Securing an Authenticated Privacy Preserving Protocol in a Group Signature Scheme Based on a Group Ring
Abstract
1. Introduction
2. Literature Review
2.1. Our Contribution
- We incorporate the two hard problems in group theory, which are the DLP and IFP. We modify and extend the existing DLP and IFP to define a new problem, DLP with factorization (DLPF), where the underlying structure is based on group rings. We will also analyze the parameters that are suitable to design an efficient and secure DLPF over a group ring;
- We implement the new problem in DLPF to construct a secure and efficient group signature scheme that simultaneously has the appealing qualities of message trustworthiness, privacy, and accountability. The fundamental advantage of group signatures over digital signatures is that only one key pair must be stored by the user, eliminating the need to maintain many anonymous credentials beforehand;
- We present an analysis that demonstrates how our protocol delivers an effective security level, system robustness, and performance efficiency. Our protocol is then executed using MATLAB R2021b. This computational analysis shows the applicability and usability of our work in practical applications.
2.2. Organization
3. Preliminaries
3.1. Discrete Logarithm Problem with Factorization (DLPF)
3.2. Security and Complexity of DLPF
3.2.1. Hardness of DDHPGR
3.2.2. Hardness of DLPF in Group Ring
4. System and Network Model
4.1. Entities
- Trusted Party. We depend on a trusted party () to manage user admittance into the system and revoke the malicious user. It is responsible for the issuing and administration of credentials. A will only disclose a misbehaving user’s identification if they are discovered to be malicious. Furthermore, the verifies and assesses the reliability of the signature;
- Users. Users in our scheme consist of a sender () to generate and forward the signature and a receiver that utilizes the verified signature;
- Adversaries. The two types of adversaries are insiders and outsiders. An outside adversary is a malicious entity that does not possess all the valid credentials and authorization to access the network. An inside adversary, on the other hand, is a malicious participant who is genuine and in possession of all necessary credentials.
4.2. Comprehensive Framework
- Registration Phase
- Step 1: submits a request to the in order to obtain a credential in order to access the network;
- Step 2: creates, distributes, and keeps credentials in its database to verify ’s authenticity within the network;
- Step 3: Following successful authentication, returns the credential to ;
- Broadcast Phase
- Step 4: produces a signature and transmits it to the ;
- Verification Phase
- Step 5: measures the signature’s validity;
- Step 6: sends to the validated signature after a successful verification;
- Step 7: validates the signature.
- Revocation Phase
- Step 8: If encounters any wrongdoing during its interaction with , they may lodge a report with the ;
- Step 9: The evaluates the validity and trustworthiness of the information after receiving reports before considering eliminating from the network.
5. Group Signature Scheme over Group Ring
5.1. System Initialization
- for all and;
- For all , and , it holds that .
5.2. Entity Registration
- Step 1: self-generates a key pair ) in order to join the network. requests validation of its self-generated public key ( at time from the while preserving its secret key ( undisclosed. Assume , and the public key is for . Then, using the private key for where is the set of integers modulo that are relatively large primes, a user computes its tracing information . The sender sends) to;
- Step 2: performs an authentication check by checking. Upon successful verification, generates a signature on . sends to . then stores) into its local database;
- Step 3: initially authenticates the sender’s validity by verifying the signature on . The has a key pair denoted by ( where the selects a randomly chosen group element from ∈ . performs the computation and where is a random matrix and element of . Upon successful computation, distributes to the legitimate sender. A sender verifies that to validate the signature. If the check is successful, the sender has successfully registered with and can employ as a group certificate over the network. The sender may generate a signature for any message using their .
5.3. Signature Generation
- Step 4: generates the message (), where Message ID is denoted as which defines the type of message; is the validity period of signature generation; and user position is indicated by . Let be the user’s group identity, allowing one to determine which group the user belongs to.
- Distribute the at random to verify that the signer is a legitimate member of the group while maintaining network anonymity. computes for a randomly chosen matrix;
- Generate a random for a group member where and produce a message link-identifier ;
- Set up the group signature on using the private key in and .
- Set up at random for an integer where where is a substantial prime number within the set of integers modulo ;
- Compute and ;
- Obtain a challenge of and where ;
- Response to the challenge with and output the group signature as of .
