Abstract
Referring to the widespread problem of diploma forgery in Indonesian educational institutions as the impetus for UNTIRTA’s latest vision as an “Integrated, Smart, and Green University,” UNTIRTA intends to use blockchain technology to prevent diploma forgery and overcome issues related to existing platforms at UNTIRTA, such as frequent connection interruptions when accessed by a large number of users simultaneously. Before using blockchain technology, UNTIRTA must evaluate several readiness issues. This study presented the interpretative structural modeling (ISM) method to assess the primary preparedness elements for adopting blockchain technology in universities and sought to provide pertinent strategy ideas for UNTIRTA’s blockchain technology application. The results reveal sixteen major parameters that influence the adoption readiness of blockchain technology at UNTIRTA. The primary variables impacting the adoption and deployment of blockchain technology at UNTIRTA are management and employee support and a grasp of the technology. To realize UNTIRTA’s mission as an “Integrated, Smart, and Green University”, the proposed method entails determining an initial agreement in which all stakeholders have a shared understanding and commitment to Blockchain technology implementation at UNTIRTA. The objective of the tactical proposal is to establish each unit’s mission in the blockchain implementation program. The objective of the technical proposal is to construct a planning document that will serve as a coordination tool between the chairman and members, as well as all parties interested in the adoption of Blockchain technology at UNTIRTA.
MSC:
97M10
1. Introduction
The field of education is constantly evolving and adopting new technologies to improve the learning experience for students [1,2]. One technology that has gained significant attention in recent years is blockchain. The use of blockchain technology in education has the potential to revolutionize the way educational institutions manage and distribute information [3]. By using blockchain, educational institutions can securely store and share student records, verify the authenticity of educational degrees, and enable institutions to decide with which other higher education institutions to share data, preventing the forgery or falsification of legitimate credentials (diplomas or certificates) [4]. This technology can help improve the efficiency and transparency of the education system and make it easier for students to access and manage their own educational records. Additionally, the use of blockchain in education can help reduce the potential for fraud and other forms of corruption, as all transactions on the blockchain are transparent and secure. Overall, the use of blockchain in education has the potential to greatly enhance the quality and accessibility of educational opportunities for learners around the world [5].
Education in Indonesia still thrives on keeping pace with the industrial revolution, though there are various problems, such as diploma falsification [6]. Sultan Ageng Tirtayasa University (UNTIRTA) is a public university in the province of Banten, Indonesia. Its latest vision is the realization of UNTIRTA as an Integrated Smart and Green University with Superior Character and Competitiveness in the ASEAN Region by 2030. The industrial revolution 4.0 at the university has various academic platforms that sometimes experience problems, such as connection timed-out when simultaneously accessed by many users. This is because the system is managed centrally, implying the need to fix the problematic platform at the control center. UNTIRTA plans to utilize blockchain as a digital-based technological development to avoid diploma entry and overcome platform-related problems. This is to prevent diploma falsification in educational institutions and is also a driving factor for the vision of UNTIRTA as an Integrated, Smart, and Green University. Blockchain technology is a decentralized distributed ledger that verifies the ownership of digital assets [7]. It is one of the current technologies with many benefits, though its acceptance is still invisible in Indonesian education, especially in UNTIRTA. Therefore, for its adoption, factors such as security, privacy, cost, scalability, and availability of infrastructure and human resources should be considered [8]. However, it is difficult for educational institutions to implement new technologies because they need to consider readiness factors. According to Steiu [9], preparation for adopting blockchain in the education system comprises legal issues, scalability, data privacy, and security. Based on these problems, this study aimed to examine the factors of readiness to adopt blockchain technology and the dependency relationship between readiness. This study also proposes relevant strategies for implementing blockchain technology in the future education system at Sultan Ageng Tirtayasa University.
This study formulates problems regarding the main readiness factors in blockchain adoption and develops a strategic framework for implementing the technology in the education system at UNTIRTA. Therefore, it aims to examine the main readiness factors for blockchain adoption and develop a strategic framework for applying this technology in the education system at UNTIRTA. The results could be useful in the development of science and technology and considerations in policymaking.
The remaining article is organized as follows: Section 2 reviews the blockchain technology adoption models and the proposed method. Section 3 presents the implementation of the proposed approach to identify the key criteria for blockchain technology adoption in universities. In Section 4 and Section 5, the results are analyzed and discussed. Section 6 proposes strategies to successfully adopt blockchain technology in universities. Finally, the conclusions are presented in Section 7.
2. Blockchain Technology, Blockchain Adoption Models and the Proposed Method
Many studies have established evaluation models to analyze the criteria for the adoption of blockchain technology in many areas. This section discusses blockchain technology, blockchain adoption models and the proposed method to determine readiness factors for blockchain technology adoption in higher education institutions.
