1. Introduction and Preliminaries
Recent years have shown a significant interest in studying algorithmic problems related to higher-order residuosity. That is because higher-order residuosity may help design cryptographic systems at the binary stream level, while quadratic residuosity is usually limited to bit-by-bit data processing [
1,
2,
3,
4,
5,
6,
7,
8,
9,
10,
11]. Unfortunately, the use of higher-order residuosity in cryptography faces several challenging problems related to the computation of higher-order residues. A lot of research has recently been dedicated to these kinds of problems [
12,
13,
14,
15,
16,
17].
In this paper, we focus on roots of power residues modulo powers of two. Given a positive integer
n,
nth roots of power residues modulo powers of two are solutions to the congruence
where
a is an odd integer and
. This congruence can be easily solved when
or
because in such a case, the multiplicative group
of integers modulo 2
e has primitive roots. For instance, when
,
is a primitive root modulo
. Thus, solving (
1) comes down to finding solutions to the linear congruence
where
is the index of
a with respect to
g [
18,
19]. The congruence (
2) has solutions if and only if the gcd of
n and 2, denoted
, divides
. Moreover, if it has solutions, then it has
solutions in
. Two cases are now to be considered:
n is odd. In this case,
and so the congruence (
2) has exactly one solution in
, no matter
a;
n is even. In this case, the congruence (
2) has solutions if and only if
, which is equivalent to saying that
. Moreover, if the congruence has solutions, then it has exactly two solutions in
, namely 1 and 3.
Solving (
1) when
is harder mainly because
does not have primitive roots. When
n is odd, the unique solution modulo
can be lifted to 2
e in exactly one way. Thus, for
n odd, the congruence (
1) always has a unique solution in
.
The case when
n is even contrasts sharply with the case when
n is odd. It can be shown in this case [
20,
21] that the congruence (
1) is solvable if and only if
, where
. Moreover, if the congruence is solvable, then it has
solutions in
. This result gives information about the solvability of (
1) when
n is even, but it does not say anything about the form of the solutions or how to obtain them. Nor does its proof in [
21] provide a characterization of the solutions.
In this paper, we provide a characterization of the solutions to , where , , k is odd, and . More precisely, we show that each solution to this congruence can be written in the form , where u is uniformly distributed in a set with exactly two odd integers less than , while q is uniformly distributed between 0 and . Moreover, we show that u can be obtained recursively from one of the two integers in the set . This characterization leads to a reasonably efficient algorithm to generate random solutions for the above congruence:
Choose randomly an integer from the set ;
Apply the recursive procedure to in steps to get an integer ;
Randomly generate q between 0 and ;
Return the solution .
We recall some basic notation and terminology on elementary number theory that we are going to use in the paper. For details, the reader is referred to [
18,
19].
The set of integers is denoted by . For two positive integers a and b, stands for the number of combinations of a taken by b.
The gcd of two integers a and b is denoted . a and b are called co-prime if . If m is another integer, then a and b are called congruent modulo m, which are denoted or , if m divides . The remainder of the integer division of a by m, assuming , is denoted .
Given a positive integer m, stands for and . The cardinality of is , where is Euler’s totient function. As a multiplicative group, is cyclic if and only if m is 2, 4, , or for some prime and . When is cyclic, it has generators (also called primitive roots), and each integer can be written as for any generator g and some unique that depends on g. The integer i is called the index of a with respect to g modulo m, which is denoted .
Let
f be a polynomial with integer coefficients,
p be a prime, and
. If
is a solution to the congruence
then
is a solution to the congruence
When a solution
to (
4) gives rise to a solution
a to (
3) such that
, we say that
r is lifted from to . The theorem below provides the lifting criteria.
Theorem 1 (Hensel’s Lemma, [
18,
19])
. Let be a prime integer, , and be a solution to (4). Then, the following properties hold:- 1.
If , where is the formal derivative of f, then r can be lifted from to in a unique way , where q is the unique solution modulo p to the linear congruence; - 2.
If and , then r can be lifted from to in exactly p distinct ways , for all ;
- 3.
