Abstract
A bad randomness may cause catastrophic results in security; thus, it is of importance to make cryptographic systems secure against bad randomness. In this paper, we focus on a practical situation where an adversary is able to force participants in an authenticated key exchange (AKE) system to reuse the random values and the functions of these values, called related randomness attack (RRA). Following the existing randomness resetting security model of AKE and the RRA security model of public-key encryption, we present a model of RRA security for authenticated key exchange, as well as the necessary restrictions on the related randomness functions used to obtain the security definition. Then we show how a related randomness attack adversary breaks the security of some existing AKE protocols, and propose some constructions of RRA-secure authenticated key exchange in the random oracle model and standard model, respectively.
MSC:
68P27
1. Introduction
Cryptographic primitives are heavy users of randomness, but due to problems including insufficient estimation of system entropy, poor design of algorithms, bugs in software, and virtual machine randomness resetting, random number generators may fail to generate required randomness in practice [1]. This failure of randomness can cause catastrophic results: private signing keys of digital signatures could be exposed [2], low-entropy plaintexts in public-key encryption schemes might be recovered [3], the procedure of key generation would be severely weakened [4,5], ephemeral Diffie–Hellman keys may become predictable, resulting in the exposure of session keys [3], and electronic wallet security might be compromised [3]. Obviously, standard security notions of indistinguishability under chosen plaintext attacks or chosen ciphertext attacks [6] (IND-CPA or IND-CCA security) are not sufficient when these attacks on randomness are possible. This observation leads the research community to target effort into addressing this problem (e.g., [3,7,8,9]). However, it is unlikely that the failures of randomness can be completely eliminated [3]. A commonly adopted approach is to try to hedge against randomness failures, which can make cryptographic primitives offer some degree of security when encountering randomness failures.
1.1. Motivation and Contributions
An authenticated key exchange (AKE) protocol allows the communication of two parties to generate a common session key over an insecure network, which has been widely applied in real-world applications (e.g., online banking, virtual private networks (VPNs), wireless communication protocols such as Wi-Fi Protected Access (WPA), etc.) to secure network communications. An AKE protocol is composed of a tuple of randomized algorithms which take random coins produced by pseudorandom number generators (PRNGs) as the input and yield bit-strings computationally indistinguishable from truly random strings given the truly fresh and random seeds [10]. However, in practice, these seeds are constructed via data collection from an entropy pool which could be controlled by an adversary who might modify the random data, making the randomness become bad. In this context, Yang et al. [11] raised a natural question: would existing well-known AKE protocols still be secure under bad randomness? They defined two security models for reset attacks (RAs) as Reset-1 (where the random coins used by the algorithms are controlled the adversary) and Reset-2 (where a device can be reset by the adversary to force algorithms to reuse certain random coins) to capture such a security, and showed that some widely used AKE protocols become insecure when the randomness becomes bad.
Motivated by the challenge of protecting security in the case of randomness failures, we consider the security for AKE under the setting of related randomness attacks (RRAs) [3], where the adversary not only can force to reuse existing random values as in the RA setting, but also can force to use those random values’ functions, i.e., the random bits become predictable in such a way that the adversary is aware of the relations among the randomness in one session and its subsequent sessions. This capability is similar to the ability granted to the adversary in the setting of related-key attacks (RKAs) [6], under which an adversary is capable of tampering with the secret (or private) keys used in cryptographic computations. In actuality, the RA setting can be regarded as a special case of the RRA setting to allow the modelling of RAs such that the adversary cannot reset randomness, but the randomness used is in some way related to that used on previous sessions. These behaviours were discussed in the experimental work in [7], where the bad randomness was divided into reused randomness (the Reset-2 model), exposed randomness, predictable randomness (the RRA model), and chosen randomness (the Reset-1 model). Our RRA setting on authenticated key exchange builds on the bad randomness setting on AKE [11], and it also has interesting connections with related-key attacks for pseudorandom function (PRF) [12], and deterministic digital signature [11].
Contributions. We build an RRA security model for AKE in the RRA setting in this paper, under which the protocol is secure even after the adversary is able to reset a participant to use related random coins in multiple AKE sessions. Based on the security models Bellare–Rogaway (BR) [13] and Canetti–Krawczyk (CK) [14], we define the RRA security by providing additional capabilities to the adversaries in the Reset-2 model in [11]. In our RRA model, the adversary can reset to make the random coins used in multiple AKE sessions related to each other by satisfying some function defined by the adversary, which is called related-randomness deriving (RRD) function. Since the RRD functions can set the random coins in one AKE session identical to the random values in other AKE sessions, it is straightforward that the RRA model is stronger than the Reset-2 model. Different from that in the Reset-1 model [11], the adversary under related randomness attacks does not know the exact values of the used randomness, so our model allows the adversary to corrupt either participant’s long-lived key, thereby capturing the weak forward secrecy (FS) [15], which requires that compromising the long-lived secret keys of the participants will not compromise any already established session key. This reflects that, similar to the relations between the Reset-1 and Reset-2 models analysed in [11], the Reset-1 and RRA models are incomparable and we need to preclude an RRA adversary from making queries such that the RRD functions are set to be constants, i.e., the adversary controls the random coins used in the AKE protocol.
Then we show that the AKE protocols in [11] become insecure against RRAs if the adversary can manipulate randomness in a way defined in related randomness attacks. In addition, we present techniques to build RRA-secure AKE protocols from the random oracle model and the standard model, respectively.
- Random oracle construction. This can be simply realised by hashing the output session key.
- Standard model construction. We achieve this by slightly changing the way of applying pseudorandom function (PRF) in Yang et al.’s ISO-R protocol.
The above two constructions mess up the relations of different session keys, thereby building RRA-secure authenticated key exchange protocols with restrictions on the related-randomness deriving functions and additional requirements on the PRFs.
In addition, given the power of the adversary in the RRA setting, a certain set of adversarial queries must be excluded to prevent the adversary from trivially breaking security. For example, constant functions must be disallowed for security in our RRA setting, which could be regarded as the Reset-1 model for the chosen randomness in [11], where the random coins are controlled by the adversary. When the related randomness functions are restricted to be from some set , we name the functions -restricted RRD functions, and call the corresponding adversary a -restricted adversary.