2.1. Blockchain Technology
Over the course of more than a decade, the technology known as the blockchain has been developed as a system in which a decentralized database keeps track of all the transactions that have ever taken place inside the network. It is considered a paradigm of distributed computing that successfully overcomes problems associated with relying on a single administrator or organization. Due to its distinctive qualities, such as decentralization, reliability, and security, this technology has recently been used in education. Massachusetts Institute of Technology (MIT) Media Lab developed Blockcerts, an open standard for generating, issuing, examining, and validating certificates based on the blockchain. These digital records are registered on a distributed ledger, cryptographically signed, tamper-resistant, and shareable [10]. Cheng et al. [11] developed a system for issuing and validating certificates using blockchain and smart contracts based on Ethereum to solve diploma fraud issues through the use of blockchain. Taufiq et al. [12] proposed a crypto-governance model for processing student documents and diplomas involving several actors using a private blockchain network.
There are three types of blockchains based on the characteristics of the peers who participate in them. Public or permissionless blockchains impose no limits on joining, leaving, or gaining access to the data stored (e.g., Bitcoin, Ethereum, etc.). In private or permissioned blockchains, on the other hand, members may only participate if invited; thus, they are closed systems managed within institutions (e.g., Hyperledger Fabric, Iroha, Quorum, etc.). All information is kept confidential among approved members. Lastly, consortium blockchains are a hybrid of the two preceding categories and are run by a group of institutions with a common aim. In this manner, authorized parties can join or leave the blockchain upon request [13].
2.2. Blockchain Adoption Models
Blockchain technologies have piqued the interest of both academia and businesses because of their unique characteristics, such as data protection, distribution, security, decentralization, and reliability. However, their adoption rate is still low and is thus one of the main reasons for conducting research on user satisfaction and adoption of these technologies. Determining the influencing factors for the use and acceptance of blockchain technology can help to handle their adoption difficulties more effectively [14].
Blockchain adoption studies use a variety of approaches. Based on 902 shortlisted papers and 30 empirical studies that satisfied the qualifying requirements and were comprehensively evaluated, the findings from [14] revealed that the technology-organization-environment and the technology acceptance model were the most common for evaluating blockchain adoption. Other methodologies have also been suggested, such as the maturity model [15] and the machine learning-based model [16].
2.3. Proposed Method
2.3.1. Design
This was a prospective study that used the observation method to collect data on blockchain technology that has not yet been implemented. It is expected to help plan future blockchain implementations in the education system at UNTIRTA. Additionally, this cross-sectional study was conducted only once by providing questionnaires to previously determined respondents. The study is not carried out in the long term to assess changes in subjective opinion.
The determination of the adoption readiness factors in this study is referred to the Blockchain Organizational E-Readiness (BOER) and Blockchain External E-Readiness (BEER) framework models based on Broni [17]. The interpretive structural modeling (ISM) method is used to determine the main readiness factor for blockchain adoption in universities. Also, data were analyzed descriptively and qualitatively through MICMAC analysis to determine the main readiness factors for adoption.
2.3.2. Data Collection Technique
The data were collected through literature studies, questionnaires, and interviews.
- 1.
- Literature Study
Data were collected using the BOER and BEER framework models based on studies on blockchain adoption readiness factors.
- 2.
- Interviews
The interviews were conducted to confirm the blockchain adoption readiness factors from the earlier published studies. Respondents were selected through purposive sampling based on the study objectives.
- 3.
- Questionnaire
Data were also collected by distributing ISM questionnaires to the respondents. In this technique, respondents provide answers using symbols V, A, X, and O to determine the main readiness factors compared to the others.
2.3.3. The Problem-Solving Flow
Figure 1 shows the ISM method and MICMAC analysis to determine the main readiness factors for blockchain adoption in a university.
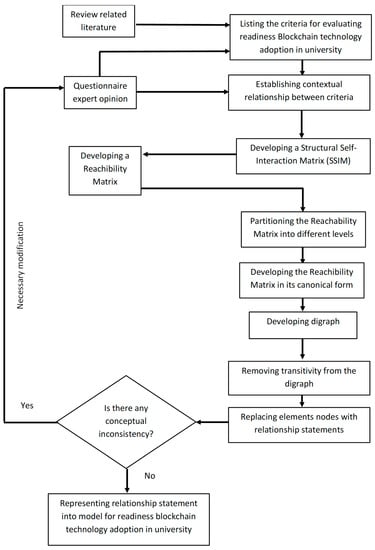
Figure 1.
Proposed method to determine the main readiness factors for blockchain adoption in a university.
The idea behind ISM is to create a hierarchical relational modeling approach based on complex element relationships. A directed graph is drawn after the relational structure model has been examined utilizing experts’ specialized understanding of the contextual connections between elements. ISM uses diagrams and words in a well-crafted pattern to identify and analyze the correlations between particular variables representing an issue, topic, system, or field of study. A structural self-interaction matrix (SSIM) is generated following a pairwise comparison of the variables; it is then transformed into a reachability matrix whose transitivity is examined. A matrix model is created following the completion of the transitivity embedding. Below is a list of the ISM method’s steps [18].
