Research on Virus Propagation Network Intrusion Detection Based on Graph Neural Network
Abstract
1. Introduction
- (1)
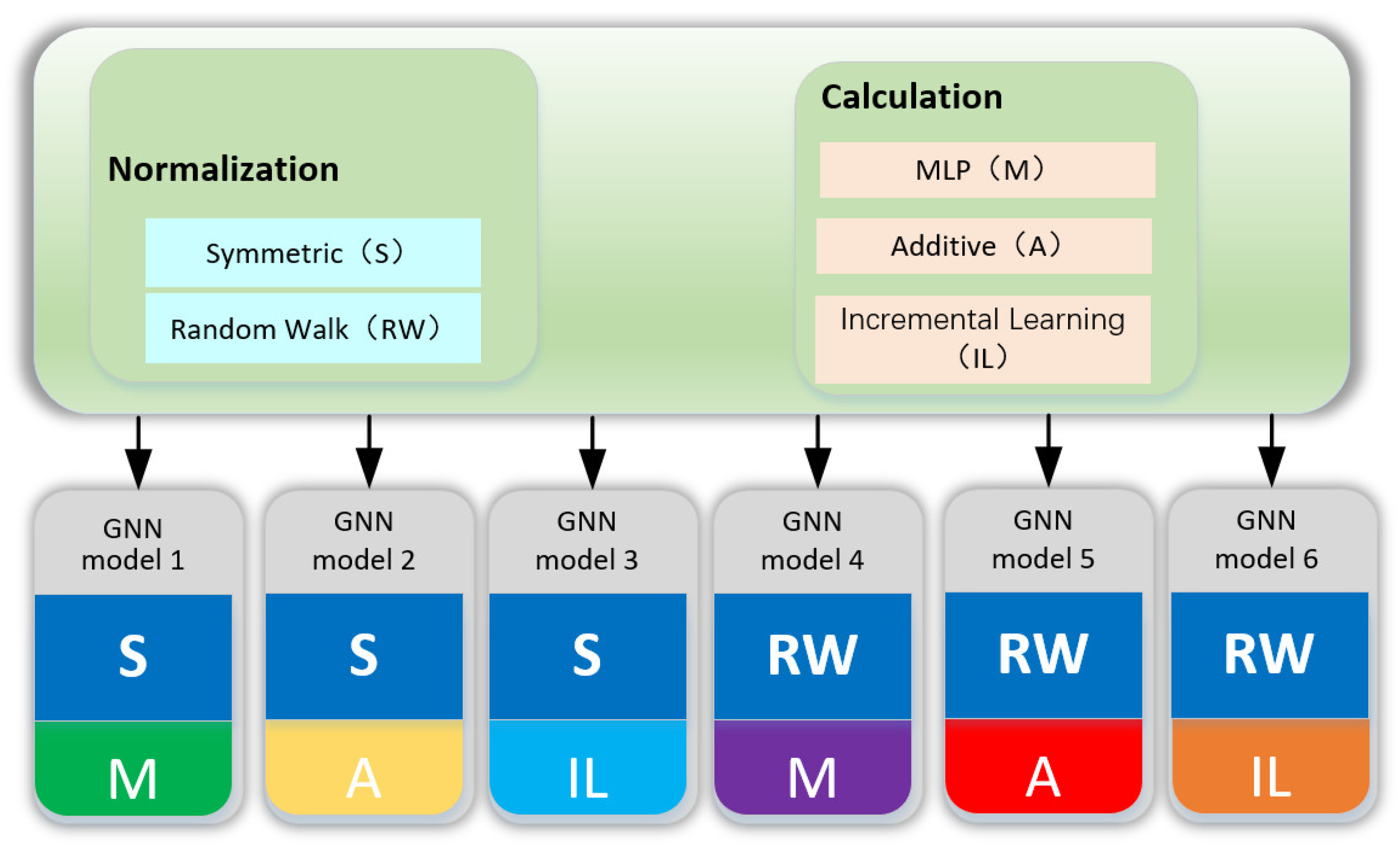
- We construct a GNN model. Our GNN model consists of the standardization module and the computation module—the two modules stack on top of each other to form a powerful GNN model.
