Abstract
The traditional centralized power trading model suffers from high maintenance costs, low processing efficiency and unsynchronized information, and it cannot adapt to the high-frequency and small-dollar distributed energy trading scenario. To address the above issues, we propose Trust-DETM, a model for the implementation of distributed energy trading based on a trusted execution environment. First, we introduce a reputation metric mechanism and propose a transaction matching algorithm based on the reputation metric to achieve the accurate matching of transaction objects. Secondly, as the distributed energy trading model lacks an effective trust mechanism, we propose a commitment scheme based on smart contracts and a trusted execution environment to solve the trust problem between producers and consumers. Finally, we conduct a comprehensive experimental evaluation of the efficiency of Trust-DETM. Through comparative experiments, we find that Trust-DETM achieves trade matching and trusted execution in a lower simultaneous running time than comparable distributed trading models.
MSC:
94A60
1. Introduction
The traditional centralized electricity trading architecture is shown in Figure 1, where all electricity sales orders are processed by the trading center. With access to distributed energy, the huge amount of data on electricity transactions will lead to inefficiencies and high latency in the centralized model. Moreover, a single point of attack is always a security risk. The centralized structure relies on an exchange to allow users to trade energy. Once the exchange is attacked maliciously, the entire trading network will not work. More importantly, the user’s asset security will be threatened, and the single-point structure cannot recover from the attack. Microgrids are gaining more and more attention due to their advantages in terms of power supply reliability, safety and sustainability. The concept of the microgrid [1] aims to realize the flexible and efficient application of distributed power and solve the problem of the grid connection of distributed power with a large number and various forms. Microgrids are small, distributed systems that are self-controlled, protected and managed. The development and extension of a microgrid can fully promote large-scale access to distributed power and renewable energy and realize a highly reliable supply of various energy forms for the load. It is an effective solution to realize an active distribution network. However, the distributed architecture of microgrids presents new challenges for energy trading. First of all, the traditional energy trading model is inefficient and untimely and cannot respond quickly to the huge number of trading requests in the microgrid. Secondly, centralized trading models are vulnerable to a single point of attack, resulting in unrecoverable data loss.
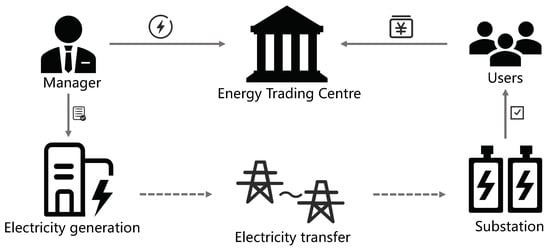
Figure 1.
Centralized energy trading architecture.
The rapid development of blockchain technology offers new possibilities for distributed electricity trading models. With decentralization, openness, autonomy, integrity and anonymity, blockchain ensures the security of energy transactions, improves the efficiency of distributed transactions and reduces transaction costs. However, the number of users in the blockchain-based distributed energy trading market is large, information data cannot be shared synchronously and it is difficult to achieve reasonable matching between the two sides of the transaction. Therefore, we introduce a reputation metric mechanism and propose a transaction matching algorithm based on the reputation metric to achieve the accurate matching of transaction objects. The system extracts the credibility judging indicators from users’ historical transaction behaviors and classify these evaluation indicators into two types: benefit-based and cost-based. Then, the system quantifies the index parameters and then calculates the weighted user reputation. Finally, the system matches transactions with the goal of maximizing the satisfaction of both parties in the transaction. On the other hand, as a specific commodity, the supply of electric energy is a long-term process and it cannot be traded instantaneously. As a result, the parties in a transaction are highly susceptible to disputes after reaching a deal. If the electricity sales node does not deliver the electricity within the agreed time limit, the rights and interests of those who consume the electricity will be harmed. For energy sellers, a malicious energy consumer may resist and refuse to pay. In distributed energy transactions, the main means to solve dishonest transactions is to conduct dispute arbitration and pursue accountability. Arbitration of the above transaction disputes is difficult to achieve in a distributed environment that lacks a centralized trusted third party. As a result, the two parties in a distributed energy transaction cannot establish a reliable trust relationship, and the security of the transaction is difficult to guarantee.
To address the above issues, we introduce Software Guard Extensions (SGX) [2], a trusted execution environment provided by Intel. As an important technical implementation of the Trusted Execution Environment (TEE), Intel SGX can virtualize a trusted security zone called an “enclave” in a specific hardware environment such as memory with the support of the CPU. This enclave is independent of the operating system, virtual machine and BIOS system, effectively blocking various attacks and preventing data or code from being stolen or tampered with. We design a mortgage commitment mechanism for distributed energy transactions based on smart contracts in Enclave, which solves the trust problem between both parties.
Finally, we propose Trust-DETM, a distributed energy trading model based on a trusted execution environment. Trust-DETM improves the trading efficiency and realizes the reasonable matching of trading objects, generates a trustworthy execution environment, solves the trust problem between trading centers, producers and consumers and forms a good background for electricity trading. Our specific contributions are shown below.
- We propose Trust-DETM, a distributed energy trading model based on a trusted execution environment. We build trust by introducing a trusted execution environment to avoid transaction disputes.
- We propose a new trading matching mechanism in Trust-DETM, which greatly improves the transaction success rates. This matching model measures the trustworthiness of the transaction user by setting a reputation metric to achieve the most reasonable match between the two sides of the transaction.
- We conduct a comprehensive analysis of Trust-DETM in terms of time overhead and storage overhead. Experimental results show that our scheme is efficient.
The rest of this paper is organized as follows. Section 2 recalls related work on energy trading. Section 3 introduces the preliminaries. Section 4 describes the system model, threat model and design objectives for Trust-DETM. The details of our proposed solution are presented in Section 5. Section 6 analyzes the security of Trust-DETM. Section 7 analyzes the performance of the scheme. Finally, we conclude the paper in Section 8.
2. Related Works
As a new generation of energy supply mode, the distributed energy system is directly oriented toward users, produces and supplies energy on the spot according to the needs of users, has multiple functions and can meet multiple goals of medium and small energy conversion and utilization systems [3]. Distributed energy solutions have also become a popular topic of research, and, in 2002, the concept of microgrids was introduced. The concept of microgrids provides a new paradigm for the definition of the operation of distributed generation [4]. Afterwards, the Energy Internet was proposed as a distributed energy system [5]. The Energy Internet realizes peer-to-peer energy exchange and sharing networks with two-way energy flow [6,7,8,9].