- Step 1
- List the elements relevant to the system;
- Step 2
- Develop the contextual relationship between the elements identified in Step 1;
- Step 3
- Perform pairwise comparisons between the elements to develop an SSIM;
- Step 4
- Generate a reachability matrix based on the SSIM and check the transitivity of the matrix;
- Step 5
- Divide the matrix into different levels;
- Step 6
- Draw a relational graph according to the reachability matrix in Step 3 and remove the transitive links;
- Step 7
- Replace transitive nodes with statements to convert the directed graph obtained in Step 6 into an ISM model;
- Step 8
- Check the conceptual inconsistency of the ISM model and modify the model if necessary.
3. Implementation of the Proposed Approach
This section provides an example of how the model was applied to a higher education institution to validate the suggested methodology for examining problems with blockchain adoption in higher education. Our understanding of creating a readiness factor for implementing blockchain technology in higher education institutions is improved as a result of this approach. The analysis of the preparedness factors and methodology steps are presented below.
3.1. Step 1: Collecting and Defining the Criteria of Blockchain Technology Adoption Factors
The first step in integrating blockchain technology in a university is to gather and create evaluation criteria. Our team consulted five university employees and subject-matter specialists to know their thoughts on the challenges of implementing blockchain technology. This was done through in-person meetings and emails. We also looked at the collection of papers from reputable journals like Springer, Elsevier, and Emerald. Finally, with the aid of industry experts and earlier studies, we pinpointed crucial problems with implementing blockchain technology in a university based on the BOER and BEER framework models [17]. Table 1 lists the blockchain technology adoption readiness factors at UNTIRTA.

Table 1.
Blockchain Technology Adoption Readiness Factors at Sultan Ageng Tirtayasa University (UNTIRTA).
3.2. Step 2: Questionnaire Development Based on the Evaluation Criteria
A questionnaire was created and distributed to university and educational professionals to determine the impact and importance of different variables. E-inquiries and meetings were used for all university and educational relations. We gathered the most important elements influencing the adoption of blockchain technology in a university and started comparing them based on the responses we received.
3.3. Step 3: Analyzing the Blockchain Adoption Criteria Using the Interpretive Structural Modeling Approach
The implementation steps of the ISM are as follows:
- 1.
- Development of the structural self-interaction matrix
ISM is a collaborative learning process with numerous closely connected components. The model has the ability to describe a complex problem’s structure explicitly. The initial stage of the ISM method establishes the contextual relationship between all components through the use of expert opinions. The relationships between the criteria were denoted by the letters V, A, X, and O. We can generate the following evaluations using i and j as the standards:
- A: Criterion j causes criterion i;
- V: Criterion i causes criterion j;
- X: Criterion i causes criterion j, and criterion j causes criterion i;
- O: Criteria i and j are not related.
One component “causes” another means that one factor causes the other. Expert assessments of the link between two parameters provide the foundation of an SSIM. The experts vouch for the inclusion of important agile components by focusing on their interdependence and describing their purpose. The process is complete once all of the experts have given their approval to the specified relationships. In this study, pairwise comparisons were made by the experts. We created the SSIM once the pairwise comparisons were created, as indicated in Table 2.

Table 2.
Structural self-interaction matrix.
Table 2 shows the assessment of the relationship between criteria or elements so that the assessment can represent the respondent’s perception of the relationship between the criteria in question. There are symbols used, namely, the symbol V, which means that the row of criteria affects the column of criteria; the symbol A, which means that the row of criteria affects the column of criteria; the symbol X, which means that the row and column affect each other; and the symbol O, which means that there is no influence at all on the row and column of criteria. The relationship obtained between criteria is then represented in the form of a Structural Self Interaction Matrix (SSIM).
- 2.
- The Reachability matrix
By changing V, A, X, and O in the SSIM to 1 and 0 correspondingly, a binary matrix known as the initial reachability matrix is created. Table 3 lists the guidelines for converting 1 s and 0 s. Table 4 presents the generated initial reachability matrix. The final reachability matrix is generated by Equations (1) and (2).
where I is the identity matrix, k is the power matrix, MR is the reachability matrix, and Mk is the stable or final reachability matrix. The reachability matrix is computed using the addition law and Boolean multiplication (that is, 1 × 1 = 1, 1 × 0 = 0 × 1 = 0, 1 + 1 = 1, 1 + 0 = 0 + 1 = 1, and 0 + 0 = 0). The final reachability matrix shown in Table 5 is the result of the transitivity checks from the ISM approach’s criteria.

Table 3.
The transforming rules for the substitution.

Table 4.
Initial Reachability Matrix.

Table 5.
Final Reachability Matrix.