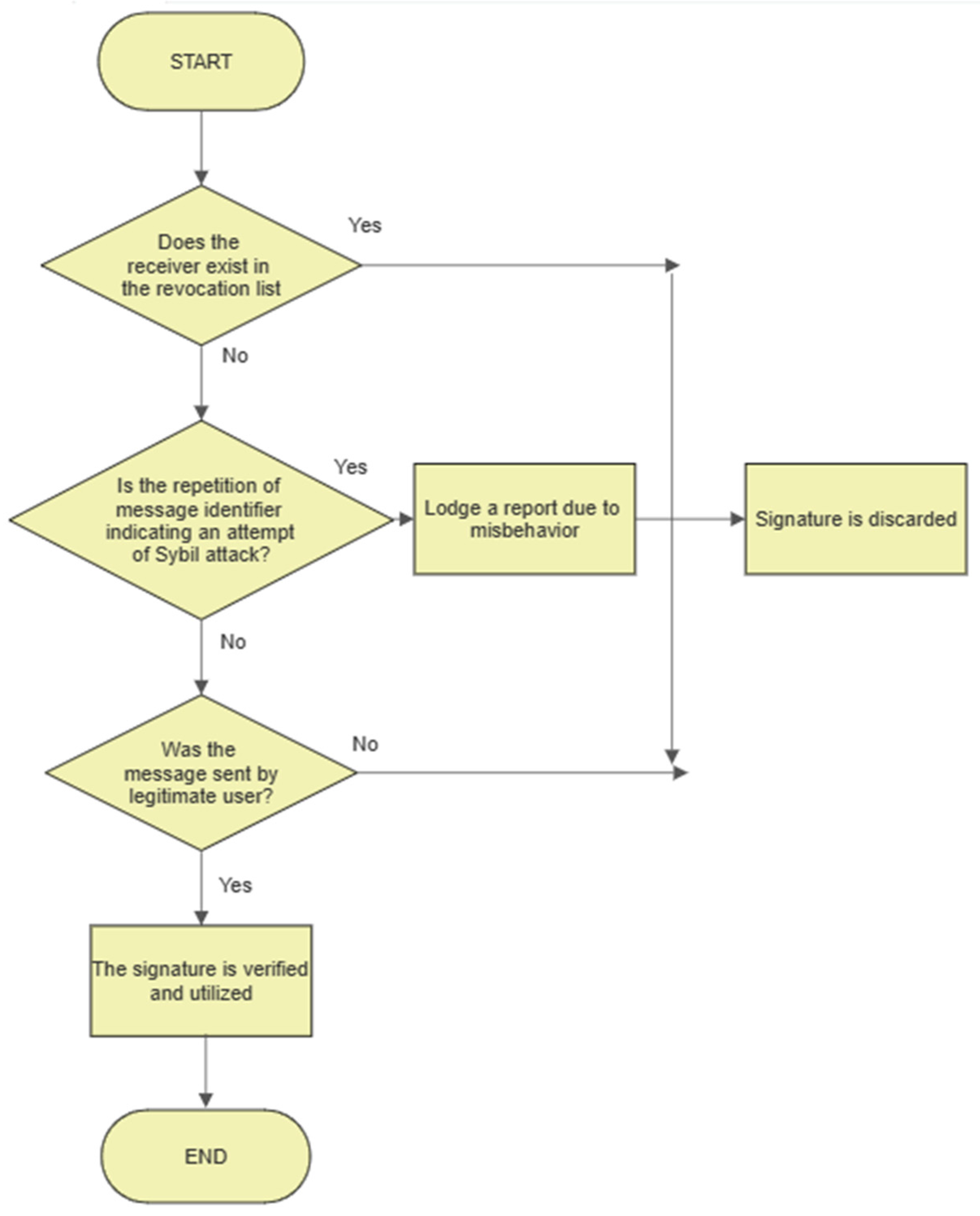
5.4. Signature Verification
- Step 5: The validity of the safety messages is assessed by . Since a replay of the same shows that the same messages were generated by the same user several times, rejects signatures that contain the same component of .
- Step 6: For message verification:
- Step 7: validates the message’s content by examining the . The signature is regarded as trustworthy if both message verification checks succeed and is valid at that time.
