1. Introduction
In many binary communication channels, the majority of errors, besides uniformly distributed single-bit errors, consist of error configurations of several bits that are closely placed in a subsequence of b consecutive bits. We call such a subsequence b-bits byte (b-byte in short). We avoid the term b-burst, since its classical definition requires the first and the last bits to be 1s, while the error configurations considered in the paper have a more general form.
Integer codes are codes over a ring of integers modulo given a positive integer, and have been studied—though only from theoretical point of view—since the beginning of coding theory. Such codes for correcting asymmetric errors are proposed in [
1,
2]. The name "integer codes" appears for the first time in [
3], where such codes are applied to magnetic recording and frame synchronization. Since that time, integer codes have been successfully used in many applications. Error control systems for flash memory [
4,
5,
6,
7] and coded modulation [
8,
9,
10] are two examples for such applications. In [
11], integer codes are applied to cryptographic construction. Integer codes over
with
that correct configurations of error bits in a single
b-byte are found via computer search in [
12,
13,
14,
15,
16]. The specific use of integer codes is presented in [
17].
Herein, we propose an algebraic construction of codes over the ring of integers modulo . The obtained codes can correct at least up to two bit errors in a b-byte. The codes can simultaneously correct some configurations of three or more erroneous bits, but not all possible ones.
The next section contains a summary of existing results and necessary notations and definitions that are required for reading the paper. The proposed construction based on the cyclotomic cosets of 2 modulo
is described in
Section 3.
Section 4 discusses applications of constructed codes to error control in binary channels.
2. Preliminaries
Let us recall the basic definitions concerning integer codes.
Definition 1. Let be the ring of integers modulo A. An integer code of length n with parity-check matrix , is referred to as a subset of , defined bywhere all zero vectors (We will write only if there is no possibility for ambiguity.) is said to be integer code. Let us note that in this paper, the notation only means that has m rows, n columns, and entries from , not that C is a linear code. For the not-prime A, the code is a submodule, not a linear subspace. However in our case, the difference does not concern correcting properties of considered codes.
The idea behind use of integer codes is that they demonstrate better performance in correcting specific types of errors. The parity-check matrix can be chosen, thinking about dominant errors.
Definition 2. Let and be positive integers, The code is said to be a single that is error correctable if it can correct any error vector with only one nonzero entry with value or
The existence of codes with the above defined property implies a lower bound for the size
A of the alphabet:
Indeed, the possible single error vectors must have pairwise disjoint syndromes .
The sequence of bits in a binary communication channel can be considered as a sequence of blocks of bits with the same length b. (We call such blocks b-bytes, but b is not necessarily equal to 8). The advantage of this consideration is that the blocks can be interpreted as nonnegative integers less than , that is, as elements of with Hence, the binary input sequence can be transformed into a sequence of elements of , and then it can be encoded using integer codes over with
It seems the natural choice is , but it is not the right choice in any case. Indeed, the situation is more complex. Note that changing one bit in a b-byte is equivalent to adding or subtracting to the integer corresponding to the b-byte. However, divides , which generates complications. If , there are elements of A that cannot be transmitted over the channel; thus, they must not appear as coordinates of the codewords. Hence, the encoding procedure has to comply with this requirement.
Let be the integer corresponding to a given b-byte sent through the communication channel. At the other end of the channel, the received b-byte may differ in several bits from the original. This difference results in adding a nonzero integer to B, that is, the integer value of the received b-byte is .
Here is the correspondence between single-bit errors and E in a b-byte.
- E1
The -th bit : .
- E2
The -th bit : .
All other error configurations in a single
b-byte correspond to combinations of E1 and E2; thus,
E is a sum of powers (positive or negative) of 2. For example, in the case of transposition of two adjacent different bits (The existence of such errors has been reported in the literature),
or
. Note that the same values correspond to the change of one bit in the
b-byte. It may seem amusing, but the decoding procedure of integer codes corrects the
b-byte. The explanation is in the difference between the corresponding values of
B (in
). We also discuss this fact in
Section 4.
3. Construction of Integer Code
In this section, we propose a construction of a class of integer codes that is based on cyclotomic cosets.
Recall a cyclotomic coset of
q modulo
with leader
s is the set
where
m is the minimal positive integer, such that
. The two cyclotomic cosets are either disjoint,
; or they coincide,
Hereafter, in this paper, .
There are two arguments for our choice:
is coprime with 2; thus, we can use cyclotomic cosets of 2 modulo A.
is the smallest integer greater than . Hence, we have to avoid the use of only as a coordinate of a codeword.
Here are several simple but useful properties of cyclotomic cosets of 2 modulo . Their proofs are straightforward.
- P1
If b has odd divisor d, then divides In partial, if b is odd,
- P2
If , then has length . If there is a cyclotomic coset of length , then divides A.