Other Results. In [11], Yang et al. also presented a generic transformation on a Reset-2 secure AKE protocol to obtain a Reset-1 and Reset-2 secure ABE protocol. Their technique is to make a PRF be a strong randomness extractor (SRE) [11] such that the output of the PRF is close to uniform distribution even when the secret key used in the function is revealed. In our construction in the standard model, we ask the PRF to be RKA-secure to build the RRA-secure AKE protocols. Can our constructions for RRA-secure ABE be extended to cover the Reset-1 model? To our best knowledge, we cannot give an affirmative answer in this paper (this will be explained later with regard to the concrete constructions), and we leave this as an open problem.
1.2. Related Work
Authenticated Key Exchange. In 1993, Bellare and Rogaway [13] gave the first theoretical treatment of the security notion of AKE, which, referred to as the BR model, became the standard for analysing AKE protocols. Later, in 2001, Canetti and Krawczyk [14] gave another security model, known as the CK model, where they showed that AKE protocols composed with symmetric key encryption and authentication functions can be secure in their model to provide secure communication channels. Several popular AKE protocols (e.g., ISO [14], SIGMA [16,17], and HMQV [18]) have been proved to be secure under the CK model. LaMacchia, Lauter, and Mityagin [19] extended the CK model to the eCK model in 2007, where either the long-lived keys or the ephemeral keys of the participants of a protocol session can be comprised by the adversary. Even though there are many comparisons between the CK model and the eCK model [19,20,21], it is suggested by Boyd et al. [20] that these two models are incomparable.
Bad Randomness. For signatures, there exists a method that can avoid security issues arising from bad randomness while keeping the verification procedure as normal, which simply strengthens the private key in the signature scheme with a key for a PRF, and derives any needed randomness during the signing by applying this PRF to the “to be signed” message.
Regarding the randomness used in symmetric encryption setting, Rogaway [22] proposed nonce-based encryption, Rogaway and Shrimpton [23] proposed the notion of misuse-resistant authenticated-encryption concerning residual security when then nonce is repeated, and Kamara and Katz [24] introduced the security model of such attacks that the random coins are poorly generated, and showed generic transformations for achieving security in this context.
In the public-key setting, Bellare et al. [25] provided the best possible security guarantees for public-key encryption using bad randomness, and gave several public-key encryption schemes achieving this notion. Ristenpart and Yilek [7] studied the use of “hedge” to protect broad classes of randomness failures in already-deployed systems in the random oracle model, and performed this technique in OpenSSL. Yilek [8] focused on the public-key encryption security in a setting where resetting and reusing random numbers are possible, and presented a simple and efficient way to make any existing public-key encryption scheme secure under this model. Paterson, Schuldt, and Sibborn [3], to preserve security under randomness failures, initiated the study of security for public-key encryption in the setting of related randomness attack (RRA).
In terms of authenticated key exchange, Aiello et al. [26] discussed the reuse of Diffie–Hellman (DH) exponents in multiple AKE sessions, excluding reusing the same randomness to sign different messages in the authentication and key exchange phase. Yang et al. [11] presented its formal security model under bad randomness where the adversary is given the power of controlling or resetting the random coins used by the stateless AKE algorithms, but their approaches of building AKE protocols cannot be extended to achieve RRA security. Feltz and Cremers also [1] systematically analysed the security of both stateless and stateful AKE protocols under bad randomness, but the maliciously registered public keys are disallowed in their systems.
1.3. Organization
The rest in this paper is structured as follows. In Section 2, we briefly review the notions and definition related to this work. In Section 3, we elaborate the security model of RRA-secure AKE protocol. In Section 4, we point out some simple related randomness attacks on the AKE under bad randomness protocols. In Section 5, we present constructions of AKE with RRA security based on signature. In Section 6, we propose a construction of AKE with RRA security based on encryption. Finally, this paper is summarised in Section 7.
2. Preliminaries
In this section, we recall some basic notions to be used in this paper.
2.1. Pseudorandom Functions
Let K× D→ R be a set of PRFs [10] with being a security parameter, and K, D, and R being arbitrary finite sets. Following the security games in Figure 1, the advantage of a PRF adversary against is
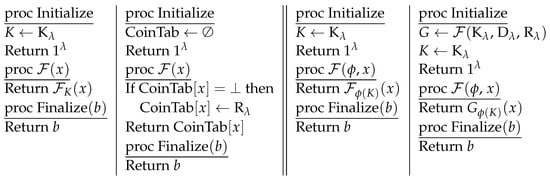
Figure 1.
Games defining security and related-key attack security for a set of pseudorandom functions . Left side of ∥: Game REAL is on the left while Game RAND is on the right. Right side of ∥: Game RKA-REAL is on the left while Game RKA-RAND is on the right.
We say that is a secure PRF family if the advantage of any probabilistic polynomial time adversary is negligible in the security parameter .
RKA-secure pseudorandom functions. Let be a class of related-key deriving functions K→K mapping a key to a related key, which is a finite set of functions with the same domain and range [2]. Let K× D→ R be a set of PRFs indexed by a security parameter with K, D, and R being arbitrary finite sets. The advantage of a -restricted related-key attack secure pseudorandom function (-RKA-PRF) adversary against is
where the security games (following the definitions in [12]) are shown in Figure 1.
We say that is a related-key attack secure PRF family if the advantage of any polynomial-time adversary (PPT) is negligible in the security parameter .
2.2. Deterministic Digital Signatures
If the signing algorithm .Sign of a digital signature scheme = .SKG, .Sign, .Vf) is deterministic, then is deterministic. A randomised digital signature scheme can be transformed into a deterministic one as follows [11].
- Firstly, the signing key is expanded to include a uniformly random key from the key space of a PRF family.
- To sign a message m, it computes random coin , where is a pseudorandom function, and then invokes the randomised signing algorithm .Sign with random coin r.
We say that is existentially unforgeable under adaptive chosen message attacks (uf-cma), if for any PPT algorithm , the advantage function
is negligible in the security parameter .
