Abstract
Smart home environments are a vital component of the larger ecosystem within smart cities, aiming to revolutionize residential living through the integration of Internet of Things (IoT) devices and advanced technologies. However, ensuring robust security and preserving privacy in these interconnected ecosystems present significant challenges. During the monitoring and controlling tasks in the smart home environment, diverse commands are exchanged between the IoT device and the user over the public Internet. The public Internet is open and vulnerable to various security attacks, which can corrode the monitoring and controlling operation of the smart home. In addition, conventional security algorithms are inappropriate for IoT devices deployed in the smart home. However, various pernicious security attacks are equally efficacious in the resource-limited smart home environment. Thus, various authenticated encryption schemes are proposed to enable security services in resource-constricted smart home environments. This paper presents a lightweight and efficient authentication framework for a smart home environment by leveraging the features of an authenticated encryption scheme and the hash function called “ESCI-AKA”. ESCI-AKA checks the authenticity of the user at the local device and exchanges three messages among the user, gateway, and smart embedded device for establishing a secure channel for indecipherable communication by setting a session key. In addition, we corroborate the security of the established session key through the random oracle model and informal security analysis. Moreover, the Scyther tool is employed for the security validation of ESCI-AKA. Finally, the performance comparison of ESCI-AKA and other eminent security frameworks explicates that ESCI-AKA requires low computational and communication costs while providing robust security features.
MSC:
94A60; 68P25
1. Introduction
The Internet of Things (IoT) has emerged as a crucial enabler in the advancement of smart cities. These cities strive to leverage technological innovations to improve urban living standards, promote sustainability, and enhance overall efficiency. IoT devices and sensors deployed throughout a city enable the collection, analysis, and utilization of vast amounts of data to improve various aspects of urban life [1,2]. In a smart home, IoT devices such as thermostats, lighting systems, security cameras, door locks, appliances, and entertainment systems are interconnected and can be controlled remotely through a central hub or a mobile application. These devices can communicate with each other, share data, and respond to user commands or environmental conditions, creating an interconnected and intelligent living environment [3].
The implementation of smart home technologies necessitates significant attention to security and privacy concerns, while smart homes endeavor to improve urban living through the employment of state-of-the-art technologies, they also introduce potential risks related to data security and privacy breaches [4]. Smart homes yield extensive amounts of data via sensors, cameras, and other connected IoT devices. To safeguard against unauthorized access, data breaches, and the misuse of sensitive information, it is essential to employ robust data security measures. This includes implementing strong encryption, authentication mechanisms, and access controls.
In Figure 1, we can observe a smart home setup, enabling remote communication between the user and resource-constrained IoT devices present within the premises. The user has the capability to send diverse command and control instructions to accomplish various tasks within the smart home environment. However, it is essential to address potential security risks. The command and control information transmitted through a public communication channel is exposed to potential security vulnerabilities. Consequently, it becomes crucial to implement authenticated key agreement (AKA) mechanisms to safeguard the confidentiality of information [5]. By employing such mechanisms, the communicated command and control information can be protected, ensuring that only authorized individuals or entities can access sensitive data.
Figure 1.
Smart home environment.
Several AKA frameworks have been proposed to establish secure and encrypted communication within the smart home environment. Despite the presence of various existing AKA frameworks, several significant security concerns remain unresolved. These include the prevention of impersonation, mitigation of denial of service (DoS) attacks, protection against man-in-the-middle (MITM) attacks, and the need to ensure resource efficiency. Recently, various authenticated encryption (AE) schemes have been developed to enable security services in the resource-limited IIoT/IoT environment [6,7,8]. AEAD schemes are more lightweight regarding computational resources than symmetric and asymmetric encryption schemes [9]. Thus, a cost-effective AKA framework requiring low computational and communication delays can be realized using an AEAD encryption scheme. Therefore, this paper proposes tackling the aforementioned security challenges, and we have introduced a resource-efficient AKA framework for the smart home called “ESCI-AKA”.
1.1. Research Contribution
- ESCI-AKA is designed with the integration of resource-efficient cryptographic primitives, such as the ASCON encryption scheme and a “hash function”. Its primary goal is to enable the establishment of a secure channel (session key) between users and devices within the smart home environment, utilizing the gateway node. By setting up this secure channel, ESCI-AKA allows users and devices to securely communicate sensitive information in an encrypted format, thereby ensuring protection against unauthorized access. Moreover, ESCI-AKA introduces an innovative mechanism for the login and password change processes, which rely on a single encryption operation. This simplifies the authentication procedures involved, streamlining the overall user experience and enhancing system efficiency.
- The security of ESCI-AKA is validated using the widely recognized formal mechanism known as ROM. This ensures the credibility of the security claims associated with ESCI-AKA. In addition to its security features, ESCI-AKA prioritizes user anonymity, safeguarding the privacy of users within the smart home environment. To further ensure the security of ESCI-AKA, Scyther, a security verification tool, is employed. Scyther aids in validating and confirming that ESCI-AKA is indeed secure and meets the intended security objectives.
- The efficiency of ESCI-AKA is evaluated based on its computational and communication costs. A comparison is made between ESCI-AKA and several relevant user authentication frameworks, including references [10,11,12,13,14,15,16]. ESCI-AKA demonstrates superior efficiency, achieving (65.71%, 66.18%, 84.87%, 66.18%, 79.65%, 61.01%, 86.27%) lower computational costs compared to references [10,11,12,13,14,15,16], respectively. Furthermore, ESCI-AKA outperforms these reference frameworks in terms of communication costs, achieving (44.71%, 57.66%, 40.51%, 57.66%, 54.29%, 47.78%, 65.94%) lower communication costs, respectively. In addition to its improved efficiency, ESCI-AKA also provides enhanced security features compared to the relevant security frameworks.
1.2. Paper Organization
The paper’s remaining structure is outlined as follows: In Section 2, we provide an overview of the related AKA frameworks. Section 3 offers a comprehensive explanation of the authentication and system models employed in the study. The design procedure of the proposed ESCI-AKA is presented in Section 4, emphasizing the key aspects of its development. Section 5 conducts both formal and informal analyses of ESCI-AKA to evaluate its security capabilities. The performance of ESCI-AKA is demonstrated in Section 6, showcasing its efficiency and effectiveness in real-world scenarios. Finally, in Section 7, the paper concludes with a summary and key findings.
2. Related Work
In the smart home environment, the devices deployed face resource limitations, including restricted computational power, communication capabilities, and storage capacity. Despite these constraints, it is paramount to guarantee the security of information exchange among IIoT devices over the public Internet. Several authors, as referenced in [17,18,19], have conducted surveys on information protection necessities in both IoT and smart home environments, shedding light on the diverse problems that require handling. In the context of a 6LoWPAN-based IoT environment, the study in [20] offers a user authentication technique. This technique operates an AEAD scheme and a hash function, and undergoes security confirmation operating the random oracle model (ROM) and Scyther. Another article [21] demonstrates an authentication technique, which also undergoes security verification via ROM and Scyther. However, the security technique presented in [22] is discovered to be weak against identity guessing, impersonation, and “man-in-the-middle” (MITM) attacks. To handle these problems, an authentication technique operating ECC and a hash function is suggested in [23]. The security of this technique is corroborated by operating the ROM and BAN logic.
