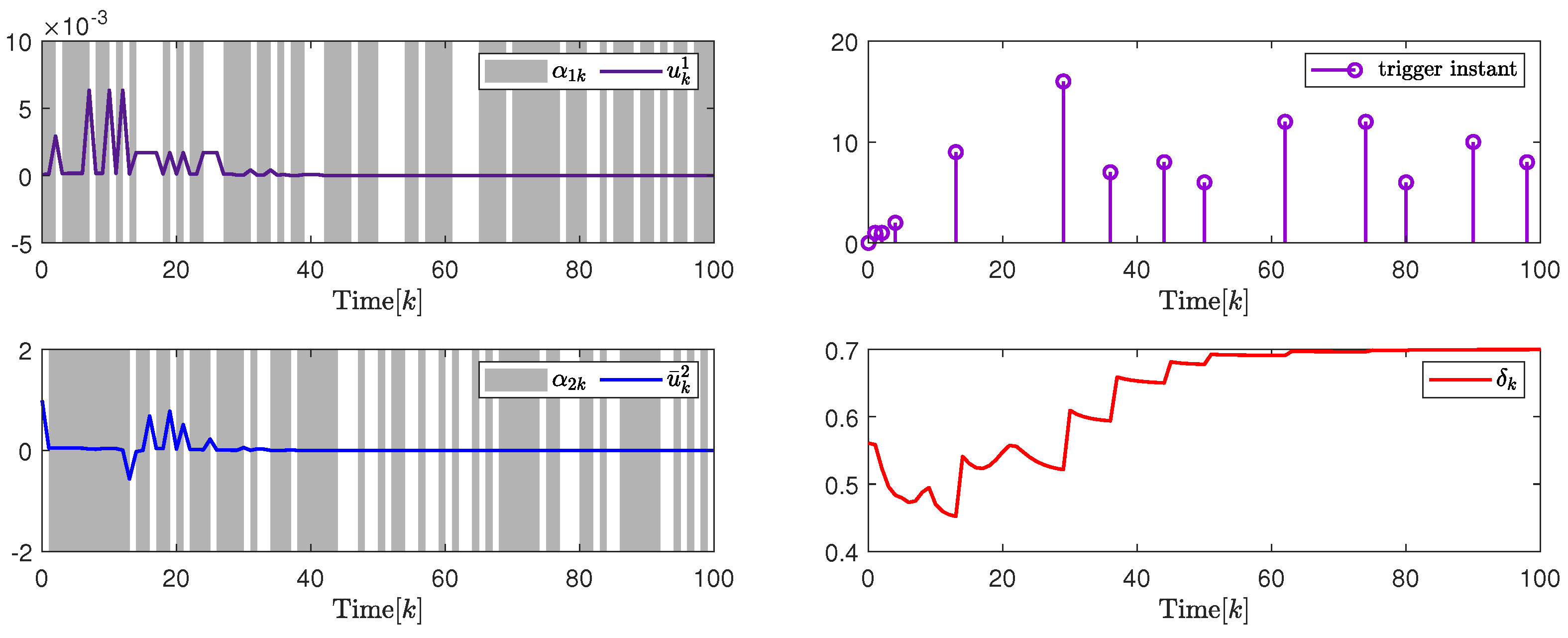
In addition, to further illustrate the impact of the attack probability on packet transmission rate adjustment and system performance, Figure 5 and Figure 6, and Table 1 give the analysis results under different attack probability . By the design results in Theorem 2, the quantization parameter, security fuzzy controller gains, and the ADAETM weighting matrix are obtained as follows: , , , , with . , , , , with .
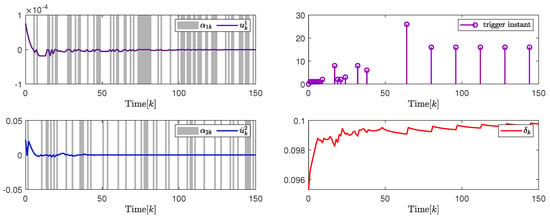
Figure 5.
(Left). The control input and with ; (Right). The release instants and the release intervals and the adaptive law with .
