1. Introduction
The attention of equipment manufacturers and carriers is now turned to future networks with terabit data rates. Such networks are expected to mark a groundbreaking shift from the services of yesterday, such as the Internet of Things [
1], to those of the future, such as the Internet of Everything (IoE) [
2,
3]. One IoE scenario which attracts increasing attention these days is an intelligent autonomous system that performs certain missions without human involvement. Such systems include autonomous UAVs fleets (or drones swarms, drones fleets) [
4,
5] capable of solving tasks and making decisions independently without interaction with the control center. This is especially relevant when the standard positioning technologies (Global Navigation Satellite System (GNSS), base stations, Wi-Fi) are not available [
6].
Lack of positioning information from external sources can be caused by many reasons. There are areas where infrastructure deployment is challenging (mountainous terrain), and sometimes economically unprofitable (remote areas). In some areas, there is no network coverage due to natural reflectors (forests, caves). Nevertheless, some scenarios require communications to be maintained under any conditions. During search and rescue operations in remote and inaccessible places, it is crucial not only to keep a drone swarm connected but also to transmit information quickly and efficiently [
7]. Another scenario could include the use of swarms indoors, for example, inside large shopping malls, to identify and eliminate the causes of local disasters. Indoors, the GPS signal is typically absent due to shielding, and additional sources of drone positioning information, such as the cellular network, may also be partly unavailable (e.g., due to an emergency situation).
There are many aspects to consider when designing an intelligent autonomous drone swarm system: control and management of the swarm, its efficiency, and performance of the distributed computations. Nevertheless, one of the main challenges is to maintain the connectivity of an autonomous drone swarm [
8]. Connectivity is needed (i) to maintain swarm integrity (if any drone is lost, the swarm loses its structure, resulting in reduced functionality) (ii) to traverse various complex objects (e.g., tree crowns), and (iii) to perform distributed or a centralized computation within the swarm and exchange information between drones. Thus, it is necessary to ensure the efficient routing of information within the swarm.
As it was mentioned before, the support of UAVs (or drones) connectivity is challenging. One of the solutions is wireless ad hoc networks—decentralized wireless networks with no permanent structure [
9]. Due to the simplicity and low cost of deployment, wireless ad hoc networks perfectly fit many applications in medical, intelligent transport, and other fields. Among all the possible use cases, UAV ad hoc networks remain the most promising one—for instance, the specifics of ad hoc networks perfectly suit the purposes of search and rescue operations [
10].
Traditional routing protocols based on the awareness of each network node about the location of all other nodes require regular exchange of signaling information between all network nodes and are inefficient in these conditions due to excessive overheads. Alternatively, one might use data about the local position of devices obtained from external sources for routing in ad hoc networks. Geographical routing is an example of a protocol that uses the geographical coordinates of the device to deliver data. However, as mentioned above, external information may not always be available.
In this paper, we propose an iterative algorithm for positioning nodes in the developed Unit Virtual Coordinate System (UVCS), which allows, using the information available in the node only about the presence of neighbors in a given radius and the distance to each of them, to determine its coordinates in the UVCS. Based on the UVCS, it becomes possible to apply one of the geographic routing algorithms to build a route to any network node, without even knowing the direction to the destination node. The developed approach, which combines the UVCS system and a geographic routing algorithm, allows maintainenance self-organization and topology to ensure the connectivity of a drones swarm.
The iterative algorithm for positioning nodes in the UVCS system works on the principle of fast gradient descent and minimizes the difference between the known estimate of the distance to a neighboring node and the distance in the UVCS system, averaged over all neighboring nodes.
The main contributions of our study are as follows:
we propose an approach for self-organization and topology support in drone swarms in the complete absence of external positioning information using the developed Unit Virtual Coordinate System;
we propose metrics to analyze the characteristics of intra-swarm routing on top of the developed Unit Virtual Coordinate System;
we carry out a comparative analysis of the characteristics of self-organization according to the topology formed by the developed algorithm, with the topology obtained with complete knowledge of the network. Methods of queuing theory are used to carry out the analysis.