- (2)
- (3)
- The computing module consists of three parts: multi-layer perceptron (MLP) (ref. [24,25,26]) and additive and incremental learning methods. MLP is a classical neural network model with a wide range of applications; the additive method is a simple and effective algorithm that can quickly adapt to new input data; the incremental learning rule is a method of updating model parameters, which can improve the training effect and generalization ability of the model. These three parts constitute an efficient and reliable computing module that performs well in data classification and text clustering tasks.
2. Related Work
3. Virus Transmission Detection Model Based on Graph Neural Network
3.1. Model Overview
3.2. GNN Model of Virus Transmission Network Detection
| Algorithm 1 GNN model training process of virus transmission network |
| Input: original datasets D; Output: Accuracy and interpretability scores r of six GNN models; 1. Raw data preprocessing; 2. while original datasets D do; 3. Edges with scores greater than or equal to the critical value are taken out to form a star topology model; 4. end while; 5. Design and training of GNN model for virus transmission network detection: 6. GNN layer design: Determine the normalization method and calculation method; 7. Train the GNN model; 8. while star topology A, node feature X do; 9. Through , get input A get; 10. end while; 11. GNN model analysis; 12. Calculate the detection accuracy of the GNN model according to (7); 13. Calculate the interpretability score r of the GNN model according to (9); 14. return , r; |
4. Results and Analysis
4.1. Experimental Datasets
4.2. Scoring Criteria
4.3. Experimental Results and Analysis
- (1)
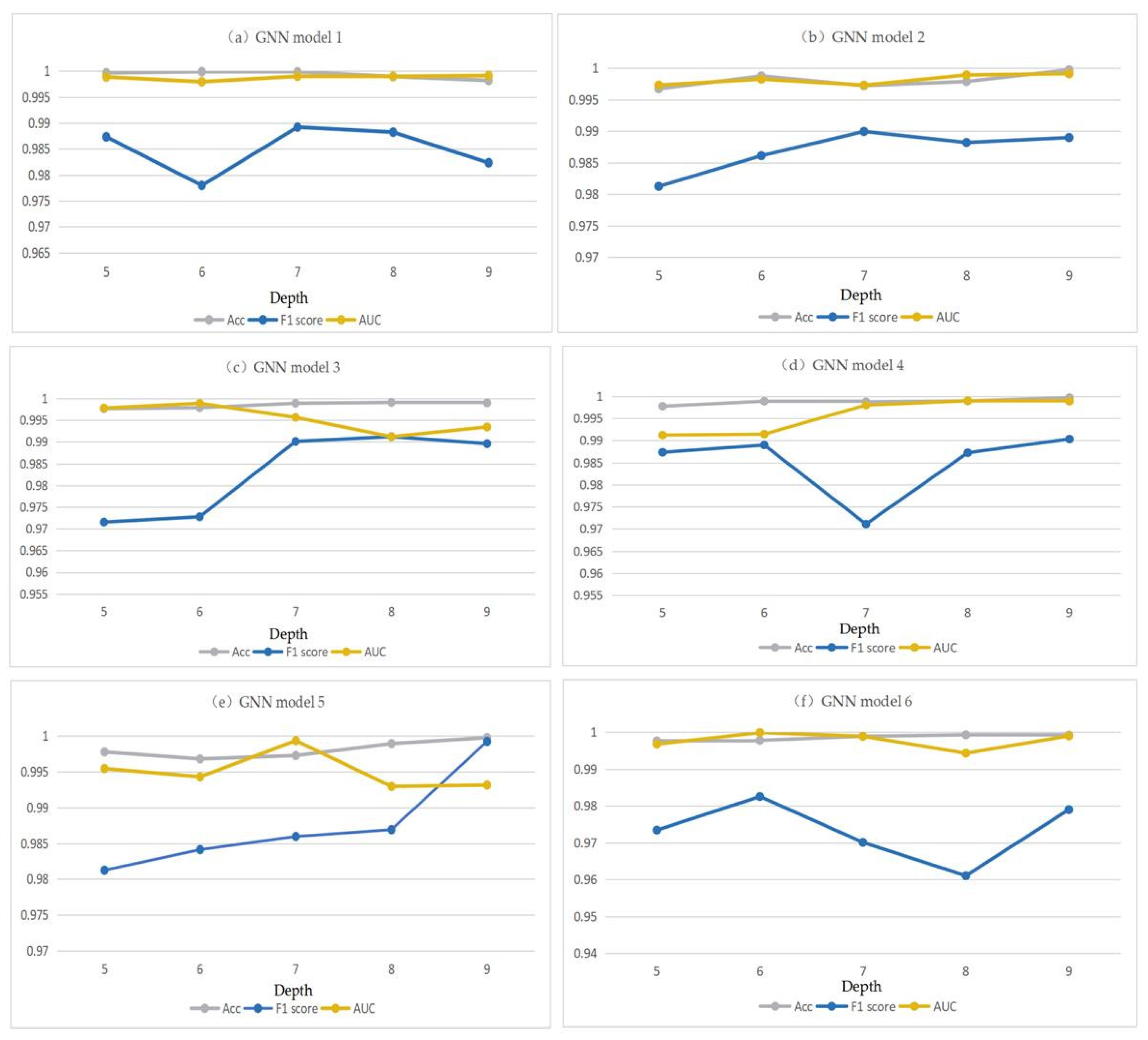