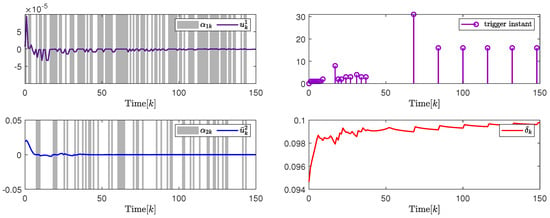
Figure 6.
(Left). The control input and with ; (Right). The release instants and the release intervals and the adaptive law with .

Table 1.
Data transmission with different ETMs in Example with PPBTS.
Based on the above calculation results under different attack probability , Figure 5 on the left and Figure 6 on the left show that the trajectory changes of the control input converge to 0 under and , respectively, and the release instants, and the release intervals, the adaptive law are shown on the right in Figure 5 and Figure 6, respectively, which indicates the effectiveness of the designed security cascade controller for multi-channel deception attacks. Moreover, to further verify the superiority of the proposed ADAETM, it is compared with the triggered mechanism in [27], and the system performance under different attack probability is calculated. Through the transmission number (TN) and transmission rate in Figure 5 on the right and Figure 6 on the right, and Table 1, it can be seen that the ADAETM designed in this article has great advantages. With the increase in attack probability, the number of triggers will also increase, and the system performance index will decrease, which explains the rationality of the design of ADAETM to a certain extent. In addition, to further strengthen the demonstration of the superiority of the proposed control design, quantitative performance index analysis under different attack probabilities, such as system convergence time, network channel bandwidth utilization, and optimal performance index, is presented in Table 2. It can be seen that the increase in attack probability will affect the convergence time of the system and the number of triggered packets to a certain extent, but the design strategy proposed in this article can balance the relationship between attack probability and the number of triggered packets, and maintain the optimal performance index.