Lemma 1. If , then the cyclotomic cosets of 2 modulo A have even length. In partial for s and A coprime, the length and Proof. gives . Hence, the order m of 2 modulo A is a divisor of . The assumption leads to , which is a contradiction. Thus, , where , that is, is an even number. Let Let i.e., l be the smallest positive integer such that . If , then thus (see above), Otherwise, we have , where l is the minimal positive integer with this property. Since we have . Hence, The structure of follows from . □
Let S be the set of the leaders of all cyclotomic cosets with length .
Theorem 1. Any integer code over having parity check matrix where can correct single error, .
Proof. Syndromes belong to the coset and since cyclotomic cosets are disjoint, all syndromes corresponding to single errors are pairwise different. □
We have to note that if is the corresponding value to a given bit errors configuration in a b-byte then its cyclic shifts corresponds to . This simple observation leads us to the following
Theorem 2. Let be a set of cyclotomic cosets containing . If there exist such that are disjoint sets of different cosets, then the code with check matrix can correct error values belonging to , and of course, bit error configurations corresponding to them.
Proof. The proof is straightforward. □
4. Application of the Constructed Codes
In this section, we will apply the considered integer codes to correct up to two erroneous bits in a
b-byte. As we have noted in the Introduction, there are binary channels where these types of errors dominate. The experiments with simulations of several channels we have made also confirm this observation. We shall explain the idea behind these simulations by describing in short one such form of optical wireless communication (for an example, we will describe one of our experiments in this direction). We generated a very long random binary sequence and applied simulation procedure of the optical wireless channel given in [
18] to determine the error sequence (the difference between the input and output sequences). Then, with a code of length
n over
in the mind, we divided the error sequence into blocks of
nb-bytes. The next step is to count the number of 1s in each block and how they are distributed among
b-bytes: what part of blocks contain only one 1, what part of blocks have two 1s in one
b-byte, and so on.
Table 1 illustrates the results that we obtained. With the exception of the cases of the very small signal-to-noise ratio (SNR
decibels (dB)), the considered error configurations (columns two and three) are the majority. Very soon (SNR
dB), the error configuration that consists of one erroneous bit per a codeword (see second column of
Table 1) becomes the dominant error type.
Now, let us fix some notations. In this paper, the leftmost bit is the least significant bit and the rightmost bit is the most significant in a b-byte, that is, the latter represents the number .
Let
be an arbitrary
b-byte. Below lists the possible error transformation of
i-th and
-th bits and the corresponds to them the alteration
E of the integer value of the byte.
| T1 | … 0 … 0 … | → | … 1 … 1 … | |
| T2 | … 1 … 1 … | → | … 0 … 0 … | |
| T3 | … 1 … 0 … | → | … 0 … 1 … | |
| T4 | … 0 … 1 … | → | … 1 … 0 … | |
where
and
.
Obviously, the error values
for T1 and T2, while
for T3 and T4. However, since
, we have
as well as