The rest of the paper is organized as follows.
Section 2 reviews the current state of the problem of connectivity support and routing in autonomous swarms. In
Section 3, we introduce an algorithm for assigning virtual coordinates based on the locally available knowledge. In
Section 4, we specify the mathematical model.
Section 5 introduces the metrics of interest. The numerical results are presented in
Section 6, and conclusions are drawn in the last section.
2. Related Work
With the emergence of the Internet of Things (IoT), devices have been firmly embedded in daily lives. For simplicity of deployment and operation of such large decentralized systems, it is convenient to combine devices into a single distributed network, which can be controlled remotely. Wireless self-organizing dynamic networks utilized for this task are a particular case of well-known ad hoc networks.
An ad hoc network is a collection of wireless mobile nodes dynamically forming a temporary network without the use of any existing network infrastructure or centralized administration [
11]. A distinguishing feature of such networks is that each node acts as both an end system and a router. Ad hoc networks can be deployed in territories with no infrastructure, for example, in scenarios such as disaster relief. The topology of ad hoc networks changes much more frequently as compared to wired networks. The routing protocol must ensure network scalability, robustness [
12], and energy efficiency [
13].
Over the past decades, many algorithms have been proposed for routing in wireless communication networks [
14]. Table-driven routing traditionally implemented in wired networks, despite the reliability of operation and simplicity of configuration, have a number of drawbacks when deployed on wireless ad hoc systems. Specifically, the dynamics of the system topology require frequent updates of the routing tables, sometimes even non-incremental ones. On the other hand, on-demand routing protocols, such as the Ad hoc On-Demand Distance Vector (AODV) routing protocol, introduce large delays required to route discovery prior to information transmission [
15].
As an alternative solution to table-driven and on-demand routing, geographic routing protocols can be utilized [
16,
17]. According to them, packets are forwarded between nodes based on their geographic locations, which are utilized as addresses. At each intermediate node, the process of selecting the next node for forwarding is based on the geographic position of the destination node and the coordinates of the neighboring forwarding candidates. The simplest strategy is to use greedy forwarding and by sending the data packets to the neighbor that is geographically closest to the destination.
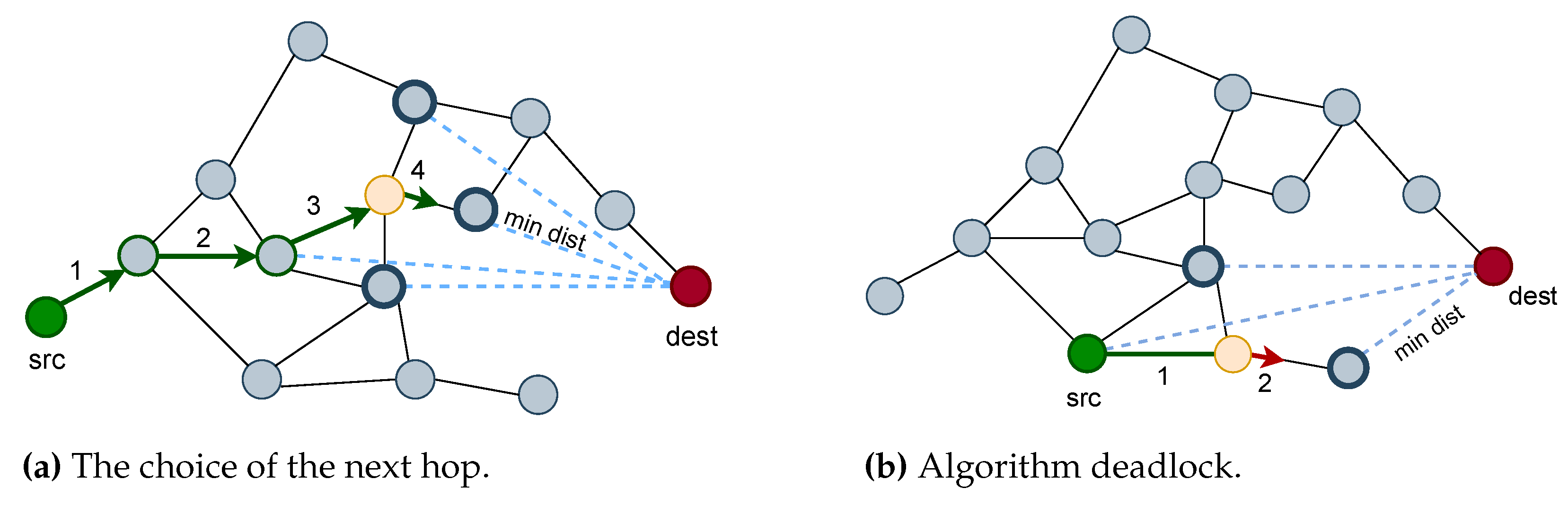
Figure 1a shows a scenario where data are transferred from the green node src to the red node dest. Specifically, the next node is chosen based on two characteristics. Firstly, it should be adjacent to the current node. Secondly, the distance between the potential node and the destination node should be minimal. The figure illustrates the choice of the node in the fourth step. The current node, highlighted in yellow, has four adjacent nodes (marked in bold). Comparing the distances between the bold and dest node (lengths of dashed lines) one ends up choosing the node at the minimum distance from the dest.