Table 4 is the initial reachability matrix used to turn the symbols on SSIM into numbers or initial numbers on the reachability matrix by substituting four symbols (V, A, X, or O) with 1 or 0. If the relationship between Ei and Ej on SSIM is V, then the elements Eij and Eji in the reachability matrix are 1 and 0. If the relationship between Ei and Ej on SSIM is A, then Eij = 0 and Eji = 1. If the relationship between Ei and Ej on SSIM equals X, then Eij = 1 and Eji = 1. If the relationship between Ei and Ej on SSIM is O, then Eij and Eji both equal 0 in the reachability matrix.
Table 5 represents the concluding reachability matrix. The initial reachability matrix (Table 4) was examined for transitivity to generate the final reachability matrix. Transitivity is a fundamental assumption, indicating that if A is associated with B and B is associated with C, then A is specifically related to C. From the final reachability matrix, the driving and dependence powers of each criterion were deduced.
The calculation results showed that the highest driving power value was 15 and was located on A7 (Management and staff support) and A8 (Technology understanding).
- 3.
- Level partitions
A partition of the reachability matrix was formed by continually assessing the reachability and prior sets for each criterion. The attainable requirements were part of the reachability set. The criteria and other factors that might help them be achieved were part of the antecedent set. For all criteria, the intersection of these sets was produced. If the criteria migrated in the same direction toward the reachability set and intersection set, they were classified in the first level of the ISM hierarchy. However, the criteria cannot be used to judge other criteria below their level. The same procedure was used to find the criteria for the next level. The criteria, their levels, intersection set, antecedent set, and reachability set are listed in Table 6.

Table 6.
Level Partitioning.
The canonical matrix shown in Table 7 was used to determine levels based on level partitioning. In this case, readiness sub-factors with the same level traverse columns and rows to develop a conical matrix. Table 8 shows the level of each factor based on the canonical matrix.

Table 7.
The Canonical Matrix.

Table 8.
Determination of the Factor Level.
Determining the level of partition with seven iterations shows that the readiness factor for implementing blockchain in university at Level I comprises the use and availability of learning platforms. Level II represents accessibility to relevant learning resources, while level III consists of the affordability and accessibility of IT resources, technological efficiency, and risk and capital. Level IV comprises knowledge of technology use, strategies, and business processes. Level V consists of policies and regulations, government initiatives in technology, and the availability of technical components. Similarly, level VI represents knowledge of technology use and the availability of a skilled workforce, while level VII involves understanding the technology, management, and staff support.
- 4.
- Formation of the ISM Model using a directed graph
A model of the importance of various criteria in the blockchain technology adoption process of the higher education institution in Indonesia was prepared using the data listed in Table 8 (Figure 2).
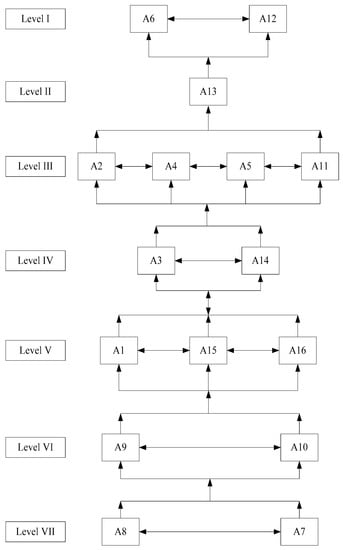
Figure 2.
Interpretive structural modeling-based influence diagram for the blockchain adoption criteria in university.
4. MICMAC Analysis
The MICMAC analysis is shown by the MICMAC diagram, which is categorized into four different clusters, including autonomous, independent, linkage, and dependent. The MICMAC diagram is prepared based on the final reachability matrix with the transitivity rules, where the driving power and dependence values are the y and x-axes, respectively. The readiness factor for blockchain implementation at universities, especially UNTIRTA, is divided into independent, linkage, and dependent sectors. The independent sector has high driving power but low dependence, comprising management and staff support (A7), technology understanding (A8), knowledge of technology use (A9), and skilled workers’ availability (A10). In contrast, the dependent sector has low driving power but high dependence and comprises resource affordability (A2), level of use (A6), availability of learning platforms (A12), and accessibility to relevant learning resources (A13). The linkage sector has high driving power and dependence; it comprises the availability of technical components (A1), government initiatives in technology (A16), IT resources availability (A3), strategies and business processes (A14), risk and capital (A11), policies and regulations (A15), accessibility of IT resources (A4), and technology efficiency (A5). However, there are no sub-factors in the autonomous sector owing to its low driving power and dependence. This shows that all sub-factors of readiness to implement blockchain in UNTIRTA should be considered and prepared carefully to realize a Smart and Green University. The MICMAC analysis results are shown in Figure 3.
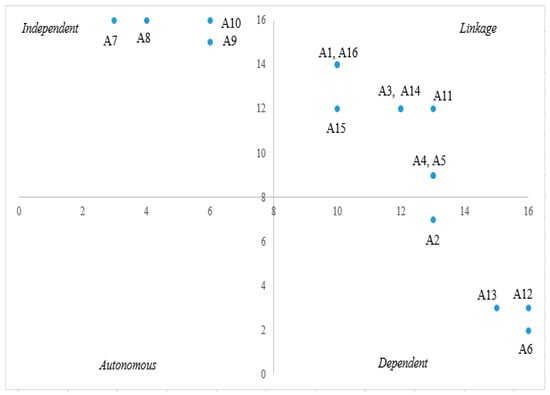
Figure 3.