The authentication technique suggested in [24] operates a hash function but is encountered to be powerless to “privilege insider, password guessing, and temporary secret number leakage attack”, as evidenced in [25]. Moreover, user anonymity remains unprotected within the security technique presented in [24]. In contrast, the authors of [11] designed a user authentication technique utilizing ECC and a hash function. However, this technique is incapable of withstanding “password guessing, impersonation, MITM, stolen smart card, and device capture” attacks. Likewise, it does not guarantee user anonymity. Similarly, the authentication technique suggested in [26] for the IoT environment, which operates symmetric encryption and a hash function, fails to prevent device capture and desynchronization attacks. Additionally, the user authentication framework presented in [26] does not guarantee user anonymity. Another three-factor authentication scheme using ECC and a hash function is proposed in [10], but it is found to be weak against device capture and impersonation attacks. Additionally, user anonymity is not ensured by the user authentication technique in [10]. For an IoT-enabled healthcare system, an authentication technique based on a hash function is suggested in [27], while resource-efficient, this technique is susceptible to diverse attacks, and it does not cover user anonymity. An AEAD and hash-function-based authentication technique is suggested in [28]. The security of this technique is corroborated by operating ROM and Scyther-based formal security analysis. Lastly, an authentication technique for a 6LoWPAN-enabled IoT environment is demonstrated in [29], which mandates fewer computational and communication resources for the authentication phase.
The authors of [30] developed a user authentication technique that lacks mutual authentication capability. In [31], an authentication technique is suggested particularly for the smart home environment. This technique utilizes XOR, concatenation, and hash function operations. For real-time data retrieval from IIoT devices, a cloud-assisted authentication technique is suggested in [32]. This technique employs the chaotic map and hash function. The security of the technique suggested in [33] is validated via ROM. This work demonstrates a strong and efficient authentication technique established on AEAD and hash function, and its security is substantiated by employing ROM and Scyther. In the context of smart grids, an authentication technique is familiarized in [34]. This technique depends on the hash function “Esch256”, authenticated encryption, and XOR operations. Further, the security of this technique is corroborated by operating the ROM and Scyther. An exhaustive examination of diverse user authentication techniques is demonstrated in Table 1 [35,36].

Table 1.
Overview of Existing User AKA Frameworks.
3. System Models
This subsection focuses on the explication of the authentication and attack models, which play a crucial role in the design of the proposed scheme. These models are employed to ensure robust security measures within the system.
3.1. Authentication Model
The authentication model employed for the proposed ESCI-AKA consists of the following components, as illustrated in Figure 2:
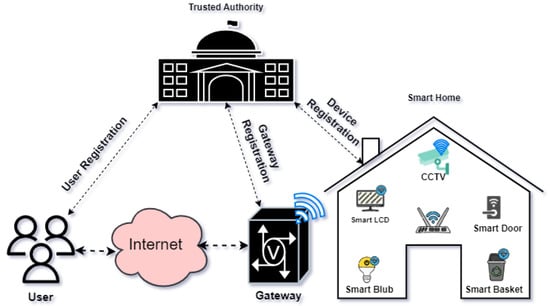
Figure 2.
Authentication model for the smart home environment.
- Gateway: The trusted authority (TA) assumes the responsibility of deploying gateway nodes () within the smart home environment. These gateway nodes provide internet connectivity to the IIoT-enabled devices deployed in the environment. Additionally, stores the sensitive parameters associated with the remote user and smart embedded devices. It possesses the capability to establish connections between IIoT-enabled devices and the Internet, using cellular or other Internet connectivity options. Furthermore, all IIoT-enabled devices deployed in the environment are connected to through communication protocols such as WiFi, 6LoWPAN, or Zigbee.
- Smart Embedded Device: Smart embedded devices (SEDs) refer to resource-limited devices deployed within the smart home environment. Each SED, denoted as , is equipped with communication, storage, and computational resources. These devices can establish communication with using communication protocols like WiFi, 6LoWPAN, or Zigbee. Additionally, SEDs are equipped with sensing modules, allowing them to collect sensitive information from their surrounding environment. This collected data can be transmitted to a central location for further analysis.
- Remote User: The user possesses smart devices () equipped with biometric sensors. Communication between and occurs through the gateway node (). Furthermore, can communicate with utilizing cellular or internet technology. In order to access real-time information from the deployed in the smart home environment, it is crucial to ensure that only authorized can obtain such information. To aid in comprehending the proposed scheme, Table 2 provides an elucidation of the various symbols employed.
 Table 2. Notations Utilized in ESCI-AKA.
Table 2. Notations Utilized in ESCI-AKA.
3.2. Attack Model
In order to evaluate the security of the ESCI-AKA framework, we utilize the widely acknowledged Dolev–Yao (DY) model [53,54]. The DY model effectively simulates the smart home environment. In the simulation, we consider that all parties in the smart home environment establish their trust in a trusted authority (TA) and communicate information securely via a dedicated communication channel with the TA. The TA handles the system initialization, user registration, and cancellation. Apart from exchanges with the TA, all parties intercommunicate with other parties via public channels. In the DY model, an attacker has the capability to both eavesdrop and modify messages if they are communicated over open channels. Given the complex nature of the smart home environment, an attacker may also resort to physically seizing devices to obtain private parameters and information.
Furthermore, there is a potential risk that the user’s may be stolen or lost, which can result in the adversary attaining access to the user’s confidential information via the compromised device. This emphasizes the importance of addressing security concerns related to users’ s. In addition, we consider the CK adversary attack model, which builds upon the DY model and enhances the capabilities of the adversary. This model grants the adversary the ability to obtain secret public parameters during the authentication session, thereby enabling them to acquire a short-lived partial key. This further amplifies the adversary’s capabilities and underscores the need for robust security measures.
4. The Proposed ESCI-AKA Framework
The ESCI-AKA system includes several phases: smart embedded registration, remote user registration, AKA, and password and biometric change. Each of these phases will be discussed in detail in the subsequent subsections.
4.1. Gateway Registration Phase
The TA is responsible for registration and deployment in the smart home environment. For deploying , TA selects a distinct identity, , and generates a long-term gateway key, , and stores the parameters {, } in the database of the .
4.2. Smart Embedded Device Registration Phase
The TA is responsible for deploying in the smart home environment after its registration. The following steps are imperative for the registration of .
Step SEDRP-1
The TA selects a unique identity for and computes . Finally, TA stores the parameters {, } in the memory of and stores the parameter in the database of .
4.3. Remote User Registration Phase
TA executes the following steps to register using a secure channel.
4.3.1. Step RMURP-1
selects its own secret parameter, such as distinct identity, , and password, . In addition, wakes its own biometric information () on the biometric sensor deployed on the IoT-enabled smart device (), and uses to generate the biometric key by computing after taking as the input. In addition, picks a random number, , and, by using hashing algorithm, computes and, by using the ASCON encryption algorithm, computes = , where , , and are the ciphertext, , , and are the plaintext, and is the associative data. Moreover, computes and constructs the message with parameters {, } and sends it to TA via secure channel.