However, this method can lead to deadlock situations.
Figure 1b illustrates the case when packets are forwarded to a node without neighbors apart from the current node. In the second step the current yellow node choses the node that is at the shortest distance from the dest red node but has no neighbors. In such cases, alternative forwarding strategies such as an Adaptive Greedy-compass Energy-aware Multipath protocol (AGEM) [
18] can be utilized.
Geographic routing algorithms offer a number of advantages, such as simplicity, efficiency, and scalability. Another important advantage of geographic routing is that there is no need to store large routing tables and/or flood the network with route discovery packets. However, nodes’ location information may not always be available in specific environments such as deep woods, indoors, and mountains.
One of the ways how to utilize geographic routing without explicit nodes’ location information is to rely upon the use of virtual coordinates instead of geographic coordinates. To be suitable for this task, virtual coordinates should reflect the position of nodes relative to each other in the virtual graphs similar to the physical world. To be applicable in practice, algorithms for deducing virtual coordinates should be distributed in nature, operating with minimal overhead by relying upon information about the closest proximity of nodes, for example, locations of neighbor nodes within the communications range [
19]. Virtual coordinate systems (VCSs) can be classified into systems that rely upon the use of anchor nodes [
20,
21,
22] and those that do not utilize this information [
23,
24].
Table 1 summarizes the related algorithms according to the anchor involvement. Anchor nodes (or landmarks) are designed to serve as a guide for other nodes in determining their virtual coordinates. A set of anchor nodes can consist of nodes that have information about their geographic location or are assigned according to some rule. In general, the performance of VCSs systems relying upon the anchor nodes is better as compared to those, where this information is not utilized.
In VCS algorithms that utilize anchor nodes, the location of the anchor nodes in the network is of special importance. In [
25], the authors proposed two utilize the voting functions, whose values are assigned to network nodes and define the priority to be declared as anchor nodes. The authors propose two anchor node distribution patterns: (i) uniformly over the network at the maximum distance relative to each other and (ii) along the network boundary. The simulation results demonstrate that the proposed algorithm improves the efficiency of greedy forwarding, preserving the simplicity and high scalability of this routing technique. The authors in [
27] utilized perimeter nodes as anchor ones and considered two cases: (i) when none of the nodes has knowledge about its position and (ii) when some of the nodes have location information. They proceed by proposing geographic routing protocols by replacing geographic coordinates with virtual coordinates. Their study was further continued in [
28], where an approximate solution for the values of virtual coordinates in terms of fixed coordinates of peripheral anchor nodes is proposed.