With the widespread adoption of distributed energy systems, distributed trading methods for energy are receiving increasing attention. In 2022, Safa et al. proposed a sustainable energy trade model based on joint learning at the edge and blockchain in the context of the Industry 4.0 architecture [10]. Lu et al. proposed a distributed power transaction model. The scheme achieves fine-grained access control through transaction arbitration in the form of ciphertext to maximize the protection of private information [11]. The arbitration mechanism in the above scheme effectively solves the trust problem caused by the lack of centralized exchanges in distributed energy transactions. Identity-based access control schemes prevent fraudulent actions by malicious actors. However, the above-mentioned distributed models do not consider the privacy protection of users, and information such as transaction prices and transaction quantities is disclosed and then executed in smart contracts. In 2020, they also proposed a distributed energy trading scheme with privacy protection, which enables a full process of privacy protection for trading users [12]. Aitzhan et al. proposed privacy protection for distributed energy transactions through multiple signatures, blockchain and anonymous message flows [1]. Wang et al. used federated learning (FL) to implement a blockchain-based model for connected vehicle energy transactions [13]. Finally, there are some references that summarize solutions for distributed energy trading [14,15,16].
The above schemes effectively address the security of distributed energy transactions, but few studies have focused on transaction matching. Wei et al. proposed a distributed matching algorithm aimed at optimizing the user pairing and power allocation between weak and strong users according to their target rate requirements [17]. Su et al. proposed an optimal personalized demand matching mechanism for energy from electric vehicles based on contract theory to achieve the rational distribution of distributed energy [18]. Kang et al. proposed a peer-to-peer (P2P) distributed power trading model to realize the problem of matching electric vehicles (PHEVs) with electrical energy sales nodes in a microgrid [19]. However, the above solutions do not consider the user’s trust metric in the matching model, and they cannot achieve accurate matching with the maximum satisfaction of both parties.
As the most typical representative of trusted execution environment applications, SGX, introduced by Intel, has been very widely used [2,20,21,22]. Li et al. proposed Nereus in 2022 to integrate smart contracts into the Software Guard Extensions (SGX) enclave to create private smart contracts to prevent collusion [23]. In the same year, they also proposed Astraea, which integrates distributed smart contracts (DiSC) with SGX Enclave to build a donation system with privacy protection [24]. Dong et al. proposed T-Counter, a framework based on Intel SGX. T-Counter allows applications to build a trusted solution to measure their CPU usage in the cloud itself [25]. Fang et al. demonstrated a novel permissioned blockchain smart contract execution framework, SEFrame, that enables intra- and inter-node concurrency under the confidentiality guarantees of Intel SGX [26]. Fang et al. proposed a two-phase framework based on the trusted hardware of Intel SGX, which effectively avoids the duplicate execution of smart contracts and improves node parallelism [27]. Meanwhile, distributed solutions based on SGX have been proposed. wu et al. proposed a T-SGX framework that allows the dynamic loading of shared objects in enclaves to guarantee the confidentiality of distributed tasks [28]. Wang et al. were the first to integrate the crash fault tolerance (CFT) protocol with the trusted execution environment (TEE) to build secure, high-performance and confidential byzantine fault tolerance (BFT) consensuses [29].
3. Preliminaries
In this section, we introduce the preliminaries, including the blockchain, smart contracts and the architecture of Intel SGX, mentioned in Section 4.
3.1. Blockchain
Blockchain originated from Bitcoin [30], which is a technical solution for the collective maintenance of a reliable database through decentralization and trustlessness. Blockchain relies on cryptography and clever distributed algorithms to enable participants to reach a consensus without the intervention of any third party center on the Internet, where trust relationships cannot be established, solving the challenge of the reliable transfer of trust and value at a very low cost. Blockchains based on distributed ledger technology record various types of transaction information, as well as ownership information for any asset, in a reliable and secure manner, in a peer-to-peer network.
3.2. Smart Contract
Smart contracts [31] are digital contracts, stored on the blockchain, that are automatically executed when pre-determined terms and conditions are met. They are often used to automate the execution of protocols so that the outcome can be determined immediately by all participants, without any intermediary involvement and without wasting time. They can also automate the workflow, triggering the next operation when the conditions are met.
Smart contracts have distinct advantages. Firstly, smart contracts are digital and automated, so there is no need to deal with paperwork or spend time checking for errors that would normally be caused by the completion of documents by hand. In terms of security, smart contracts avoid the risk of a single point of failure, and no party can tamper with the results. In terms of efficiency, smart contracts are cheap to execute. This reduces the cost of intermediaries and the time required because there is no need for them to be involved.
Although smart contracts have the above advantages, they also have their own shortcomings. Native smart contracts do not have privacy protection capabilities, and each participant can have a complete contract algorithm and data backup. Although there have been some solutions for smart contract privacy protection, most cryptography-based privacy protection introduces additional overhead, resulting in reduced system performance [32,33,34]. However, our proposed scheme effectively solves this problem.
3.3. Intel SGX
In 2013, Intel launched the SGX [35] instruction set extension, which aims to provide a trusted execution environment for a user space with hardware security as a mandatory guarantee, independent of the security status of firmware and software. With a new set of instruction set extensions and access control mechanisms, SGX enables isolated operation between different applications, safeguarding the confidentiality and integrity of critical user code and data from malware.
SGX is a new extension to the Intel architecture that adds a new set of instruction sets and memory access mechanisms to the original architecture. These extensions allow applications to implement a container called an enclave [20,36], which carves out a protected area of the application’s address space, providing confidentiality and integrity protection for the code and data inside the container from malicious software with unique privileges. The overall SGX architecture is shown in Figure 2.
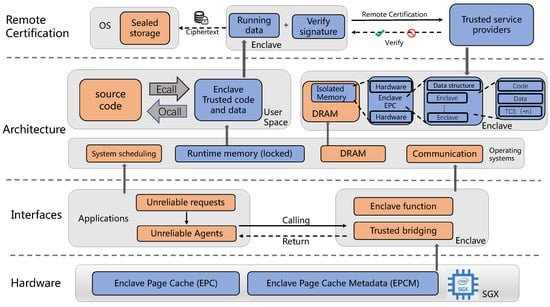
Figure 2.