Table 2.
Quantitative performance index with different attack probabilities in Example with PPBTS.
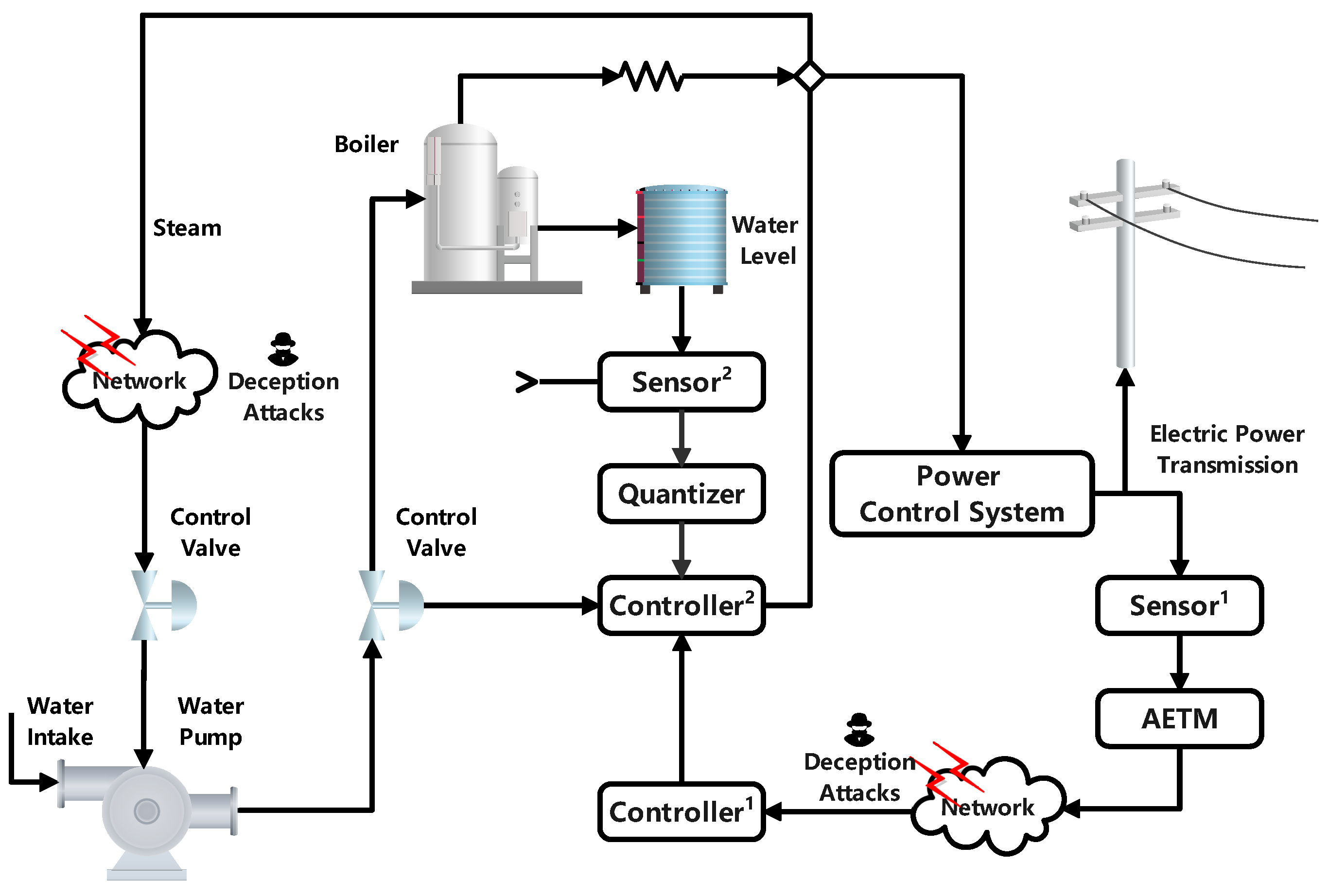
4.2. Comparison Example with PPBPGCS
In order to further verify the superiority of the derived results of Theorem 2, a nonlinear PPBPGCS based on fuzzy model is given. The structure of the NCCS is shown in Figure 7. In the main control loop, is used to measure the output power supply voltage of the power control system. After the influence of ADAETM and deception attacks, the measurement data are fed back to and compared with the expected data. The output signal of is transmitted to as the expected data. In the secondary control loop, compares the boiler liquid level data, valve parameters measured by the quantized with the expected data, and transmits the control output signal to the valve that controls the inlet to control the main steam temperature.
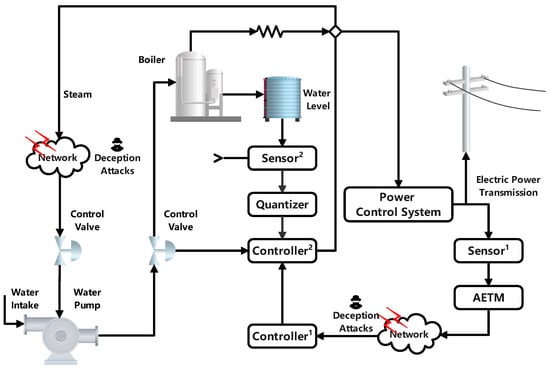
Figure 7.
Structure diagram of an NCCS for a nonlinear PPBPGCS.
Suppose that the discrete nonlinear networked PPBPGCS parameters considered in this article are as follows:
Moreover, the MFs are chosen by , , , and . The initial states of the and are given as and the external disturbance is given as follows: , ; Otherwise, .
Selecting , , , , , , , , , , , , , and . By the design results in Theorem 2, the quantization parameter, security fuzzy controller gains, and the ADAETM weighting matrix are obtained as , , , , and .