To find virtual coordinates, it is convenient to represent the network as a graph. Unit disk graph (UDG) models have proven useful in simulating a variety of real-world physics problems. In [
29], UDGs are defined as follows: given
n circles with the same radius in the plane, construct a graph with
n vertices corresponding to
n circles and edges between two vertices if one of the corresponding circles contains the center of the other. The UDG model has been repeatedly used in routing problems [
26,
30].
Summarizing the related work, we note that the anchor-based algorithms proposed to date so far are a good fit for static networks. Although the complexity and execution time of the anchor node assignment algorithm is greatly reduced, this process requires both time and computational resources. In the cited works, anchor nodes are usually distributed along the edge of the network, but due to the nodes’ mobility the edge nodes change, which will require the dynamical reassignment of anchor nodes. The choice of the number of anchor nodes is also not unambiguous. In our paper, we design an algorithm that efficiently utilizes only the information available on the neighboring nodes which solves the described above issue. Specifically, instead of choosing anchor nodes, we employ locally available information and received signal strength (RSS) to calculate the virtual coordinates of the nodes.
3. Requirements for Implementation of the Virtual Coordinate System Algorithm
The algorithm developed in this paper works in a system of virtual coordinates called the Unit Virtual Coordinate System. The algorithm assumes that each node has and regularly updates information about all neighboring nodes. In the case of applying the UVCS to a UAVs swarms, due to radio signal attenuation the distance at which UAVs are able to communicate is limited, so we consider neighbors to be adjacent nodes directly available for communication via a radio interface without any intermediate relay nodes. The name of the system came about by analogy with the unit disk graph [
29], if the maximum distance between directly connected UAVs is normalized to one.
The main objective of the proposed UVCS is to enable a network node to calculate its virtual address based on locally available network knowledge in order to minimize the overhead of distributing information throughout the network. The system works in such a way that network nodes do not need to have access to information obtained from external sources, such as absolute geographic GPS coordinates or cellular infrastructure data.
To maintain proper operation of the system, each node in the network must perform a set of actions independent of the other nodes in the network, i.e., a node makes all decisions locally and only notifies the other nodes of the decisions made. All nodes in the network must perform the same set of actions based on the chosen algorithm. This ensures that the system can operate under dynamic conditions, even when individual nodes in the network are completely isolated. These actions include (shown schematically in
Figure 2):
Constantly wait for signal data packets from other nodes in the network and updating information about them in its database.
Timely removal of information about other nodes in the network from its database if the signal data packet was not received from them for a certain period of time.
Within a given period, recalculate its virtual coordinates based on the collected information about the other nodes of the network since the last recalculation of coordinates (or inclusion in the network).
Within a given period, notify all neighboring nodes of the network about their calculated coordinates, and, if set by the selected algorithm, other necessary data, such as the coordinates of their one-hop neighbors. This action is performed by sending a special broadcast data signal packet containing all the necessary data.
If specified by the selected algorithm, to perform instantaneous processing of signal messages about the subnet merging.
The proposed system allocates and dynamically assigns logical addresses to nodes based on information received from their immediate neighbors, which periodically exchange special broadcast data signal packets, and estimates their distances based on the RSS of the signal packet. The system dynamically adapts to changing network conditions, including network mergers and disconnections, node disconnections, and node mobility. Thus, the network can dynamically create and maintain a topology, based on which the network nodes have the ability to instantly determine the next node (hop) when forwarding a data packet to the destination. It is worth noting that routes are built according to geographic routing based on the information about the location of nodes in the UVCS. In a similar formulation, the problem is solved in [
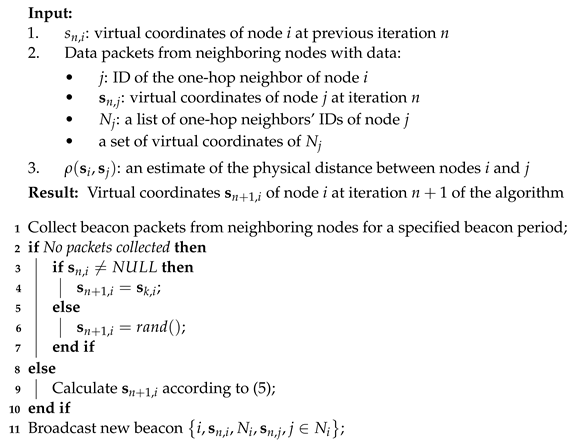
19], however, unlike our model, the GAR algorithm requires information not only about immediate neighbors, the so-called “first handshake” neighbors, but also about neighbors of neighbors, i.e., “second handshake” neighbors. Thus, maintaining a network topology by the GAR algorithm requires a slightly larger amount of signaling traffic and higher overheads. Algorithm 1 shows a single iteration of the UVCS algorithm for a single node. The same algorithm is assumed to run on every node in the considered network indefinitely to support the timely updates of a node’s virtual coordinates, which are required in the case of nodes’ mobility. The number of operations on a node at each iteration of the algorithm is of the order of the number of node’s neighbors and depends on the density of nodes in the network which leads to polynomial computational complexity for the whole network. The low complexity of the algorithm makes it possible to run the algorithm in real time even on embedded devices.