The MICMAC Analysis Diagram.
5. Discussion
The driving power analysis with the highest and smallest dependence value based on the digraph presented in Figure 2 shows that the key success measure of the blockchain implementation at Sultan Ageng Tirtayasa University is technological understanding (A8), management, and staff support (A7). The two sub-factors are at Level VII and the most robust driving factors to support the other 14 readiness factors with dependence. This supports Alannita and Suaryana [19], which stated that management participation positively affects individual performance. Therefore, the support given by higher leadership for organization-wide information systems is critical in determining the achievement of all information-related activities [20]. Moreover, one requires investing effort to understand how to implement technology in education, such as promoting the technological literacy movement [21].
Level VI comprises the use of knowledge of technology (A9) and the availability of skilled workers (A10). The two factors have a high driving power with little dependence, making them important in implementing blockchain at UNTIRTA. This is in line with Alannita and Suaryana [19], which state that the technical ability of technology and information system users positively affects individual performance. The era of the industrial revolution 4.0 requires skilled workers who adapt to existing technological developments, such as an understanding and the ability to use information and communication technology. Moreover, level VI affects other readiness sub-factors at levels V, IV, III, II, and I and is influenced by readiness factors at level VII.
Level V comprises policies and regulations (A15), government initiatives in technology (A16), and the availability of technical components (A1). The three factors are essential because the driving power and dependence are equally strong. The readiness factors are interrelated because the growth of the Information and Communication Technology (ICT) infrastructure significantly affects the implementation of various government tasks in all fields. These tasks include determining various policies and regulations, developing infrastructure and accessibility, using technology productively, disseminating information and research, and developing human resources [22]. Level V affects readiness sub-factors at levels IV, III, II, and I and is influenced by readiness sub-factors at levels VI and VII.
Level IV comprises the availability of IT resources (A3), business strategies, and processes (A14). These factors are important because the driving power and dependence are equally strong. The two readiness factors are interrelated because strategy formulation promotes appropriate communication in an organization. This affects policy selection to regulate the availability of human resources, budget, technology infrastructure, computer networks, and operators with good skills [23]. Level IV affects readiness sub-factors at levels III, II, and I and is influenced by readiness sub-factors at levels V, VI, and VII.
Level III consists of affordability (A2) and accessibility of IT resources (A4), technology efficiency (A5), and risk and capital (A11). The readiness factors are important because the driving power and dependence are equally robust. The four sub-factors are interrelated due to technology development risk management in an organization. Level III assists in making better decisions and improves the efficiency and effectiveness in allocating human resources, infrastructure, information, applications, security, availability, performance, technical issues, and business risks [24]. Level III also affects the readiness factor at Levels II and I and is influenced by the readiness factor at Levels IV, V, VI, and VII.
Level II represents the accessibility to relevant learning resources (A13), where the readiness factor is less important in developing blockchain at the university due to the weak driving power with high dependence. Nonetheless, it remains yet to be considered by policymakers. Therefore, educators should utilize appropriate and relevant learning resources to equip themselves with abilities and skills and become a success factor in learning. Also, educators need the ability and skills to select the right resources in the technology learning process and, thus, should understand the criteria for selecting learning resources [25]. Accessibility to relevant learning resources affects readiness sub-factors at Level I and is influenced by readiness sub-factors at Levels III, IV, V, VI, and VII.
Level I comprises the level of use (A6) and the availability of a learning platform (A12). At the university, the readiness factor is less important in developing blockchain because of the small driving power and high dependence. Nonetheless, it needs to be considered by policymakers because the implementation of a new system in an institution involving information and communication technology is influenced by user readiness [26]. Applying the right information and communication technology, such as selecting the availability of learning platforms, improves the quality of education and human resources [27]. These two factors are interrelated, and level I is influenced by other factors due to the high dependence value with low driving power.
6. Strategies Proposal to Adopt Blockchain in the University
The study results show that the strongest driving factor for the successful adoption of blockchain technology in UNTIRTA to realize its vision as a smart and green university are management, staff support, and technological understanding. The two sub-factors have the highest driving power supported by the smallest level of dependence. Furthermore, the proposed strategies that support management and staff support factors are:
- (1)
- Performance agreement preparation
a. Strategic proposal
- 1
- Determine the initial agreement where stakeholders build understanding and commitment to the importance of implementing blockchain technology at UNTIRTA to achieve the vision of Smart and Green University.