5.5. Signature Revocation
- Step 8: Upon detecting malicious behavior in the network, submits a revocation report to the .
- Step 9: To revoke misbehaving , the verifies the validity of . We observe that possesses some trapdoor knowledge of . The searches its local database to connect with ’s identification for revocation and law enforcement purposes.
| The sequential flow of our proposed scheme |
| Setup: • • System parameters: . Registration phase: Key Generation: • S’s public key isfor ; • S’s private key is for ; • TP’s keypair is . User computes TP verifies: . TP computes: , where is a random matrix and element of . S verifies: . Signing Phase: • The message format is: . • The user executes the following computation in order to generate a message-linkable signature: • Randomize where computes:
• Generate the group signature using in and . • To establish a group signature, computes: • Randomly choses ; • Compute commitments and ; • Acquire a challenge according to the computed commitments ; • Response to the challenge with ; • Output the group signature as of . Broadcast: . Verification Phase: • For checking purposes: TP verifies:
• validates by examining the . Revocation Phase: • If encounters misbehavior; • searches its local database to connect with ’s identification for revocation. |
6. Security and Performance Evaluation
6.1. Security Evaluation
- Trustworthiness: A message must be transmitted by a reliable user in its unaltered state for it to be considered reliable (sender authenticity and message integrity). Furthermore, the message conveyed must accurately depict the incident. Additionally, there is a significant probability that the event has already occurred (message truthfulness). Additionally, a minimal percentage of inside adversaries should be tolerable for the system (system robustness).
- Privacy: If the sending user behaves properly, its identification should be kept private (anonymity). Furthermore, if the same sender produces two distinct messages, they cannot be connected to one another (unlinkability).
- Accountability: Users that exhibit improper behavior can be traced. In addition, they must prove non-repudiation, or the assertion that they are the message’s sender (non-repudiation). The violating user’s access to the network can then be revoked (revocation).
6.2. Robustness Analysis
- Impersonation attacks. By adopting their identities, an adversary can manipulate trustworthy communications by disguising themselves as other genuine users;
- Man-in-the-middle attacks. The messages transmitted by the user to the trusted party, who believes they are directly communicating with one another, are eavesdropped on, intercepted, and possibly modified by an adversary.
- Robustness against Impersonation Attacks
- Impersonation attack against outside adversaries.
- Impersonation attack against inside adversaries.
- An adversary randomly chooses an integer for a random value and let ;
- The signing protocol for the message is executed;
- A fake message, is announced.
- 2