- We must determine the optimal depth of each GNN model based on the performance of different GNN models at different depths to ensure that different GNN models are in the best state during the comparison. We conducted experiments on the virus transmission network using different models. To demonstrate objectivity and simplicity, we used the line chart in Figure 2 to show the changes in the models with varying performances under different depths. Depth 5–9 was selected for the chart description. It can be seen from Figure 2 that different design models all performed well. The F1, Acc, and AUC values of varying design models at different depths are more significant than 0.96, 0.99, and 0.97, respectively. Since the value of F1 has the most significant variation amplitude under the same model, we choose the value of F1 as the index to select the optimal depth under the same model.
- (2)
- We can evaluate the model numerically using the extraction density, detection accuracy, and model score value, making it more standardized, specific, and reliable.
- (3)
- As can be seen from Table 2, when the extraction densities of the six models are close, the detection accuracy of GNN model 4, which is composed of the random walk method and multi-layer perceptron, is 91.7%, which is much higher than that of the other six models. Its model score is 0.683, which is the highest among the six groups. Moreover, we find that when the calculation modules are the same, and the normalization module is the random walk method, the variance in the detection accuracy is generally smaller than that when the normalization module is symmetric, indicating better detection stability.
- (4)
- It can be seen from Figure 3 that the variation curves of each model at different depths and the comparison between each model show that the GNN model formed by stacking random walk and MLP has higher detection accuracy than other models at different depths. According to Table 3, the detection accuracy ACCd of the GNN model formed by random walk and the MLP stack is higher than that of the machine learning model and deep learning model, and the model score value r of this GNN model is much higher than that of other models.