Intel SGX architecture.
4. Problem Statement
In this section, we introduce the system model, threat model and design objectives of the proposed Trust-DETM.
4.1. System Model
The entities in Trust-DETM mainly include buyer nodes, seller nodes and manager nodes. The definition of each entity is shown below.
- Buyer nodes. The concept of diverse power quality for the supply of electricity is an important feature of microgrids. Large-scale access to distributed power sources has led to a shift from traditional centralized electricity sales to a distributed model. The seller nodes sell electricity as distributed electricity sales units in the microgrid.
- Seller nodes. In Trust-DETM, electricity users participate in electricity transactions in the form of distributed nodes. Buyer nodes consist of businesses, households, schools, government agencies and other electricity users. Buyer nodes can trade electrical energy in Trust-DETM by submitting a trade request.
- Manager nodes. We use the DPoS election mechanism to select managers from distributed energy blockchain nodes [37]. The trading system elects several manager nodes according to the activity of participating in energy transactions. The higher the activity, the higher the probability of being elected. These manager nodes are completely equivalent. Management nodes are not allowed to participate in this round of transactions. As an incentive, management nodes will be paid after the transaction is completed. The manager nodes collect transaction requests from user nodes and calculate the value of their trustworthiness.
Our proposed energy trading blockchain uses the model of a federated blockchain. Transaction nodes (buyer nodes and seller nodes) wishing to join the energy trading blockchain need to apply for registration with the current manager nodes. Once the application is received, the manager node will assign a registered address (pseudonym) to the user who applied.
Manager nodes are elected in each round using transaction participation as a measure. We consider nodes with a high level of activity to have a higher level of trust. These nodes tend to have very low offline rates and network latency. As an incentive, the manager nodes will receive an appropriate fee for each successful transaction. Finally, in order to prevent the system’s incorrect functioning due to the offline nature of a single node, we select multiple manager nodes in a round of transactions to form a group.
As shown in Figure 3, there are six stages in Trust-DETM.
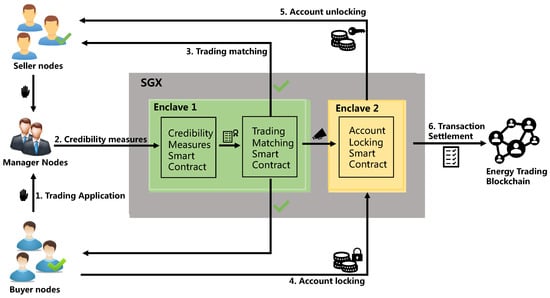
Figure 3.
Trust-DETM architecture.
Step 1: Trading Application. Both the buyer nodes and the seller nodes are free to make transaction requests to the manager nodes. The manager nodes receive the transaction request and statistically line up the reputation metric values of the trading nodes into registration information. After the transaction requests for the current round are closed, the manager nodes transmit the registration information to the credibility measurement smart contract as a trigger condition.
Step 2: Credibility Measurement. The trustworthiness measure smart contract performs a trustworthiness measurement for users who have applied to join a transaction in the current round. The contract generates a trustworthiness measurement score for each user in the given trading round by weighting the values of the trustworthiness measures received. This score will be transmitted to the trading matching smart contract as a reference for the trade matching rules.
Step 3: Trading Matching. Both the credibility measure smart contract and the trading match smart contract are executed in a closed enclave in isolation created by SGX. The trading user’s credibility measurement is used as input to trigger the trading matching smart contract. The matching algorithm is automatically executed in the contract and outputs the matching result.
Step 4: Account Locking. After the matching is completed, the transaction matching smart contract sends the matching result to the account locking smart contract. Then, the successfully matched buyer node needs to provide an account address with a sufficient balance. In order to prevent the buyer from withdrawing before the power transmission is completed, the account lock smart contract temporarily locks the agreed account balance, waiting for the completion of the transaction. Likewise, the account locking contract is securely executed in a new enclave for privacy and confidentiality.
Step 5: Account Unlocking. Once the transmission of electricity is complete, the smart meter will automatically transmit back an account unlock command to the account lock smart contract. The contract takes the previously locked account and transfers the balance to the seller’s node’s account. If the seller’s node defaults and does not complete the transmission of electricity within the agreed timeframe, the account is automatically unlocked and the locked balance is returned to the buyer’s node when the deadline is reached. As a penalty, an increase in the seller’s default rate affects the priority of the next match.
Step 6: Transaction Settlement. To ensure high efficiency, Trust-DETM settles transactions in a periodic manner. At the end of each energy transaction cycle, Trust-DETM will package all the transaction information completed in this round to form a block. Then, the blocks formed in each transaction cycle will be broadcast in the energy transaction blockchain. After the block is recorded in the blockchain through the consensus protocol, the round of energy trading is officially over.
4.2. Threat Model
We construct the threat model in this section for Trust-DETM, mentioned in Section 4.1.
- Trading users. In Trust-DETM, we assume that both buyers and sellers are honest but curious. Users will engage in energy trading honestly, but they will always wish to know private information about other users at the trade matching and account locking stages in order to make trading decisions. This characteristic may not only expose private user information but also undermine the fairness of the transaction.
- Managers. We assume that the manager nodes are equally honest but curious. In the energy trading process, manager nodes are ranked above trading users because they have access to evaluation metrics for trading user credibility measures. While they have no incentive to undermine the fairness of the deal, they are still sufficiently curious to pry into the matching mechanism and outcome of the deal.
- Energy Trading Blockchain. Blockchain systems are honest and trusted networks for distributed energy transactions. Trust mechanisms based on consensus mechanisms and cryptographic algorithms are a technical guarantee that blockchains can ensure data security, tamper prevention and transparency. In theory, there is no means to prevent a node with sufficient computing resources on the blockchain from executing any operations. In a realistic situation, it is somewhat feasible to launch a 51% attack [38]. However, such an attack would be extremely costly and we assume that this is unlikely to happen.
- SGX. We assume a powerful network adversary who has full control of the operating system and network connections, but we also assume that the contract code running in the enclave can neither be accessed secretly nor tampered with.
4.3. Design Objectives
We describe the design objectives of Trust-DETM in this section. Our design goals are divided into three main areas: security, privacy and efficiency.