- Robustness against man-in-the-middle attacks
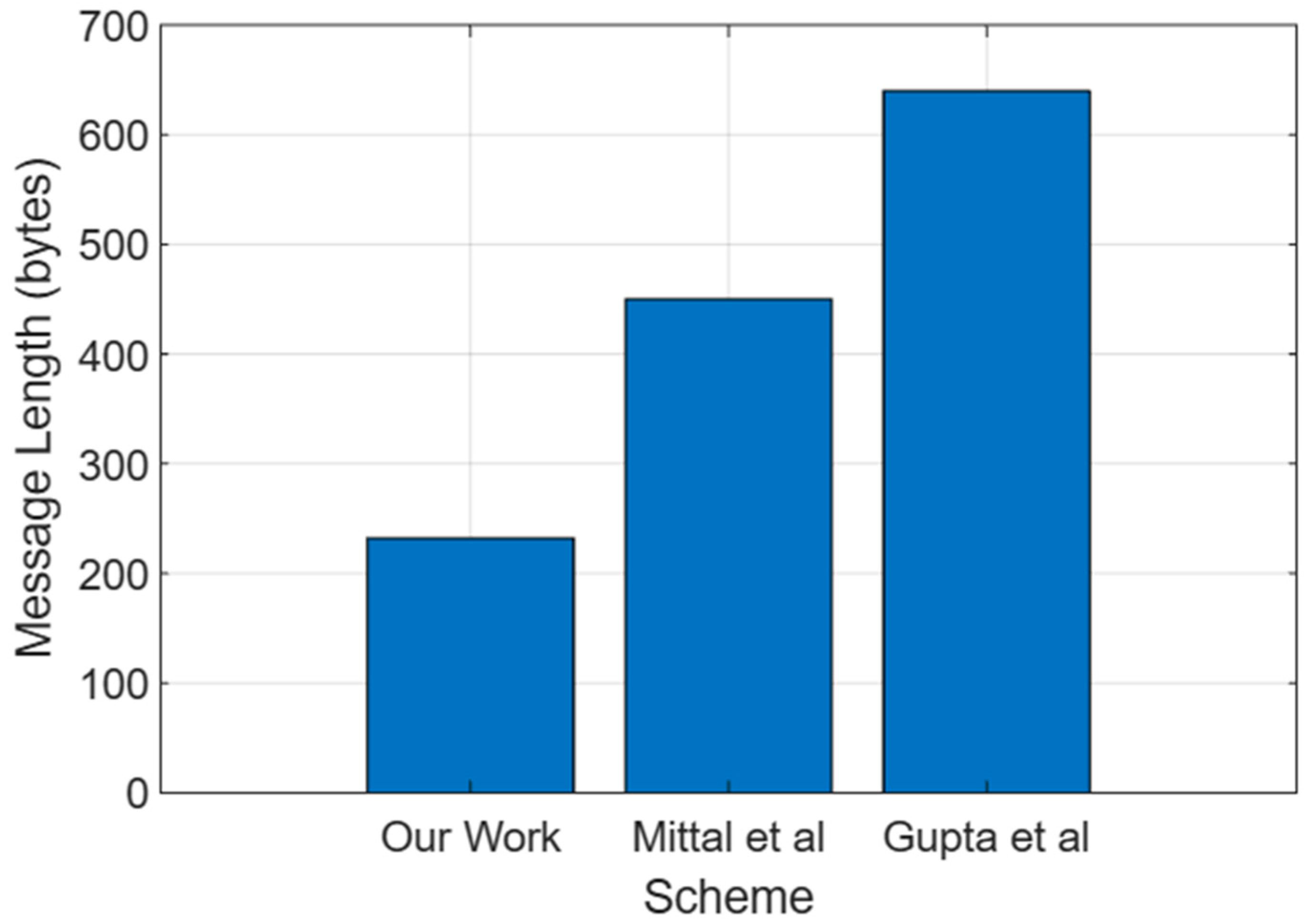
6.3. Performance Analysis
6.4. Simulation
- Message latency with respect to user count: the time needed to carry out cryptographic procedures to authenticate broadcasted messages;
- Message loss ratio with respect to number of users: since there are more revoked users on the ’s database, message delivery times are becoming slower.
7. Conclusions
Author Contributions
Funding
Data Availability Statement
Acknowledgments
Conflicts of Interest
References
- Venkatraman, S.; Venkatraman, R. Big data security challenges and strategies. AIMS Math. 2019, 4, 860–879. [Google Scholar] [CrossRef]
- Song, C.; Gu, X.; Wang, L.; Liu, Z.; Ping, Y. Research on identity-based batch anonymous authentication scheme for VANET. KSII Trans. Internet Inf. Syst. 2019, 13, 6175–6189. [Google Scholar]
- Emura, K.; Hayashi, T. Road-to-user communications with time-dependent anonymity: A lightweight construction and its experimental results. IEEE Trans. Veh. Technol. 2017, 67, 1582–1597. [Google Scholar] [CrossRef]
- Amir, N.A.S.; Malip, A.; Othman, W.A.M. Securing Anonymous Authenticated Announcement Protocol for Group Signature in Internet of Users. KSII Trans. Internet Inf. Syst. 2020, 14, 4573–4594. [Google Scholar]
- Amir, N.A.S.; Othman, W.A.M.; Wong, K.B. Efficient Privacy Preserving Anonymous Authentication Announcement Protocol for Secure Vehicular Cloud Network. KSII Trans. Internet Inf. Syst. 2023, 17, 1450–1470. [Google Scholar]
- Brickell, E.; Camenisch, J.; Chen, L. Direct anonymous attestation. In Proceedings of the 11th ACM Conference on Computer and Communications Security, Washington, DC, USA, 25–29 October 2004; pp. 132–145. [Google Scholar]
- Chaum, D.; Van, H.E. Group signatures (PDF). In Advances in Cryptology—EUROCRYPT’91: Workshop on the Theory and Application of Cryptographic Techniques, Brighton, UK, 8–11 April 1991; Springer: Berlin/Heidelberg, Germany, 1991; pp. 257–265. [Google Scholar]
- Koblitz, N. A Course in Number Theory and Cryptography; Springer Science & Business Media: Berlin/Heidelberg, Germany, 1994; Volume 114, pp. 1–10. [Google Scholar]
- Landau, E. Elementary Number theory. Am. Math. Soc. 2021, 125, 3. [Google Scholar]
- Yanlin, Q.; Xiaoping, W. New digital signature scheme based on both ECDLP and IFP. In Proceedings of the 2009 2nd IEEE International Conference on Computer Science and Information Technology, Beijing, China, 8–11 August 2009; pp. 348–351. [Google Scholar]
- Harn, L. Public-key cryptosystem design based on factoring and discrete logarithms. IEEE Proc. Comput. Digit. Tech. 1994, 141, 193–195. [Google Scholar] [CrossRef]
- Poulakis, D. A public key encryption scheme based on factoring and discrete logarithm. J. Discret. Math. Sci. Cryptogr. 2009, 12, 745–752. [Google Scholar] [CrossRef]
- Grover, L.K. Quantum mechanics helps in searching for a needle in a haystack. Phys. Rev. Lett. 1997, 79, 325. [Google Scholar] [CrossRef]
- Proos, J.; Zalka, C. Shor’s discrete logarithm quantum algorithm for elliptic curves. arXiv 2003, arXiv:quant-ph/0301141. [Google Scholar] [CrossRef]