If and , then r cannot be lifted from to .
An integer a co-prime with m is an nth residue modulo m, where , if the congruence is solvable. When solvable, any solution to this congruence will be called an nth root of a modulo m.
2. Characterization Results
Let
be an even integer,
a be an odd integer, and
, where
. In the study of the solutions to the congruence (
1), we will distinguish two important cases: the first case is the one in which
, and the second is the one in which
.
Before entering into the treatment of the two cases, we present a technical result.
Lemma 1. Let be an even integer, where . Then, for any , divides , where stands for the floor function.
Proof. Recall from [
22] (Chapter 1, §15) that the highest power of a prime
p that divides
, where
, is given by
Taken
and assuming that
for some
, we obtain
Now, given
, we have
Let , where a is odd. According to the above result, .
The factors , , and so on are all even. There are such factors. As , we conclude that must divide . □
The following lemma completely treats the first case.
Lemma 2. Let a be an odd integer and be an even integer, where . Then, for any , the following two properties hold:
- 1.
is solvable in if and only if ;
- 2.
If the congruence (6) is solvable, then it has solutions in , namely all the odd integers in this set.
The standard proof of Lemma 2 is based on the fact that any odd integer
r fulfills the congruence
for any
(remark that we can only get
by Euler’s theorem). This fact was first noticed in [
21] and can be easily proved by mathematical induction. According to this fact, the congruence (
6) is solvable if and only if
and, when it is solvable, any odd integer is a solution to it.
We can also prove Lemma 2 by using Hensel’s Lemma. For the sake of uniformity and completeness with the second case that we discuss further, we attach in
Appendix A a proof of this type for Lemma 2.
We now turn to the second case mentioned at the beginning of the section.
Theorem 2. Let a be an odd integer and be an even integer, where and k is odd. Then, for any , the following two properties hold:
- 1.
The congruenceis solvable in if and only if . - 2.
If the congruence (7) is solvable, then there exists a set with exactly two odd integers less than such that the set of solutions in to the congruence (7) isand has the cardinality .
Proof. The congruence (
7) is solvable if and only if the congruence
is solvable and at least one of its solutions can be lifted from
to
. According to Lemma 2, the congruence
is solvable if and only if
. We will further show that, when
is solvable, half of its solutions can be lifted, in consecutive steps, from
to
.
For the sake of clarity, we denote by
the set of solution in
to the congruence (
7). According to the division theorem, for any
, there exist unique
u and
q such that
,
, and
. Moreover,
u must be odd. We further use the following notation:
—the set of remainders u of the solutions , as defined above;
—the set of all such that the remainder of dividing r by is u;
—the set of all such that the quotient of dividing r by is even;
—the set of all such that the quotient of dividing r by is odd.
We are now ready to prove by mathematical induction on the following properties:
- (P1)
The set contains exactly two odd integers and . As a result, ;
- (P2)
, for any ;
- (P3)
For any and depending on it, either all solutions in or all solutions in fulfill the lifting requirement from to . Then, is obtained by lifting all solutions r that fulfill the lifting requirement in exactly two ways, namely r and .
Base step:. According to Lemma 2, the solutions to are all the integers in . According to the division theorem, each of them can be written as , where and . Then, we can easily show that the properties and are true.
We focus now on the property . Let . We remark that and, therefore, according to Hensel’s Lemma, a solution can be lifted from to if and only if . The last condition is equivalent to .
Let
, where
and
. Then,
Now, remark that
k and
u are odd and
divides
, for all
(Lemma 1). Therefore,
It remains now to investigate the relationship between
and
a modulo
. Looking back to the binomial expansion of
, we conclude that
. As
(because
), we obtain
. Combining this with
, we get
for some
and integer
, and
for some
and integer
.
Two cases are to be considered now:
. In such a case, . As for all , we obtain for all . This means that all fulfill the lifting requirement from to ;
. This is equivalent to , and therefore, . As in the previous case, we obtain for all and so, all solutions in can be lifted from to .