4.3.2. Step RMURP-2
TA, after obtaining {, }, picks and computes . In addition, TA selects the list of registered for , from where can access real-time information. TA stores the parameters {, } in the database of . Finally, TA sends the parameters {, , , } to / through a secure channel.
4.3.3. Step RMURP-3
/, after sending the parameters {, , , } to / from TA, computes the following:
Finally, / stores the parameters {, , , , , , , } in its own memory.
Remark 1.
In the proposed ESCI-AKA, we utilize ASCON [6] as the encryption/decryption algorithm. ASCON is an AEAD scheme that ensures the simultaneous provision of integrity, authenticity, and confidentiality of information. The encryption operation of ASCON can be represented as , where C, MAC, , P, and K represent the ciphertext, authentication code (Tag), associated data, plaintext, and encryption key, respectively.
Similarly, the decryption operation can be expressed as . In this case, the generated MAC1 during the decryption operation will be valid if it matches the original MAC value. If the condition, , holds, the plaintext will be considered valid. Otherwise, if the condition is not satisfied, the plaintext will be deemed invalid.
Definition 1.
An AEAD scheme is reflected as protected if s ultimate OCCA3 advantage is insignificant. The OCCA3 advantage of on an AEAD is the cumulative advantage of for performing a chosen plaintext attack and compromising the integrity of an AEAD scheme [55,56].
Here, , , , , , and denote the advantage, number of queries performed by , length, polynomial time, online permutations, and ciphertext integrity, respectively.
Remark 2.
In the proposed ESCI-AKA, the fuzzy extractor (FE) technique is utilized to derive a reliable biometric key from the user’s biometric information. The FE consists of two main functions: and . The function takes the biometric information of the user as input and generates both the biometric key and the corresponding helper data. On the other hand, the function takes the helper data and the biometric information as input and reconstructs the biometric key. To reconstruct the biometric key, a condition is imposed: . Here, denotes the Hamming distance, and represents the allowable difference between and (the login biometric template and the current biometric sample, respectively). If the Hamming distance between these two values falls within the specified threshold, , the biometric key can be successfully reconstructed.
4.4. AKA Phase
During this stage, / and work together to establish a secure channel, also known as a session key, for secure information exchange. The secure channel is established through mutual authentication and session key exchange. The subsequent algorithms are performed by using / and to initiate the setup of the session key or secure channel.
4.4.1. Local Authentication and Generation of
Algorithm 1 accomplishes the task of local authentication and generates the authentication message, . The algorithm starts by taking the input parameters as , , , , and . It then generates the biometric key () using the reproduction function of FE. This reproduction function takes the biometric information of the user and helper data as input and produces the biometric key. Furthermore, the algorithm derives the encryption key and utilizes the ASCON encryption algorithm for encryption. In this encryption process, , , and serve as the plaintext, while , , and represent the associated ciphertext. The integrity of the secret credentials and the local authentication of the user is verified by checking if . Upon successful local authentication, the algorithm retrieves the values , , and for further processing.
In addition, the algorithm proceeds to derive a temporary pseudo-identity and compute associative data. ASCON encryption is employed to encrypt certain parameters, such as and . It is worth noting that the nonce used in the ASCON encryption and decryption algorithm is computed by XORing associative data and a secret encryption key. Finally, constructs the message, , which includes (timestamp), (pseudo-identity), , , and . This message is then transmitted to using an open channel of communication.
4.4.2. Validates and Generates
Algorithm 2 facilitates the validation of the received message, , by and generates . Upon receiving the message, , performs several checks to ensure its validity. Firstly, it examines whether the message is a replay by comparing the condition . If the message is determined to be a replay, discards . Otherwise, proceeds with further checks.
| Algorithm 1 Performs Local Authentication and Generates |
| Input: {, , , , } Output: {}
|
verifies if the condition is satisfied. If it holds true, retrieves and from its own database. On the other hand, if the condition is met, retrieves and from its database. Here, refers to the received pseudo-identity with the message , represents the current pseudo-identity, and corresponds to the old pseudo-identity. If no match is found in either case, terminates the AKA process.
Upon obtaining and , calculates the associative data, , and nonce, . Furthermore, after performing the decryption using as the secret key, obtains . The decryption operation is carried out utilizing the ASCON decryption algorithm. Moreover, verifies the integrity of the received message by checking if (). Finally, retrieves the values, and , for further processing.
performs the computation of plaintexts , , and , along with the generation of associative data, . By utilizing the ASCON encryption algorithm and the encryption key, , the encryption process encrypts , , and , resulting in the generation of . Finally, constructs the message, : {}, and sends to using the open communication channel.
Remark 3.
To avoid identity desynchronization, computes a new pseudo-identity, , and updates with . In addition, also keeps and updates with . Furthermore, also updates with and keeps and in its own database.
| Algorithm 2 Validates and Generates |
| Input: {} Output: {}
|
4.4.3. Validates and Generates
Algorithm 3 is designed to enable the validation of the received message, , by and subsequently generate . The freshness of the message is validated by using the condition . If the received message is determined to not be fresh, terminates the authentication process. Conversely, if the message is fresh, proceeds to compute the associative data, , and the decryption key, . The ASCON decryption algorithm utilizes to decrypt the ciphertext and generate the plaintext along with the authentication parameter, i.e., . The integrity of these returned parameters is verified by comparing with . If they match, the returned is considered valid, where = , is equal to , and is equal to . In the case of a mismatch, the authentication process is terminated by .
| Algorithm 3 Validates and Generates |
| Input: {} Output:
|
Moreover, proceeds to select and , followed by the computation of the session key, , for future secure communication with the user. Once is computed, proceeds to calculate the associative data, ; nonce, ; encryption key, ; and plaintexts, and . By utilizing the ASCON encryption algorithm, encrypts and with the encryption key, , generating . Subsequently, constructs the message, , as and transmits it to or the user via the public communication channel.
4.4.4. Validates and Session Key
Algorithm 4 is designed to enable the validation of the received message by and subsequently generate the session key. If or the user verifies the freshness of the message , they need to check the condition . If the message is determined to be valid, calculates the decryption key, , and the nonce, . By utilizing the ASCON decryption algorithm with and , and are generated.
In addition, the integrity of the message, , is checked by comparing with . To ensure secure encrypted communication between and , a session key, , is established. In order to verify the session key, computes and checks whether matches . If they match, this indicates that the session keys derived at and , which are identical.
Finally, is computed, and updates with the new value, .