- Security. Trust-DETM needs to provide a secure mechanism designed to ensure secure operation despite strong adversary assumptions. Firstly, we need to ensure the security, fairness and trustworthiness of the transaction matching process. Even if an adversary controls the host computer and underlying software, such as the operating system, the system needs hardware-based, enhanced security to more effectively block these attacks and prevent the theft or tampering of the contract data or code within it.
- Privacy. In Trust-DETM, private information is mainly divided into two categories, the transaction matching model and user account information. Our systems need to ensure that neither type of information can be observed by an adversary. Secondly, users involved in a transaction also do not have access to information about other competitors’ bids, reputation, etc. Finally, trading account information cannot be observed by other nodes and adversaries, including other trading users and managers.
- Efficiency. Trust-DETM should be efficient. We need to evaluate our system design mechanisms in terms of both communication overhead and storage overhead to ensure that the system has low latency and high performance. Finally, we illustrate the efficiency of the system through an experimental analysis in Section 7.
5. Trust-DETM
We introduce the details of Trust-DETM in this section.
5.1. Trading Application
There are two types of nodes in the distributed electricity trading network: buyers and sellers. When nodes wish to join the energy transaction, they will send a transaction application to the manager node. We assume that there are a total of n nodes applying to participate in the transaction. We introduce a reputation metric mechanism as a basis for decision making in trading matching and set m reputation metrics . denotes the value of the indicator in the kth cycle of the trading node . is the weight of indicator and is the reputation measure of trading node in the kth cycle.
We only give the calculation process here and do not discuss specific indicators. The credibility evaluation indicators can be customized by the system. Evaluation indicators can be divided into the benefit type and cost type. The benefit type represents some positive evaluation indicators, such as the historical transaction success rate, power stability, etc. Therefore, the higher the value of the benefit index, the higher the credibility of the transaction user node. On the contrary, the cost type represents the opposite evaluation indices, such as the default rate, power loss, etc. The higher the value of the cost index, the lower the credibility of the trading user node.
5.2. Credibility Measurement
After the trading nodes send their transaction requests, the manager nodes register information for the nodes and collect their reputation measurement metric data. The credibility measure smart contract then seals the execution of the credibility measure algorithm in the enclave. The credibility score considering the degree of variation in the trading node metrics is calculated as follows.
We use the extreme value processing method to quantify and calculate the index value according to the benefit index and the cost index.
For the benefit-based index,
For the cost-based index,
In the above equation, and denote the maximum and minimum values of the metrics for all nodes involved in electricity trading in the kth cycle, respectively.
We use the matrix to represent the quantified confidence measures, and the information entropy of the indicator is expressed as follows.
Among them, represents the ratio of the jth index of transaction node to the sum of all node indices.
Next, we calculate the weight of each indicator of the trading node in the following way.
Finally, the reputation measure for trading node is as follows.
5.3. Trading Matching
During the transaction matching phase, the trade matching smart contract is executed in a sealed container, enclave 1, created by SGX. The contract measures the reputations of all trading nodes and transmits as the basis for matching to the trading matching smart contract.
We assume that is the seller nodes, is the buyer nodes and . The interval for the value of satisfaction of trading nodes is . The contract matches transactions with the objective of maximum satisfaction for both parties, with the most satisfied being 1 and the least satisfied being 0. In the trading matching process, in addition to considering the reputation measurement value, both parties are also interested in parameters such as the transaction price and power consumption. In a round of trading matching, the transaction indicator parameter referenced by the seller nodes is set to . Among them, s represents the total number of parameters considered by the seller nodes.
When denotes benefit-based parameters, the desired value of the seller nodes is , the lowest acceptable value of the parameter is and the actual parameter value of the buyer node is . Thus, for the parameter , the satisfaction of the seller nodes can be expressed as follows.
When denotes cost-based parameters, the desired value of the seller nodes is , the highest acceptable value of the parameter is and the actual parameter value of the buyer node is . Thus, for the parameter , the satisfaction of the seller nodes can be expressed as follows.
Therefore, the overall satisfaction of with respect to can be expressed as follows.
In Equation (11), is the weight of in all parameters.
We assume that the buyer node is satisfied with the seller node as .
In Equation (13), represents the trading matching result. If , and are matched for electrical energy transactions. Otherwise, , and the match fails.
It is clear that Equations (13) and (14) can be mathematically modeled for the standard 0–1 assignment problem by appropriate deformations. The model introduces a total of 0–1 shaped variables. As a combinatorial optimization algorithm to solve the assignment problem in polynomial time, the Hungarian algorithm has the advantage of low computational time complexity, so, from the perspective of system efficiency, we use the Hungarian algorithm to solve the model.
Obviously, Formulas (13) and (14) can establish a mathematical model of the standard 0–1 assignment problem through proper deformation. The model introduces variables of 0–1 shape. As a combinatorial optimization algorithm to solve task allocation problems in polynomial time, the Hungarian algorithm [39] has the advantage of low computational time complexity. Therefore, considering the system efficiency, we use the Hungarian algorithm to solve the model.
5.4. Account Locking
Once the trading match is complete, the manager creates the sealed container enclave 2 and executes the account locking smart contract in it. The buyer nodes lock the account balance used for payment in the contract as a “commitment”.
To prevent the buyer node from withdrawing before the electricity is delivered and the seller node from receiving payment, the account locking smart contract locks an account address with a sufficient balance as collateral. The collateral cannot be redeemed for a limited period of time. In a trade matching round, we set up an account locking smart contract that locks all successfully matched trades in the current round.
Contracts complete execution in only two situations. In the first case, all matching transactions for the current round are completed and the account is unlocked. In the second case, the contract reaches the set limit time (the seller does not complete the transmission of electricity within the specified time) and the balance of the locked account is automatically redeemed.
The specific process is as follows.
Step 1: The successfully matched buyer nodes transmit the respective account as input to the account locking smart contract.
Step 2: The smart contract checks the account balance and verifies that has not been spent in the account. If the verification fails, the transaction is terminated.
Step 3: The smart contract executes a locking procedure for the account to ensure that it cannot be transferred out or spent early.
Step 4: The contract calculates the token and returns to as proof of account locking.
The smart contract locks the transaction accounts of all successfully matched buyer nodes, and the seller nodes can start to transmit the electricity for sale.