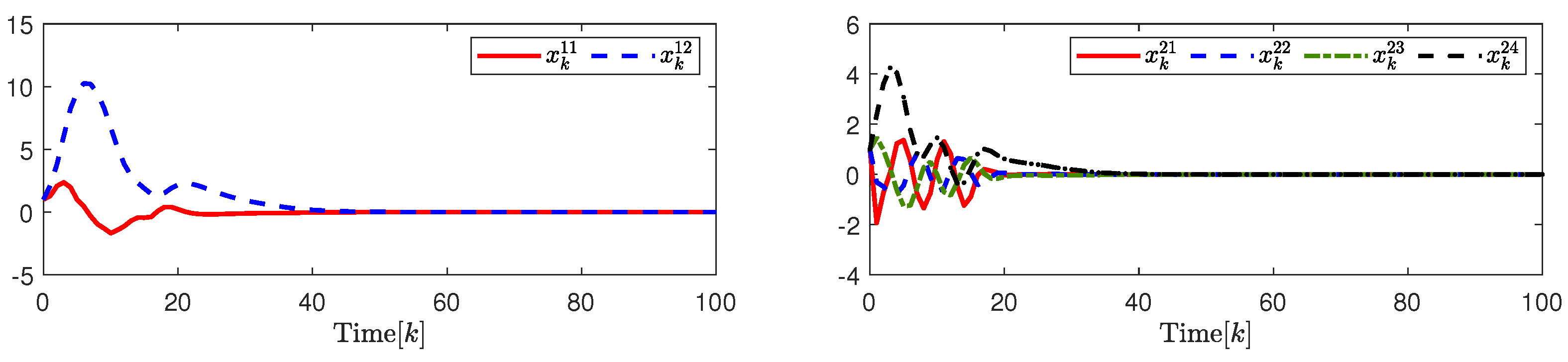
The state responses of and are shown in Figure 8. The change trajectory in the control signals and are demonstrated on the left in Figure 9. The release instants, the release intervals, and the adaptive law are shown on the right in Figure 9.
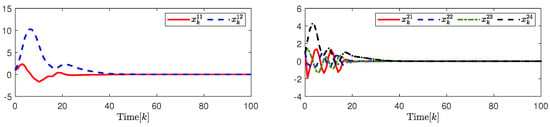
Figure 8.
(Left). The response of system state ; (Right). The response of system state .
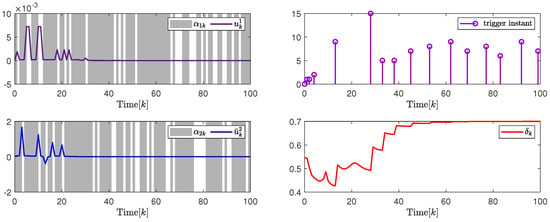
Figure 9.
(Left). The control input and with ; (Right). The release instants and the release intervals and the adaptive law with .
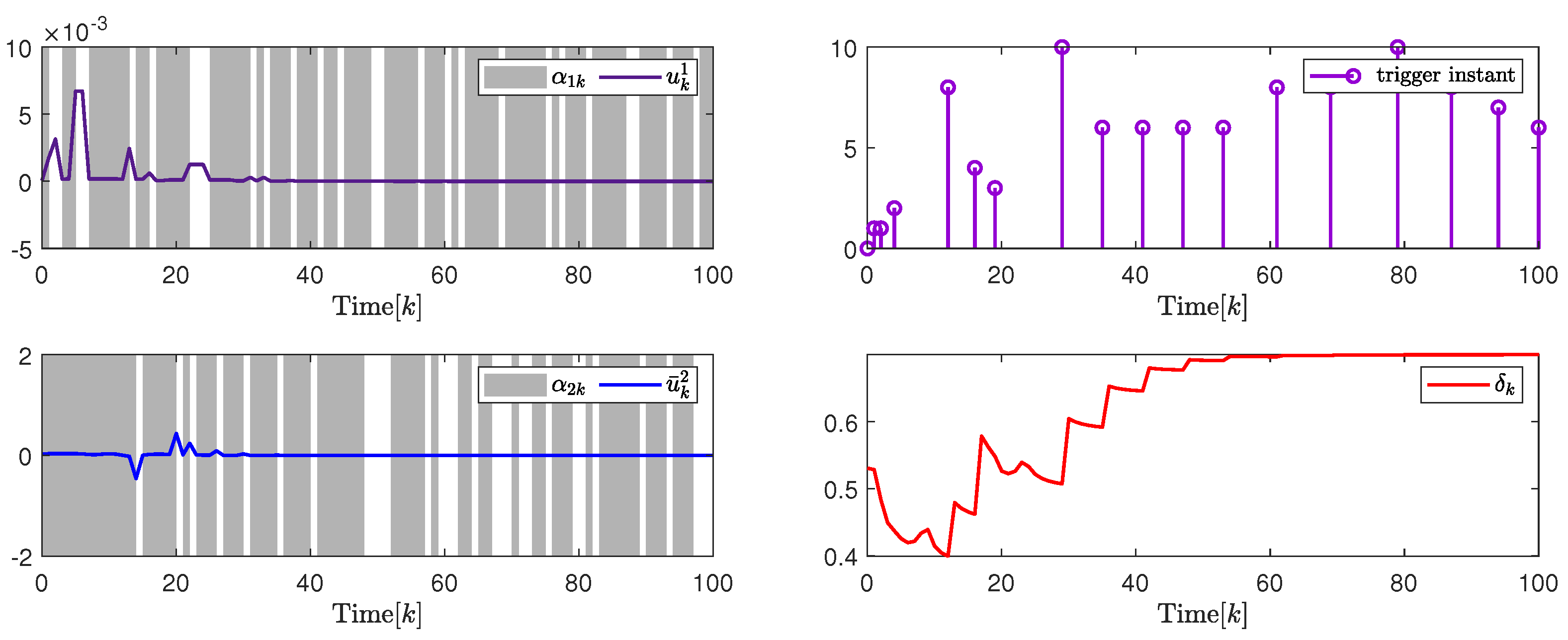
In addition, to further illustrate the impact of the attack probability on packet transmission rate adjustment and system performance, Figure 10 and Figure 11, and Table 2 give the analysis results under different attack probability . By the design results in Theorem 2, the quantization parameter, security fuzzy controller gains, and the ADAETM weighting matrix are obtained as follows: , , , , with . , , , , with .
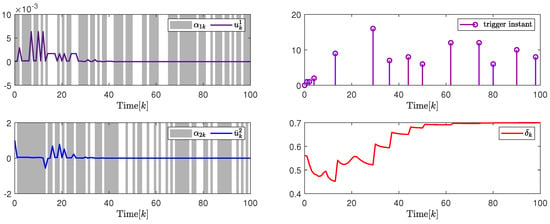
Figure 10.
(Left). The control input and with ; (Right). The release instants and the release intervals and the adaptive law with .
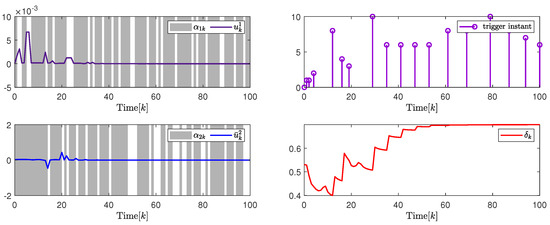
Figure 11.
(Left). The control input and with ; (Right). The release instants and the release intervals and the adaptive law with .