One has also to remark that if a solution in can be lifted from to , then no solution in can be lifted from to , and vice versa. Moreover, the lifting requirement above is depended on u.
According to Hensel’s Lemma, a solution r is lifted to in exactly two ways, r and . Thus, the property is proved.
Inductive step: Assume that the three properties hold for and we prove them for . The elements of the set are obtained by lifting the elements of either or , depending on , from to .
If
, then
and
where
,
. Therefore, if
is lifted to
, then
and
will include all the integers
with and even
q,
.
If
, then
and
where
,
. Therefore, if
is lifted to
, then
and
will include all the integers
with an odd
q,
.
These show that and hold. The property is proven in a quite similar way as in the base step of the induction, and so it is omitted.
As the three properties , , and hold, we conclude that the theorem holds. □
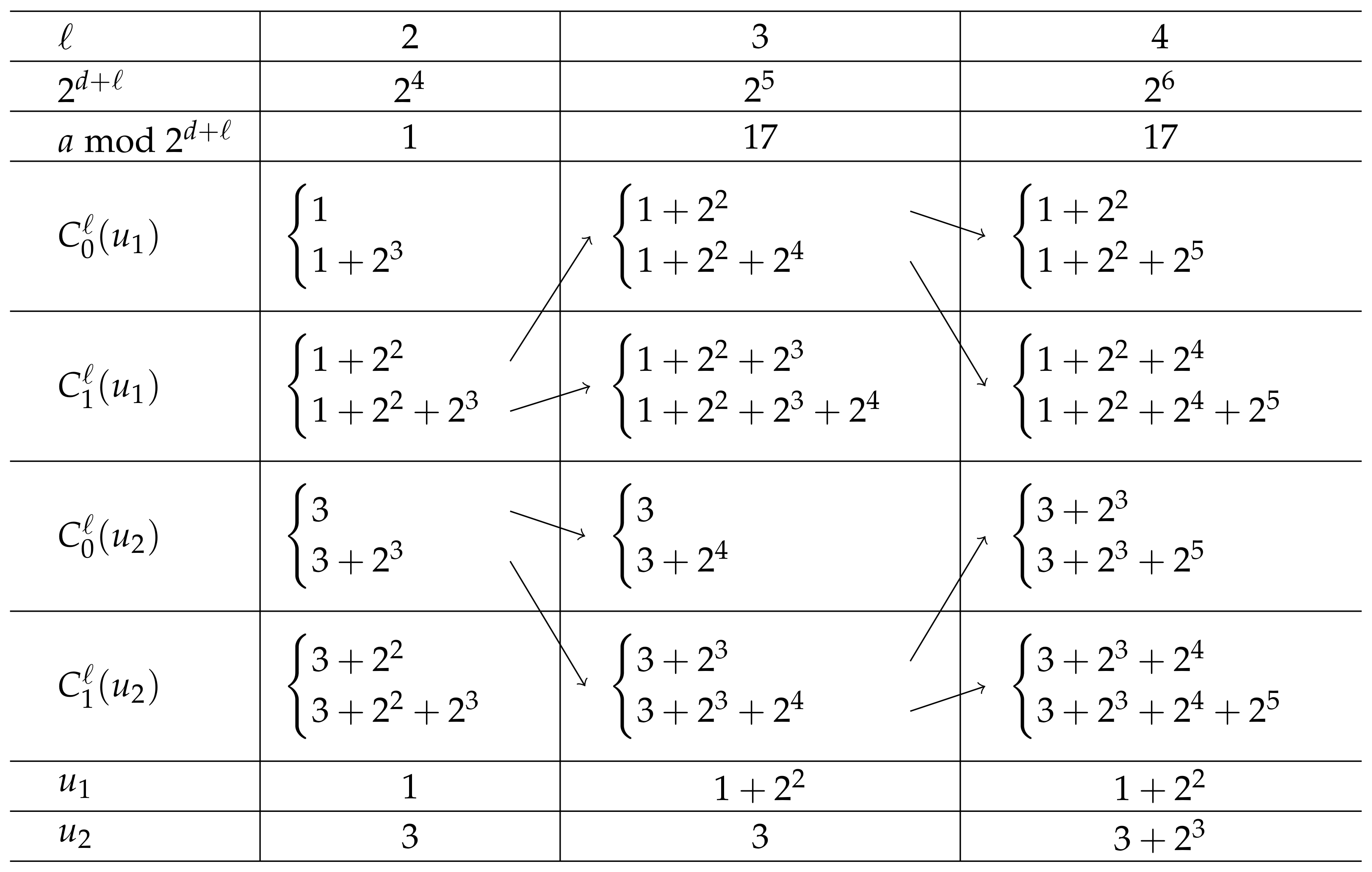
Example 1. Assume that we want to lift the solutions to the congruence to and . In this case, , , , and .