5.5. Account Unlocking
After the successful seller node completes the power transmission as agreed, the smart meters will automatically transmit back the account unlock commands to trigger the account locking contract. The successful seller nodes can unlock the account balance locked by the smart contract with token after completing the transmission of electricity as agreed. The account unlocking process is shown below.
Step 1: When the seller node has transmitted the power as agreed, the buyer node transmits the token to the matching seller nodes via a secure channel.
Step 2: The seller nodes transmit the obtained token as evidence to the account locking smart contract to request the unlocking of the contract balance.
Step 3: The account locking smart contract validates the token. If , the validation passes. Otherwise, the contract rejects the application token.
Step 4: If the verification passes, the smart contract accepts the request to unlock the account balance. The account locked in the smart contract is unlocked to obtain the output .
The unlocked account balance is transferred to the account of the seller nodes. Thus far, a round of power trading has been completed.
5.6. Transaction Settlement
Once the transaction is completed, we package all the transactions and upload them to the energy trading blockchain. Real-time transactions result in frequent updates to the account status. In order to improve the efficiency of Trust-DETM, we store transaction records closed in the trusted execution environment SGX and package and broadcast the “settlement” information in the blockchain at a certain frequency (e.g., once an hour or once a day). At the end of each energy transaction cycle, Trust-DETM will package all the transaction information completed in this round to form a block. Then, the blocks formed in each transaction cycle will be broadcast in the energy transaction blockchain. After the block is recorded in the blockchain through the consensus protocol, the round of energy trading is officially over.
Both the energy trading matching and fund transfer process are carried out in the closed container enclave. SGX introduces a revolutionary new security architecture that protects smart contract executions from compromise and modification. SGX guarantees the confidentiality and integrity of the energy trading process even in the presence of privileged malware at the OS, BIOS, VMM or SMM layer. As a result, Trust-DETM, which relies on SGX, uses timed broadcasts to dramatically improve the efficiency of the distributed trading model while ensuring that transactions are secure and trustworthy.
6. Security Analysis
In this section, we provide a security analysis of the algorithm details mentioned in Section 5. Our proposed Trust-DETM’s security relies on a trusted execution environment. We analyze SGX in detail in terms of three aspects: security, privacy and integrity.
6.1. Security
SGX takes hardware security as a mandatory guarantee and does not depend on the security status of firmware and software. We encapsulate the energy trading matching and account locking contracts in an enclave to protect them from malware attacks. Neither privileged nor unprivileged software can access the contracts executed in the enclave. This means that once the contract code and data are located in the enclave, even the operating system and the VMM [40] (Hypervisor) cannot influence the execution of the contract in the enclave. The enclave’s security perimeter contains only the CPU and itself.
6.2. Integrity
When the trading matching and account locking contracts are loaded into the enclave, SGX protects them from being accessed by any external software. Enclave can authenticate itself by remote proof and provide the necessary functional structure to securely provide keys. The manager nodes will perform integrity checks when creating an enclave to determine whether the smart contract code and data have been tampered with during the creation process. Therefore, the integrity of the transaction data is guaranteed.
6.3. Privacy
SGX enables the isolated execution of transactions through a hardware-based trusted execution environment. Although smart contracts are executed in clear text, the enclave ensures that no adversary can pry into the identity information and matching mechanisms of the users involved in the transaction. As an important matter of privacy, the accounts of trading users are also sealed in the enclave and no information is available to honest but curious third parties.
7. Performance Analysis
In this section, we provide a comprehensive analysis of Trust-DETM’s performance. We compare the overheads of Trust-DETM with those of other similar distributed energy trading schemes by designing comparative experiments. Finally, we analyze the experimental results and provide conclusions.
Next, we briefly describe the similarities between the chosen comparison scheme and Trust-DETM. The distributed energy trading scheme PP-BCETS [6], based on the ABE [41] cryptographic primitives, focuses on the privacy protection features of the transactions. Although we use different technical solutions, we also enable secure distributed energy trading with privacy protection. Another solution, FeneChain [16], builds a secure energy trading system to realize the supervision of the transaction process and energy management. The scheme uses anonymous authentication to protect user privacy and designs a mechanism based on time commitment to ensure verifiable fairness in the energy transaction process. Our proposed account locking protocol and FeneChain’s time commitment mechanism both attempt to achieve fairness in energy trading, but use different technical solutions. Therefore, we design experiments that compare the performance against the above scheme for two performance metrics, the storage overhead and system execution efficiency.
Our experiments are carried out on the Intel i5-8250U (1.60 GHz) platform, which supports SGX and has 8 GB of physical memory. The system software running on this platform is Ubuntu 18.04.4 with the SGX v2.6 driver installed.
7.1. Storage Overhead
In terms of storage overhead, there are mainly two types: the mortgage records of users and electricity providers stored in TEE and the transaction record . Through analysis, it has been found that the storage overhead M is approximately proportional to the number of transactions n.
The storage overhead of our system mainly has a transaction information overhead and TEE storage overhead. The TEE stores the addresses of users and power suppliers , public–private key pairs and their reputations and other related information . After the transaction is completed, the transaction information will be stored on the blockchain. The overall storage overhead is as follows:
N in the formula is the number of nodes, which is a constant when the system is stable.
According to the experimental results as shown in Figure 4, the storage overhead of Trust-DETM is lower than that of FeneChain as the number of transactions increases. In Trust-DETM, the use of the TEE allows mortgage records to be stored in a more efficient and secure manner as the TEE provides hardware-level efficiency, security and confidentiality guarantees that do not exist in traditional blockchain systems. As a result, Trust-DETM is able to process more transactions at a lower storage overhead than FeneChain.
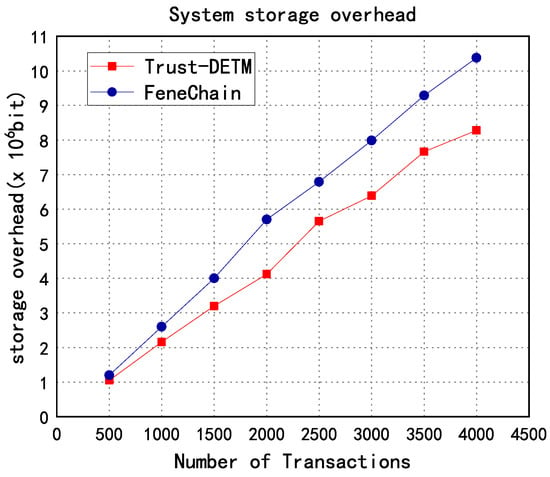
Figure 4.