Based on the above calculation results under different attack probability , the left in Figure 10 and Figure 11 are show the trajectory changes of the control input converge to 0 under and , respectively, which indicates the effectiveness of the designed security cascade controller for multi-channel deception attacks. Similar to the analysis of Example with PPBTS, the data in Figure 10 and Figure 11, and Table 3 also show the effectiveness of the designed security cascade controller design algorithm against multi-channel deception attacks. Similar to the analysis results in Section 4.1, Table 4 also gives quantitative performance analysis under different attack probabilities, which further verifies the superiority of the control design.

Table 3.
Data transmission with different ETMs in Example with PPBPGCS.

Table 4.
Quantitative performance index with different attack probability in Example with PPBPGCS.
5. Conclusions
This article mainly explores the SCOFC design problem of nonlinear NCCSs based on ADAETM and dynamic quantization under multi-channel deception attacks interference. The adaptive function of ADAETM can flexibly adjust the triggered threshold according to the state of deception attacks, and further alleviate the impact of deception attacks on system performance and stability. By using Lyapunov–Krasovskii stability theory, matrix decoupling lemma, and relaxation matrix technique, sufficient conditions for the mean square asymptotically stable and prescribed performance of the system are obtained. The criteria for the joint design of event-triggered weight matrix, dynamic quantizer parameters and controller are given in terms of a set of LMIs. Finally, the proposed SCOFC design strategy is verified by simulation of PPBTS and PPBPGCS.