| Algorithm 1: Single iteration of UVCS algorithm. |
![Mathematics 11 00694 i001 Mathematics 11 00694 i001]() |
In the next section, we show the mathematical model underlying our algorithm for assigning or refinement virtual coordinates in the UVCS.
4. Mathematical Model at the Heart of the Algorithm
Consider a UAV swarm represented as a mobile network whose nodes can appear, disappear, and move, and in which two nodes are connected if circles of unit radius around these nodes intersect. Recall that the transmission range, i.e., maximum distance between directly connected UAVs, is limited due to radio signal attenuation and the model construction is normalized to one. The corresponding finite oriented graph is defined as
with set of vertices
, set of edges
, and edge lengths
. The purpose of the algorithm is to find a set of virtual coordinates
, where
,
, such that for all edges
the distance between point
and point
is close to
(
Figure 3). A more precise formulation of the minimization problem will be given later.
Let us introduce the following notation:
: the set of all vertices to which there are edges from node
i;
: the set of vertices from which the edges enter node
j. We also define the distance between points
and
as
When solving the localization problem, we should specify point
in relation to point
in such a way that node
k becomes
far from node
j. Intuitively, it would be good to move the point
to a new position
:
If we average the desired positions of the point
with respect to all the surrounding points
,
, then we obtain
This brings us to the iterative procedure
where
: the parameter determining how drastically the new value
of the vector
will differ from its previous value
[
31]. Iterations (
4) are very similar to the coordinate-wise minimization of some function
with iterations
There are various methods for choosing parameters
and vectors
in (
5) [
32]. The classic approach is the fast descent method, in which the gradient
is taken as a vector
.
In
Appendix A, it is shown that, for the minimization problem of a function,
and with differentiated terms
the gradient
is given by
where
.
An important special case of graph
is the one with symmetric adjacency matrix. Regarding application to a UAVs swarm analysis, this property reflects the features of a connection in the real swarm — if data transfer from node
i to node
j is possible, then it is possible in the opposite direction. In this case, the conditions
are satisfied. For such graphs, (
8) takes the form
For illustration, if
and
in (
6), (
8) have the form of
then Equation (
10) takes the form of
where
are some coefficient,
. One may compare to (
3) with
.
Therefore, the localization problem of obtaining
takes the form of minimization (
7) subject to (
9), (
10).
In the UVCS approach, descending in an iterative procedure (
4) is carried out by cycles in which the number of steps is equal to the number of variables of the minimized function, in our case
. It is also possible to carry out optimization at each step not for individual variables, but for groups of some variables. In our case, those groups are vectors
,
[
33].
To calculate the next approximation, the gradient descent method suggests
where
is some constant,
is a gradient of the function
by the variable
, i.e,
The convergence of iterative procedure (
13) is defined by the Lipschitz condition [
34]. The parameter
should be chosen in such a way that after the replacement
of
the new value of the function
increases drastically.
Finally, in the UVCS approach the gradient descent algorithm itself is as follows.