- 2
- Determine the distribution of performance between the chief and members in each unit or community implementing the blockchain development program at UNTIRTA.
b. Tactical proposal
- 1
- Determine the mission of each unit, the Technical Implementation Unit (UPT). The Smart Campus Information and Service Data Center and Smart and Green Campus units at the university and faculty level achieve the vision of realizing blockchain development at UNTIRTA.
- 2
- Identify performance measures and targets for each chairman and member of the implementing unit of the blockchain development program at UNTIRTA.
c. Technical proposal
- 1
- Conducting a strengths, weaknesses, opportunities, and threats (SWOT) analysis on each implementing unit of the blockchain development program at UNTIRTA to promote mission effectiveness and efficiency.
- 2
- Creating a planning document as a coordination instrument between the chief and members or all parties involved in blockchain development in UNTIRTA.
- (2)
- Preparing general and specific guidelines for blockchain technology development
a. Strategic proposal
- 1
- Determining the long- and short-term goals for each implementing unit for blockchain technology development and implementation at UNTIRTA.
- 2
- Determining references, frameworks, guidelines, and benchmarks in blockchain technology development innovations at UNTIRTA. This helps monitor and regulate blockchain operations, Information and Communication Technology Infrastructure, and accessible global resources.
b. Tactical proposal
- 1
- Determining performance management and distribution in each implementing unit of the blockchain development program to align the design with field implementation per year.
- 2
- Increasing knowledge of the blockchain ecosystem through a clear understanding of the technology, structure, requirements, opportunities, and threats in its application. Also, there is a need to predict the ability and impact of adopting blockchain technology at UNTIRTA.
c. Technical proposal
- 1
- Making performance action plans, such as implementing ongoing operations, duties, and responsibilities of each unit of the blockchain development program in line with the previous plan.
- 2
- Conducting direct or indirect surveys or investigations of parties that have developed blockchain technology in their systems. This helps obtain data and information regarding infrastructure facilities, Internet Service Providers (ISPs), supporting technology, and the availability of capital and human resources needed.
- (3)
- Determination of Budget Allocation for Blockchain Development
a. Strategic proposal
Determining the budget sources for blockchain development in UNTIRTA and allocating them according to the target and the goals planned. It is also conducted based on general and specific guidelines previously formulated by parties involved in the blockchain innovation program at UNTIRTA.
b. Tactical proposal
Planning financial management, starting from preparation, analysis, implementation, and control of financial flows tailored to activities in line with the needs of blockchain implementation to minimize the source of budgets to be issued.
c. Technical proposal
Recording every expenditure and income systematically to monitor every financial flow in UNTIRTA and increase accountability and transparency in financial management. This provides information to the management in making the right decisions regarding blockchain implementation at UNTIRTA.
- (4)
- Preparation of the blockchain development roadmap at UNTIRTA
a. Strategic proposal
Identifying problems through data analysis based on performance and activities conducted. This establishes comparisons according to the performance agreement of the implementing unit of the blockchain innovation program in UNTIRTA, as well as general and specific guidelines with filed facts.
b. Tactical proposal
Review and analysis of field visits, achievements in using budgets, and physical activities, including information and communication technology infrastructure, sophisticated hardware, benefits, impacts, problems, and obstacles faced in blockchain development at UNTIRTA.
c. Technical proposal
Collecting data and information from each performance and activity of each implementing unit adjusted to the targets and goals to help provide the right decisions for further policymaking.
The strategic proposals that support the factors for realizing technological understanding are:
- (1)
- Blockchain Training Program
a. Strategic proposal
UNTIRTA could determine the best-accredited training programs and facilitators in blockchain education, starting from understanding technology theoretically and practically.
b. Tactical proposal
Training academic facilitators and experts at UNTIRTA could design blockchain learning model scenarios theoretically and practically. This would ensure systematic implementation of blockchain technology to produce a conformity evaluation of learning outcomes with the competencies to be achieved.
c. Technical proposal
Conducting analysis on trainers, facilitators, and instructors with appropriate expertise and experience in using blockchain technology.
- (2)
- Blockchain Seminar
a. Strategic proposal
Formulating targets and strategies to be obtained through blockchain education seminars tailored to blockchain development at UNTIRTA.
b. Tactical proposal
Analyze the needs of blockchain seminar instructors and facilitators by considering various aspects, such as the role of the presenter, resource person, language used, use of tools, and software for computer programming languages used for blockchain simulations during seminars.
c. Technical proposal
Training academic facilitators and experts at UNTIRTA could design a blockchain learning model that ensures a systematic conformity evaluation of learning outcomes with the competencies to be achieved.
7. Conclusions
From the study, we know that the readiness factors for blockchain adoption in the education system of UNTIRTA are the availability of technical components (A1), IT resource affordability (A2), IT resource availability (A3), IT resources accessibility (A4), technology efficiency (A5), usage rate (A6), management and staff support (A7), and technology understanding (A8). Other factors are the knowledge of technology use (A9), availability of skilled workers (A10), risk and capital (A11), availability of learning platforms (A12), accessibility to relevant learning resources (A13), business strategies and processes (A14), policies and regulations (A15), and government initiatives in technology (A16). These readiness factors should be considered because they are essential as a whole with different levels of importance. The readiness factors for blockchain applications are not included in the autonomous sector, which requires one or more of the factors to be removed from the system.