The ADAETM proposed in this article is designed under the assumption that the attack probability is known in advance. Such assumptions inevitably make the design results have certain limitations. In an open network environment, complex, hybrid, and multiple attacks caused by various types of network attacks and a variety of network attack combinations often occur. Therefore, based on the existing work and literature, the future research focus of the security controller design and attack signal observer design problem of NCCSs under multi-channel complex attacks is considered. In addition, the controller design problem of NCCSs affected by internal time-varying delays and other network-induced factors is also a common problem in practical industrial engineering, which also stimulates future research work.
Author Contributions
Conceptualization, X.-M.L. and X.-H.C.; methodology, X.-M.L. and X.-H.C.; software, X.-M.L.; formal analysis, X.-M.L.; investigation, X.-M.L., X.-H.C. and L.-W.H.; writing—original draft preparation, X.-M.L., X.-H.C. and L.-W.H.; writing—review and editing, X.-M.L., X.-H.C. and L.-W.H.; funding acquisition, X.-H.C. All authors have read and agreed to the published version of the manuscript.
Funding
This research was supported by the Basic scientific research project of colleges and universities of Liaoning Province Education Department under Grant LJ212410167048.
Data Availability Statement
The raw data supporting the conclusions of this article will be made available by the authors upon request.
Conflicts of Interest
The authors declare no conflicts of interest.
Abbreviations
The following abbreviations are used in this manuscript:
| T-S | Takagi–Sugeno |
| NCSs | Networked control systems |
| NCCSs | Networked cascade control systems |
| DoS | Denial of service |
| ETM | Event-triggered mechanism |
| ADAETM | Attack-dependent adaptive event-triggered mechanism |
| MFs | Membership functions |
| SCOFC | Security cascade output feedback controller |
| LMIs | Linear matrix inequalities |
| PPBTS | Power plant boiler–turbine system |
| PPBPGCS | Power plant boiler power generation control system |
| TN | Transmission number |
References
- Franks, R.G.; Worley, C.W. Quantitive analysis of cascade control. Ind. Eng. Chem. 1956, 48, 1074–1079. [Google Scholar] [CrossRef]
- Raja, G.L.; Ali, A. Enhanced tuning of Smith predictor based series cascaded control structure for integrating processes. ISA Trans. 2021, 114, 191–205. [Google Scholar] [CrossRef] [PubMed]
- Jia, Y.; Chai, T.; Wang, H.; Su, C.-Y. A signal compensation based cascaded PI control for an industrial heat exchange system. Control Eng. Pract. 2020, 98, 104372. [Google Scholar] [CrossRef]
- Du, Z.; Zhang, C.; Yang, X.; Ye, H.; Li, J. Discrete-time event-triggered H-infinity stabilization for three closed-loop cyber-physical system with uncertain delay. Appl. Math. Comput. 2025, 488, 129127. [Google Scholar] [CrossRef]
- Zhu, H.; Liu, G.; Yu, Z.; Li, Z. Detectability in discrete event systems using unbounded Petri nets. Mathematics 2023, 11, 3862. [Google Scholar] [CrossRef]
- Song, J.; Chang, X.-H.; Li, Z.-M. Secure P2P nonfragile sampled-data controller design for nonlinear networked system under sensor saturation and DoS attack. IEEE Trans. Netw. Sci. Eng. 2023, 10, 1575–1585. [Google Scholar] [CrossRef]