By carrying out n cycles, we have the following.
Vectors remain unchanged while we minimize the function by the vector .
We obtain the approximation , where —the optimal value of the vector .
Vectors remain unchanged while we minimize the function by the vector .
We obtain the approximation , where —is the optimal value of the vector .
…
Vectors remain unchanged while we minimize the function by the vector .
We obtain the approximation , where — is the optimal value of the vector .
After N steps, where each step corresponds to vector , , the -th cycle is finished. The process is repeated for until the stopping condition is satisfied either by the execution time or by an achieved accuracy.
As a result of solving the localization problem for each vertex
, we obtain the values
of virtual coordinates, that form the desired set of virtual coordinates
for UAVs in the swarm. Note that the representation
allows us to work with it by standard routing methods. In
Section 5, we define the performance metrics and in
Section 6 evaluate the performance of the proposed UVCS approach in comparison with Greedy Forwarding Geographic Routing (Geo) algorithm, Gradient Assisted Routing (GAR) algorithm [
19], and Dijkstra algorithm as a benchmark.
5. Performance Metrics
The development of metrics for evaluation of the effectiveness of the developed UVCS approach for self-organization and topology support in a drone swarm is a separate task, that has two aspects. On the one hand, positioning accuracy can be evaluated, while, on the other hand, the ability to maintain swarm connectivity should be estimated. The peculiarity is that graphs built on the known physical coordinates and on the calculated virtual coordinates are isomorphic [
35,
36]. It should also be taken into account that different routing algorithms in the same coordinate system can give different results in terms of the route characteristics.
A routing algorithm can be formally described by the rule for choosing the first vertex on the path from vertex i to vertex k. Here , , where is the set of vertices containing edges originating from vertex i including a vertex i itself.
For the Geo algorithm the choice of node
follows the principle
This section describes several performance metrics: topological similarity index, routing similarity index, number of discovered paths, and average discovered path length. All metrics depend on the routing algorithm that works on the top of the coordinate system—either physical or virtual.
The Geo routing algorithm (
15) is used by default for all metrics, and we also use Dijkstra’s algorithm for the shortest path finding as a benchmark to evaluate the last two metrics—number and mean length of discovered paths.
The
topological similarity index compares the degree to which the virtual graph replicates the physical graph in terms of distances between vertices. We calculate by (
1) the distance
in all pairs
of vertices, regardless of their connectivity, and, using Pearson’s correlation coefficient [
37], compare the pairwise distances between them.
The next metrics of interest are a group of routing metrics—routing similarity index, number of discovered paths, and average discovered path length.
The
routing similarity index is based on application of the apparatus of closed queuing networks and is carried out in two steps. The first step is to develop the stochastic routing matrix
of transition probabilities,
. Assuming that, from each node, a customer equiprobably chooses one of the adjacent nodes from
, we obtain
Then, the transition probability from node
i to node
j,
, is as the following:
In the second step, we solve the balance equations
and obtain a vector
with the components
representing the proportion of time spent by the customer in node
or the frequency of usage of node
i while routing. As a measure of the difference between the two routing schemes the following metric can be considered:
In case
is a vector related to the physical graph, and
is related to the virtual one, metric (
19) shows the degree of similarity of routing in the physical and virtual graphs. The approach (
19) can also be used to evaluate the degree of similarity of two routing algorithms.
Finally, we define two more routing metrics—the number of paths and the average path length metrics. They show how many paths are found and how many edges they contain on average at a given time stamp according to the given routing scheme.
6. Numerical Results
In this section, we evaluate the performance of the proposed UVCS virtual coordinate system on the top of the Geo routing algorithm based on (i) topological metrics, describing the similarity between virtual and physical topology, and (ii) routing metrics, reflecting the routing performance. We also compare the proposed approach to other routing schemes such as the Gradient Assisted Routing (GAR) algorithm [
19] with virtual coordinates, as well as the Geo routing algorithm with known physical coordinates and the Dijkstra algorithm as a benchmark.