2.3. Complexity Assumption
Decisional Diffie–Hellman (DDH). The DDH problem is that for any PPT algorithm, it is difficult to distinguish , , , from , , , , where g, , a, are randomly and independently selected.
3. Modeling RRA Security
In this section, after reviewing the related notions about AKE, we describe its security model in detail.
3.1. Restricted Related-Randomness Deriving Functions
Let be a set of functions that maps from randomness R to randomness R. Let and be positive integers. Based on the properties of the -related-key deriving functions described in [12], we exhibit some necessary conditions that the -restricted related-randomness deriving functions must satisfy with the difference that the latter is concerned with the functions executing on the randomness used in the AKE schemes rather than the PRF keys.
- , -output-unpredictability for . We say that a set is output-unpredictable if, for all sets , R over the randomness r, the probability that there exist and such that = , is negligible. This can be formally defined aswhere , R, , . This restriction guarantees that under related randomness attacks, the adversary has negligible probability of learning the randomness used in the queried session.
- -collision-resistance for . We say that a set is collision-resistant if, for all sets over the randomness r, the probability that there exist two distinct such that = , is negligible. This can be formally defined aswhere , . This restriction makes sure that the adversary, given the access to the related randomness in the AKE system, has negligible probability of yielding the same session key within two different sessions.
3.2. Protocol Descriptions
An AKE protocol is composed of two PPT algorithms [11]: the long-lived key generation algorithm SKG (we consider the public-key setting in this paper where algorithm SKG returns a private and public key pair for each invocation) and the protocol execution algorithm P.
- Protocol participants. Let be a set of parties which is not empty. Each party is named by a unique string with some fixed length. Let be a set of malicious parties added by adversary to the system after the initialisation stage. Every malicious participant is also assigned with a distinctive fixed-length string without being used by another party inside the system.
- Long-lived keys. Each participant has a public key and private key created by the SKG algorithm, but each participant ’s public key can be any value as long as has never been claimed as the public key by another participant inside the system (this is to ensure that is uniquely possessed by each party).
- Instances. One participant may run many instances at the same time. We denote instance i of party U by . When a new instance is built, a unique instance number within the party is selected, a sequence of random coins are created and added to that instance, and the instance is set to the “ready” state.
- Protocol execution. A protocol execution algorithm decides how instances of participants behave to respond to messages from their environment. Upon receiving an incoming message , an instance runs the protocol P and createswhere is the responding message, acc is the decision made by the instance, term is whether the protocol execution has been terminated, sid is the session identity and pid is the partner identity that may be generated during the protocol run, is the session key hold by the instance when the decision is accepted, and is the internal state information which is deleted from U’s memory once term is true.In this paper, unless otherwise stated explicitly, the session identity will be defined as the concatenation of the messages exchanged between the two participants in the form of (initiator-messageresponder-message), and two matching instances will generate the same session identity.
- Partnership. The partnership between two instances is defined via the partner identity (named as) pid with which the instance believes it has an exchanged key, and the session identity sid uniquely labelling the AKE session as an identifier. If pid=V, pid=U and sid= sid, we say that two instances and are partners.
3.3. Security Model
We define the security model RRA-AKE to capture the scenario where the related randomness will be used in an authenticated key exchange protocol, on the basis of the strong corruption Reset-2 security model, under the assumption that the all honest participants’ long-lived keys in the set are securely yielded with fresh random coins, defined in [11].
RRA Security Model. In this case, we consider that the adversary can launch related randomness attacks but cannot directly set random coins’ values. The game RRA-AKE, defined in Figure 2, is used to define the security of AKE protocols in the related randomness setting, of which the queries are explained as follows.

Figure 2.
Game RRA-AKE in the strong corruption model. If the RevealState queries are removed from the game, it becomes the game of RRA-AKE security in the weak corruption model.
- AddUser, : With this query, adversary can add a new user U with public key . The adversary does not need to prove the knowledge on the secret key corresponding to . In other words, either the public key or the user identity U exists in the system.
- NewInstance, i, j, : This query allows adversary to initialise a new instance within party U. Adversary can specify an existing instance , and Adversary can set to make use fresh random coins.
- Send, i, : This query invokes the instance i of U with a message . The instance runs P, U, , , , , and sends the response to adversary which includes whether terminates or accepts the session identity sid and partner identity pid when they are available.
- Reveal, : The key is returned to adversary if instance has been accepted and a session key is generated.
- RevealState, : Adversary obtains the state information from making this query. This is similar to the Canetti–Krawczyk approach [14] where adversary is allowed to obtain the secret information stored in the parties memories. Note that adversary is prohibited from issuing this query to the target instance or its partner instance (if exists).
- Corrupt: Adversary can access to the party U’s long-lived secret key from this query.
- Test, : This query is only issued one time in the whole game. Adversary in this query chooses a challenge instance . If is accepted and a session key is created, then is returned to adversary if the coin b flipped in the Initialise phase or a session key randomly selected from the session key space is returned to adversary if the coin b is 0.
An adversary’s success is determined by its capability to distinguish a random key in the session key space from a real session key. However, some queries could expose the session keys; thus, adversary can trivially win the game by asking these queries.
- Adversary can obtain a session key if adversary itself is one of the parties involved in that session.
- Adversary can know the value of a session key from a Reveal query. Under related randomness attacks, adversary can also learn a session key through reset-and-reply attacks [11] where adversary first invokes a protocol execution between instance with random value and instance with random value , and then it activates another instance with random value . Thus, adversary can make = by replaying the same message from . In this case, revealing (or ) will simultaneously disclose (or ). Such attacks tell that if the randomness of instance is used by instance in a way that = = and their partner instances and share the same randomness (i.e., the random tapes at the sides of the initiator and the responder are reset to the identical ones for a previous session), it is impossible to guarantee the security on the session keys generated during these two instances. Therefore, when defining the freshness of an instance, it is necessary to require that either its randomness or its partner’s randomness will never be used by another instance in the same format. In this paper, our goal is to design AKE protocols secure against related-randomness attacks such that the security of session keys generated by those one-side reset and un-reset instances will not be affected.