- Liu, Y.; Wei, Y.; Wang, C.; Wu, H. Trajectory optimization for adaptive deformed wheels to overcome steps using an improved hybrid genetic algorithm and an adaptive particle swarm optimization. Mathematics 2024, 12, 2077. [Google Scholar] [CrossRef]
- Mathiyalagan, K.; Park, J.H.; Sakthivel, R. New results on passivity-based H∞ control for networked cascade control systems with application to power plant boiler–turbine system. Nonlinear Anal. Hybrid Syst. 2015, 17, 56–69. [Google Scholar] [CrossRef]
- Huang, C.; Bai, Y.; Liu, X. H-infinity state feedback control for a class of networked cascade control systems with uncertain delay. IEEE Trans. Ind. Inform. 2010, 6, 62–72. [Google Scholar] [CrossRef]
- Pang, Z.-H.; Fan, L.-Z.; Guo, H.; Shi, Y.; Chai, R.; Sun, J.; Liu, G.-P. Security of networked control systems subject to deception attacks: A survey. Int. J. Syst. Sci. 2022, 53, 3577–3598. [Google Scholar] [CrossRef]
- Gu, Z.; Zhang, T.; Yang, F.; Zhao, H.; Shen, M. A novel event-triggered mechanism for networked cascade control system with stochastic nonlinearities and actuator failures. J. Frankl. Inst. 2019, 356, 1955–1974. [Google Scholar] [CrossRef]
- Zhao, N.; Shi, P.; Xing, W.; Agarwal, R.K. Resilient event-triggered control for networked cascade control systems under denial-of-service attacks and actuator saturation. IEEE Syst. J. 2022, 16, 1114–1122. [Google Scholar] [CrossRef]
- Fallahnejad, M.; Kazemy, A.; Shafiee, M. Event-triggered H∞ stabilization of networked cascade control systems under periodic DoS attack: A switching approach. Int. J. Electr. Power Energy Syst. 2023, 153, 109278. [Google Scholar] [CrossRef]
- An, L.; Yang, G.-H. Improved adaptive resilient control against sensor and actuator attacks. Inf. Sci. 2018, 423, 145–156. [Google Scholar] [CrossRef]
- Ding, D.; Wei, G.; Zhang, S.; Liu, Y.; Alsaadi, F.E. On scheduling of deception attacks for discrete-time networked systems equipped with attack detectors. Neurocomputing 2016, 219, 99–106. [Google Scholar] [CrossRef]
- Wang, X.; Cao, Y.; Niu, B.; Song, Y. A novel bipartite consensus tracking control for multiagent systems under sensor deception attacks. IEEE Trans. Cybern. 2023, 53, 5984–5993. [Google Scholar] [CrossRef]
- Ding, D.; Wang, Z.; Ho, D.W.C.; Wei, G. Distributed recursive filtering for stochastic systems under uniform quantizations and deception attacks through sensor networks. Automatica 2017, 78, 231–240. [Google Scholar] [CrossRef]
- Guo, H.; Pang, Z.-H.; Sun, J.; Li, J. An output-coding-based detection scheme against replay attacks in cyber-physical systems. IEEE Trans. Circuits Syst. II Express Briefs 2021, 68, 3306–3310. [Google Scholar] [CrossRef]
- Xie, J.; Zhu, S.; Zhang, D. Distributed interval state estimation with l∞-gain optimization for cyber-physical systems subject to bounded disturbance and random stealthy attacks. ISA Trans. 2022, 127, 22–31. [Google Scholar] [CrossRef]
- Liu, J.; Gu, Y.; Xie, X.; Yue, D.; Park, J.H. Hybrid-driven-based H∞ control for networked cascade control systems with actuator saturations and stochastic cyber attacks. IEEE Trans. Syst. Man Cybern. Syst. 2019, 49, 2452–2463. [Google Scholar] [CrossRef]
- Hu, Z.; Chen, K.; Deng, F.; Luo, S.; Hu, S. H∞ controller design for networked systems with two-channel packet dropouts and FDI attacks. IEEE Trans. Cybern. 2024, 54, 1661–1670. [Google Scholar] [CrossRef] [PubMed]
- Zhang, H.; Zhao, N.; Wang, S.; Agarwal, R.K. Improved event-triggered dynamic output feedback control for networked T-S fuzzy systems with actuator failure and deception attacks. IEEE Trans. Cybern. 2023, 53, 7989–7999. [Google Scholar] [CrossRef] [PubMed]