6.1. Metrics of Interest and Scenario
As the primary indicator of the overall similarity between the network topology and the virtual one, we utilize the so-called topology similarity index. This index is defined as the Pearson correlation coefficient [
37] between pairwise distances in the virtual and physical topology. For the routing performance, we provide a set of different metrics that, when considered together, propose deep insights into the developed approach’s performance by assessing how close it is to the perfect case with full knowledge based on the Dijkstra algorithm. These metrics include (a) path similarity index that shows how close are chosen routes to those detected by the Dijkstra algorithm, (b) total number of discovered routes, and (c) average length of discovered routes, reflecting the ability of the routing protocol to discover paths in a network. Finally, we also compare the proposed approach to the Gradient Assisted Routing (GAR) algorithm specified in [
19].
To perform the comparison, we consider a wireless stationary network with a maximum of 50 randomly located nodes. Nodes appear one by one with a small delay (approximately five time steps) until all 50 nodes are online. At every given time instant, all currently online nodes organize a fully connected graph. Once all nodes are online, some additional time is given for the UVCS algorithm to converge.
6.2. Topological Metric
We start with the topological metric in
Figure 4 illustrating the topology similarity index as a function of the successive algorithm time steps. It can be observed that the GAR algorithm provides a closer overall topology resemblance to the original physical graph, while both GAR and the proposed UVCS approaches improve the virtual topology in time. We specifically emphasize the ability of the proposed UVCS algorithm to converge much faster—in less than 100 steps. The Geo routing algorithm based on physical coordinates is not included in that figure, as it relies on the real nodes coordinates, resulting in the one-to-one similarity.
6.3. Routing Metrics
Recall that the main aim of the proposed UVCS algorithm is to perform efficient routing between possibly mobile nodes. At the same time, observe that even perfect topology matching does not guarantee that the routing performance will be similar for different routing algorithms. For this reason, we now proceed to investigate the routing performance of the proposed UVCS approach using different routing metrics including practical geographical routing protocols.
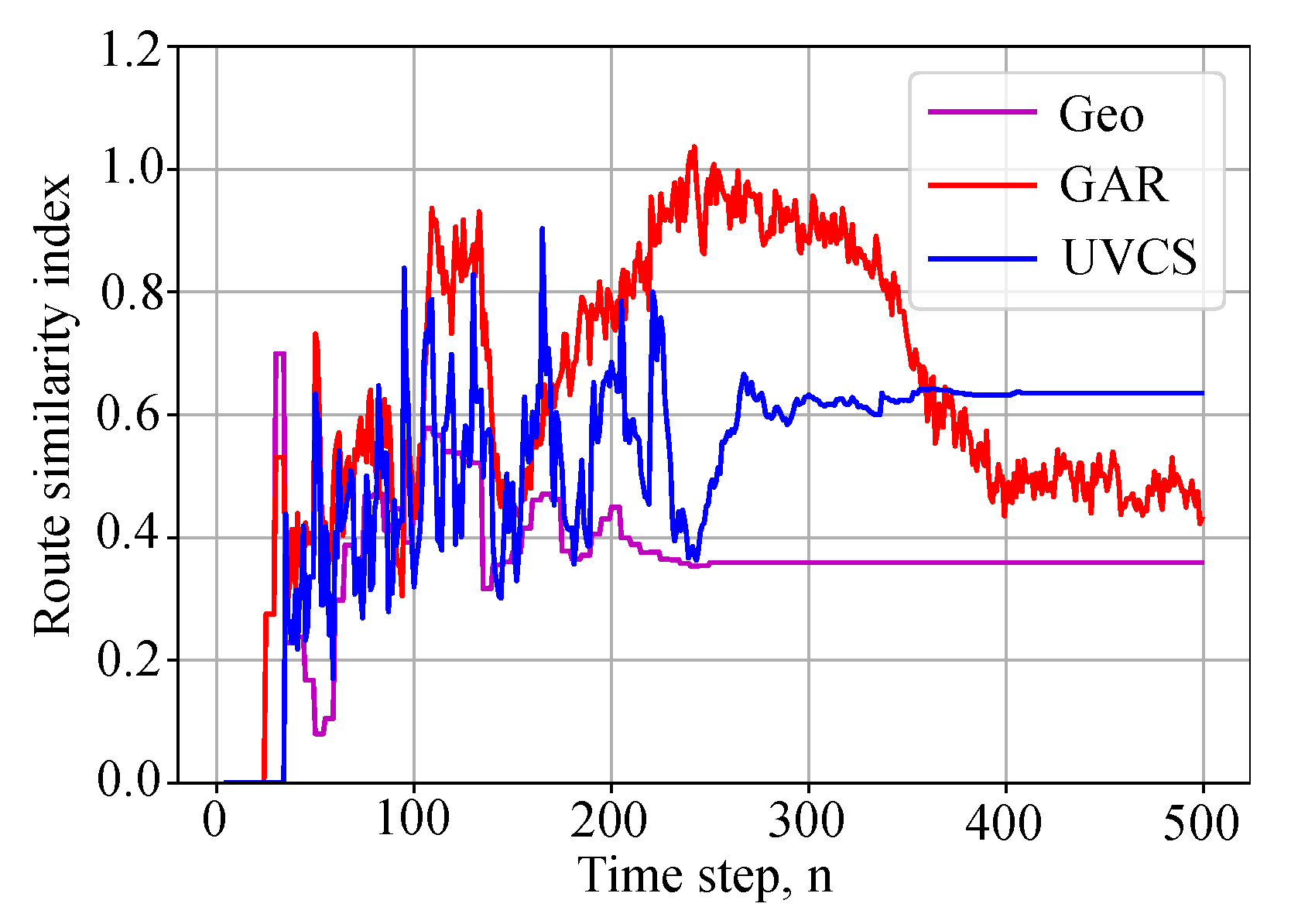
Here, we start with the path similarity index provided in