We do not consider these trivial attacks, and adversary is said to be successful only if it can specify a fresh one in the Test query [11].
This model can be used to achieve forward secrecy (fs), which requires that the adversary does not have an advantage in revealing any (already) created session key by compromising the long-lived secret keys of two users. If an instance is true in any of the conditions below, we say that it is fs-unfresh in the RRA model.
- pid is generated by adversary from an AddUser query.
- Adversary exposes the session key of either or its partner instance (if it exists).
- There exists another instance of U whose session key equals that of either () or ’s partner instance (, if it exists), i.e., related randomness attacks = against and = against ’s partner instance (if it exists) have happened.
- Adversary corrupts pid if does not have a partner instance.
Otherwise, is said to be fs-fresh.
Definition 1.
We denote as an AKE protocol, as a Φ-restricted RRA adversary against , and λ as a security parameter. Adversary ’s advantage is defined to be
The protocol is said to be RRA-secure if
- Two partnering instances generate the same session key when a benign adversary honestly transmits messages;
- For any PPT adversary , is negligible in the security parameter λ.
4. Security Analysis on Yang’s Authenticated Key Exchange Protocols
In this section, we point out that Yang’s authenticated key exchange protocols under bad randomness are vulnerable in our security model.
4.1. A Related Randomness Attack on Yang’s ISO-R2 Protocol
We define G as a prime-order (which is p) group with a generator g and we let = .SKG, .Sign, .Vf) be a deterministic digital signature scheme. We revisit the AKE protocol under bad randomness ISO-R2 of Yang et al. [11] between two entities A and B in Figure 3.
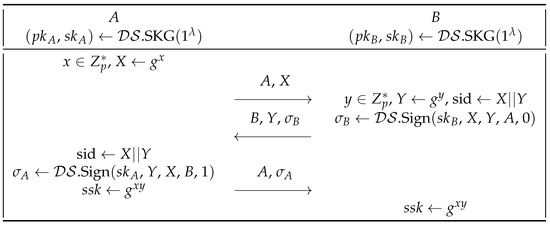
Figure 3.
The ISO-R2 protocol between the participants A and B.
The attack. We show that under the related randomness attacks, the security of this scheme can be broken. Let the related-randomness deriving functions → be indexed by such that = ≠r, where * could be addition (+) or multiplication (·).
- The adversary activates a new session of A. After receiving , for from A, the adversary sends , to B.
- * The adversary activates A another session of using the related randomness = = . After receiving , for from A, the adversary sends , to B.
- After receiving , Y, for from B, the adversary sends back , Y, to A.
- * The adversary activates B to use the related randomness = =y. After receiving , , for , ←.Sign, X, , A, from B, the adversary sends back , , to A.
- After receiving from A, the adversary sends back to B.
- * The adversary receives for ←.Sign, , X, B, from A, and sends back to B.
In the above process, the adversary builds two sessions between A and B with sid = and sid = , respectively. In this case, once the adversary knows the session key sid, it obtains the session key sid from
Notice that since the reset attack has happened to B, the result of cannot be x. Otherwise, the session sid = between A and B will not regarded as a fresh session.
4.2. A Related Randomness Attack on Yang’s ISO-R Protocol
Let G be a group of prime order p with a generator g. Let = →| be a pseudorandom function family and a strong randomness extractor (SRE) [27], where is the polynomial of . Let = .SKG, .Sign, .Vf) be a deterministic digital signature scheme. We revisit the AKE protocol under bad randomness ISO-R between two entities A and B of Yang et al. [11] in Figure 4.
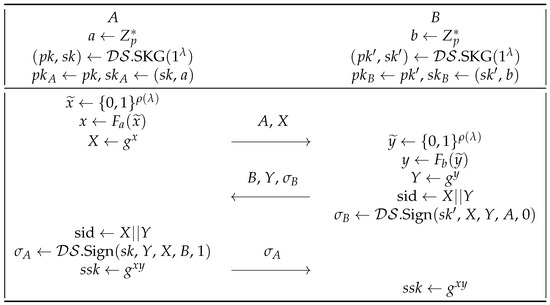
Figure 4.
The ISO-R protocol between two participants A and B.
The attack. We show that under the related randomness attacks, the security of this scheme can be broken. Let the related-randomness deriving functions → be indexed by such that ≠r. The attack mostly follows that ofISO-R2 protocol. After the attack, the adversary builds two sessions between A and B with sid = and sid = , respectively. As the adversary is given A’s long-lived secret key a, it is highly possible that it controls the pseudorandom function and thereby inferring the relationship between = and x = (if is poorly built in the form such as ). Denote the relation between x and as = . If * is addition (+) or multiplication (·), then once the adversary knows the session key of sid, it obtains the session key of sid from
Likewise, cannot be equal . Otherwise, the session between A and B for sid = is not a fresh session.
5. Authenticated Key Exchange under Related Randomness Attacks Based on Signature
In the previous section, we show that Yang’s authenticated key exchange protocols are insecure under the related randomness attack model. Here, we modify Yang’s authenticated key exchange protocols based on signature to make it resistant against related randomness attacks. For brevity, we omit all the related verification algorithms in the protocols.
5.1. Construction in the Random Oracle Model
In Figure 5, we present a slightly modified protocol to Yang’s ISO-R2 protocol [8], and call it ISO-RR2. We denote G as a group of prime order p with a generator g, and H as a collision resistant hash function. We let = .SKG, .Sign, .Vf) be a deterministic digital signature scheme.
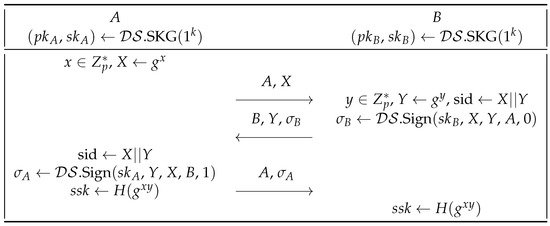
Figure 5.
The ISO-RR2 protocol between two participants A and B.
Related Randomness Attack. The ISO-RR2 protocol is similar to Yang’s ISO-R2 protocol with the difference that a hash function is used to generate the session key. The modification can prevent the related randomness attack described in Section 4, because the relation between two session keys is messed up by the hash function, thereby disabling the adversary to learn one session key from the other session key.