4.5. Secret Credentials Change Phase
The ESCI-AKA mechanism offers a user-friendly way to modify the secret credentials (e.g., passwords and biometrics) of using Algorithm 5. To initiate this process, provides its old secret credentials, namely, and , and biometric information to . Upon receiving these secret credentials, utilizes the FE to generate the biometric key, , from and as input parameters. Subsequently, derives the encryption key, , and employs the ASCON encryption algorithm to encrypt , resulting in using the encryption key, , and .
| Algorithm 4 Validates and Generates Session Key |
| Input: Output: {Session key Generation and Mutual Authentication}
|
| Algorithm 5 Performs Password Change and Biometric Update |
| Input: {, , , , , , , , , , } Output: {, , , , , , , }
|
To ensure the authenticity of the secret credentials and perform local authentication, verifies the condition, . If the condition holds true, derives the parameters , , and . Moreover, notifies to input a new and update the biometric information to to complete the process. picks a new random number, , and computes {, , , , , , , }. Finally, it replaces {, , , , , , , } with {, , , , , , , } in ’s memory.
5. Security Validation
We provide a security analysis of ESCI-AKA, formally and informally, in this section.
5.1. Informal Security Analysis
In this subsection, we provide an informal security analysis of the proposed ESCI-AKA framework.
5.1.1. Secret Credential Change Attack
, after capturing , can obtain the sensitive parameters, such as {, , , , , , , }, which are stored in the memory of at the time of registration. cannot update the secret credentials, such as , , and , because needs to compute:
can update the secret credentials, such as , if Condition (8) holds. However, cannot generate the biometric key. Thus, without knowing the secret credentials, it is hard for to update the password and biometric key. Hence, the proposed ESCI-AKA is resistant to password and biometric key update attacks.
5.1.2. Replay Attack
To prevent a replay attack, in ESCI-AKA, timestamps are incorporated in all the communicated messages. The freshness of the messages, , , and , are checked through the conditions , , and , respectively. If any of the conditions fail, the associated message is considered to be invalid or replayed. Thus, the proposed ESCI-AKA demonstrates resistance against replay attacks.
5.1.3. DoS Attack
The proposed scheme prevents a DoS attack through the local authentication of secret credentials. To achieve local authentication, the of needs to perform the following computations:
If the condition in (13) holds, then sends the authentication and AKA request to . Otherwise, stops the further execution of the AKA phase. In this way, the proposed ESCI-AKA prevents DoS attacks.
5.1.4. MITM Attack
An authentication and key agreement mechanism must be capable of resisting an MITM attack. In the proposed ESCI-AKA, there are three messages, such as : , : , and : , which are disseminated by , , and , respectively, to accomplish a secure channel. To effectuate an MITM attack, requires knowing the secret parameters, which are used in the construction of all the messages communicated during the AKA phase, such as , , , , , , , and . A lack of knowledge of these parameters makes it hard for to generate an MITM attack. This way, ESCI-AKA exhibits resistance to MITM attacks.
5.1.5. Impersonation Attack
In ESCI-AKA, when the message : is transmitted to for authentication and the AKA process, an impersonation attack requires to generate fabricated or modified messages using random parameters, like , , and . However, since does not possess the knowledge of the actual valid parameters (, , and ), it is unable to generate a valid message, especially the parameter . Consequently, cannot impersonate a valid user in the smart home environment. Therefore, ESCI-AKA effectively prevents user impersonation attacks.
5.1.6. Impersonation Attack
In ESCI-AKA, the message, : , is transmitted to . Therefore, in order to impersonate a valid , would need to generate a fabricated message, . However, for the generation of , must possess knowledge of the parameters , , , , , and . Without knowing these parameters, cannot generate a valid . As a result, the proposed ESCI-AKA effectively safeguards against impersonation attacks targeting .
5.1.7. Temporary Parameter Leakage Attack
In ESCI-AKA, the session key is computed as , which incorporates a combination of ephemeral and long-term parameters to enhance its security measure. needs to obtain ephemeral parameters, such as , , , and , and long-term parameters, such as , , , , and , to breach the security of the session key. Hence, the proposed ESCI-AKA is resistant to temporary parameter leakage attacks.
5.1.8. Anonymity and Untraceability
During the secure channel establishment (AKA) phase, three messages are exchanged: : , : , and : . After capturing these messages, is unable to determine the user’s identity, which prevents user tracking. Additionally, all the messages generated during the current and previous AKA phases are different and random, making it impossible for to establish any correlation between captured messages from different sessions. Furthermore, even if obtains parameters such as {, , , , , , , }, it cannot extract the real identity of the user. Thus, the proposed ESCI-AKA ensures anonymous communication.
5.1.9. Desynchronization
In the proposed authentication scheme, the pseudo-identity is updated at the gateway. However, this updating of pseudo-identities introduces vulnerability to desynchronization attacks. To mitigate the risk of desynchronization attacks, we have implemented a solution by retaining both the old and current pseudo-identities at the gateway. In the event of eavesdropping or jamming attacks, an attacker can capture messages and drop them at any point during the execution of the proposed scheme. Nevertheless, even if the messages are dropped, users can still utilize the old identities to successfully complete the AKA phase of the scheme. This safeguard ensures protection against desynchronization attacks.
5.2. ROM-Based Validation
A formal analysis of the security of the session key generated during the AKA phase of ESCI-AKA is conducted using the random oracle model (ROM). The essential components of the ROM are outlined below:
- Participants: In ESCI-AKA, there are three main participants: , , and . We represent the instances, , , and , of , , and of these participants as , , and , which serve as oracles in the system.
- Partnership: Upon reaching the acceptance state, the instances, and , establish a partnership if they possess a shared session key.
- Freshness: is incapable of disclosing the session key that is established between and during the AKA phase.
The capabilities of are analyzed in Section 3.2. Furthermore, can influence different queries to execute various attacks on ESCI-AKA.
- : A passive attack can be simulated employing this query, authorizing to model and observe the passive attack. With this query, can acquire all the messages exchanged during the AKA process of ESCI-AKA.
- : operates this query to demonstrate whether the imagined session key is definitely the correct session key or merely a random guess.
- : This query is effectuated by to acquire the session key maintained by the oracle, .
- : This query is effectuated to establish an active attack. Additionally, can transmit a message, , to and acquire an affiliated response.
- : This query is effectuated by to acquire the long-term parameters held in the memory of .
Theorem 1.
We consider that is a polynomial-time () adversary endeavoring to crack the security of the session key established between the user and in ESCI-AKA. Hence, the advantage of in successfully cracking the security of the session key can be derived as follows:
In the above equation, , , , and , represent the number of queries for the hash function, send queries, password space, biometric key space/length, and hash function space, respectively. Furthermore, [55] denotes the advantage of in breaking the security of ASCON within a polynomial-time constraint.
Proof.
The proof of Theorem 1 is conducted in the same way as in [54,57,58]. Here, we consider the four games , where the winning probability of to determine the correct bit “b” is denoted by . All the games are explicated in the following sections in detail.
: This is considered an initial attack from against ESCI-AKA in the ROM model. As “b” must be decided before , it is obvious that
: This game enables to perform . By using this query, can capture all the messages, such as : , : , and : , exchanged between network participants, such as , , and , respectively. Now, the primary objective of is to construct the session key , which is constructed during the execution of the AKA phase. As the session key in ESCI-AKA is generated using a combination of long-term and ephemeral parameters, such as , , , , , , , and , the query is employed at the end of to reveal the session key, and the query is used to verify whether the constructed session key is a valid output or a random one. However, the probability of winning without knowledge of , , , , , , , and is extremely low. Therefore, and can be considered equivalent. Thus, we can conclude that
: An active attack is conducted by executing queries. In ESCI-AKA, the hash function generates the session key (SK) for and . attempts to find a collision by constructing queries to compromise the security of the SK. However, the likelihood of a collision is minimal, as indicated by the birthday paradox.