- Manzoor, E.; Shah, N.B. Uncovering latent biases in text: Method and application to peer review. arXiv 2020, arXiv:2010.15300. [Google Scholar] [CrossRef]
- Rötteler, M. Quantum algorithms: A survey of some recent results. Inform. Forsch. Und Entwickl. 2006, 21, 3–20. [Google Scholar] [CrossRef]
- Greenwell, R.N. Polynomial-time algorithms for prime factorization and discrete logarithms on a quantum computer. Coll. Math. J. 2000, 31, 70. [Google Scholar]
- Alvarez, R.; Martinez, F.M.; Vicent, J.F.; Zamora, A. A new public key cryptosystem based on matrices. WSEAS Inf. Secur. Priv. 2007, 3639. Available online: https://dl.acm.org/doi/abs/10.5555/1981242.1981247 (accessed on 11 September 2023).
- Climent, J.J.; Navarro, P.R.; Tortosa, L. Key exchange protocols over noncommutative rings. The case of End (Zp × Zp2). Int. J. Comput. Math. 2012, 89, 1753–1763. [Google Scholar] [CrossRef][Green Version]
- Stickel, E. A new public-key cryptosystem in non-abelian groups. In Proceedings of the Thirteenth International Conference on Information Systems Development, Vilnius Technika, Vilnius, Lithuania, 9–11 September 2004; pp. 70–80. [Google Scholar]
- Ezhilmaran, D.; Muthukumaran, V. Key exchange protocol using decomposition problem in near-ring. Gazi Univ. J. Sci. 2016, 29, 123–127. [Google Scholar]
- Menezes, A.J.; Wu, Y.H. The discrete logarithm problem in GL (n, q). Ars Comb. 1997, 47, 23–32. [Google Scholar]
- Cheng, Q.; Zhang, J.; Zhuang, J. LWE from non-commutative group rings. Des. Codes Cryptogr. 2022, 90, 239–263. [Google Scholar] [CrossRef]
- Kahrobaei, D.; Koupparis, C.; Shpilrain, V. Public key exchange using matrices over group rings. Groups-Complexity-Cryptology 2013, 5, 97–115. [Google Scholar] [CrossRef]
- Rososhek, S.K. Cryptosystems in automorphism groups of group rings of Abelian groups. J. Math. Sci. 2008, 154, 386–391. [Google Scholar] [CrossRef]
- Kahrobaei, D.; Koupparis, C.; Shpilrain, V. A CCA secure cryptosystem using matrices over group rings. Contemp. Math. Amer. Math. Soc. 2015, 633, 73–80. [Google Scholar]
- Koupparis, C.M. Non-Commutative Cryptography: Diffie-Hellman and CCA Secure Cryptosystems Using Matrices over Group Rings and Digital Signatures; City University of New York: New York, NY, USA, 2012. [Google Scholar]
- Inam, S.; Ali, R. A new ElGamal-like cryptosystem based on matrices over group ring. Neural Comput. Appl. 2018, 29, 1279–1283. [Google Scholar] [CrossRef]
- Zhang, J.; Yang, Y.J.; Li, Y.P. A New Key Exchange Protocol Based on Infinite Non-Abelian Groups. Secur. Commun. Netw. 2022, 2022, 7942353. [Google Scholar] [CrossRef]
- Lanel, G.H.J.; Jinasena, T.M.K.K.; Welihinda, B.A.K. Cryptographic Protocols using Semidirect Products of Finite Groups. Int. J. Comput. Sci. Netw. Secur. 2021, 21, 17–27. [Google Scholar]
- Pandey, A.; Gupta, I. A new undeniable signature scheme on general linear group over group ring. J. Discret. Math. Sci. Cryptogr. 2022, 15, 1261–1273. [Google Scholar] [CrossRef]