Interleaving attacks [11]. An interleaving attack occurs when the session identity is denoted as the concatenation of the initiator’s and the responder’s random group elements. To resist such an attack, a role indicator (’1’ for initiator and ’0’ for responder) can be added into the signed message of each party. In addition to adding a role indicator, there are other ways to resolve the problem [11]: (1) denoting “(self-messagepeer-message)” as the session identity to make different session identities for two matching instances; (2) using an explicit session identity rather than the concatenation of exchanged messages between two entities.
Theorem 1.
The ISO-RR2 protocol is RRA-secure for a Φ-restricted adversary in the random oracle model if DDH assumption holds in the underlying group and the deterministic digital signature is a uf-cma secure.
Proof.
The proof of this part is very similar to that in [11] except that in the last game, the session key outputted by the simulator is from a random oracle controlled by the simulator itself. It is not difficult to see that the random oracle plays a very important role here, which prevents the adversary, given the relation between the random coins in different instances, from learning one session key from another session key. We omit the details of the proof. □
Reset-1 Security. In the Reset-1 model, the adversary controls the randomness and is not allowed to corrupt the long-lived key of either participant in the protocol. Thus, in the ISO-RR2 protocol, x is chosen by the adversary. Similar to the analysis about the ISO-R2 protocol in [11], it is not difficult to see that the ISO-RR2 protocol cannot achieve the Reset-1 security.
5.2. Construction from RKA-PRFs
In Figure 6, we present a slightly modified protocol to Yang’s ISO-R protocol [11] (denoted by ISO-RR), and prove its RRA security. We denote G as a group of prime order p wiht a generator of g. We denote = →| as a related-key attack secure PRF family, where is the polynomial of . We assume that = .SKG, .Sign, .Vf) is a deterministic digital signature scheme.
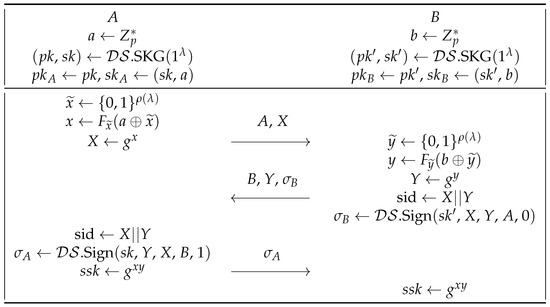
Figure 6.
The ISO-RR protocol between two participants A and B.
The ISO-RR protocol is similar to Yang’s ISO-R protocol with the difference that the pseudorandom function F is related-key attack secure, and it takes the randomness, rather than the long-lived key, as the key. The reason that Yang’s ISO-R protocol fails to prevent related randomness attacks is that when the long-lived key and the underlying relationship of the random coins are known to the adversary, it is hard to assume that the outputs of the strong randomness extractor SRE function [27] under different random coins are still independent of each other. Our modification is to prevent the related randomness attack described in Section 4, as now, due to the RKA security, the outputs of the pseudorandom function become unknown to the adversary.
Theorem 2.
The ISO-RR protocol is secure in the RRA-AKE model for a Φ-restricted adversary if the deterministic digital signature is a uf-cma secure, is a Φ-restricted related-key attack secure pseudorandom function family, and DDH assumption holds in the underlying group.
Proof.
If an adversary in the Test query outputs an instance , , then there should be a partner instance , for , . Otherwise, the security of the signature scheme is broken. We prove it as follows.
Let be a restricted RRA adversary that adversary creates an instance , with a partner instance , in the Test query. Given an adversary against the RRA security model in the ISO-RR protocol, we construct adversary to answer all adversary ’s queries using its own oracle. If adversary generates an instance , without a partner instance, adversary halts. Otherwise, adversary generates , in the Test query, and returns the received response to adversary . When adversary outputs a bit and halts, adversary outputs and halts.
We denote Forge by the event that adversary in the game generates a pair , such that a party , which is not corrupted when adversary outputs , , exists such that true ←.Vf, , , and the party I has never created a signature on message .
We denote E as the event that adversary outputs an instance , (without a partner instance) in the Test query. A Forge event occurs if the event E occurs. Adversary and adversary will be the same if the event E does not occur. Therefore, we conclude that
Below, we prove that there is a negligible probability for the event Forge to occur, or the signature ’s uf-cma security is broken. Given adversary in the original RRA-AKE game, we can build a signature forger which is given a public key created by , ←.SKG, and the access to the signing oracle .Sign, . Forger randomly chooses an entity , sets = , and then creates the long-lived keys for all entities in the set for .
Forger simulates the original RRA-AKE game for adversary . If a Forge event occurs in the simulation and , then Forger outputs the forgery by adversary and halts. Thus, we conclude that
Therefore, we have
Given adversary with advantage , we define another restricted adversary, , which outputs two integers l and after the Initialise phase. Adversary assumes that the Test session outputted by adversary is between the l-th and -th instances. Given adversary making at most NewInstance queries, adversary can be constructed as
Game. Let be the PRF with the key used by the party in the RRA-AKE game, and be the PRF with the key used by the party in the RRA-AKE game. We modify the RRA-AKE game for adversary to a game Game such that the output of the function in the l-th instance (or , ) is a random string, and the output of the function in -th instance (or , ) is another random string. Adversary has similar advantages in the original RRA-AKE game and game Game, or we can construct an adversary against the RKA security of the PRF.
Adversary has access to an oracle which returns either a true result of or a random output of , where . Adversary simulates the RRA-AKE game by honestly running all operations except that adversary simulates the PRFs of party and of party by asking its own oracle. Finally, when adversary outputs a bit and halts, adversary outputs the same and halts. We can then conclude that
Game. We modify the game Game to a game Game such that the simulator randomly chooses a key and sets it as the session key of the l-th and the -th instances. Adversary has similar advantages in game Game and game Game, or we can construct an adversary breaking the DDH assumption.