: In this scenario, captures the of a user and extracts sensitive parameters, including {, , , , , , , }, from the memory of . To accomplish this, executes . The objective of is to modify or change the user’s password and biometrics. However, generating or guessing biometric keys is challenging, and the length of the biometric key, denoted as , makes the probability of guessing the biometric key () negligible. Furthermore, considering the limited number of permissible incorrect password attempts, we can deduce that the probability of successfully guessing or modifying the user’s password and biometrics within the allowed number of attempts is extremely low. Therefore, the security of ESCI-AKA is maintained, as it effectively protects against unauthorized access to and manipulation of user credentials. Hence, we have the following:
: In this game, conducts a real attack by capturing all the exchanged messages, including , , and , using the query. It is important to note that all the messages transmitted during the AKA phase are encrypted using the ASCON encryption algorithm. Based on the security definition of ASCON (refer to Definition 1), ASCON is deemed safe for usage. Consequently, the advantage of in cracking the security of the AEAD scheme is nominal. Thus, we can extrapolate that
, after finishing games, such as , receives no considerable advantage to gain the correct bit “b”. Thus, we arrive at
From (21), we obtain
Upon considering the triangular inequality, we have
5.3. Formal Validation Using Scyther
Scyther is employed to analyze potential vulnerabilities in security frameworks. Developed in Python, Scyther ensures that all cryptographic operations/functions are impenetrable. This implies that unless an attacker manages to seize the decryption key, the encrypted transmission remains incomprehensible to them. In this article, we employ Scyther to examine the security characteristics of ESCI-AKA. ESCI-AKA is implemented using Security Protocol Description Language (SPDL), which defines three roles: (i) (gateway role), (ii) (smart embedded device role), and (iii) (user role). The SPDL script contains both manually established claims and automatically generated ones, all of which are verified by Scyther, as depicted in Figure 3. Consequently, we can affirm that ESCI-AKA is well protected and secure, as illustrated in Figure 3.
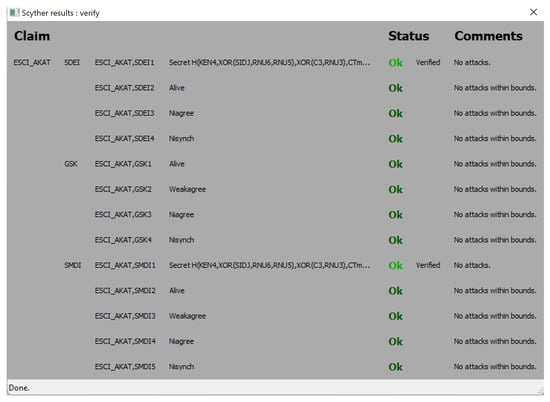
Figure 3.
Results generated through Scyther.
6. Performance Comparison
The proposed ESCI-AKA was compared with several references, including [10,11,12,13,14,15,16], in terms of their security characteristics and communication and computational costs. To evaluate the computational performance of various cryptographic primitives, we conducted tests on “Raspberry-Pi-3 with a CPU clocked at 1.2 GHz and 1 GB of RAM”, running the Ubuntu operating system. Each cryptographic primitive was executed 100 times, and the average time taken by each primitive is presented in Table 3.

Table 3.
Execution Time.
6.1. Security Comparison
In this subsection, we correlate the security characteristics of ESCI-AKA with other references: [10,11,12,13,14,15,16]. The security mechanism offered in [10] lacks protection against impersonation and device capture attacks, and it does not guarantee mutual authentication. The authentication mechanism offered in [11] is defenseless against password guessing, impersonation, and MITM attacks. Moreover, it is unable to accomplish mutual authentication and achieve user anonymity. The authentication mechanism offered in [12] does not guarantee protection against privileged insider, user anonymity, stolen smart card, and password guessing attacks. The security mechanism offered in [13] is ineffective against password guessing and temporary secret leakage, and it also lacks anonymity and untraceability characteristics. The scheme offered in [14] is defenseless against privileged insider, impersonation, replay, stolen smart card, identity guessing, and password guessing attacks. The security protocol proposed in [16] is unable to resist privileged insider and temporary parameter leakage attacks. In contrast, the proposed ESCI-AKA is protected against diverse security attacks. A comparison of the security characteristics is represented in Table 4.

Table 4.
Security Properties Comparison.
6.2. Memory Cost
In the proposed scheme, the memory requirements at different nodes are as follows:
- Smart device node: , = {128 + 256} = 384 bits;
- Gateway node: 2 × () = {256 × 2} = 512 bits;
- User device: {, , , , , , , } = {128 + 128 + 128 + 256 + 160} = 800 bits. In the proposed scheme, the total memory cost required is 1696 bits, while the works referenced as [10,11,12,13,14,15,16] require 1888 bits, 2048 bits, 1928 bits, 1024 bits, 992 bits, 1024 bits, and 992 bits, respectively. The proposed scheme requires more memory compared to certain security schemes but still demands less memory compared to other relevant security schemes. The proposed scheme, in comparison to related security schemes, incurs lower computational and communication costs while offering more significant security features.
6.3. Computational Cost
The computational cost of the proposed ESCI-AKA and other relevant security frameworks are computed using the computational time given in Table 3. The aggregated computational cost of ESCI-AKA is 8.569 ms, which is 65.71%, 66.18%, 84.87%, 66.18%, 79.65%, 61.01%, and 86.27% less than the security frameworks presented in [10,11,12,13,14,15,16], respectively. In addition, a comparison of the total computational cost is given in Figure 4, which indicates that the proposed ESCI-AKA requires low computational time to accomplish the AKA phase. The computational costs at , , and are 6.201 ms, 1.184 ms, and 1.184 ms, respectively. A comparison of computational cost at , , and is provided in Figure 5, which shows that ESCI-AKA requires low computation resources at , , and .
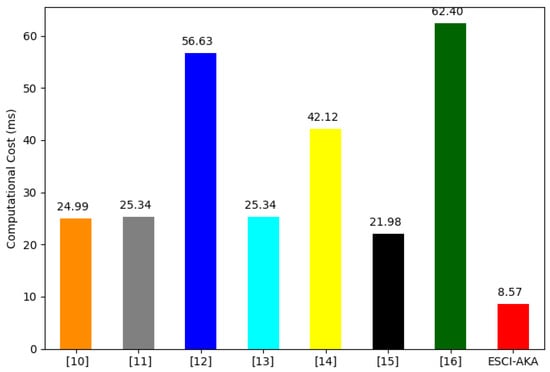
Figure 4.
Computation cost to complete the secret channel establishment phase.