Based on the digraph analysis, the strongest driving factors are management and staff support (A7) and technology understanding (A8) in influencing the achievement of the strategic targets of 14 other readiness factors with low dependence on blockchain adoption in the education system of UNTIRTA.
According to the directional graph results, the primary and important readiness factors are management and staff support, as well as technological understanding. Therefore, the strategic target proposals relevant to the management and staff support sub-factors are the preparation of performance agreements, a blockchain development strategic plan, and general and specific guidelines to develop blockchain technology. Other proposals are the preparation of legal documents, public relations and staffing, financial reports, and work evaluation reports. In this case, the planning proposals are categorized as strategic, tactical, and technical. Strategic proposals to support the realization of technology understanding include performing target activities such as training, seminars, and conference programs that educate about blockchain technology. This approach is based on expert comments and may lead to some bias. Furthermore, the numerical validation of the model is yet to be performed. The analytical network process (ANP) could be utilized to evaluate the consistency ratio and index. The hypothetical models might be validated by adopting a linear structural relationship technique, also known as structural equational modeling. As a result, future studies need to focus on validating and improving the framework.
Author Contributions
Conceptualization, V.F.Y. and A.B.; methodology, A.B.; software, A.B. and A.F.; validation, V.F.Y., A.B., P.F.F. and S.-W.L.; formal analysis, A.B., P.F.F. and A.F.; investigation, A.B. and A.F.; resources, V.F.Y.; data curation, V.F.Y., A.B. and P.F.F.; writing—original draft preparation, A.B. and A.F.; writing—review and editing, V.F.Y., A.B., P.F.F. and S.-W.L.; visualization, A.B. and A.F.; supervision, V.F.Y. and S.-W.L.; project administration, V.F.Y.; funding acquisition, V.F.Y. and S.-W.L. All authors have read and agreed to the published version of the manuscript.
Funding
The research of the first author is partially supported by the National Science and Technology Council, Taiwan, under Grant MOST 108-2221-E-011-051-MY3 and the Center for Cyber-Physical System Innovation from the Featured Areas Research Center Program within the framework of the Higher Education Sprout Project by the Ministry of Education in Taiwan. The last author of this study is grateful to the National Science and Technology Council, Taiwan, and the Linkou Chang Gung Memorial Hospital for financially supporting this research under grants NTSC 109-2410-H-182-009-MY3 and BMRPA19, respectively.
Institutional Review Board Statement
Not applicable.
Informed Consent Statement
Not applicable.
Data Availability Statement
Not applicable.
Conflicts of Interest
The authors declare no conflict of interest.
References
- Silverstone, S.; Phadungtin, J.; Buchanan, J. Technologies to Support Effective Learning and Teaching in the 21st Century. In Advanced Technologies; IntechOpen: London, UK, 2009. [Google Scholar]
- Chen, N.-S.; Cheng, I.; Chew, S.W. Evolution is not enough: Revolutionizing current learning environments to smart learning environments. Int. J. Artif. Intell. Educ. 2016, 26, 561–581. [Google Scholar]
- Tapscott, D.; Kaplan, A. Blockchain Revolution in Education and Lifelong Learning; Blockchain Research Institute-Ibm Institute for Business Value: Mountain View, CA, USA, 2019. [Google Scholar]
- Raimundo, R.; Rosário, A. Blockchain system in the higher education. Eur. J. Investig. Health Psychol. Educ. 2021, 11, 276–293. [Google Scholar] [CrossRef] [PubMed]
- Sousa, M.J.; Dal Mas, F.; Gonçalves, S.P.; Calandra, D. AI and Blockchain as New Triggers in the Education Arena. Eur. J. Investig. Health Psychol. Educ. 2022, 12, 445–447. [Google Scholar] [CrossRef] [PubMed]
- BASRA. Buka Usaha Pemalsuan Ijazah, Warga Surabaya Raup Rp 86 Juta. Available online: https://kumparan.com/beritaanaksurabaya/buka-usaha-pemalsuan-ijazah-warga-surabaya-raup-rp-86-juta-1vzVhklpmDy (accessed on 22 June 2021).
- Bucea-Manea-Țoniş, R.; Martins, O.M.; Bucea-Manea-Țoniş, R.; Gheorghiță, C.; Kuleto, V.; Ilić, M.P.; Simion, V.-E. Blockchain Technology Enhances Sustainable Higher Education. Sustainability 2021, 13, 12347. [Google Scholar] [CrossRef]
- Alammary, A.; Alhazmi, S.; Almasri, M.; Gillani, S. Blockchain-based applications in education: A systematic review. Appl. Sci. 2019, 9, 2400. [Google Scholar] [CrossRef]
- Steiu, M.-F. Blockchain in education: Opportunities, applications, and challenges. First Monday 2020, 25, 9. [Google Scholar] [CrossRef]
- About Blockcerts. Available online: https://www.blockcerts.org/about.html (accessed on 8 November 2022).