Given a tuple , , , , adversary ’s goal is to guess whether Z is a random group element or . Following the procedure of the game Game, adversary simulates the game Game for adversary except that the ephemeral public key in the l-th instance is set to be X by adversary , the ephemeral public key in the -th instance is set to be Y by adversary , and the session key of the l-th and the -th instances is set to be Z by adversary . We then conclude that
Since in Game, adversary has no advantage in winning the game, i.e., = 0. Combining all the above results, we have
□
Reset-1 Security. In the Reset-1 model, the adversary controls the randomness and is not allowed to corrupt the long-lived key of either participant in the protocol. Thus, in the ISO-RR protocol, is known to the adversary. Therefore, according to the approach used to obtain the Reset-1 and Reset-2 security from a Reset-2 secure AKE protocol in [11], the pseudorandom function should be a strong extractor. However, the PRF in the ISO-RR protocol is already set to be RKA-secure. Do such kind of pseudorandom functions, which are RKA-secure and can be strong extractors as well, exist? To the best of our knowledge, we cannot affirmatively answer this.
6. RRA-Secure Authenticated Key Exchange Based on Encryption
In the full version of [11], there are also authenticated key exchange constructions on the basis of public-key encryption with message authentication code. If we modify the PKEDH-R2 and PKEDH-R protocols in [11] following the modifications to the ISO-R2 and ISO-R protocols, and require the underlying public-key encryption scheme to be secure against related randomness attacks [3], we can achieve weak corruption RRA security in both of them. To show this, below, we will take the modified PKEDH-R protocol (which is named as PKEDH-RR) as an instance.
Public-Key Encryption (PKE). A PKE scheme is composed of three algorithms [11]: a key generation algorithm .SKG outputting a public key and private key on inputting a security parameter, an encryption algorithm .Enc, outputting a ciphertext c on inputting a message m and the public key , and a decryption algorithm .Dec, outputting a failure symbol ⊥ or a message m on inputting the private key and a ciphertext c. The encryption algorithm can also be denoted as .Enc, m; , meaning that message m is encrypted under public key using randomness r.
If for any PPT adversary = , , the advantage function for the scheme
is negligible in the security parameter and adversary is excluded from making a decryption query on the ciphertext , then the PKE scheme is IND-CCA secure.
Message Authentication Code (MAC). An MAC scheme with key space [11] consists of a message authentication algorithm MAC outputting an authentication tag on inputting a message m and a key , and a verification algorithm MAV, outputting 0 or 1 on inputting a message and tag pair , and a key .
If for any PPT adversary , the advantage function for the scheme
is negligible in the security parameter , then the MAC scheme is secure under chosen message attacks.
6.1. A PKEDH-RR Protocol
Let = →| be a related-key attack secure PRF family where is the polynomial of . Let = .SKG, .Enc, .Dec) be a PKE scheme. Let =(MAC, MAV) be an MAC scheme. We present the PKEDH-RR protocol in Figure 7, where G is a group of prime order p, and g is a generator of G.
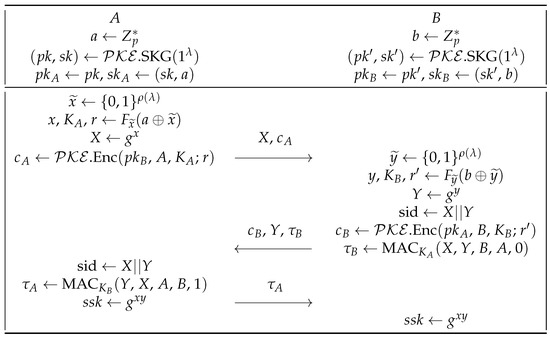
Figure 7.
The PKEDH-RR protocol between two participants A and B. Related decryption and verification algorithms in the protocol are omitted due to the brevity consideration.
Similarly, the PKEDH-RR protocol is similar to Yang’s PKEDH-R protocol with the difference that the pseudorandom function F is related-key attack secure, and it takes the randomness rather than the long-lived key as the key. The reason that Yang’s PKEDH-R protocol fails to prevent related randomness attacks is that when the long-lived key and the underlying relationship of the random coins are known to the adversary, it is hard to assume that the outputs of the strong randomness extractor SRE function [27] under different random coins are still independent of each other. Our modification is to prevent the related randomness attack described in Section 4, as now, due to the RKA security, the outputs of the pseudorandom function become unknown to the adversary.
6.2. Security Proof
Theorem 3.
The PKEDH-RR protocol is secure in the weak corruption RRA-AKE model for a Φ-restricted adversary if is an IND-CCA secure PKE scheme, is an MAC scheme secure under adaptive chosen message attacks, is a Φ-restricted related-key attack secure pseudorandom function family, and DDH assumption holds in the underlying group.
Proof.
Similar to the proof of Theorem 2, there must be a partner instance , corresponding to an instance , output by an adversary in the Test query, or the security of the public-key encryption scheme or the message authentication code could be broken. □
Following the proof in [11], we define an encryption forger . Let , ←.SKG, and ←.Enc, S, , where S is a randomly selected string by forger , and is a randomly selected key from ’s key space (unknown to forger ). Given , , and access to an oracle decrypting ciphertexts unequal to , and an oracle returning MAC on an input m, the goal of forger is to output , MAC with forger never querying to the oracle on .
We denote E by the event that the instance , in the Test query created by adversary has no partner instance. We can build an encryption forger in the RRA-AKE game if the event E occurs.
We denote as the maximum number of NewInstance queries sent by adversary . Forger randomly chooses two entities , from (=n), and creates all long-lived keys for other entities in . Forger then chooses an integer l←, , and requests the challenger to return the challenge = .Enc, , on input under , and then it sets = , and simulates the RRA-AKE game with adversary with an exception in cases below.
- Forger halts if adversary does not make a Test query with an instance of .
- Forger halts if pid≠.
- Forger halts if , is not the l-th instance.
- Forger halts if adversary makes a corrupt query with input .
- Forger sets = in the l-th instance, generates the ephemeral DH public and private key pair for , , utilises to obtain N←.Dec, , and honestly yields the tag with N.
- If adversary forwards a message , to with , forger queries c to its decryption oracle , and proceeds as usual after receiving from .