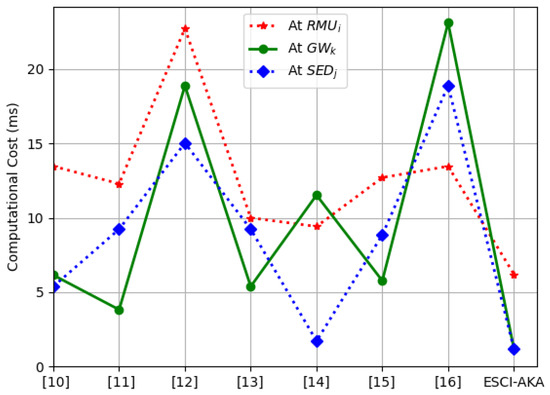
Figure 5.
Computational cost at , , and side during the accomplishment of the AKA phase.
In addition, the proposed ESCI-AKA requires fewer computational resources when many users are sending the security channel establishment or authentication request to . A comparison of computation cost when increasing the number of users at is provided in Figure 6 and Table 5.
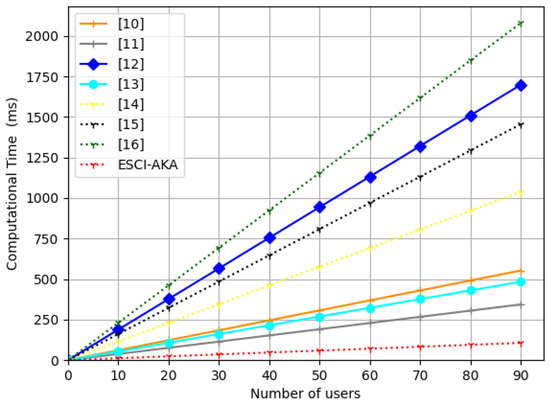
Figure 6.
Computational cost at server increasing the number of .

Table 5.
Computational Cost.
6.4. Communication Cost
To estimate the communication cost of the proposed ESCI-AKA during the AKA phase or authentication phase, we consider the sizes of the different parameters given in Table 3. In ESCI-AKA, three messages are exchanged among various network entities: : , : , and : . The sizes of , , and are 544 bits, 544 bits, and 416 bits, respectively. ESCI-AKA requires 544 + 544 + 416 = 1540 bits to complete the AKA phase. In comparison, the communication costs required by [10,11,12,13,14,15,16] (shown in Figure 7 and Table 6) are 2720 bits, 3550 bits, 2528 bits, 3552 bits, 3290 bits, 2880 bits, and 4416 bits, respectively. Figure 7 and Table 6 provide a comparison of the communication costs between ESCI-AKA and other related security mechanisms.
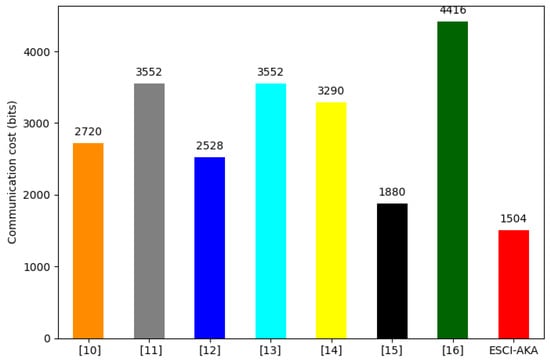
Figure 7.
Communication cost required to accomplish the AKA phase.

Table 6.
Communication Cost.
7. Conclusions
In this paper, we introduced ESCI-AKA, an innovative secure authentication framework designed specifically for the smart home environment. The primary goal of ESCI-AKA is to establish a secure channel between a user’s device and the smart home, ensuring secure communication over the public Internet. To achieve optimal resource efficiency, ESCI-AKA makes use of the lightweight cryptographic authenticated encryption scheme called “ASCON” and incorporates a hash function. The security of the session key established by ESCI-AKA is verified through a thorough ROM-based analysis. Furthermore, extensive informal analysis has demonstrated ESCI-AKA’s robustness against various types of attacks, including replay attacks, MITM attacks, and desynchronization attacks. This ensures that the communication between the device and the smart home remains secure even in the presence of potential threats. The security claims of ESCI-AKA are further supported by a Scyther-based implementation, which reinforces its reliability in real-world scenarios. This implementation has proven its effectiveness in practical applications, enhancing the overall security of the framework. Moreover, in performance evaluations, ESCI-AKA has shown significant improvements in computational and communication costs. The framework achieves a significant computational cost reduction, ranging from 61.01% to 86.27%, and a communication cost reduction, ranging from 40.51% to 65.94%. These improvements not only enhance the efficiency of the system but also ensure that the security features remain intact. In the future, we plan to utilize lightweight cryptographic primitives, such as ASCON and Esch256, to design data sharing and access control mechanisms using blockchain technology.
Author Contributions
Conceptualization, H.A. and M.T.; Methodology, H.A.; Software, H.A.; Formal analysis, H.A. and M.T.; Investigation, H.A.; Data curation, H.A.; Writing—original draft, M.T. All authors have read and agreed to the published version of the manuscript.
Funding
This research was funded by the Deanship of Scientific Research at King Khalid University through Large Group Research Project under grant number RGP.2/312/44.
Data Availability Statement
This study did not utilize any external datasets in its analysis.
Acknowledgments
The authors extend their appreciation to the Deanship of Scientific Research at King Khalid University for funding this work through the large group research project under grant number RGP2/312/44.
Conflicts of Interest
The authors state that there are no conflict of interest to disclose.