Comparison of storage overhead.
7.2. System Time Overhead
The main system time overheads of our scheme encompass two aspects. One is the computational costs caused by the transaction matching algorithm , and the other is the communication overhead between users of energy trading and other roles in the system .
The time overhead of our system is mainly derived from the above two parts. System-time-overhead-related parameters are shown in Table 1. The total system overhead is as follows:

Table 1.
Parameters related to system time overhead.
Based on the above analysis, we consider that represents the system execution time and the rest is negligible. Therefore, we measure the communication overhead for the three schemes at different numbers of transactions n. The experimental data are shown in Table 2.

Table 2.
Communication times for different schemes.
Based on the experimental data in Table 2, we obtain Figure 5. Trust-DETM outperforms the other two solutions (PP-BCETS and FeneChain) in terms of communication overhead for all numbers of transactions tested. This indicates that Trust-DETM has better communication efficiency compared to the other solutions, which is an important advantage in scenarios with high-frequency and small-dollar distributed energy trading.
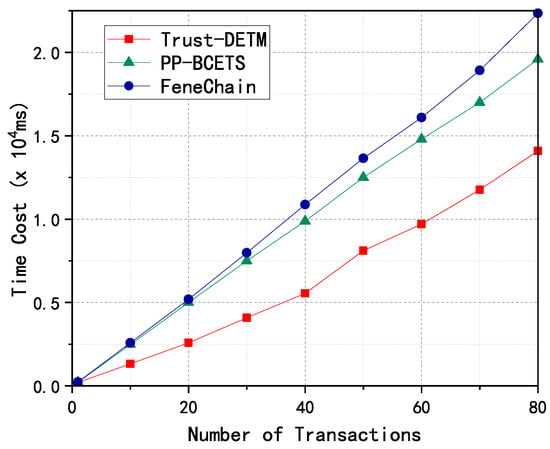
Figure 5.
Comparison of communication overhead.
According to the above analysis, we believe that the main time overhead of the system comes from the matching algorithm and communication delay. In contrast, the time overhead incurred by the rest of the system is so low that it can be ignored. Therefore, we assume that is the total time overhead of the system. We measure the time overhead of , , , , , , respectively, and calculate the total time overhead for the three schemes when the number of transactions is n. The experimental data are shown in Table 3.

Table 3.
Execution time of different schemes.
Based on the experimental data in Table 3, we obtain Figure 6. As shown in Figure 6, we can see that Trust-DERM has a lower total time overhead when processing all numbers of transactions tested, which is a clear advantage over FeneChain. The lower total time overhead in Trust-DETM indicates that the proposed solution may be more efficient and effective in processing transactions and providing the reliable and secure trading of distributed energy.
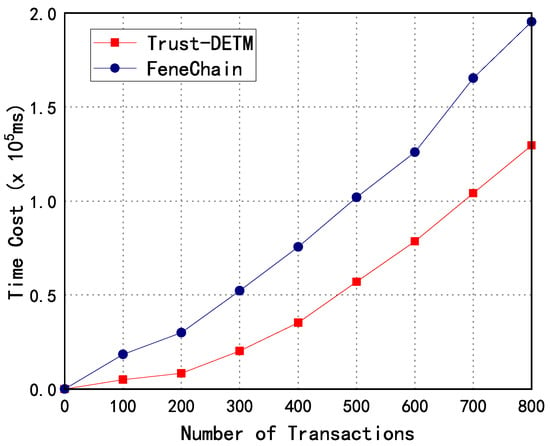
Figure 6.
Comparison of system time overhead.
Another reason for the better performance of Trust-DETM is the introduction of a reputation metric mechanism and the proposal of a transaction matching algorithm based on the reputation metric. These mechanisms enable the accurate matching of transaction objects and efficient communication between users and power providers, leading to a lower communication overhead. Furthermore, Trust-DETM proposes a commitment solution based on smart contracts and a trusted execution environment, which solves the trust problem between producers and consumers. This could increase the security and reliability of the energy trading platform, which is a crucial factor in the adoption of such platforms.
The use of a blockchain-enabled energy trading settlement platform in Trust-DETM could also contribute to its higher efficiency and security. The platform avoids complex iterations of large-scale distributed devices, improves the trading efficiency and ensures trading security. This could enable more efficient energy trading compared to other solutions.
Overall, the experimental results suggest that Trust-DETM is a promising solution for distributed energy trading, with advantages in communication efficiency, security and reliability.
8. Conclusions
This paper proposes Trust-DETM, a distributed energy trading model based on a trusted execution environment, which solves the problems of high maintenance costs, low processing efficiency and unsynchronized information in the traditional centralized electricity trading model. By incorporating a trusted execution environment and smart contracts, Trust-DETM enables the secure trading of distributed energy while protecting privacy. In addition, we propose a new transaction matching mechanism in Trust-DETM to achieve secure and accurate transaction matching, which greatly improves the success rate of transactions. This mechanism measures the trustworthiness of the trading user by setting a credibility indicator to achieve the most reasonable match between the two sides of a transaction. We also design a collateral commitment mechanism to lock the trading account through a smart contract to ensure the security and fairness of electricity trading. Finally, we describe comparative experiments to evaluate the performance of our proposed scheme in terms of both storage overhead and time overhead. The experimental results show that Trust-DETM outperforms the comparison scheme and the performance metrics meet the design requirements.
Author Contributions
Conceptualization, X.L.; Methodology, X.L.; Software, X.L. and H.G.; Validation, X.L.; Formal analysis, X.L.; Data curation, H.G.; Writing—original draft, X.L.; Writing—review & editing, X.L. All authors have read and agreed to the published version of the manuscript.
Funding
This work is supported by the National Natural Science Foundation of China (NSFC) under grants 62172040, 61872041 and U1836212, and the National Key Research and Development Program of China under grants 2021YFB2701200 and 2022YFB2702402.
Data Availability Statement
Not applicable.
Conflicts of Interest
The authors declare no conflict of interest.