- Cheng, J.-C.; Lee, N.-Y.; Chi, C.; Chen, Y.-H. Blockchain and smart contract for digital certificate. In Proceedings of the 2018 IEEE International Conference on Applied System Invention (ICASI), Chiba, Japan, 13–17 April 2018; pp. 1046–1051. [Google Scholar]
- Taufiq, R.; Trisetyarso, A.; Kosala, R.; Ranti, B.; Supangkat, S.; Abdurachman, E. Robust Crypto-Governance Graduate Document Storage and Fraud Avoidance Certificate in Indonesian Private University. In Proceedings of the 2019 International Conference on Information Management and Technology (ICIMTech), Jakarta/Bali, Indonesia, 19–20 August 2019; pp. 339–344. [Google Scholar]
- Castro, R.Q.; Au-Yong-Oliveira, M. Blockchain and higher education diplomas. Eur. J. Investig. Health Psychol. Educ. 2021, 11, 154–167. [Google Scholar] [CrossRef] [PubMed]
- AlShamsi, M.; Al-Emran, M.; Shaalan, K. A Systematic Review on Blockchain Adoption. Appl. Sci. 2022, 12, 4245. [Google Scholar] [CrossRef]
- Wang, H.; Chen, K.; Xu, D. A maturity model for blockchain adoption. Financ. Innov. 2016, 2, 12. [Google Scholar] [CrossRef]
- Kamble, S.S.; Gunasekaran, A.; Kumar, V.; Belhadi, A.; Foropon, C. A machine learning based approach for predicting blockchain adoption in supply Chain. Technol. Forecast. Soc. Chang. 2021, 163, 120465. [Google Scholar] [CrossRef]
- Broni, F.E.J. Blockchain Technology Readiness in Firms: Industry Experts’ Perspectives from a Developing Economy; University of Ghana: Accra, Ghana, 2019. [Google Scholar]
- Yu, V.F.; Chiang, F.-Y.; Le, T.H.A.; Lin, S.-W. Using the ISM Method to Analyze the Relationships between Various Contractor Prequalification Criteria. Appl. Sci. 2022, 12, 3726. [Google Scholar] [CrossRef]
- Alannita, N.; Suaryana, I. Pengaruh Kecanggihan Teknologi Informasi, Partisipasi Manajemen, Dan Kemampuan Teknik Pemakai Sistem Informasi Akuntansi Pada Kinerja Individu. J. Akunt. 2014, 10, 354–369. [Google Scholar]
- Dwitrayani, M.C.; Widanaputra, A.; Putri, I.M.A.D. Pengaruh Kecanggihan Teknologi Informasi, Partispasi Manajemen, Budaya Organisasi, dan Kepuasan Pengguna pada Efektivitas Sistem Informasi Akuntansi Bank Pengkreditan Rakyat di Kabupaten Bandung. E-J. Ekon. Dan Bisnis Univ. Udayana 2017, 6, 197–222. [Google Scholar]
- Helaluddin, H. Peningkatan kemampuan literasi teknologi dalam upaya mengembangkan inovasi pendidikan di perguruan tinggi. PENDAIS 2019, 1, 44–55. [Google Scholar]
- Ardipandanto, A.; Budiman, A. Dinamika Pelaksanaan Urusan di Bidang Persandian Pemerintah Daerah; Yayasan Pustaka Obor Indonesia: Jakarta, Indonesia, 2018. [Google Scholar]
- Yohanes, Y. Strategi Penerapan Teknologi Informasi di Pemerintah Kabupaten Sintang Provinsi Kalimantan Barat. JPMIS 2013, 1, 1–22. [Google Scholar]
- Husein, G.M.; Imbar, R.V. Analisis Manajemen Risiko Teknologi Informasi Penerapan Pada Document Management System di PT. JABAR TELEMATIKA (JATEL). JuTISI (J. Tek. Inform. Dan Sist. Inf.) 2015, 1, 2. [Google Scholar]
- Samsinar, S. Urgensi learning resources (sumber belajar) dalam meningkatkan kualitas pembelajaran. Didakt. J. Kependidikan 2020, 13, 194–205. [Google Scholar]
- Qadrya, H.A. Faktor-Faktor Yang Mempengaruhi Kesiapan Penerapan Sistem Single Sign-on di Uin Syarif Hidayatullah Jakarta. Bachelor’s Thesis, Fakultas Sains dan Teknologi Universitas Islam Negeri Syarif Hidayatullah, Banten, Indonesia, 2018. [Google Scholar]
- Munir, D.; IT, M. Pembelajaran jarak jauh berbasis teknologi informasi dan komunikasi. Bdg. Alf. 2009, 24, 277–282. [Google Scholar]
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2023 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).