References
- Hassan, W.H. Current research on Internet of Things (IoT) security: A survey. Comput. Netw. 2019, 148, 283–294. [Google Scholar]
- Kaur, B.; Dadkhah, S.; Shoeleh, F.; Neto, E.C.P.; Xiong, P.; Iqbal, S.; Lamontagne, P.; Ray, S.; Ghorbani, A.A. Internet of things (IoT) security dataset evolution: Challenges and future directions. Internet Things 2023, 22, 100780. [Google Scholar] [CrossRef]
- Toh, C. Security for Smart Cities. IET Smart Cities 2020, 2, 95–104. [Google Scholar] [CrossRef]
- Fabrègue, B.F.; Bogoni, A. Privacy and Security Concerns in the Smart City. Smart Cities 2023, 6, 586–613. [Google Scholar] [CrossRef]
- Ragothaman, K.; Wang, Y.; Rimal, B.; Lawrence, M. Access control for IoT: A survey of existing research, dynamic policies and future directions. Sensors 2023, 23, 1805. [Google Scholar] [CrossRef]
- Dobraunig, C.; Eichlseder, M.; Mendel, F.; Schläffer, M. Ascon v1.2: Lightweight authenticated encryption and hashing. J. Cryptol. 2021, 34, 33. [Google Scholar] [CrossRef]
- Wu, H.; Preneel, B. AEGIS: A fast authenticated encryption algorithm. In Proceedings of the Selected Areas in Cryptography–SAC 2013: 20th International Conference, Burnaby, BC, Canada, 14–16 August 2013; Revised Selected Papers 20; Springer: Berlin/Heidelberg, Germany, 2014; pp. 185–201. [Google Scholar]
- Aagaard, M.; AlTawy, R.; Gong, G.; Mandal, K.; Rohit, R. ACE: An authenticated encryption and hash algorithm. LWC 2019. in submission. [Google Scholar]
- Tanveer, M.; Bhutta, M.N.M.; Alzahrani, B.A.; Albeshri, A.; Alsubhi, K.; Chaudhry, S.A. CMAP-IoT: Chaotic Map-Based Authentication Protocol for Crowdsourcing Internet of Things. Arab. J. Sci. Eng. 2023, 1–14. [Google Scholar] [CrossRef]
- Li, X.; Peng, J.; Obaidat, M.S.; Wu, F.; Khan, M.K.; Chen, C. A secure three-factor user authentication protocol with forward secrecy for wireless medical sensor network systems. IEEE Syst. J. 2019, 14, 39–50. [Google Scholar] [CrossRef]
- Yuanbing, W.; Wanrong, L.; Bin, L. An Improved Authentication Protocol for Smart Healthcare System Using Wireless Medical Sensor Network. IEEE Access 2021, 9, 105101–105117. [Google Scholar] [CrossRef]
- Challa, S.; Wazid, M.; Das, A.K.; Kumar, N.; Reddy, A.G.; Yoon, E.J.; Yoo, K.Y. Secure signature-based authenticated key establishment scheme for future IoT applications. IEEE Access 2017, 5, 3028–3043. [Google Scholar] [CrossRef]
- Choi, Y.; Lee, D.; Kim, J.; Jung, J.; Nam, J.; Won, D. Security enhanced user authentication protocol for wireless sensor networks using elliptic curves cryptography. Sensors 2014, 14, 10081–10106. [Google Scholar] [CrossRef]
- Butt, T.M.; Riaz, R.; Chakraborty, C.; Rizvi, S.S.; Paul, A. Cogent and energy efficient authentication protocol for wsn in iot. Comput. Mater. Contin. 2021, 68, 1877–1898. [Google Scholar]
- Zou, S.; Cao, Q.; Wang, C.; Huang, Z.; Xu, G. A Robust Two-Factor User Authentication Scheme-Based ECC for Smart Home in IoT. IEEE Syst. J. 2022, 16, 4938–4949. [Google Scholar] [CrossRef]
- Sureshkumar, V.; Amin, R.; Vijaykumar, V.; Sekar, S.R. Robust secure communication protocol for smart healthcare system with FPGA implementation. Future Gener. Comput. Syst. 2019, 100, 938–951. [Google Scholar] [CrossRef]
- Liu, Y.; Wang, J.; Yan, Z.; Wan, Z.; Jäntti, R. A Survey on Blockchain-based Trust Management for Internet of Things. IEEE Internet Things J. 2023, 10, 5898–5922. [Google Scholar] [CrossRef]
- Corallo, A.; Lazoi, M.; Lezzi, M.; Luperto, A. Cybersecurity awareness in the context of the Industrial Internet of Things: A systematic literature review. Comput. Ind. 2022, 137, 103614. [Google Scholar] [CrossRef]
- Hussain, S.; Ullah, S.S.; Ali, I.; Xie, J.; Inukollu, V.N. Certificateless signature schemes in Industrial Internet of Things: A comparative survey. Comput. Commun. 2022, 181, 116–131. [Google Scholar] [CrossRef]
- Tanveer, M.; Abbas, G.; Abbas, Z.H.; Bilal, M.; Mukherjee, A.; Kwak, K.S. LAKE-6SH: Lightweight User Authenticated Key Exchange for 6LoWPAN-Based Smart Homes. IEEE Internet Things J. 2022, 9, 2578–2591. [Google Scholar] [CrossRef]
- Tanveer, M.; Khan, A.U.; Kumar, N.; Hassan, M.M. RAMP-IoD: A Robust Authenticated Key Management Protocol for the Internet of Drones. IEEE Internet Things J. 2022, 9, 1339–1353. [Google Scholar] [CrossRef]
- Srinivas, J.; Das, A.K.; Wazid, M.; Vasilakos, A.V. Designing secure user authentication protocol for big data collection in IoT-based intelligent transportation system. IEEE Internet Things J. 2020, 8, 7727–7744. [Google Scholar] [CrossRef]
- Xu, H.; Hsu, C.; Harn, L.; Cui, J.; Zhao, Z.; Zhang, Z. Three-factor anonymous authentication and key agreement based on fuzzy biological extraction for Industrial Internet of Things. IEEE Trans. Serv. Comput. 2023. [Google Scholar] [CrossRef]
- Kwon, D.K.; Yu, S.J.; Lee, J.Y.; Son, S.H.; Park, Y.H. WSN-SLAP: Secure and lightweight mutual authentication protocol for wireless sensor networks. Sensors 2021, 21, 936. [Google Scholar] [CrossRef] [PubMed]
- Kumar, D. Cryptanalysis and improvement of an authentication protocol for wireless sensor networks. Trans. Emerg. Telecommun. Technol. 2023, 34, e4747. [Google Scholar]
- Ali, R.; Pal, A.K.; Kumari, S.; Sangaiah, A.K.; Li, X.; Wu, F. An enhanced three factor based authentication protocol using wireless medical sensor networks for healthcare monitoring. J. Ambient. Intell. Humaniz. Comput. 2018, 1–22. [Google Scholar] [CrossRef]
- Masud, M.; Gaba, G.S.; Choudhary, K.; Hossain, M.S.; Alhamid, M.F.; Muhammad, G. Lightweight and anonymity-preserving user authentication scheme for IoT-based healthcare. IEEE Internet Things J. 2021, 9, 2649–2656. [Google Scholar] [CrossRef]
- Tanveer, M.; Alkhayyat, A.; Khan, A.U.; Kumar, N.; Alharbi, A.G. REAP-IIoT: Resource-Efficient Authentication Protocol for the Industrial Internet of Things. IEEE Internet Things J. 2022, 9, 24453–24465. [Google Scholar] [CrossRef]
- Ashrif, F.F.; Sundarajan, E.A.; Ahmed, R.; Hasan, M.K. SLAE6: Secure and Lightweight Authenticated Encryption Scheme for 6LoWPAN Networks. In Proceedings of the 12th International Conference on Sensor Networks-SENSORNETS, Online, 23–24 February 2023. [Google Scholar]