- If adversary forwards a message , to , forger queries to its oracle to obtain the response tag.
- If adversary forwards the MAC tag to the l-th instance, forger outputs its forgery with the message and MAC tag pair and halts.
Therefore, we can conclude that
Given an encryption forger , we can build another adversary against the PKE scheme in the IND-CCA security game. Adversary is given a public key and can access both encryption and decryption oracles. When forger requests a challenge on the input S, adversary randomly chooses numbers and , and requests its challenger with inputs and . Adversary sets , as forger ’s challenge after obtaining the challenge . When forger queries to the encryption oracle on a ciphertext , adversary queries to the decryption oracle on the input c to its challenger. When forger queries to the MAC oracle on a message m, adversary responds to forger MAC. Lastly, adversary outputs 0 if forger makes a successful forgery MAC, meaning that is a ciphertext for . Otherwise, adversary outputs 0 if forger ’s forgery fails, meaning that is a ciphertext for . Hence, we can conclude that
where the last line is summarised from the fact that forger is in the encryption forger game when , and forger is in the chosen message attack game when , is independent of .
Integrating all previous results, we can conclude that
The rest of the proof is similar to that in Theorem 2, so we omit the details.
Reset-1 Security. The method used to construct a PKEDH-RR protocol that is RRA-secure is similar to that used in the ISO-RR protocol. Therefore, for the same reason, we are not sure whether the PKEDH-RR protocol can be extended to cover the Reset-1 model defined in [11].
7. Conclusions
Several recent incidents caused by the various kinds of randomness failures make the research community begin to find methods hedging cryptographic primitives against such failures. In this paper, we focus on a special attack, called related randomness attack (RRA), executed on the randomness used in authenticated key exchange, where an adversary is able to force the participants of an authenticated key exchange scheme to reuse the random values and the functions of these values. We start from formalising the RRA security model for an authenticated key exchange protocol. Following the RRA security model of public-key encryption and the randomness resetting security model of authenticated key exchange, we present our model of RRA security for authenticated key exchange. After pointing out the related randomness attacks on the authenticated key exchange protocols in [11], we propose several constructions of authenticated key exchange under related randomness attacks.
Author Contributions
Methodology, H.C.; Formal analysis, G.M. All authors have read and agreed to the published version of the manuscript.
Funding
This research was funded by National Natural Science Foundation of China grant number 62072369.
Conflicts of Interest
The authors declare no conflict of interest.
References
- Feltz, M.; Cremers, C. Strengthening the security of authenticated key exchange against bad randomness. Des. Codes Cryptogr. 2018, 86, 481–516. [Google Scholar] [CrossRef]
- Cui, H.; Qin, B.; Susilo, W.; Nepal, S. Robust digital signature revisited. Theor. Comput. Sci. 2020, 844, 87–96. [Google Scholar] [CrossRef]
- Paterson, K.G.; Schuldt, J.C.N.; Sibborn, D.L. Related Randomness Attacks for Public Key Encryption. In Public Key Cryptography; Lecture Notes in Computer Science; Springer: Berlin/Heidelberg, Germany, 2014; Volume 8383, pp. 465–482. [Google Scholar]
- Heninger, N.; Durumeric, Z.; Wustrow, E.; Halderman, J.A. Mining Your Ps and Qs: Detection of Widespread Weak Keys in Network Devices. In Proceedings of the USENIX Security Symposium, Bellevue, WA, USA, 8–10 August 2012; Volume 2012, pp. 205–220. [Google Scholar]
- Lenstra, A.K.; Hughes, J.P.; Augier, M.; Bos, J.W.; Kleinjung, T.; Wachter, C. Public Keys. In Proceedings of the CRYPTO, Santa Barbara, CA, USA, 19–23 August 2012; Lecture Notes in Computer Science. Springer: Berlin/Heidelberg, Germany, 2012; Volume 7417, pp. 626–642. [Google Scholar]
- Cui, H.; Mu, Y.; Au, M.H. Relations between robustness and RKA security under public-key encryption. Theor. Comput. Sci. 2016, 628, 78–91. [Google Scholar] [CrossRef]
- Ristenpart, T.; Yilek, S. When Good Randomness Goes Bad: Virtual Machine Reset Vulnerabilities and Hedging Deployed Cryptography. In Proceedings of the NDSS, San Diego, CA, USA, 28 February–3 March 2010; Volume 2010. [Google Scholar]
- Yilek, S. Resettable Public-Key Encryption: How to Encrypt on a Virtual Machine. In Proceedings of the CT-RSA, San Francisco, CA, USA, 1–5 March 2010; Lecture Notes in Computer Science. Springer: Berlin/Heidelberg, Germany, 2010; Volume 5985, pp. 41–56. [Google Scholar]
- Yuen, T.H.; Zhang, C.; Chow, S.S.M.; Yiu, S. Related Randomness Attacks for Public Key Cryptosystems. In Proceedings of the 10th ACM Symposium on Information, Computer and Communications Security, ASIA CCS ’15, Singapore, 14–17 April 2015; Bao, F., Miller, S., Zhou, J., Ahn, G., Eds.; ACM: New York, NY, USA, 2015; pp. 215–223. [Google Scholar] [CrossRef]
- Blackman, D.; Vigna, S. Scrambled Linear Pseudorandom Number Generators. ACM Trans. Math. Softw. 2021, 47, 36:1–36:32. [Google Scholar] [CrossRef]