References
- Aitzhan, N.Z.; Svetinovic, D. Security and privacy in decentralized energy trading through multi-signatures, blockchain and anonymous messaging streams. IEEE Trans. Dependable Secur. Comput. 2018, 15, 840–852. [Google Scholar] [CrossRef]
- Costan, V.; Devadas, S. Intel SGX explained. Cryptol. Eprint Arch. 2016. Available online: https://eprint.iacr.org/2016/086.pdf (accessed on 14 May 2023).
- Huang, A.Q.; Crow, M.L.; Heydt, G.T.; Zheng, J.P.; Dale, S.J. The future renewable electric energy delivery and management (FREEDM) system: The energy internet. Proc. IEEE 2010, 99, 133–148. [Google Scholar] [CrossRef]
- Wang, K.; Yu, J.; Yu, Y.; Qian, Y.; Zeng, D.; Guo, S.; Xiang, Y.; Wu, J. A Survey on Energy Internet: Architecture, Approach, and Emerging Technologies. IEEE Syst. J. 2018, 12, 2403–2416. [Google Scholar] [CrossRef]
- Lasseter, R. MicroGrids. In Proceedings of the 2002 IEEE Power Engineering Society Winter Meeting, Conference Proceedings (Cat. No. 02CH37309), New York, NY, USA, 27–31 January 2002; Volume 1, pp. 305–308. [Google Scholar] [CrossRef]
- Guan, Z.; Lu, X.; Yang, W.; Wu, L.; Wang, N.; Zhang, Z. Achieving efficient and Privacy-preserving energy trading based on blockchain and ABE in smart grid. J. Parallel Distrib. Comput. 2021, 147, 34–45. [Google Scholar] [CrossRef]
- Ejaz, W.; Naeem, M.; Shahid, A.; Anpalagan, A.; Jo, M. Efficient Energy Management for the Internet of Things in Smart Cities. IEEE Commun. Mag. 2017, 55, 84–91. [Google Scholar] [CrossRef]
- Gai, K.; Wu, Y.; Zhu, L.; Qiu, M.; Shen, M. Privacy-Preserving Energy Trading Using Consortium Blockchain in Smart Grid. IEEE Trans. Ind. Inform. 2019, 15, 3548–3558. [Google Scholar] [CrossRef]
- Guan, Z.; Si, G.; Zhang, X.; Wu, L.; Guizani, N.; Du, X.; Ma, Y. Privacy-Preserving and Efficient Aggregation Based on Blockchain for Power Grid Communications in Smart Communities. IEEE Commun. Mag. 2018, 56, 82–88. [Google Scholar] [CrossRef]
- Otoum, S.; Al Ridhawi, I.; Mouftah, H. A federated learning and blockchain-enabled sustainable energy-trade at the edge: A framework for industry 4.0. IEEE Internet Things J. 2022, 10, 3018–3026. [Google Scholar] [CrossRef]
- Lu, X.; Guan, Z.; Zhou, X.; Wu, L.; Du, X.; Guizani, M. An Efficient and Privacy-Preserving Energy Trading Scheme Based on Blockchain. In Proceedings of the 2019 IEEE Global Communications Conference (GLOBECOM), Waikoloa, HI, USA, 9–13 December 2019; pp. 1–6. [Google Scholar] [CrossRef]
- Guan, Z.; Lu, X.; Wang, N.; Wu, J.; Du, X.; Guizani, M. Towards secure and efficient energy trading in IIoT-enabled energy internet: A blockchain approach. Future Gener. Comput. Syst. 2020, 110, 686–695. [Google Scholar] [CrossRef]
- Wang, N.; Yang, W.; Wang, X.; Wu, L.; Guan, Z.; Du, X.; Guizani, M. A blockchain based privacy-preserving federated learning scheme for Internet of Vehicles. Digit. Commun. Netw. 2022. [Google Scholar] [CrossRef]
- Gregoratti, D.; Matamoros, J. Distributed Energy Trading: The Multiple-Microgrid Case. IEEE Trans. Ind. Electron. 2015, 62, 2551–2559. [Google Scholar] [CrossRef]
- Wang, N.; Zhou, X.; Lu, X.; Guan, Z.; Wu, L.; Du, X.; Guizani, M. When energy trading meets blockchain in electrical power system: The state of the art. Appl. Sci. 2019, 9, 1561. [Google Scholar] [CrossRef]
- Li, M.; Hu, D.; Lal, C.; Conti, M.; Zhang, Z. Blockchain-Enabled Secure Energy Trading With Verifiable Fairness in Industrial Internet of Things. IEEE Trans. Ind. Inform. 2020, 16, 6564–6574. [Google Scholar] [CrossRef]
- Liang, W.; Ding, Z.; Li, Y.; Song, L. User pairing for downlink non-orthogonal multiple access networks using matching algorithm. IEEE Trans. Commun. 2017, 65, 5319–5332. [Google Scholar] [CrossRef]
- Su, Z.; Wang, Y.; Xu, Q.; Fei, M.; Tian, Y.C.; Zhang, N. A Secure Charging Scheme for Electric Vehicles With Smart Communities in Energy Blockchain. IEEE Internet Things J. 2019, 6, 4601–4613. [Google Scholar] [CrossRef]
- Kang, J.; Yu, R.; Huang, X.; Maharjan, S.; Zhang, Y.; Hossain, E. Enabling Localized Peer-to-Peer Electricity Trading Among Plug-in Hybrid Electric Vehicles Using Consortium Blockchains. IEEE Trans. Ind. Inform. 2017, 13, 3154–3164. [Google Scholar] [CrossRef]
- Jain, P.; Desai, S.J.; Shih, M.W.; Kim, T.; Kim, S.M.; Lee, J.H.; Choi, C.; Shin, Y.; Kang, B.B.; Han, D. OpenSGX: An Open Platform for SGX Research. In Proceedings of the NDSS, San Diego, CA, USA, 21–24 February 2016; Volume 16, pp. 21–24. [Google Scholar]
- Arnautov, S.; Trach, B.; Gregor, F.; Knauth, T.; Martin, A.; Priebe, C.; Lind, J.; Muthukumaran, D.; O’keeffe, D.; Stillwell, M.; et al. Scone: Secure linux containers with intel sgx. In Proceedings of the OSDI, Savannah, GA, USA, 2–4 November 2016; Volume 16, pp. 689–703. [Google Scholar]