- Fotouhi, M.; Bayat, M.; Das, A.K.; Far, H.A.N.; Pournaghi, S.M.; Doostari, M.A. A lightweight and secure two-factor authentication scheme for wireless body area networks in health-care IoT. Comput. Netw. 2020, 177, 107333. [Google Scholar] [CrossRef]
- Fan, Q.; Chen, J.; Shojafar, M.; Kumari, S.; He, D. SAKE*: A Symmetric Authenticated Key Exchange Protocol with Perfect Forward Secrecy for Industrial Internet of Things. IEEE Trans. Ind. Inform. 2022, 18, 6424–6434. [Google Scholar] [CrossRef]
- Hu, H.; Liao, L.; Zhao, J. Secure Authentication and Key Agreement Protocol for Cloud-Assisted Industrial Internet of Things. Electronics 2022, 11, 1652. [Google Scholar] [CrossRef]
- Tanveer, M.; Alkhayyat, A.; Chaudhry, S.A.; Zikria, Y.B.; Kim, S.W. REAS-TMIS: Resource-efficient authentication scheme for telecare medical information system. IEEE Access 2022, 10, 23008–23021. [Google Scholar] [CrossRef]
- Tanveer, M.; Alasmary, H. LACP-SG: Lightweight Authentication Protocol for Smart Grids. Sensors 2023, 23, 2309. [Google Scholar] [CrossRef] [PubMed]
- Liu, Z.; Guo, J.; Huang, F.; Cai, D.; Wu, Y.; Chen, X.; Igorevich, K.K. Lightweight trustworthy message exchange in unmanned aerial vehicle networks. IEEE Trans. Intell. Transp. Syst. 2023, 24, 2144–2157. [Google Scholar] [CrossRef]
- Guo, J.; Xiong, L.; Li, J.; Liu, J.; Tian, S.; Li, H. An incentive mechanism for horizontal federated learning based on principle of compound interest. Phys. Commun. 2023, 60, 102128. [Google Scholar] [CrossRef]
- Meshram, C.; Obaidat, M.S.; Lee, C.C.; Meshram, S.G. An Efficient, Robust, and Lightweight Subtree-Based Three-Factor Authentication Procedure for Large-Scale DWSN in Random Oracle. IEEE Syst. J. 2021, 15, 4927–4938. [Google Scholar] [CrossRef]
- Li, Y.; Tian, Y. A Lightweight and Secure Three-Factor Authentication Protocol with Adaptive Privacy-Preserving Property for Wireless Sensor Networks. IEEE Syst. J. 2022, 16, 6197–6208. [Google Scholar] [CrossRef]
- Wu, F.; Li, X.; Xu, L.; Vijayakumar, P.; Kumar, N. A novel three-factor authentication protocol for wireless sensor networks with IoT notion. IEEE Syst. J. 2020, 15, 1120–1129. [Google Scholar] [CrossRef]
- Hussain, S.; Chaudhry, S.A.; Alomari, O.A.; Alsharif, M.H.; Khan, M.K.; Kumar, N. Amassing the Security: An ECC-Based Authentication Scheme for Internet of Drones. IEEE Syst. J. 2021, 15, 4431–4438. [Google Scholar] [CrossRef]
- Zhang, M.; Xu, C.; Li, S.; Jiang, C. On the Security of an ECC-Based Authentication Scheme for Internet of Drones. IEEE Syst. J. 2022, 16, 6425–6428. [Google Scholar] [CrossRef]
- Aman, M.N.; Basheer, M.H.; Sikdar, B. A Lightweight Protocol for Secure Data Provenance in the Internet of Things Using Wireless Fingerprints. IEEE Syst. J. 2021, 15, 2948–2958. [Google Scholar] [CrossRef]
- Aminian Modarres, A.M.; Sarbishaei, G. An Improved Lightweight Two-Factor Authentication Protocol for IoT Applications. IEEE Trans. Ind. Inform. 2022, 19, 6588–6598. [Google Scholar] [CrossRef]
- Lee, J.; Oh, J.; Park, Y. A Secure and Anonymous Authentication Protocol Based on Three-Factor Wireless Medical Sensor Networks. Electronics 2023, 12, 1368. [Google Scholar] [CrossRef]
- Kwon, D.; Park, Y.; Park, Y. Provably secure three-factor-based mutual authentication scheme with PUF for wireless medical sensor networks. Sensors 2021, 21, 6039. [Google Scholar] [CrossRef] [PubMed]
- Ding, Z.; Xie, Q. Provably Secure Dynamic Anonymous Authentication Protocol for Wireless Sensor Networks in Internet of Things. Sustainability 2023, 15, 5734. [Google Scholar] [CrossRef]
- Rangwani, D.; Om, H. A secure user authentication protocol based on ECC for cloud computing environment. Arab. J. Sci. Eng. 2021, 46, 3865–3888. [Google Scholar] [CrossRef]
- Wazid, M.; Das, A.K.; Kumar, N.; Vasilakos, A.V. Design of secure key management and user authentication scheme for fog computing services. Future Gener. Comput. Syst. 2019, 91, 475–492. [Google Scholar] [CrossRef]
- Yeh, H.L.; Chen, T.H.; Liu, P.C.; Kim, T.H.; Wei, H.W. A secured authentication protocol for wireless sensor networks using elliptic curves cryptography. Sensors 2011, 11, 4767–4779. [Google Scholar] [CrossRef]
- Cho, Y.; Oh, J.; Kwon, D.; Son, S.; Lee, J.; Park, Y. A Secure and Anonymous User Authentication Scheme for IoT-Enabled Smart Home Environments Using PUF. IEEE Access 2022, 10, 101330–101346. [Google Scholar] [CrossRef]
- Kaveh, M.; Mosavi, M.R. A lightweight mutual authentication for smart grid neighborhood area network communications based on physically unclonable function. IEEE Syst. J. 2020, 14, 4535–4544. [Google Scholar] [CrossRef]
- Safkhani, M.; Bagheri, N.; Ali, S.; Hussain Malik, M.; Hassan Ahmed, O.; Hosseinzadeh, M.; Mosavi, A.H. Improvement and Cryptanalysis of a Physically Unclonable Functions Based Authentication Scheme for Smart Grids. Mathematics 2022, 11, 48. [Google Scholar] [CrossRef]
- Tanveer, M.; Ahmad, M.; Nguyen, T.N.; Abd El-Latif, A.A. Resource-Efficient Authenticated Data Sharing Mechanism for Smart Wearable Systems. IEEE Trans. Netw. Sci. Eng. 2022. [Google Scholar] [CrossRef]
- Tanveer, M.; Ahmad, M.; Khalifa, H.S.; Alkhayyat, A.; Abd El-Latif, A.A. A new anonymous authentication framework for secure smart grids applications. J. Inf. Secur. Appl. 2022, 71, 103336. [Google Scholar] [CrossRef]
- Abed, F.; Forler, C.; Lucks, S. General classification of the authenticated encryption schemes for the CAESAR competition. Comput. Sci. Rev. 2016, 22, 13–26. [Google Scholar] [CrossRef]
- Tanveer, M.; Bashir, A.K.; Alzahrani, B.A.; Albeshrir, A.; Alsubhi, K.; Chaudhry, S.A. CADF-CSE: Chaotic map-based authenticated data access/sharing framework for IoT-enabled cloud storage environment. Phys. Commun. 2023, 59, 102087. [Google Scholar] [CrossRef]
- Tanveer, M.; Alkhayyat, A.; Naushad, A.; Khan, A.U.; Kumar, N.; Alharbi, A.G. RUAM-IoD: A Robust User Authentication Mechanism for the Internet of Drones. IEEE Access 2022, 10, 19836–19851. [Google Scholar] [CrossRef]
- Tanveer, M.; Khan, A.U.; Kumar, N.; Naushad, A.; Chaudhry, S.A. A Robust Access Control Protocol for the Smart Grid Systems. IEEE Internet Things J. 2022, 9, 6855–6865. [Google Scholar] [CrossRef]
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2023 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).