As , the congruence has solutions in . These solutions can be obtained as shown by Lemma 2. They can be lifted to and by the procedure shown in the proof of Theorem 2. The process is illustrated in Figure 1. 3. Computational Aspects
Let
be an even integer,
, and let
a be an odd integer such that
, where
. Finding solutions to the congruence (
6) is easy. According to Lemma 2, any odd integer between 0 and
is a solution to this congruence, and therefore, what we have to do is to generate integers in this interval. If a random integer in this interval is odd, then it is a solution to the congruence. Otherwise, we may increment or decrement it by one to get a solution.
Let us consider now
,
, and
such that
,
is odd, and
. The proof of Theorem 2 leads to an efficient algorithm to generate solutions to the congruence (
7). The algorithm is based on the following remarks:
- 1.
Each solution r has the form , where and ;
- 2.
To compute
r comes down to compute
u. This can be efficiently done in a recursive way starting with some
and updating it by
for all
(
denotes the
th bit in the binary representation of
x);
- 3.
When is reached, randomly choose and return .
The algorithm is presented below.
The correctness of Algorithm 1 follows from the proof of Theorem 2. As one can see, the most complex operation is the modular exponentiation . This step can be optimized by using Euler’s theorem. Namely:
The correctness of this is based on the fact that if
, where
, then
due to the Euler’s theorem, according to which
.
The extraction of the bits of the binary representations of a and , and also the addition and multiplication by powers of two, are very efficient operations that can be neglected.
Hensel’s lifting procedure is a general methodology for lifting solutions to polynomial congruences. Algorithm 1 should be seen as a practical streamlining of the lifting process, reducing the number of operations and the size of the operands. More precisely:
By Hensel’s lifting, we start with an odd integer in the interval and try to lift it in consecutive steps to ;
Assume that we have obtained
in the interval
, where
. If the lifting requirement for
is fulfilled, then
is lifted to
in one of the two possible ways. Otherwise, we go back to
and lift it again in the second possible way if it has not been tried yet. If both lifting possibilities have been tried, then we go back to
. Thus, we are faced with a backtracking process that can be very expensive. For instance, let us look to the table in
Figure 1. The solution
in the second column is lifted to
and then to
. However,
cannot be lifted further and so, we have to go back to
. Even the second lifting possibility for
will not be able to lift further. As a result, we go back to
;
Algorithm 1 completely avoids the backtracking process above;
Hensel’s lifting procedure exponentiates integers in to see if they can be lifted from to . Algorithm 1 exponentiates only two residues modulo to get all solution modulo .
Our discussion above shows that the complexity of Algorihm 1 is , while the complexity of Hensel’s lifting can be estimated to:
Best case: , where ℓ is the parameter in Algorithm 1;
Worst case: , where is the maximum number of backtraking possibilities at the ith lifting.
4. Conclusions
We have proposed a characterization for the roots of power residues modulo powers of two. Namely, by this characterization, each solution to , where , , is odd, and can be written in the form , where is uniformly distributed in a set with two integers les than and q is uniformly distributed between 0 and . Moreover, we have also obtained a recurrence relation for , starting from some .
This characterization leads to a reasonably efficient algorithm to generate random solutions for the above congruence. Finding a way to efficiently compute from , where , would lead to a great improvement of Algorithm 1.