- Goel, N.; Gupta, I.; Dubey, M.K.; Dass, B.K. Undeniable signature scheme based over group ring. Appl. Algebra Eng. Commun. Comput. 2016, 27, 523–535. [Google Scholar] [CrossRef]
- Magyarik, R.; Wagner, N.R. A public key cryptosystem based on the word problem. In Workshop on the Theory and Application of Cryptographic Techniques CRYPTO 1984: Advances in Cryptology; Springer: Berlin/Heidelberg, Germany, 1985; Volume 196, pp. 19–36. [Google Scholar]
- Birget, J.C.; Magliveras, S.S.; Sramka, M. On public key cryptosystems based on combinatorial group theory. Tatra Mt. Math. Publ. 2006, 33, 137–148. [Google Scholar]
- Anshel, I.; Anshel, M.; Goldfeld, D. An algebraic method for public-key cryptography. Math. Res. Lett. 1999, 6, 287–291. [Google Scholar] [CrossRef]
- Ko, K.H.; Lee, S.J.; Cheon, J.H.; Han, J.H.; Kang, J.S.; Park, C. New public-key cryptosystem using braid groups. In Proceedings of the Advances in Cryptology—CRYPTO 2000: 20th Annual International Cryptology Conference, Santa Barbara, CA, USA, 20–24 August 2000; pp. 166–183. [Google Scholar]
- Kubo, J. The dihedral group as a family group. In Quantum Field Theory and Beyond; World Science Publication: Singapore, 2008; pp. 46–63. [Google Scholar]
- Cha, J.C.; Ko, K.H.; Lee, S.J.; Han, J.W.; Cheon, J.H. An efficient implementation of braid groups. Lect. Notes Comput. Sci. 2001, 2248, 144–156. [Google Scholar]
- Anshel, I.; Anshel, M.; Goldfeld, D. Non-abelian key agreement protocols. Discret. Appl. Math. 2003, 130, 3–12. [Google Scholar] [CrossRef]
- Dehornoy, P. Braid-based cryptography. AMS Ebooks Contemp. Math. 2004, 360, 1–29. [Google Scholar]
- Anshel, I.; Anshel, M.; Goldfeld, D. A linear time matrix key agreement protocol over small finite fields. Appl. Algebra Eng. Commun. Comput. 2006, 17, 195–203. [Google Scholar] [CrossRef]
- Paeng, S.H.; Ha, K.C.; Kim, J.H.; Chee, S.; Park, C. New public key cryptosystem using finite non abelian groups. In Advances in Cryptology-CRYPTO of Lecture Notes in Computer Science; Springer: Berlin/Heidelberg, Germany, 2001; pp. 470–485. [Google Scholar]
- Cao, Z.; Dong, X.; Wang, L. New public key cryptosystems using polynomials over noncommutative rings. J. Cryptol. IACR 2007, 9, 1–35. [Google Scholar]
- Reddy, V.; Gsgn, A.; Reddy, V.R.; Mokkala, P. New digital signature scheme using polynomials over noncommutative groups. Int. J. Comput. Sci. Netw. Secur. 2008, 8, 245–250. [Google Scholar]
- Mittal, G.; Kumar, S.; Kumar, S. A quantum secure ID-based cryptographic encryption based on group rings. Sādhanā 2022, 47, 1–16. [Google Scholar] [CrossRef]
- Mittal, G.; Kumar, S.; Narain, S.; Kumar, S. Group ring based public key cryptosystems. J. Discret. Math. Sci. Cryptogr. 2022, 25, 1683–1704. [Google Scholar] [CrossRef]
- Kumar, S.; Mittal, G.; Kumar, S. Digital signature schemes based on group ring. SN Comput. Sci. 2022, 3, 398. [Google Scholar] [CrossRef]
- Passman, D.S. The Algebraic Structure of Group Rings; Courier Corporation: Chelmsford, MA, USA, 2011. [Google Scholar]