| GNN Model | Normalization | Calculation | Extraction Density ρ | Detection Accuracy ACCd | Score r | Variance of Detection Accuracy |
|---|---|---|---|---|---|---|
| 1 | Symmetric | MLP | 24.3% | 65.1% | 0.428 | 0.0058 |
| 2 | Symmetric | Additive | 24.2% | 63.2% | 0.459 | 0.0061 |
| 3 | Symmetric | IL | 25.1% | 67.3% | 0.512 | 0.0052 |
| 4 | Random walk | MLP | 25.4% | 91.7% | 0.683 | 0.0023 |
| 5 | Random walk | Additive | 25.2% | 68.9% | 0.487 | 0.0032 |
| 6 | Random walk | IL | 25.4% | 63.5% | 0.493 | 0.0029 |
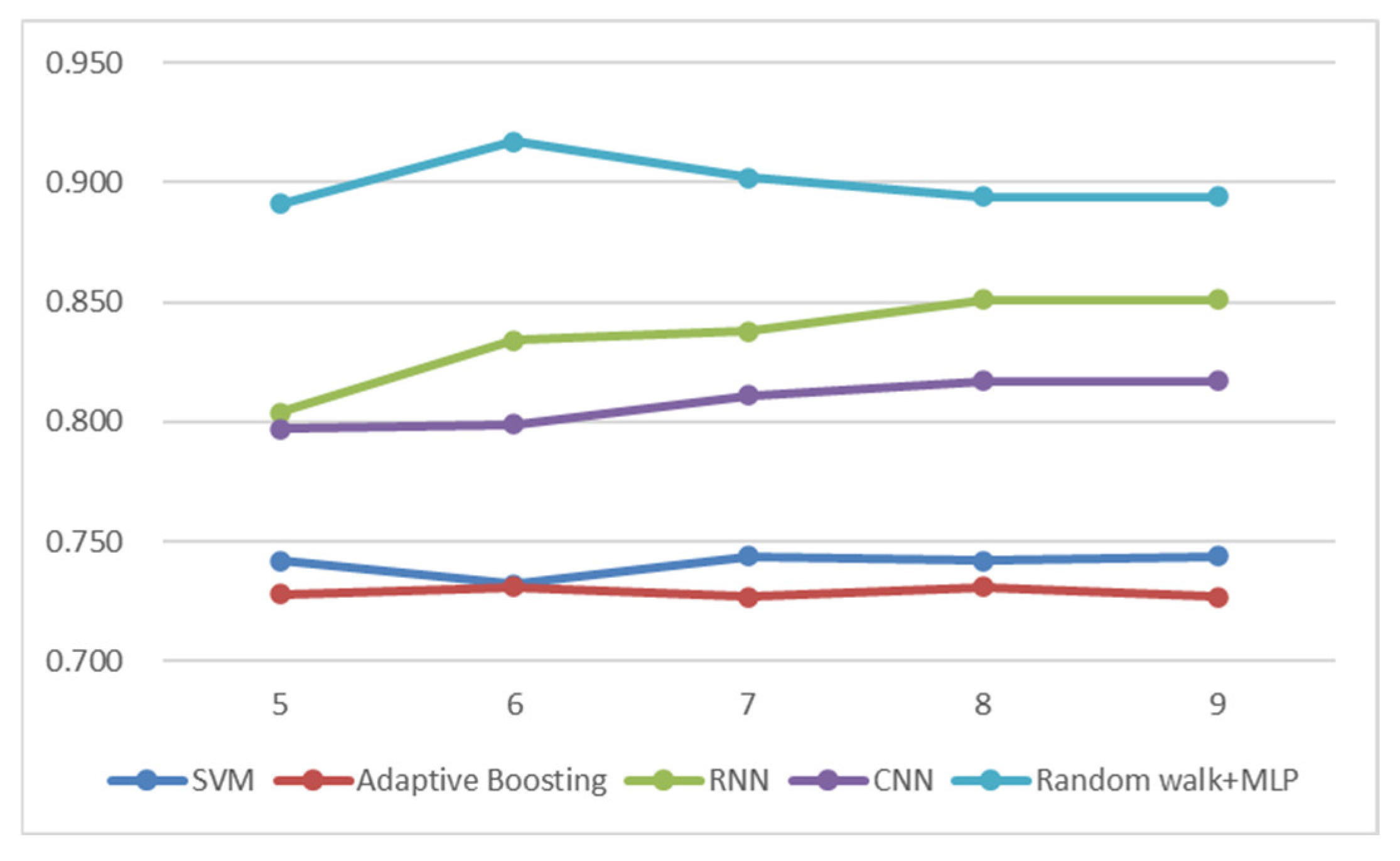
| Category | Algorithm | Detection Accuracy ACCd | Score r |
|---|---|---|---|
| Machine learning | SVM | 74.4% | 0.446 |
| Adaptive Boosting | 73.1% | 0.439 | |
| Deep learning | RNN | 85.1% | 0.468 |
| CNN | 81.7% | 0.454 | |
| GNN | Random walk + MLP | 91.7% | 0.683 |
5. Conclusions
Author Contributions
Funding
Data Availability Statement
Acknowledgments
Conflicts of Interest
References
- Dung, N.Q.; Viet, L.H. Directed-System-Call-Graph Feature for IoT Botnet Detection. J. Intell. Fuzzy Syst. 2022, 43, 5453–5470. [Google Scholar] [CrossRef]
- Rezaei, A. Using Ensemble Learning Technique for Detecting Botnet on IoT. SN Comput. Sci. 2021, 2, 148. [Google Scholar] [CrossRef]
- Popoola, S.I.; Adebisi, B.; Hammoudeh, M.; Gui, G.; Gacanin, H. Hybrid Deep Learning for Botnet Attack Detection in the Internet-of-Things Networks. IEEE Internet Things J. 2021, 8, 4944–4956. [Google Scholar] [CrossRef]
- Wan Nur Hidayah, I.; Anuar, S.; Selamat, A.; Krejcar, O.; Crespo, R.G.; Herrera-Viedma, E.; Fujita, H. Multilayer Framework for Botnet Detection Using Machine Learning Algorithms. IEEE Access 2021, 9, 48753–48768. [Google Scholar]
- Alothman, Z.; Alkasassbeh, M.; Al Haj Baddar, S. An efficient approach to detect IoT botnet attacks using machine learning. J. High Speed Netw. 2020, 26, 241–254. [Google Scholar] [CrossRef]
- Hiebeler, D.E.; Audibert, A.; Strubell, E.; Michaud, I.J. An epidemiological model of internet worms with hierarchical dispersal and spatial clustering of hosts. J. Theor. Biol. 2017, 418, 8–15. [Google Scholar] [CrossRef]
- Maniriho, P.; Mahmood, A.N.; Chowdhury, M.M. A study on malicious software behaviour analysis and detection techniques: Taxonomy, current trends and challenges. J. Theor. Biol. 2017, 418, 8–15. [Google Scholar] [CrossRef]
- Ashik, M.; Jyothish, A.; Anandaram, S.; Vinod, P.; Mercaldo, F.; Martinelli, F.; Santone, A. Detection of Malicious Software by Analyzing Distinct Artifacts Using Machine Learning and Deep Learning Algorithms. Electronics 2021, 10, 1694. [Google Scholar] [CrossRef]