- Schunter, M. Intel software guard extensions: Introduction and open research challenges. In Proceedings of the 2016 ACM Workshop on Software Protection, Vienna, Austria, 24–28 October 2016; p. 1. [Google Scholar]
- Li, M.; Chen, Y.; Lal, C.; Conti, M.; Martinelli, F.; Alazab, M. Nereus: Anonymous and Secure Ride-Hailing Service based on Private Smart Contracts. IEEE Trans. Dependable Secur. Comput. 2022, 1–18. [Google Scholar] [CrossRef]
- Li, M.; Chen, Y.; Zhu, L.; Zhang, Z.; Ni, J.; Lal, C.; Conti, M. Astraea: Anonymous and Secure Auditing Based on Private Smart Contracts for Donation Systems. IEEE Trans. Dependable Secur. Comput. 2022, 1–17. [Google Scholar] [CrossRef]
- Dong, C.; Shen, Q.; Ding, X.; Yu, D.; Luo, W.; Wu, P.; Wu, Z. T-Counter: Trustworthy and Efficient CPU Resource Measurement Using SGX in the Cloud. IEEE Trans. Dependable Secur. Comput. 2023, 20, 867–885. [Google Scholar] [CrossRef]
- Fang, M.; Zhou, X.; Zhang, Z.; Jin, C.; Zhou, A. SEFrame: An SGX-enhanced Smart Contract Execution Framework for Permissioned Blockchain. In Proceedings of the 2022 IEEE 38th International Conference on Data Engineering (ICDE), Kuala Lumpur, Malaysia, 9–12 May 2022; pp. 3166–3169. [Google Scholar] [CrossRef]
- Fang, M.; Zhang, Z.; Jin, C.; Zhou, A. High-Performance Smart Contracts Concurrent Execution for Permissioned Blockchain Using SGX. In Proceedings of the 2021 IEEE 37th International Conference on Data Engineering (ICDE), Chania, Greece, 19–22 April 2021; pp. 1907–1912. [Google Scholar] [CrossRef]
- Wu, P.; Ning, J.; Luo, W.; Huang, X.; He, D. Exploring Dynamic Task Loading in SGX-Based Distributed Computing. IEEE Trans. Serv. Comput. 2023, 16, 288–301. [Google Scholar] [CrossRef]
- Wang, W.; Deng, S.; Niu, J.; Reiter, M.K.; Zhang, Y. ENGRAFT: Enclave-guarded Raft on Byzantine Faulty Nodes. In Proceedings of the 2022 ACM SIGSAC Conference on Computer and Communications Security, Los Angeles, CA, USA, 7–11 November 2022; pp. 2841–2855. [Google Scholar]
- Nakamoto, S. Bitcoin: A peer-to-peer electronic cash system. Decentralized Bus. Rev. 2008, 21260. Available online: https://bitcoin.org/bitcoin.pdf (accessed on 14 May 2023).
- Zou, W.; Lo, D.; Kochhar, P.S.; Le, X.B.D.; Xia, X.; Feng, Y.; Chen, Z.; Xu, B. Smart contract development: Challenges and opportunities. IEEE Trans. Softw. Eng. 2019, 47, 2084–2106. [Google Scholar] [CrossRef]
- Kosba, A.; Miller, A.; Shi, E.; Wen, Z.; Papamanthou, C. Hawk: The blockchain model of cryptography and privacy-preserving smart contracts. In Proceedings of the 2016 IEEE Symposium on Security and Privacy (SP), San Jose, CA, USA, 22–26 May 2016; pp. 839–858. [Google Scholar]
- Steffen, S.; Bichsel, B.; Vechev, M. Zapper: Smart Contracts with Data and Identity Privacy. In Proceedings of the 2022 ACM SIGSAC Conference on Computer and Communications Security, Los Angeles, CA, USA, 7–11 November 2022; pp. 2735–2749. [Google Scholar]
- Steffen, S.; Bichsel, B.; Baumgartner, R.; Vechev, M. Zeestar: Private smart contracts by homomorphic encryption and zero-knowledge proofs. In Proceedings of the 2022 IEEE Symposium on Security and Privacy (SP), Francisco, CA, USA, 23–25 May 2022; pp. 179–197. [Google Scholar]
- McKeen, F.; Alexandrovich, I.; Anati, I.; Caspi, D.; Johnson, S.; Leslie-Hurd, R.; Rozas, C. Intel® software guard extensions (Intel® SGX) support for dynamic memory management inside an enclave. In Proceedings of the Hardware and Architectural Support for Security and Privacy 2016, Seoul, Republic of Korea, 18 June 2016; pp. 1–9. [Google Scholar]
- Zhao, S.; Zhang, Q.; Qin, Y.; Feng, W.; Feng, D. Sectee: A software-based approach to secure enclave architecture using tee. In Proceedings of the 2019 ACM SIGSAC Conference on Computer and Communications Security, London, UK, 11–15 November 2019; pp. 1723–1740. [Google Scholar]
- Xu, G.; Liu, Y.; Khan, P.W. Improvement of the DPoS consensus mechanism in blockchain based on vague sets. IEEE Trans. Ind. Inform. 2019, 16, 4252–4259. [Google Scholar] [CrossRef]
- Li, X.; Jiang, P.; Chen, T.; Luo, X.; Wen, Q. A survey on the security of blockchain systems. Future Gener. Comput. Syst. 2020, 107, 841–853. [Google Scholar] [CrossRef]
- Kuhn, H.W. The Hungarian method for the assignment problem. Nav. Res. Logist. Q. 1955, 2, 83–97. [Google Scholar] [CrossRef]
- Liu, J.; Huang, W.; Abali, B.; Panda, D.K. High Performance VMM-Bypass I/O in Virtual Machines. In Proceedings of the USENIX Annual Technical Conference, General Track, Boston, MA, USA, 27 June–2 July 2006; pp. 29–42. [Google Scholar]
- Bethencourt, J.; Sahai, A.; Waters, B. Ciphertext-Policy Attribute-Based Encryption. In Proceedings of the 2007 IEEE Symposium on Security and Privacy (SP’07), Oakland, CA, USA, 20–23 May 2007; pp. 321–334. [Google Scholar] [CrossRef]
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2023 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).