- Wang, X.-Y.; Chang, X.-H. Nonlinear continuous-time system H∞ control based on dynamic quantization and event-triggered mechanism. Neural Process. Lett. 2023, 55, 12223–12238. [Google Scholar] [CrossRef]
- Xie, Y.; Ding, S.; Jing, Y.; Xie, X. Distributed set-membership estimation over sensor networks via an event-driven dynamic quantization scheme. IEEE Syst. J. 2024, 18, 1151–1161. [Google Scholar] [CrossRef]
- Zhu, Q. Event-triggered sampling problem for exponential stability of stochastic nonlinear delay systems driven by Le´vy processes. IEEE Trans. Autom. Control 2024, in press. Available online: https://ieeexplore.ieee.org/document/10643716 (accessed on 22 August 2024). [CrossRef]
- Du, Z.; Yuan, W.; Hu, S. Discrete-time event-triggered H-infinity stabilization for networked cascade control systems with uncertain delay. J. Frankl. Inst. 2019, 356, 9524–9544. [Google Scholar] [CrossRef]
- Liu, J.; Wang, Y.; Zha, L.; Yan, H. Event-based control for networked T-S fuzzy cascade control systems with quantization and cyber attacks. J. Frankl. Inst. 2019, 356, 9451–9473. [Google Scholar] [CrossRef]
- Takagi, T.; Sugeno, M. Fuzzy identification of systems and its applications to modeling and control. IEEE Trans. Syst. Man Cybern. 1985, SMC-15, 116–132. [Google Scholar] [CrossRef]
- Tan, Y.; Wang, K.; Su, X.; Xue, F.; Shi, P. Event-triggered fuzzy filtering for networked systems with application to sensor fault detection. IEEE Trans. Fuzzy Syst. 2021, 29, 1409–1422. [Google Scholar] [CrossRef]
- Zhu, Z.; Zhu, Q. Adaptive event-triggered fuzzy control for stochastic highly nonlinear systems with time delay and nontriangular structure interconnections. IEEE Trans. Fuzzy Syst. 2024, 32, 27–37. [Google Scholar] [CrossRef]
- Zhang, L.; Zong, G.; Zhao, X.; Zhao, N.; Sharaf, S. Reachable set control for discrete-time takagi–sugeno fuzzy singular Markov jump system. IEEE Trans. Fuzzy Syst. 2023, 31, 3173–3184. [Google Scholar] [CrossRef]
- Yang, F.; Hu, S.; Xie, X.; Yue, D.; Sun, J. Resilient fuzzy control synthesis of nonlinear DC microgrid via a time-constrained DoS attack model. IEEE Trans. Autom. Sci. Eng. 2024, 21, 5270–5279. [Google Scholar] [CrossRef]
- Zhao, X.-Y.; Chang, X.-H. H∞ filtering for nonlinear discrete-time singular systems in encrypted state. Neural Process. Lett. 2023, 55, 2843–2866. [Google Scholar] [CrossRef]
- Liu, X.-M.; Chang, X.-H. Adaptive event-triggered tracking control for nonlinear networked systems with dynamic quantization and deception attacks. Int. J. Robust Nonlinear Control 2024, 34, 8311–8333. [Google Scholar] [CrossRef]
- Zha, L.; Liao, R.; Liu, J.; Xie, X.; Tian, E.; Cao, J. Dynamic event-triggered output feedback control for networked systems subject to multiple cyber attacks. IEEE Trans. Cybern. 2022, 52, 13800–13808. [Google Scholar] [CrossRef]
- Elahi, A.; Alfi, A. Finite-time stabilisation of discrete networked cascade control systems under transmission delay and packet dropout via static output feedback control. Int. J. Syst. Sci. 2020, 51, 87–101. [Google Scholar] [CrossRef]
- Zhu, Q. Stabilization of stochastic nonlinear delay systems with exogenous disturbances and the event-triggered feedback control. IEEE Trans. Autom. Control 2019, 9, 3764–3771. [Google Scholar] [CrossRef]
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2024 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).