- Dounavi, H.M.; Mpanti, A.; Nikolopoulos, S.D.; Polenakis, I. A graph-based framework for malicious software detection and classification utilizing temporal-graphs. Electronics 2021, 10, 1694. [Google Scholar] [CrossRef]
- Ali, M.; Shiaeles, S.; Clarke, N.; Kontogeorgis, D. A proactive malicious software identification approach for digital forensic examiners. J. Inf. Secur. Appl. 2019, 47, 139–155. [Google Scholar] [CrossRef]
- Awad, M.; Fraihat, S.; Salameh, K.; Al Redhaei, A. Examining the Suitability of NetFlow Features in Detecting IoT Network Intrusions. Sensors 2022, 22, 6164. [Google Scholar] [CrossRef] [PubMed]
- Tao, Y.; Ruiqi, Y. Detecting Abnormal Interactions among Intranet Groups Based on Netflow Data. IOP Conf. Ser. Earth Environ. Sci. 2020, 428, 012039. [Google Scholar]
- Tania, K.P.; Putra, N.S.; Made, D.W. NetFlow dalam Monitoring Penggunaan Internet. Maj. Ilm. Teknol. Elektro 2017, 16, 86. [Google Scholar]
- Liu, L.; Wang, P.; Lin, J.; Liu, L. Intrusion Detection of Imbalanced Network Traffic Based on Machine Learning and Deep Learning. IEEE Access 2021, 9, 7550–7563. [Google Scholar] [CrossRef]
- Li, Z.; Hou, J.; Wang, H.; Wang, C.; Kang, C.; Fu, P. Ethereum Behavior Analysis with NetFlow Data. IEICE Proceeding Ser. 2019, 59, TS2–TS4. [Google Scholar]
- Sun, A.Y.; Jiang, P.; Yang, Z.L.; Xie, Y.; Chen, X. A graph neural network (GNN) approach to basin-scale river network learning: The role of physics-based connectivity and data fusion. Hydrol. Earth Syst. Sci. 2022, 26, 5163–5184. [Google Scholar] [CrossRef]
- Govindaraju, S.; Vinisha WV, R.; Shajin, F.H.; Sivasakthi, D.A. Intrusion detection framework using auto-metric graph neural network optimized with hybrid woodpecker mating and capuchin search optimization algorithm in IoT network. Concurr. Comput. Pract. Exp. 2022, 34, e7197. [Google Scholar] [CrossRef]
- Sun, L.; Liu, T.; Wang, D.; Huang, C.; Xie, Y. Deep learning method based on graph neural network for performance prediction of supercritical CO2 power systems. Appl. Energy 2022, 324, 119739. [Google Scholar] [CrossRef]
- Chen, Y.; Tang, X.; Qi, X.; Li, C.G.; Xiao, R. Learning graph normalization for graph neural networks. Neurocomputing 2022, 493, 613–625. [Google Scholar] [CrossRef]
- Peng, L.; Hu, R.; Kong, F.; Gan, J.; Mo, Y.; Shi, X.; Zhu, X. Reverse Graph Learning for Graph Neural Network. IEEE Trans. Neural Netw. Learn. Syst. 2022, 35, 4530–4541. [Google Scholar] [CrossRef]
- Zhou, J.; Li, L.; Zeng, A.; Fan, Y.; Di, Z. Random walk on signed networks. Phys. A Stat. Mech. Its Appl. 2018, 508, 558–566. [Google Scholar] [CrossRef]