- Hoffstein, J.; Pipher, J.; Silverman, J. An Introduction of Mathematical Cryptography; Springer: New York, NY, USA, 2008. [Google Scholar]
- Eftekhari, M. A Diffie–Hellman key exchange protocol using matrices over noncommutative rings. Group Complex Cryptol. 2012, 4, 167–176. [Google Scholar] [CrossRef]
- Ogundoyin, S.O. An autonomous lightweight conditional privacy-preserving authentication scheme with provable security for vehicular ad-hoc networks. Int. J. Comput. Appl. 2020, 42, 196–211. [Google Scholar] [CrossRef]
- Wu, Q.; Domingo-Ferrer, J.; Gonzalez’-Nicolas, U. Balanced trustworthiness, safety and privacy in user-to-user communications. IEEE Trans. Veh. Technol. 2010, 59, 559–573. [Google Scholar]
- Mei, Q.; Xiong, H.; Zhao, Y.; Yeh, K.H. Toward blockchain-enabled IoV with edge computing: Efficient and privacy-preserving vehicular communication and dynamic updating. In Proceedings of the 2021 IEEE Conference on Dependable and Secure Computing (DSC), Fukushima, Japan, 30 January–2 February 2021; pp. 1–8. [Google Scholar]
- Menezes, A. An introduction to pairing-based cryptography. Recent Trends Cryptogr. 2009, 477, 47–65. [Google Scholar]
- Kaiwartya, O.; Abdullah, A.H.; Cao, Y.; Altameem, A.; Prasad, M.; Lin, C.; Liu, X. Internet of users: Motivation, layered architecture, network model, challenges, and future aspects. IEEE Access 2016, 4, 5356–5373. [Google Scholar] [CrossRef]

| Security Objective | Security Component | Gupta et al. [31] | Mittal et al. [45] | Our Work |
|---|---|---|---|---|
| Trustworthiness | Authenticity of sender | / | / | / |
| Message integrity | / | / | / | |
| Message origin authentication | X | X | / | |
| Privacy | Anonymous | / | / | / |
| Unlikability | X | / | / | |
| Accountability | Traceability | / | / | / |
| Non repudiate | / | X | / | |
| Revocability | X | X | / |
| Symbol | Description | Execution Time (ms) |
|---|---|---|
| Bilinear pairing operation | 5.5852 | |
| Scalar multiplications in | 0.817 | |
| General hash function operation | 0.0012 | |
| Modular multiplication in | 0.0119 |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2023 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Amir, N.A.S.; Othman, W.A.M.; Wong, K.B. Securing an Authenticated Privacy Preserving Protocol in a Group Signature Scheme Based on a Group Ring. Mathematics 2023, 11, 3918. https://doi.org/10.3390/math11183918
Amir NAS, Othman WAM, Wong KB. Securing an Authenticated Privacy Preserving Protocol in a Group Signature Scheme Based on a Group Ring. Mathematics. 2023; 11(18):3918. https://doi.org/10.3390/math11183918
Chicago/Turabian StyleAmir, Nur Afiqah Suzelan, Wan Ainun Mior Othman, and Kok Bin Wong. 2023. "Securing an Authenticated Privacy Preserving Protocol in a Group Signature Scheme Based on a Group Ring" Mathematics 11, no. 18: 3918. https://doi.org/10.3390/math11183918
APA StyleAmir, N. A. S., Othman, W. A. M., & Wong, K. B. (2023). Securing an Authenticated Privacy Preserving Protocol in a Group Signature Scheme Based on a Group Ring. Mathematics, 11(18), 3918. https://doi.org/10.3390/math11183918