- Yang, G.; Duan, S.; Wong, D.S.; Tan, C.H.; Wang, H. Authenticated Key Exchange under Bad Randomness. In Proceedings of the Financial Cryptography and Data Security-15th International Conference, FC 2011, Gros Islet, Saint Lucia, 28 February–4 March 2011; Revised Selected Papers. Springer: Berlin/Heidelberg, Germany, 2011; Volume 7035, pp. 113–126. [Google Scholar]
- Bellare, M.; Kohno, T. A Theoretical Treatment of Related-Key Attacks: RKA-PRPs, RKA-PRFs, and Applications. In Proceedings of the EUROCRYPT; Lecture Notes in Computer Science, Warsaw, Poland, 4–8 May 2003; Springer: Berlin/Heidelberg, Germany, 2003; Volume 2656, pp. 491–506. [Google Scholar]
- Bellare, M.; Rogaway, P. Entity Authentication and Key Distribution. In Proceedings of the Advances in Cryptology-CRYPTO ’93, 13th Annual International Cryptology Conference, Santa Barbara, CA, USA, 22–26 August 1993; Springer: Berlin/Heidelberg, Germany, 1993; Volume 773, pp. 232–249. [Google Scholar]
- Canetti, R.; Krawczyk, H. Analysis of Key-Exchange Protocols and Their Use for Building Secure Channels. In Proceedings of the Advances in Cryptology-EUROCRYPT 2001, International Conference on the Theory and Application of Cryptographic Techniques, Innsbruck, Austria, 6–10 May 2001; Springer: Berlin/Heidelberg, Germany, 2001; Volume 2045, pp. 453–474. [Google Scholar]
- Becerra, J.; Ostrev, D.; Skrobot, M. Forward Secrecy of SPAKE2. In Proceedings of the Provable Security-12th International Conference, ProvSec 2018, Jeju, Republic of Korea, 25–28 October 2018; Baek, J., Susilo, W., Kim, J., Eds.; Lecture Notes in Computer Science. Springer: Berlin/Heidelberg, Germany, 2018; Volume 11192, pp. 366–384. [Google Scholar] [CrossRef]
- Canetti, R.; Krawczyk, H. Security Analysis of IKE’s Signature-Based Key-Exchange Protocol. In Proceedings of the Advances in Cryptology-CRYPTO 2002, 22nd Annual International Cryptology Conference, Santa Barbara, CA, USA, 18–22 August 2002; Springer: Berlin/Heidelberg, Germany, 2002; Volume 2442, pp. 143–161. [Google Scholar]
- Krawczyk, H. SIGMA: The ’SIGn-and-MAc’ Approach to Authenticated Diffie-Hellman and Its Use in the IKE-Protocols. In Proceedings of the Advances in Cryptology-CRYPTO 2003, 23rd Annual International Cryptology Conference, Santa Barbara, CA, USA, 17–21 August 2003; Springer: Berlin/Heidelberg, Germany, 2003; Volume 2729, pp. 400–425. [Google Scholar]
- Krawczyk, H. HMQV: A High-Performance Secure Diffie-Hellman Protocol. In Proceedings of the Advances in Cryptology-CRYPTO 2005: 25th Annual International Cryptology Conference, Santa Barbara, CA, USA, 14–18 August 2005; Springer: Berlin/Heidelberg, Germany, 2005; Volume 3621, pp. 546–566. [Google Scholar]
- LaMacchia, B.A.; Lauter, K.E.; Mityagin, A. Stronger Security of Authenticated Key Exchange. In Proceedings of the Provable Security, First International Conference, ProvSec 2007, Wollongong, Australia, 1–2 November 2007; Springer: Berlin/Heidelberg, Germany, 2007; Volume 4784, pp. 1–16. [Google Scholar]
- Boyd, C.; Cliff, Y.; Nieto, J.M.G.; Paterson, K.G. Efficient One-Round Key Exchange in the Standard Model. In Proceedings of the Information Security and Privacy, 13th Australasian Conference, ACISP 2008, Wollongong, Australia, 7–9 July 2008; Springer: Berlin/Heidelberg, Germany, 2008; Volume 5107, pp. 69–83. [Google Scholar]
- Okamoto, T. Authenticated Key Exchange and Key Encapsulation in the Standard Model. In Proceedings of the Advances in Cryptology-ASIACRYPT 2007, 13th International Conference on the Theory and Application of Cryptology and Information Security, Kuching, Malaysia, 2–6 December 2007; Springer: Berlin/Heidelberg, Germany, 2007; Volume 4833, pp. 474–484. [Google Scholar]
- Rogaway, P. Nonce-Based Symmetric Encryption. In Proceedings of the FSE, Delhi, India, 5–7 February 2004; Lecture Notes in Computer Science. Springer: Berlin/Heidelberg, Germany, 2004; Volume 3017, pp. 348–359. [Google Scholar]
- Rogaway, P.; Shrimpton, T. A Provable-Security Treatment of the Key-Wrap Problem. In Proceedings of the EUROCRYPT, St. Petersburg, Russia, 28 May–1 June 2006; Lecture Notes in Computer Science. Springer: Berlin/Heidelberg, Germany, 2006; Volume 4004, pp. 373–390. [Google Scholar]
- Kamara, S.; Katz, J. How to Encrypt with a Malicious Random Number Generator. In Proceedings of the FSE, Lausanne, Switzerland, 10–13 February 2008; Lecture Notes in Computer Science. Springer: Berlin/Heidelberg, Germany, 2008; Volume 5086, pp. 303–315. [Google Scholar]
- Bellare, M.; Brakerski, Z.; Naor, M.; Ristenpart, T.; Segev, G.; Shacham, H.; Yilek, S. Hedged Public-Key Encryption: How to Protect against Bad Randomness. In Proceedings of the ASIACRYPT, Tokyo, Japan, 6–10 December 2009; Lecture Notes in Computer Science. Springer: Berlin/Heidelberg, Germany, 2009; Volume 5912, pp. 232–249. [Google Scholar]
- Aiello, W.; Bellovin, S.M.; Blaze, M.; Canetti, R.; Ioannidis, J.; Keromytis, A.D.; Reingold, O. Just fast keying: Key agreement in a hostile internet. ACM Trans. Inf. Syst. Secur. 2004, 7, 242–273. [Google Scholar] [CrossRef]
- Feng, H.; Tang, Q. Computational Robust (Fuzzy) Extractors for CRS-Dependent Sources with Minimal Min-entropy. In Proceedings of the Theory of Cryptography-19th International Conference, TCC 2021, Raleigh, NC, USA, 8–11 November 2021; Part II. Nissim, K., Waters, B., Eds.; Lecture Notes in Computer Science. Springer: Berlin/Heidelberg, Germany, 2021; Volume 13043, pp. 689–717. [Google Scholar] [CrossRef]
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2023 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).