- Xu, X.K.; Zhu, J.J. Flexible sampling large-scale social networks by self-adjustable random walk. Phys. A Stat. Mech. Its Appl. 2016, 463, 356–365. [Google Scholar] [CrossRef]
- Hilário, M.; Den Hollander, F.; Sidoravicius, V.; Soares dos Santos, R.; Teixeira, A. Random walk on random walks. Electron. J. Probab. 2015, 20, 1–35. [Google Scholar] [CrossRef]
- Naskath, J.; Sivakamasundari, G.; Begum, A.A.S. A Study on Different Deep Learning Algorithms Used in Deep Neural Nets: MLP SOM and DBN. Wirel. Pers. Commun. 2022, 21–24. [Google Scholar] [CrossRef] [PubMed]
- Kumar, M.; Verma, G. Machine Learning Intrusion Detection System Based on MLP and RNN Stochastic Optimization Technology. J. Res. Sci. Eng. 2022, 4. [Google Scholar] [CrossRef] [PubMed]
- Ding, Q.; Yin, S.; Liu, L.; Wang, C. Hardware Trojan detection research based on MLP. J. Phys. Conf. Ser. 2020, 1684, 012065. [Google Scholar] [CrossRef]
- Buczak, A.L.; Guven, E. A survey of data mining and machine learning methods for cyber security intrusion detection. IEEE Commun. Surv. Tutor. 2015, 18, 1153–1176. [Google Scholar] [CrossRef]
- Ahmad, I.; Basheri, M.; Iqbal, M.J.; Rahim, A. Performance comparison of support vector machine, random forest, and extreme learning machine for intrusion detection. IEEE Access 2018, 6, 33789–33795. [Google Scholar] [CrossRef]
- Hu, C.J.; Wang, J. The SVM and Layered Intrusion Detection System Based on Network Hierarchical. In Internet of Things, Proceedings of the International Workshop, IOT 2012, Changsha, China, 17–19 August 2012; Springer: Berlin/Heidelberg, Germany, 2012; Volume 312, p. 312. [Google Scholar]
- Manghnani, T.; Thirumaran, T. Computational CBGSA–SVM Model for Network Based Intrusion Detection System. In Applications and Techniques in Information Security, Proceedings of the 10th International Conference, ATIS 2019, Thanjavur, India, 22–24 November 2019; Springer: Singapore, 2019; Volume 1116, p. 1116. [Google Scholar]
- Louk, M.H.L.; Tama, B.A. Dual-IDS: A bagging-based gradient boosting decision tree model for network anomaly intrusion detection system. Expert Syst. Appl. 2023, 213, 119030. [Google Scholar] [CrossRef]
- Srikanth, Y.M.; Kalpana, R. Recurrent nonsymmetric deep auto encoder approach for network intrusion detection system. Meas. Sens. 2022, 24, 100527. [Google Scholar]
- Shen, Y. An Intrusion Detection Algorithm for DDoS Attacks Based on DBN and Three-way Decisions. J. Phys. Conf. Ser. 2022, 2356, 012044. [Google Scholar] [CrossRef]