Figure 5 and show how fast the routes may converge to the shortest ones based on the Dijkstra algorithm. Recall that the closer the value is to 0 the better the match in terms of selected paths is. Here, we can see that the proposed algorithm again converges to its final solution much faster, even though the similarity index is not as good as for the GAR or Geo algorithms—0.6 against 0.5 and 0.4, respectively.
One of the weakest points of the GAR, originally proposed in [
19], is a low number of total discovered paths in the network. Even though the proposed UVCS algorithm does not show the best performance in terms of topology similarity metric,
Figure 6 shows that the total number of discovered routes is higher compared to the GAR algorithm. This number is even comparable and is getting very close to the Geo algorithm that relies on external information for routing. To achieve these performance gains in terms of the number of discovered paths, the proposed algorithm in some cases finds longer, less optimal routes to the destination, shown in
Figure 7, which may be considered a minor drawback for delay critical applications. However, recalling that the UVCS does not rely on any external positioning information, unlike the original Geo algorithm, this slight increase in average path length enables a much higher number of discovered paths together with a faster convergence time.
7. Conclusions
This paper proposes an approach to organize and maintain the topology of a distributed network. The proposed UVCS algorithm is designed to find the coordinates of a network node, operating only with local information available at the node itself. One of the advantages of the UVCS is its minimal input information requirements. Further, the virtual coordinates can be used to implement geographic routing in the network. In the performance evaluation, we assessed the UVCS by topological and routing metrics. Numerical analysis showed that the virtual coordinates found with the UVCS algorithm are close to the physical coordinates. Secondly, the UVCS algorithm outperforms all known algorithms in terms of the total number of discovered paths, which can be critical to maintaining the connectivity of a UAV swarm. However, the main advantage of the UVCS is its fast convergence. In future, the problem can be developed in the direction of building virtual coordinate systems with anchor nodes, while the number and rule for assigning nodes as an anchor can become the subject of research to maintain a balance is between positioning accuracy and overheads due to the amount of service traffic when implementing the algorithm. Analysis of data transmission delay depending on the route scheme is also a part of this research.