Therefore, we can conclude that cosets , but only for , contain error values E for error configurations T1–T4. (Note that for b, even .)
Hence the set of error values is a proper subset of
Theorem 3. If consists of t cyclotomic cosets, thenis a necessary condition for the existence of an integer code that can correct the error configurations of types T1–T4 defined by . In partial a necessary condition for the code to correct all the considered error configurations T1–T4 is Proof. If
is a parity check matrix of an integer code capable to correct all error configurations T1–T4, the sets of cyclotomic cosets
have to be disjoint, with lengths of
each. Hence, we obtain the following necessary condition (inequality):
Since
t is at most
we obtain (
2). □
Example 1 (
(see
Appendix A.2))
. The minimal b that satisfies inequality (2) (for the minimal ) is , but a required code does not exist. Such a code exists for and . In that case, and Example 2 (
(see
Appendix A.3))
. In this case, a code that corrects all two-bit errors in a single b-byte per a codeword exists: the code with Length is the maximal possible value for the existence of such a code. Example 3 (
(see
Appendix A.1))
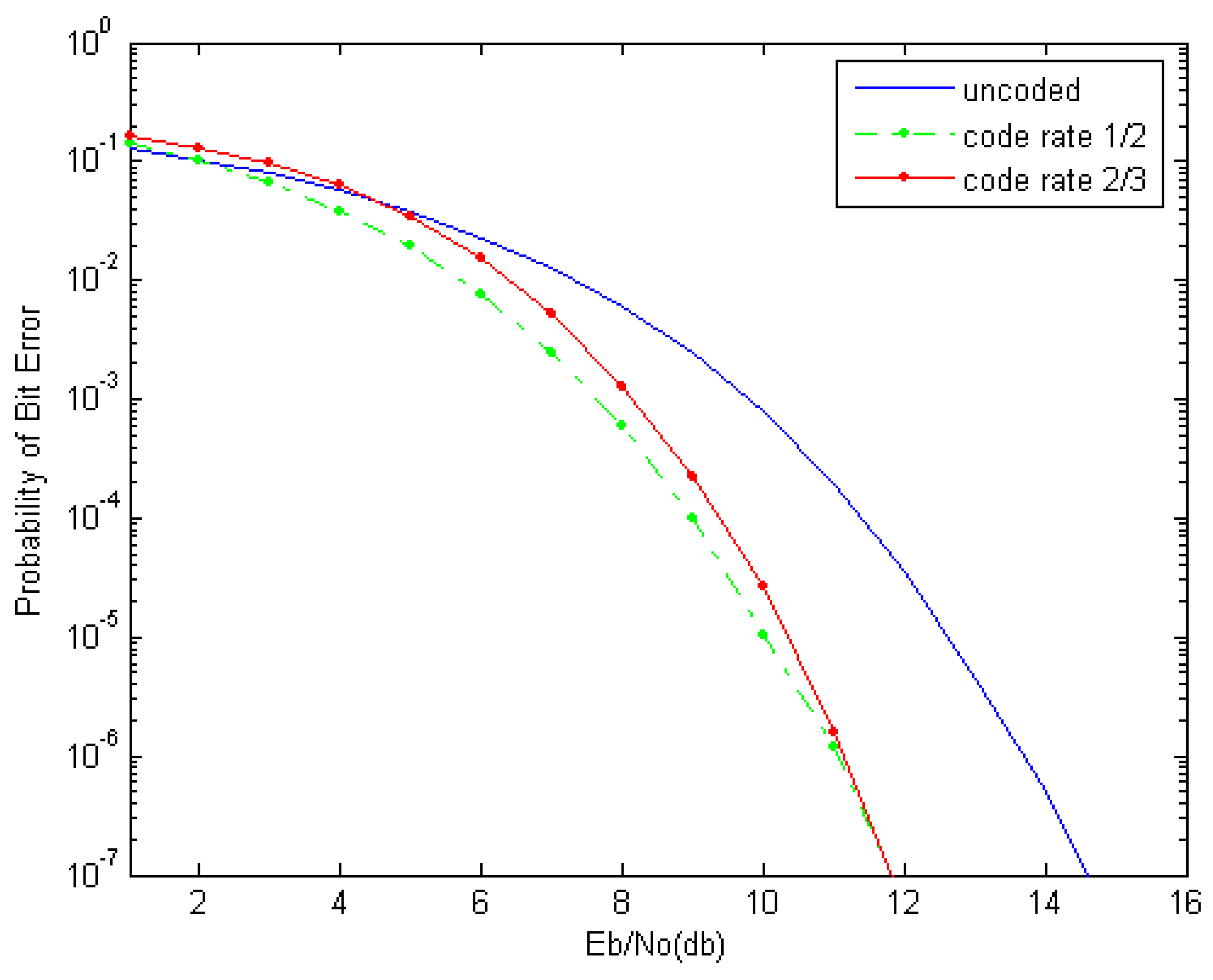
. If we restrict ourselves to , that is, to the case when we correct only erroneous bits that are either adjacent or there is one correct bit between them, we can construct codes with larger rates.When i.e. the code with (the rate is 3/4) corrects a single b-byte of the aforesaid configurations with up to 2 erroneous bits. Indeed, Figure 1 presents in graphical form probability of bit error (BER) versus signal/noise ratio per bit in decibels for the aforesaid simulation of noisy wireless optical channel [
18]. The blue curve gives BER in the case when no error correcting codes are used. The green and red curves correspond to applying the codes given in Example 1 and Example 2, respectively. The reader can note that the code from Example 2 demonstrates slightly worse performance, but this is the price we pay for the higher code rate.
5. Discussion
In this paper, we propose a general construction of codes over , which can be used for correcting two erroneous bits (as well as several specific configurations of erroneous bits) in a single b-byte in a codeword of b-bytes. Like any integer codes, the proposed codes have very simple encoding and decoding without involving arithmetic in finite fields. The proposed construction avoids the exhaustive computer search commonly used for construction similar codes. Determining the cyclotomic cosets of 2 modulo can be performed with the simplest mathematical packages (even manually).
Figure 1 (and other our experiments) show that the proposed codes demonstrate good performance. This performance is in some sense unexpected, since the application of integer codes to the considered binary channel is not so proper as their application to coded modulation and flash memory. For example, we performed a comparison between the code given in Example 2 and a BCH code with close length and rate. Our expectation was for the BCH code to demonstrate better performance since the considered errors are not strongly dominant. However, the results were similar. Hence, with their simple encoding and decoding procedures, integer codes are at least commensurable with other codes with similar parameters, but have complicated encoding and decoding.