- Wang, J.; Liu, H.; Liu, F. Research on Deep Learning Method Based on Blockchain and Intrusion Detection Model. J. Phys. Conf. Ser. 2022, 2356, 012057. [Google Scholar] [CrossRef]
- Deore, B.; Bhosale, S. Intrusion Detection System Based on RNN Classifier for Feature Reduction. SN Comput. Sci. 2022, 3, 114. [Google Scholar] [CrossRef]
- Sheikhan, M.; Jadidi, Z.; Farrokhi, A. Intrusion detection using reduced-size RNN based on feature grouping. Neural Comput. Appl. 2012, 21, 1185–1190. [Google Scholar] [CrossRef]
- Gan, B.; Chen, Y.; Dong, Q.; Guo, J.; Wang, R. A convolutional neural network intrusion detection method based on data imbalance. J. Supercomput. 2022, 78, 19401–19434. [Google Scholar] [CrossRef]
| ID | IRC | SPAM | CF | PS | DDOS | FF | P2P | US | HTTP | Abnormal Edge | Normal Edge | Background Flow |
|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1 | ✓ | ✓ | ✓ | 39,933 | 30,387 | 2,753,290 | ||||||
| 2 | ✓ | ✓ | ✓ | 18,839 | 9120 | 1,778,061 | ||||||
| 3 | ✓ | ✓ | ✓ | 26,759 | 116,887 | 4,566,929 | ||||||
| 4 | ✓ | ✓ | ✓ | 1719 | 25,268 | 1,094,040 | ||||||
| 5 | ✓ | ✓ | ✓ | 695 | 4679 | 124,252 | ||||||
| 6 | ✓ | 4431 | 7494 | 546,795 | ||||||||
| 7 | ✓ | 37 | 1677 | 112,337 | ||||||||
| 8 | ✓ | 5052 | 72,822 | 2,875,282 | ||||||||
| 9 | ✓ | ✓ | ✓ | ✓ | 179,880 | 43,340 | 2,525,565 | |||||
| 10 | ✓ | ✓ | ✓ | 106,315 | 15,847 | 1,187,592 | ||||||
| 11 | ✓ | ✓ | ✓ | 8161 | 2718 | 96,369 | ||||||
| 12 | ✓ | 2143 | 7628 | 315,675 | ||||||||
| 13 | P | ✓ | ✓ | 38,791 | 31,939 | 1,853,217 |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2024 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Ying, X.; Pan, M.; Chen, X.; Zhou, Y.; Liu, J.; Li, D.; Guo, B.; Zhu, Z. Research on Virus Propagation Network Intrusion Detection Based on Graph Neural Network. Mathematics 2024, 12, 1534. https://doi.org/10.3390/math12101534
Ying X, Pan M, Chen X, Zhou Y, Liu J, Li D, Guo B, Zhu Z. Research on Virus Propagation Network Intrusion Detection Based on Graph Neural Network. Mathematics. 2024; 12(10):1534. https://doi.org/10.3390/math12101534
Chicago/Turabian StyleYing, Xianer, Mengshuang Pan, Xiner Chen, Yiyi Zhou, Jianhua Liu, Dazhi Li, Binghao Guo, and Zihao Zhu. 2024. "Research on Virus Propagation Network Intrusion Detection Based on Graph Neural Network" Mathematics 12, no. 10: 1534. https://doi.org/10.3390/math12101534
APA StyleYing, X., Pan, M., Chen, X., Zhou, Y., Liu, J., Li, D., Guo, B., & Zhu, Z. (2024). Research on Virus Propagation Network Intrusion Detection Based on Graph Neural Network. Mathematics, 12(10), 1534. https://doi.org/10.3390/math12101534







